网络防火墙
NAT
NAT: network address translation
PREROUTING,INPUT,OUTPUT,POSTROUTING
请求报文:修改源/目标IP,由定义如何修改
响应报文:修改源/目标IP,根据跟踪机制自动实现
SNAT:source NAT POSTROUTING, INPUT
让本地网络中的主机通过某一特定地址访问外部网络,实现地址伪装
请求报文:修改源IP
准备:
firewall:开启ip_forward功能
[root@firewall ~]#vim /etc/sysctl.conf
net.ipv4.ip_forward = 1
[root@firewall ~]#sysctl -p
[root@firewall ~]#sysctl -a
1、SNAT:
场景:SNAT固定IP映射:模拟内网访问外网地址转换,策略添加在nat表的POSTROUTING链上chain
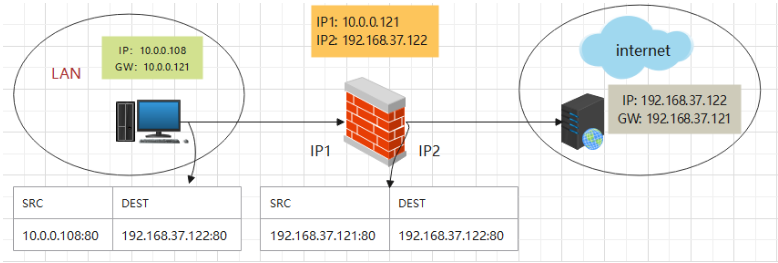
1.1、固定IP
nat表的target:
SNAT:固定IP:
可以是一个连续范围:
--to-source [ipaddr[-ipaddr]][:port[-port]]
--random
规范:iptables -t nat -A POSTROUTING -s LocalNET ! -d LocalNet -j SNAT --to source ExtIP
示例:
iptables -t nat -A POSTROUTING -s 10.0.0.0/24 ! –d 10.0.0.0/24 -j SNAT --to-source 192.168.37.121
示例:SNAT固定IP映射:

1 [root@firewall-121 ~]# iptables -t nat -A POSTROUTING -s 10.0.0.0/24 -j SNAT --to-source 192.168.37.121 2 #/模拟内外IP ping外网/ 3 [root@CentOS7-108 ~]# ping 192.168.37.122 4 PING 192.168.37.122 (192.168.37.122) 56(84) bytes of data. 5 64 bytes from 192.168.37.122: icmp_seq=1 ttl=63 time=0.712 ms 6 64 bytes from 192.168.37.122: icmp_seq=2 ttl=63 time=1.89 ms 7 64 bytes from 192.168.37.122: icmp_seq=3 ttl=63 time=0.585 ms 8 64 bytes from 192.168.37.122: icmp_seq=4 ttl=63 time=0.512 ms 9 ... 10 #/模拟外网tcpdump抓包,地址已转换为内外出口IP/ 11 [root@CentOS7-122 ~]# tcpdump -i ens33 -nn 12 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode 13 listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes 14 09:56:08.485437 IP 192.168.37.121 > 192.168.37.122: ICMP echo request, id 13431, seq 9, length 64 15 09:56:08.485457 IP 192.168.37.122 > 192.168.37.121: ICMP echo reply, id 13431, seq 9, length 64 16 09:56:09.485988 IP 192.168.37.121 > 192.168.37.122: ICMP echo request, id 13431, seq 10, length 64 17 09:56:09.486012 IP 192.168.37.122 > 192.16P echo rep8.37.121: ICMly, id 13431, seq 10, length 64
1.2、动态IP
MASQUERADE:动态IP,如拨号网络
--to-ports port[-port]
--random
规范:iptables -t nat -A POSTROUTING -s LocalNET ! -d LocalNet -j MASQUERADE
示例:
iptables -t nat -A POSTROUTING -s 10.0.0.0/24 ! –d 10.0.0.0/24 -j MASQUERADE
示例:SNAT动态IP映射:

1 [root@firewall ~]# iptables -t nat -R POSTROUTING 1 -s 10.0.0.0/24 -j MASQUERADE










