1 SRTP源码下载
源码下载在github采用的库为libsrtp2.5.0:
weget https://github.com/cisco/libsrtp/archive/refs/tags/v2.5.0.tar.gz
2 SRTP交叉编译
新增交叉编译脚本,这里需要支持openssl。
./configure --host=arm-linux-androideabi --prefix=$(pwd)/object --enable-openssl crypto_LIBS="-L$(pwd)/../../third_party/openssl-1.1.0h/lib" crypto_CFLAGS="-I$(pwd)/../../third_party/openssl-1.1.0h/include" && make && make install
下面是交叉编译过程
tar -xvf libsrtp-2.5.0.tar.gz
cd libsrtp-2.5.0
touch config_android.sh
./config_android.sh
./
成果物主要包括头文件和静态库:

3 SRTP移植
3.1 API封装设计
API设计采用handle的实现方式,init只需要进程初始化一次。srtp_app_alloc需要每次会话创建都进行一次初始化,需要传入srtp秘钥。protect和unprotect是实时进行加解密操作。
//srtp handle
typedef struct srtp_handle_t{int (*protect)(void *pthis, void *rtp, size_t *pkt_octet_len);int (*unprotect)(void *pthis, void *audio_dat, size_t *pkt_octet_len);void* priv;
}srtp_handle_t;#ifdef __cplusplus
extern "C" {
#endif
// 初始化
int srtp_app_init();
void srtp_app_denit();
//会话创建
int srtp_app_alloc(srtp_handle_t **pthis, const char *srtp_dec, const char *srtp_enc);
void srtp_app_free(srtp_handle_t *pthis);
3.2 初始化实现
初始化和反初始化,只需要在开启进程初始化一次。
int srtp_app_init()
{int ret = srtp_init();if(ret < 0)return -1;return 0;
}void srtp_app_denit()
{srtp_shutdown();
}
3.3 会话创建实现
会话创建和销毁,需要每次建立会话都要重新创建,每次的秘钥都需要采用协商的加密和解密秘钥。
static int srtp_app_set_crypto_suites(int profile, srtp_crypto_policy_t *rtp)
{if(rtp == NULL){return -1;}switch (profile){case rl_srtp_profile_aes128_cm_sha1_32:{srtp_crypto_policy_set_aes_cm_128_hmac_sha1_32(rtp);rl_log_debug("loc srtp_profile_aes128_cm_sha1_32");break;}case rl_srtp_profile_aes128_cm_sha1_80:{srtp_crypto_policy_set_aes_cm_128_hmac_sha1_80(rtp);rl_log_debug("loc srtp_profile_aes128_cm_sha1_80");break;}case rl_srtp_profile_aes256_cm_sha1_32:{srtp_crypto_policy_set_aes_cm_256_hmac_sha1_32(rtp);rl_log_debug("loc srtp_profile_aes256_cm_sha1_32");break;} case rl_srtp_profile_aes256_cm_sha1_80:{srtp_crypto_policy_set_aes_cm_256_hmac_sha1_80(rtp);rl_log_debug("loc srtp_profile_aes256_cm_sha1_80");break;}default:{rl_log_debug("loc policy none");break;}}return 0;}static int srtp_app_start(void *pthis, const char *srtp_dec, const char *strp_enc)
{rl_log_debug("SRTP start");srtp_config_t srtp_config_loc;srtp_config_t srtp_config_dist;srtp_handle_t *p = (srtp_handle_t *)pthis;if((!pthis || !srtp_dec || !strp_enc || strlen(srtp_dec) == 0 || strlen(strp_enc) == 0))return -1;srtp_handle_priv_t* priv = p->priv;if (!priv)return -1; int ret = srtp_parse_config(strp_enc, &srtp_config_loc);if ( ret < 0 ){return ret;}ret = srtp_parse_config(srtp_dec, &srtp_config_dist);if ( ret < 0 ){return ret;}priv->srtp_opt = 1; memcpy(priv->srtp_params.key_loc, srtp_config_loc.key, 30);memcpy(priv->srtp_params.key_dist, srtp_config_dist.key, 30);srtp_app_set_crypto_suites(srtp_config_loc.profile, &priv->srtp_params.policy_loc.rtp);priv->srtp_params.policy_loc.key = priv->srtp_params.key_loc;priv->srtp_params.policy_loc.next = NULL;srtp_app_set_crypto_suites(srtp_config_dist.profile, &priv->srtp_params.policy_dist.rtp);priv->srtp_params.policy_dist.ssrc.type = ssrc_any_inbound;priv->srtp_params.policy_dist.key = priv->srtp_params.key_dist;priv->srtp_params.policy_dist.next = NULL;rl_log_debug("srtp_create ret=%i", srtp_create(&priv->srtp_params.scall_session, &priv->srtp_params.policy_dist));return 0;
}static void srtp_app_stop(void *pthis)
{srtp_handle_t *p = (srtp_handle_t *)pthis;if(!pthis)return;srtp_handle_priv_t* priv = p->priv;if (!priv)return;rl_log_debug("SRTP stop\n");if (priv->srtp_opt > 0){priv->srtp_opt = 0;priv->srtp_params.prev_ssrc = 0;rl_memset(priv->srtp_params.key_loc, 0, sizeof(priv->srtp_params.key_loc));rl_memset(priv->srtp_params.key_dist, 0, sizeof(priv->srtp_params.key_dist));rl_log_debug("srtp_dealloc ret=%i", srtp_dealloc(priv->srtp_params.scall_session)); }
}int srtp_app_alloc(srtp_handle_t **pthis, const char *srtp_dec, const char *srtp_enc)
{if(!pthis)return -1;srtp_handle_t* p = (srtp_handle_t*)malloc(sizeof(srtp_handle_t));if (p == NULL){rl_log_err("[%s-%d] malloc failed.",__FUNCTION__, __LINE__);return -1;}memset(p, 0, sizeof(srtp_handle_t));p->protect = srtp_app_protect;p->unprotect = srtp_app_unprotect;p->priv = (srtp_handle_priv_t *)malloc(sizeof(srtp_handle_priv_t));if(!p->priv){free(p);return -1;}memset(p->priv , 0, sizeof(srtp_handle_priv_t));int ret = srtp_app_start(p, srtp_dec, srtp_enc);if (ret != 0){srtp_app_free(p);return -1;}*pthis = p;return 0;}void srtp_app_free(srtp_handle_t *pthis)
{if(!pthis)return;srtp_app_stop(pthis);if (pthis->priv){free(pthis->priv);pthis->priv = NULL;}free(pthis);}
3.4 加解密实现
加密和解密只需要传入rtp封装后的数据和长度即可进行加解密操作,操作后数据是直接替换原数据的。
static int srtp_app_protect(void *pthis, void *rtp, size_t *pkt_octet_len)
{ if(!pthis || !rtp || !pkt_octet_len)return -1;int ret = 0;unsigned int current_ssrc;srtp_handle_t *p = (srtp_handle_t *)pthis;srtp_handle_priv_t* priv = p->priv;if (!priv)return -1;srtp_t session = priv->srtp_params.scall_session;if(priv->srtp_opt){ current_ssrc = *((unsigned int *)((char *)rtp + 8));current_ssrc = htonl(current_ssrc);if(priv->srtp_params.prev_ssrc != current_ssrc) {if (priv->srtp_params.prev_ssrc > 0 ){srtp_app_remove_stream(priv->srtp_params.scall_session, priv->srtp_params.prev_ssrc);}priv->srtp_params.policy_loc.ssrc.type = ssrc_specific;priv->srtp_params.policy_loc.ssrc.value = current_ssrc;rl_log_debug("new ssrc 0x%x, %u", current_ssrc,current_ssrc);srtp_app_add_stream(priv->srtp_params.scall_session, &priv->srtp_params.policy_loc);priv->srtp_params.prev_ssrc = current_ssrc;}ret = srtp_protect(priv->srtp_params.scall_session, rtp, (int *)pkt_octet_len);if(ret > 0){rl_log_err("--srtp_protect problem ret=%i", ret);return -1;}}return 0;
}static int srtp_app_unprotect(void *pthis, void *audio_dat, size_t *pkt_octet_len)
{if(!pthis || !audio_dat || !pkt_octet_len)return -1;int ret = 0;srtp_handle_t *p = (srtp_handle_t *)pthis;srtp_handle_priv_t* priv = p->priv;if (!priv)return -1;srtp_t session = priv->srtp_params.scall_session;if(priv->srtp_opt){ret = srtp_unprotect(priv->srtp_params.scall_session, audio_dat, (int *)pkt_octet_len);if(ret > 0){/* If the decryption fail then d'nt give this packet to DSP throw the packets */rl_log_err("rtp_SRtpPlRecv srtp unencryption problems ret=%i", ret);return -1;}}return 0;
}
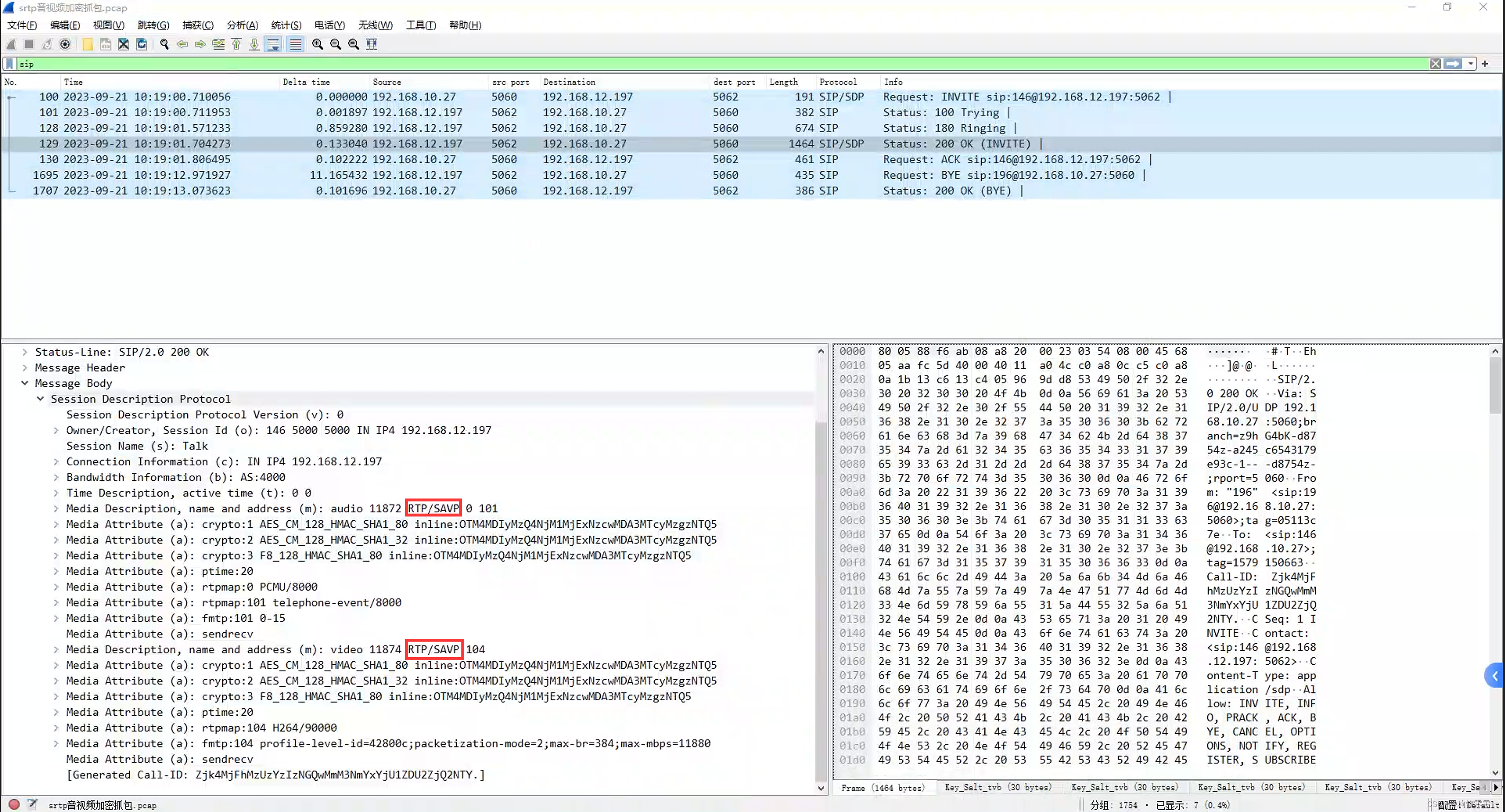
4 SRTP抓包分析
SRTP加密后可以通过wareshark抓包看到协议部分是显示SRTP,具体如下图所示。
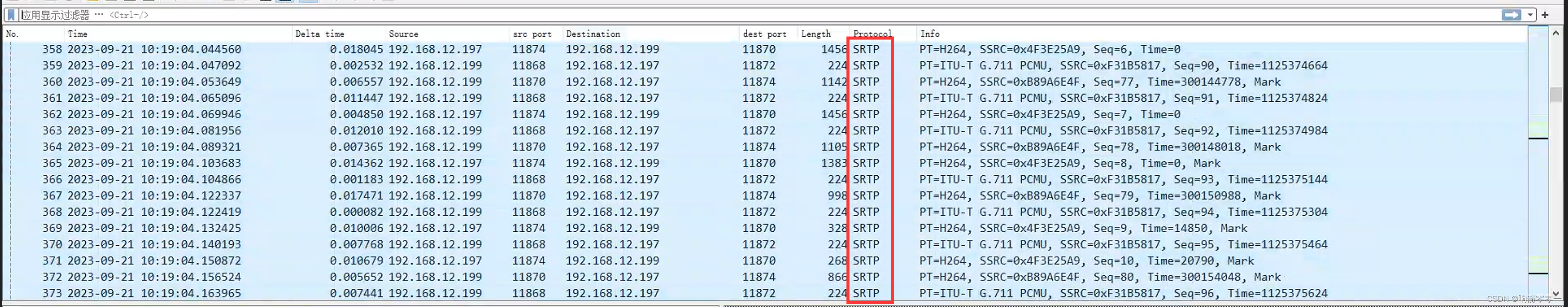
其实wareshark是通过sip协商RTP/SAVP来显示srtp的标识,所以SDP协商一定要正确。