该篇主要介绍了利用配置ca.cnf、server.cnf、client.cnf在certs路径下生成证书文件(非执行bootstrap脚本,网上也有很多直接通过openssl命令方式生成的文章),主要参考(概括中心思想)官方手册,以及本地证书的认证(参考《使用FREERADIUS搭建EAP认证环境 | SVEN (lishiwen4.github.io)》)。https://networkradius.com/doc/FreeRADIUS-Implementation-Ch6.pdf![]() https://networkradius.com/doc/FreeRADIUS-Implementation-Ch6.pdf(对于该手册,有点不严谨,里面多处笔误,主要体现在生成服务器证书和客户端证书时提到的配置文件上,具体地方由诸位私下去发现,也有点遗漏,链接上前面有提到EAP-TLS的例子,但是文档最后都未提到。这么多年过去了,官方是不是需要重新更新一下各种文档啦~@FreeRADIUS)
https://networkradius.com/doc/FreeRADIUS-Implementation-Ch6.pdf(对于该手册,有点不严谨,里面多处笔误,主要体现在生成服务器证书和客户端证书时提到的配置文件上,具体地方由诸位私下去发现,也有点遗漏,链接上前面有提到EAP-TLS的例子,但是文档最后都未提到。这么多年过去了,官方是不是需要重新更新一下各种文档啦~@FreeRADIUS)
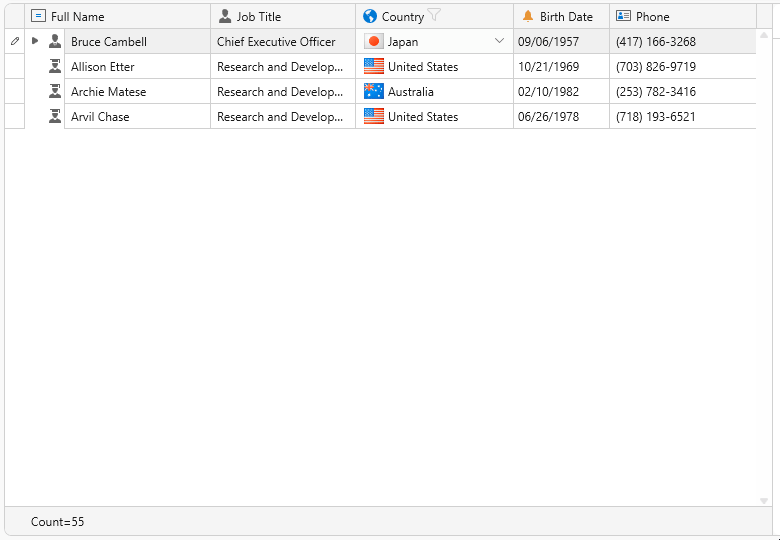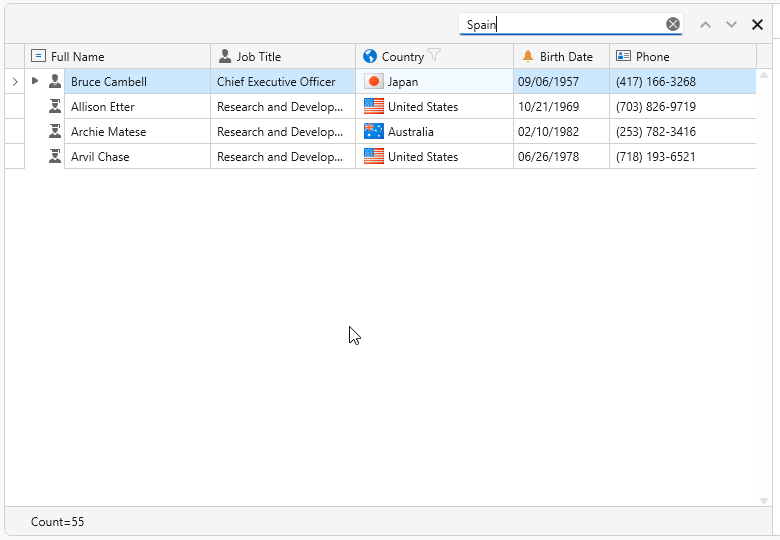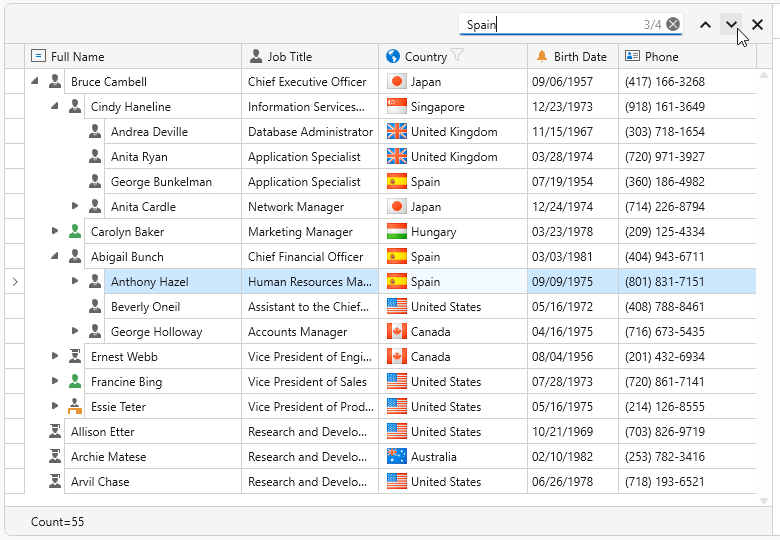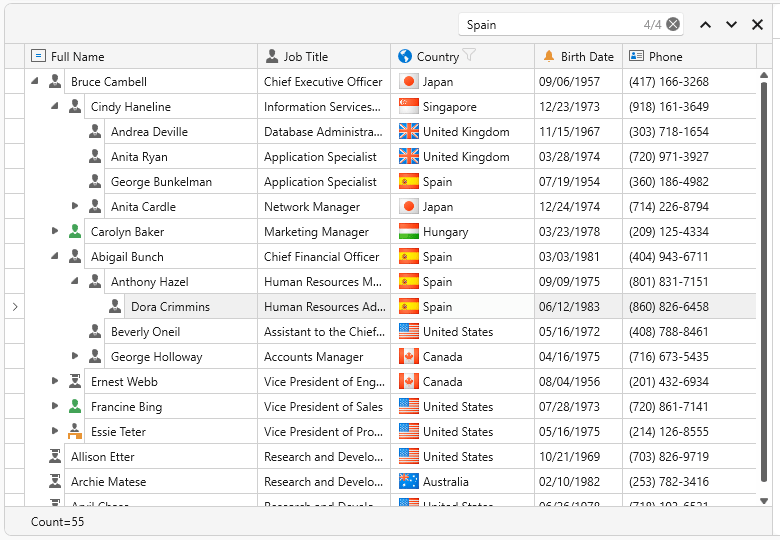
证书创建
删除测试证书文件
# rm -f *.pem *.der *.csr *.crt *.key *.p12 serial* index.txt*清除干净后也可以将bootstrap脚本文件也删除(文档建议,我没删)。
生成根证书
# gedit certs/ca.cnf打开该文件并按实际需要(比如加密方法、有效期、国家、城市、公司、邮箱等等)进行编辑修改,我按照文档修改了[certificate_authority]区域的内容(input_password和output_password我未动,其他证书该部分均未修改),有一点需要注意,每一种证书该文件里面的commonName字段内容必须唯一,否则可能会报错。
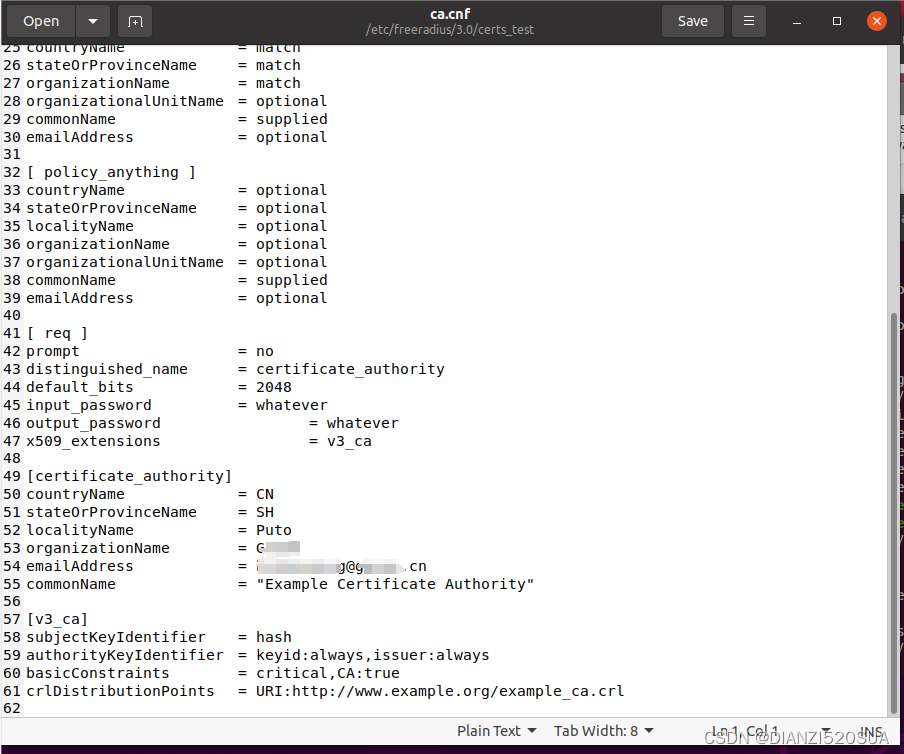
保存好配置后执行如下命令生成目标证书ca.pem.
# make ca.pem对于Windows平台可以make ca.der生成自签名证书。
生成服务器证书
# gedit server.cnf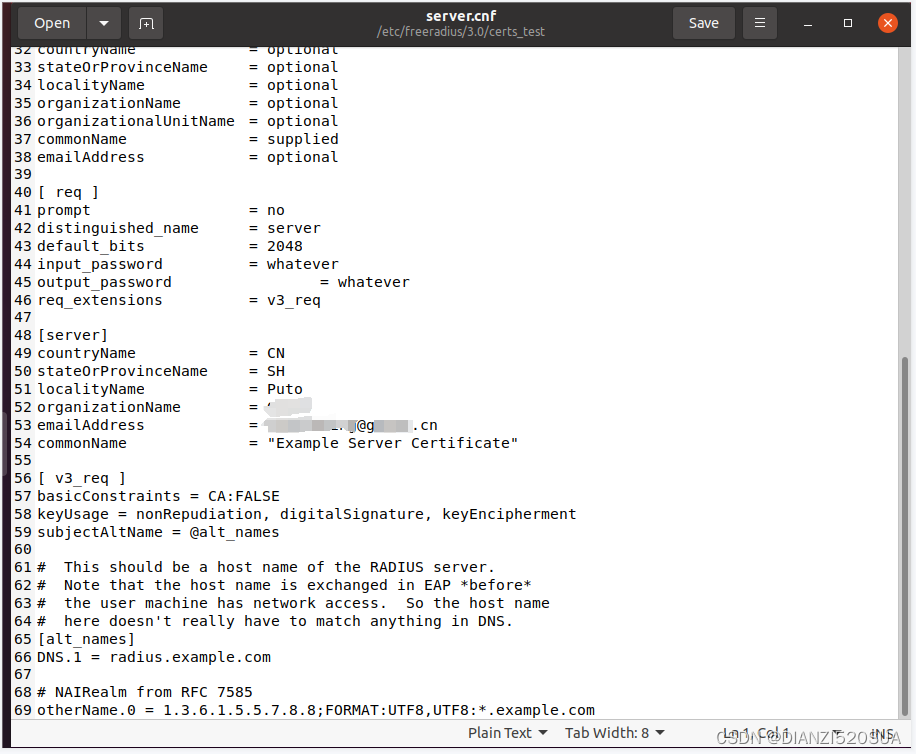
# make server.pem生成客户端证书
# gedit client.cnf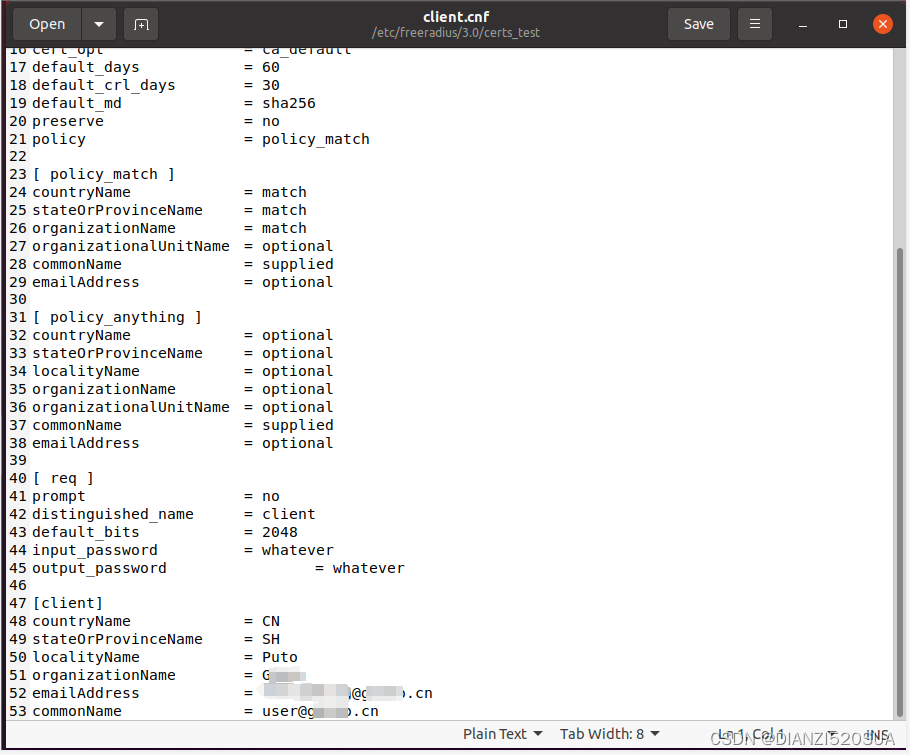
# make client.pem如果要创建生成多个客户端证书,重复以上步骤,需要注意的是密码、登录用户名及commonName域需要保持唯一。
证书测试
首次体验
eap-tls.conf文件创建,内容如下(主要方便eapol_test程序读取应用):
network={eap=TLSeapol_flags=0key_mgmt=IEEE8021Xidentity="testing"password="password"ca_cert="/etc/freeradius/3.0/certs/ca.pem"client_cert="/etc/freeradius/3.0/certs/client.pem"private_key="/etc/freeradius/3.0/certs/client.key"private_key_passwd="whatever"
}测试的用户名是之前配置在users文件中的testing,没用MySQL中的mike,eapol_flags必须置零(该文档注释上有说明,主要针对有线),打开两个终端,分别运行如下语句,
#freeradius -X#eapol_test -c eap-tls.conf -a 127.0.0.1 -p 1812 -s testing123 -r 1不幸的是,结果返回了Failure,有提示什么“asn1....wrong tag”之类的,表面描述直接原因是证书内容不对,最后尝试过生成其他格式的证书,还是一样的问题,最后没招,直接用了certs文件夹内bootstrap脚本生成的证书,依然没有奇迹。
解决问题
有位网友比较细心且有耐心,直接根据报错打印找到wpa_supplicant源码当中去了,得出的结论是老版本的wpa_supplicant对证书的某些校验方法不支持(解析不完善),我当前用的wpa_supplicant版本是0.7.3(编译的openssl版本是0.9.8e),ubuntu20.04里面的openssl版本是1.1.1,所以我们下一步就是升级wpa_supplicant(同样也需升级openssl)。
升级wpa_supplicant
主要参考《wpa_supplicant交叉编译_wpa_supplicant-2.8.tar.gz-CSDN博客》此篇文章,下面简述下主要步骤(桌面版,非嵌入式版本)。
准备版本:wpa_supplicant-2.10.tar.gz + openssl-1.1.1w.tar.gz + libnl-3.9.0.tar.gz
注意项:新版本wpa_supplicant依赖项需要增加libnl(netlink).
下载链接:
[ Downloads ] - /source/index.html (openssl.org) ---> openssl
libnl-3.9.0 (linuxfromscratch.org) ---> libnl
Index of /releases (w1.fi) ---> wpa_supplicant
1.创建文件夹
分别创建ssl、nl文件夹,用来存放安装编译后的openssl及libnl相关的头文件及库文件,方便wpa_supplicant的.config文件引用。
2.1 openssl编译安装
进入openssl源码主目录,依次执行如下命令,注意安装路径需要写上绝对路径,不然会报错。
# ./config --prefix=/home/mike/work/wpa_supplicant/2.10/ssl
# make&&make install2.2 libnl编译安装
进入libnl源码主目录,依次执行如下命令,如果提示找不到flex、bison之类的错误,可以通过sudo apt-get install flex和sudo apt-get install bison解决。
# ./configure --prefix=/home/mike/work/wpa_supplicant/2.10/nl
# make&&make install2.3 wpa_supplicant编译安装
进入wpa_supplicant源码主目录,依次执行如下命令,
# cd wpa_supplicant
# cp deconfig .config打开.config文件作如下修改,打开EAPOL_TEST注释,让生成eapol_test文件供测试,
CFLAGS += -I/home/mike/work/wpa_supplicant/2.10/ssl/include
LIBS += -L//home/mike/work/wpa_supplicant/2.10/ssl/libCFLAGS += -I/home/mike/work/wpa_supplicant/2.10/nl/include/libnl3
LIBS += -L/home/mike/work/wpa_supplicant/2.10/nl/libexport PKG_CONFIG_PATH=/home/mike/work/wpa_supplicant/2.10/nl/lib/pkgconfig:$PKG_CONFIG_PATHCONFIG_EAPOL_TEST=y保存好后直接执行make,但凡事都不会那么顺利,这最后一步一般会报dbus相关的错误,我的解决方式是注释掉DBUS相关的内容(.config),让dbus不参与编译,如下,
#CONFIG_CTRL_IFACE_DBUS_NEW=y#CONFIG_CTRL_IFACE_DBUS_INTRO=y还可参考《https://www.linuxfromscratch.org/blfs/view/svn/basicnet/wpa_supplicant.html》这篇打补丁解决(如果实际需要IFACE_DBUS相关功能的话)。
执行完make后wpa_supplicant、wpa_passphrase、wpa_cli均有生成,但是没有eapol_test,只有个eapol_test.py,单独通过如下命令生成eapol_test执行文件,
# make eapol_test至此升级工作完成。
再次测试
将之前创建的eap-tls.conf文件复制到新的wpa_supplicant路径下,开启俩终端,分别执行
# freeradius -X# eapol_test -c eap-tls.conf -a 127.0.0.1 -p 1812 -s testing123 -r 1(测试用的证书是bootstrap脚本生成)
freeradius端部分输出如下:
(1) EAP-Message = 0x01b503ec0dc000000b5c160303003d02000039030311eac75f3f748e3dfcf6e1de94d5d4832800322221b5f49efcb8ce4a0ba8c0ad00c030000011ff01000100000b0004030001020017000016030308e90b0008e50008e20003de308203da308202c2a003020102020101300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a307c310b3009060355040613024652310f300d06035504080c0652616469757331153013060355040a0c0c4578616d706c6520496e632e3123302106035504030c1a4578616d70
(1) Message-Authenticator = 0x00000000000000000000000000000000
(1) State = 0x6c230b426d9606dd3f72ef77da978e44
(1) Finished request
Waking up in 4.9 seconds.
(2) Received Access-Request Id 2 from 127.0.0.1:37016 to 127.0.0.1:1812 length 140
(2) User-Name = "testing"
(2) NAS-IP-Address = 127.0.0.1
(2) Calling-Station-Id = "02-00-00-00-00-01"
(2) Framed-MTU = 1400
(2) NAS-Port-Type = Wireless-802.11
(2) Service-Type = Framed-User
(2) Connect-Info = "CONNECT 11Mbps 802.11b"
(2) EAP-Message = 0x02b500060d00
(2) State = 0x6c230b426d9606dd3f72ef77da978e44
(2) Message-Authenticator = 0xb59edee3915c6dc7cc64ec2d9d00e109
(2) session-state: No cached attributes
(2) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(2) authorize {
(2) policy filter_username {
(2) if (&User-Name) {
(2) if (&User-Name) -> TRUE
(2) if (&User-Name) {
(2) if (&User-Name =~ / /) {
(2) if (&User-Name =~ / /) -> FALSE
(2) if (&User-Name =~ /@[^@]*@/ ) {
(2) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(2) if (&User-Name =~ /\.\./ ) {
(2) if (&User-Name =~ /\.\./ ) -> FALSE
(2) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(2) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(2) if (&User-Name =~ /\.$/) {
(2) if (&User-Name =~ /\.$/) -> FALSE
(2) if (&User-Name =~ /@\./) {
(2) if (&User-Name =~ /@\./) -> FALSE
(2) } # if (&User-Name) = notfound
(2) } # policy filter_username = notfound
(2) [preprocess] = ok
(2) [chap] = noop
(2) [mschap] = noop
(2) [digest] = noop
(2) suffix: Checking for suffix after "@"
(2) suffix: No '@' in User-Name = "testing", looking up realm NULL
(2) suffix: No such realm "NULL"
(2) [suffix] = noop
(2) eap: Peer sent EAP Response (code 2) ID 181 length 6
(2) eap: No EAP Start, assuming it's an on-going EAP conversation
(2) [eap] = updated
(2) files: users: Matched entry testing at line 87
(2) [files] = ok
(2) [expiration] = noop
(2) [logintime] = noop
(2) pap: WARNING: Auth-Type already set. Not setting to PAP
(2) [pap] = noop
(2) } # authorize = updated
(2) Found Auth-Type = eap
(2) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(2) authenticate {
(2) eap: Expiring EAP session with state 0x6c230b426d9606dd
(2) eap: Finished EAP session with state 0x6c230b426d9606dd
(2) eap: Previous EAP request found for state 0x6c230b426d9606dd, released from the list
(2) eap: Peer sent packet with method EAP TLS (13)
(2) eap: Calling submodule eap_tls to process data
(2) eap_tls: Continuing EAP-TLS
(2) eap_tls: Peer ACKed our handshake fragment
(2) eap_tls: [eaptls verify] = request
(2) eap_tls: [eaptls process] = handled
(2) eap: Sending EAP Request (code 1) ID 182 length 1004
(2) eap: EAP session adding &reply:State = 0x6c230b426e9506dd
(2) [eap] = handled
(2) } # authenticate = handled
(2) Using Post-Auth-Type Challenge
(2) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(2) Challenge { ... } # empty sub-section is ignored
(2) Sent Access-Challenge Id 2 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(2) EAP-Message = 0x01b603ec0dc000000b5cd38235a4811c3f2e4cc129e388ad6f6c6237386b5f4d7ecc8d193c2465dfe051194474b53e1ac364e4b8fdcb527d6de8ca809cbfd5eb53a47785e62eaa3f7bafbeff699f9e631a78efbd38d6270004fe308204fa308203e2a00302010202144a1dec91e0857d76d65f37d6ddaab4191176ebcb300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d657768657265
(2) Message-Authenticator = 0x00000000000000000000000000000000
(2) State = 0x6c230b426e9506dd3f72ef77da978e44
(2) Finished request
Waking up in 4.9 seconds.
(3) Received Access-Request Id 3 from 127.0.0.1:37016 to 127.0.0.1:1812 length 140
(3) User-Name = "testing"
(3) NAS-IP-Address = 127.0.0.1
(3) Calling-Station-Id = "02-00-00-00-00-01"
(3) Framed-MTU = 1400
(3) NAS-Port-Type = Wireless-802.11
(3) Service-Type = Framed-User
(3) Connect-Info = "CONNECT 11Mbps 802.11b"
(3) EAP-Message = 0x02b600060d00
(3) State = 0x6c230b426e9506dd3f72ef77da978e44
(3) Message-Authenticator = 0xc5f5d8ac30024f696a340a2a89a1c0cb
(3) session-state: No cached attributes
(3) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(3) authorize {
(3) policy filter_username {
(3) if (&User-Name) {
(3) if (&User-Name) -> TRUE
(3) if (&User-Name) {
(3) if (&User-Name =~ / /) {
(3) if (&User-Name =~ / /) -> FALSE
(3) if (&User-Name =~ /@[^@]*@/ ) {
(3) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(3) if (&User-Name =~ /\.\./ ) {
(3) if (&User-Name =~ /\.\./ ) -> FALSE
(3) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(3) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(3) if (&User-Name =~ /\.$/) {
(3) if (&User-Name =~ /\.$/) -> FALSE
(3) if (&User-Name =~ /@\./) {
(3) if (&User-Name =~ /@\./) -> FALSE
(3) } # if (&User-Name) = notfound
(3) } # policy filter_username = notfound
(3) [preprocess] = ok
(3) [chap] = noop
(3) [mschap] = noop
(3) [digest] = noop
(3) suffix: Checking for suffix after "@"
(3) suffix: No '@' in User-Name = "testing", looking up realm NULL
(3) suffix: No such realm "NULL"
(3) [suffix] = noop
(3) eap: Peer sent EAP Response (code 2) ID 182 length 6
(3) eap: No EAP Start, assuming it's an on-going EAP conversation
(3) [eap] = updated
(3) files: users: Matched entry testing at line 87
(3) [files] = ok
(3) [expiration] = noop
(3) [logintime] = noop
(3) pap: WARNING: Auth-Type already set. Not setting to PAP
(3) [pap] = noop
(3) } # authorize = updated
(3) Found Auth-Type = eap
(3) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(3) authenticate {
(3) eap: Expiring EAP session with state 0x6c230b426e9506dd
(3) eap: Finished EAP session with state 0x6c230b426e9506dd
(3) eap: Previous EAP request found for state 0x6c230b426e9506dd, released from the list
(3) eap: Peer sent packet with method EAP TLS (13)
(3) eap: Calling submodule eap_tls to process data
(3) eap_tls: Continuing EAP-TLS
(3) eap_tls: Peer ACKed our handshake fragment
(3) eap_tls: [eaptls verify] = request
(3) eap_tls: [eaptls process] = handled
(3) eap: Sending EAP Request (code 1) ID 183 length 930
(3) eap: EAP session adding &reply:State = 0x6c230b426f9406dd
(3) [eap] = handled
(3) } # authenticate = handled
(3) Using Post-Auth-Type Challenge
(3) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(3) Challenge { ... } # empty sub-section is ignored
(3) Sent Access-Challenge Id 3 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(3) EAP-Message = 0x01b703a20d8000000b5c857d76d65f37d6ddaab4191176ebcb300f0603551d130101ff040530030101ff30360603551d1f042f302d302ba029a0278625687474703a2f2f7777772e6578616d706c652e6f72672f6578616d706c655f63612e63726c300d06092a864886f70d01010b050003820101005a51d379e5b56b816e7a7bd9ea454a1a686230c60c53f17ca70b7f716c0c0da2ebafbaacf1615dac121f23e4b9f83b66700c2dbf935a16e9ad936fb6c608f9f12cbd45027e0889e6b59c78cc47f407ea36e32bdd38ae9a5bf3909bf68c0328e3bef677fec2d98731b1bd09456832b211c86574121e3f2e8de75602b0f5eb974f3a4de26a81549722779451a947d69b5dc9f7b388e21974d5ed3518b704d951a1eda7301d009493e3fc407ebbae924df016903a69adc37909ecdf3722eb1b964633fccd6eefd8f94ccce6108ce3e84b1d4d6e8a257b20e0babdc53cd8b240e9ca8440bd977a4db811814164a7890abb48d0642a83d23a901c605465ffeeeac24116
(3) Message-Authenticator = 0x00000000000000000000000000000000
(3) State = 0x6c230b426f9406dd3f72ef77da978e44
(3) Finished request
Waking up in 4.9 seconds.
(4) Received Access-Request Id 4 from 127.0.0.1:37016 to 127.0.0.1:1812 length 1552
(4) User-Name = "testing"
(4) NAS-IP-Address = 127.0.0.1
(4) Calling-Station-Id = "02-00-00-00-00-01"
(4) Framed-MTU = 1400
(4) NAS-Port-Type = Wireless-802.11
(4) Service-Type = Framed-User
(4) Connect-Info = "CONNECT 11Mbps 802.11b"
(4) EAP-Message = 0x02b705800dc000000a6e16030308de0b0008da0008d70003d3308203cf308202b7a003020102020102300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a3071310b3009060355040613024652310f300d06035504080c0652616469757331153013060355040a0c0c4578616d706c6520496e632e3119301706035504030c1075736572406578616d706c652e6f7267311f301d06092a864886f70d010901161075736572406578616d706c652e6f726730820122300d06092a864886f70d0101010500038201
(4) State = 0x6c230b426f9406dd3f72ef77da978e44
(4) Message-Authenticator = 0x8228db5cf9000b6b8ed9b81d4a63193b
(4) session-state: No cached attributes
(4) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(4) authorize {
(4) policy filter_username {
(4) if (&User-Name) {
(4) if (&User-Name) -> TRUE
(4) if (&User-Name) {
(4) if (&User-Name =~ / /) {
(4) if (&User-Name =~ / /) -> FALSE
(4) if (&User-Name =~ /@[^@]*@/ ) {
(4) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(4) if (&User-Name =~ /\.\./ ) {
(4) if (&User-Name =~ /\.\./ ) -> FALSE
(4) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(4) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(4) if (&User-Name =~ /\.$/) {
(4) if (&User-Name =~ /\.$/) -> FALSE
(4) if (&User-Name =~ /@\./) {
(4) if (&User-Name =~ /@\./) -> FALSE
(4) } # if (&User-Name) = notfound
(4) } # policy filter_username = notfound
(4) [preprocess] = ok
(4) [chap] = noop
(4) [mschap] = noop
(4) [digest] = noop
(4) suffix: Checking for suffix after "@"
(4) suffix: No '@' in User-Name = "testing", looking up realm NULL
(4) suffix: No such realm "NULL"
(4) [suffix] = noop
(4) eap: Peer sent EAP Response (code 2) ID 183 length 1408
(4) eap: No EAP Start, assuming it's an on-going EAP conversation
(4) [eap] = updated
(4) files: users: Matched entry testing at line 87
(4) [files] = ok
(4) [expiration] = noop
(4) [logintime] = noop
(4) pap: WARNING: Auth-Type already set. Not setting to PAP
(4) [pap] = noop
(4) } # authorize = updated
(4) Found Auth-Type = eap
(4) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(4) authenticate {
(4) eap: Expiring EAP session with state 0x6c230b426f9406dd
(4) eap: Finished EAP session with state 0x6c230b426f9406dd
(4) eap: Previous EAP request found for state 0x6c230b426f9406dd, released from the list
(4) eap: Peer sent packet with method EAP TLS (13)
(4) eap: Calling submodule eap_tls to process data
(4) eap_tls: Continuing EAP-TLS
(4) eap_tls: Peer indicated complete TLS record size will be 2670 bytes
(4) eap_tls: Expecting 2 TLS record fragments
(4) eap_tls: Got first TLS record fragment (1398 bytes). Peer indicated more fragments to follow
(4) eap_tls: [eaptls verify] = first fragment
(4) eap_tls: ACKing Peer's TLS record fragment
(4) eap_tls: [eaptls process] = handled
(4) eap: Sending EAP Request (code 1) ID 184 length 6
(4) eap: EAP session adding &reply:State = 0x6c230b42689b06dd
(4) [eap] = handled
(4) } # authenticate = handled
(4) Using Post-Auth-Type Challenge
(4) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(4) Challenge { ... } # empty sub-section is ignored
(4) Sent Access-Challenge Id 4 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(4) EAP-Message = 0x01b800060d00
(4) Message-Authenticator = 0x00000000000000000000000000000000
(4) State = 0x6c230b42689b06dd3f72ef77da978e44
(4) Finished request
Waking up in 4.9 seconds.
(5) Received Access-Request Id 5 from 127.0.0.1:37016 to 127.0.0.1:1812 length 1422
(5) User-Name = "testing"
(5) NAS-IP-Address = 127.0.0.1
(5) Calling-Station-Id = "02-00-00-00-00-01"
(5) Framed-MTU = 1400
(5) NAS-Port-Type = Wireless-802.11
(5) Service-Type = Framed-User
(5) Connect-Info = "CONNECT 11Mbps 802.11b"
(5) EAP-Message = 0x02b804fe0d000382010f003082010a0282010100d7ab97ba11f901e2bcbe703c7b5a468fea2a402bd27b361c815926d7d1f57fc33a400483d80c8a3fbceb16bca825981cda2ec7330b407800f17dcff77618b2f6a4a7a92216ef2ca4200e5be35a17a0f2a15bf8b43312c66290729aeab2c5ba237ec94e9a1f5257483eeede76626d677f0dd91ee89202fc8dae4e3c015fb98a4f0750aa0e7ed1bd5c3a6b8623638d876f4dab25690be87e096d7e887529072bd3eedea0bff065fd9b79914e0e7b740f236f20372b3b0ad1e9acec52b37541cea0af33729dae3e4a6322e86b44a159c6df35790b0b6a26fc9428a8f323e35198648b7b509350f3dd72929ab5f2970f5dd4ef271575f3665b69b5bd94768b84783f0203010001a38201423082013e301d0603551d0e0416041401571d779e50f5b591d6dad496f89ac3bc91cf273081d30603551d230481cb3081c8801401571d779e50f5b591d6dad496f89ac3bc91cf27a18199a48196308193310b3009060355040613
(5) State = 0x6c230b42689b06dd3f72ef77da978e44
(5) Message-Authenticator = 0x9e2711b54704816bd91181531d40d2ae
(5) session-state: No cached attributes
(5) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(5) authorize {
(5) policy filter_username {
(5) if (&User-Name) {
(5) if (&User-Name) -> TRUE
(5) if (&User-Name) {
(5) if (&User-Name =~ / /) {
(5) if (&User-Name =~ / /) -> FALSE
(5) if (&User-Name =~ /@[^@]*@/ ) {
(5) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(5) if (&User-Name =~ /\.\./ ) {
(5) if (&User-Name =~ /\.\./ ) -> FALSE
(5) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(5) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(5) if (&User-Name =~ /\.$/) {
(5) if (&User-Name =~ /\.$/) -> FALSE
(5) if (&User-Name =~ /@\./) {
(5) if (&User-Name =~ /@\./) -> FALSE
(5) } # if (&User-Name) = notfound
(5) } # policy filter_username = notfound
(5) [preprocess] = ok
(5) [chap] = noop
(5) [mschap] = noop
(5) [digest] = noop
(5) suffix: Checking for suffix after "@"
(5) suffix: No '@' in User-Name = "testing", looking up realm NULL
(5) suffix: No such realm "NULL"
(5) [suffix] = noop
(5) eap: Peer sent EAP Response (code 2) ID 184 length 1278
(5) eap: No EAP Start, assuming it's an on-going EAP conversation
(5) [eap] = updated
(5) files: users: Matched entry testing at line 87
(5) [files] = ok
(5) [expiration] = noop
(5) [logintime] = noop
(5) pap: WARNING: Auth-Type already set. Not setting to PAP
(5) [pap] = noop
(5) } # authorize = updated
(5) Found Auth-Type = eap
(5) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(5) authenticate {
(5) eap: Expiring EAP session with state 0x6c230b42689b06dd
(5) eap: Finished EAP session with state 0x6c230b42689b06dd
(5) eap: Previous EAP request found for state 0x6c230b42689b06dd, released from the list
(5) eap: Peer sent packet with method EAP TLS (13)
(5) eap: Calling submodule eap_tls to process data
(5) eap_tls: Continuing EAP-TLS
(5) eap_tls: Got final TLS record fragment (1272 bytes)
(5) eap_tls: [eaptls verify] = ok
(5) eap_tls: Done initial handshake
(5) eap_tls: TLS_accept: SSLv3/TLS write server done
(5) eap_tls: <<< recv TLS 1.2 [length 08de]
(5) eap_tls: TLS - Creating attributes from certificate OIDs
(5) eap_tls: TLS-Cert-Serial := "4a1dec91e0857d76d65f37d6ddaab4191176ebcb"
(5) eap_tls: TLS-Cert-Expiration := "240421025525Z"
(5) eap_tls: TLS-Cert-Subject := "/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authority"
(5) eap_tls: TLS-Cert-Issuer := "/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authority"
(5) eap_tls: TLS-Cert-Common-Name := "Example Certificate Authority"
(5) eap_tls: TLS - Creating attributes from certificate OIDs
(5) eap_tls: TLS-Client-Cert-Serial := "02"
(5) eap_tls: TLS-Client-Cert-Expiration := "240421025525Z"
(5) eap_tls: TLS-Client-Cert-Subject := "/C=FR/ST=Radius/O=Example Inc./CN=user@example.org/emailAddress=user@example.org"
(5) eap_tls: TLS-Client-Cert-Issuer := "/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authority"
(5) eap_tls: TLS-Client-Cert-Common-Name := "user@example.org"
(5) eap_tls: TLS-Client-Cert-X509v3-Extended-Key-Usage += "TLS Web Client Authentication"
(5) eap_tls: TLS-Client-Cert-X509v3-Extended-Key-Usage-OID += "1.3.6.1.5.5.7.3.2"
(5) eap_tls: TLS_accept: SSLv3/TLS read client certificate
(5) eap_tls: <<< recv TLS 1.2 [length 0046]
(5) eap_tls: TLS_accept: SSLv3/TLS read client key exchange
(5) eap_tls: <<< recv TLS 1.2 [length 0108]
(5) eap_tls: TLS_accept: SSLv3/TLS read certificate verify
(5) eap_tls: TLS_accept: SSLv3/TLS read change cipher spec
(5) eap_tls: <<< recv TLS 1.2 [length 0010]
(5) eap_tls: TLS_accept: SSLv3/TLS read finished
(5) eap_tls: >>> send TLS 1.2 [length 0001]
(5) eap_tls: TLS_accept: SSLv3/TLS write change cipher spec
(5) eap_tls: >>> send TLS 1.2 [length 0010]
(5) eap_tls: TLS_accept: SSLv3/TLS write finished
(5) eap_tls: (other): SSL negotiation finished successfully
(5) eap_tls: TLS - Connection Established
(5) eap_tls: TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(5) eap_tls: TLS-Session-Version = "TLS 1.2"
(5) eap_tls: TLS - got 51 bytes of data
(5) eap_tls: [eaptls process] = handled
(5) eap: Sending EAP Request (code 1) ID 185 length 61
(5) eap: EAP session adding &reply:State = 0x6c230b42699a06dd
(5) [eap] = handled
(5) } # authenticate = handled
(5) Using Post-Auth-Type Challenge
(5) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(5) Challenge { ... } # empty sub-section is ignored
(5) session-state: Saving cached attributes
(5) TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(5) TLS-Session-Version = "TLS 1.2"
(5) Sent Access-Challenge Id 5 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(5) EAP-Message = 0x01b9003d0d80000000331403030001011603030028dc53bb3b9e6835a8a8c0d2fbd020917f5be216dd2e27079dbcfa8fb4ed08494bfd8bd80050b4c025
(5) Message-Authenticator = 0x00000000000000000000000000000000
(5) State = 0x6c230b42699a06dd3f72ef77da978e44
(5) Finished request
Waking up in 4.9 seconds.
(6) Received Access-Request Id 6 from 127.0.0.1:37016 to 127.0.0.1:1812 length 140
(6) User-Name = "testing"
(6) NAS-IP-Address = 127.0.0.1
(6) Calling-Station-Id = "02-00-00-00-00-01"
(6) Framed-MTU = 1400
(6) NAS-Port-Type = Wireless-802.11
(6) Service-Type = Framed-User
(6) Connect-Info = "CONNECT 11Mbps 802.11b"
(6) EAP-Message = 0x02b900060d00
(6) State = 0x6c230b42699a06dd3f72ef77da978e44
(6) Message-Authenticator = 0xd60ee5f5d4e73503749e17011d6c7964
(6) Restoring &session-state
(6) &session-state:TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(6) &session-state:TLS-Session-Version = "TLS 1.2"
(6) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(6) authorize {
(6) policy filter_username {
(6) if (&User-Name) {
(6) if (&User-Name) -> TRUE
(6) if (&User-Name) {
(6) if (&User-Name =~ / /) {
(6) if (&User-Name =~ / /) -> FALSE
(6) if (&User-Name =~ /@[^@]*@/ ) {
(6) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(6) if (&User-Name =~ /\.\./ ) {
(6) if (&User-Name =~ /\.\./ ) -> FALSE
(6) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(6) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(6) if (&User-Name =~ /\.$/) {
(6) if (&User-Name =~ /\.$/) -> FALSE
(6) if (&User-Name =~ /@\./) {
(6) if (&User-Name =~ /@\./) -> FALSE
(6) } # if (&User-Name) = notfound
(6) } # policy filter_username = notfound
(6) [preprocess] = ok
(6) [chap] = noop
(6) [mschap] = noop
(6) [digest] = noop
(6) suffix: Checking for suffix after "@"
(6) suffix: No '@' in User-Name = "testing", looking up realm NULL
(6) suffix: No such realm "NULL"
(6) [suffix] = noop
(6) eap: Peer sent EAP Response (code 2) ID 185 length 6
(6) eap: No EAP Start, assuming it's an on-going EAP conversation
(6) [eap] = updated
(6) files: users: Matched entry testing at line 87
(6) [files] = ok
(6) [expiration] = noop
(6) [logintime] = noop
(6) pap: WARNING: Auth-Type already set. Not setting to PAP
(6) [pap] = noop
(6) } # authorize = updated
(6) Found Auth-Type = eap
(6) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(6) authenticate {
(6) eap: Expiring EAP session with state 0x6c230b42699a06dd
(6) eap: Finished EAP session with state 0x6c230b42699a06dd
(6) eap: Previous EAP request found for state 0x6c230b42699a06dd, released from the list
(6) eap: Peer sent packet with method EAP TLS (13)
(6) eap: Calling submodule eap_tls to process data
(6) eap_tls: Continuing EAP-TLS
(6) eap_tls: Peer ACKed our handshake fragment. handshake is finished
(6) eap_tls: [eaptls verify] = success
(6) eap_tls: [eaptls process] = success
(6) eap: Sending EAP Success (code 3) ID 185 length 4
(6) eap: Freeing handler
(6) [eap] = ok
(6) } # authenticate = ok
(6) # Executing section post-auth from file /etc/freeradius/3.0/sites-enabled/default
(6) post-auth {
(6) if (session-state:User-Name && reply:User-Name && request:User-Name && (reply:User-Name == request:User-Name)) {
(6) if (session-state:User-Name && reply:User-Name && request:User-Name && (reply:User-Name == request:User-Name)) -> FALSE
(6) update {
(6) &reply::TLS-Session-Cipher-Suite += &session-state:TLS-Session-Cipher-Suite[*] -> 'ECDHE-RSA-AES256-GCM-SHA384'
(6) &reply::TLS-Session-Version += &session-state:TLS-Session-Version[*] -> 'TLS 1.2'
(6) } # update = noop
(6) [exec] = noop
(6) policy remove_reply_message_if_eap {
(6) if (&reply:EAP-Message && &reply:Reply-Message) {
(6) if (&reply:EAP-Message && &reply:Reply-Message) -> FALSE
(6) else {
(6) [noop] = noop
(6) } # else = noop
(6) } # policy remove_reply_message_if_eap = noop
(6) } # post-auth = noop
(6) Sent Access-Accept Id 6 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(6) MS-MPPE-Recv-Key = 0xd27cad7f33ed9c410cc93eca5a5446ca011de90bd79a519d1ce1e48be7f843da
(6) MS-MPPE-Send-Key = 0x60876a7943b0c5ea972e79747049c2033c1f557f0b5e68d1897f4ab3b2fccd10
(6) EAP-Message = 0x03b90004
(6) Message-Authenticator = 0x00000000000000000000000000000000
(6) User-Name = "testing"
(6) Finished request
Waking up in 4.9 seconds.
(7) Received Access-Request Id 7 from 127.0.0.1:37016 to 127.0.0.1:1812 length 128
(7) User-Name = "testing"
(7) NAS-IP-Address = 127.0.0.1
(7) Calling-Station-Id = "02-00-00-00-00-01"
(7) Framed-MTU = 1400
(7) NAS-Port-Type = Wireless-802.11
(7) Service-Type = Framed-User
(7) Connect-Info = "CONNECT 11Mbps 802.11b"
(7) EAP-Message = 0x02ab000c0174657374696e67
(7) Message-Authenticator = 0x0a71043021b8182be018447a91ae3247
(7) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(7) authorize {
(7) policy filter_username {
(7) if (&User-Name) {
(7) if (&User-Name) -> TRUE
(7) if (&User-Name) {
(7) if (&User-Name =~ / /) {
(7) if (&User-Name =~ / /) -> FALSE
(7) if (&User-Name =~ /@[^@]*@/ ) {
(7) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(7) if (&User-Name =~ /\.\./ ) {
(7) if (&User-Name =~ /\.\./ ) -> FALSE
(7) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(7) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(7) if (&User-Name =~ /\.$/) {
(7) if (&User-Name =~ /\.$/) -> FALSE
(7) if (&User-Name =~ /@\./) {
(7) if (&User-Name =~ /@\./) -> FALSE
(7) } # if (&User-Name) = notfound
(7) } # policy filter_username = notfound
(7) [preprocess] = ok
(7) [chap] = noop
(7) [mschap] = noop
(7) [digest] = noop
(7) suffix: Checking for suffix after "@"
(7) suffix: No '@' in User-Name = "testing", looking up realm NULL
(7) suffix: No such realm "NULL"
(7) [suffix] = noop
(7) eap: Peer sent EAP Response (code 2) ID 171 length 12
(7) eap: EAP-Identity reply, returning 'ok' so we can short-circuit the rest of authorize
(7) [eap] = ok
(7) } # authorize = ok
(7) Found Auth-Type = eap
(7) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(7) authenticate {
(7) eap: Peer sent packet with method EAP Identity (1)
(7) eap: Calling submodule eap_tls to process data
(7) eap_tls: Initiating new TLS session
(7) eap_tls: Setting verify mode to require certificate from client
(7) eap_tls: [eaptls start] = request
(7) eap: Sending EAP Request (code 1) ID 172 length 6
(7) eap: EAP session adding &reply:State = 0xfb1c2c65fbb0217d
(7) [eap] = handled
(7) } # authenticate = handled
(7) Using Post-Auth-Type Challenge
(7) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(7) Challenge { ... } # empty sub-section is ignored
(7) Sent Access-Challenge Id 7 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(7) EAP-Message = 0x01ac00060d20
(7) Message-Authenticator = 0x00000000000000000000000000000000
(7) State = 0xfb1c2c65fbb0217da229744af77aa30f
(7) Finished request
Waking up in 4.8 seconds.
(8) Received Access-Request Id 8 from 127.0.0.1:37016 to 127.0.0.1:1812 length 324
(8) User-Name = "testing"
(8) NAS-IP-Address = 127.0.0.1
(8) Calling-Station-Id = "02-00-00-00-00-01"
(8) Framed-MTU = 1400
(8) NAS-Port-Type = Wireless-802.11
(8) Service-Type = Framed-User
(8) Connect-Info = "CONNECT 11Mbps 802.11b"
(8) EAP-Message = 0x02ac00be0d0016030100b3010000af03039dafb8191c05970d0fc3a0a66a19b33e516cbd830a9cf0d7df324390c3af4a30000038c02cc030009fcca9cca8ccaac02bc02f009ec024c028006bc023c0270067c00ac0140039c009c0130033009d009c003d003c0035002f00ff0100004e000b000403000102000a000c000a001d0017001e001900180016000000170000000d002a0028040305030603080708080809080a080b080408050806040105010601030303010302040205020602
(8) State = 0xfb1c2c65fbb0217da229744af77aa30f
(8) Message-Authenticator = 0xd9bf7e70fd9068540f30a0b63f123be0
(8) session-state: No cached attributes
(8) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(8) authorize {
(8) policy filter_username {
(8) if (&User-Name) {
(8) if (&User-Name) -> TRUE
(8) if (&User-Name) {
(8) if (&User-Name =~ / /) {
(8) if (&User-Name =~ / /) -> FALSE
(8) if (&User-Name =~ /@[^@]*@/ ) {
(8) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(8) if (&User-Name =~ /\.\./ ) {
(8) if (&User-Name =~ /\.\./ ) -> FALSE
(8) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(8) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(8) if (&User-Name =~ /\.$/) {
(8) if (&User-Name =~ /\.$/) -> FALSE
(8) if (&User-Name =~ /@\./) {
(8) if (&User-Name =~ /@\./) -> FALSE
(8) } # if (&User-Name) = notfound
(8) } # policy filter_username = notfound
(8) [preprocess] = ok
(8) [chap] = noop
(8) [mschap] = noop
(8) [digest] = noop
(8) suffix: Checking for suffix after "@"
(8) suffix: No '@' in User-Name = "testing", looking up realm NULL
(8) suffix: No such realm "NULL"
(8) [suffix] = noop
(8) eap: Peer sent EAP Response (code 2) ID 172 length 190
(8) eap: No EAP Start, assuming it's an on-going EAP conversation
(8) [eap] = updated
(8) files: users: Matched entry testing at line 87
(8) [files] = ok
(8) [expiration] = noop
(8) [logintime] = noop
(8) pap: WARNING: Auth-Type already set. Not setting to PAP
(8) [pap] = noop
(8) } # authorize = updated
(8) Found Auth-Type = eap
(8) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(8) authenticate {
(8) eap: Expiring EAP session with state 0xfb1c2c65fbb0217d
(8) eap: Finished EAP session with state 0xfb1c2c65fbb0217d
(8) eap: Previous EAP request found for state 0xfb1c2c65fbb0217d, released from the list
(8) eap: Peer sent packet with method EAP TLS (13)
(8) eap: Calling submodule eap_tls to process data
(8) eap_tls: Continuing EAP-TLS
(8) eap_tls: Got final TLS record fragment (184 bytes)
(8) eap_tls: WARNING: Total received TLS record fragments (184 bytes), does not equal indicated TLS record length (0 bytes)
(8) eap_tls: [eaptls verify] = ok
(8) eap_tls: Done initial handshake
(8) eap_tls: (other): before SSL initialization
(8) eap_tls: TLS_accept: before SSL initialization
(8) eap_tls: TLS_accept: before SSL initialization
(8) eap_tls: <<< recv TLS 1.3 [length 00b3]
(8) eap_tls: TLS_accept: SSLv3/TLS read client hello
(8) eap_tls: >>> send TLS 1.2 [length 003d]
(8) eap_tls: TLS_accept: SSLv3/TLS write server hello
(8) eap_tls: >>> send TLS 1.2 [length 08e9]
(8) eap_tls: TLS_accept: SSLv3/TLS write certificate
(8) eap_tls: >>> send TLS 1.2 [length 014d]
(8) eap_tls: TLS_accept: SSLv3/TLS write key exchange
(8) eap_tls: >>> send TLS 1.2 [length 00cc]
(8) eap_tls: TLS_accept: SSLv3/TLS write certificate request
(8) eap_tls: >>> send TLS 1.2 [length 0004]
(8) eap_tls: TLS_accept: SSLv3/TLS write server done
(8) eap_tls: TLS_accept: Need to read more data: SSLv3/TLS write server done
(8) eap_tls: TLS - In Handshake Phase
(8) eap_tls: TLS - got 2908 bytes of data
(8) eap_tls: [eaptls process] = handled
(8) eap: Sending EAP Request (code 1) ID 173 length 1004
(8) eap: EAP session adding &reply:State = 0xfb1c2c65fab1217d
(8) [eap] = handled
(8) } # authenticate = handled
(8) Using Post-Auth-Type Challenge
(8) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(8) Challenge { ... } # empty sub-section is ignored
(8) Sent Access-Challenge Id 8 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(8) EAP-Message = 0x01ad03ec0dc000000b5c160303003d0200003903034292638f3837c75352d28e65b5fe48f830b19c085747f176374c9014f0c9f31e00c030000011ff01000100000b0004030001020017000016030308e90b0008e50008e20003de308203da308202c2a003020102020101300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a307c310b3009060355040613024652310f300d06035504080c0652616469757331153013060355040a0c0c4578616d706c6520496e632e3123302106035504030c1a4578616d70
(8) Message-Authenticator = 0x00000000000000000000000000000000
(8) State = 0xfb1c2c65fab1217da229744af77aa30f
(8) Finished request
Waking up in 4.8 seconds.
(9) Received Access-Request Id 9 from 127.0.0.1:37016 to 127.0.0.1:1812 length 140
(9) User-Name = "testing"
(9) NAS-IP-Address = 127.0.0.1
(9) Calling-Station-Id = "02-00-00-00-00-01"
(9) Framed-MTU = 1400
(9) NAS-Port-Type = Wireless-802.11
(9) Service-Type = Framed-User
(9) Connect-Info = "CONNECT 11Mbps 802.11b"
(9) EAP-Message = 0x02ad00060d00
(9) State = 0xfb1c2c65fab1217da229744af77aa30f
(9) Message-Authenticator = 0xa01251081874341f20265ae787acbd1e
(9) session-state: No cached attributes
(9) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(9) authorize {
(9) policy filter_username {
(9) if (&User-Name) {
(9) if (&User-Name) -> TRUE
(9) if (&User-Name) {
(9) if (&User-Name =~ / /) {
(9) if (&User-Name =~ / /) -> FALSE
(9) if (&User-Name =~ /@[^@]*@/ ) {
(9) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(9) if (&User-Name =~ /\.\./ ) {
(9) if (&User-Name =~ /\.\./ ) -> FALSE
(9) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(9) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(9) if (&User-Name =~ /\.$/) {
(9) if (&User-Name =~ /\.$/) -> FALSE
(9) if (&User-Name =~ /@\./) {
(9) if (&User-Name =~ /@\./) -> FALSE
(9) } # if (&User-Name) = notfound
(9) } # policy filter_username = notfound
(9) [preprocess] = ok
(9) [chap] = noop
(9) [mschap] = noop
(9) [digest] = noop
(9) suffix: Checking for suffix after "@"
(9) suffix: No '@' in User-Name = "testing", looking up realm NULL
(9) suffix: No such realm "NULL"
(9) [suffix] = noop
(9) eap: Peer sent EAP Response (code 2) ID 173 length 6
(9) eap: No EAP Start, assuming it's an on-going EAP conversation
(9) [eap] = updated
(9) files: users: Matched entry testing at line 87
(9) [files] = ok
(9) [expiration] = noop
(9) [logintime] = noop
(9) pap: WARNING: Auth-Type already set. Not setting to PAP
(9) [pap] = noop
(9) } # authorize = updated
(9) Found Auth-Type = eap
(9) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(9) authenticate {
(9) eap: Expiring EAP session with state 0xfb1c2c65fab1217d
(9) eap: Finished EAP session with state 0xfb1c2c65fab1217d
(9) eap: Previous EAP request found for state 0xfb1c2c65fab1217d, released from the list
(9) eap: Peer sent packet with method EAP TLS (13)
(9) eap: Calling submodule eap_tls to process data
(9) eap_tls: Continuing EAP-TLS
(9) eap_tls: Peer ACKed our handshake fragment
(9) eap_tls: [eaptls verify] = request
(9) eap_tls: [eaptls process] = handled
(9) eap: Sending EAP Request (code 1) ID 174 length 1004
(9) eap: EAP session adding &reply:State = 0xfb1c2c65f9b2217d
(9) [eap] = handled
(9) } # authenticate = handled
(9) Using Post-Auth-Type Challenge
(9) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(9) Challenge { ... } # empty sub-section is ignored
(9) Sent Access-Challenge Id 9 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(9) EAP-Message = 0x01ae03ec0dc000000b5cd38235a4811c3f2e4cc129e388ad6f6c6237386b5f4d7ecc8d193c2465dfe051194474b53e1ac364e4b8fdcb527d6de8ca809cbfd5eb53a47785e62eaa3f7bafbeff699f9e631a78efbd38d6270004fe308204fa308203e2a00302010202144a1dec91e0857d76d65f37d6ddaab4191176ebcb300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d657768657265
(9) Message-Authenticator = 0x00000000000000000000000000000000
(9) State = 0xfb1c2c65f9b2217da229744af77aa30f
(9) Finished request
Waking up in 4.8 seconds.
(10) Received Access-Request Id 10 from 127.0.0.1:37016 to 127.0.0.1:1812 length 140
(10) User-Name = "testing"
(10) NAS-IP-Address = 127.0.0.1
(10) Calling-Station-Id = "02-00-00-00-00-01"
(10) Framed-MTU = 1400
(10) NAS-Port-Type = Wireless-802.11
(10) Service-Type = Framed-User
(10) Connect-Info = "CONNECT 11Mbps 802.11b"
(10) EAP-Message = 0x02ae00060d00
(10) State = 0xfb1c2c65f9b2217da229744af77aa30f
(10) Message-Authenticator = 0x1c2532f478e413662af2678f7059a2fd
(10) session-state: No cached attributes
(10) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(10) authorize {
(10) policy filter_username {
(10) if (&User-Name) {
(10) if (&User-Name) -> TRUE
(10) if (&User-Name) {
(10) if (&User-Name =~ / /) {
(10) if (&User-Name =~ / /) -> FALSE
(10) if (&User-Name =~ /@[^@]*@/ ) {
(10) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(10) if (&User-Name =~ /\.\./ ) {
(10) if (&User-Name =~ /\.\./ ) -> FALSE
(10) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(10) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(10) if (&User-Name =~ /\.$/) {
(10) if (&User-Name =~ /\.$/) -> FALSE
(10) if (&User-Name =~ /@\./) {
(10) if (&User-Name =~ /@\./) -> FALSE
(10) } # if (&User-Name) = notfound
(10) } # policy filter_username = notfound
(10) [preprocess] = ok
(10) [chap] = noop
(10) [mschap] = noop
(10) [digest] = noop
(10) suffix: Checking for suffix after "@"
(10) suffix: No '@' in User-Name = "testing", looking up realm NULL
(10) suffix: No such realm "NULL"
(10) [suffix] = noop
(10) eap: Peer sent EAP Response (code 2) ID 174 length 6
(10) eap: No EAP Start, assuming it's an on-going EAP conversation
(10) [eap] = updated
(10) files: users: Matched entry testing at line 87
(10) [files] = ok
(10) [expiration] = noop
(10) [logintime] = noop
(10) pap: WARNING: Auth-Type already set. Not setting to PAP
(10) [pap] = noop
(10) } # authorize = updated
(10) Found Auth-Type = eap
(10) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(10) authenticate {
(10) eap: Expiring EAP session with state 0xfb1c2c65f9b2217d
(10) eap: Finished EAP session with state 0xfb1c2c65f9b2217d
(10) eap: Previous EAP request found for state 0xfb1c2c65f9b2217d, released from the list
(10) eap: Peer sent packet with method EAP TLS (13)
(10) eap: Calling submodule eap_tls to process data
(10) eap_tls: Continuing EAP-TLS
(10) eap_tls: Peer ACKed our handshake fragment
(10) eap_tls: [eaptls verify] = request
(10) eap_tls: [eaptls process] = handled
(10) eap: Sending EAP Request (code 1) ID 175 length 930
(10) eap: EAP session adding &reply:State = 0xfb1c2c65f8b3217d
(10) [eap] = handled
(10) } # authenticate = handled
(10) Using Post-Auth-Type Challenge
(10) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(10) Challenge { ... } # empty sub-section is ignored
(10) Sent Access-Challenge Id 10 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(10) EAP-Message = 0x01af03a20d8000000b5c857d76d65f37d6ddaab4191176ebcb300f0603551d130101ff040530030101ff30360603551d1f042f302d302ba029a0278625687474703a2f2f7777772e6578616d706c652e6f72672f6578616d706c655f63612e63726c300d06092a864886f70d01010b050003820101005a51d379e5b56b816e7a7bd9ea454a1a686230c60c53f17ca70b7f716c0c0da2ebafbaacf1615dac121f23e4b9f83b66700c2dbf935a16e9ad936fb6c608f9f12cbd45027e0889e6b59c78cc47f407ea36e32bdd38ae9a5bf3909bf68c0328e3bef677fec2d98731b1bd09456832b211c86574121e3f2e8de75602b0f5eb974f3a4de26a81549722779451a947d69b5dc9f7b388e21974d5ed3518b704d951a1eda7301d009493e3fc407ebbae924df016903a69adc37909ecdf3722eb1b964633fccd6eefd8f94ccce6108ce3e84b1d4d6e8a257b20e0babdc53cd8b240e9ca8440bd977a4db811814164a7890abb48d0642a83d23a901c605465ffeeeac24116
(10) Message-Authenticator = 0x00000000000000000000000000000000
(10) State = 0xfb1c2c65f8b3217da229744af77aa30f
(10) Finished request
Waking up in 4.8 seconds.
(11) Received Access-Request Id 11 from 127.0.0.1:37016 to 127.0.0.1:1812 length 1552
(11) User-Name = "testing"
(11) NAS-IP-Address = 127.0.0.1
(11) Calling-Station-Id = "02-00-00-00-00-01"
(11) Framed-MTU = 1400
(11) NAS-Port-Type = Wireless-802.11
(11) Service-Type = Framed-User
(11) Connect-Info = "CONNECT 11Mbps 802.11b"
(11) EAP-Message = 0x02af05800dc000000a6e16030308de0b0008da0008d70003d3308203cf308202b7a003020102020102300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a3071310b3009060355040613024652310f300d06035504080c0652616469757331153013060355040a0c0c4578616d706c6520496e632e3119301706035504030c1075736572406578616d706c652e6f7267311f301d06092a864886f70d010901161075736572406578616d706c652e6f726730820122300d06092a864886f70d0101010500038201
(11) State = 0xfb1c2c65f8b3217da229744af77aa30f
(11) Message-Authenticator = 0x1fd16a3aa49b0dc01535f283156a1807
(11) session-state: No cached attributes
(11) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(11) authorize {
(11) policy filter_username {
(11) if (&User-Name) {
(11) if (&User-Name) -> TRUE
(11) if (&User-Name) {
(11) if (&User-Name =~ / /) {
(11) if (&User-Name =~ / /) -> FALSE
(11) if (&User-Name =~ /@[^@]*@/ ) {
(11) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(11) if (&User-Name =~ /\.\./ ) {
(11) if (&User-Name =~ /\.\./ ) -> FALSE
(11) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(11) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(11) if (&User-Name =~ /\.$/) {
(11) if (&User-Name =~ /\.$/) -> FALSE
(11) if (&User-Name =~ /@\./) {
(11) if (&User-Name =~ /@\./) -> FALSE
(11) } # if (&User-Name) = notfound
(11) } # policy filter_username = notfound
(11) [preprocess] = ok
(11) [chap] = noop
(11) [mschap] = noop
(11) [digest] = noop
(11) suffix: Checking for suffix after "@"
(11) suffix: No '@' in User-Name = "testing", looking up realm NULL
(11) suffix: No such realm "NULL"
(11) [suffix] = noop
(11) eap: Peer sent EAP Response (code 2) ID 175 length 1408
(11) eap: No EAP Start, assuming it's an on-going EAP conversation
(11) [eap] = updated
(11) files: users: Matched entry testing at line 87
(11) [files] = ok
(11) [expiration] = noop
(11) [logintime] = noop
(11) pap: WARNING: Auth-Type already set. Not setting to PAP
(11) [pap] = noop
(11) } # authorize = updated
(11) Found Auth-Type = eap
(11) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(11) authenticate {
(11) eap: Expiring EAP session with state 0xfb1c2c65f8b3217d
(11) eap: Finished EAP session with state 0xfb1c2c65f8b3217d
(11) eap: Previous EAP request found for state 0xfb1c2c65f8b3217d, released from the list
(11) eap: Peer sent packet with method EAP TLS (13)
(11) eap: Calling submodule eap_tls to process data
(11) eap_tls: Continuing EAP-TLS
(11) eap_tls: Peer indicated complete TLS record size will be 2670 bytes
(11) eap_tls: Expecting 2 TLS record fragments
(11) eap_tls: Got first TLS record fragment (1398 bytes). Peer indicated more fragments to follow
(11) eap_tls: [eaptls verify] = first fragment
(11) eap_tls: ACKing Peer's TLS record fragment
(11) eap_tls: [eaptls process] = handled
(11) eap: Sending EAP Request (code 1) ID 176 length 6
(11) eap: EAP session adding &reply:State = 0xfb1c2c65ffac217d
(11) [eap] = handled
(11) } # authenticate = handled
(11) Using Post-Auth-Type Challenge
(11) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(11) Challenge { ... } # empty sub-section is ignored
(11) Sent Access-Challenge Id 11 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(11) EAP-Message = 0x01b000060d00
(11) Message-Authenticator = 0x00000000000000000000000000000000
(11) State = 0xfb1c2c65ffac217da229744af77aa30f
(11) Finished request
Waking up in 4.8 seconds.
(12) Received Access-Request Id 12 from 127.0.0.1:37016 to 127.0.0.1:1812 length 1422
(12) User-Name = "testing"
(12) NAS-IP-Address = 127.0.0.1
(12) Calling-Station-Id = "02-00-00-00-00-01"
(12) Framed-MTU = 1400
(12) NAS-Port-Type = Wireless-802.11
(12) Service-Type = Framed-User
(12) Connect-Info = "CONNECT 11Mbps 802.11b"
(12) EAP-Message = 0x02b004fe0d000382010f003082010a0282010100d7ab97ba11f901e2bcbe703c7b5a468fea2a402bd27b361c815926d7d1f57fc33a400483d80c8a3fbceb16bca825981cda2ec7330b407800f17dcff77618b2f6a4a7a92216ef2ca4200e5be35a17a0f2a15bf8b43312c66290729aeab2c5ba237ec94e9a1f5257483eeede76626d677f0dd91ee89202fc8dae4e3c015fb98a4f0750aa0e7ed1bd5c3a6b8623638d876f4dab25690be87e096d7e887529072bd3eedea0bff065fd9b79914e0e7b740f236f20372b3b0ad1e9acec52b37541cea0af33729dae3e4a6322e86b44a159c6df35790b0b6a26fc9428a8f323e35198648b7b509350f3dd72929ab5f2970f5dd4ef271575f3665b69b5bd94768b84783f0203010001a38201423082013e301d0603551d0e0416041401571d779e50f5b591d6dad496f89ac3bc91cf273081d30603551d230481cb3081c8801401571d779e50f5b591d6dad496f89ac3bc91cf27a18199a48196308193310b3009060355040613
(12) State = 0xfb1c2c65ffac217da229744af77aa30f
(12) Message-Authenticator = 0x0d1f87fc26c15c46ab2a694795fef902
(12) session-state: No cached attributes
(12) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(12) authorize {
(12) policy filter_username {
(12) if (&User-Name) {
(12) if (&User-Name) -> TRUE
(12) if (&User-Name) {
(12) if (&User-Name =~ / /) {
(12) if (&User-Name =~ / /) -> FALSE
(12) if (&User-Name =~ /@[^@]*@/ ) {
(12) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(12) if (&User-Name =~ /\.\./ ) {
(12) if (&User-Name =~ /\.\./ ) -> FALSE
(12) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(12) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(12) if (&User-Name =~ /\.$/) {
(12) if (&User-Name =~ /\.$/) -> FALSE
(12) if (&User-Name =~ /@\./) {
(12) if (&User-Name =~ /@\./) -> FALSE
(12) } # if (&User-Name) = notfound
(12) } # policy filter_username = notfound
(12) [preprocess] = ok
(12) [chap] = noop
(12) [mschap] = noop
(12) [digest] = noop
(12) suffix: Checking for suffix after "@"
(12) suffix: No '@' in User-Name = "testing", looking up realm NULL
(12) suffix: No such realm "NULL"
(12) [suffix] = noop
(12) eap: Peer sent EAP Response (code 2) ID 176 length 1278
(12) eap: No EAP Start, assuming it's an on-going EAP conversation
(12) [eap] = updated
(12) files: users: Matched entry testing at line 87
(12) [files] = ok
(12) [expiration] = noop
(12) [logintime] = noop
(12) pap: WARNING: Auth-Type already set. Not setting to PAP
(12) [pap] = noop
(12) } # authorize = updated
(12) Found Auth-Type = eap
(12) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(12) authenticate {
(12) eap: Expiring EAP session with state 0xfb1c2c65ffac217d
(12) eap: Finished EAP session with state 0xfb1c2c65ffac217d
(12) eap: Previous EAP request found for state 0xfb1c2c65ffac217d, released from the list
(12) eap: Peer sent packet with method EAP TLS (13)
(12) eap: Calling submodule eap_tls to process data
(12) eap_tls: Continuing EAP-TLS
(12) eap_tls: Got final TLS record fragment (1272 bytes)
(12) eap_tls: [eaptls verify] = ok
(12) eap_tls: Done initial handshake
(12) eap_tls: TLS_accept: SSLv3/TLS write server done
(12) eap_tls: <<< recv TLS 1.2 [length 08de]
(12) eap_tls: TLS - Creating attributes from certificate OIDs
(12) eap_tls: TLS-Cert-Serial := "4a1dec91e0857d76d65f37d6ddaab4191176ebcb"
(12) eap_tls: TLS-Cert-Expiration := "240421025525Z"
(12) eap_tls: TLS-Cert-Subject := "/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authority"
(12) eap_tls: TLS-Cert-Issuer := "/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authority"
(12) eap_tls: TLS-Cert-Common-Name := "Example Certificate Authority"
(12) eap_tls: TLS - Creating attributes from certificate OIDs
(12) eap_tls: TLS-Client-Cert-Serial := "02"
(12) eap_tls: TLS-Client-Cert-Expiration := "240421025525Z"
(12) eap_tls: TLS-Client-Cert-Subject := "/C=FR/ST=Radius/O=Example Inc./CN=user@example.org/emailAddress=user@example.org"
(12) eap_tls: TLS-Client-Cert-Issuer := "/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authority"
(12) eap_tls: TLS-Client-Cert-Common-Name := "user@example.org"
(12) eap_tls: TLS-Client-Cert-X509v3-Extended-Key-Usage += "TLS Web Client Authentication"
(12) eap_tls: TLS-Client-Cert-X509v3-Extended-Key-Usage-OID += "1.3.6.1.5.5.7.3.2"
(12) eap_tls: TLS_accept: SSLv3/TLS read client certificate
(12) eap_tls: <<< recv TLS 1.2 [length 0046]
(12) eap_tls: TLS_accept: SSLv3/TLS read client key exchange
(12) eap_tls: <<< recv TLS 1.2 [length 0108]
(12) eap_tls: TLS_accept: SSLv3/TLS read certificate verify
(12) eap_tls: TLS_accept: SSLv3/TLS read change cipher spec
(12) eap_tls: <<< recv TLS 1.2 [length 0010]
(12) eap_tls: TLS_accept: SSLv3/TLS read finished
(12) eap_tls: >>> send TLS 1.2 [length 0001]
(12) eap_tls: TLS_accept: SSLv3/TLS write change cipher spec
(12) eap_tls: >>> send TLS 1.2 [length 0010]
(12) eap_tls: TLS_accept: SSLv3/TLS write finished
(12) eap_tls: (other): SSL negotiation finished successfully
(12) eap_tls: TLS - Connection Established
(12) eap_tls: TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(12) eap_tls: TLS-Session-Version = "TLS 1.2"
(12) eap_tls: TLS - got 51 bytes of data
(12) eap_tls: [eaptls process] = handled
(12) eap: Sending EAP Request (code 1) ID 177 length 61
(12) eap: EAP session adding &reply:State = 0xfb1c2c65fead217d
(12) [eap] = handled
(12) } # authenticate = handled
(12) Using Post-Auth-Type Challenge
(12) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(12) Challenge { ... } # empty sub-section is ignored
(12) session-state: Saving cached attributes
(12) TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(12) TLS-Session-Version = "TLS 1.2"
(12) Sent Access-Challenge Id 12 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(12) EAP-Message = 0x01b1003d0d80000000331403030001011603030028e6d41ca2aa87391a58eb70f47b2cb52c809102c061d01056c64fafec1b7192f45a219dafde4a6548
(12) Message-Authenticator = 0x00000000000000000000000000000000
(12) State = 0xfb1c2c65fead217da229744af77aa30f
(12) Finished request
Waking up in 4.8 seconds.
(13) Received Access-Request Id 13 from 127.0.0.1:37016 to 127.0.0.1:1812 length 140
(13) User-Name = "testing"
(13) NAS-IP-Address = 127.0.0.1
(13) Calling-Station-Id = "02-00-00-00-00-01"
(13) Framed-MTU = 1400
(13) NAS-Port-Type = Wireless-802.11
(13) Service-Type = Framed-User
(13) Connect-Info = "CONNECT 11Mbps 802.11b"
(13) EAP-Message = 0x02b100060d00
(13) State = 0xfb1c2c65fead217da229744af77aa30f
(13) Message-Authenticator = 0x3ae623aad6afd92f4daf0f414aec7d4d
(13) Restoring &session-state
(13) &session-state:TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(13) &session-state:TLS-Session-Version = "TLS 1.2"
(13) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(13) authorize {
(13) policy filter_username {
(13) if (&User-Name) {
(13) if (&User-Name) -> TRUE
(13) if (&User-Name) {
(13) if (&User-Name =~ / /) {
(13) if (&User-Name =~ / /) -> FALSE
(13) if (&User-Name =~ /@[^@]*@/ ) {
(13) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(13) if (&User-Name =~ /\.\./ ) {
(13) if (&User-Name =~ /\.\./ ) -> FALSE
(13) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(13) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(13) if (&User-Name =~ /\.$/) {
(13) if (&User-Name =~ /\.$/) -> FALSE
(13) if (&User-Name =~ /@\./) {
(13) if (&User-Name =~ /@\./) -> FALSE
(13) } # if (&User-Name) = notfound
(13) } # policy filter_username = notfound
(13) [preprocess] = ok
(13) [chap] = noop
(13) [mschap] = noop
(13) [digest] = noop
(13) suffix: Checking for suffix after "@"
(13) suffix: No '@' in User-Name = "testing", looking up realm NULL
(13) suffix: No such realm "NULL"
(13) [suffix] = noop
(13) eap: Peer sent EAP Response (code 2) ID 177 length 6
(13) eap: No EAP Start, assuming it's an on-going EAP conversation
(13) [eap] = updated
(13) files: users: Matched entry testing at line 87
(13) [files] = ok
(13) [expiration] = noop
(13) [logintime] = noop
(13) pap: WARNING: Auth-Type already set. Not setting to PAP
(13) [pap] = noop
(13) } # authorize = updated
(13) Found Auth-Type = eap
(13) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(13) authenticate {
(13) eap: Expiring EAP session with state 0xfb1c2c65fead217d
(13) eap: Finished EAP session with state 0xfb1c2c65fead217d
(13) eap: Previous EAP request found for state 0xfb1c2c65fead217d, released from the list
(13) eap: Peer sent packet with method EAP TLS (13)
(13) eap: Calling submodule eap_tls to process data
(13) eap_tls: Continuing EAP-TLS
(13) eap_tls: Peer ACKed our handshake fragment. handshake is finished
(13) eap_tls: [eaptls verify] = success
(13) eap_tls: [eaptls process] = success
(13) eap: Sending EAP Success (code 3) ID 177 length 4
(13) eap: Freeing handler
(13) [eap] = ok
(13) } # authenticate = ok
(13) # Executing section post-auth from file /etc/freeradius/3.0/sites-enabled/default
(13) post-auth {
(13) if (session-state:User-Name && reply:User-Name && request:User-Name && (reply:User-Name == request:User-Name)) {
(13) if (session-state:User-Name && reply:User-Name && request:User-Name && (reply:User-Name == request:User-Name)) -> FALSE
(13) update {
(13) &reply::TLS-Session-Cipher-Suite += &session-state:TLS-Session-Cipher-Suite[*] -> 'ECDHE-RSA-AES256-GCM-SHA384'
(13) &reply::TLS-Session-Version += &session-state:TLS-Session-Version[*] -> 'TLS 1.2'
(13) } # update = noop
(13) [exec] = noop
(13) policy remove_reply_message_if_eap {
(13) if (&reply:EAP-Message && &reply:Reply-Message) {
(13) if (&reply:EAP-Message && &reply:Reply-Message) -> FALSE
(13) else {
(13) [noop] = noop
(13) } # else = noop
(13) } # policy remove_reply_message_if_eap = noop
(13) } # post-auth = noop
(13) Sent Access-Accept Id 13 from 127.0.0.1:1812 to 127.0.0.1:37016 length 0
(13) MS-MPPE-Recv-Key = 0xd7bcddf7af6224b50c992f45d54c1c132df258c925dfdddf8a027fc184b15204
(13) MS-MPPE-Send-Key = 0x4fd8b558db5e3260847feff053527cb4117d5a697c28f3aedd818614742ba5ee
(13) EAP-Message = 0x03b10004
(13) Message-Authenticator = 0x00000000000000000000000000000000
(13) User-Name = "testing"
(13) Finished request
Waking up in 4.8 seconds.
(0) Cleaning up request packet ID 0 with timestamp +17
(1) Cleaning up request packet ID 1 with timestamp +17
(2) Cleaning up request packet ID 2 with timestamp +17
(3) Cleaning up request packet ID 3 with timestamp +17
(4) Cleaning up request packet ID 4 with timestamp +17
(5) Cleaning up request packet ID 5 with timestamp +17
(6) Cleaning up request packet ID 6 with timestamp +17
(7) Cleaning up request packet ID 7 with timestamp +17
(8) Cleaning up request packet ID 8 with timestamp +17
(9) Cleaning up request packet ID 9 with timestamp +17
(10) Cleaning up request packet ID 10 with timestamp +17
(11) Cleaning up request packet ID 11 with timestamp +17
(12) Cleaning up request packet ID 12 with timestamp +17
(13) Cleaning up request packet ID 13 with timestamp +17
Ready to process requests
eapol_test端输出如下:
Reading configuration file 'eap-tls.conf'
Line: 1 - start of a new network block
eap methods - hexdump(len=16): 00 00 00 00 0d 00 00 00 00 00 00 00 00 00 00 00
eapol_flags=0 (0x0)
key_mgmt: 0x8
identity - hexdump_ascii(len=7):74 65 73 74 69 6e 67 testing
password - hexdump_ascii(len=8):70 61 73 73 77 6f 72 64 password
ca_cert - hexdump_ascii(len=32):2f 65 74 63 2f 66 72 65 65 72 61 64 69 75 73 2f /etc/freeradius/33 2e 30 2f 63 65 72 74 73 2f 63 61 2e 70 65 6d 3.0/certs/ca.pem
client_cert - hexdump_ascii(len=36):2f 65 74 63 2f 66 72 65 65 72 61 64 69 75 73 2f /etc/freeradius/33 2e 30 2f 63 65 72 74 73 2f 63 6c 69 65 6e 74 3.0/certs/client2e 70 65 6d .pem
private_key - hexdump_ascii(len=36):2f 65 74 63 2f 66 72 65 65 72 61 64 69 75 73 2f /etc/freeradius/33 2e 30 2f 63 65 72 74 73 2f 63 6c 69 65 6e 74 3.0/certs/client2e 6b 65 79 .key
private_key_passwd - hexdump_ascii(len=8):77 68 61 74 65 76 65 72 whatever
Priority group 0id=0 ssid=''
Authentication server 127.0.0.1:1812
RADIUS local address: 127.0.0.1:37016
ENGINE: Loading builtin engines
ENGINE: Loading builtin engines
EAPOL: SUPP_PAE entering state DISCONNECTED
EAPOL: KEY_RX entering state NO_KEY_RECEIVE
EAPOL: SUPP_BE entering state INITIALIZE
EAP: EAP entering state DISABLED
EAPOL: External notification - portValid=0
EAPOL: External notification - portEnabled=1
EAPOL: SUPP_PAE entering state CONNECTING
EAPOL: SUPP_BE entering state IDLE
EAP: EAP entering state INITIALIZE
EAP: EAP entering state IDLE
Sending fake EAP-Request-Identity
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_PAE entering state RESTART
EAP: EAP entering state INITIALIZE
EAP: EAP entering state IDLE
EAPOL: SUPP_PAE entering state AUTHENTICATING
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=179 method=1 vendor=0 vendorMethod=0
EAP: EAP entering state IDENTITY
CTRL-EVENT-EAP-STARTED EAP authentication started
EAP: Status notification: started (param=)
EAP: EAP-Request Identity data - hexdump_ascii(len=0):
EAP: using real identity - hexdump_ascii(len=7):74 65 73 74 69 6e 67 testing
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=12)
TX EAP -> RADIUS - hexdump(len=12): 02 b3 00 0c 01 74 65 73 74 69 6e 67
Encapsulating EAP message into a RADIUS packet
Learned identity from EAP-Response-Identity - hexdump(len=7): 74 65 73 74 69 6e 67
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=0 length=128Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=14Value: 02b3000c0174657374696e67Attribute 80 (Message-Authenticator) length=18Value: 8156437e4fb3d643ab0c0f9bbc2b5f07
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 64 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=0 length=64Attribute 79 (EAP-Message) length=8Value: 01b400060d20Attribute 80 (Message-Authenticator) length=18Value: 6abcc84aa4d8854b512e51a7052b9192Attribute 24 (State) length=18Value: 6c230b426c9706dd3f72ef77da978e44
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=180 len=6) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=180 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state GET_METHOD
CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=13
EAP: Status notification: accept proposed method (param=TLS)
EAP: Initialize selected EAP method: vendor 0 method 13 (TLS)
TLS: using phase1 config options
TLS: Trusted root certificate(s) loaded
OpenSSL: SSL_use_certificate_chain_file --> OK
OpenSSL: tls_use_private_key_file (PEM) --> loaded
SSL: Private key loaded successfully
CTRL-EVENT-EAP-METHOD EAP vendor 0 method 13 (TLS) selected
EAP: EAP entering state METHOD
SSL: Received packet(len=6) - Flags 0x20
EAP-TLS: Start
SSL: (where=0x10 ret=0x1)
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:before SSL initialization
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 01 00 b3
OpenSSL: TX ver=0x303 content_type=22 (handshake/client hello)
OpenSSL: Message - hexdump(len=179): 01 00 00 af 03 03 7e 68 ad 1c 85 d2 20 ab f7 73 85 46 c7 5a 38 5b f6 4d c6 b4 d4 b0 9f ca 12 e9 ba bd eb d5 98 cc 00 00 38 c0 2c c0 30 00 9f cc a9 cc a8 cc aa c0 2b c0 2f 00 9e c0 24 c0 28 00 6b c0 23 c0 27 00 67 c0 0a c0 14 00 39 c0 09 c0 13 00 33 00 9d 00 9c 00 3d 00 3c 00 35 00 2f 00 ff 01 00 00 4e 00 0b 00 04 03 00 01 02 00 0a 00 0c 00 0a 00 1d 00 17 00 1e 00 19 00 18 00 16 00 00 00 17 00 00 00 0d 00 2a 00 28 04 03 05 03 06 03 08 07 08 08 08 09 08 0a 08 0b 08 04 08 05 08 06 04 01 05 01 06 01 03 03 03 01 03 02 04 02 05 02 06 02
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write client hello
SSL: (where=0x1002 ret=0xffffffff)
SSL: SSL_connect:error in SSLv3/TLS write client hello
SSL: SSL_connect - want more data
SSL: 184 bytes pending from ssl_out
SSL: Using TLS version TLSv1.2
SSL: 184 bytes left to be sent out (of total 184 bytes)
EAP: method process -> ignore=FALSE methodState=MAY_CONT decision=FAIL eapRespData=0x55f53f3be820
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=190)
TX EAP -> RADIUS - hexdump(len=190): 02 b4 00 be 0d 00 16 03 01 00 b3 01 00 00 af 03 03 7e 68 ad 1c 85 d2 20 ab f7 73 85 46 c7 5a 38 5b f6 4d c6 b4 d4 b0 9f ca 12 e9 ba bd eb d5 98 cc 00 00 38 c0 2c c0 30 00 9f cc a9 cc a8 cc aa c0 2b c0 2f 00 9e c0 24 c0 28 00 6b c0 23 c0 27 00 67 c0 0a c0 14 00 39 c0 09 c0 13 00 33 00 9d 00 9c 00 3d 00 3c 00 35 00 2f 00 ff 01 00 00 4e 00 0b 00 04 03 00 01 02 00 0a 00 0c 00 0a 00 1d 00 17 00 1e 00 19 00 18 00 16 00 00 00 17 00 00 00 0d 00 2a 00 28 04 03 05 03 06 03 08 07 08 08 08 09 08 0a 08 0b 08 04 08 05 08 06 04 01 05 01 06 01 03 03 03 01 03 02 04 02 05 02 06 02
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=1 length=324Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=192Value: 02b400be0d0016030100b3010000af03037e68ad1c85d220abf7738546c75a385bf64dc6b4d4b09fca12e9babdebd598cc000038c02cc030009fcca9cca8ccaac02bc02f009ec024c028006bc023c0270067c00ac0140039c009c0130033009d009c003d003c0035002f00ff0100004e000b000403000102000a000c000a001d0017001e001900180016000000170000000d002a0028040305030603080708080809080a080b080408050806040105010601030303010302040205020602Attribute 24 (State) length=18Value: 6c230b426c9706dd3f72ef77da978e44Attribute 80 (Message-Authenticator) length=18Value: b00bca82686b95588c82b16531aaf1a2
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 1068 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=1 length=1068Attribute 79 (EAP-Message) length=255Value: 01b503ec0dc000000b5c160303003d02000039030311eac75f3f748e3dfcf6e1de94d5d4832800322221b5f49efcb8ce4a0ba8c0ad00c030000011ff01000100000b0004030001020017000016030308e90b0008e50008e20003de308203da308202c2a003020102020101300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c65204365Attribute 79 (EAP-Message) length=255Value: 72746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a307c310b3009060355040613024652310f300d06035504080c0652616469757331153013060355040a0c0c4578616d706c6520496e632e3123302106035504030c1a4578616d706c65205365727665722043657274696669636174653120301e06092a864886f70d010901161161646d696e406578616d706c652e6f726730820122300d06092a864886f70d01010105000382010f003082010a0282010100d1c0abffd46f4b5369d6d00416364ab0adef9cb6e6650d29521299d8ad893bf218f0934d0b97018b2dca90Attribute 79 (EAP-Message) length=255Value: 3b2bc3dc35144dbebe52e72021d263a2138231492ba3a6aadf640bcdabc40433c22d6d53ce4fb384c2576cc9326dae0befaaad84207485b03751401051d13e1e175a15926d4bd9ddabdc4bc327fd88eba4b01d6e4e61c54b3a36b8c3150d6b44699045e265040c85d67f181bd51e236f437e03b0755418b6d7c570f22c5216defb52dc25e1dbd6438f262dfa04f673f1fd325abad4e9d05cd1aa66258a27d5d174e6c2d4c3ecd756b1c9d2806c8fd7998d765e3bc8091101fba7ccadbb33f92560d6fba647c303d21366450adfd6c296d829c693870203010001a34f304d30130603551d25040c300a06082b0601050507030130360603551d1f042f30Attribute 79 (EAP-Message) length=247Value: 2d302ba029a0278625687474703a2f2f7777772e6578616d706c652e636f6d2f6578616d706c655f63612e63726c300d06092a864886f70d01010b05000382010100bd49899734116830715ab1b59f5748c02d47b925228a7c180cba3966d09c61d906ee2cc792065be7f44ea25da7837bd142d3b280178fbce6eda7abd9031f01f0cbbf17607d4543f9c649656f331584f56273933afd58fd4de6c40b9dff9dc2c4b7bcf09a713fcdf81a07ad00a73d099cbef6f1e81474d5fda07a975248861de4116171a7db5360e650bee856f75c838d51ae3bb1841f05e9f39166ff132a23e81cff02855b53cf09f7d54070be0c5107f64ab5Attribute 80 (Message-Authenticator) length=18Value: b50afbc7936f06e5f3cb15bcd2cbb0e3Attribute 24 (State) length=18Value: 6c230b426d9606dd3f72ef77da978e44
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=181 len=1004) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=181 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state METHOD
SSL: Received packet(len=1004) - Flags 0xc0
SSL: TLS Message Length: 2908
SSL: Need 1914 bytes more input data
SSL: Building ACK (type=13 id=181 ver=0)
EAP: method process -> ignore=FALSE methodState=MAY_CONT decision=FAIL eapRespData=0x55f53f3a75a0
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=6)
TX EAP -> RADIUS - hexdump(len=6): 02 b5 00 06 0d 00
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=2 length=140Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=8Value: 02b500060d00Attribute 24 (State) length=18Value: 6c230b426d9606dd3f72ef77da978e44Attribute 80 (Message-Authenticator) length=18Value: b59edee3915c6dc7cc64ec2d9d00e109
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 1068 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=2 length=1068Attribute 79 (EAP-Message) length=255Value: 01b603ec0dc000000b5cd38235a4811c3f2e4cc129e388ad6f6c6237386b5f4d7ecc8d193c2465dfe051194474b53e1ac364e4b8fdcb527d6de8ca809cbfd5eb53a47785e62eaa3f7bafbeff699f9e631a78efbd38d6270004fe308204fa308203e2a00302010202144a1dec91e0857d76d65f37d6ddaab4191176ebcb300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f7267312630Attribute 79 (EAP-Message) length=255Value: 2406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f7269747930820122300d06092a864886f70d01010105000382010f003082010a0282010100d7Attribute 79 (EAP-Message) length=255Value: ab97ba11f901e2bcbe703c7b5a468fea2a402bd27b361c815926d7d1f57fc33a400483d80c8a3fbceb16bca825981cda2ec7330b407800f17dcff77618b2f6a4a7a92216ef2ca4200e5be35a17a0f2a15bf8b43312c66290729aeab2c5ba237ec94e9a1f5257483eeede76626d677f0dd91ee89202fc8dae4e3c015fb98a4f0750aa0e7ed1bd5c3a6b8623638d876f4dab25690be87e096d7e887529072bd3eedea0bff065fd9b79914e0e7b740f236f20372b3b0ad1e9acec52b37541cea0af33729dae3e4a6322e86b44a159c6df35790b0b6a26fc9428a8f323e35198648b7b509350f3dd72929ab5f2970f5dd4ef271575f3665b69b5bd94768b84Attribute 79 (EAP-Message) length=247Value: 783f0203010001a38201423082013e301d0603551d0e0416041401571d779e50f5b591d6dad496f89ac3bc91cf273081d30603551d230481cb3081c8801401571d779e50f5b591d6dad496f89ac3bc91cf27a18199a48196308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f7269747982144a1dec91e0Attribute 80 (Message-Authenticator) length=18Value: 00b5705651e74dc6fe4c19414be35aaeAttribute 24 (State) length=18Value: 6c230b426e9506dd3f72ef77da978e44
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=182 len=1004) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=182 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state METHOD
SSL: Received packet(len=1004) - Flags 0xc0
SSL: TLS Message Length: 2908
SSL: Need 920 bytes more input data
SSL: Building ACK (type=13 id=182 ver=0)
EAP: method process -> ignore=FALSE methodState=MAY_CONT decision=FAIL eapRespData=0x55f53f3a75a0
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=6)
TX EAP -> RADIUS - hexdump(len=6): 02 b6 00 06 0d 00
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=3 length=140Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=8Value: 02b600060d00Attribute 24 (State) length=18Value: 6c230b426e9506dd3f72ef77da978e44Attribute 80 (Message-Authenticator) length=18Value: c5f5d8ac30024f696a340a2a89a1c0cb
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 994 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=3 length=994Attribute 79 (EAP-Message) length=255Value: 01b703a20d8000000b5c857d76d65f37d6ddaab4191176ebcb300f0603551d130101ff040530030101ff30360603551d1f042f302d302ba029a0278625687474703a2f2f7777772e6578616d706c652e6f72672f6578616d706c655f63612e63726c300d06092a864886f70d01010b050003820101005a51d379e5b56b816e7a7bd9ea454a1a686230c60c53f17ca70b7f716c0c0da2ebafbaacf1615dac121f23e4b9f83b66700c2dbf935a16e9ad936fb6c608f9f12cbd45027e0889e6b59c78cc47f407ea36e32bdd38ae9a5bf3909bf68c0328e3bef677fec2d98731b1bd09456832b211c86574121e3f2e8de75602b0f5eb974f3a4de26a815497Attribute 79 (EAP-Message) length=255Value: 22779451a947d69b5dc9f7b388e21974d5ed3518b704d951a1eda7301d009493e3fc407ebbae924df016903a69adc37909ecdf3722eb1b964633fccd6eefd8f94ccce6108ce3e84b1d4d6e8a257b20e0babdc53cd8b240e9ca8440bd977a4db811814164a7890abb48d0642a83d23a901c605465ffeeeac241160303014d0c00014903001741044fc4be1793f52fc8aea544cfb477c28321a079dbc530af7f2e222e7706970a47246fa3fc49e0652d9614ebb71aa124b8106be51efbf65cc796e2aed0d5af0df7080401002b89cd21ada9d57eb5781a33ee62fc149c35446bf856ea9f6f92ccdde900a2d022241cb63070794eb24ed6f755f39a35661bAttribute 79 (EAP-Message) length=255Value: 87c6c2d7d4cda5f65d246e389391c1d1d6e70b3d2d9762c4c091b89fbea7955d982d6bd11a8e5ca93b553e917571d89a3595efecc25d05c6c8e206400fbd92107c6776e43f59e730796eabebe5410cf28dd9783d523d956dc384a66fbd92260e3fe2229abd5bb78099be5f120f7daed16f205c74d88f45cb164666a792b37e17e8d1b1d90c5f71df167bee7588fbeae1c1dd60fd882c28c9dbef58bc9d23dc6d409c6c6067ca49a284b0abbb4c8b5f896059643e36965ebbc12b741581813b437434a5b73e56aafbc2d4bdc7dac616030300cc0d0000c8030102400028040305030603080708080809080a080b08040805080604010501060103030301Attribute 79 (EAP-Message) length=173Value: 030204020502060200980096308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f7269747916030300040e000000Attribute 80 (Message-Authenticator) length=18Value: 537cc966c9a9ead8369128815c3e6e1eAttribute 24 (State) length=18Value: 6c230b426f9406dd3f72ef77da978e44
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=183 len=930) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=183 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state METHOD
SSL: Received packet(len=930) - Flags 0x80
SSL: TLS Message Length: 2908
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 3d
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write client hello
OpenSSL: RX ver=0x303 content_type=22 (handshake/server hello)
OpenSSL: Message - hexdump(len=61): 02 00 00 39 03 03 11 ea c7 5f 3f 74 8e 3d fc f6 e1 de 94 d5 d4 83 28 00 32 22 21 b5 f4 9e fc b8 ce 4a 0b a8 c0 ad 00 c0 30 00 00 11 ff 01 00 01 00 00 0b 00 04 03 00 01 02 00 17 00 00
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 08 e9
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read server hello
OpenSSL: RX ver=0x303 content_type=22 (handshake/certificate)
OpenSSL: Message - hexdump(len=2281): 0b 00 08 e5 00 08 e2 00 03 de 30 82 03 da 30 82 02 c2 a0 03 02 01 02 02 01 01 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 7c 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 23 30 21 06 03 55 04 03 0c 1a 45 78 61 6d 70 6c 65 20 53 65 72 76 65 72 20 43 65 72 74 69 66 69 63 61 74 65 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 d1 c0 ab ff d4 6f 4b 53 69 d6 d0 04 16 36 4a b0 ad ef 9c b6 e6 65 0d 29 52 12 99 d8 ad 89 3b f2 18 f0 93 4d 0b 97 01 8b 2d ca 90 3b 2b c3 dc 35 14 4d be be 52 e7 20 21 d2 63 a2 13 82 31 49 2b a3 a6 aa df 64 0b cd ab c4 04 33 c2 2d 6d 53 ce 4f b3 84 c2 57 6c c9 32 6d ae 0b ef aa ad 84 20 74 85 b0 37 51 40 10 51 d1 3e 1e 17 5a 15 92 6d 4b d9 dd ab dc 4b c3 27 fd 88 eb a4 b0 1d 6e 4e 61 c5 4b 3a 36 b8 c3 15 0d 6b 44 69 90 45 e2 65 04 0c 85 d6 7f 18 1b d5 1e 23 6f 43 7e 03 b0 75 54 18 b6 d7 c5 70 f2 2c 52 16 de fb 52 dc 25 e1 db d6 43 8f 26 2d fa 04 f6 73 f1 fd 32 5a ba d4 e9 d0 5c d1 aa 66 25 8a 27 d5 d1 74 e6 c2 d4 c3 ec d7 56 b1 c9 d2 80 6c 8f d7 99 8d 76 5e 3b c8 09 11 01 fb a7 cc ad bb 33 f9 25 60 d6 fb a6 47 c3 03 d2 13 66 45 0a df d6 c2 96 d8 29 c6 93 87 02 03 01 00 01 a3 4f 30 4d 30 13 06 03 55 1d 25 04 0c 30 0a 06 08 2b 06 01 05 05 07 03 01 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 63 6f 6d 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 bd 49 89 97 34 11 68 30 71 5a b1 b5 9f 57 48 c0 2d 47 b9 25 22 8a 7c 18 0c ba 39 66 d0 9c 61 d9 06 ee 2c c7 92 06 5b e7 f4 4e a2 5d a7 83 7b d1 42 d3 b2 80 17 8f bc e6 ed a7 ab d9 03 1f 01 f0 cb bf 17 60 7d 45 43 f9 c6 49 65 6f 33 15 84 f5 62 73 93 3a fd 58 fd 4d e6 c4 0b 9d ff 9d c2 c4 b7 bc f0 9a 71 3f cd f8 1a 07 ad 00 a7 3d 09 9c be f6 f1 e8 14 74 d5 fd a0 7a 97 52 48 86 1d e4 11 61 71 a7 db 53 60 e6 50 be e8 56 f7 5c 83 8d 51 ae 3b b1 84 1f 05 e9 f3 91 66 ff 13 2a 23 e8 1c ff 02 85 5b 53 cf 09 f7 d5 40 70 be 0c 51 07 f6 4a b5 d3 82 35 a4 81 1c 3f 2e 4c c1 29 e3 88 ad 6f 6c 62 37 38 6b 5f 4d 7e cc 8d 19 3c 24 65 df e0 51 19 44 74 b5 3e 1a c3 64 e4 b8 fd cb 52 7d 6d e8 ca 80 9c bf d5 eb 53 a4 77 85 e6 2e aa 3f 7b af be ff 69 9f 9e 63 1a 78 ef bd 38 d6 27 00 04 fe 30 82 04 fa 30 82 03 e2 a0 03 02 01 02 02 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 d7 ab 97 ba 11 f9 01 e2 bc be 70 3c 7b 5a 46 8f ea 2a 40 2b d2 7b 36 1c 81 59 26 d7 d1 f5 7f c3 3a 40 04 83 d8 0c 8a 3f bc eb 16 bc a8 25 98 1c da 2e c7 33 0b 40 78 00 f1 7d cf f7 76 18 b2 f6 a4 a7 a9 22 16 ef 2c a4 20 0e 5b e3 5a 17 a0 f2 a1 5b f8 b4 33 12 c6 62 90 72 9a ea b2 c5 ba 23 7e c9 4e 9a 1f 52 57 48 3e ee de 76 62 6d 67 7f 0d d9 1e e8 92 02 fc 8d ae 4e 3c 01 5f b9 8a 4f 07 50 aa 0e 7e d1 bd 5c 3a 6b 86 23 63 8d 87 6f 4d ab 25 69 0b e8 7e 09 6d 7e 88 75 29 07 2b d3 ee de a0 bf f0 65 fd 9b 79 91 4e 0e 7b 74 0f 23 6f 20 37 2b 3b 0a d1 e9 ac ec 52 b3 75 41 ce a0 af 33 72 9d ae 3e 4a 63 22 e8 6b 44 a1 59 c6 df 35 79 0b 0b 6a 26 fc 94 28 a8 f3 23 e3 51 98 64 8b 7b 50 93 50 f3 dd 72 92 9a b5 f2 97 0f 5d d4 ef 27 15 75 f3 66 5b 69 b5 bd 94 76 8b 84 78 3f 02 03 01 00 01 a3 82 01 42 30 82 01 3e 30 1d 06 03 55 1d 0e 04 16 04 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 30 81 d3 06 03 55 1d 23 04 81 cb 30 81 c8 80 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 a1 81 99 a4 81 96 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 82 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0f 06 03 55 1d 13 01 01 ff 04 05 30 03 01 01 ff 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 6f 72 67 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 5a 51 d3 79 e5 b5 6b 81 6e 7a 7b d9 ea 45 4a 1a 68 62 30 c6 0c 53 f1 7c a7 0b 7f 71 6c 0c 0d a2 eb af ba ac f1 61 5d ac 12 1f 23 e4 b9 f8 3b 66 70 0c 2d bf 93 5a 16 e9 ad 93 6f b6 c6 08 f9 f1 2c bd 45 02 7e 08 89 e6 b5 9c 78 cc 47 f4 07 ea 36 e3 2b dd 38 ae 9a 5b f3 90 9b f6 8c 03 28 e3 be f6 77 fe c2 d9 87 31 b1 bd 09 45 68 32 b2 11 c8 65 74 12 1e 3f 2e 8d e7 56 02 b0 f5 eb 97 4f 3a 4d e2 6a 81 54 97 22 77 94 51 a9 47 d6 9b 5d c9 f7 b3 88 e2 19 74 d5 ed 35 18 b7 04 d9 51 a1 ed a7 30 1d 00 94 93 e3 fc 40 7e bb ae 92 4d f0 16 90 3a 69 ad c3 79 09 ec df 37 22 eb 1b 96 46 33 fc cd 6e ef d8 f9 4c cc e6 10 8c e3 e8 4b 1d 4d 6e 8a 25 7b 20 e0 ba bd c5 3c d8 b2 40 e9 ca 84 40 bd 97 7a 4d b8 11 81 41 64 a7 89 0a bb 48 d0 64 2a 83 d2 3a 90 1c 60 54 65 ff ee ea c2 41
OpenSSL: Peer certificate - depth 1
Certificate:Data:Version: 3 (0x2)Serial Number:4a:1d:ec:91:e0:85:7d:76:d6:5f:37:d6:dd:aa:b4:19:11:76:eb:cbSignature Algorithm: sha256WithRSAEncryptionIssuer: C=FR, ST=Radius, L=Somewhere, O=Example Inc./emailAddress=admin@example.org, CN=Example Certificate AuthorityValidityNot Before: Feb 21 02:55:25 2024 GMTNot After : Apr 21 02:55:25 2024 GMTSubject: C=FR, ST=Radius, L=Somewhere, O=Example Inc./emailAddress=admin@example.org, CN=Example Certificate AuthoritySubject Public Key Info:Public Key Algorithm: rsaEncryptionRSA Public-Key: (2048 bit)Modulus:00:d7:ab:97:ba:11:f9:01:e2:bc:be:70:3c:7b:5a:46:8f:ea:2a:40:2b:d2:7b:36:1c:81:59:26:d7:d1:f5:7f:c3:3a:40:04:83:d8:0c:8a:3f:bc:eb:16:bc:a8:25:98:1c:da:2e:c7:33:0b:40:78:00:f1:7d:cf:f7:76:18:b2:f6:a4:a7:a9:22:16:ef:2c:a4:20:0e:5b:e3:5a:17:a0:f2:a1:5b:f8:b4:33:12:c6:62:90:72:9a:ea:b2:c5:ba:23:7e:c9:4e:9a:1f:52:57:48:3e:ee:de:76:62:6d:67:7f:0d:d9:1e:e8:92:02:fc:8d:ae:4e:3c:01:5f:b9:8a:4f:07:50:aa:0e:7e:d1:bd:5c:3a:6b:86:23:63:8d:87:6f:4d:ab:25:69:0b:e8:7e:09:6d:7e:88:75:29:07:2b:d3:ee:de:a0:bf:f0:65:fd:9b:79:91:4e:0e:7b:74:0f:23:6f:20:37:2b:3b:0a:d1:e9:ac:ec:52:b3:75:41:ce:a0:af:33:72:9d:ae:3e:4a:63:22:e8:6b:44:a1:59:c6:df:35:79:0b:0b:6a:26:fc:94:28:a8:f3:23:e3:51:98:64:8b:7b:50:93:50:f3:dd:72:92:9a:b5:f2:97:0f:5d:d4:ef:27:15:75:f3:66:5b:69:b5:bd:94:76:8b:84:78:3fExponent: 65537 (0x10001)X509v3 extensions:X509v3 Subject Key Identifier: 01:57:1D:77:9E:50:F5:B5:91:D6:DA:D4:96:F8:9A:C3:BC:91:CF:27X509v3 Authority Key Identifier: keyid:01:57:1D:77:9E:50:F5:B5:91:D6:DA:D4:96:F8:9A:C3:BC:91:CF:27DirName:/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authorityserial:4A:1D:EC:91:E0:85:7D:76:D6:5F:37:D6:DD:AA:B4:19:11:76:EB:CBX509v3 Basic Constraints: criticalCA:TRUEX509v3 CRL Distribution Points: Full Name:URI:http://www.example.org/example_ca.crlSignature Algorithm: sha256WithRSAEncryption5a:51:d3:79:e5:b5:6b:81:6e:7a:7b:d9:ea:45:4a:1a:68:62:30:c6:0c:53:f1:7c:a7:0b:7f:71:6c:0c:0d:a2:eb:af:ba:ac:f1:61:5d:ac:12:1f:23:e4:b9:f8:3b:66:70:0c:2d:bf:93:5a:16:e9:ad:93:6f:b6:c6:08:f9:f1:2c:bd:45:02:7e:08:89:e6:b5:9c:78:cc:47:f4:07:ea:36:e3:2b:dd:38:ae:9a:5b:f3:90:9b:f6:8c:03:28:e3:be:f6:77:fe:c2:d9:87:31:b1:bd:09:45:68:32:b2:11:c8:65:74:12:1e:3f:2e:8d:e7:56:02:b0:f5:eb:97:4f:3a:4d:e2:6a:81:54:97:22:77:94:51:a9:47:d6:9b:5d:c9:f7:b3:88:e2:19:74:d5:ed:35:18:b7:04:d9:51:a1:ed:a7:30:1d:00:94:93:e3:fc:40:7e:bb:ae:92:4d:f0:16:90:3a:69:ad:c3:79:09:ec:df:37:22:eb:1b:96:46:33:fc:cd:6e:ef:d8:f9:4c:cc:e6:10:8c:e3:e8:4b:1d:4d:6e:8a:25:7b:20:e0:ba:bd:c5:3c:d8:b2:40:e9:ca:84:40:bd:97:7a:4d:b8:11:81:41:64:a7:89:0a:bb:48:d0:64:2a:83:d2:3a:90:1c:60:54:65:ff:ee:ea:c2:41CTRL-EVENT-EAP-PEER-CERT depth=1 subject='/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authority' hash=5a7df6ac8a17be4f95d70e75e60d255c20228efd5de61400b72207dfbc976477
TLS: tls_verify_cb - preverify_ok=1 err=0 (ok) ca_cert_verify=1 depth=1 buf='/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authority'
OpenSSL: Peer certificate - depth 0
Certificate:Data:Version: 3 (0x2)Serial Number: 1 (0x1)Signature Algorithm: sha256WithRSAEncryptionIssuer: C=FR, ST=Radius, L=Somewhere, O=Example Inc./emailAddress=admin@example.org, CN=Example Certificate AuthorityValidityNot Before: Feb 21 02:55:25 2024 GMTNot After : Apr 21 02:55:25 2024 GMTSubject: C=FR, ST=Radius, O=Example Inc., CN=Example Server Certificate/emailAddress=admin@example.orgSubject Public Key Info:Public Key Algorithm: rsaEncryptionRSA Public-Key: (2048 bit)Modulus:00:d1:c0:ab:ff:d4:6f:4b:53:69:d6:d0:04:16:36:4a:b0:ad:ef:9c:b6:e6:65:0d:29:52:12:99:d8:ad:89:3b:f2:18:f0:93:4d:0b:97:01:8b:2d:ca:90:3b:2b:c3:dc:35:14:4d:be:be:52:e7:20:21:d2:63:a2:13:82:31:49:2b:a3:a6:aa:df:64:0b:cd:ab:c4:04:33:c2:2d:6d:53:ce:4f:b3:84:c2:57:6c:c9:32:6d:ae:0b:ef:aa:ad:84:20:74:85:b0:37:51:40:10:51:d1:3e:1e:17:5a:15:92:6d:4b:d9:dd:ab:dc:4b:c3:27:fd:88:eb:a4:b0:1d:6e:4e:61:c5:4b:3a:36:b8:c3:15:0d:6b:44:69:90:45:e2:65:04:0c:85:d6:7f:18:1b:d5:1e:23:6f:43:7e:03:b0:75:54:18:b6:d7:c5:70:f2:2c:52:16:de:fb:52:dc:25:e1:db:d6:43:8f:26:2d:fa:04:f6:73:f1:fd:32:5a:ba:d4:e9:d0:5c:d1:aa:66:25:8a:27:d5:d1:74:e6:c2:d4:c3:ec:d7:56:b1:c9:d2:80:6c:8f:d7:99:8d:76:5e:3b:c8:09:11:01:fb:a7:cc:ad:bb:33:f9:25:60:d6:fb:a6:47:c3:03:d2:13:66:45:0a:df:d6:c2:96:d8:29:c6:93:87Exponent: 65537 (0x10001)X509v3 extensions:X509v3 Extended Key Usage: TLS Web Server AuthenticationX509v3 CRL Distribution Points: Full Name:URI:http://www.example.com/example_ca.crlSignature Algorithm: sha256WithRSAEncryptionbd:49:89:97:34:11:68:30:71:5a:b1:b5:9f:57:48:c0:2d:47:b9:25:22:8a:7c:18:0c:ba:39:66:d0:9c:61:d9:06:ee:2c:c7:92:06:5b:e7:f4:4e:a2:5d:a7:83:7b:d1:42:d3:b2:80:17:8f:bc:e6:ed:a7:ab:d9:03:1f:01:f0:cb:bf:17:60:7d:45:43:f9:c6:49:65:6f:33:15:84:f5:62:73:93:3a:fd:58:fd:4d:e6:c4:0b:9d:ff:9d:c2:c4:b7:bc:f0:9a:71:3f:cd:f8:1a:07:ad:00:a7:3d:09:9c:be:f6:f1:e8:14:74:d5:fd:a0:7a:97:52:48:86:1d:e4:11:61:71:a7:db:53:60:e6:50:be:e8:56:f7:5c:83:8d:51:ae:3b:b1:84:1f:05:e9:f3:91:66:ff:13:2a:23:e8:1c:ff:02:85:5b:53:cf:09:f7:d5:40:70:be:0c:51:07:f6:4a:b5:d3:82:35:a4:81:1c:3f:2e:4c:c1:29:e3:88:ad:6f:6c:62:37:38:6b:5f:4d:7e:cc:8d:19:3c:24:65:df:e0:51:19:44:74:b5:3e:1a:c3:64:e4:b8:fd:cb:52:7d:6d:e8:ca:80:9c:bf:d5:eb:53:a4:77:85:e6:2e:aa:3f:7b:af:be:ff:69:9f:9e:63:1a:78:ef:bd:38:d6:27CTRL-EVENT-EAP-PEER-CERT depth=0 subject='/C=FR/ST=Radius/O=Example Inc./CN=Example Server Certificate/emailAddress=admin@example.org' hash=442c76845b6912ab534b2e2ea69570c8c86cd0e6098e66239bfd6bcc0a40d9fc
TLS: tls_verify_cb - preverify_ok=1 err=0 (ok) ca_cert_verify=1 depth=0 buf='/C=FR/ST=Radius/O=Example Inc./CN=Example Server Certificate/emailAddress=admin@example.org'
EAP: Status notification: remote certificate verification (param=success)
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 01 4d
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read server certificate
OpenSSL: RX ver=0x303 content_type=22 (handshake/server key exchange)
OpenSSL: Message - hexdump(len=333): 0c 00 01 49 03 00 17 41 04 4f c4 be 17 93 f5 2f c8 ae a5 44 cf b4 77 c2 83 21 a0 79 db c5 30 af 7f 2e 22 2e 77 06 97 0a 47 24 6f a3 fc 49 e0 65 2d 96 14 eb b7 1a a1 24 b8 10 6b e5 1e fb f6 5c c7 96 e2 ae d0 d5 af 0d f7 08 04 01 00 2b 89 cd 21 ad a9 d5 7e b5 78 1a 33 ee 62 fc 14 9c 35 44 6b f8 56 ea 9f 6f 92 cc dd e9 00 a2 d0 22 24 1c b6 30 70 79 4e b2 4e d6 f7 55 f3 9a 35 66 1b 87 c6 c2 d7 d4 cd a5 f6 5d 24 6e 38 93 91 c1 d1 d6 e7 0b 3d 2d 97 62 c4 c0 91 b8 9f be a7 95 5d 98 2d 6b d1 1a 8e 5c a9 3b 55 3e 91 75 71 d8 9a 35 95 ef ec c2 5d 05 c6 c8 e2 06 40 0f bd 92 10 7c 67 76 e4 3f 59 e7 30 79 6e ab eb e5 41 0c f2 8d d9 78 3d 52 3d 95 6d c3 84 a6 6f bd 92 26 0e 3f e2 22 9a bd 5b b7 80 99 be 5f 12 0f 7d ae d1 6f 20 5c 74 d8 8f 45 cb 16 46 66 a7 92 b3 7e 17 e8 d1 b1 d9 0c 5f 71 df 16 7b ee 75 88 fb ea e1 c1 dd 60 fd 88 2c 28 c9 db ef 58 bc 9d 23 dc 6d 40 9c 6c 60 67 ca 49 a2 84 b0 ab bb 4c 8b 5f 89 60 59 64 3e 36 96 5e bb c1 2b 74 15 81 81 3b 43 74 34 a5 b7 3e 56 aa fb c2 d4 bd c7 da c6
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 cc
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read server key exchange
OpenSSL: RX ver=0x303 content_type=22 (handshake/certificate request)
OpenSSL: Message - hexdump(len=204): 0d 00 00 c8 03 01 02 40 00 28 04 03 05 03 06 03 08 07 08 08 08 09 08 0a 08 0b 08 04 08 05 08 06 04 01 05 01 06 01 03 03 03 01 03 02 04 02 05 02 06 02 00 98 00 96 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 04
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read server certificate request
OpenSSL: RX ver=0x303 content_type=22 (handshake/server hello done)
OpenSSL: Message - hexdump(len=4): 0e 00 00 00
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read server done
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 08 de
OpenSSL: TX ver=0x303 content_type=22 (handshake/certificate)
OpenSSL: Message - hexdump(len=2270): 0b 00 08 da 00 08 d7 00 03 d3 30 82 03 cf 30 82 02 b7 a0 03 02 01 02 02 01 02 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 71 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 19 30 17 06 03 55 04 03 0c 10 75 73 65 72 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 1f 30 1d 06 09 2a 86 48 86 f7 0d 01 09 01 16 10 75 73 65 72 40 65 78 61 6d 70 6c 65 2e 6f 72 67 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 ac 64 f9 52 38 ec f6 6d 2e 16 5e 9e 5b 33 10 ca 9d b0 b8 2d c7 98 21 6e 76 49 c9 e7 73 48 82 90 a6 fd 40 85 2f 7a 6f a8 50 7f a8 8a 81 33 e1 b6 51 75 40 17 ea 49 bb 27 d3 f7 55 ee c4 47 0b 82 4e 29 3e 7d e0 b0 6e 6c aa 88 55 99 3e 21 a1 5e 22 35 22 01 71 2d 04 87 82 25 39 0a 26 d5 44 b2 8f eb 4d e3 29 46 a7 83 de e5 01 d5 81 e4 2c ed bf fe 7f 57 70 df 52 f0 64 77 e9 8f ff 30 43 19 8e 08 28 76 99 99 89 6f 8e a1 d4 e6 5e 34 6f 04 67 30 b9 b3 a1 94 53 3c 9f c6 e7 71 3e ad 2a 11 ff 38 33 24 35 3f 76 ee 91 cf da 03 51 56 3d 4a 12 7d 05 0c 73 8b 88 f4 d0 38 27 b3 e8 09 3c 8d ff 67 cc 2d 1f ce 02 c1 d8 34 62 2b 42 5a 33 19 ae cd 30 4a 89 54 74 6b b2 28 59 f7 65 7c 72 29 04 3d e1 fc 31 c8 c9 ad 8a 1c 10 17 4a 71 88 99 aa 44 28 f7 3d 18 d3 8f 9f 17 3e ca 71 56 bd 67 02 03 01 00 01 a3 4f 30 4d 30 13 06 03 55 1d 25 04 0c 30 0a 06 08 2b 06 01 05 05 07 03 02 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 63 6f 6d 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 7f 6a 16 6b 0b 48 1b c5 b6 2f 4f e2 49 42 fe 84 16 f4 46 c3 f5 dd ea 61 2b e4 e9 91 ed 8f 00 c3 15 bc 58 ba c2 9a da 2b d6 c9 2f c1 a9 10 b3 fb 15 10 0c 2b 8f 3f 82 67 73 05 f2 69 45 46 26 8c a9 76 6c 07 67 af 42 a1 7d a8 5b 4a 1c c5 59 33 8e 7d c8 d4 e5 4b 93 7a 31 cf aa be 2e 9c 65 29 73 c7 02 3b b7 c1 49 a2 f5 54 ca 73 de b0 12 b4 55 03 44 34 aa cb 81 0e 11 4f a0 13 a7 d8 63 f3 3d 70 86 48 e7 88 ee 56 5c eb 83 04 c4 77 a7 e7 8d da 95 a6 1c b4 86 0c 48 51 b1 8a c6 b8 52 44 b8 3b 55 59 78 60 e9 94 42 c7 a1 28 4b 1d c7 95 fc 0e 5a 3f 63 56 2b 4c 9a 0e c6 2d 41 61 ad 1c e5 86 3b f3 71 14 1f e9 03 82 c6 41 3d 9d f7 88 77 d0 55 a0 dc cc d9 c3 1f 68 40 5f 07 a4 18 8d cf cc dd 11 13 bd 59 79 c7 f7 2c f1 2e 97 f7 63 47 28 92 c1 91 04 91 6e db e9 44 2f d8 c5 4a be 00 04 fe 30 82 04 fa 30 82 03 e2 a0 03 02 01 02 02 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 d7 ab 97 ba 11 f9 01 e2 bc be 70 3c 7b 5a 46 8f ea 2a 40 2b d2 7b 36 1c 81 59 26 d7 d1 f5 7f c3 3a 40 04 83 d8 0c 8a 3f bc eb 16 bc a8 25 98 1c da 2e c7 33 0b 40 78 00 f1 7d cf f7 76 18 b2 f6 a4 a7 a9 22 16 ef 2c a4 20 0e 5b e3 5a 17 a0 f2 a1 5b f8 b4 33 12 c6 62 90 72 9a ea b2 c5 ba 23 7e c9 4e 9a 1f 52 57 48 3e ee de 76 62 6d 67 7f 0d d9 1e e8 92 02 fc 8d ae 4e 3c 01 5f b9 8a 4f 07 50 aa 0e 7e d1 bd 5c 3a 6b 86 23 63 8d 87 6f 4d ab 25 69 0b e8 7e 09 6d 7e 88 75 29 07 2b d3 ee de a0 bf f0 65 fd 9b 79 91 4e 0e 7b 74 0f 23 6f 20 37 2b 3b 0a d1 e9 ac ec 52 b3 75 41 ce a0 af 33 72 9d ae 3e 4a 63 22 e8 6b 44 a1 59 c6 df 35 79 0b 0b 6a 26 fc 94 28 a8 f3 23 e3 51 98 64 8b 7b 50 93 50 f3 dd 72 92 9a b5 f2 97 0f 5d d4 ef 27 15 75 f3 66 5b 69 b5 bd 94 76 8b 84 78 3f 02 03 01 00 01 a3 82 01 42 30 82 01 3e 30 1d 06 03 55 1d 0e 04 16 04 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 30 81 d3 06 03 55 1d 23 04 81 cb 30 81 c8 80 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 a1 81 99 a4 81 96 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 82 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0f 06 03 55 1d 13 01 01 ff 04 05 30 03 01 01 ff 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 6f 72 67 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 5a 51 d3 79 e5 b5 6b 81 6e 7a 7b d9 ea 45 4a 1a 68 62 30 c6 0c 53 f1 7c a7 0b 7f 71 6c 0c 0d a2 eb af ba ac f1 61 5d ac 12 1f 23 e4 b9 f8 3b 66 70 0c 2d bf 93 5a 16 e9 ad 93 6f b6 c6 08 f9 f1 2c bd 45 02 7e 08 89 e6 b5 9c 78 cc 47 f4 07 ea 36 e3 2b dd 38 ae 9a 5b f3 90 9b f6 8c 03 28 e3 be f6 77 fe c2 d9 87 31 b1 bd 09 45 68 32 b2 11 c8 65 74 12 1e 3f 2e 8d e7 56 02 b0 f5 eb 97 4f 3a 4d e2 6a 81 54 97 22 77 94 51 a9 47 d6 9b 5d c9 f7 b3 88 e2 19 74 d5 ed 35 18 b7 04 d9 51 a1 ed a7 30 1d 00 94 93 e3 fc 40 7e bb ae 92 4d f0 16 90 3a 69 ad c3 79 09 ec df 37 22 eb 1b 96 46 33 fc cd 6e ef d8 f9 4c cc e6 10 8c e3 e8 4b 1d 4d 6e 8a 25 7b 20 e0 ba bd c5 3c d8 b2 40 e9 ca 84 40 bd 97 7a 4d b8 11 81 41 64 a7 89 0a bb 48 d0 64 2a 83 d2 3a 90 1c 60 54 65 ff ee ea c2 41
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write client certificate
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 46
OpenSSL: TX ver=0x303 content_type=22 (handshake/client key exchange)
OpenSSL: Message - hexdump(len=70): 10 00 00 42 41 04 00 76 b7 24 8a c2 72 34 69 ff dd 85 1e a2 3e f6 df a9 5e ba 2a 57 7c 49 a0 bc 8d 52 12 42 b4 9f f7 ce c9 98 e5 e1 24 2a f9 bb a5 8b d0 e3 8f e7 4c fb a6 77 4b f9 48 c9 ce 65 26 6c 28 64 82 9b
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write client key exchange
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 01 08
OpenSSL: TX ver=0x303 content_type=22 (handshake/certificate verify)
OpenSSL: Message - hexdump(len=264): 0f 00 01 04 08 04 01 00 35 c6 e4 96 6e 51 08 e5 20 1f e6 2c 5b d2 f6 25 d1 18 97 ff 20 17 ab bc 55 8a fb 63 d7 8c 96 08 26 cd 4d ae a2 b0 a0 73 5e 1d d6 f8 3c 9e f0 71 2e c9 ed 68 de 45 58 cd 2b 6e 4e 72 43 79 b9 23 e5 ca 86 4e 56 33 a6 c1 ec 9e b6 50 c2 a7 ed 81 26 3d b9 59 1b 8a 08 f2 3d 30 94 e1 0b 3a 0d 29 95 de d5 45 33 f1 1f 6d 4d 68 65 b4 94 97 a9 07 4f 5a 18 a2 f1 8d 43 16 34 76 21 fe 53 7b df 41 64 fc 51 19 0d 43 5c 7f 15 46 7c 74 1e bf a4 6c 85 5d ef a7 4d 07 c5 19 7d c2 ad 9b 82 91 ad 2c f6 af 83 19 8e bb 7f 27 35 7f 9d f5 e0 de 36 d1 b5 de 02 b2 1e b7 c5 1e 1b 50 db 9d 3f ea ec 39 4e e1 8f ff f7 fc 44 ac fc 16 12 8c 34 11 b2 f6 bb 31 15 63 6e 6f fc a7 24 7c 8c ce 11 5e dc 36 3d a4 3d 77 cd 3a d0 1e b0 87 e7 65 90 4a 87 6b c8 9d 3a c9 ba ad 34 05 fd d6 71 8f ac 3b f2 c8
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write certificate verify
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 14 03 03 00 01
OpenSSL: TX ver=0x303 content_type=20 (change cipher spec/)
OpenSSL: Message - hexdump(len=1): 01
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write change cipher spec
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 28
OpenSSL: TX ver=0x303 content_type=22 (handshake/finished)
OpenSSL: Message - hexdump(len=16): 14 00 00 0c df 27 77 5d d2 f1 cb 0f 5a 0b ef f0
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write finished
SSL: (where=0x1002 ret=0xffffffff)
SSL: SSL_connect:error in SSLv3/TLS write finished
SSL: SSL_connect - want more data
SSL: 2670 bytes pending from ssl_out
SSL: Using TLS version TLSv1.2
SSL: 2670 bytes left to be sent out (of total 2670 bytes)
SSL: sending 1398 bytes, more fragments will follow
EAP: method process -> ignore=FALSE methodState=MAY_CONT decision=FAIL eapRespData=0x55f53f3cade0
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=1408)
TX EAP -> RADIUS - hexdump(len=1408): 02 b7 05 80 0d c0 00 00 0a 6e 16 03 03 08 de 0b 00 08 da 00 08 d7 00 03 d3 30 82 03 cf 30 82 02 b7 a0 03 02 01 02 02 01 02 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 71 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 19 30 17 06 03 55 04 03 0c 10 75 73 65 72 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 1f 30 1d 06 09 2a 86 48 86 f7 0d 01 09 01 16 10 75 73 65 72 40 65 78 61 6d 70 6c 65 2e 6f 72 67 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 ac 64 f9 52 38 ec f6 6d 2e 16 5e 9e 5b 33 10 ca 9d b0 b8 2d c7 98 21 6e 76 49 c9 e7 73 48 82 90 a6 fd 40 85 2f 7a 6f a8 50 7f a8 8a 81 33 e1 b6 51 75 40 17 ea 49 bb 27 d3 f7 55 ee c4 47 0b 82 4e 29 3e 7d e0 b0 6e 6c aa 88 55 99 3e 21 a1 5e 22 35 22 01 71 2d 04 87 82 25 39 0a 26 d5 44 b2 8f eb 4d e3 29 46 a7 83 de e5 01 d5 81 e4 2c ed bf fe 7f 57 70 df 52 f0 64 77 e9 8f ff 30 43 19 8e 08 28 76 99 99 89 6f 8e a1 d4 e6 5e 34 6f 04 67 30 b9 b3 a1 94 53 3c 9f c6 e7 71 3e ad 2a 11 ff 38 33 24 35 3f 76 ee 91 cf da 03 51 56 3d 4a 12 7d 05 0c 73 8b 88 f4 d0 38 27 b3 e8 09 3c 8d ff 67 cc 2d 1f ce 02 c1 d8 34 62 2b 42 5a 33 19 ae cd 30 4a 89 54 74 6b b2 28 59 f7 65 7c 72 29 04 3d e1 fc 31 c8 c9 ad 8a 1c 10 17 4a 71 88 99 aa 44 28 f7 3d 18 d3 8f 9f 17 3e ca 71 56 bd 67 02 03 01 00 01 a3 4f 30 4d 30 13 06 03 55 1d 25 04 0c 30 0a 06 08 2b 06 01 05 05 07 03 02 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 63 6f 6d 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 7f 6a 16 6b 0b 48 1b c5 b6 2f 4f e2 49 42 fe 84 16 f4 46 c3 f5 dd ea 61 2b e4 e9 91 ed 8f 00 c3 15 bc 58 ba c2 9a da 2b d6 c9 2f c1 a9 10 b3 fb 15 10 0c 2b 8f 3f 82 67 73 05 f2 69 45 46 26 8c a9 76 6c 07 67 af 42 a1 7d a8 5b 4a 1c c5 59 33 8e 7d c8 d4 e5 4b 93 7a 31 cf aa be 2e 9c 65 29 73 c7 02 3b b7 c1 49 a2 f5 54 ca 73 de b0 12 b4 55 03 44 34 aa cb 81 0e 11 4f a0 13 a7 d8 63 f3 3d 70 86 48 e7 88 ee 56 5c eb 83 04 c4 77 a7 e7 8d da 95 a6 1c b4 86 0c 48 51 b1 8a c6 b8 52 44 b8 3b 55 59 78 60 e9 94 42 c7 a1 28 4b 1d c7 95 fc 0e 5a 3f 63 56 2b 4c 9a 0e c6 2d 41 61 ad 1c e5 86 3b f3 71 14 1f e9 03 82 c6 41 3d 9d f7 88 77 d0 55 a0 dc cc d9 c3 1f 68 40 5f 07 a4 18 8d cf cc dd 11 13 bd 59 79 c7 f7 2c f1 2e 97 f7 63 47 28 92 c1 91 04 91 6e db e9 44 2f d8 c5 4a be 00 04 fe 30 82 04 fa 30 82 03 e2 a0 03 02 01 02 02 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=4 length=1552Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=255Value: 02b705800dc000000a6e16030308de0b0008da0008d70003d3308203cf308202b7a003020102020102300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a3071310b3009060355040613024652Attribute 79 (EAP-Message) length=255Value: 310f300d06035504080c0652616469757331153013060355040a0c0c4578616d706c6520496e632e3119301706035504030c1075736572406578616d706c652e6f7267311f301d06092a864886f70d010901161075736572406578616d706c652e6f726730820122300d06092a864886f70d01010105000382010f003082010a0282010100ac64f95238ecf66d2e165e9e5b3310ca9db0b82dc798216e7649c9e773488290a6fd40852f7a6fa8507fa88a8133e1b651754017ea49bb27d3f755eec4470b824e293e7de0b06e6caa8855993e21a15e22352201712d04878225390a26d544b28feb4de32946a783dee501d581e42cedbffe7f5770df52f0Attribute 79 (EAP-Message) length=255Value: 6477e98fff3043198e0828769999896f8ea1d4e65e346f046730b9b3a194533c9fc6e7713ead2a11ff383324353f76ee91cfda0351563d4a127d050c738b88f4d03827b3e8093c8dff67cc2d1fce02c1d834622b425a3319aecd304a8954746bb22859f7657c7229043de1fc31c8c9ad8a1c10174a718899aa4428f73d18d38f9f173eca7156bd670203010001a34f304d30130603551d25040c300a06082b0601050507030230360603551d1f042f302d302ba029a0278625687474703a2f2f7777772e6578616d706c652e636f6d2f6578616d706c655f63612e63726c300d06092a864886f70d01010b050003820101007f6a166b0b481bc5b62f4fAttribute 79 (EAP-Message) length=255Value: e24942fe8416f446c3f5ddea612be4e991ed8f00c315bc58bac29ada2bd6c92fc1a910b3fb15100c2b8f3f82677305f2694546268ca9766c0767af42a17da85b4a1cc559338e7dc8d4e54b937a31cfaabe2e9c652973c7023bb7c149a2f554ca73deb012b455034434aacb810e114fa013a7d863f33d708648e788ee565ceb8304c477a7e78dda95a61cb4860c4851b18ac6b85244b83b55597860e99442c7a1284b1dc795fc0e5a3f63562b4c9a0ec62d4161ad1ce5863bf371141fe90382c6413d9df78877d055a0dcccd9c31f68405f07a4188dcfccdd1113bd5979c7f72cf12e97f763472892c19104916edbe9442fd8c54abe0004fe308204fa30Attribute 79 (EAP-Message) length=255Value: 8203e2a00302010202144a1dec91e0857d76d65f37d6ddaab4191176ebcb300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a308193310b3009060355040613024652310f300d06035504080cAttribute 79 (EAP-Message) length=145Value: 065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f7269747930820122300d06092a864886f70d0101010500Attribute 24 (State) length=18Value: 6c230b426f9406dd3f72ef77da978e44Attribute 80 (Message-Authenticator) length=18Value: 8228db5cf9000b6b8ed9b81d4a63193b
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 64 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=4 length=64Attribute 79 (EAP-Message) length=8Value: 01b800060d00Attribute 80 (Message-Authenticator) length=18Value: 59d4660db4b29806d55a0478b9a4c9a2Attribute 24 (State) length=18Value: 6c230b42689b06dd3f72ef77da978e44
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=184 len=6) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=184 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state METHOD
SSL: Received packet(len=6) - Flags 0x00
SSL: 1272 bytes left to be sent out (of total 2670 bytes)
EAP: method process -> ignore=FALSE methodState=MAY_CONT decision=FAIL eapRespData=0x55f53f3cade0
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=1278)
TX EAP -> RADIUS - hexdump(len=1278): 02 b8 04 fe 0d 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 d7 ab 97 ba 11 f9 01 e2 bc be 70 3c 7b 5a 46 8f ea 2a 40 2b d2 7b 36 1c 81 59 26 d7 d1 f5 7f c3 3a 40 04 83 d8 0c 8a 3f bc eb 16 bc a8 25 98 1c da 2e c7 33 0b 40 78 00 f1 7d cf f7 76 18 b2 f6 a4 a7 a9 22 16 ef 2c a4 20 0e 5b e3 5a 17 a0 f2 a1 5b f8 b4 33 12 c6 62 90 72 9a ea b2 c5 ba 23 7e c9 4e 9a 1f 52 57 48 3e ee de 76 62 6d 67 7f 0d d9 1e e8 92 02 fc 8d ae 4e 3c 01 5f b9 8a 4f 07 50 aa 0e 7e d1 bd 5c 3a 6b 86 23 63 8d 87 6f 4d ab 25 69 0b e8 7e 09 6d 7e 88 75 29 07 2b d3 ee de a0 bf f0 65 fd 9b 79 91 4e 0e 7b 74 0f 23 6f 20 37 2b 3b 0a d1 e9 ac ec 52 b3 75 41 ce a0 af 33 72 9d ae 3e 4a 63 22 e8 6b 44 a1 59 c6 df 35 79 0b 0b 6a 26 fc 94 28 a8 f3 23 e3 51 98 64 8b 7b 50 93 50 f3 dd 72 92 9a b5 f2 97 0f 5d d4 ef 27 15 75 f3 66 5b 69 b5 bd 94 76 8b 84 78 3f 02 03 01 00 01 a3 82 01 42 30 82 01 3e 30 1d 06 03 55 1d 0e 04 16 04 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 30 81 d3 06 03 55 1d 23 04 81 cb 30 81 c8 80 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 a1 81 99 a4 81 96 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 82 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0f 06 03 55 1d 13 01 01 ff 04 05 30 03 01 01 ff 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 6f 72 67 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 5a 51 d3 79 e5 b5 6b 81 6e 7a 7b d9 ea 45 4a 1a 68 62 30 c6 0c 53 f1 7c a7 0b 7f 71 6c 0c 0d a2 eb af ba ac f1 61 5d ac 12 1f 23 e4 b9 f8 3b 66 70 0c 2d bf 93 5a 16 e9 ad 93 6f b6 c6 08 f9 f1 2c bd 45 02 7e 08 89 e6 b5 9c 78 cc 47 f4 07 ea 36 e3 2b dd 38 ae 9a 5b f3 90 9b f6 8c 03 28 e3 be f6 77 fe c2 d9 87 31 b1 bd 09 45 68 32 b2 11 c8 65 74 12 1e 3f 2e 8d e7 56 02 b0 f5 eb 97 4f 3a 4d e2 6a 81 54 97 22 77 94 51 a9 47 d6 9b 5d c9 f7 b3 88 e2 19 74 d5 ed 35 18 b7 04 d9 51 a1 ed a7 30 1d 00 94 93 e3 fc 40 7e bb ae 92 4d f0 16 90 3a 69 ad c3 79 09 ec df 37 22 eb 1b 96 46 33 fc cd 6e ef d8 f9 4c cc e6 10 8c e3 e8 4b 1d 4d 6e 8a 25 7b 20 e0 ba bd c5 3c d8 b2 40 e9 ca 84 40 bd 97 7a 4d b8 11 81 41 64 a7 89 0a bb 48 d0 64 2a 83 d2 3a 90 1c 60 54 65 ff ee ea c2 41 16 03 03 00 46 10 00 00 42 41 04 00 76 b7 24 8a c2 72 34 69 ff dd 85 1e a2 3e f6 df a9 5e ba 2a 57 7c 49 a0 bc 8d 52 12 42 b4 9f f7 ce c9 98 e5 e1 24 2a f9 bb a5 8b d0 e3 8f e7 4c fb a6 77 4b f9 48 c9 ce 65 26 6c 28 64 82 9b 16 03 03 01 08 0f 00 01 04 08 04 01 00 35 c6 e4 96 6e 51 08 e5 20 1f e6 2c 5b d2 f6 25 d1 18 97 ff 20 17 ab bc 55 8a fb 63 d7 8c 96 08 26 cd 4d ae a2 b0 a0 73 5e 1d d6 f8 3c 9e f0 71 2e c9 ed 68 de 45 58 cd 2b 6e 4e 72 43 79 b9 23 e5 ca 86 4e 56 33 a6 c1 ec 9e b6 50 c2 a7 ed 81 26 3d b9 59 1b 8a 08 f2 3d 30 94 e1 0b 3a 0d 29 95 de d5 45 33 f1 1f 6d 4d 68 65 b4 94 97 a9 07 4f 5a 18 a2 f1 8d 43 16 34 76 21 fe 53 7b df 41 64 fc 51 19 0d 43 5c 7f 15 46 7c 74 1e bf a4 6c 85 5d ef a7 4d 07 c5 19 7d c2 ad 9b 82 91 ad 2c f6 af 83 19 8e bb 7f 27 35 7f 9d f5 e0 de 36 d1 b5 de 02 b2 1e b7 c5 1e 1b 50 db 9d 3f ea ec 39 4e e1 8f ff f7 fc 44 ac fc 16 12 8c 34 11 b2 f6 bb 31 15 63 6e 6f fc a7 24 7c 8c ce 11 5e dc 36 3d a4 3d 77 cd 3a d0 1e b0 87 e7 65 90 4a 87 6b c8 9d 3a c9 ba ad 34 05 fd d6 71 8f ac 3b f2 c8 14 03 03 00 01 01 16 03 03 00 28 fb 60 0b d3 9c cb e7 d7 dd 29 d9 e5 5f c9 aa 28 5b 50 af 61 f3 e0 c9 c6 d0 e3 44 d8 e2 54 7e af cc 5a 6a d0 b7 57 63 eb
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=5 length=1422Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=255Value: 02b804fe0d000382010f003082010a0282010100d7ab97ba11f901e2bcbe703c7b5a468fea2a402bd27b361c815926d7d1f57fc33a400483d80c8a3fbceb16bca825981cda2ec7330b407800f17dcff77618b2f6a4a7a92216ef2ca4200e5be35a17a0f2a15bf8b43312c66290729aeab2c5ba237ec94e9a1f5257483eeede76626d677f0dd91ee89202fc8dae4e3c015fb98a4f0750aa0e7ed1bd5c3a6b8623638d876f4dab25690be87e096d7e887529072bd3eedea0bff065fd9b79914e0e7b740f236f20372b3b0ad1e9acec52b37541cea0af33729dae3e4a6322e86b44a159c6df35790b0b6a26fc9428a8f323e35198648b7b509350f3dd7292Attribute 79 (EAP-Message) length=255Value: 9ab5f2970f5dd4ef271575f3665b69b5bd94768b84783f0203010001a38201423082013e301d0603551d0e0416041401571d779e50f5b591d6dad496f89ac3bc91cf273081d30603551d230481cb3081c8801401571d779e50f5b591d6dad496f89ac3bc91cf27a18199a48196308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574Attribute 79 (EAP-Message) length=255Value: 686f7269747982144a1dec91e0857d76d65f37d6ddaab4191176ebcb300f0603551d130101ff040530030101ff30360603551d1f042f302d302ba029a0278625687474703a2f2f7777772e6578616d706c652e6f72672f6578616d706c655f63612e63726c300d06092a864886f70d01010b050003820101005a51d379e5b56b816e7a7bd9ea454a1a686230c60c53f17ca70b7f716c0c0da2ebafbaacf1615dac121f23e4b9f83b66700c2dbf935a16e9ad936fb6c608f9f12cbd45027e0889e6b59c78cc47f407ea36e32bdd38ae9a5bf3909bf68c0328e3bef677fec2d98731b1bd09456832b211c86574121e3f2e8de75602b0f5eb974f3a4de26aAttribute 79 (EAP-Message) length=255Value: 81549722779451a947d69b5dc9f7b388e21974d5ed3518b704d951a1eda7301d009493e3fc407ebbae924df016903a69adc37909ecdf3722eb1b964633fccd6eefd8f94ccce6108ce3e84b1d4d6e8a257b20e0babdc53cd8b240e9ca8440bd977a4db811814164a7890abb48d0642a83d23a901c605465ffeeeac24116030300461000004241040076b7248ac2723469ffdd851ea23ef6dfa95eba2a577c49a0bc8d521242b49ff7cec998e5e1242af9bba58bd0e38fe74cfba6774bf948c9ce65266c2864829b16030301080f0001040804010035c6e4966e5108e5201fe62c5bd2f625d11897ff2017abbc558afb63d78c960826cd4daea2b0a0735eAttribute 79 (EAP-Message) length=255Value: 1dd6f83c9ef0712ec9ed68de4558cd2b6e4e724379b923e5ca864e5633a6c1ec9eb650c2a7ed81263db9591b8a08f23d3094e10b3a0d2995ded54533f11f6d4d6865b49497a9074f5a18a2f18d4316347621fe537bdf4164fc51190d435c7f15467c741ebfa46c855defa74d07c5197dc2ad9b8291ad2cf6af83198ebb7f27357f9df5e0de36d1b5de02b21eb7c51e1b50db9d3feaec394ee18ffff7fc44acfc16128c3411b2f6bb3115636e6ffca7247c8cce115edc363da43d77cd3ad01eb087e765904a876bc89d3ac9baad3405fdd6718fac3bf2c81403030001011603030028fb600bd39ccbe7d7dd29d9e55fc9aa285b50af61f3e0c9c6d0e344Attribute 79 (EAP-Message) length=15Value: d8e2547eafcc5a6ad0b75763ebAttribute 24 (State) length=18Value: 6c230b42689b06dd3f72ef77da978e44Attribute 80 (Message-Authenticator) length=18Value: 9e2711b54704816bd91181531d40d2ae
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 119 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=5 length=119Attribute 79 (EAP-Message) length=63Value: 01b9003d0d80000000331403030001011603030028dc53bb3b9e6835a8a8c0d2fbd020917f5be216dd2e27079dbcfa8fb4ed08494bfd8bd80050b4c025Attribute 80 (Message-Authenticator) length=18Value: d4e716bd5bb080da3b4c34ba4be986c0Attribute 24 (State) length=18Value: 6c230b42699a06dd3f72ef77da978e44
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=185 len=61) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=185 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state METHOD
SSL: Received packet(len=61) - Flags 0x80
SSL: TLS Message Length: 51
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 14 03 03 00 01
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write finished
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 28
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read change cipher spec
OpenSSL: RX ver=0x303 content_type=22 (handshake/finished)
OpenSSL: Message - hexdump(len=16): 14 00 00 0c bd f4 c5 5b 76 2c 1d ce d3 3d ab 9f
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read finished
SSL: (where=0x20 ret=0x1)
SSL: (where=0x1002 ret=0x1)
SSL: 0 bytes pending from ssl_out
OpenSSL: Handshake finished - resumed=0
SSL: No Application Data included
SSL: Using TLS version TLSv1.2
SSL: No data to be sent out
EAP-TLS: Done
EAP-TLS: Derived key - hexdump(len=64): d2 7c ad 7f 33 ed 9c 41 0c c9 3e ca 5a 54 46 ca 01 1d e9 0b d7 9a 51 9d 1c e1 e4 8b e7 f8 43 da 60 87 6a 79 43 b0 c5 ea 97 2e 79 74 70 49 c2 03 3c 1f 55 7f 0b 5e 68 d1 89 7f 4a b3 b2 fc cd 10
EAP-TLS: Derived EMSK - hexdump(len=64): 9c cd 14 96 df 3d 8c 9a 85 3b c0 f1 80 c8 a9 9f 88 81 65 c4 57 b0 66 c0 27 6c 1d 88 89 2d 0c d2 16 e7 fb 31 64 79 ae 20 3d 01 26 02 84 26 b4 5f a1 3a 0c ec cf 25 fe 6e e7 1f e1 b3 a1 b2 bf a4
EAP-TLS: Derived Session-Id - hexdump(len=65): 0d 7e 68 ad 1c 85 d2 20 ab f7 73 85 46 c7 5a 38 5b f6 4d c6 b4 d4 b0 9f ca 12 e9 ba bd eb d5 98 cc 11 ea c7 5f 3f 74 8e 3d fc f6 e1 de 94 d5 d4 83 28 00 32 22 21 b5 f4 9e fc b8 ce 4a 0b a8 c0 ad
SSL: Building ACK (type=13 id=185 ver=0)
EAP: method process -> ignore=FALSE methodState=DONE decision=UNCOND_SUCC eapRespData=0x55f53f3c67f0
EAP: Session-Id - hexdump(len=65): 0d 7e 68 ad 1c 85 d2 20 ab f7 73 85 46 c7 5a 38 5b f6 4d c6 b4 d4 b0 9f ca 12 e9 ba bd eb d5 98 cc 11 ea c7 5f 3f 74 8e 3d fc f6 e1 de 94 d5 d4 83 28 00 32 22 21 b5 f4 9e fc b8 ce 4a 0b a8 c0 ad
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=6)
TX EAP -> RADIUS - hexdump(len=6): 02 b9 00 06 0d 00
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=6 length=140Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=8Value: 02b900060d00Attribute 24 (State) length=18Value: 6c230b42699a06dd3f72ef77da978e44Attribute 80 (Message-Authenticator) length=18Value: d60ee5f5d4e73503749e17011d6c7964
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 169 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=2 (Access-Accept) identifier=6 length=169Attribute 26 (Vendor-Specific) length=58Value: 000001371134835db3b61fa4a812390f35c1a0ee360d96bb6fadaa4de889d183aef6b4b6d97172080c42372979498be0d9365ad08f1e172dAttribute 26 (Vendor-Specific) length=58Value: 0000013710348d35cf1bd49049e67b4a9dd51b3ad6094bf9a398722357d43683d9ba37f7db421553a6585e3c4e6bcf6d452dc05927015226Attribute 79 (EAP-Message) length=6Value: 03b90004Attribute 80 (Message-Authenticator) length=18Value: f5b5b912328634514791bfab1a66e1d9Attribute 1 (User-Name) length=9Value: 'testing'
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
MS-MPPE-Send-Key (sign) - hexdump(len=32): 60 87 6a 79 43 b0 c5 ea 97 2e 79 74 70 49 c2 03 3c 1f 55 7f 0b 5e 68 d1 89 7f 4a b3 b2 fc cd 10
MS-MPPE-Recv-Key (crypt) - hexdump(len=32): d2 7c ad 7f 33 ed 9c 41 0c c9 3e ca 5a 54 46 ca 01 1d e9 0b d7 9a 51 9d 1c e1 e4 8b e7 f8 43 da
decapsulated EAP packet (code=3 id=185 len=4) from RADIUS server: EAP Success
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Success
EAP: Status notification: completion (param=success)
EAP: EAP entering state SUCCESS
CTRL-EVENT-EAP-SUCCESS EAP authentication completed successfully
EAPOL: IEEE 802.1X for plaintext connection; no EAPOL-Key frames required
WPA: EAPOL processing complete
Cancelling authentication timeout
State: DISCONNECTED -> COMPLETED
EAPOL: SUPP_PAE entering state AUTHENTICATED
EAPOL: SUPP_BE entering state RECEIVE
EAPOL: SUPP_BE entering state SUCCESS
EAPOL: SUPP_BE entering state IDLE
eapol_sm_cb: result=1
EAPOL: Successfully fetched key (len=32)
PMK from EAPOL - hexdump(len=32): d2 7c ad 7f 33 ed 9c 41 0c c9 3e ca 5a 54 46 ca 01 1d e9 0b d7 9a 51 9d 1c e1 e4 8b e7 f8 43 da
No EAP-Key-Name received from servereapol_test: Triggering EAP reauthenticationSending fake EAP-Request-Identity
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_PAE entering state RESTART
EAP: EAP entering state INITIALIZE
EAP: maintaining EAP method data for fast reauthentication
EAP: EAP entering state IDLE
EAPOL: SUPP_PAE entering state AUTHENTICATING
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=171 method=1 vendor=0 vendorMethod=0
EAP: EAP entering state IDENTITY
CTRL-EVENT-EAP-STARTED EAP authentication started
EAP: Status notification: started (param=)
EAP: EAP-Request Identity data - hexdump_ascii(len=0):
EAP: using real identity - hexdump_ascii(len=7):74 65 73 74 69 6e 67 testing
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=12)
TX EAP -> RADIUS - hexdump(len=12): 02 ab 00 0c 01 74 65 73 74 69 6e 67
Encapsulating EAP message into a RADIUS packet
Learned identity from EAP-Response-Identity - hexdump(len=7): 74 65 73 74 69 6e 67
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=7 length=128Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=14Value: 02ab000c0174657374696e67Attribute 80 (Message-Authenticator) length=18Value: 0a71043021b8182be018447a91ae3247
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 64 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=7 length=64Attribute 79 (EAP-Message) length=8Value: 01ac00060d20Attribute 80 (Message-Authenticator) length=18Value: f7bc2d8b354b24b7d22e741701a20abeAttribute 24 (State) length=18Value: fb1c2c65fbb0217da229744af77aa30f
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=172 len=6) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=172 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state GET_METHOD
CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=13
EAP: Status notification: accept proposed method (param=TLS)
EAP: Using previous method data for fast re-authentication
EAP: Initialize selected EAP method: vendor 0 method 13 (TLS)
CTRL-EVENT-EAP-METHOD EAP vendor 0 method 13 (TLS) selected
EAP: EAP entering state METHOD
SSL: Received packet(len=6) - Flags 0x20
EAP-TLS: Start
SSL: (where=0x10 ret=0x1)
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:before SSL initialization
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 01 00 b3
OpenSSL: TX ver=0x303 content_type=22 (handshake/client hello)
OpenSSL: Message - hexdump(len=179): 01 00 00 af 03 03 9d af b8 19 1c 05 97 0d 0f c3 a0 a6 6a 19 b3 3e 51 6c bd 83 0a 9c f0 d7 df 32 43 90 c3 af 4a 30 00 00 38 c0 2c c0 30 00 9f cc a9 cc a8 cc aa c0 2b c0 2f 00 9e c0 24 c0 28 00 6b c0 23 c0 27 00 67 c0 0a c0 14 00 39 c0 09 c0 13 00 33 00 9d 00 9c 00 3d 00 3c 00 35 00 2f 00 ff 01 00 00 4e 00 0b 00 04 03 00 01 02 00 0a 00 0c 00 0a 00 1d 00 17 00 1e 00 19 00 18 00 16 00 00 00 17 00 00 00 0d 00 2a 00 28 04 03 05 03 06 03 08 07 08 08 08 09 08 0a 08 0b 08 04 08 05 08 06 04 01 05 01 06 01 03 03 03 01 03 02 04 02 05 02 06 02
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write client hello
SSL: (where=0x1002 ret=0xffffffff)
SSL: SSL_connect:error in SSLv3/TLS write client hello
SSL: SSL_connect - want more data
SSL: 184 bytes pending from ssl_out
SSL: Using TLS version TLSv1.2
SSL: 184 bytes left to be sent out (of total 184 bytes)
EAP: method process -> ignore=FALSE methodState=MAY_CONT decision=FAIL eapRespData=0x55f53f3be910
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=190)
TX EAP -> RADIUS - hexdump(len=190): 02 ac 00 be 0d 00 16 03 01 00 b3 01 00 00 af 03 03 9d af b8 19 1c 05 97 0d 0f c3 a0 a6 6a 19 b3 3e 51 6c bd 83 0a 9c f0 d7 df 32 43 90 c3 af 4a 30 00 00 38 c0 2c c0 30 00 9f cc a9 cc a8 cc aa c0 2b c0 2f 00 9e c0 24 c0 28 00 6b c0 23 c0 27 00 67 c0 0a c0 14 00 39 c0 09 c0 13 00 33 00 9d 00 9c 00 3d 00 3c 00 35 00 2f 00 ff 01 00 00 4e 00 0b 00 04 03 00 01 02 00 0a 00 0c 00 0a 00 1d 00 17 00 1e 00 19 00 18 00 16 00 00 00 17 00 00 00 0d 00 2a 00 28 04 03 05 03 06 03 08 07 08 08 08 09 08 0a 08 0b 08 04 08 05 08 06 04 01 05 01 06 01 03 03 03 01 03 02 04 02 05 02 06 02
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=8 length=324Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=192Value: 02ac00be0d0016030100b3010000af03039dafb8191c05970d0fc3a0a66a19b33e516cbd830a9cf0d7df324390c3af4a30000038c02cc030009fcca9cca8ccaac02bc02f009ec024c028006bc023c0270067c00ac0140039c009c0130033009d009c003d003c0035002f00ff0100004e000b000403000102000a000c000a001d0017001e001900180016000000170000000d002a0028040305030603080708080809080a080b080408050806040105010601030303010302040205020602Attribute 24 (State) length=18Value: fb1c2c65fbb0217da229744af77aa30fAttribute 80 (Message-Authenticator) length=18Value: d9bf7e70fd9068540f30a0b63f123be0
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 1068 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=8 length=1068Attribute 79 (EAP-Message) length=255Value: 01ad03ec0dc000000b5c160303003d0200003903034292638f3837c75352d28e65b5fe48f830b19c085747f176374c9014f0c9f31e00c030000011ff01000100000b0004030001020017000016030308e90b0008e50008e20003de308203da308202c2a003020102020101300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c65204365Attribute 79 (EAP-Message) length=255Value: 72746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a307c310b3009060355040613024652310f300d06035504080c0652616469757331153013060355040a0c0c4578616d706c6520496e632e3123302106035504030c1a4578616d706c65205365727665722043657274696669636174653120301e06092a864886f70d010901161161646d696e406578616d706c652e6f726730820122300d06092a864886f70d01010105000382010f003082010a0282010100d1c0abffd46f4b5369d6d00416364ab0adef9cb6e6650d29521299d8ad893bf218f0934d0b97018b2dca90Attribute 79 (EAP-Message) length=255Value: 3b2bc3dc35144dbebe52e72021d263a2138231492ba3a6aadf640bcdabc40433c22d6d53ce4fb384c2576cc9326dae0befaaad84207485b03751401051d13e1e175a15926d4bd9ddabdc4bc327fd88eba4b01d6e4e61c54b3a36b8c3150d6b44699045e265040c85d67f181bd51e236f437e03b0755418b6d7c570f22c5216defb52dc25e1dbd6438f262dfa04f673f1fd325abad4e9d05cd1aa66258a27d5d174e6c2d4c3ecd756b1c9d2806c8fd7998d765e3bc8091101fba7ccadbb33f92560d6fba647c303d21366450adfd6c296d829c693870203010001a34f304d30130603551d25040c300a06082b0601050507030130360603551d1f042f30Attribute 79 (EAP-Message) length=247Value: 2d302ba029a0278625687474703a2f2f7777772e6578616d706c652e636f6d2f6578616d706c655f63612e63726c300d06092a864886f70d01010b05000382010100bd49899734116830715ab1b59f5748c02d47b925228a7c180cba3966d09c61d906ee2cc792065be7f44ea25da7837bd142d3b280178fbce6eda7abd9031f01f0cbbf17607d4543f9c649656f331584f56273933afd58fd4de6c40b9dff9dc2c4b7bcf09a713fcdf81a07ad00a73d099cbef6f1e81474d5fda07a975248861de4116171a7db5360e650bee856f75c838d51ae3bb1841f05e9f39166ff132a23e81cff02855b53cf09f7d54070be0c5107f64ab5Attribute 80 (Message-Authenticator) length=18Value: 9b2ef2325b6c1f5345205355e04ea925Attribute 24 (State) length=18Value: fb1c2c65fab1217da229744af77aa30f
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=173 len=1004) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=173 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state METHOD
SSL: Received packet(len=1004) - Flags 0xc0
SSL: TLS Message Length: 2908
SSL: Need 1914 bytes more input data
SSL: Building ACK (type=13 id=173 ver=0)
EAP: method process -> ignore=FALSE methodState=MAY_CONT decision=FAIL eapRespData=0x55f53f3ac990
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=6)
TX EAP -> RADIUS - hexdump(len=6): 02 ad 00 06 0d 00
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=9 length=140Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=8Value: 02ad00060d00Attribute 24 (State) length=18Value: fb1c2c65fab1217da229744af77aa30fAttribute 80 (Message-Authenticator) length=18Value: a01251081874341f20265ae787acbd1e
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 1068 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=9 length=1068Attribute 79 (EAP-Message) length=255Value: 01ae03ec0dc000000b5cd38235a4811c3f2e4cc129e388ad6f6c6237386b5f4d7ecc8d193c2465dfe051194474b53e1ac364e4b8fdcb527d6de8ca809cbfd5eb53a47785e62eaa3f7bafbeff699f9e631a78efbd38d6270004fe308204fa308203e2a00302010202144a1dec91e0857d76d65f37d6ddaab4191176ebcb300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f7267312630Attribute 79 (EAP-Message) length=255Value: 2406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f7269747930820122300d06092a864886f70d01010105000382010f003082010a0282010100d7Attribute 79 (EAP-Message) length=255Value: ab97ba11f901e2bcbe703c7b5a468fea2a402bd27b361c815926d7d1f57fc33a400483d80c8a3fbceb16bca825981cda2ec7330b407800f17dcff77618b2f6a4a7a92216ef2ca4200e5be35a17a0f2a15bf8b43312c66290729aeab2c5ba237ec94e9a1f5257483eeede76626d677f0dd91ee89202fc8dae4e3c015fb98a4f0750aa0e7ed1bd5c3a6b8623638d876f4dab25690be87e096d7e887529072bd3eedea0bff065fd9b79914e0e7b740f236f20372b3b0ad1e9acec52b37541cea0af33729dae3e4a6322e86b44a159c6df35790b0b6a26fc9428a8f323e35198648b7b509350f3dd72929ab5f2970f5dd4ef271575f3665b69b5bd94768b84Attribute 79 (EAP-Message) length=247Value: 783f0203010001a38201423082013e301d0603551d0e0416041401571d779e50f5b591d6dad496f89ac3bc91cf273081d30603551d230481cb3081c8801401571d779e50f5b591d6dad496f89ac3bc91cf27a18199a48196308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f7269747982144a1dec91e0Attribute 80 (Message-Authenticator) length=18Value: 749a0511c21bbe85e2f98544f4b04083Attribute 24 (State) length=18Value: fb1c2c65f9b2217da229744af77aa30f
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=174 len=1004) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=174 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state METHOD
SSL: Received packet(len=1004) - Flags 0xc0
SSL: TLS Message Length: 2908
SSL: Need 920 bytes more input data
SSL: Building ACK (type=13 id=174 ver=0)
EAP: method process -> ignore=FALSE methodState=MAY_CONT decision=FAIL eapRespData=0x55f53f3c64f0
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=6)
TX EAP -> RADIUS - hexdump(len=6): 02 ae 00 06 0d 00
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=10 length=140Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=8Value: 02ae00060d00Attribute 24 (State) length=18Value: fb1c2c65f9b2217da229744af77aa30fAttribute 80 (Message-Authenticator) length=18Value: 1c2532f478e413662af2678f7059a2fd
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 994 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=10 length=994Attribute 79 (EAP-Message) length=255Value: 01af03a20d8000000b5c857d76d65f37d6ddaab4191176ebcb300f0603551d130101ff040530030101ff30360603551d1f042f302d302ba029a0278625687474703a2f2f7777772e6578616d706c652e6f72672f6578616d706c655f63612e63726c300d06092a864886f70d01010b050003820101005a51d379e5b56b816e7a7bd9ea454a1a686230c60c53f17ca70b7f716c0c0da2ebafbaacf1615dac121f23e4b9f83b66700c2dbf935a16e9ad936fb6c608f9f12cbd45027e0889e6b59c78cc47f407ea36e32bdd38ae9a5bf3909bf68c0328e3bef677fec2d98731b1bd09456832b211c86574121e3f2e8de75602b0f5eb974f3a4de26a815497Attribute 79 (EAP-Message) length=255Value: 22779451a947d69b5dc9f7b388e21974d5ed3518b704d951a1eda7301d009493e3fc407ebbae924df016903a69adc37909ecdf3722eb1b964633fccd6eefd8f94ccce6108ce3e84b1d4d6e8a257b20e0babdc53cd8b240e9ca8440bd977a4db811814164a7890abb48d0642a83d23a901c605465ffeeeac241160303014d0c0001490300174104e492af51bf9dc795610dc800b30775562a278bde324386060087848fbadc72370d86a3724770d6a9665d4ab220f4ce98c0e1cb83d240ba6e375834e52258ef53080401007c46439b0e1100f51dd5686c67db4e90f6117f92294b1314e716608d93a9acb02147cd80d3b05a9c01d5538efc7f2cb64294Attribute 79 (EAP-Message) length=255Value: 7612b2811a2c871c3d43adba2c307943e72cca4801dc144374a9a053e34f6208655c3fbea8a41f7e4cb5edbbf99142750f2b91931147d9080e93251b6ecdcc351e4df7e213a03b00b183e1d066b6a29ef71a1653383fc4ffb4878eb79991a61466a978dc7651133e004e9ace96f561e43fa1148b7bc162335b2e3f387828fdce5075e5b78cb3b3d778e68e88252d2363ffd2789eceaf79c2f9324657a0222800f2e9e3aef8f19b7b64e840d9349984e97394e54545b1351d74b40c2611c4fccc20e2ff15ae39db1e4d31fc0f141216030300cc0d0000c8030102400028040305030603080708080809080a080b08040805080604010501060103030301Attribute 79 (EAP-Message) length=173Value: 030204020502060200980096308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f7269747916030300040e000000Attribute 80 (Message-Authenticator) length=18Value: c9d14b72281d494785bf27e0f0234e51Attribute 24 (State) length=18Value: fb1c2c65f8b3217da229744af77aa30f
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=175 len=930) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=175 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state METHOD
SSL: Received packet(len=930) - Flags 0x80
SSL: TLS Message Length: 2908
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 3d
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write client hello
OpenSSL: RX ver=0x303 content_type=22 (handshake/server hello)
OpenSSL: Message - hexdump(len=61): 02 00 00 39 03 03 42 92 63 8f 38 37 c7 53 52 d2 8e 65 b5 fe 48 f8 30 b1 9c 08 57 47 f1 76 37 4c 90 14 f0 c9 f3 1e 00 c0 30 00 00 11 ff 01 00 01 00 00 0b 00 04 03 00 01 02 00 17 00 00
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 08 e9
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read server hello
OpenSSL: RX ver=0x303 content_type=22 (handshake/certificate)
OpenSSL: Message - hexdump(len=2281): 0b 00 08 e5 00 08 e2 00 03 de 30 82 03 da 30 82 02 c2 a0 03 02 01 02 02 01 01 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 7c 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 23 30 21 06 03 55 04 03 0c 1a 45 78 61 6d 70 6c 65 20 53 65 72 76 65 72 20 43 65 72 74 69 66 69 63 61 74 65 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 d1 c0 ab ff d4 6f 4b 53 69 d6 d0 04 16 36 4a b0 ad ef 9c b6 e6 65 0d 29 52 12 99 d8 ad 89 3b f2 18 f0 93 4d 0b 97 01 8b 2d ca 90 3b 2b c3 dc 35 14 4d be be 52 e7 20 21 d2 63 a2 13 82 31 49 2b a3 a6 aa df 64 0b cd ab c4 04 33 c2 2d 6d 53 ce 4f b3 84 c2 57 6c c9 32 6d ae 0b ef aa ad 84 20 74 85 b0 37 51 40 10 51 d1 3e 1e 17 5a 15 92 6d 4b d9 dd ab dc 4b c3 27 fd 88 eb a4 b0 1d 6e 4e 61 c5 4b 3a 36 b8 c3 15 0d 6b 44 69 90 45 e2 65 04 0c 85 d6 7f 18 1b d5 1e 23 6f 43 7e 03 b0 75 54 18 b6 d7 c5 70 f2 2c 52 16 de fb 52 dc 25 e1 db d6 43 8f 26 2d fa 04 f6 73 f1 fd 32 5a ba d4 e9 d0 5c d1 aa 66 25 8a 27 d5 d1 74 e6 c2 d4 c3 ec d7 56 b1 c9 d2 80 6c 8f d7 99 8d 76 5e 3b c8 09 11 01 fb a7 cc ad bb 33 f9 25 60 d6 fb a6 47 c3 03 d2 13 66 45 0a df d6 c2 96 d8 29 c6 93 87 02 03 01 00 01 a3 4f 30 4d 30 13 06 03 55 1d 25 04 0c 30 0a 06 08 2b 06 01 05 05 07 03 01 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 63 6f 6d 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 bd 49 89 97 34 11 68 30 71 5a b1 b5 9f 57 48 c0 2d 47 b9 25 22 8a 7c 18 0c ba 39 66 d0 9c 61 d9 06 ee 2c c7 92 06 5b e7 f4 4e a2 5d a7 83 7b d1 42 d3 b2 80 17 8f bc e6 ed a7 ab d9 03 1f 01 f0 cb bf 17 60 7d 45 43 f9 c6 49 65 6f 33 15 84 f5 62 73 93 3a fd 58 fd 4d e6 c4 0b 9d ff 9d c2 c4 b7 bc f0 9a 71 3f cd f8 1a 07 ad 00 a7 3d 09 9c be f6 f1 e8 14 74 d5 fd a0 7a 97 52 48 86 1d e4 11 61 71 a7 db 53 60 e6 50 be e8 56 f7 5c 83 8d 51 ae 3b b1 84 1f 05 e9 f3 91 66 ff 13 2a 23 e8 1c ff 02 85 5b 53 cf 09 f7 d5 40 70 be 0c 51 07 f6 4a b5 d3 82 35 a4 81 1c 3f 2e 4c c1 29 e3 88 ad 6f 6c 62 37 38 6b 5f 4d 7e cc 8d 19 3c 24 65 df e0 51 19 44 74 b5 3e 1a c3 64 e4 b8 fd cb 52 7d 6d e8 ca 80 9c bf d5 eb 53 a4 77 85 e6 2e aa 3f 7b af be ff 69 9f 9e 63 1a 78 ef bd 38 d6 27 00 04 fe 30 82 04 fa 30 82 03 e2 a0 03 02 01 02 02 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 d7 ab 97 ba 11 f9 01 e2 bc be 70 3c 7b 5a 46 8f ea 2a 40 2b d2 7b 36 1c 81 59 26 d7 d1 f5 7f c3 3a 40 04 83 d8 0c 8a 3f bc eb 16 bc a8 25 98 1c da 2e c7 33 0b 40 78 00 f1 7d cf f7 76 18 b2 f6 a4 a7 a9 22 16 ef 2c a4 20 0e 5b e3 5a 17 a0 f2 a1 5b f8 b4 33 12 c6 62 90 72 9a ea b2 c5 ba 23 7e c9 4e 9a 1f 52 57 48 3e ee de 76 62 6d 67 7f 0d d9 1e e8 92 02 fc 8d ae 4e 3c 01 5f b9 8a 4f 07 50 aa 0e 7e d1 bd 5c 3a 6b 86 23 63 8d 87 6f 4d ab 25 69 0b e8 7e 09 6d 7e 88 75 29 07 2b d3 ee de a0 bf f0 65 fd 9b 79 91 4e 0e 7b 74 0f 23 6f 20 37 2b 3b 0a d1 e9 ac ec 52 b3 75 41 ce a0 af 33 72 9d ae 3e 4a 63 22 e8 6b 44 a1 59 c6 df 35 79 0b 0b 6a 26 fc 94 28 a8 f3 23 e3 51 98 64 8b 7b 50 93 50 f3 dd 72 92 9a b5 f2 97 0f 5d d4 ef 27 15 75 f3 66 5b 69 b5 bd 94 76 8b 84 78 3f 02 03 01 00 01 a3 82 01 42 30 82 01 3e 30 1d 06 03 55 1d 0e 04 16 04 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 30 81 d3 06 03 55 1d 23 04 81 cb 30 81 c8 80 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 a1 81 99 a4 81 96 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 82 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0f 06 03 55 1d 13 01 01 ff 04 05 30 03 01 01 ff 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 6f 72 67 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 5a 51 d3 79 e5 b5 6b 81 6e 7a 7b d9 ea 45 4a 1a 68 62 30 c6 0c 53 f1 7c a7 0b 7f 71 6c 0c 0d a2 eb af ba ac f1 61 5d ac 12 1f 23 e4 b9 f8 3b 66 70 0c 2d bf 93 5a 16 e9 ad 93 6f b6 c6 08 f9 f1 2c bd 45 02 7e 08 89 e6 b5 9c 78 cc 47 f4 07 ea 36 e3 2b dd 38 ae 9a 5b f3 90 9b f6 8c 03 28 e3 be f6 77 fe c2 d9 87 31 b1 bd 09 45 68 32 b2 11 c8 65 74 12 1e 3f 2e 8d e7 56 02 b0 f5 eb 97 4f 3a 4d e2 6a 81 54 97 22 77 94 51 a9 47 d6 9b 5d c9 f7 b3 88 e2 19 74 d5 ed 35 18 b7 04 d9 51 a1 ed a7 30 1d 00 94 93 e3 fc 40 7e bb ae 92 4d f0 16 90 3a 69 ad c3 79 09 ec df 37 22 eb 1b 96 46 33 fc cd 6e ef d8 f9 4c cc e6 10 8c e3 e8 4b 1d 4d 6e 8a 25 7b 20 e0 ba bd c5 3c d8 b2 40 e9 ca 84 40 bd 97 7a 4d b8 11 81 41 64 a7 89 0a bb 48 d0 64 2a 83 d2 3a 90 1c 60 54 65 ff ee ea c2 41
OpenSSL: Peer certificate - depth 1
Certificate:Data:Version: 3 (0x2)Serial Number:4a:1d:ec:91:e0:85:7d:76:d6:5f:37:d6:dd:aa:b4:19:11:76:eb:cbSignature Algorithm: sha256WithRSAEncryptionIssuer: C=FR, ST=Radius, L=Somewhere, O=Example Inc./emailAddress=admin@example.org, CN=Example Certificate AuthorityValidityNot Before: Feb 21 02:55:25 2024 GMTNot After : Apr 21 02:55:25 2024 GMTSubject: C=FR, ST=Radius, L=Somewhere, O=Example Inc./emailAddress=admin@example.org, CN=Example Certificate AuthoritySubject Public Key Info:Public Key Algorithm: rsaEncryptionRSA Public-Key: (2048 bit)Modulus:00:d7:ab:97:ba:11:f9:01:e2:bc:be:70:3c:7b:5a:46:8f:ea:2a:40:2b:d2:7b:36:1c:81:59:26:d7:d1:f5:7f:c3:3a:40:04:83:d8:0c:8a:3f:bc:eb:16:bc:a8:25:98:1c:da:2e:c7:33:0b:40:78:00:f1:7d:cf:f7:76:18:b2:f6:a4:a7:a9:22:16:ef:2c:a4:20:0e:5b:e3:5a:17:a0:f2:a1:5b:f8:b4:33:12:c6:62:90:72:9a:ea:b2:c5:ba:23:7e:c9:4e:9a:1f:52:57:48:3e:ee:de:76:62:6d:67:7f:0d:d9:1e:e8:92:02:fc:8d:ae:4e:3c:01:5f:b9:8a:4f:07:50:aa:0e:7e:d1:bd:5c:3a:6b:86:23:63:8d:87:6f:4d:ab:25:69:0b:e8:7e:09:6d:7e:88:75:29:07:2b:d3:ee:de:a0:bf:f0:65:fd:9b:79:91:4e:0e:7b:74:0f:23:6f:20:37:2b:3b:0a:d1:e9:ac:ec:52:b3:75:41:ce:a0:af:33:72:9d:ae:3e:4a:63:22:e8:6b:44:a1:59:c6:df:35:79:0b:0b:6a:26:fc:94:28:a8:f3:23:e3:51:98:64:8b:7b:50:93:50:f3:dd:72:92:9a:b5:f2:97:0f:5d:d4:ef:27:15:75:f3:66:5b:69:b5:bd:94:76:8b:84:78:3fExponent: 65537 (0x10001)X509v3 extensions:X509v3 Subject Key Identifier: 01:57:1D:77:9E:50:F5:B5:91:D6:DA:D4:96:F8:9A:C3:BC:91:CF:27X509v3 Authority Key Identifier: keyid:01:57:1D:77:9E:50:F5:B5:91:D6:DA:D4:96:F8:9A:C3:BC:91:CF:27DirName:/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authorityserial:4A:1D:EC:91:E0:85:7D:76:D6:5F:37:D6:DD:AA:B4:19:11:76:EB:CBX509v3 Basic Constraints: criticalCA:TRUEX509v3 CRL Distribution Points: Full Name:URI:http://www.example.org/example_ca.crlSignature Algorithm: sha256WithRSAEncryption5a:51:d3:79:e5:b5:6b:81:6e:7a:7b:d9:ea:45:4a:1a:68:62:30:c6:0c:53:f1:7c:a7:0b:7f:71:6c:0c:0d:a2:eb:af:ba:ac:f1:61:5d:ac:12:1f:23:e4:b9:f8:3b:66:70:0c:2d:bf:93:5a:16:e9:ad:93:6f:b6:c6:08:f9:f1:2c:bd:45:02:7e:08:89:e6:b5:9c:78:cc:47:f4:07:ea:36:e3:2b:dd:38:ae:9a:5b:f3:90:9b:f6:8c:03:28:e3:be:f6:77:fe:c2:d9:87:31:b1:bd:09:45:68:32:b2:11:c8:65:74:12:1e:3f:2e:8d:e7:56:02:b0:f5:eb:97:4f:3a:4d:e2:6a:81:54:97:22:77:94:51:a9:47:d6:9b:5d:c9:f7:b3:88:e2:19:74:d5:ed:35:18:b7:04:d9:51:a1:ed:a7:30:1d:00:94:93:e3:fc:40:7e:bb:ae:92:4d:f0:16:90:3a:69:ad:c3:79:09:ec:df:37:22:eb:1b:96:46:33:fc:cd:6e:ef:d8:f9:4c:cc:e6:10:8c:e3:e8:4b:1d:4d:6e:8a:25:7b:20:e0:ba:bd:c5:3c:d8:b2:40:e9:ca:84:40:bd:97:7a:4d:b8:11:81:41:64:a7:89:0a:bb:48:d0:64:2a:83:d2:3a:90:1c:60:54:65:ff:ee:ea:c2:41CTRL-EVENT-EAP-PEER-CERT depth=1 subject='/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authority' hash=5a7df6ac8a17be4f95d70e75e60d255c20228efd5de61400b72207dfbc976477
TLS: tls_verify_cb - preverify_ok=1 err=0 (ok) ca_cert_verify=1 depth=1 buf='/C=FR/ST=Radius/L=Somewhere/O=Example Inc./emailAddress=admin@example.org/CN=Example Certificate Authority'
OpenSSL: Peer certificate - depth 0
Certificate:Data:Version: 3 (0x2)Serial Number: 1 (0x1)Signature Algorithm: sha256WithRSAEncryptionIssuer: C=FR, ST=Radius, L=Somewhere, O=Example Inc./emailAddress=admin@example.org, CN=Example Certificate AuthorityValidityNot Before: Feb 21 02:55:25 2024 GMTNot After : Apr 21 02:55:25 2024 GMTSubject: C=FR, ST=Radius, O=Example Inc., CN=Example Server Certificate/emailAddress=admin@example.orgSubject Public Key Info:Public Key Algorithm: rsaEncryptionRSA Public-Key: (2048 bit)Modulus:00:d1:c0:ab:ff:d4:6f:4b:53:69:d6:d0:04:16:36:4a:b0:ad:ef:9c:b6:e6:65:0d:29:52:12:99:d8:ad:89:3b:f2:18:f0:93:4d:0b:97:01:8b:2d:ca:90:3b:2b:c3:dc:35:14:4d:be:be:52:e7:20:21:d2:63:a2:13:82:31:49:2b:a3:a6:aa:df:64:0b:cd:ab:c4:04:33:c2:2d:6d:53:ce:4f:b3:84:c2:57:6c:c9:32:6d:ae:0b:ef:aa:ad:84:20:74:85:b0:37:51:40:10:51:d1:3e:1e:17:5a:15:92:6d:4b:d9:dd:ab:dc:4b:c3:27:fd:88:eb:a4:b0:1d:6e:4e:61:c5:4b:3a:36:b8:c3:15:0d:6b:44:69:90:45:e2:65:04:0c:85:d6:7f:18:1b:d5:1e:23:6f:43:7e:03:b0:75:54:18:b6:d7:c5:70:f2:2c:52:16:de:fb:52:dc:25:e1:db:d6:43:8f:26:2d:fa:04:f6:73:f1:fd:32:5a:ba:d4:e9:d0:5c:d1:aa:66:25:8a:27:d5:d1:74:e6:c2:d4:c3:ec:d7:56:b1:c9:d2:80:6c:8f:d7:99:8d:76:5e:3b:c8:09:11:01:fb:a7:cc:ad:bb:33:f9:25:60:d6:fb:a6:47:c3:03:d2:13:66:45:0a:df:d6:c2:96:d8:29:c6:93:87Exponent: 65537 (0x10001)X509v3 extensions:X509v3 Extended Key Usage: TLS Web Server AuthenticationX509v3 CRL Distribution Points: Full Name:URI:http://www.example.com/example_ca.crlSignature Algorithm: sha256WithRSAEncryptionbd:49:89:97:34:11:68:30:71:5a:b1:b5:9f:57:48:c0:2d:47:b9:25:22:8a:7c:18:0c:ba:39:66:d0:9c:61:d9:06:ee:2c:c7:92:06:5b:e7:f4:4e:a2:5d:a7:83:7b:d1:42:d3:b2:80:17:8f:bc:e6:ed:a7:ab:d9:03:1f:01:f0:cb:bf:17:60:7d:45:43:f9:c6:49:65:6f:33:15:84:f5:62:73:93:3a:fd:58:fd:4d:e6:c4:0b:9d:ff:9d:c2:c4:b7:bc:f0:9a:71:3f:cd:f8:1a:07:ad:00:a7:3d:09:9c:be:f6:f1:e8:14:74:d5:fd:a0:7a:97:52:48:86:1d:e4:11:61:71:a7:db:53:60:e6:50:be:e8:56:f7:5c:83:8d:51:ae:3b:b1:84:1f:05:e9:f3:91:66:ff:13:2a:23:e8:1c:ff:02:85:5b:53:cf:09:f7:d5:40:70:be:0c:51:07:f6:4a:b5:d3:82:35:a4:81:1c:3f:2e:4c:c1:29:e3:88:ad:6f:6c:62:37:38:6b:5f:4d:7e:cc:8d:19:3c:24:65:df:e0:51:19:44:74:b5:3e:1a:c3:64:e4:b8:fd:cb:52:7d:6d:e8:ca:80:9c:bf:d5:eb:53:a4:77:85:e6:2e:aa:3f:7b:af:be:ff:69:9f:9e:63:1a:78:ef:bd:38:d6:27CTRL-EVENT-EAP-PEER-CERT depth=0 subject='/C=FR/ST=Radius/O=Example Inc./CN=Example Server Certificate/emailAddress=admin@example.org' hash=442c76845b6912ab534b2e2ea69570c8c86cd0e6098e66239bfd6bcc0a40d9fc
TLS: tls_verify_cb - preverify_ok=1 err=0 (ok) ca_cert_verify=1 depth=0 buf='/C=FR/ST=Radius/O=Example Inc./CN=Example Server Certificate/emailAddress=admin@example.org'
EAP: Status notification: remote certificate verification (param=success)
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 01 4d
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read server certificate
OpenSSL: RX ver=0x303 content_type=22 (handshake/server key exchange)
OpenSSL: Message - hexdump(len=333): 0c 00 01 49 03 00 17 41 04 e4 92 af 51 bf 9d c7 95 61 0d c8 00 b3 07 75 56 2a 27 8b de 32 43 86 06 00 87 84 8f ba dc 72 37 0d 86 a3 72 47 70 d6 a9 66 5d 4a b2 20 f4 ce 98 c0 e1 cb 83 d2 40 ba 6e 37 58 34 e5 22 58 ef 53 08 04 01 00 7c 46 43 9b 0e 11 00 f5 1d d5 68 6c 67 db 4e 90 f6 11 7f 92 29 4b 13 14 e7 16 60 8d 93 a9 ac b0 21 47 cd 80 d3 b0 5a 9c 01 d5 53 8e fc 7f 2c b6 42 94 76 12 b2 81 1a 2c 87 1c 3d 43 ad ba 2c 30 79 43 e7 2c ca 48 01 dc 14 43 74 a9 a0 53 e3 4f 62 08 65 5c 3f be a8 a4 1f 7e 4c b5 ed bb f9 91 42 75 0f 2b 91 93 11 47 d9 08 0e 93 25 1b 6e cd cc 35 1e 4d f7 e2 13 a0 3b 00 b1 83 e1 d0 66 b6 a2 9e f7 1a 16 53 38 3f c4 ff b4 87 8e b7 99 91 a6 14 66 a9 78 dc 76 51 13 3e 00 4e 9a ce 96 f5 61 e4 3f a1 14 8b 7b c1 62 33 5b 2e 3f 38 78 28 fd ce 50 75 e5 b7 8c b3 b3 d7 78 e6 8e 88 25 2d 23 63 ff d2 78 9e ce af 79 c2 f9 32 46 57 a0 22 28 00 f2 e9 e3 ae f8 f1 9b 7b 64 e8 40 d9 34 99 84 e9 73 94 e5 45 45 b1 35 1d 74 b4 0c 26 11 c4 fc cc 20 e2 ff 15 ae 39 db 1e 4d 31 fc 0f 14 12
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 cc
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read server key exchange
OpenSSL: RX ver=0x303 content_type=22 (handshake/certificate request)
OpenSSL: Message - hexdump(len=204): 0d 00 00 c8 03 01 02 40 00 28 04 03 05 03 06 03 08 07 08 08 08 09 08 0a 08 0b 08 04 08 05 08 06 04 01 05 01 06 01 03 03 03 01 03 02 04 02 05 02 06 02 00 98 00 96 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 04
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read server certificate request
OpenSSL: RX ver=0x303 content_type=22 (handshake/server hello done)
OpenSSL: Message - hexdump(len=4): 0e 00 00 00
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read server done
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 08 de
OpenSSL: TX ver=0x303 content_type=22 (handshake/certificate)
OpenSSL: Message - hexdump(len=2270): 0b 00 08 da 00 08 d7 00 03 d3 30 82 03 cf 30 82 02 b7 a0 03 02 01 02 02 01 02 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 71 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 19 30 17 06 03 55 04 03 0c 10 75 73 65 72 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 1f 30 1d 06 09 2a 86 48 86 f7 0d 01 09 01 16 10 75 73 65 72 40 65 78 61 6d 70 6c 65 2e 6f 72 67 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 ac 64 f9 52 38 ec f6 6d 2e 16 5e 9e 5b 33 10 ca 9d b0 b8 2d c7 98 21 6e 76 49 c9 e7 73 48 82 90 a6 fd 40 85 2f 7a 6f a8 50 7f a8 8a 81 33 e1 b6 51 75 40 17 ea 49 bb 27 d3 f7 55 ee c4 47 0b 82 4e 29 3e 7d e0 b0 6e 6c aa 88 55 99 3e 21 a1 5e 22 35 22 01 71 2d 04 87 82 25 39 0a 26 d5 44 b2 8f eb 4d e3 29 46 a7 83 de e5 01 d5 81 e4 2c ed bf fe 7f 57 70 df 52 f0 64 77 e9 8f ff 30 43 19 8e 08 28 76 99 99 89 6f 8e a1 d4 e6 5e 34 6f 04 67 30 b9 b3 a1 94 53 3c 9f c6 e7 71 3e ad 2a 11 ff 38 33 24 35 3f 76 ee 91 cf da 03 51 56 3d 4a 12 7d 05 0c 73 8b 88 f4 d0 38 27 b3 e8 09 3c 8d ff 67 cc 2d 1f ce 02 c1 d8 34 62 2b 42 5a 33 19 ae cd 30 4a 89 54 74 6b b2 28 59 f7 65 7c 72 29 04 3d e1 fc 31 c8 c9 ad 8a 1c 10 17 4a 71 88 99 aa 44 28 f7 3d 18 d3 8f 9f 17 3e ca 71 56 bd 67 02 03 01 00 01 a3 4f 30 4d 30 13 06 03 55 1d 25 04 0c 30 0a 06 08 2b 06 01 05 05 07 03 02 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 63 6f 6d 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 7f 6a 16 6b 0b 48 1b c5 b6 2f 4f e2 49 42 fe 84 16 f4 46 c3 f5 dd ea 61 2b e4 e9 91 ed 8f 00 c3 15 bc 58 ba c2 9a da 2b d6 c9 2f c1 a9 10 b3 fb 15 10 0c 2b 8f 3f 82 67 73 05 f2 69 45 46 26 8c a9 76 6c 07 67 af 42 a1 7d a8 5b 4a 1c c5 59 33 8e 7d c8 d4 e5 4b 93 7a 31 cf aa be 2e 9c 65 29 73 c7 02 3b b7 c1 49 a2 f5 54 ca 73 de b0 12 b4 55 03 44 34 aa cb 81 0e 11 4f a0 13 a7 d8 63 f3 3d 70 86 48 e7 88 ee 56 5c eb 83 04 c4 77 a7 e7 8d da 95 a6 1c b4 86 0c 48 51 b1 8a c6 b8 52 44 b8 3b 55 59 78 60 e9 94 42 c7 a1 28 4b 1d c7 95 fc 0e 5a 3f 63 56 2b 4c 9a 0e c6 2d 41 61 ad 1c e5 86 3b f3 71 14 1f e9 03 82 c6 41 3d 9d f7 88 77 d0 55 a0 dc cc d9 c3 1f 68 40 5f 07 a4 18 8d cf cc dd 11 13 bd 59 79 c7 f7 2c f1 2e 97 f7 63 47 28 92 c1 91 04 91 6e db e9 44 2f d8 c5 4a be 00 04 fe 30 82 04 fa 30 82 03 e2 a0 03 02 01 02 02 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 d7 ab 97 ba 11 f9 01 e2 bc be 70 3c 7b 5a 46 8f ea 2a 40 2b d2 7b 36 1c 81 59 26 d7 d1 f5 7f c3 3a 40 04 83 d8 0c 8a 3f bc eb 16 bc a8 25 98 1c da 2e c7 33 0b 40 78 00 f1 7d cf f7 76 18 b2 f6 a4 a7 a9 22 16 ef 2c a4 20 0e 5b e3 5a 17 a0 f2 a1 5b f8 b4 33 12 c6 62 90 72 9a ea b2 c5 ba 23 7e c9 4e 9a 1f 52 57 48 3e ee de 76 62 6d 67 7f 0d d9 1e e8 92 02 fc 8d ae 4e 3c 01 5f b9 8a 4f 07 50 aa 0e 7e d1 bd 5c 3a 6b 86 23 63 8d 87 6f 4d ab 25 69 0b e8 7e 09 6d 7e 88 75 29 07 2b d3 ee de a0 bf f0 65 fd 9b 79 91 4e 0e 7b 74 0f 23 6f 20 37 2b 3b 0a d1 e9 ac ec 52 b3 75 41 ce a0 af 33 72 9d ae 3e 4a 63 22 e8 6b 44 a1 59 c6 df 35 79 0b 0b 6a 26 fc 94 28 a8 f3 23 e3 51 98 64 8b 7b 50 93 50 f3 dd 72 92 9a b5 f2 97 0f 5d d4 ef 27 15 75 f3 66 5b 69 b5 bd 94 76 8b 84 78 3f 02 03 01 00 01 a3 82 01 42 30 82 01 3e 30 1d 06 03 55 1d 0e 04 16 04 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 30 81 d3 06 03 55 1d 23 04 81 cb 30 81 c8 80 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 a1 81 99 a4 81 96 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 82 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0f 06 03 55 1d 13 01 01 ff 04 05 30 03 01 01 ff 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 6f 72 67 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 5a 51 d3 79 e5 b5 6b 81 6e 7a 7b d9 ea 45 4a 1a 68 62 30 c6 0c 53 f1 7c a7 0b 7f 71 6c 0c 0d a2 eb af ba ac f1 61 5d ac 12 1f 23 e4 b9 f8 3b 66 70 0c 2d bf 93 5a 16 e9 ad 93 6f b6 c6 08 f9 f1 2c bd 45 02 7e 08 89 e6 b5 9c 78 cc 47 f4 07 ea 36 e3 2b dd 38 ae 9a 5b f3 90 9b f6 8c 03 28 e3 be f6 77 fe c2 d9 87 31 b1 bd 09 45 68 32 b2 11 c8 65 74 12 1e 3f 2e 8d e7 56 02 b0 f5 eb 97 4f 3a 4d e2 6a 81 54 97 22 77 94 51 a9 47 d6 9b 5d c9 f7 b3 88 e2 19 74 d5 ed 35 18 b7 04 d9 51 a1 ed a7 30 1d 00 94 93 e3 fc 40 7e bb ae 92 4d f0 16 90 3a 69 ad c3 79 09 ec df 37 22 eb 1b 96 46 33 fc cd 6e ef d8 f9 4c cc e6 10 8c e3 e8 4b 1d 4d 6e 8a 25 7b 20 e0 ba bd c5 3c d8 b2 40 e9 ca 84 40 bd 97 7a 4d b8 11 81 41 64 a7 89 0a bb 48 d0 64 2a 83 d2 3a 90 1c 60 54 65 ff ee ea c2 41
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write client certificate
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 46
OpenSSL: TX ver=0x303 content_type=22 (handshake/client key exchange)
OpenSSL: Message - hexdump(len=70): 10 00 00 42 41 04 d3 c6 05 01 56 d9 2e 65 e8 0c 75 42 26 f8 9d 9e e6 58 72 36 0e af ea 5c bf 16 03 8c e6 c1 44 76 73 bf 27 85 02 02 ec 9d a3 f2 0b b2 17 de 82 a1 56 ea 3d c2 b0 83 67 ec 70 25 f2 3f 28 e2 d4 05
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write client key exchange
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 01 08
OpenSSL: TX ver=0x303 content_type=22 (handshake/certificate verify)
OpenSSL: Message - hexdump(len=264): 0f 00 01 04 08 04 01 00 7f 8e 74 99 cb 70 ee c1 f0 ff 85 a5 c9 8b bc b7 05 67 23 57 d0 ef 2b e2 2f 1e 97 29 ee ab 3c ac a5 f2 ab a3 db 42 21 3a 1b e0 12 00 a3 ef 85 bd 5d a9 96 ea f6 05 aa f6 d4 2c 77 39 91 bd e3 c8 a1 04 cd 3d 2d fc 06 bd 93 6e 20 62 fe 36 86 de 5f 00 87 41 d0 c1 7c 96 08 fd 6a ca 37 67 2e e7 68 4a 45 13 9b ec e1 f7 06 7a 49 ef 81 57 36 01 e4 bd a0 28 80 95 7a 35 ee fc bc 14 fd 1e 48 ff a6 fd 7c b9 31 6f 2b 1c 4e 45 55 ff d5 49 f9 9e 57 ad a2 4f 5b f3 67 e8 81 8b b7 7b a6 18 58 40 bf c9 21 d2 24 55 c9 89 13 b9 a3 04 c4 97 b2 26 03 84 20 c4 5d 6e 2d 1d ea b5 a6 2f ed 5c 5a 70 ba 6b 56 7d 49 8b d4 18 2c 2c af b0 fe 0e d3 c2 19 a9 2b 52 7e b2 dd 26 0c 63 52 a9 20 9f 78 22 e3 a9 45 b9 cd a0 2d 31 aa b8 74 ac 44 54 9b 01 11 5e 7f 73 66 d6 bb b8 46 54 b1 81 a1 76 4a dc
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write certificate verify
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 14 03 03 00 01
OpenSSL: TX ver=0x303 content_type=20 (change cipher spec/)
OpenSSL: Message - hexdump(len=1): 01
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write change cipher spec
OpenSSL: TX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 28
OpenSSL: TX ver=0x303 content_type=22 (handshake/finished)
OpenSSL: Message - hexdump(len=16): 14 00 00 0c 72 58 7f 2c a9 84 e1 36 75 92 67 aa
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write finished
SSL: (where=0x1002 ret=0xffffffff)
SSL: SSL_connect:error in SSLv3/TLS write finished
SSL: SSL_connect - want more data
SSL: 2670 bytes pending from ssl_out
SSL: Using TLS version TLSv1.2
SSL: 2670 bytes left to be sent out (of total 2670 bytes)
SSL: sending 1398 bytes, more fragments will follow
EAP: method process -> ignore=FALSE methodState=MAY_CONT decision=FAIL eapRespData=0x55f53f3cea60
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=1408)
TX EAP -> RADIUS - hexdump(len=1408): 02 af 05 80 0d c0 00 00 0a 6e 16 03 03 08 de 0b 00 08 da 00 08 d7 00 03 d3 30 82 03 cf 30 82 02 b7 a0 03 02 01 02 02 01 02 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 71 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 19 30 17 06 03 55 04 03 0c 10 75 73 65 72 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 1f 30 1d 06 09 2a 86 48 86 f7 0d 01 09 01 16 10 75 73 65 72 40 65 78 61 6d 70 6c 65 2e 6f 72 67 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 ac 64 f9 52 38 ec f6 6d 2e 16 5e 9e 5b 33 10 ca 9d b0 b8 2d c7 98 21 6e 76 49 c9 e7 73 48 82 90 a6 fd 40 85 2f 7a 6f a8 50 7f a8 8a 81 33 e1 b6 51 75 40 17 ea 49 bb 27 d3 f7 55 ee c4 47 0b 82 4e 29 3e 7d e0 b0 6e 6c aa 88 55 99 3e 21 a1 5e 22 35 22 01 71 2d 04 87 82 25 39 0a 26 d5 44 b2 8f eb 4d e3 29 46 a7 83 de e5 01 d5 81 e4 2c ed bf fe 7f 57 70 df 52 f0 64 77 e9 8f ff 30 43 19 8e 08 28 76 99 99 89 6f 8e a1 d4 e6 5e 34 6f 04 67 30 b9 b3 a1 94 53 3c 9f c6 e7 71 3e ad 2a 11 ff 38 33 24 35 3f 76 ee 91 cf da 03 51 56 3d 4a 12 7d 05 0c 73 8b 88 f4 d0 38 27 b3 e8 09 3c 8d ff 67 cc 2d 1f ce 02 c1 d8 34 62 2b 42 5a 33 19 ae cd 30 4a 89 54 74 6b b2 28 59 f7 65 7c 72 29 04 3d e1 fc 31 c8 c9 ad 8a 1c 10 17 4a 71 88 99 aa 44 28 f7 3d 18 d3 8f 9f 17 3e ca 71 56 bd 67 02 03 01 00 01 a3 4f 30 4d 30 13 06 03 55 1d 25 04 0c 30 0a 06 08 2b 06 01 05 05 07 03 02 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 63 6f 6d 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 7f 6a 16 6b 0b 48 1b c5 b6 2f 4f e2 49 42 fe 84 16 f4 46 c3 f5 dd ea 61 2b e4 e9 91 ed 8f 00 c3 15 bc 58 ba c2 9a da 2b d6 c9 2f c1 a9 10 b3 fb 15 10 0c 2b 8f 3f 82 67 73 05 f2 69 45 46 26 8c a9 76 6c 07 67 af 42 a1 7d a8 5b 4a 1c c5 59 33 8e 7d c8 d4 e5 4b 93 7a 31 cf aa be 2e 9c 65 29 73 c7 02 3b b7 c1 49 a2 f5 54 ca 73 de b0 12 b4 55 03 44 34 aa cb 81 0e 11 4f a0 13 a7 d8 63 f3 3d 70 86 48 e7 88 ee 56 5c eb 83 04 c4 77 a7 e7 8d da 95 a6 1c b4 86 0c 48 51 b1 8a c6 b8 52 44 b8 3b 55 59 78 60 e9 94 42 c7 a1 28 4b 1d c7 95 fc 0e 5a 3f 63 56 2b 4c 9a 0e c6 2d 41 61 ad 1c e5 86 3b f3 71 14 1f e9 03 82 c6 41 3d 9d f7 88 77 d0 55 a0 dc cc d9 c3 1f 68 40 5f 07 a4 18 8d cf cc dd 11 13 bd 59 79 c7 f7 2c f1 2e 97 f7 63 47 28 92 c1 91 04 91 6e db e9 44 2f d8 c5 4a be 00 04 fe 30 82 04 fa 30 82 03 e2 a0 03 02 01 02 02 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 1e 17 0d 32 34 30 32 32 31 30 32 35 35 32 35 5a 17 0d 32 34 30 34 32 31 30 32 35 35 32 35 5a 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 30 82 01 22 30 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=11 length=1552Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=255Value: 02af05800dc000000a6e16030308de0b0008da0008d70003d3308203cf308202b7a003020102020102300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a3071310b3009060355040613024652Attribute 79 (EAP-Message) length=255Value: 310f300d06035504080c0652616469757331153013060355040a0c0c4578616d706c6520496e632e3119301706035504030c1075736572406578616d706c652e6f7267311f301d06092a864886f70d010901161075736572406578616d706c652e6f726730820122300d06092a864886f70d01010105000382010f003082010a0282010100ac64f95238ecf66d2e165e9e5b3310ca9db0b82dc798216e7649c9e773488290a6fd40852f7a6fa8507fa88a8133e1b651754017ea49bb27d3f755eec4470b824e293e7de0b06e6caa8855993e21a15e22352201712d04878225390a26d544b28feb4de32946a783dee501d581e42cedbffe7f5770df52f0Attribute 79 (EAP-Message) length=255Value: 6477e98fff3043198e0828769999896f8ea1d4e65e346f046730b9b3a194533c9fc6e7713ead2a11ff383324353f76ee91cfda0351563d4a127d050c738b88f4d03827b3e8093c8dff67cc2d1fce02c1d834622b425a3319aecd304a8954746bb22859f7657c7229043de1fc31c8c9ad8a1c10174a718899aa4428f73d18d38f9f173eca7156bd670203010001a34f304d30130603551d25040c300a06082b0601050507030230360603551d1f042f302d302ba029a0278625687474703a2f2f7777772e6578616d706c652e636f6d2f6578616d706c655f63612e63726c300d06092a864886f70d01010b050003820101007f6a166b0b481bc5b62f4fAttribute 79 (EAP-Message) length=255Value: e24942fe8416f446c3f5ddea612be4e991ed8f00c315bc58bac29ada2bd6c92fc1a910b3fb15100c2b8f3f82677305f2694546268ca9766c0767af42a17da85b4a1cc559338e7dc8d4e54b937a31cfaabe2e9c652973c7023bb7c149a2f554ca73deb012b455034434aacb810e114fa013a7d863f33d708648e788ee565ceb8304c477a7e78dda95a61cb4860c4851b18ac6b85244b83b55597860e99442c7a1284b1dc795fc0e5a3f63562b4c9a0ec62d4161ad1ce5863bf371141fe90382c6413d9df78877d055a0dcccd9c31f68405f07a4188dcfccdd1113bd5979c7f72cf12e97f763472892c19104916edbe9442fd8c54abe0004fe308204fa30Attribute 79 (EAP-Message) length=255Value: 8203e2a00302010202144a1dec91e0857d76d65f37d6ddaab4191176ebcb300d06092a864886f70d01010b0500308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f72697479301e170d3234303232313032353532355a170d3234303432313032353532355a308193310b3009060355040613024652310f300d06035504080cAttribute 79 (EAP-Message) length=145Value: 065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574686f7269747930820122300d06092a864886f70d0101010500Attribute 24 (State) length=18Value: fb1c2c65f8b3217da229744af77aa30fAttribute 80 (Message-Authenticator) length=18Value: 1fd16a3aa49b0dc01535f283156a1807
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 64 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=11 length=64Attribute 79 (EAP-Message) length=8Value: 01b000060d00Attribute 80 (Message-Authenticator) length=18Value: 8a8e30c8f095efd8ffcb79f3a92d7d73Attribute 24 (State) length=18Value: fb1c2c65ffac217da229744af77aa30f
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=176 len=6) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=176 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state METHOD
SSL: Received packet(len=6) - Flags 0x00
SSL: 1272 bytes left to be sent out (of total 2670 bytes)
EAP: method process -> ignore=FALSE methodState=MAY_CONT decision=FAIL eapRespData=0x55f53f3cdf60
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=1278)
TX EAP -> RADIUS - hexdump(len=1278): 02 b0 04 fe 0d 00 03 82 01 0f 00 30 82 01 0a 02 82 01 01 00 d7 ab 97 ba 11 f9 01 e2 bc be 70 3c 7b 5a 46 8f ea 2a 40 2b d2 7b 36 1c 81 59 26 d7 d1 f5 7f c3 3a 40 04 83 d8 0c 8a 3f bc eb 16 bc a8 25 98 1c da 2e c7 33 0b 40 78 00 f1 7d cf f7 76 18 b2 f6 a4 a7 a9 22 16 ef 2c a4 20 0e 5b e3 5a 17 a0 f2 a1 5b f8 b4 33 12 c6 62 90 72 9a ea b2 c5 ba 23 7e c9 4e 9a 1f 52 57 48 3e ee de 76 62 6d 67 7f 0d d9 1e e8 92 02 fc 8d ae 4e 3c 01 5f b9 8a 4f 07 50 aa 0e 7e d1 bd 5c 3a 6b 86 23 63 8d 87 6f 4d ab 25 69 0b e8 7e 09 6d 7e 88 75 29 07 2b d3 ee de a0 bf f0 65 fd 9b 79 91 4e 0e 7b 74 0f 23 6f 20 37 2b 3b 0a d1 e9 ac ec 52 b3 75 41 ce a0 af 33 72 9d ae 3e 4a 63 22 e8 6b 44 a1 59 c6 df 35 79 0b 0b 6a 26 fc 94 28 a8 f3 23 e3 51 98 64 8b 7b 50 93 50 f3 dd 72 92 9a b5 f2 97 0f 5d d4 ef 27 15 75 f3 66 5b 69 b5 bd 94 76 8b 84 78 3f 02 03 01 00 01 a3 82 01 42 30 82 01 3e 30 1d 06 03 55 1d 0e 04 16 04 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 30 81 d3 06 03 55 1d 23 04 81 cb 30 81 c8 80 14 01 57 1d 77 9e 50 f5 b5 91 d6 da d4 96 f8 9a c3 bc 91 cf 27 a1 81 99 a4 81 96 30 81 93 31 0b 30 09 06 03 55 04 06 13 02 46 52 31 0f 30 0d 06 03 55 04 08 0c 06 52 61 64 69 75 73 31 12 30 10 06 03 55 04 07 0c 09 53 6f 6d 65 77 68 65 72 65 31 15 30 13 06 03 55 04 0a 0c 0c 45 78 61 6d 70 6c 65 20 49 6e 63 2e 31 20 30 1e 06 09 2a 86 48 86 f7 0d 01 09 01 16 11 61 64 6d 69 6e 40 65 78 61 6d 70 6c 65 2e 6f 72 67 31 26 30 24 06 03 55 04 03 0c 1d 45 78 61 6d 70 6c 65 20 43 65 72 74 69 66 69 63 61 74 65 20 41 75 74 68 6f 72 69 74 79 82 14 4a 1d ec 91 e0 85 7d 76 d6 5f 37 d6 dd aa b4 19 11 76 eb cb 30 0f 06 03 55 1d 13 01 01 ff 04 05 30 03 01 01 ff 30 36 06 03 55 1d 1f 04 2f 30 2d 30 2b a0 29 a0 27 86 25 68 74 74 70 3a 2f 2f 77 77 77 2e 65 78 61 6d 70 6c 65 2e 6f 72 67 2f 65 78 61 6d 70 6c 65 5f 63 61 2e 63 72 6c 30 0d 06 09 2a 86 48 86 f7 0d 01 01 0b 05 00 03 82 01 01 00 5a 51 d3 79 e5 b5 6b 81 6e 7a 7b d9 ea 45 4a 1a 68 62 30 c6 0c 53 f1 7c a7 0b 7f 71 6c 0c 0d a2 eb af ba ac f1 61 5d ac 12 1f 23 e4 b9 f8 3b 66 70 0c 2d bf 93 5a 16 e9 ad 93 6f b6 c6 08 f9 f1 2c bd 45 02 7e 08 89 e6 b5 9c 78 cc 47 f4 07 ea 36 e3 2b dd 38 ae 9a 5b f3 90 9b f6 8c 03 28 e3 be f6 77 fe c2 d9 87 31 b1 bd 09 45 68 32 b2 11 c8 65 74 12 1e 3f 2e 8d e7 56 02 b0 f5 eb 97 4f 3a 4d e2 6a 81 54 97 22 77 94 51 a9 47 d6 9b 5d c9 f7 b3 88 e2 19 74 d5 ed 35 18 b7 04 d9 51 a1 ed a7 30 1d 00 94 93 e3 fc 40 7e bb ae 92 4d f0 16 90 3a 69 ad c3 79 09 ec df 37 22 eb 1b 96 46 33 fc cd 6e ef d8 f9 4c cc e6 10 8c e3 e8 4b 1d 4d 6e 8a 25 7b 20 e0 ba bd c5 3c d8 b2 40 e9 ca 84 40 bd 97 7a 4d b8 11 81 41 64 a7 89 0a bb 48 d0 64 2a 83 d2 3a 90 1c 60 54 65 ff ee ea c2 41 16 03 03 00 46 10 00 00 42 41 04 d3 c6 05 01 56 d9 2e 65 e8 0c 75 42 26 f8 9d 9e e6 58 72 36 0e af ea 5c bf 16 03 8c e6 c1 44 76 73 bf 27 85 02 02 ec 9d a3 f2 0b b2 17 de 82 a1 56 ea 3d c2 b0 83 67 ec 70 25 f2 3f 28 e2 d4 05 16 03 03 01 08 0f 00 01 04 08 04 01 00 7f 8e 74 99 cb 70 ee c1 f0 ff 85 a5 c9 8b bc b7 05 67 23 57 d0 ef 2b e2 2f 1e 97 29 ee ab 3c ac a5 f2 ab a3 db 42 21 3a 1b e0 12 00 a3 ef 85 bd 5d a9 96 ea f6 05 aa f6 d4 2c 77 39 91 bd e3 c8 a1 04 cd 3d 2d fc 06 bd 93 6e 20 62 fe 36 86 de 5f 00 87 41 d0 c1 7c 96 08 fd 6a ca 37 67 2e e7 68 4a 45 13 9b ec e1 f7 06 7a 49 ef 81 57 36 01 e4 bd a0 28 80 95 7a 35 ee fc bc 14 fd 1e 48 ff a6 fd 7c b9 31 6f 2b 1c 4e 45 55 ff d5 49 f9 9e 57 ad a2 4f 5b f3 67 e8 81 8b b7 7b a6 18 58 40 bf c9 21 d2 24 55 c9 89 13 b9 a3 04 c4 97 b2 26 03 84 20 c4 5d 6e 2d 1d ea b5 a6 2f ed 5c 5a 70 ba 6b 56 7d 49 8b d4 18 2c 2c af b0 fe 0e d3 c2 19 a9 2b 52 7e b2 dd 26 0c 63 52 a9 20 9f 78 22 e3 a9 45 b9 cd a0 2d 31 aa b8 74 ac 44 54 9b 01 11 5e 7f 73 66 d6 bb b8 46 54 b1 81 a1 76 4a dc 14 03 03 00 01 01 16 03 03 00 28 34 5e 20 a3 cc bc c2 fb ba a7 3c 44 c3 a7 6b 58 0a 45 45 78 ff 9d c4 69 5e 33 f1 99 4f 07 e9 24 47 f2 4d ca db 0b ca ab
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=12 length=1422Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=255Value: 02b004fe0d000382010f003082010a0282010100d7ab97ba11f901e2bcbe703c7b5a468fea2a402bd27b361c815926d7d1f57fc33a400483d80c8a3fbceb16bca825981cda2ec7330b407800f17dcff77618b2f6a4a7a92216ef2ca4200e5be35a17a0f2a15bf8b43312c66290729aeab2c5ba237ec94e9a1f5257483eeede76626d677f0dd91ee89202fc8dae4e3c015fb98a4f0750aa0e7ed1bd5c3a6b8623638d876f4dab25690be87e096d7e887529072bd3eedea0bff065fd9b79914e0e7b740f236f20372b3b0ad1e9acec52b37541cea0af33729dae3e4a6322e86b44a159c6df35790b0b6a26fc9428a8f323e35198648b7b509350f3dd7292Attribute 79 (EAP-Message) length=255Value: 9ab5f2970f5dd4ef271575f3665b69b5bd94768b84783f0203010001a38201423082013e301d0603551d0e0416041401571d779e50f5b591d6dad496f89ac3bc91cf273081d30603551d230481cb3081c8801401571d779e50f5b591d6dad496f89ac3bc91cf27a18199a48196308193310b3009060355040613024652310f300d06035504080c065261646975733112301006035504070c09536f6d65776865726531153013060355040a0c0c4578616d706c6520496e632e3120301e06092a864886f70d010901161161646d696e406578616d706c652e6f72673126302406035504030c1d4578616d706c6520436572746966696361746520417574Attribute 79 (EAP-Message) length=255Value: 686f7269747982144a1dec91e0857d76d65f37d6ddaab4191176ebcb300f0603551d130101ff040530030101ff30360603551d1f042f302d302ba029a0278625687474703a2f2f7777772e6578616d706c652e6f72672f6578616d706c655f63612e63726c300d06092a864886f70d01010b050003820101005a51d379e5b56b816e7a7bd9ea454a1a686230c60c53f17ca70b7f716c0c0da2ebafbaacf1615dac121f23e4b9f83b66700c2dbf935a16e9ad936fb6c608f9f12cbd45027e0889e6b59c78cc47f407ea36e32bdd38ae9a5bf3909bf68c0328e3bef677fec2d98731b1bd09456832b211c86574121e3f2e8de75602b0f5eb974f3a4de26aAttribute 79 (EAP-Message) length=255Value: 81549722779451a947d69b5dc9f7b388e21974d5ed3518b704d951a1eda7301d009493e3fc407ebbae924df016903a69adc37909ecdf3722eb1b964633fccd6eefd8f94ccce6108ce3e84b1d4d6e8a257b20e0babdc53cd8b240e9ca8440bd977a4db811814164a7890abb48d0642a83d23a901c605465ffeeeac2411603030046100000424104d3c6050156d92e65e80c754226f89d9ee65872360eafea5cbf16038ce6c1447673bf27850202ec9da3f20bb217de82a156ea3dc2b08367ec7025f23f28e2d40516030301080f000104080401007f8e7499cb70eec1f0ff85a5c98bbcb705672357d0ef2be22f1e9729eeab3caca5f2aba3db42213a1bAttribute 79 (EAP-Message) length=255Value: e01200a3ef85bd5da996eaf605aaf6d42c773991bde3c8a104cd3d2dfc06bd936e2062fe3686de5f008741d0c17c9608fd6aca37672ee7684a45139bece1f7067a49ef81573601e4bda02880957a35eefcbc14fd1e48ffa6fd7cb9316f2b1c4e4555ffd549f99e57ada24f5bf367e8818bb77ba6185840bfc921d22455c98913b9a304c497b226038420c45d6e2d1deab5a62fed5c5a70ba6b567d498bd4182c2cafb0fe0ed3c219a92b527eb2dd260c6352a9209f7822e3a945b9cda02d31aab874ac44549b01115e7f7366d6bbb84654b181a1764adc1403030001011603030028345e20a3ccbcc2fbbaa73c44c3a76b580a454578ff9dc4695e33f1Attribute 79 (EAP-Message) length=15Value: 994f07e92447f24dcadb0bcaabAttribute 24 (State) length=18Value: fb1c2c65ffac217da229744af77aa30fAttribute 80 (Message-Authenticator) length=18Value: 0d1f87fc26c15c46ab2a694795fef902
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 119 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=11 (Access-Challenge) identifier=12 length=119Attribute 79 (EAP-Message) length=63Value: 01b1003d0d80000000331403030001011603030028e6d41ca2aa87391a58eb70f47b2cb52c809102c061d01056c64fafec1b7192f45a219dafde4a6548Attribute 80 (Message-Authenticator) length=18Value: 290e515e767eab6b8dc661941ce01e8eAttribute 24 (State) length=18Value: fb1c2c65fead217da229744af77aa30f
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
decapsulated EAP packet (code=1 id=177 len=61) from RADIUS server: EAP-Request-TLS (13)
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Request id=177 method=13 vendor=0 vendorMethod=0
EAP: EAP entering state METHOD
SSL: Received packet(len=61) - Flags 0x80
SSL: TLS Message Length: 51
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 14 03 03 00 01
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS write finished
OpenSSL: RX ver=0x0 content_type=256 (TLS header info/)
OpenSSL: Message - hexdump(len=5): 16 03 03 00 28
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read change cipher spec
OpenSSL: RX ver=0x303 content_type=22 (handshake/finished)
OpenSSL: Message - hexdump(len=16): 14 00 00 0c d0 09 7f eb 1f 0a d4 29 4e 90 0a 2b
SSL: (where=0x1001 ret=0x1)
SSL: SSL_connect:SSLv3/TLS read finished
SSL: (where=0x20 ret=0x1)
SSL: (where=0x1002 ret=0x1)
SSL: 0 bytes pending from ssl_out
OpenSSL: Handshake finished - resumed=0
SSL: No Application Data included
SSL: Using TLS version TLSv1.2
SSL: No data to be sent out
EAP-TLS: Done
EAP-TLS: Derived key - hexdump(len=64): d7 bc dd f7 af 62 24 b5 0c 99 2f 45 d5 4c 1c 13 2d f2 58 c9 25 df dd df 8a 02 7f c1 84 b1 52 04 4f d8 b5 58 db 5e 32 60 84 7f ef f0 53 52 7c b4 11 7d 5a 69 7c 28 f3 ae dd 81 86 14 74 2b a5 ee
EAP-TLS: Derived EMSK - hexdump(len=64): 50 26 34 0e ca fb ae 09 62 bb 75 dd 0c dd 9e 88 7e e0 bf a4 c0 29 43 ea 23 77 a3 be 2d 57 30 ab 4f 92 c1 4a 53 95 20 3d da d8 34 2b ae b4 3c bd 07 54 91 db 34 83 83 40 bd 83 cb f9 af 33 09 4e
EAP-TLS: Derived Session-Id - hexdump(len=65): 0d 9d af b8 19 1c 05 97 0d 0f c3 a0 a6 6a 19 b3 3e 51 6c bd 83 0a 9c f0 d7 df 32 43 90 c3 af 4a 30 42 92 63 8f 38 37 c7 53 52 d2 8e 65 b5 fe 48 f8 30 b1 9c 08 57 47 f1 76 37 4c 90 14 f0 c9 f3 1e
SSL: Building ACK (type=13 id=177 ver=0)
EAP: method process -> ignore=FALSE methodState=DONE decision=UNCOND_SUCC eapRespData=0x55f53f3acc90
EAP: Session-Id - hexdump(len=65): 0d 9d af b8 19 1c 05 97 0d 0f c3 a0 a6 6a 19 b3 3e 51 6c bd 83 0a 9c f0 d7 df 32 43 90 c3 af 4a 30 42 92 63 8f 38 37 c7 53 52 d2 8e 65 b5 fe 48 f8 30 b1 9c 08 57 47 f1 76 37 4c 90 14 f0 c9 f3 1e
EAP: EAP entering state SEND_RESPONSE
EAP: EAP entering state IDLE
EAPOL: SUPP_BE entering state RESPONSE
EAPOL: txSuppRsp
WPA: eapol_test_eapol_send(type=0 len=6)
TX EAP -> RADIUS - hexdump(len=6): 02 b1 00 06 0d 00
Encapsulating EAP message into a RADIUS packetCopied RADIUS State Attribute
Sending RADIUS message to authentication server
RADIUS message: code=1 (Access-Request) identifier=13 length=140Attribute 1 (User-Name) length=9Value: 'testing'Attribute 4 (NAS-IP-Address) length=6Value: 127.0.0.1Attribute 31 (Calling-Station-Id) length=19Value: '02-00-00-00-00-01'Attribute 12 (Framed-MTU) length=6Value: 1400Attribute 61 (NAS-Port-Type) length=6Value: 19Attribute 6 (Service-Type) length=6Value: 2Attribute 77 (Connect-Info) length=24Value: 'CONNECT 11Mbps 802.11b'Attribute 79 (EAP-Message) length=8Value: 02b100060d00Attribute 24 (State) length=18Value: fb1c2c65fead217da229744af77aa30fAttribute 80 (Message-Authenticator) length=18Value: 3ae623aad6afd92f4daf0f414aec7d4d
Next RADIUS client retransmit in 3 seconds
EAPOL: SUPP_BE entering state RECEIVE
Received 169 bytes from RADIUS server
Received RADIUS message
RADIUS message: code=2 (Access-Accept) identifier=13 length=169Attribute 26 (Vendor-Specific) length=58Value: 00000137113493a6bc8b49385baac19dd71c87926effe39f2b79770d388c7a98d56ff1d30b6451841cdea8a813dad700fd65e04ce4faff21Attribute 26 (Vendor-Specific) length=58Value: 000001371034983503d65166fc293e11efd6aaa063c72eb73400afe46d4de6aa23152c97784a560749072aec27a6b540be3d4a7f7c1ed47cAttribute 79 (EAP-Message) length=6Value: 03b10004Attribute 80 (Message-Authenticator) length=18Value: 3e6c4a927c53298e7dec4ea27d972819Attribute 1 (User-Name) length=9Value: 'testing'
STA 02:00:00:00:00:01: Received RADIUS packet matched with a pending request, round trip time 0.00 secRADIUS packet matching with station
MS-MPPE-Send-Key (sign) - hexdump(len=32): 4f d8 b5 58 db 5e 32 60 84 7f ef f0 53 52 7c b4 11 7d 5a 69 7c 28 f3 ae dd 81 86 14 74 2b a5 ee
MS-MPPE-Recv-Key (crypt) - hexdump(len=32): d7 bc dd f7 af 62 24 b5 0c 99 2f 45 d5 4c 1c 13 2d f2 58 c9 25 df dd df 8a 02 7f c1 84 b1 52 04
decapsulated EAP packet (code=3 id=177 len=4) from RADIUS server: EAP Success
EAPOL: Received EAP-Packet frame
EAPOL: SUPP_BE entering state REQUEST
EAPOL: getSuppRsp
EAP: EAP entering state RECEIVED
EAP: Received EAP-Success
EAP: Status notification: completion (param=success)
EAP: EAP entering state SUCCESS
CTRL-EVENT-EAP-SUCCESS EAP authentication completed successfully
EAPOL: SUPP_PAE entering state AUTHENTICATED
EAPOL: SUPP_BE entering state RECEIVE
EAPOL: SUPP_BE entering state SUCCESS
EAPOL: SUPP_BE entering state IDLE
eapol_sm_cb: result=1
EAPOL: Successfully fetched key (len=32)
PMK from EAPOL - hexdump(len=32): d7 bc dd f7 af 62 24 b5 0c 99 2f 45 d5 4c 1c 13 2d f2 58 c9 25 df dd df 8a 02 7f c1 84 b1 52 04
No EAP-Key-Name received from server
WPA: Clear old PMK and PTK
EAP: deinitialize previously used EAP method (13, TLS) at EAP deinit
ENGINE: engine deinit
MPPE keys OK: 2 mismatch: 0
SUCCESS
看到最后的SUCCESS,说明证书认证成功。
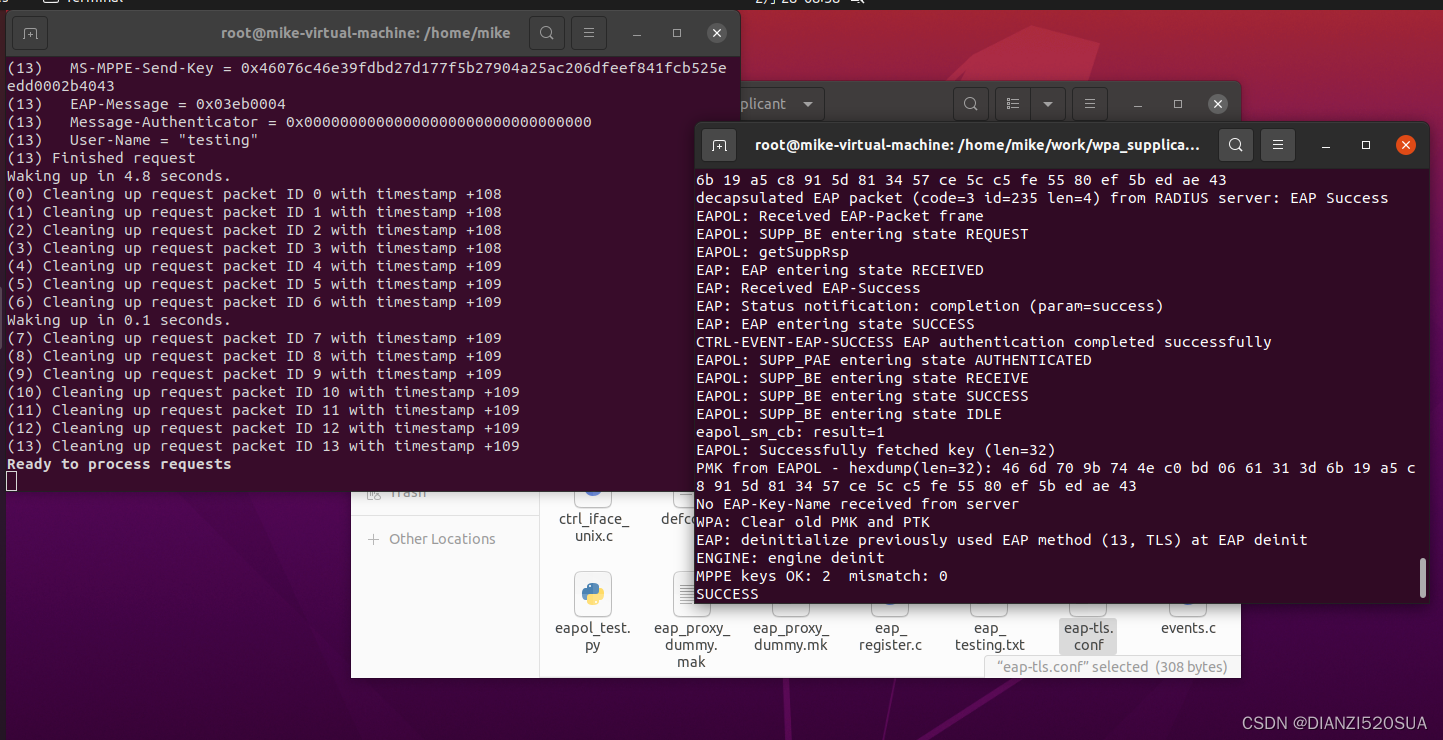
至此,本地eap-tls认证实验结束。
下篇我们可能会看到一款NAS设备的配置相关内容,敬请期待。