Lecture 1 the theoretical basis for networking
Network edge and core
地理覆盖范围:广WAN,城MAN,局LAN,个PAN
交换方式,电路,报文,分组
电路交换vs报文vs分组
Network performance
protocol layers and service models***


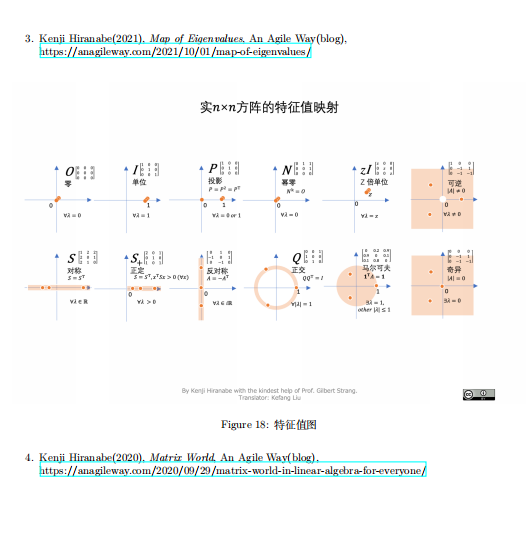
OSI七层




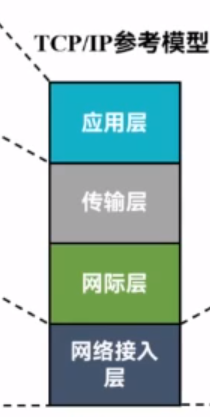
TCP/IP四层

 ···························
···························
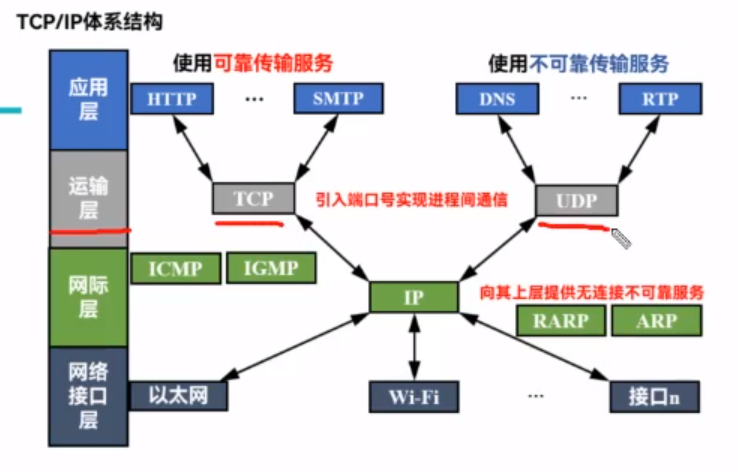
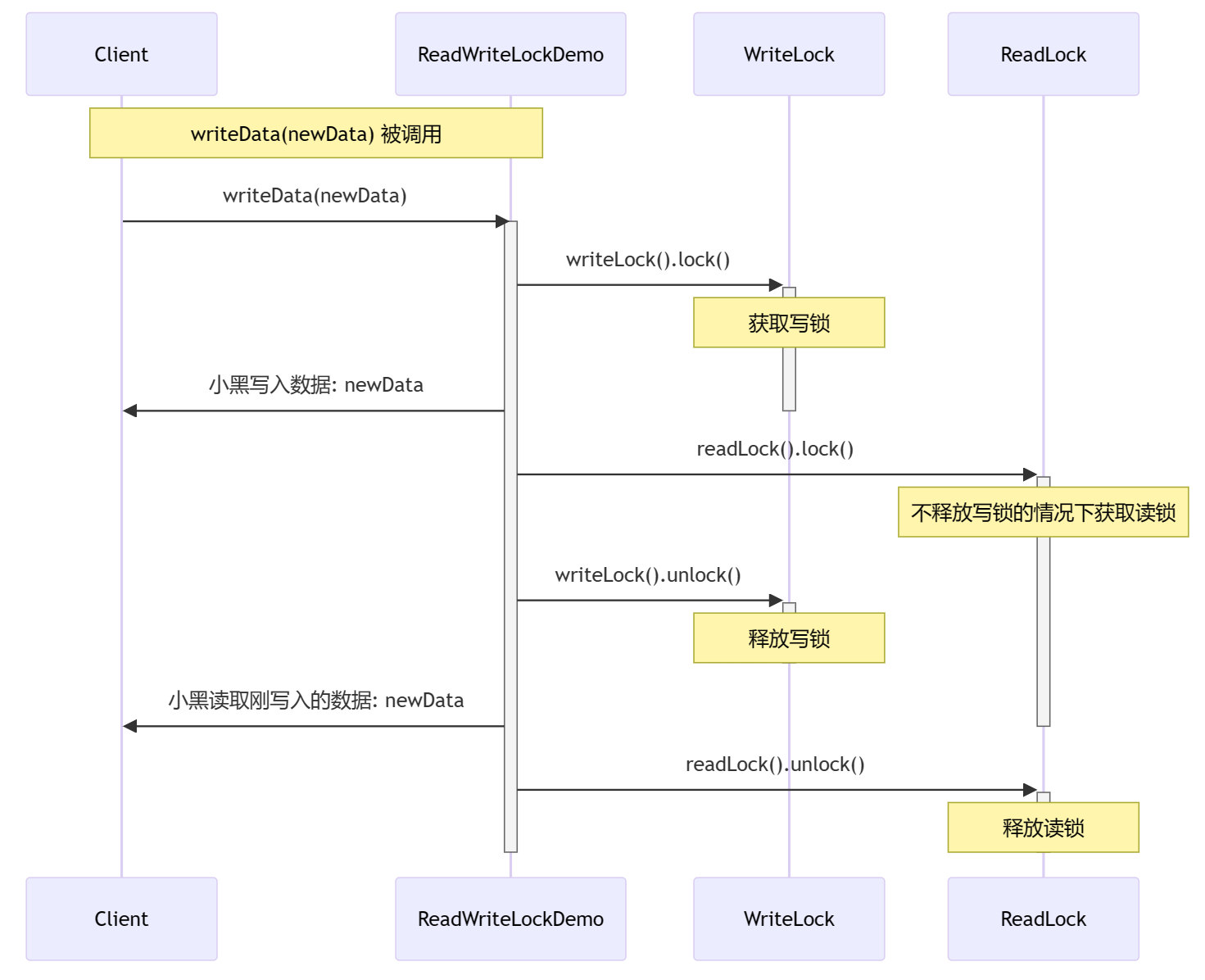
e.g 网站访问中不同层所涉及的协议
-
Application Layer:
- HTTP (Hypertext Transfer Protocol): This protocol is used for transmitting text, images, and other web page components between your browser and the web server. In this case, when you enter the URL, your browser initiates an HTTP request to the server.
-
Transport Layer:
- TCP (Transmission Control Protocol): HTTP typically uses TCP as its transport layer protocol. TCP ensures reliable and ordered delivery of data between your computer and the web server. It establishes a connection, breaks down large messages into smaller packets, and ensures they are delivered without errors.
-
Network Layer:
- IP (Internet Protocol): IP is responsible for routing packets between devices across different networks. In this scenario, it helps route the TCP packets containing the HTTP requests and responses between your computer and the university's web server.
-
Link Layer:
- Ethernet (or other link layer protocols): At the link layer, Ethernet is often used to transmit frames between devices within the same local network. Your router uses Ethernet to send data to and receive data from your computer.
-
Physical Layer:
- Physical medium (e.g., Ethernet cables, Wi-Fi signals): The physical layer deals with the actual hardware transmission of bits over the physical medium. This could be Ethernet cables, Wi-Fi signals, or other physical means connecting your computer to the router and the router to the wider Internet.
In summary, when you enter the URL in your browser, it initiates an HTTP request. This request is encapsulated in TCP, which is then further encapsulated in IP for routing. The data is transmitted over the physical medium using link layer protocols like Ethernet. Finally, your router facilitates the communication between your computer and the web server.
network security
core - package switching
delay
分组信息的优缺点
优点
1.Error control: Each packet includes a checksum, which can be used to detect and correct errors that may occur during transmission. If an error is detected in a packet, only that packet needs to be retransmitted, rather than the entire message.
2.Flow control: Network devices such as routers can use the sequence numbers in packets to monitor and control the flow of data through the network.
3.Flexibility: By breaking a message into smaller packets, it can be sent over different paths in a network and reassembled at the destination. This is known as packet switching and enables efficient use of network resources.
4.Reliability: Each packet has a header that contains information about the packet's destination, so if a packet is lost or corrupted in transit, it can be retransmitted without having to retransmit the entire message.
5.Scalability: Segmentation allows messages of any size to be sent, regardless of the maximum packet size that a network can handle.
缺点
1. Increased overhead. Each packet must include additional information, such as a sequence number, for reassembling the original information at the destination. This increases the amount of data that needs to be sent and can reduce the overall efficiency of the network.
2. Processing delays. The process of breaking the message into packets and adding the necessary headers introduces additional latency.
3. Complexity. The process of segmentation and reassembly introduces additional complexity into the system, which can make it more difficult to troubleshoot and maintain.
4. Security risks. As packets travel over the network, they may pass through multiple intermediate devices, which increases the risk of unauthorized access or tampering.
5. Delivery errors: Packets are sent independently and may take different paths through the network, so they may arrive out of order or be lost. These errors can occur due to congestion, routing loops, and other problems.
6. Network congestion. When a large number of packets are transmitted in a short period of time, it can cause network congestion, resulting in delays or even loss of packets.
Lecture 2-3 the application layer
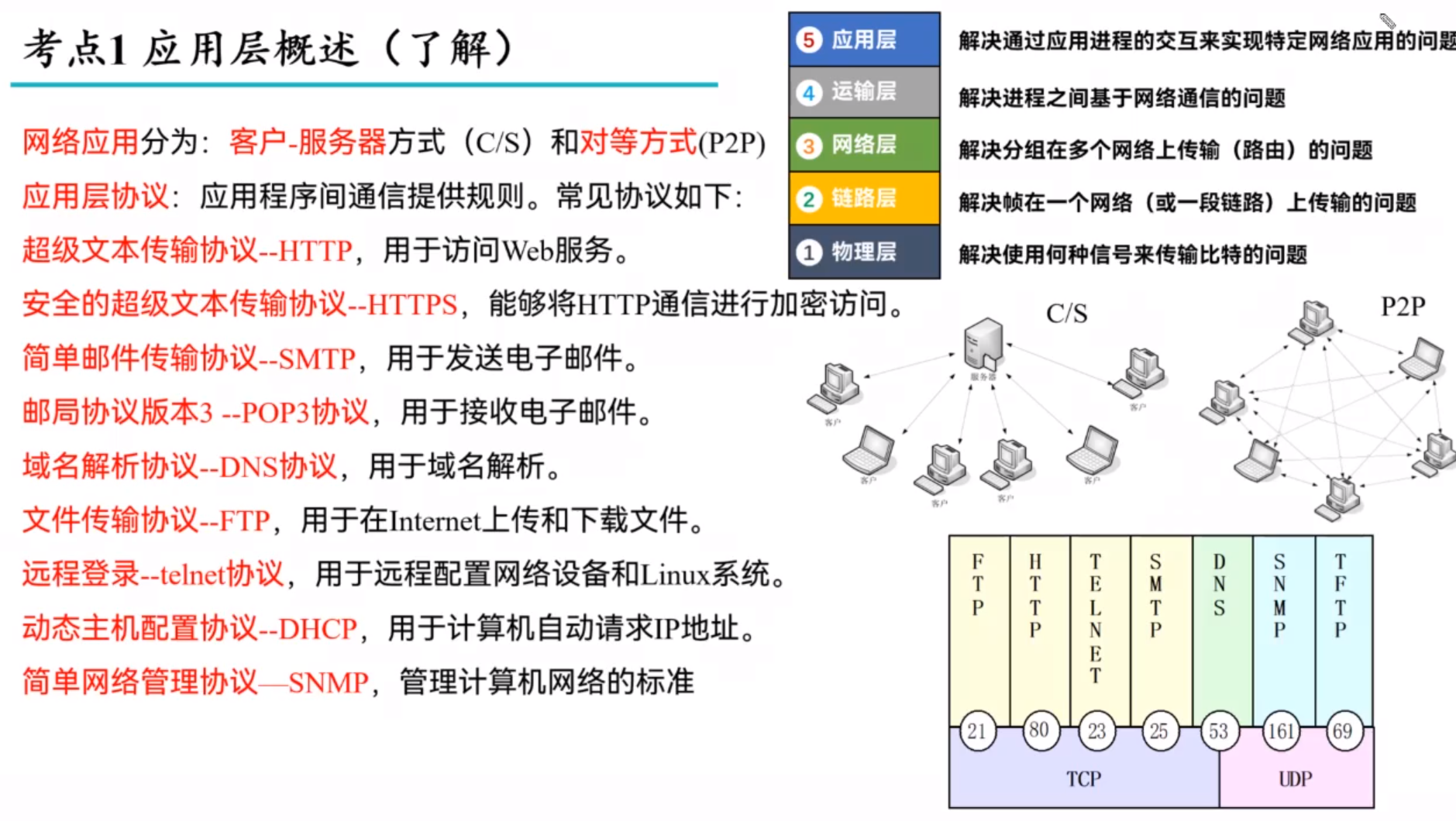
Principle of network application
web application
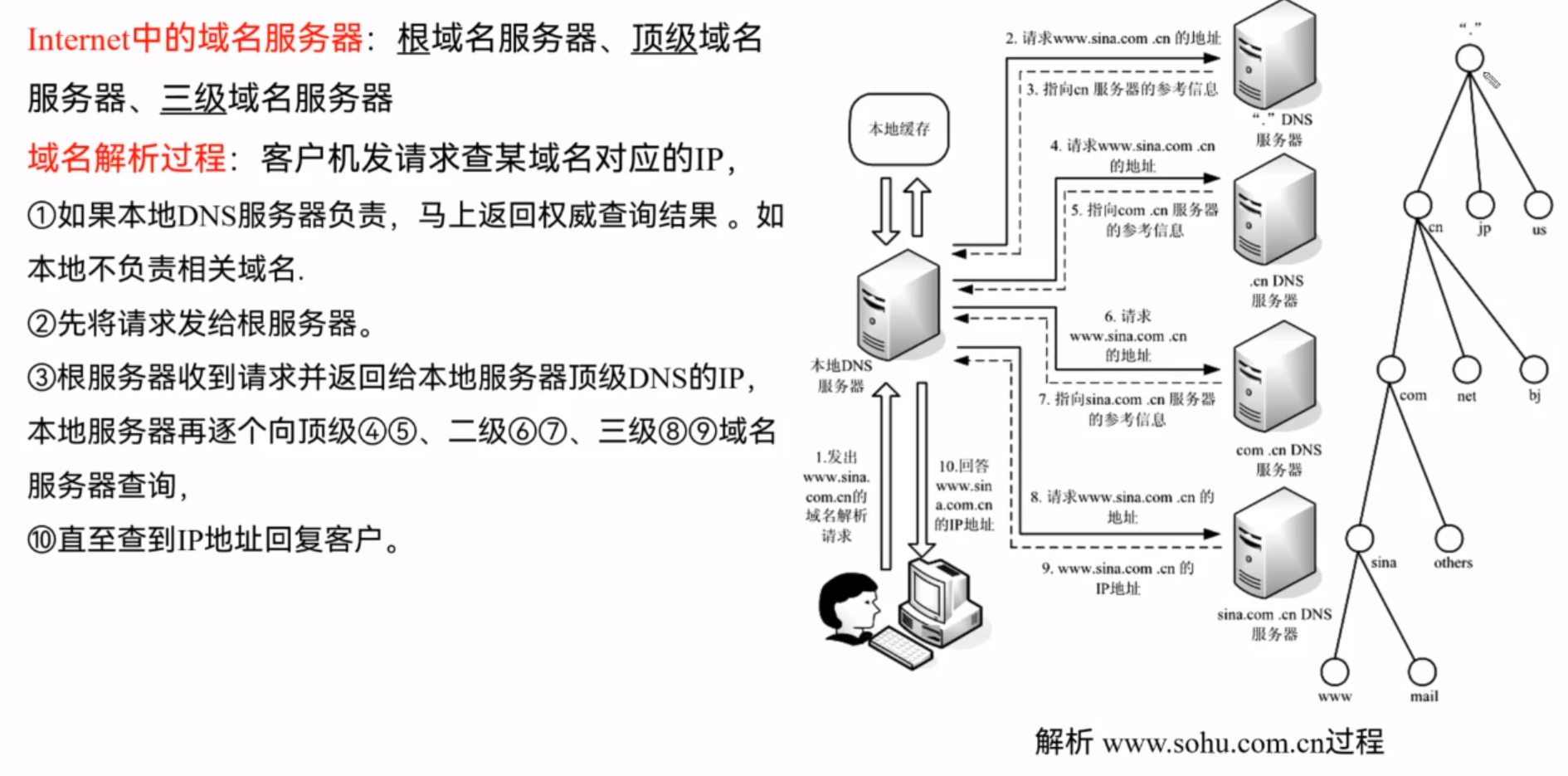
Domain Name System(DNS)


P2P Applications
Socket Programming
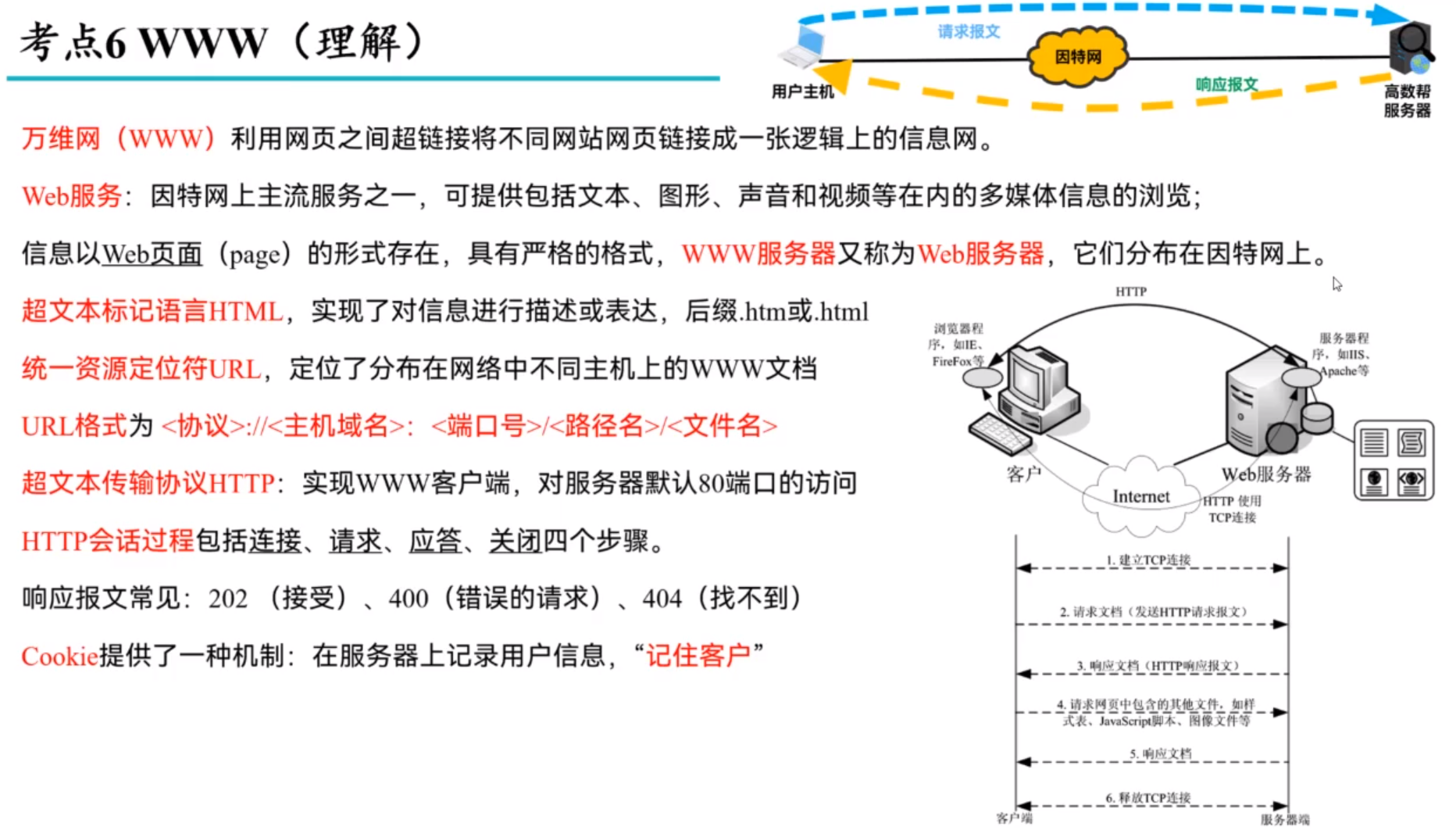
HTTP(协议)
为什么browser信息是需要的
The browser is included as a header field in the HTTP request message because it provides the server with important information about the client making the request. Here are a few reasons why the browser is required in the HTTP request message
Device compatibility. Different browsers have different capabilities and support different technologies, so browser information helps the server determine if the client can handle the requested content.
Security. Different browsers have different levels of security, and the server can use this information to determine if the client is using the latest secure browser before serving content.
Analysis and logging. Browser information is used to analyze the performance of the site and to understand how the site is being used, such as browser type, version, etc.
Content delivery. Depending on the browser, the server may choose to deliver different content, such as images or web styles, to optimize the user experience.
Malicious user agents. Some attackers may use malware, scripts, or malware to make requests that provide a fake user agent to evade detection. User agent strings are useful in detecting such cases
Compliance: Certain regulations, such as GDPR, CCPA, etc., may require logging of user agents for compliance purposes.
In summary, browser information in HTTP request messages is used to provide the server with important information about the client that can be used to optimize user experience, security and performance, and compliance.
Lecture 4-5 the transport layer
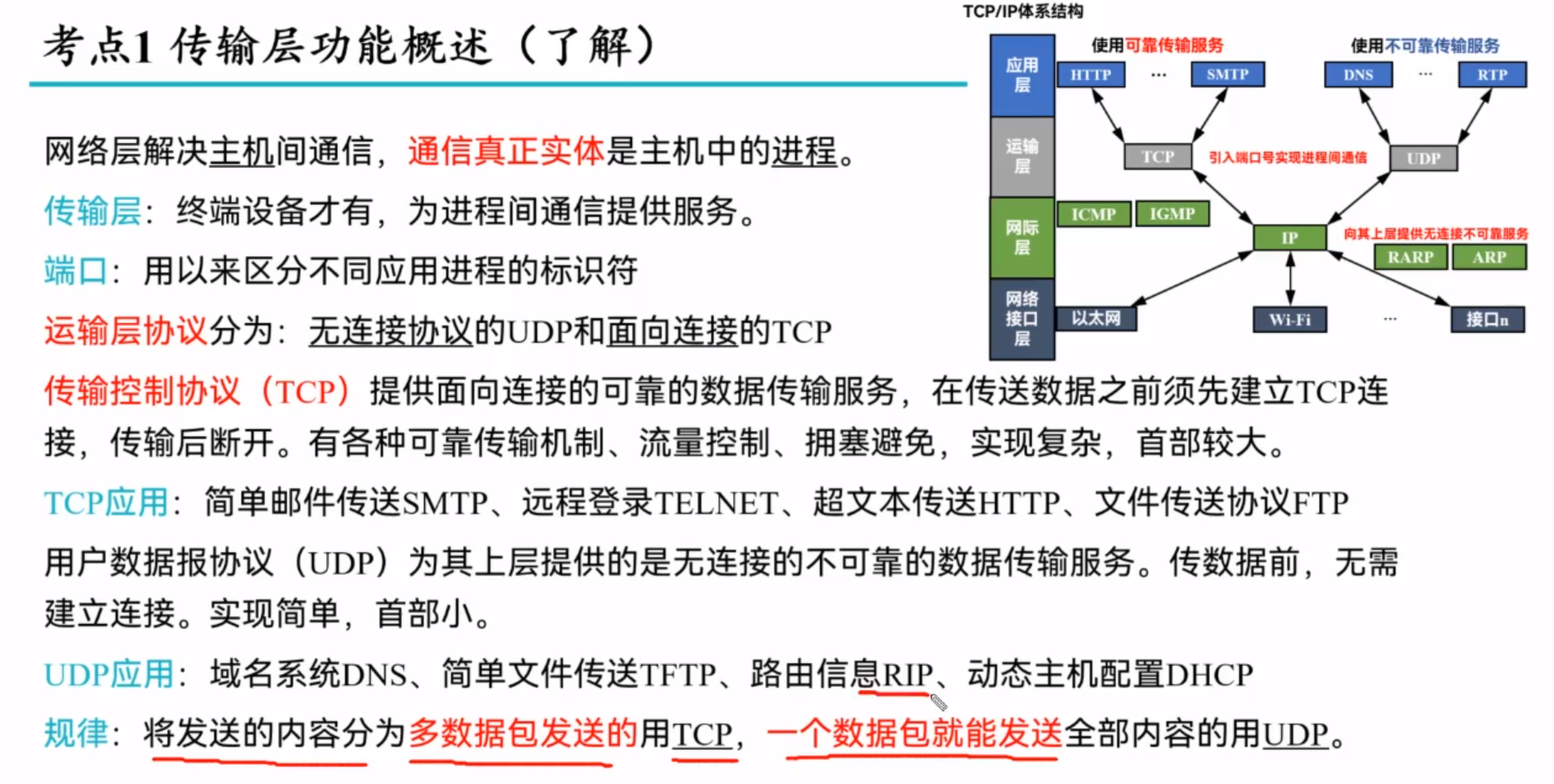
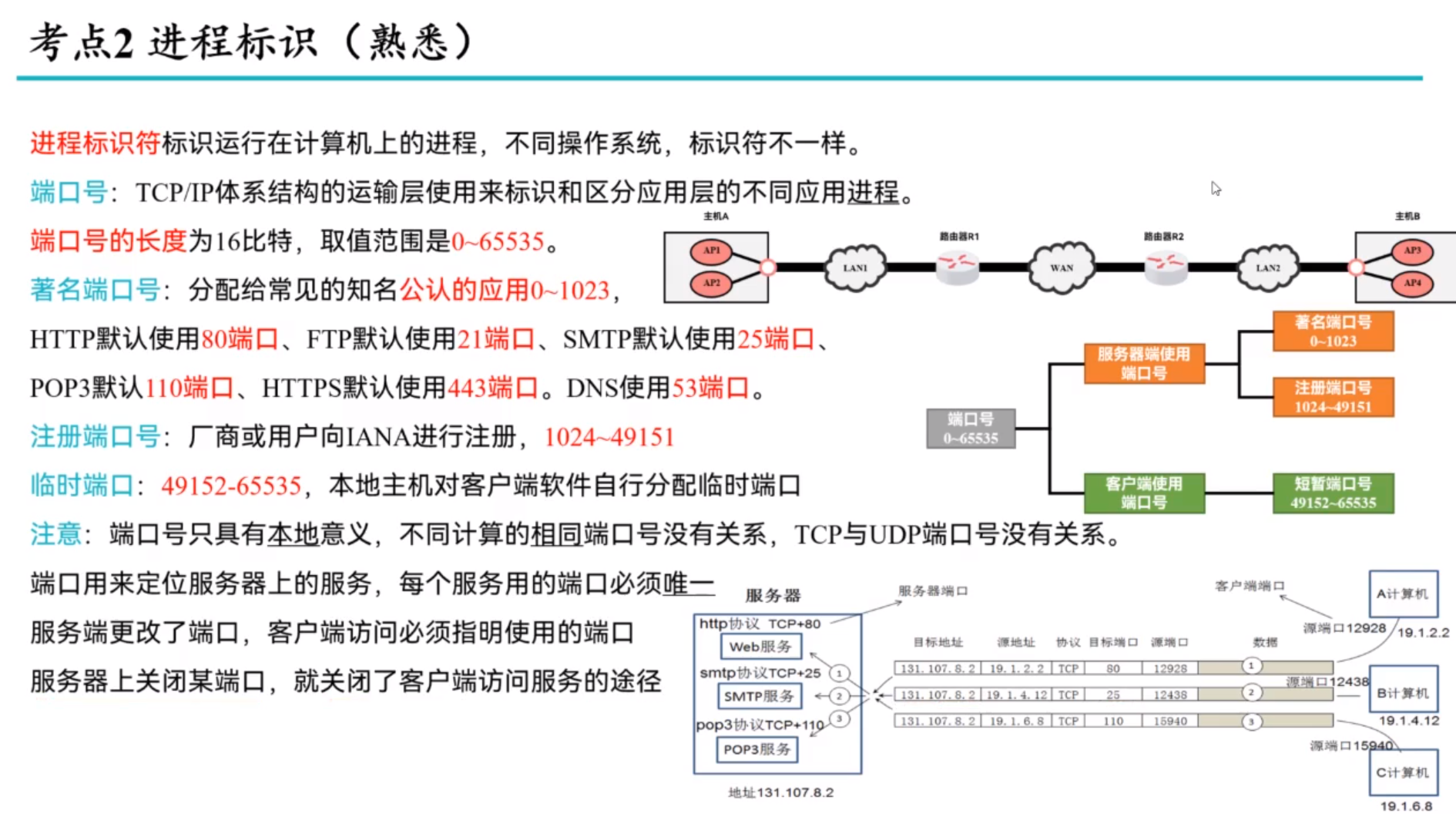
Transport-layer services
Multiplexing and demultiplexing
Connectionless Transpor: UDP

Principles of reliable data transfer
Piplined communication
TCP: connection-oriented transport
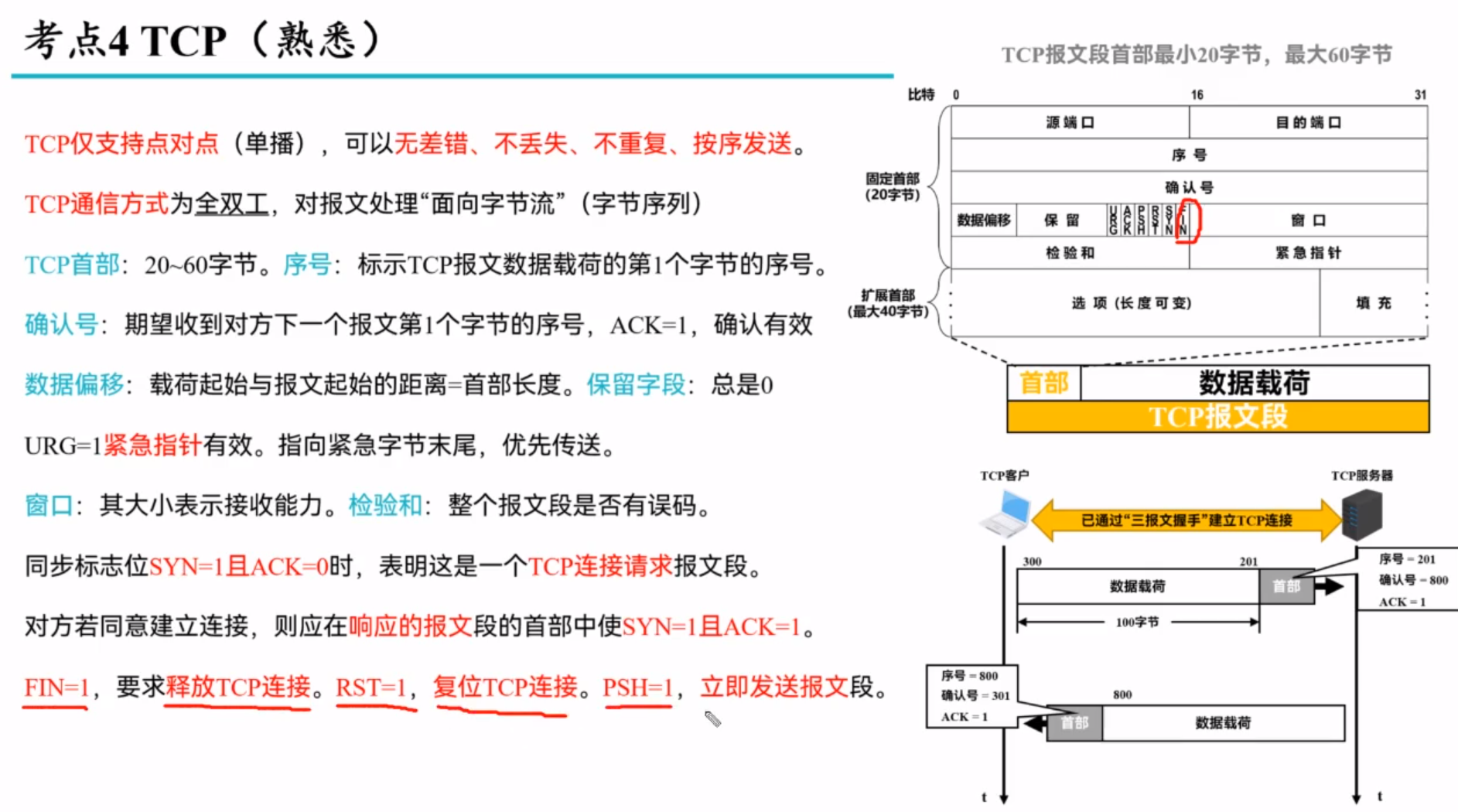
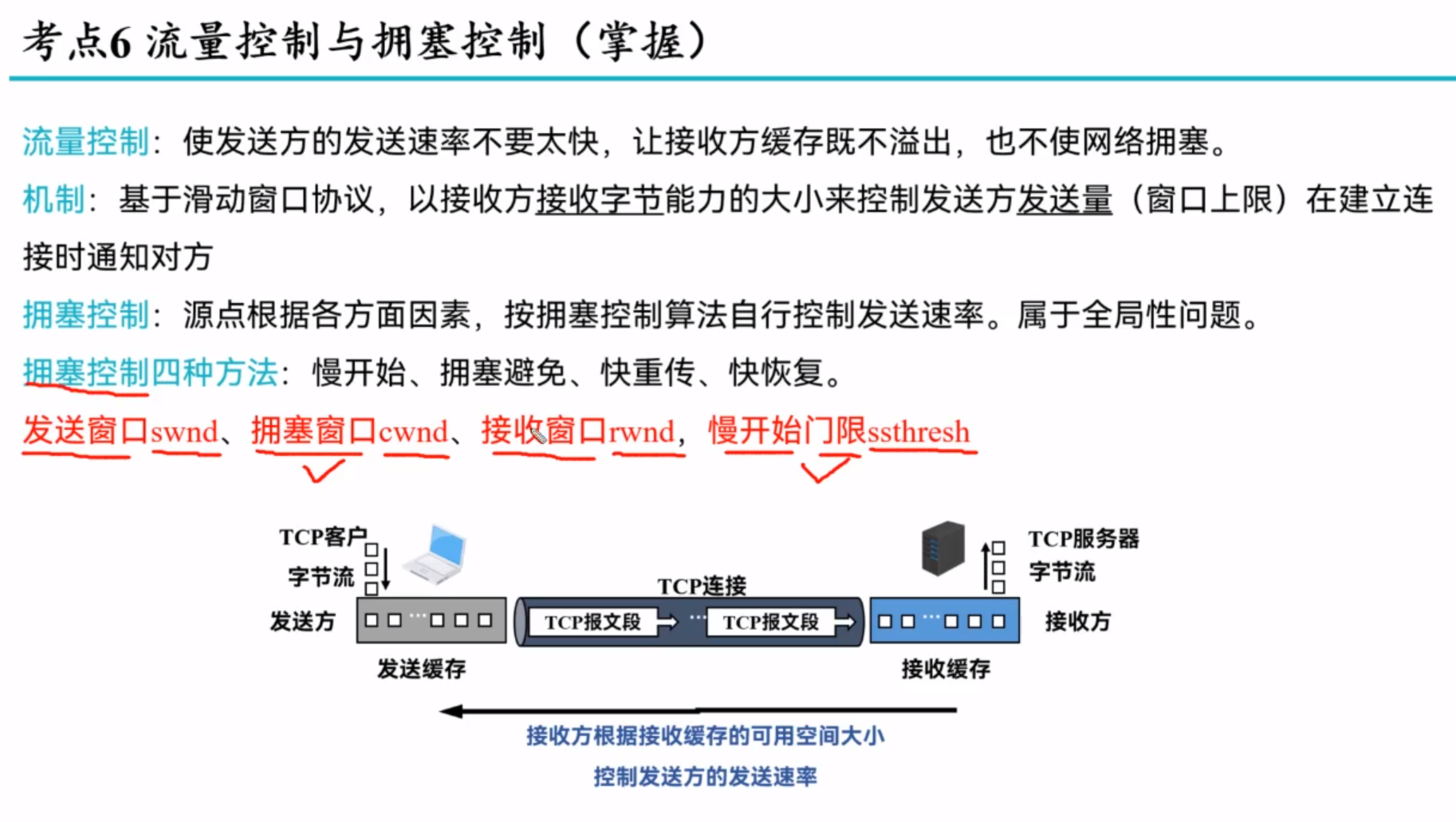
Principles of congestion control


Lecture 6-8 the network layer
Overview




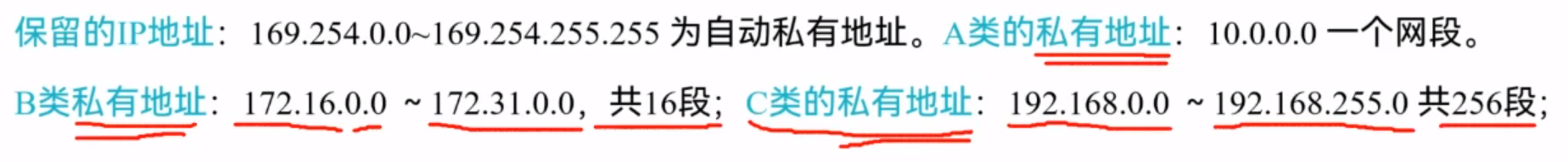
私有地址通常不被因特网上的路由器所转发
子网划分:主机部分不能全为1
Router
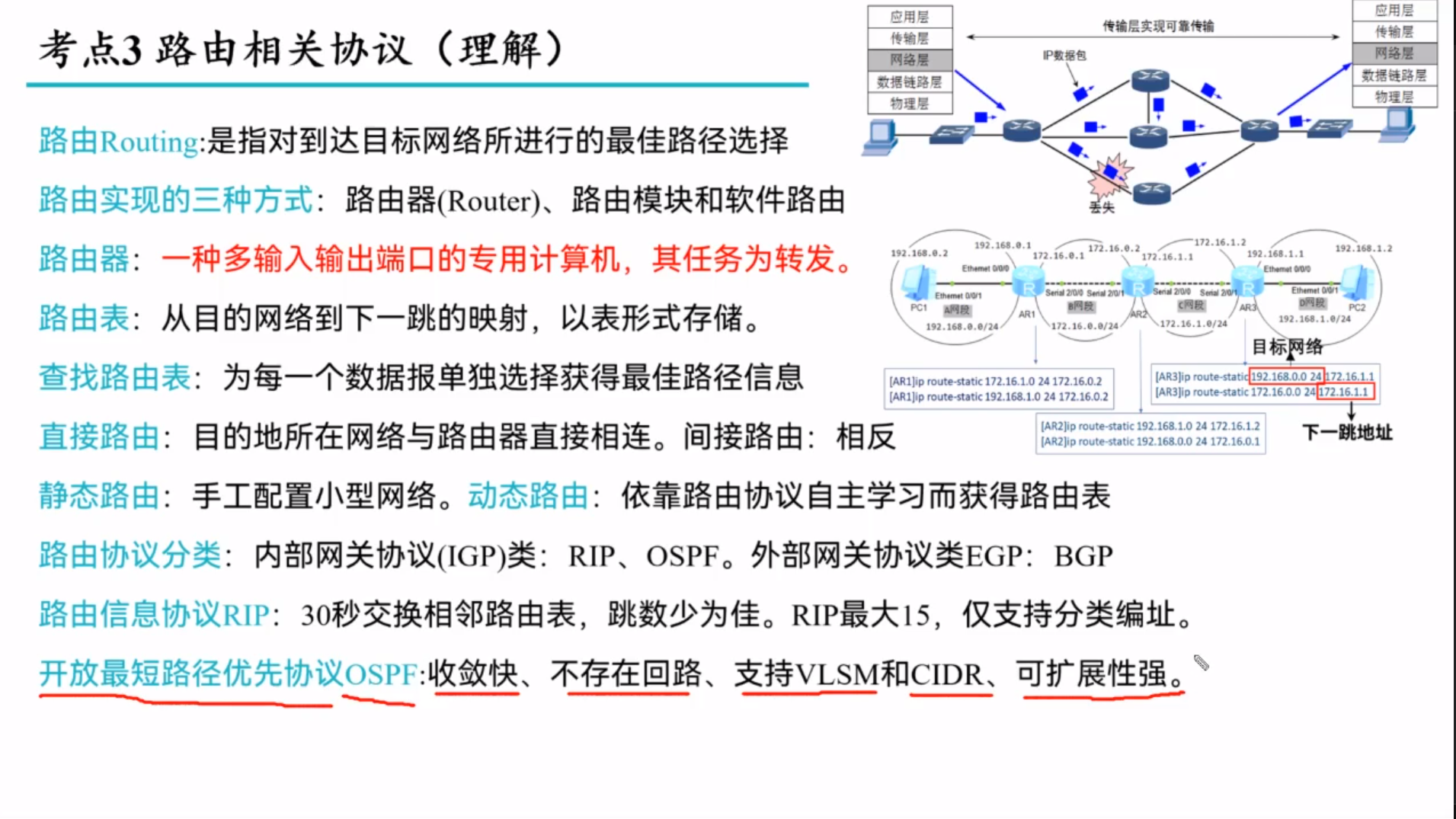


Internet Protocol
IPv4 addressing
NAT
IPv6
Generalized Forward and SDN
Routing - Distance vector algorithm
Intra-AS routing in the Internet: OSPF
Routing among the ISPs: BGP
The SDN control plan
ICMP
是互联网控制消息协议,是网络层(第三层)中的一个协议。它用于在IP网络上发送错误消息和操作信息,通常用于网络诊断和错误报告。一些常见的 ICMP 消息类型包括 Echo Request 和 Echo Reply,它们被用于 Ping 工具,以测试网络连接和测量往返时间(RTT)。
SNMP
SNMP(Simple Network Management Protocol)是一种用于管理和监控网络设备的协议。它允许网络管理员远程监视和管理网络中的设备,包括路由器、交换机、服务器等。SNMP使得管理员可以检索设备的信息、监视网络性能并进行配置更改。 SNMP采用客户端-服务器模型,其中网络中的管理系统(通常是NMS,Network Management System)通过SNMP协议与被管理的设备进行通信。
Lecture 9-10 - The link layer

Service of link layer

Error detction and correction
Multiple access protocols
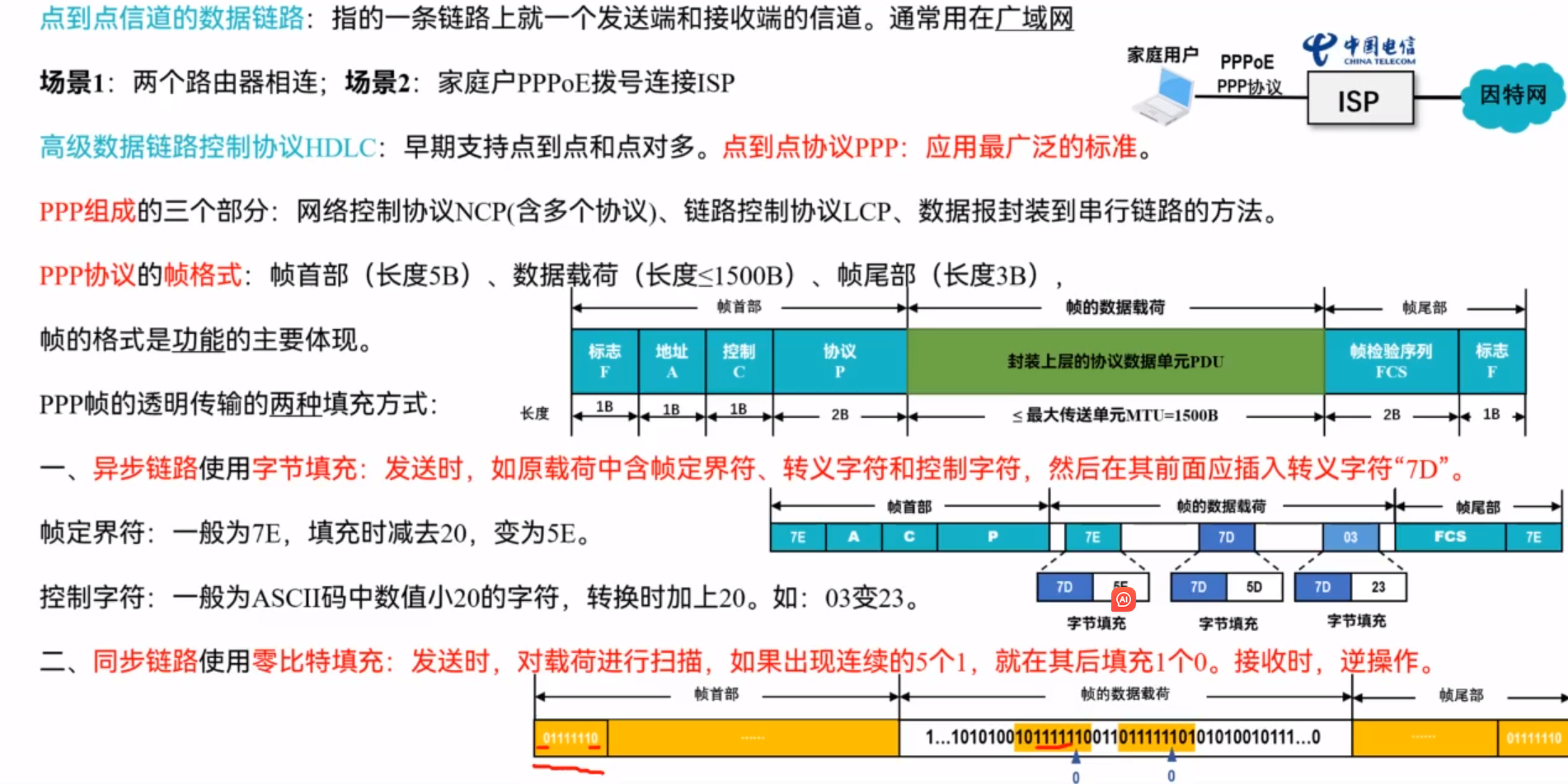
Addressing and ARP
Ethernet 以太网
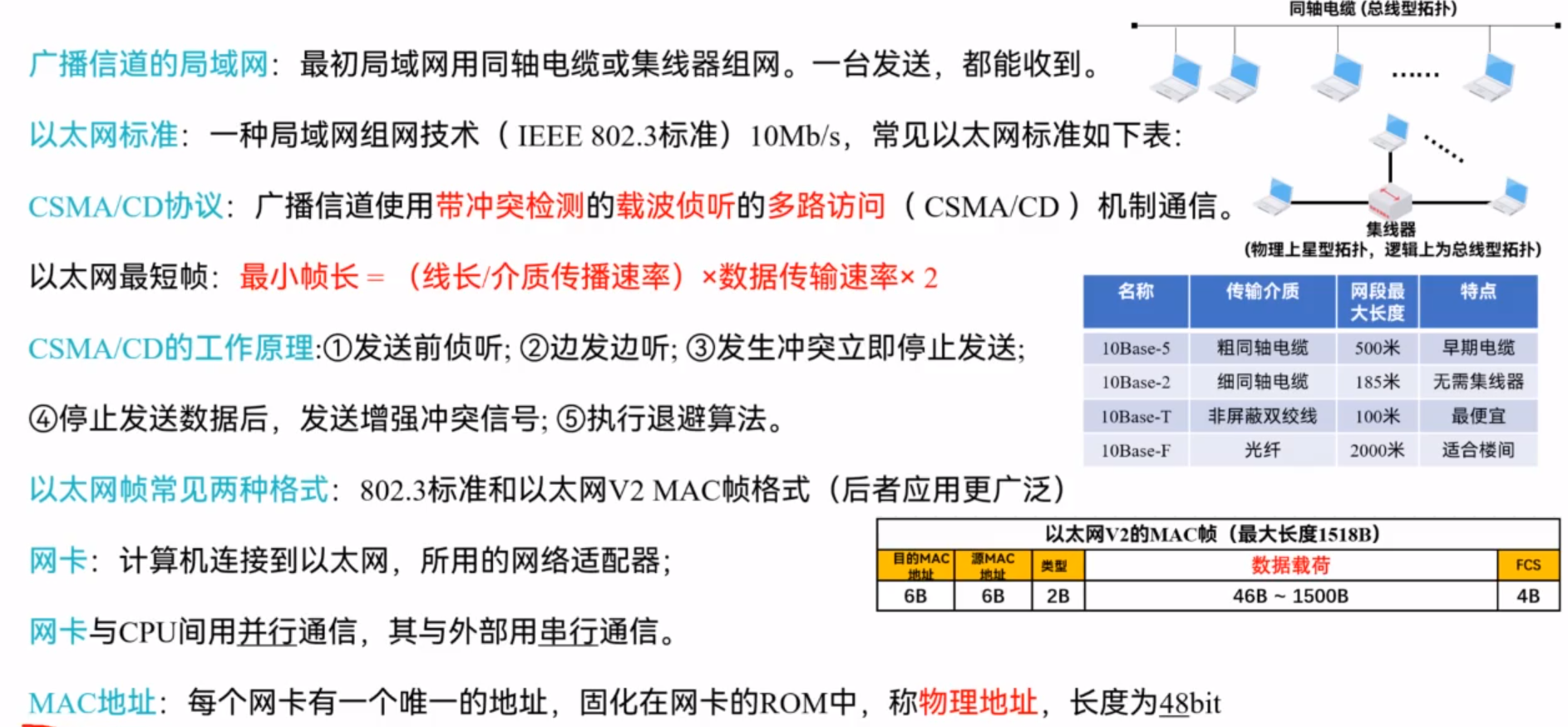

Switches
交换机域叫广播域,集线器域叫冲突域

VLANs 虚拟局域网


Data center networking
Lecture11-12 Network Security

Principles of cryptography
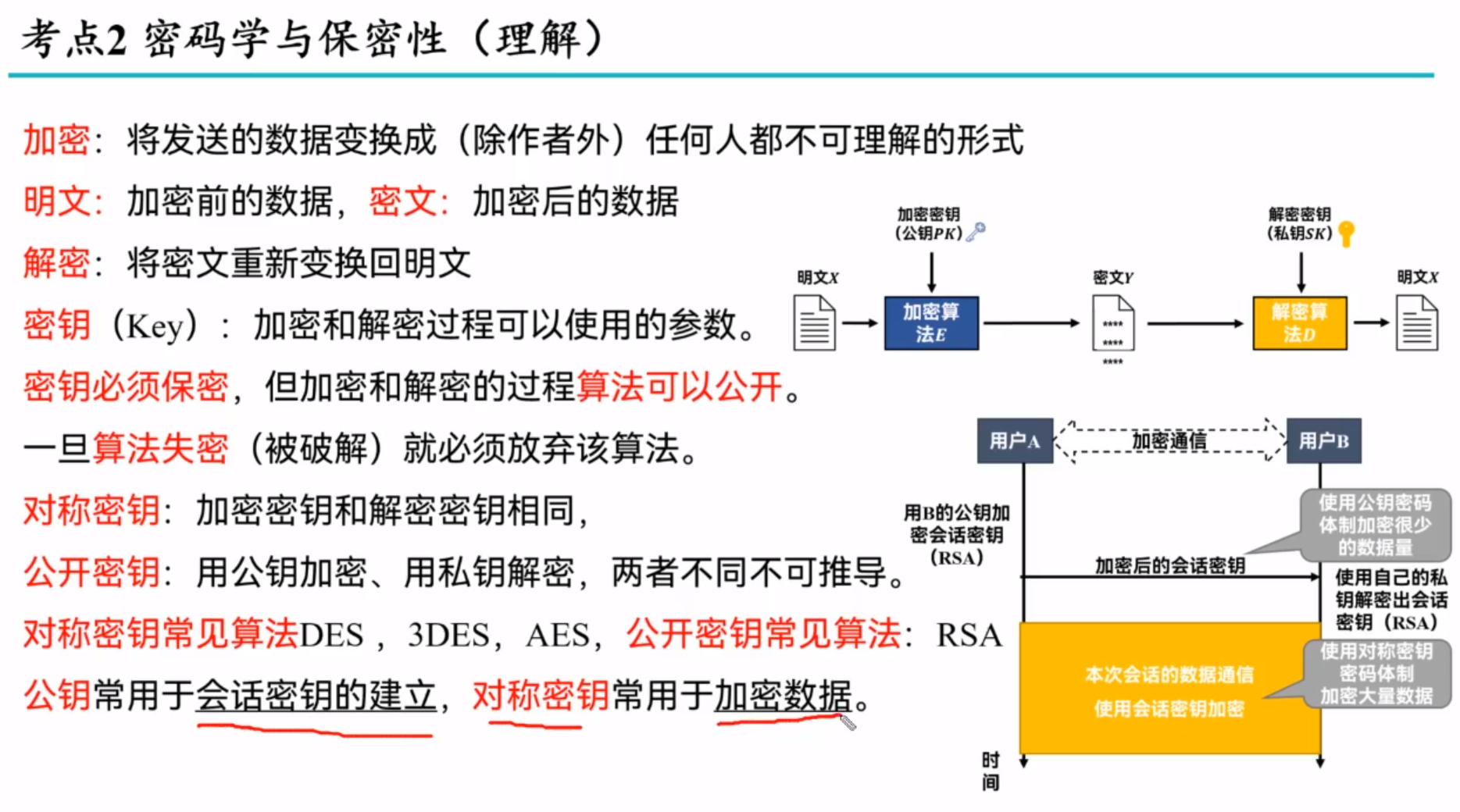
消息认证技术


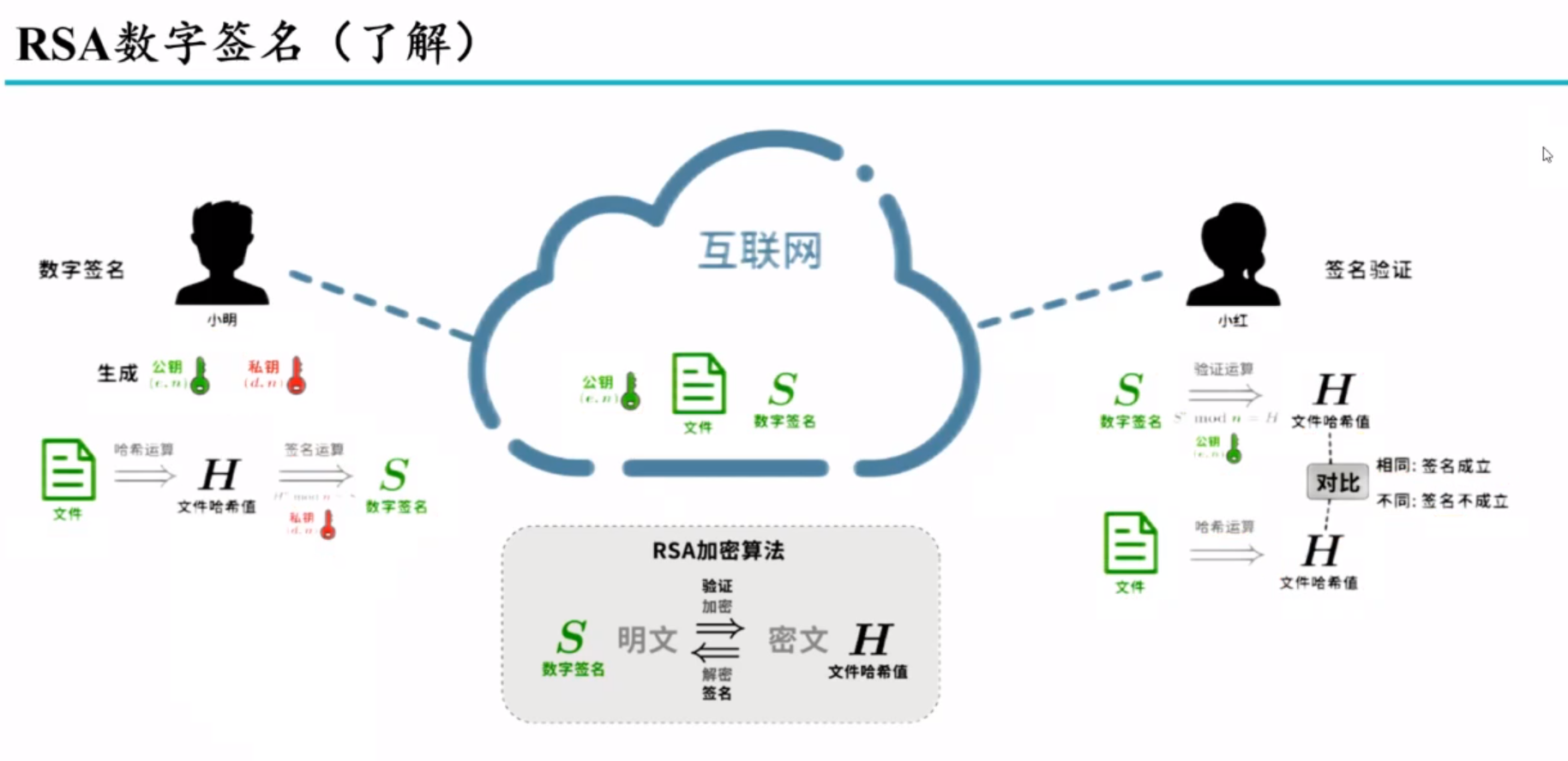

对称加密的优缺点
-
效率高: 对称加密算法通常比非对称加密算法更快速,因为它们使用相同的密钥进行加密和解密操作,不涉及复杂的数学运算。
-
适合大量数据: 对称加密对于加密大量数据是非常有效的,因为它相对较快且计算成本较低。
-
实现简单: 对称加密算法的实现相对简单,容易理解和部署。
缺点:
-
密钥管理: 对称加密需要在通信双方共享密钥,这可能涉及到密钥的安全分发和管理问题。如果密钥在传输过程中被拦截或者泄露,整个加密系统可能会受到威胁。
-
不适合开放环境: 对称加密在需要在不同实体之间安全地共享密钥时可能会面临困难,特别是在开放环境中,比如互联网。
-
密钥数量增长: 在多方通信的情况下,密钥的数量会迅速增长。每对通信实体之间都需要一个独特的密钥,这可能导致密钥管理的复杂性增加。
-
不提供身份验证: 对称加密本身不提供身份验证机制,因此在通信的两端之间可能无法确保对方的身份。
Message integrity, authentication
Securing e-mail
Securing TCP connections:SSL (传输层)
Network layer security:IPsec (网络层)
Operational security: firewalls and IDS入侵检测系统()
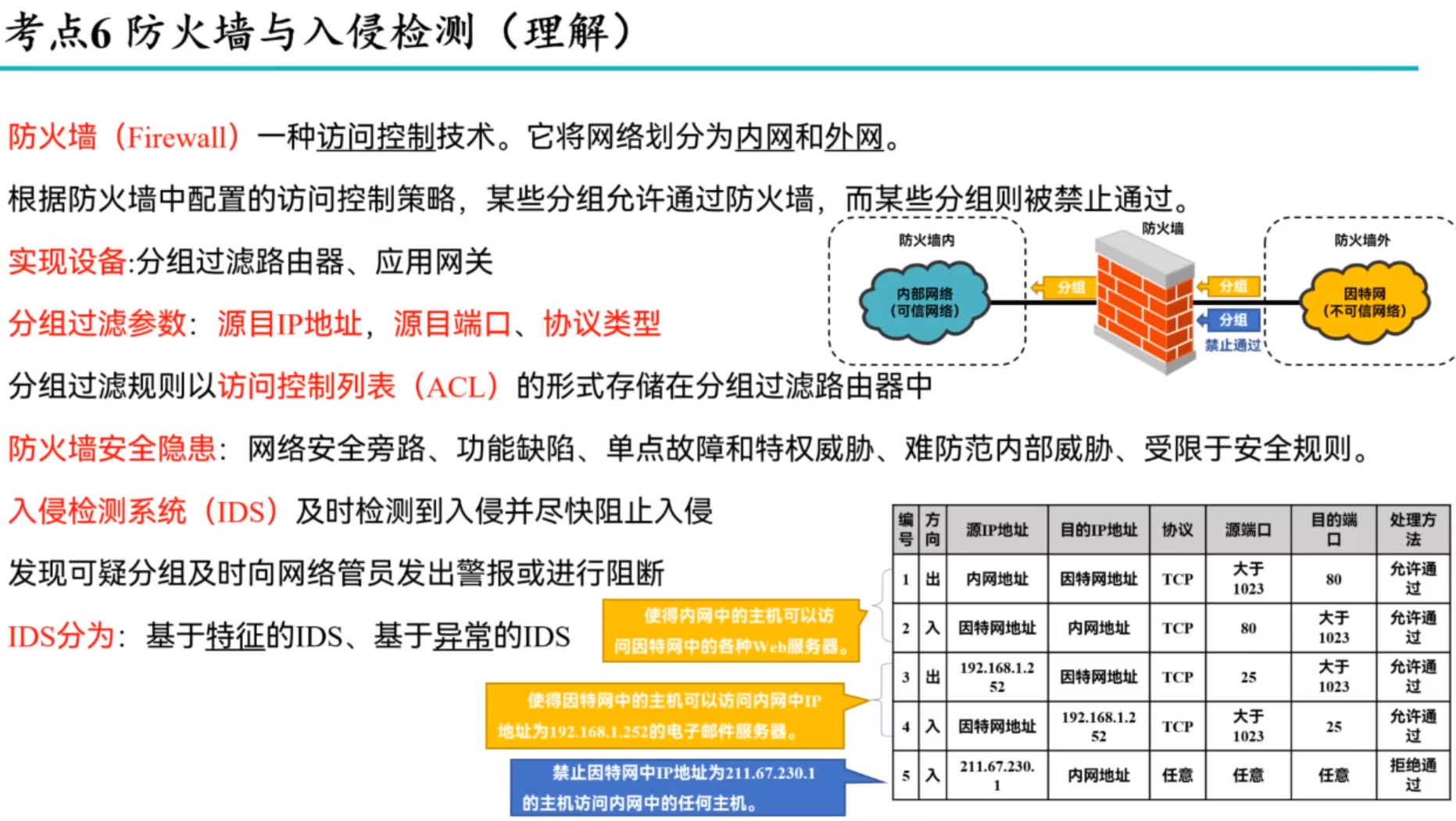
异常:如异常读取等