1)、搭建hdfs单机服务器搭建
2)、kdc单机kerberos认证
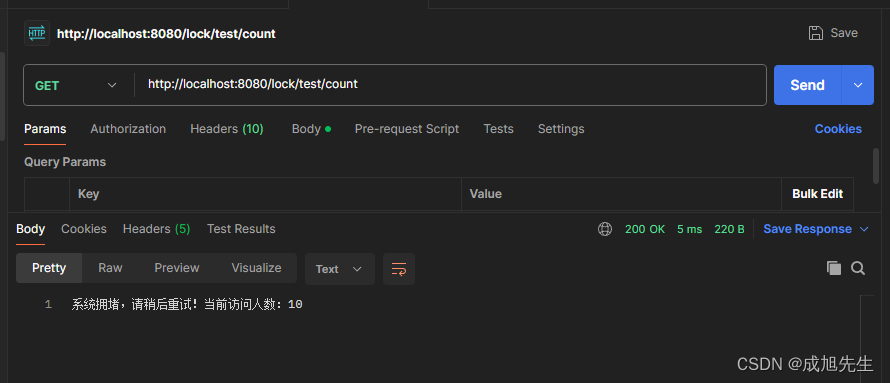
我的服务器:192.168.1.166
1、安装kerberos
1.1 执行命令:yum -y install krb5-libs krb5-server krb5-workstation
1.2 修改host文件:vim /etc/hosts,加入
192.168.1.166 myli
192.168.1.166 kerberos.example.com
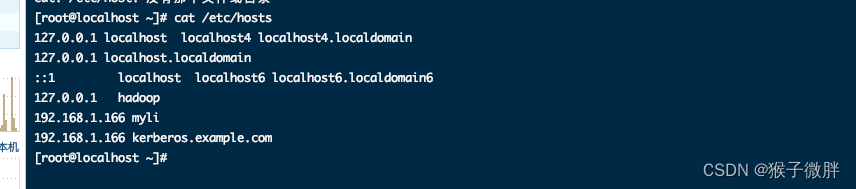
1.3 KDC中服务器涉及到三个配置文件
/etc/krb5.conf
/var/kerberos/krb5kdc/kdc.conf
/var/kerberos/krb5kdc/kadm5.aclkrb5.conf
includedir /etc/krb5.conf.d/[logging]default = FILE:/var/log/krb5libs.logkdc = FILE:/var/log/krb5kdc.logadmin_server = FILE:/var/log/kadmind.log[libdefaults]dns_lookup_realm = falseticket_lifetime = 24hrenew_lifetime = 7dforwardable = truepkinit_anchors = FILE:/etc/pki/tls/certs/ca-bundle.crtdefault_realm = EXAMPLE.COM
# default_ccache_name = KEYRING:persistent:%{uid}[realms]EXAMPLE.COM = {kdc = kerberos.example.comadmin_server = kerberos.example.com}[domain_realm].example.com = EXAMPLE.COMexample.com = EXAMPLE.COM
kdc.conf
[kdcdefaults]kdc_ports = 88kdc_tcp_ports = 88[realms]EXAMPLE.COM = {#master_key_type = aes256-ctsacl_file = /var/kerberos/krb5kdc/kadm5.acldict_file = /usr/share/dict/wordsmax_renewable_life = 7dmax_life = 1dadmin_keytab = /var/kerberos/krb5kdc/kadm5.keytabsupported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal}
~ 为了能够不直接访问 KDC 控制台而从 Kerberos 数据库添加和删除主体,请对 Kerberos 管理服务器指示允许哪些主体执行哪些操作。通过编辑文件 /var/lib/kerberos/krb5kdc/kadm5.acl 完成此操作。ACL(访问控制列表)允许您精确指定特权。
$ cat /var/kerberos/krb5kdc/kadm5.acl*/admin@EXAMPLE.COM *
1.4 kdb5_util create -r EXAMPLE.COM -s # 另一个终端 cat /dev/sda > /d