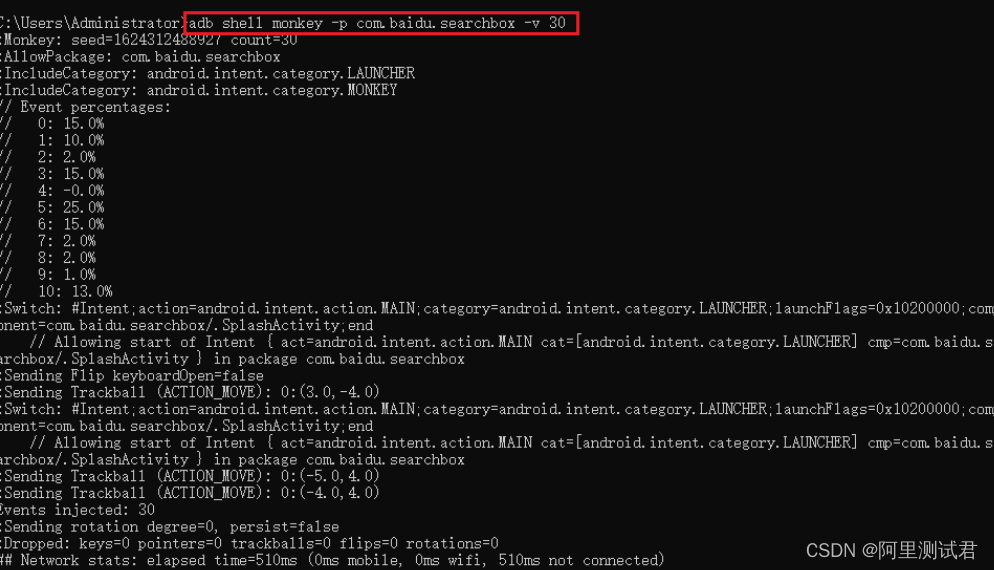
03驱动断链
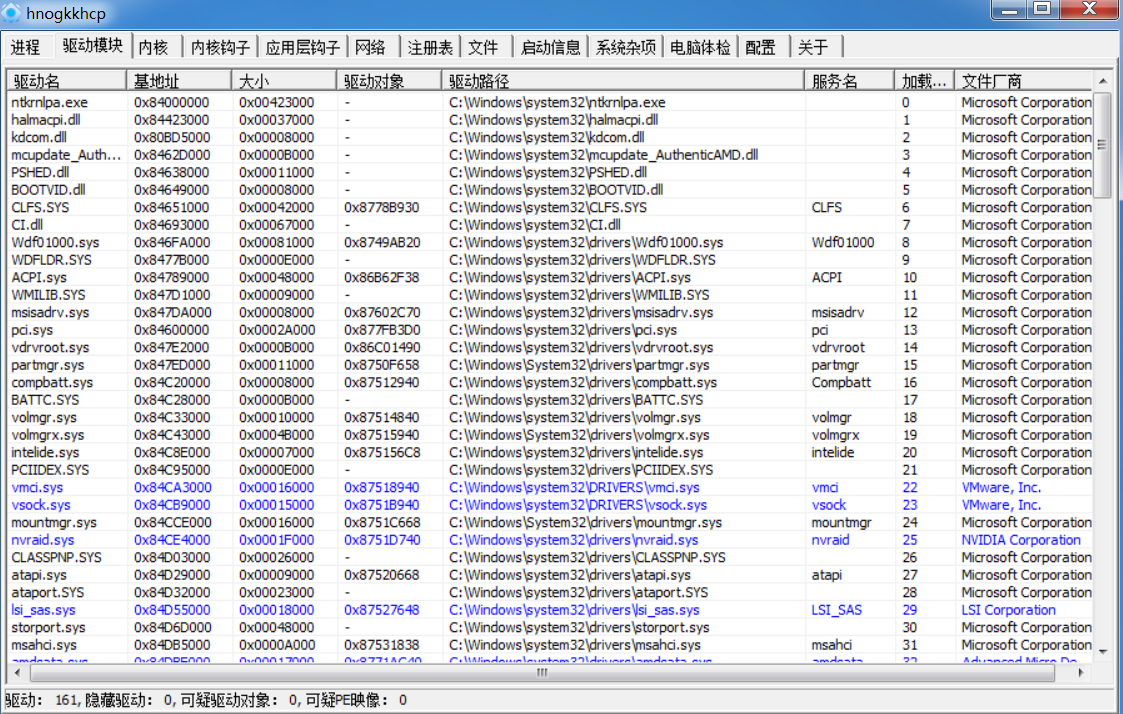
获取驱动信息的途径是从Driver和FileSystem两个目录下获得的
正常情况下我们自己做驱动遍历只能便利Driver下的所有驱动,也就是驱动链表里的驱动
分析
这里我们F12进去找一下DRIVER_OBJECT的结构
typedef struct _DRIVER_OBJECT *PDRIVER_OBJECT;
WinDbg里dt一下
kd> dt _DRIVER_OBJECT
ntdll!_DRIVER_OBJECT+0x000 Type : Int2B+0x002 Size : Int2B+0x004 DeviceObject : Ptr32 _DEVICE_OBJECT+0x008 Flags : Uint4B+0x00c DriverStart : Ptr32 Void+0x010 DriverSize : Uint4B+0x014 DriverSection : Ptr32 Void+0x018 DriverExtension : Ptr32 _DRIVER_EXTENSION+0x01c DriverName : _UNICODE_STRING+0x024 HardwareDatabase : Ptr32 _UNICODE_STRING+0x028 FastIoDispatch : Ptr32 _FAST_IO_DISPATCH+0x02c DriverInit : Ptr32 long +0x030 DriverStartIo : Ptr32 void +0x034 DriverUnload : Ptr32 void +0x038 MajorFunction : [28] Ptr32 long
其中DriverSection里面存放了一个类似于R3的PEB的链表
+0x014 DriverSection : Ptr32 Void
PEB
kd> dt _PEB
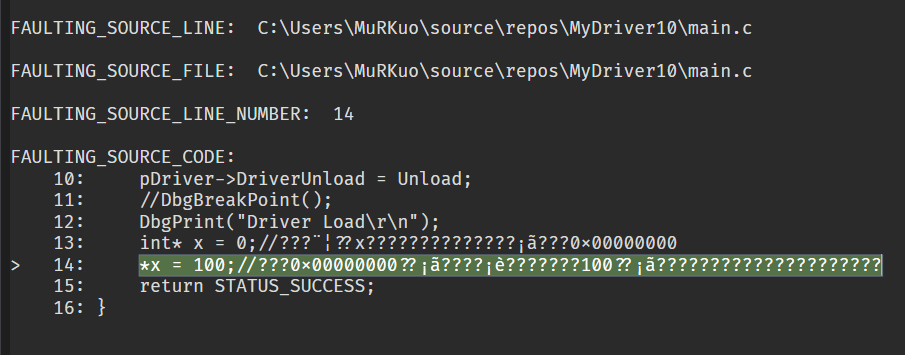
ntdll!_PEB+0x000 InheritedAddressSpace : UChar+0x001 ReadImageFileExecOptions : UChar+0x002 BeingDebugged : UChar+0x003 BitField : UChar+0x003 ImageUsesLargePages : Pos 0, 1 Bit+0x003 IsProtectedProcess : Pos 1, 1 Bit+0x003 IsLegacyProcess : Pos 2, 1 Bit+0x003 IsImageDynamicallyRelocated : Pos 3, 1 Bit+0x003 SkipPatchingUser32Forwarders : Pos 4, 1 Bit+0x003 SpareBits : Pos 5, 3 Bits+0x004 Mutant : Ptr32 Void+0x008 ImageBaseAddress : Ptr32 Void+0x00c Ldr : Ptr32 _PEB_LDR_DATA+0x010 ProcessParameters : Ptr32 _RTL_USER_PROCESS_PARAMETERS+0x014 SubSystemData : Ptr32 Void+0x018 ProcessHeap : Ptr32 Void+0x01c FastPebLock : Ptr32 _RTL_CRITICAL_SECTION+0x020 AtlThunkSListPtr : Ptr32 Void+0x024 IFEOKey : Ptr32 Void+0x028 CrossProcessFlags : Uint4B+0x028 ProcessInJob : Pos 0, 1 Bit+0x028 ProcessInitializing : Pos 1, 1 Bit+0x028 ProcessUsingVEH : Pos 2, 1 Bit+0x028 ProcessUsingVCH : Pos 3, 1 Bit+0x028 ProcessUsingFTH : Pos 4, 1 Bit+0x028 ReservedBits0 : Pos 5, 27 Bits+0x02c KernelCallbackTable : Ptr32 Void+0x02c UserSharedInfoPtr : Ptr32 Void+0x030 SystemReserved : [1] Uint4B+0x034 AtlThunkSListPtr32 : Uint4B+0x038 ApiSetMap : Ptr32 Void+0x03c TlsExpansionCounter : Uint4B+0x040 TlsBitmap : Ptr32 Void+0x044 TlsBitmapBits : [2] Uint4B+0x04c ReadOnlySharedMemoryBase : Ptr32 Void+0x050 HotpatchInformation : Ptr32 Void+0x054 ReadOnlyStaticServerData : Ptr32 Ptr32 Void+0x058 AnsiCodePageData : Ptr32 Void+0x05c OemCodePageData : Ptr32 Void+0x060 UnicodeCaseTableData : Ptr32 Void+0x064 NumberOfProcessors : Uint4B+0x068 NtGlobalFlag : Uint4B+0x070 CriticalSectionTimeout : _LARGE_INTEGER+0x078 HeapSegmentReserve : Uint4B+0x07c HeapSegmentCommit : Uint4B+0x080 HeapDeCommitTotalFreeThreshold : Uint4B+0x084 HeapDeCommitFreeBlockThreshold : Uint4B+0x088 NumberOfHeaps : Uint4B+0x08c MaximumNumberOfHeaps : Uint4B+0x090 ProcessHeaps : Ptr32 Ptr32 Void+0x094 GdiSharedHandleTable : Ptr32 Void+0x098 ProcessStarterHelper : Ptr32 Void+0x09c GdiDCAttributeList : Uint4B+0x0a0 LoaderLock : Ptr32 _RTL_CRITICAL_SECTION+0x0a4 OSMajorVersion : Uint4B+0x0a8 OSMinorVersion : Uint4B+0x0ac OSBuildNumber : Uint2B+0x0ae OSCSDVersion : Uint2B+0x0b0 OSPlatformId : Uint4B+0x0b4 ImageSubsystem : Uint4B+0x0b8 ImageSubsystemMajorVersion : Uint4B+0x0bc ImageSubsystemMinorVersion : Uint4B+0x0c0 ActiveProcessAffinityMask : Uint4B+0x0c4 GdiHandleBuffer : [34] Uint4B+0x14c PostProcessInitRoutine : Ptr32 void +0x150 TlsExpansionBitmap : Ptr32 Void+0x154 TlsExpansionBitmapBits : [32] Uint4B+0x1d4 SessionId : Uint4B+0x1d8 AppCompatFlags : _ULARGE_INTEGER+0x1e0 AppCompatFlagsUser : _ULARGE_INTEGER+0x1e8 pShimData : Ptr32 Void+0x1ec AppCompatInfo : Ptr32 Void+0x1f0 CSDVersion : _UNICODE_STRING+0x1f8 ActivationContextData : Ptr32 _ACTIVATION_CONTEXT_DATA+0x1fc ProcessAssemblyStorageMap : Ptr32 _ASSEMBLY_STORAGE_MAP+0x200 SystemDefaultActivationContextData : Ptr32 _ACTIVATION_CONTEXT_DATA+0x204 SystemAssemblyStorageMap : Ptr32 _ASSEMBLY_STORAGE_MAP+0x208 MinimumStackCommit : Uint4B+0x20c FlsCallback : Ptr32 _FLS_CALLBACK_INFO+0x210 FlsListHead : _LIST_ENTRY+0x218 FlsBitmap : Ptr32 Void+0x21c FlsBitmapBits : [4] Uint4B+0x22c FlsHighIndex : Uint4B+0x230 WerRegistrationData : Ptr32 Void+0x234 WerShipAssertPtr : Ptr32 Void+0x238 pContextData : Ptr32 Void+0x23c pImageHeaderHash : Ptr32 Void+0x240 TracingFlags : Uint4B+0x240 HeapTracingEnabled : Pos 0, 1 Bit+0x240 CritSecTracingEnabled : Pos 1, 1 Bit+0x240 SpareTracingBits : Pos 2, 30 Bits
其中 +0x00c Ldr:Ptr32 _PEB_LDR_DATA中存放了一个_PEB_LDR_DATA
kd> dt _PEB_LDR_DATA
ntdll!_PEB_LDR_DATA+0x000 Length : Uint4B+0x004 Initialized : UChar+0x008 SsHandle : Ptr32 Void+0x00c InLoadOrderModuleList : _LIST_ENTRY+0x014 InMemoryOrderModuleList : _LIST_ENTRY+0x01c InInitializationOrderModuleList : _LIST_ENTRY+0x024 EntryInProgress : Ptr32 Void+0x028 ShutdownInProgress : UChar+0x02c ShutdownThreadId : Ptr32 Void
其中就就有模块链表
+0x00c InLoadOrderModuleList : _LIST_ENTRY+0x014 InMemoryOrderModuleList : _LIST_ENTRY+0x01c InInitializationOrderModuleList : _LIST_ENTRY
_KLDR_DATA_TABLE_ENTRY
这里我们使用R0的_KLDR_DATA_TABLE_ENTRY结构体
这里我使用WRK搜索拿到这个结构体的
这个是32位的
typedef struct _KLDR_DATA_TABLE_ENTRY {LIST_ENTRY InLoadOrderLinks;ULONG __Undefined1;ULONG __Undefined2;ULONG __Undefined3;ULONG NonPagedDebugInfo;ULONG DllBase;ULONG EntryPoint;ULONG SizeOfImage;UNICODE_STRING FullDllName;UNICODE_STRING BaseDllName;ULONG Flags;USHORT LoadCount;USHORT __Undefined5;ULONG __Undefined6;ULONG CheckSum;ULONG TimeDateStamp;
} KLDR_DATA_TABLE_ENTRY, * PKLDR_DATA_TABLE_ENTRY;
查看当前驱动的_KLDR_DATA_TABLE_ENTRY结构
#include <ntifs.h>VOID Unload(PDRIVER_OBJECT pDriver)
{DbgPrint("unload\r\n");
}
//定义未公开结构体
typedef struct _KLDR_DATA_TABLE_ENTRY {LIST_ENTRY InLoadOrderLinks;ULONG __Undefined1;ULONG __Undefined2;ULONG __Undefined3;ULONG NonPagedDebugInfo;ULONG DllBase;ULONG EntryPoint;ULONG SizeOfImage;UNICODE_STRING FullDllName;UNICODE_STRING BaseDllName;ULONG Flags;USHORT LoadCount;USHORT __Undefined5;ULONG __Undefined6;ULONG CheckSum;ULONG TimeDateStamp;
} KLDR_DATA_