上一节介绍了基于jsencrypt实现的密码加密解密登录功能,这次来介绍基于sm-crypto实现前后端登录密码加密,本次采用的是sm2进行的加密解密。
后端
首先从后端代码开始写起(因为公钥和私钥都是要从java代码中生成):
首先需要引入sm-crypto的jar包,点击获取jar包,然后拷贝到下面的目录下

然后再pom.xml文件中引入依赖,然后刷新依赖
<!--sm2jar包依赖--><dependency><groupId>com.sm2</groupId><artifactId>sm2</artifactId><version>1.0</version><scope>system</scope><systemPath>${basedir}/src/main/resources/lib/sm-crypto-0.3.2.jar</systemPath></dependency>
然后就是新建一个工具类
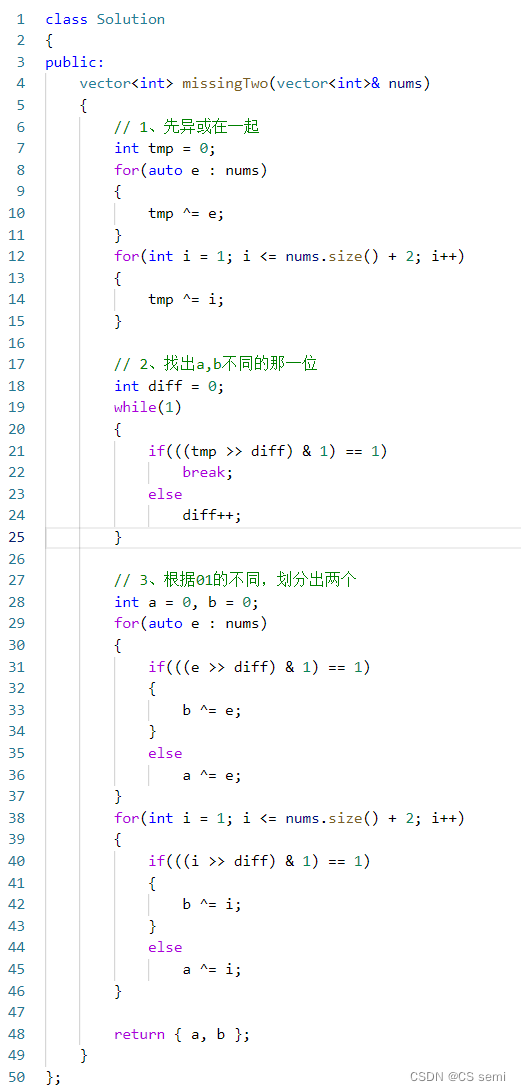
package com.ruoyi.common.utils.sm2Encrypt;import com.antherd.smcrypto.sm2.Keypair;
import com.antherd.smcrypto.sm2.Sm2;
import io.netty.util.internal.StringUtil;
import org.springframework.stereotype.Component;import java.util.ArrayList;@Component
public class SM2Encryptor {private static final SmKeyPair smKeyPair = new SmKeyPair();public static String privateKeys = "";private static String publicKeyStr = "";private static String privateKeyStr = "92b704fee9ac448ac27abfa537021ab42d0035151f01fdc03e49b0c2f5496148";/*** 加密,使用公钥** @param publicKey* @param originalText* @return*/public static String encryptText(String publicKey, String originalText) throws Exception {if (StringUtil.isNullOrEmpty(publicKey)) {throw new Exception("密钥不能为空...");}if (StringUtil.isNullOrEmpty(originalText)) {throw new Exception("明文不能为空...");}try {return Sm2.doEncrypt(originalText, publicKey);//HexUtil.encodeHexStr(cipherText); // 加密结果} catch (Exception e) {throw new Exception("加密错误:密钥不正确...");}}public static String getPublicKey() {return publicKeyStr;}public static String getPrivateKey() {return privateKeyStr;}public static SmKeyPair smKeyPair() {return smKeyPair;}/*** 解密,使用私钥** @param privateKey* @param cipherText* @return*/public static String decryptText(String privateKey, String cipherText) throws Exception {if (StringUtil.isNullOrEmpty(privateKey)) {throw new Exception("密钥不能为空...");}if (StringUtil.isNullOrEmpty(cipherText)) {throw new Exception("明文不能为空...");}try {String s = Sm2.doDecrypt(cipherText, privateKey);System.out.println(s);return Sm2.doDecrypt(cipherText, privateKey); // new String(sm2.decrypt(sourceData,prvKey)); // 解密结果} catch (Exception e) {throw new Exception("解密错误:密钥不正确...");}}/*** 获取sm2密钥对,** @return 返回String[];第0个为公钥,第1个为私钥* @throws Exception*/public static String[] generateKeyPair() throws Exception {try {Keypair keypair = Sm2.generateKeyPairHex();String[] result = new String[2];if (keypair != null) {result[0] = keypair.getPublicKey(); //公钥smKeyPair.setPublicKey(keypair.getPublicKey());publicKeyStr = keypair.getPublicKey();result[1] = keypair.getPrivateKey(); // 私钥smKeyPair.setPrivateKey(keypair.getPrivateKey());privateKeyStr = keypair.getPrivateKey();}return result;} catch (Exception e) {throw new Exception("生成密钥对失败...");}}public static void main(String[] args) throws Exception {
// 生成一对 公钥与私钥String[] keys = generateKeyPair();
// 公钥String publicKey = keys[0];
// String publicKey = publicKeyStr;System.out.println("公钥" + publicKey);
// 私钥String privateKey = privateKeyStr;System.out.println("私钥" + privateKey);// String str = "测试使用SM2加密、解密";String str = "166ed3fc69afcfee4f1ba2034c36dac93d86dcad176219407776100130a506d9";try {//加密字符串String encryptText = SM2Encryptor.encryptText(publicKey, str);System.out.println(encryptText);} catch (Exception e) {}//解密字符串String decryptText = "null";try {decryptText = SM2Encryptor.decryptText("", str);System.out.println("成功解密后为:"+decryptText);} catch (Exception e) {System.out.println("失败");}}public static void main11(String[] args) throws Exception {ArrayList<String> strings = new ArrayList<>();String str = ("$2a$10$0OXfRm8Jc4XdRFHeXFovB.UKX2DjLfgPYYS/6mz7KSym87LazK.6a,$2a$10$0OXfRm8Jc4XdRFHeXFovB.UKX2DjLfgPYYS/6mz7KSym87LazK.6a,$2a$10$0OXfRm8Jc4XdRFHeXFovB.UKX2DjLfgPYYS/6mz7KSym87LazK.6a,$2a$10$nByAilbqXIko9uf/hj5VKOXiHYlW0e7x0HDDrqLuc/BtYantNFe2u,$2a$10$4O5pYOYvPZPbZNiP5Pn2BeiMD7hTiZi4cenk6heyKFx12E2IMqlTG,$2a$10$obSpw9ZU.el9F06cVudY4us4xqcW7M2gsdU2QrfmMmfqhyOjWzGc6,$2a$10$rKXmSKy9WLhOE5fY2HdL0.OcEWWzmP2yfmCMfGlMRTZl/mC2JOIVi,$2a$10$VUQ2jwnZftQM063Ln5icce2BFmbiWLn.PiYdg7VrrH64SOiiux8zC,"+"$2a$10$XnLqxv.CrFadLsdVvhW95.BViBnV3eOWSUshugmnBKPUob2XHm.xy,$2a$10$dUSnoJ5bXAii8CxGE1IcVOQxReiNXi0U2Cpl59lBefAruaIfrs88y,2a$10$xhHW7ERYY/Hw3IwL01u0P.8eLzdWNmagMikN/2WGtfrIdCOR.QLVa,$2a$10$W0bxfRzFzCtZcaLIqDWPQeIjIy/IaFXLbd3C6Ex6IE94JAhkPH7Jm,$2a$10$z1v1aRBeUE0XwASZXbjURO685AWBM008iL1BQpdFTccvXvg1h1uxe,$2a$10$WjoOi6vBZejpENmiXBFKZeJHPxF9i4Xtc0q2qObrdRS5fQ7tjWJeK,$2a$10$YbwwDYokkeVAkiKvdsUeveYirXfDZ50cxwWcX7RY7Wq97WBaJHdzK,$2a$10$gBUTW.okA8122Uxz5d7opu/nHSY7ketS1m8OkIXsr/7yYmkv8Fpru,$2a$10$9w/CwxYzdAWtczRP0AhIW.HLZSnWjPYSqyUDsbtW0Prg7doVuG9se,$2a$10$BNNKWdbm4D0.x77SDV/ME.kVjN78bfiBuC9UFf7fmWwLWIX4CLwsq,$2a$10$lzRWuhQKCiD5gK2waXYdEOD.YvjX1d/cbwOXJNtjajNxMCNvOUMGa,$2a$10$wE2i08bEY/x84R/IRAqPoeJyc2EuDrH84tNzesoFhr18qc.3cpXLG,$2a$10$fd/LEGgdfWe6JchTJP2G1ukwOY5chU3Gc4AyTujknzqcA6lnpryq.,$2a$10$nao.cM1CCRxjAcabg16fmunEhZJJQUQvOAreUOTrXIzosuQfwUgcq,"+"$2a$10$rb1lodozm6F2O1HZOwDbLus89XhJDW5sBbZIsi9Dt/PPPETvpo.Oe,$2a$10$hyyW3XZd6QrgYRWPbQVXxeouO2Onipjexlvuxp2kTh6h3RdLnREXS,$2a$10$9xEXMdd6t5JDyHmf5b2JZOgswBvoifkJHw.d6lk/pXH7rQ1vTRPwq,$2a$10$BNlXJqjRQ08lHoh1mAYfleQYJ7KHjRw9VKJq7IZeYwILpjurWlWA6,$2a$10$.5zW9ORnRQsS6OtjsfQmauprEj7z9EhB9YfSGN8qZMN9YJ3PaUEou,$2a$10$iX43ZtDY/8fyDiYjavXj1Oj6rj.2osBI3y.IfNkiXz5AV5rMfbT7K,$2a$10$FuCMGR.znZn7zGZNwYCa/.bKFPjBX.8Iq2blu7QtHfEf8Hu9IbkLu,$2a$10$wIbkN50SjpmsbxCXjuwcaOfq0EQ05YfxCTqNzrCUwVIROOvfo9D/.,"+"$2a$10$k1WDKOPXoEVu4p6mk8rTROUONXvZGEK8l0RO8NdNjVqnUvLaqEx9a,$2a$10$jlNUUjFiXACK70h4cHLRyuZ0Z1ldyeb167SrCU/OXwbSkkd2PbpMO,$2a$10$OyI36lNuUN1FlIrjaVW9KuESt/OxcKQ2GttQ378JL.stFxlb/hjdi,$2a$10$MaAGznguMJuWpFt.dHfywuEZ5QOr0YV0NDL.qbYN97uEX6pfZXwRi,$2a$10$D6ON3RwVT2frFZfaOA.nNuSBuMQmGY57/vnehKZfhXoztYCYhtyKK,$2a$10$YHpxrHMKC56vkyybaHfstuHGy9YOt2a828qP7VyWnAVOeY8o3SVYy,$2a$10$E.91z/MiLlOono1pwmzo2..Ka2Hf6pyr.uVQCYJYqrOZLnfe9BqLG,$2a$10$f02b1NTFiPBGWVwyMOyMw.g7xVq1hsegBpPdoi0afT17PqNrLOaba,"+"$2a$10$WS4zO1Odf0pa2S3SB0UDbObR5tVQWnql6XnXrnxSjGdasq24kx9VG,$2a$10$xPhPCcYIZO0UFJMnkl8ZW.30wgfc494IdUSKu6/DP3Z7GnqOxZ1By,$2a$10$.yLwueJ/xQueMcH3qa55eOBPjWJDB0oBLS3F3VGY8il8zvoft6EJu,$2a$10$Nx8pouYgkoBSCz86uEcvn.ExNQNaXIStSqB3fsNfbdP5Oj47zx4Ra,$2a$10$u3cFkCt2qgpYMMewjAuBm.C.FFvBjMSr0VaI6r1e8epInmvNpEbBy,$2a$10$vV7cPypCsNemcD9ZiQrNG.bUskbxKzzz73t4Fnq5UoRPQGtFSQePq,$2a$10$OKb.aK9Ofb/cEMHYvjWFwuu.CdFwby15ZdyetNwGUKxRMYLmZNk52,$2a$10$WarCwyP5JWp2Rrc4xC3CUex1FKRX4bY62fSj..tUd8PmlHxF8I82G,"+"$2a$10$y/JUE6C7NPnTuZjJWnMW1u7VRfeFbn18kB1HK1H1yT5cxQbJcvgIW,$2a$10$f1DBVIc1CQWVbZAY1zsk4OMS7ovVOPF8fzb9J4oUSpJ5tl5PLlOJe,$2a$10$OsgtQDRgQ0Qqnc0m/Oe3g.Fac6/6MmoFd7YIa38Jm8MiywlcvhrVG,$2a$10$2YkCgG9I6I/ihqW0mdzMKuSgntMiqfIN128ynjm/fJkMJCcaK7Ae.,$2a$10$tDKZGVoIk9bmsB8Zta4DweuPSG4gwzNHG5nqL/tONWqewKSmVPrYW,$2a$10$zHMR6OOPfE8oVVpdWIWANOIVPT75n1FhPknmRVloVmzyotH5G0JD.,$2a$10$AbbSKDa9HFL5LHg1PRif.ukfiC90Ybp4dBrLL82xKj3Qc19N4S7I2,$2a$10$4KJULL05MP3ZPihFp3Myu.kDQORG7qFdv2MHJnef7FUfidChXNUjm,"+"$2a$10$bMoOo/2zkM6CUOghx6Onk.P2yfMmqzX849k.MxB8Nm5ezVia14yW.,$2a$10$5uFQ/Jo/TfEPM8MA9MGisu/0RnXZO7jhjp8ewt.luFjEUnIZrjnHm,$2a$10$TYx.EIPGoEZwkKIQY7rAr.Jy/AiKNHj1kdYOacy81YsEkHtnecXDW,$2a$10$hP/tWvd4rwZP3vFMrE5DTez.b09QP8VOVGHSudYIGO079FKaHis86,$2a$10$kLz0tAJV6X9nnpyR/Aeh3OPtzqA4cBtMLCCRg8nX7TRbpGei8YkX6,$2a$10$njtEzD8ByMxIhrsKLwkpW.Rjy/IigzxOdsmnUcJ0H91JenXufZ3zS,$2a$10$le42slw2CQuB/miKG7mwBOgjMuhV5/kKOatcH02rsn.i5TKFcgilm,$2a$10$kSgjpIQDX0cK7PVzuUwEtexvUFLtMrJto7fujg2GG40j0r5wHy3qa,"+"$2a$10$MaPwMPePfNeLxm0uHvGqSOv/n8GnFj2DADJptclHIA3QHvXLCnS46,$2a$10$WorTE9Pfwdo4NyN8U6yHFu.Fek7jzQwuYlJyN26T2XO3kjKCB9SlS,$2a$10$hlFqSYJfHRaT/xp9c2rBb.wrjkQ/xGZ0qjO.aBrmHJFDZqWzTtHda,$2a$10$uvpPJsnFS4llREzWF28o7eOJk0LW8RwACfINCG1dgG/RaePpdRC0S,$2a$10$8JRFUion6Ti73uMM.vs1QeMB.IbB1BZlwiGM0yIk2UWdgkovx6yBK,$2a$10$TQXkcaewixOK3l14vLUxg.HLYK5eJshvBKptE9D8pXiuhw5d/Z6du,$2a$10$N1xgnv.hEYUliyfXgLdeNe3gu206P3jP.jB5OqDFFhxAMS.p6Je9i,$2a$10$EBoY8MP2rSCKi4Rsx28PTOUzwItMFTfnNaCqy5JxBtYOt024ZpWLa,"+"$2a$10$yV16ItAE/QnTmk58Bqybl.5GyGs1lODq/eXzSNzFzYNQF67QU2UqC,$2a$10$pfUsqj2DbJh95X0Dfx/j6Oe1KVNnaHg.JJDnzG49ALuhI5nbH81wW,$2a$10$IxlPhjKsfrOTfoFkY4EXqOUUrsA3HFMwi88T/CgpTOaqJTZHTzPEy,$2a$10$Mo5PVL7q6IZZx5mjdQVWquZjj8tCYAtT/WvOi3Dh5uCLOsSmY5Oxi,$2a$10$bF9l.0MqIFP8nND.Bnew/OO1C1A1HzC5H/zH8pMEbGKz.StTl2UMG,$2a$10$0fOx2IGytasxA9A4bZHcm.FxV4vXRXEggQOzFQ9H9ZvRoRlN08wby,$2a$10$afmUV4Ea98i7M46C67sVS.EgAO4q3bociwUXrg.MryBbGvTyk1rdO,$2a$10$BaydepEWPGWKHpztcy0X9.MT3JT9N8ok3qMYniSyDTb70UitqCACi,"+"$2a$10$rm8ACuVu/L5WrGIx6GQzmOCe5jIeFWqMea4PK7LiIY9y3lA6V2mue,$2a$10$g78j/vHGwDbJ6owQyLAVX.aZltVX7tiLkPUX74B2o2MSfdEHfD8Je,$2a$10$WlsChXQbTsXH0Ixfzquif.nwvym91K0nAemBEyudvfzVQAefE/.5a,$2a$10$B1QKr/6AYWbW6LP7zn.IIOCkSw/KGPr4FLtfPU0c0eplDvO88uF8m,$2a$10$u7nf2JtZVSwaRsmrpL/0iOmUrv3C7rKr9ZgCUe4tYF/qshtnwgR2a,$2a$10$vhQWireOCR4WF24XTXOoQuKSlFg8B9WmOSb3iFXmU50MAf1Qjmj7i,$2a$10$56cj/0IFOJi7cBPY3GgepuQA/VC98PjJtprYA8YBIkg7WDvd3K5Da,$2a$10$IePmIGZ4WcQGBeR.9vsqgu0UcnP/lPgApJ8uReJBAzImuk3wL1wUC,"+"$2a$10$is6Qwxc1/yKJrOITuf4z4.IGgLOJIFovpZhvGd91dfrsdoSs28LlO,$2a$10$SnDCCzlrIqT7oTAZ5KUnB.2ODLSBg4UUDpJ5tbhnflMH1ZcXF/.46,$2a$10$q97bqc579DEFSU8.9ka0ruuCkCQ2qybDvFdt5xsYgokxpldpSqIGu,$2a$10$8CVy5hN8ztP80p/5i9BYq.7ev5q9NNun1JG8P/re3wglgvcIG.MuG,$2a$10$0mud1YlzY.l5rxHkV16Veu3Qtw3Dbfc9MC9AqSSyS5c7X5orTGGdC,$2a$10$E2NhAxELYXJZQvwtEjhh5Of/tLKlhy7NCAtjacxQXfE1totdK2TUm,$2a$10$CghuySHeWIzrmzsYq2Q.HeLItIK5SeAoaLTC6sThidNtAk50BVbCC,$2a$10$gAa8lhKJpiK5KFMWgH7VCuioNsys/8EEsFOOzw.0G.O1jEbsoNyCC,"+"$2a$10$LpBends9aroD4uZOR0UB9.u7HROrFRtHOj5DbnCiUD3bT49HJTovK,$2a$10$SePADrelDadID7JmXqyfC.a0oaj0cScph6oXXamodOZdr//dnZSje,$2a$10$ghijJFE5V7uGzoQ6Yrq0Ce6CC.Yj8v.onKr9yuxdHYZcGx2rXzWTK,$2a$10$9NV3bUgsS4c.RHcwnF6OVOd7w1u.sa0X4vQkDq1J9.pPT5o8AWbx6,$2a$10$vH5cEESBaZWgOBf3GQsMHuW8LbtFH.7hvYNYYWsAOBad353uz8FhG,$2a$10$L7T0X60X.Bme0HOx.xR4s.BfRCzMEBinj2lfL8UXgZWNvDM2TnUh6,$2a$10$PkxOj4JHd53OCttbQPZofuLfRkyWno7hGQfKw1.hBy3jD0gUisJgm,$2a$10$B8.QnBNqITn1uT4nydWuneM9X.mqKYCPSxohR/7SF.S1X3b/XWYLa,"+"$2a$10$nnK/wOCVzZTwU2ZrYVoNdOuhyWm/vDiqNJn.vTkVEFu137HOQagu.,$2a$10$wuFgwwNS9DDnj1vi.iq94up3KStQFUs7pN2gO/ndI6ERMbdeAa2sm,$2a$10$I6HqOxQe7YCZ5Icmva3jw.h3KGw9B6N9Uo6Tcg0r62bHKg6xWYKO6,$2a$10$yRn6PaFnHoujIgXqfEJcHepvXvEN0m5Qa.19RNV28H7IwzOt4Hhxu,$2a$10$ucs4zz9jCSzyDEA0LJqrX.RosuU1sPuSvBiM1IPL1nsX5V59it0Au,$2a$10$7YFVsVTqykrSXVu3bPl1S.uoj2onQwi21eVt6mZY3Y/dVpxTEgoLW,$2a$10$hNcAC5qMNTTxz.vH1nZLP.T4S9sPNTuG0KgDX1hylcMrMpaEfwRZ2,$2a$10$kupfow5/FMa7LNSaLoKM5.d5zU0icKtKSH8WHx30irK3G.C3pLyee,"+"$2a$10$N6xPqq44DmnBlWbJgiMNye/Fzm3.yxYwXIDBeALhBZNN1.xonwMdG,$2a$10$pYPzdyOaDBlOUd1PcGZDJeK5dtE35j4qNgJVHdCYPpxctmZ56Jrum,$2a$10$jRU.o6rq0fe3mPqO/YDZiu/rWyZop4UPYjUf27EbEfTxX56e2eM82,$2a$10$.tZ6GCOI/EG1x5Z7scAauOgNkFduxJf94oVB0tyEGllcRXje6UX9u,$2a$10$uIg7q24d34w4qa81YnQjwuYVK25EJxgw6DPn0KiLVQQ04CNfqd.0u,$2a$10$Hl67tZsGzurSuq1aXOmTguu6QF46GURJuyJxGIHTRATxSMsNFtJ2W,$2a$10$Qo0gRZUYigjxwJ5KmhkRIOjBkttk3GM06drYv96ERpk53F9039FgC,$2a$10$a/g0xm854nvQAuh4Ko0PYuVo70zIGSuD1g5MVkMD2ciVXKDntwtj2,"+"$2a$10$RT5td108sIGzIY23M4X1weksRvuydT34d3N7duu1Cd6OZMh2agOt2,$2a$10$.qd.8zD81cBQOrnzhSgWUuLYAuft2M86hfsD6siHvVTCyL0MZwfQG,$2a$10$eYDWFSzBwhQssYhpJh1UK.XMndeQtW2uTbAb3TTU5SK8q0eCHiqYG,$2a$10$6PueANimU3hlXN8j3IKX..1zWPRVnI9y1sdR1d9C/cVYYK55.ZEgC,$2a$10$j7xKdgRPgu4XtFnfjDAkdObkEuSByemURcPOpz3NuG/W5oPVLQcOC,$2a$10$ZLVe.LAKVMW66f7rvYpcNu8BlJj6cxs2zST.bLFTIHCjz6GKhA7L.,$2a$10$aJYhOZNu.bZKu6wyHy5u6uUowAr2sY4NcSn/IpQexn9nemlVZBdfa,$2a$10$Q66gF1W1WYQuigYOaXtWT.Npoz4.0Zl.OJacjvE5bVrlbbKVJQjuW,$2a$10$mV4b7hq3gpJq7cwaiLUJ8OBnu1bOopWyeTuk8aCID6WzlaM3TuoEy,$2a$10$rkSIXEFmcmSOHs0eIc16Ous0gC83P3uIg9EV1vqkw3G9YysKKRof6,"+"$2a$10$LxyHFhCGKN85FYn4I3s/yeVxaEV4Q4zutHpQMiaYFTO/m.neAJ2eK,$2a$10$RmdiQrErmW4T1H91bARr3eOb/5EeJdGElP1VPKbplOKBi8VK1PZ1O,$2a$10$6Sc/VvEvcxhAIgH7kUY60.QlM4xU2eHKFxdxXBsQmMZzis4GY2buS,$2a$10$G9FBv5rBu/stjHXImxETgukeTIK2DC65x9m3Ogd91UR8/7L/WhX9W");String[] split = str.split(",");//私钥String privateKey = privateKeyStr;for (String s : split) {//解密字符串String decryptText = SM2Encryptor.decryptText(privateKey, s);System.out.println("解密后密码:"+decryptText);}}/*** 获取sm2密钥对,** @return 返回String[];第0个为公钥,第1个为私钥* @throws Exception*/
// @Beanpublic void startGenerateKeyPair() throws Exception {try {Keypair keypair = Sm2.generateKeyPairHex();String[] result = new String[2];if (keypair != null) {result[0] = keypair.getPublicKey(); //公钥smKeyPair.setPublicKey(keypair.getPublicKey());publicKeyStr = keypair.getPublicKey();result[1] = keypair.getPrivateKey(); // 私钥smKeyPair.setPrivateKey(keypair.getPrivateKey());privateKeyStr = keypair.getPrivateKey();}} catch (Exception e) {throw new Exception("生成密钥对失败...");}}/*** RSA密钥对对象*/public static class SmKeyPair {private String publicKey;private String privateKey;public SmKeyPair() {}public SmKeyPair(String publicKey, String privateKey) {this.publicKey = publicKey;this.privateKey = privateKey;}public String getPublicKey() {return publicKey;}public void setPublicKey(String publicKey) {this.publicKey = publicKey;}public String getPrivateKey() {return privateKey;}public void setPrivateKey(String privateKey) {this.privateKey = privateKey;}}}然后运行里面的main方法获取公钥和私钥,保存起来
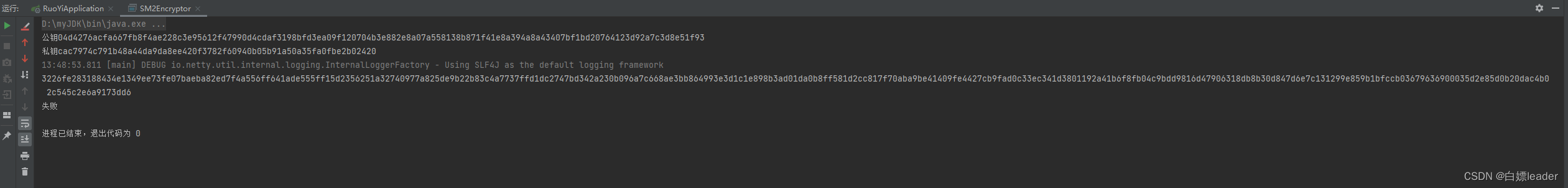
然后再application.yml文件中加入一个配置:

#SM2解密私钥
SM_privateKey: 92b704fee9ac448ac27abfa537021ab42d0035151f01fdc03e49b0c2f5496148
最后在登录接口那里调用解密方法
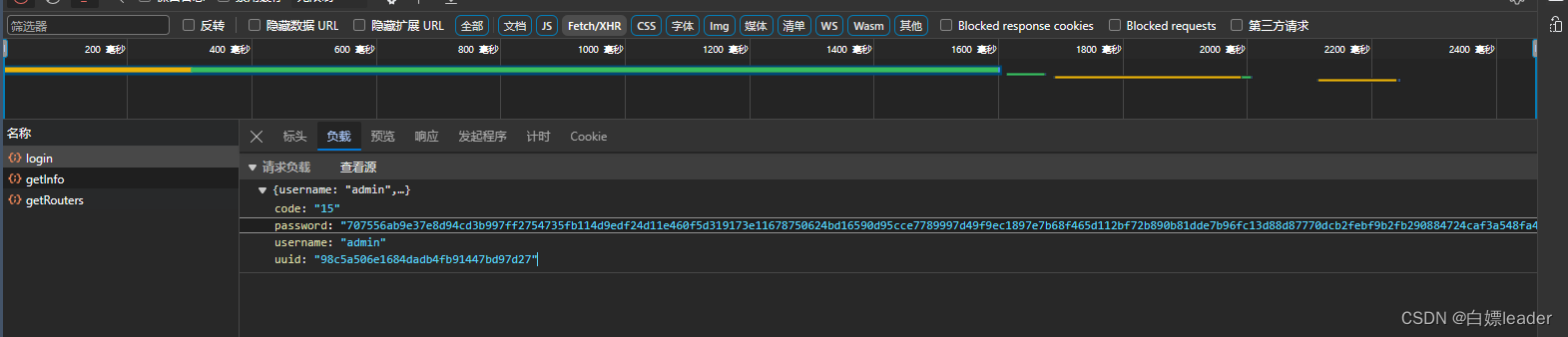
/*** 登录方法* * @param loginBody 登录信息* @return 结果*/@PostMapping("/login")public AjaxResult login(@RequestBody LoginBody loginBody) throws Exception{AjaxResult ajax = AjaxResult.success();// 生成令牌String token = loginService.login(loginBody.getUsername(), SM2Encryptor.decryptText(SM_privateKey, loginBody.getPassword()), loginBody.getCode(),loginBody.getUuid());ajax.put(Constants.TOKEN, token);return ajax;}

到此后端的工作就做完了
前端
前段需要先
npm i sm-crypto
在需要生成的模块,如common模块下新建一个工具类
前端代码:
在utils下新建smcrypto.js,把公钥和私钥放进来
import { sm2 } from 'sm-crypto'const publicKey = "04b9fd451e0d0d5517069076edbc7dc83b3a885307bc8cf00185769f6818bcdf958f8dc4c8575f33dcfbe0bb18c4f651892a05a4fd923f01db2e3ad09fc4bf2878"
const privateKey = '92b704fee9ac448ac27abfa537021ab42d0035151f01fdc03e49b0c2f5496148'
const cipherMode=1// sm2公钥加密
export function smEncryptor(password) {password = sm2.doEncrypt(password, publicKey, cipherMode)return password
}// sm私钥解密
export function decrypt(txt) {return sm2.doDecrypt(txt, privateKey, cipherMode)
}然后在登录的地方进行加密:
const password = smEncryptor(userInfo.password)
最后就是测试效果