影响:
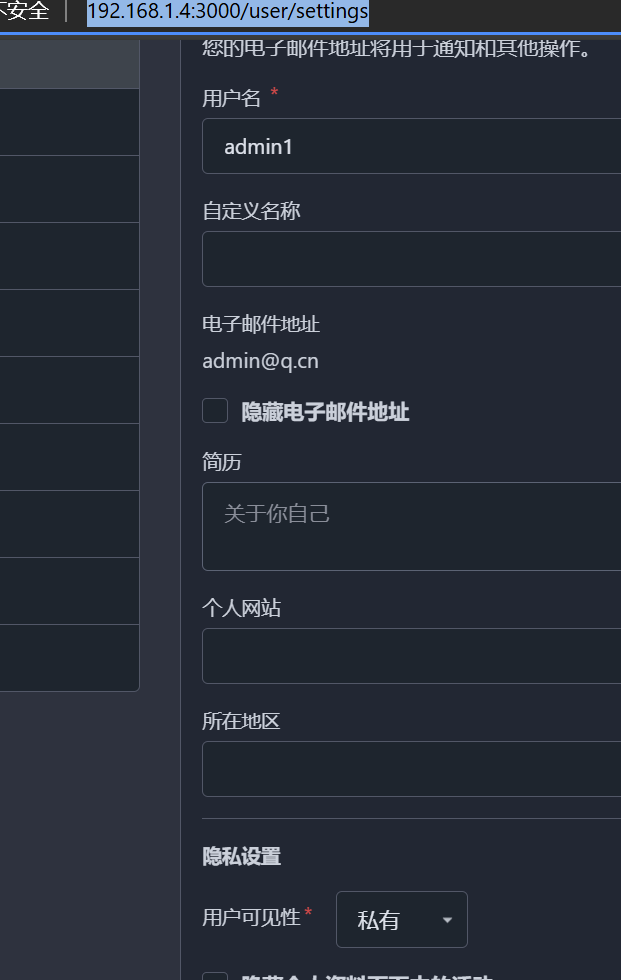
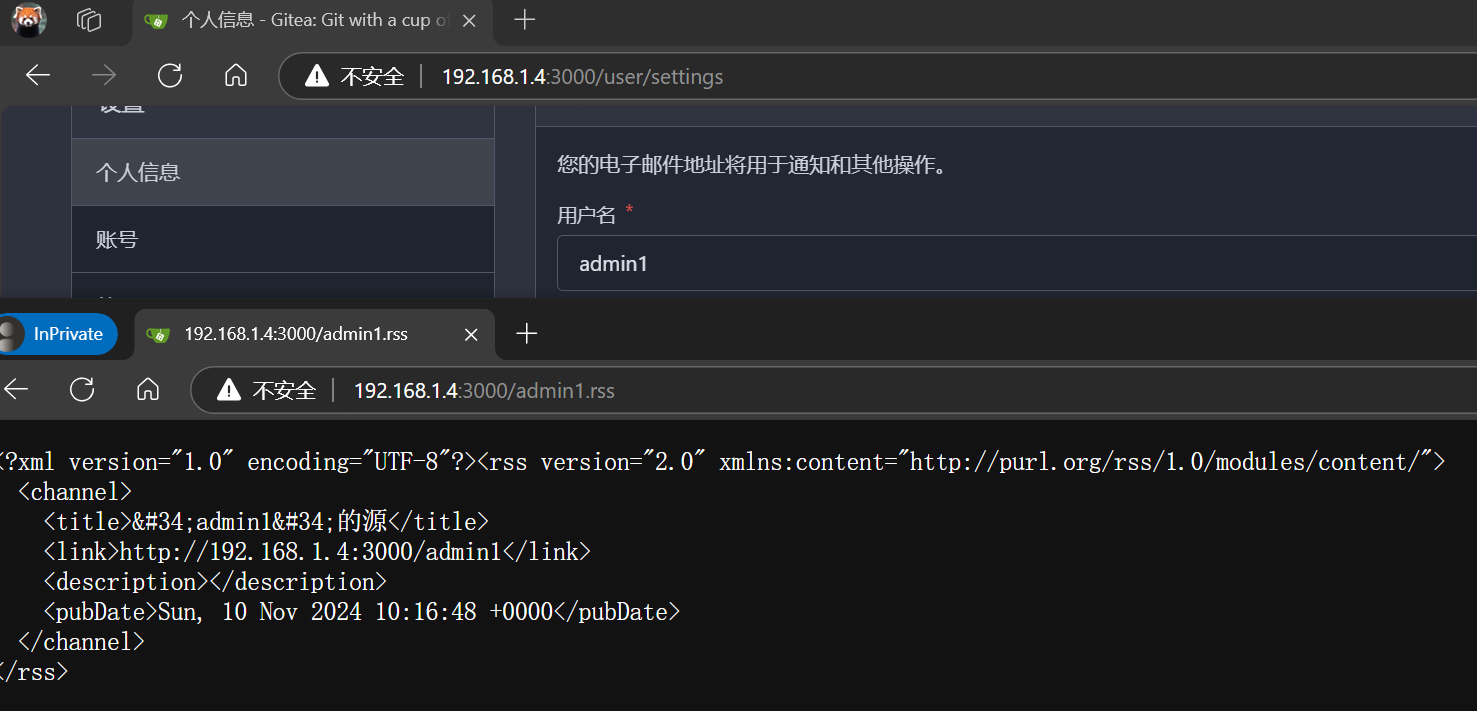
攻击者通过在URL中添加.rss(或其他扩展名)来测试私有用户账户的存在。攻击者可以利用该漏洞获取敏感信息,增加隐私风险
将个人账号设置为私有
`
https://codeberg.org/forgejo/forgejo/commit/d7408d8b0b04afd2a3c8e23cc908e7bd3849f34d
routers/web/user/home.go
@ -821,6 +821,11 @@ func UsernameSubRoute(ctx *context.Context) {
reloadParam := func(suffix string) (success bool) {
ctx.SetParams("username", strings.TrimSuffix(username, suffix))
context_service.UserAssignmentWeb()(ctx)
// check view permissions
if !user_model.IsUserVisibleToViewer(ctx, ctx.ContextUser, ctx.Doer) {
ctx.NotFound("user", fmt.Errorf(ctx.ContextUser.Name))
return false
}
return !ctx.Written()
}
switch {`
完整代码
func UsernameSubRoute(ctx *context.Context) {
// WORKAROUND to support usernames with "." in it
// https://github.com/go-chi/chi/issues/781
username := ctx.Params("username")
reloadParam := func(suffix string) (success bool) {
ctx.SetParams("username", strings.TrimSuffix(username, suffix))
context_service.UserAssignmentWeb()(ctx)// check view permissionsif !user_model.IsUserVisibleToViewer(ctx, ctx.ContextUser, ctx.Doer) {ctx.NotFound("user", fmt.Errorf(ctx.ContextUser.Name))return false}return !ctx.Written()
}
switch {
case strings.HasSuffix(username, ".png"):if reloadParam(".png") {AvatarByUserName(ctx)}
case strings.HasSuffix(username, ".keys"):if reloadParam(".keys") {ShowSSHKeys(ctx)}
case strings.HasSuffix(username, ".gpg"):if reloadParam(".gpg") {ShowGPGKeys(ctx)}
case strings.HasSuffix(username, ".rss"):if !setting.Other.EnableFeed {ctx.Error(http.StatusNotFound)return}if reloadParam(".rss") {context_service.UserAssignmentWeb()(ctx)feed.ShowUserFeedRSS(ctx)}
case strings.HasSuffix(username, ".atom"):if !setting.Other.EnableFeed {ctx.Error(http.StatusNotFound)return}if reloadParam(".atom") {feed.ShowUserFeedAtom(ctx)}
账号设置为隐私状态,通过添加对应文件扩展名可以判断用户是否存在。