1、简介
Xilinx FPGA、SOC器件和自适应计算加速平台(ACAPs)通常由多个硬件和软件二进制文件组成,用于启动这些设备后按照预期设计进行工作。这些二进制文件可以包括FPGA比特流、固件镜像、bootloader引导程序、操作系统和用户选择的应用程序,它们可以以非安全和安全的方式进行加载。
Bootgen是一个Xilinx工具,用于整合二进制文件并且生成设备引导镜像文件。同时Bootgen在给Xilinx设备创建boot images时,定义了输入的多种特征、属性和参数。
Bootgen同时提供了GUI接口和命令行选项。集成到Vitis中的GUI用于生成基本的boot images,除此之外的多数Bootgen选项都是命令行驱动的。驱动Bootgen的是一个boot image format(BIF)配置文件,后缀.bif。
2、Boot Image结构
2.1 说明
创建一个boot image包含如下两步:
(1)创建一个BIF文件;
(2)运行Bootgen可执行文件来创建一个boot image。
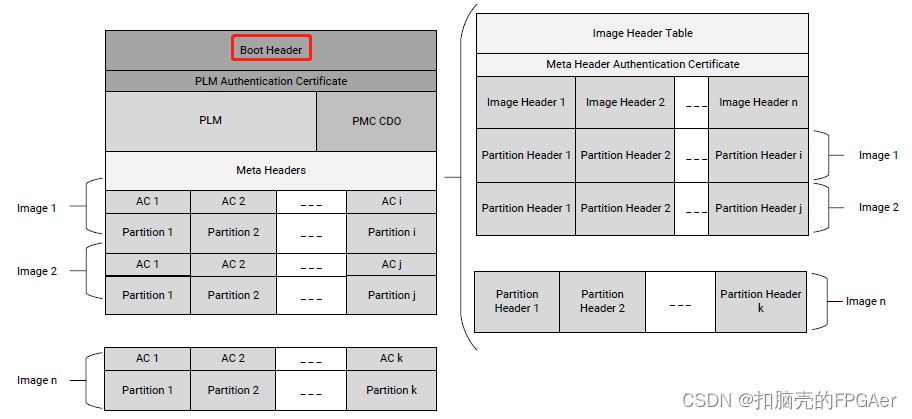
Xilinx不同系列的boot image格式是不同的,这里我们只学习记录下Versal ACAP的boot image,下图是Versal ACAP boot image的组件,也被称为Programmable Device Image(PDI)。
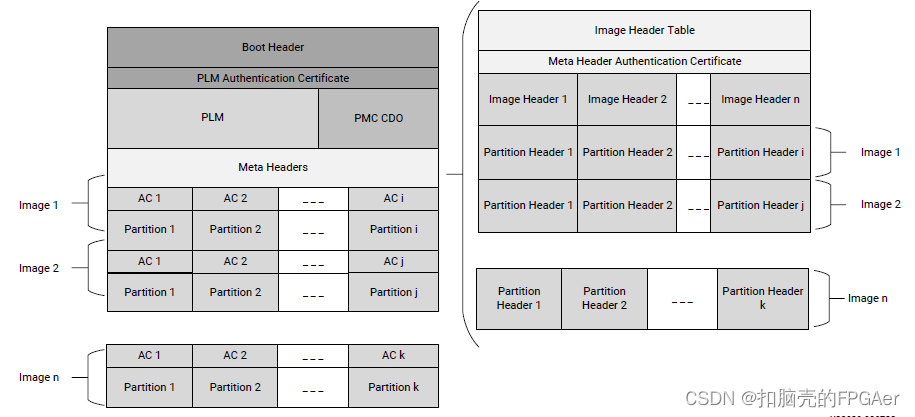
2.2 PMC
Versal ACAP中的平台管理控制器主要用于boot和配置。我们重点关注的是两个PMC MicroBlaze处理器(ROM code unit(RCU) / platform processing unit(PPU))处理的boot image。
(1)RCU
ROM code unit包含了一个三重冗余MicroBlaze处理器和一个ROM,该ROM中包含了BootROM可执行文件。BootROM可执行文件不能被改变。RCU中的MicroBlaze用于验证和运行BootROM可执行文件。RCU还负责启动后的安全监控,以及物理防克隆功能(physical unclonable function,PUF)管理
(2)PPU
Platform processing unit也包含了一个三重冗余MicroBlaze处理器,以及一个专用的384KB大小的PPU RAM。这个MicroBlaze用于运行平台加载和管理器(platform loader and manager)。
在Versal ACAP中,自适应引擎(PL)由rCDO和rNPI文件组成。rCDO文件主要包含CFrame数据以及PL和NoC电源域初始化命令。rNPI文件包含与NPI块相关的配置数据。NPI区块包括NoC元素:NMU、NSU、NPS、NCRB;DDR、XPHY、XPIO、GTY、MMCM等。
2.3 Versal ACAP Boot Header
在boot image的顶部就是Boot Header:
PMC的BootROM会使用这里的Boot Header。基于Boot Header里面的属性信息,PMC BootROM可以验证平台加载和管理器(PLM),并将PLM加载进PPU的RAM中。
Boot Header的前16字节用于检测SelectMAP总线。PMC的BootROM和PLM会忽略这些数据,因此Bootgen在进行checksum/SHA/RSA/加密等操作时不会包含这些数据。前16字节有以下3种情况:
-
X8: [LSB] 00 00 00 DD 11 22 33 44 55 66 77 88 99 AA BB CC [MSB]
-
X16: [LSB] 00 00 DD 00 22 11 44 33 66 55 88 77 AA 99 CC BB [MSB]
-
X32: [LSB] DD 00 00 00 44 33 22 11 88 77 66 55 CC BB AA 99 [MSB]
以实际的PDI文件为例:
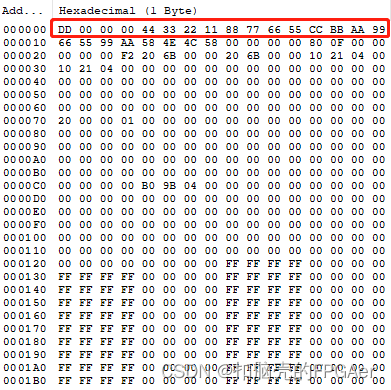
默认的SelectMAP位宽就是X32。
Boot Header具体格式如下:
| Offset (Hex) | Size (Bytes) | Description | Details |
| 0x00 | 16 | SelectMAP bus width | Used to determine if the SelectMAP bus width is x8, x16, or x32 |
| 0x10 | 4 | QSPI bus width | QSPI bus width description. This is required to identify the QSPI flash in single/dual stacked or dual parallel mode. 0xAA995566 in the little endian format. |
| 0x14 | 4 | Image identification | Boot image identification string. Contains 4 bytes X, N, L, X in byte order, which is 0x584c4e58 in the little endian format. |
| 0x18 | 4 | Encryption key source | This field is used to identify the AES key source: 0x00000000 0x00000000 - Unencrypted 0xA5C3C5A3 - eFUSE red key 0xA5C3C5A5 - eFUSE black key 0x3A5C3C5A - BBRAM red key 0x3A5C3C59 - BBRAM black key 0xA35C7C53 - Boot Header black key |
| 0x1C | 4 | PLM source offset | PLM source start address in PDI |
| 0x20 | 4 | PMC data load address | PMC CDO address to load |
| 0x24 | 4 | PMC data length | PMC CDO length |
| 0x28 | 4 | Total PMC data length | PMC CDO length including authentication and encryption overhead |
| 0x2C | 4 | PLM length | PLM original image size |
| 0x30 | 4 | Total PLM length | PLM image size including the authentication and encryption overhead |
| 0x34 | 4 | Boot header attributes | Boot Header Attributes |
| 0x38 | 32 | Black key | 256-bit key, only valid when encryption status is set to black key in boot header |
| 0x58 | 12 | Black IV | Initialization vector used when decrypting the black key |
| 0x64 | 12 | Secure header IV | Secure header initialization vector |
| 0x70 | 4 | PUF shutter value | Length of the time the PUF samples before it closes the shutter Note: This shutter value must match the shutter value that was used during PUF registration. |
| 0x74 | 12 | Secure Header IV for PMC Data | The IV used to decrypt secure header of PMC data. |
| 0x80 | 68 | Reserved | Populate with zeroes. |
| 0xC4 | 4 | Meta Header Offset | Offset to the start of meta header |
| 0xC8-0x124 | 96 | Reserved | |
| 0x128 | 2048 | Register init | Stores register write pairs for system register initialization |
| 0x928 | 1544 | PUF helper data | PUF helper data |
| 0xF30 | 4 | Checksum | Header checksum |
| 0xF34 | 76 | SHA3 padding | SHA3 standard padding |
2.4 Boot Header Attributes
| Field Name | Bit Offset | Width | Default Value | Description |
| Reserved | [31:18] | 14 | 0x0 | Reserved for future use, Must be 0 |
| PUF Mode | [17:16] | 2 | 0x0 | 0x3 - PUF 4K mode. 0x0 - PUF 12K mode. |
| Boot Header Authentication | [15:14] | 2 | 0x0 | 0x3 - Authentication of the boot image is done, excluding verification of PPK hash and SPK ID. All others - Authentication will be decided based on eFUSE RSA/ECDSA bits. |
| Reserved | [13:12] | 2 | 0x0 | Reserved for future use, Must be 0 |
| DPA counter measure | [11:10] | 2 | 0x0 | 0x3 - Enabled All others disabled. (eFUSE over rides this) |
| Checksum selection | [9:8] | 2 | 0x0 | 0x0, 0x1, 0x2 - Reserved 0x3 - SHA3 is used as hash function to do Checksum. |
| PUF HD | [7:6] | 2 | 0x0 | 0x3 - PUF HD is part of boot header All other - PUF HD is in eFUSE. |
| Reserved | [5:0] | 6 | 0x0 | Reserved |
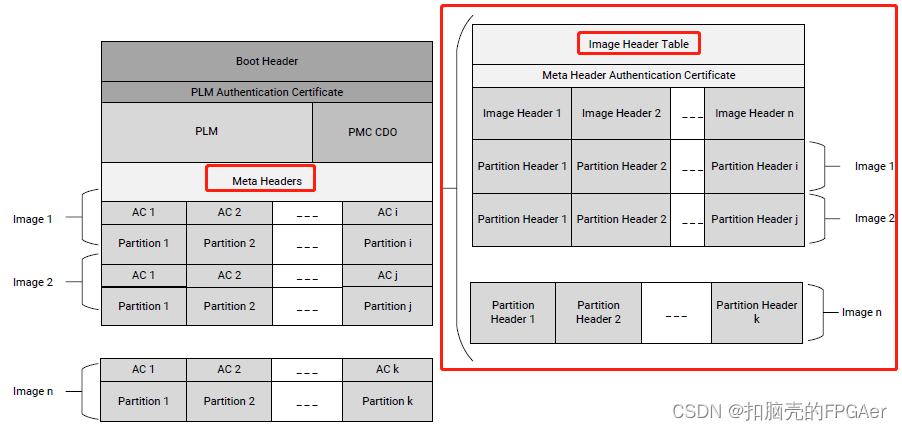
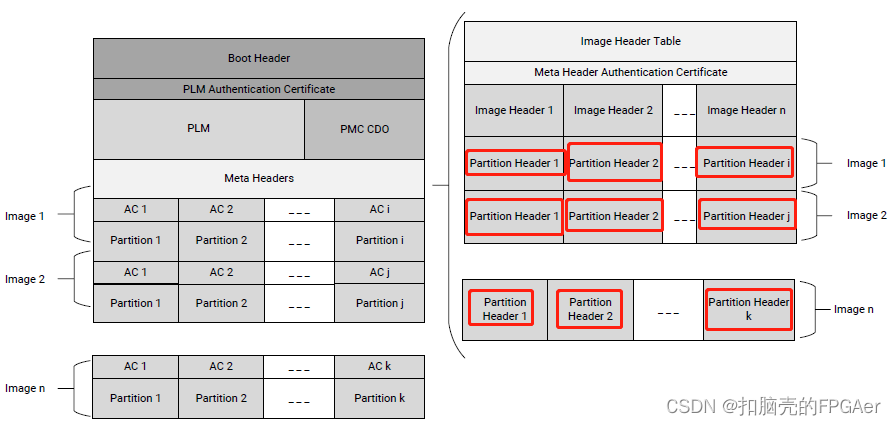
2.5 Versal ACAP Image Header Table
要找到Image Header Table,需要先在Boot Header中找到0xC4 Meta Header Offset:
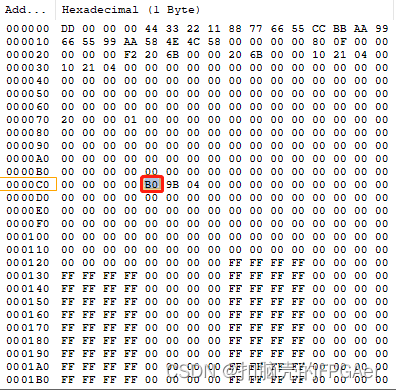
从实际的PDI 0xc4地址开始的4字节的值为0x00 0x04 0x9B 0xB0,那么Meta Header offset为0x0004_9BB0
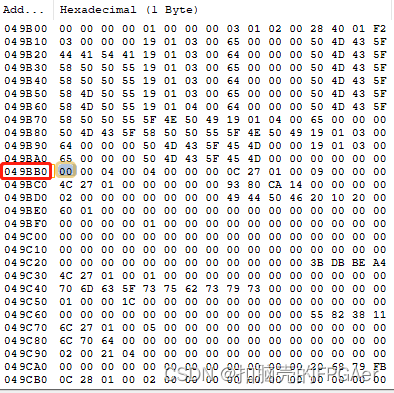
Image Header表内容如下:
| Offset | Name | Description |
| 0x0 | Version | 0x00040000(v4.0) : 1. Added AAD support for IHT. 2. Hash is included into the 32k secure chunk. 0x00030000(v3.0): updated secure chunk size to 32 KB from 64 KB 0x00020000(v2.00): IHT, PHT sizes doubled |
| 0x4 | Total Number of Images | Total number of images in the PDI |
| 0x8 | Image header offset | Address to start of first image header |
| 0xC | Total Number of Partitions | Total number of partitions in the PDI |
| 0x10 | Partition Header Offset | Offset to the start of partitions headers |
| 0x14 | Secondary boot device address | Indicates the address where secondary image is present. This is only valid if secondary boot device is present in attributes |
| 0x1C | Image Header Table Attributes | Refer to Table 22: Versal ACAP Image Header Table Attributes |
| 0x20 | PDI ID | Used to identify a PDI |
| 0x24 | Parent ID | ID of initial boot PDI. For boot PDI, it will be same as PDI ID |
| 0x28 | Identification string | Full PDI if present with boot header –“FPDI” Partial/Sub-system PDI – “PPDI” |
| 0x2C | Headers size | 0-7: Image header table size in words 8-15: Image header size in words 16-23: Partition header size in words 24-31: Reserved |
| 0x30 | Total meta header length | Including authentication and encryption overhead (excluding IHT and including AC) |
| 0x34 -0x3C | IV for encryption of meta header | IV for decrypting SH of header table |
| 0x40 | Encryption status | Encryption key source, only key source used for PLM is valid for meta header. 0x00000000 - Unencrypted 0xA5C3C5A3 - eFuse red key 0xA5C3C5A5 - eFUSE black key 0x3A5C3C5A - BBRAM red key 0x3A5C3C59 - BBRAM black key 0xA35C7C53 - Boot Header black key |
| 0x48 | Meta Header AC Offset (Word) | Word Offset to Meta Header Authentication Certificate |
| 0x4c | Meta Header Black/IV | IV that is used to encrypt the Black key used to encrypt the Meta Header. |
| 0x44 - 0x78 | Reserved | 0x0 |
| 0x7C | Checksum | A sum of all the previous words in the image header table |
Image Header Table Attributes表如下:
| Bit Field | Name | Description |
| 31:14 | Reserved | 0 |
| 14 | PUF Helper Data Location | Location of the PUF Helper Data efuse/BH |
| 12 | dpacm enable | DPA Counter Measure enable or not |
| 11:6 | Secondary boot device | Indicates the device on which rest of the data is present in. 0 - Same boot device (default) 1 - QSPI32 2 - QSPI24 3 - NAND 4 - SD0 5 - SD1 6 - SDLS 7 - MMC 8 - USB 9 - ETHERNET 10 - PCIe 11 - SATA 12 - OSPI 13 - SMAP 14 - SBI 15 - SD0RAW 16 - SD1RAW 17 - SDLSRAW 18 - MMCRAW 19 - MMC0 20 - MMC0RAW All others are reserved Note: These options are supported for various devices in Bootgen. For the exact list of secondary boot devices supported by any device, refer to its corresponding Systems Software Developers Guide (SSDG). |
| 5:0 | Reserved |
从Image Header Table的地址0x1c查到Image Header Table Attributes的4字节内容为0x0000_0000:
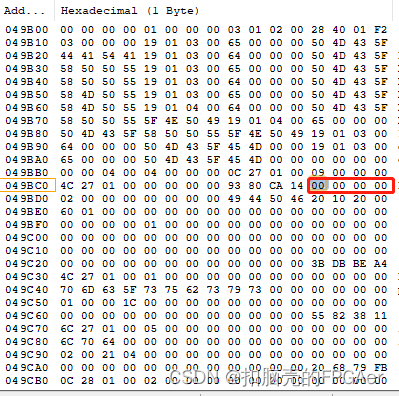
2.6 Versal ACAP Image Header
要找到Image Header,需要先在Image Header Table中找到地址0x8 Image header offset的4字节内容:
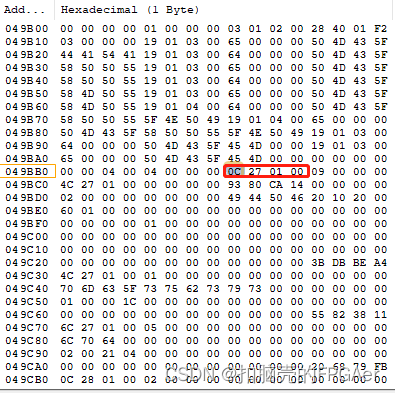
4字节内容为0x0001_270c,即Image Header是从地址0x0001_270c开始:
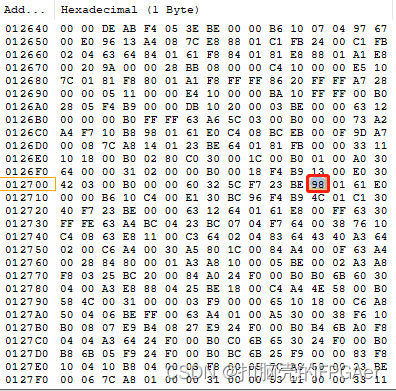
Image Header内容如下:
| Offset | Name | Description |
| 0x0 | First Partition Header | Word offset to first partition header |
| 0x4 | Number of Partitions | Number of partitions present for this image |
| 0x8 | Revoke ID | Revoke ID for Meta Header |
| 0xC | Image Attributes | See Image Attributes table |
| 0x10-0x1C | Image Name | ASCII name of the image. Max of 16 characters. Fill with Zeros when padding is required. |
| 0x20 | Image/Node ID | Defines the resource node the image is initializing |
| 0x24 | Unique ID | Defines the affinity/compatibility identifier when required for a given device resource |
| 0x28 | Parent Unique ID | Defines the required parent resource UID for the configuration content of the image, if required |
| 0x2c | Function ID | Identifier used to capture the unique function of the image configuration data |
| 0x30 | DDR Low Address for Image Copy | The DDR lower 32-bit address where the image should be copied when memcpy is enabled in BIF |
| 0x34 | DDR High Address for Image Copy | The DDR higher 32-bit address where image should be copied when memcpy is enabled in BIF |
| 0x38 | Reserved | |
| 0x3C | Checksum | A sum of all the previous words. |
Image Header Attibutes内容如下:
| Bit Field | Name | Description |
| 31:9 | Reserved | 0 |
| 8 | Delay Hand off | 0 – Handoff the image now (default) 1 – Handoff the image later |
| 7 | Delay load | 0 – Load the image now (default) 1 – Load the image later |
| 6 | Copy to memory | 0 – No copy to memory (Default) 1 – Image to be copied to memory |
| 5:3 | Image Owner | 0 - PLM (default) 1 - Non-PLM 2-7 – Reserved |
| 2:0 | Reserved | 0 |
2.7 Versal ACAP Partition Header
要找到Partition Header,需要先在Image Header Table中找到地址0x10 Partition Header Offset的4字节内容:
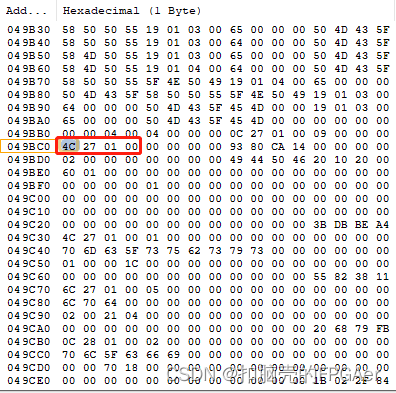
4字节内容为0x0001_274c,即Partition Header是从地址0x0001_274c开始: