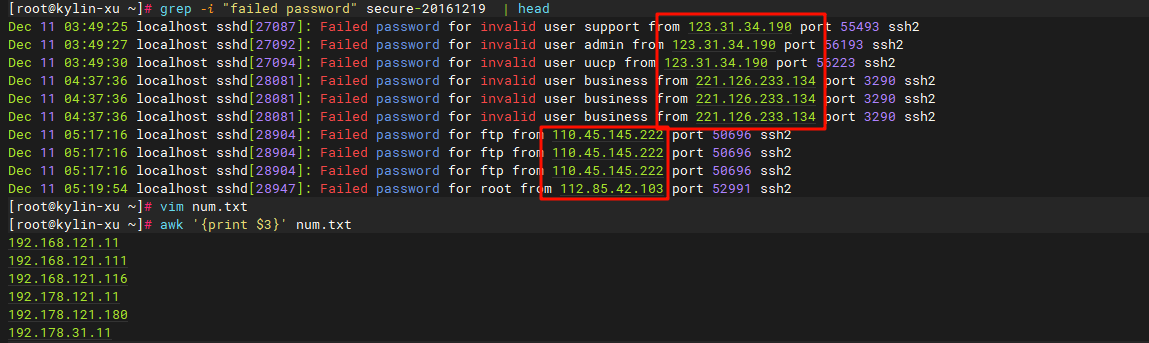
题目链接:reverse3。
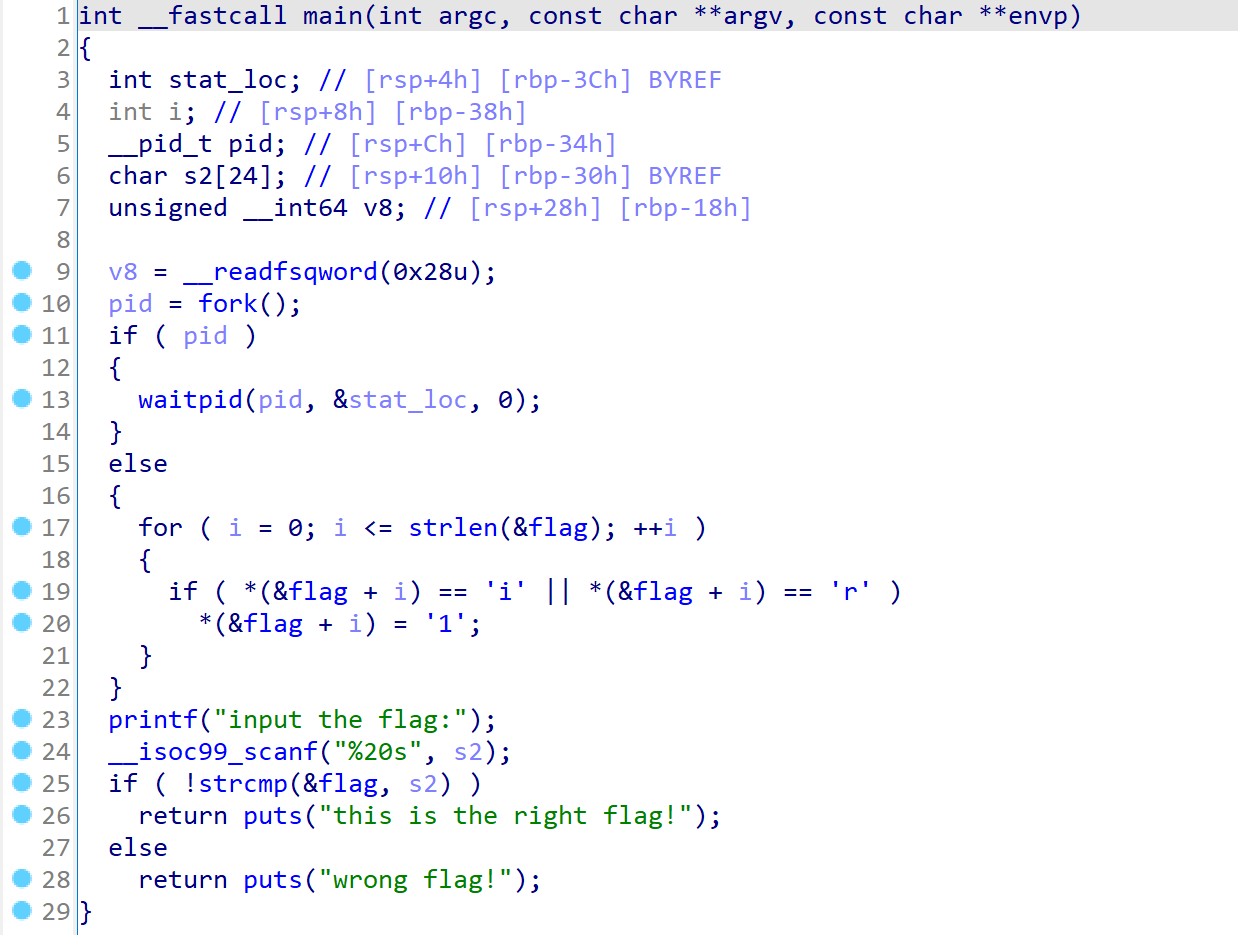
下载附件后,使用 IDA 打开,进行反编译,定位到 main 函数如下。
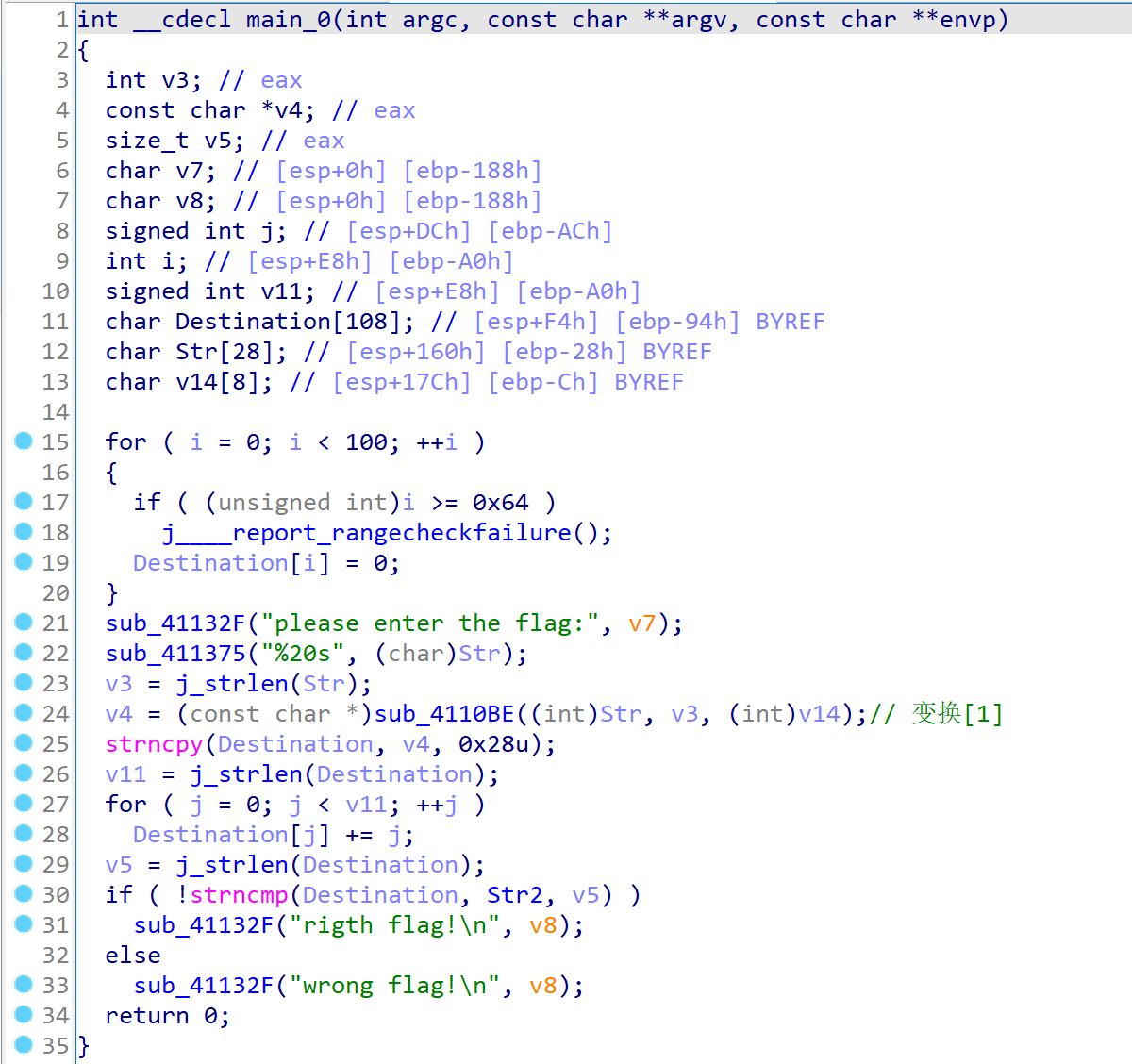
通过分析 main 函数流程,可以发现主要是对用户输入的字符串进行了两次操作,第一次是函数 "sub_4110BE",第二次是对函数 "sub_4110BE" 处理后得到的字符串进行简单的加减运算,随后就与目标字符串进行比对。
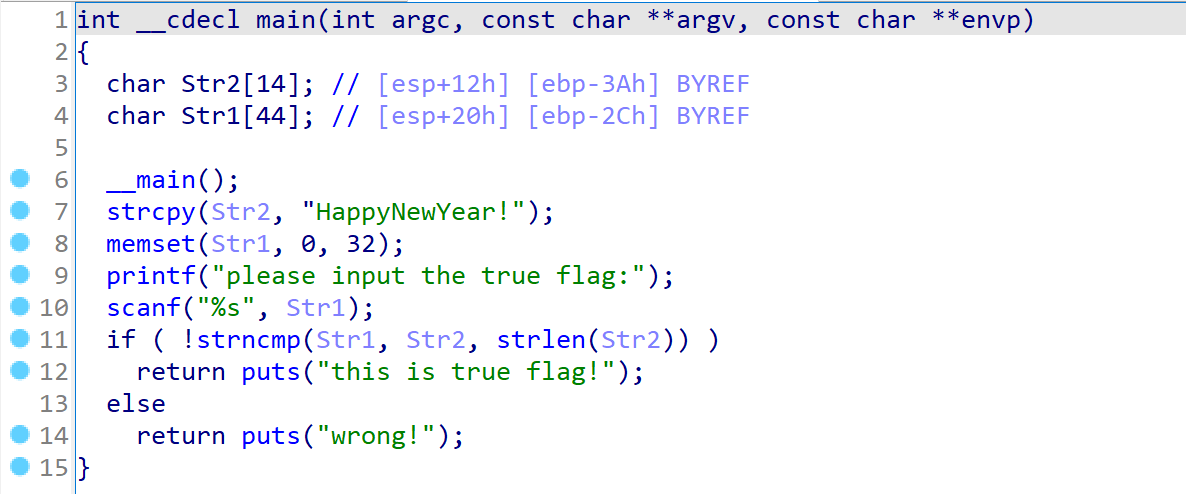
函数 "sub_4110BE" 最终执行的流程如下。
void *__cdecl sub_411AB0(char *a1, unsigned int a2, int *a3)
{int v4; // [esp+D4h] [ebp-38h]int v5; // [esp+D4h] [ebp-38h]int v6; // [esp+D4h] [ebp-38h]int v7; // [esp+D4h] [ebp-38h]int i; // [esp+E0h] [ebp-2Ch]unsigned int v9; // [esp+ECh] [ebp-20h]int v10; // [esp+ECh] [ebp-20h]int v11; // [esp+ECh] [ebp-20h]void *v12; // [esp+F8h] [ebp-14h]char *v13; // [esp+104h] [ebp-8h]if ( !a1 || !a2 )return 0;v9 = a2 / 3;if ( (int)(a2 / 3) % 3 )++v9;v10 = 4 * v9;*a3 = v10;v12 = malloc(v10 + 1);if ( !v12 )return 0;j_memset(v12, 0, v10 + 1);v13 = a1;v11 = a2;v4 = 0;while ( v11 > 0 ){byte_41A144[2] = 0;byte_41A144[1] = 0;byte_41A144[0] = 0;for ( i = 0; i < 3 && v11 >= 1; ++i ){byte_41A144[i] = *v13;--v11;++v13;}if ( !i )break;switch ( i ){case 1:*((_BYTE *)v12 + v4) = aAbcdefghijklmn[(int)(unsigned __int8)byte_41A144[0] >> 2];v5 = v4 + 1;*((_BYTE *)v12 + v5) = aAbcdefghijklmn[((byte_41A144[1] & 0xF0) >> 4) | (16 * (byte_41A144[0] & 3))];*((_BYTE *)v12 + ++v5) = aAbcdefghijklmn[64];*((_BYTE *)v12 + ++v5) = aAbcdefghijklmn[64];v4 = v5 + 1;break;case 2:*((_BYTE *)v12 + v4) = aAbcdefghijklmn[(int)(unsigned __int8)byte_41A144[0] >> 2];v6 = v4 + 1;*((_BYTE *)v12 + v6) = aAbcdefghijklmn[((byte_41A144[1] & 0xF0) >> 4) | (16 * (byte_41A144[0] & 3))];*((_BYTE *)v12 + ++v6) = aAbcdefghijklmn[((byte_41A144[2] & 0xC0) >> 6) | (4 * (byte_41A144[1] & 0xF))];*((_BYTE *)v12 + ++v6) = aAbcdefghijklmn[64];v4 = v6 + 1;break;case 3:*((_BYTE *)v12 + v4) = aAbcdefghijklmn[(int)(unsigned __int8)byte_41A144[0] >> 2];v7 = v4 + 1;*((_BYTE *)v12 + v7) = aAbcdefghijklmn[((byte_41A144[1] & 0xF0) >> 4) | (16 * (byte_41A144[0] & 3))];*((_BYTE *)v12 + ++v7) = aAbcdefghijklmn[((byte_41A144[2] & 0xC0) >> 6) | (4 * (byte_41A144[1] & 0xF))];*((_BYTE *)v12 + ++v7) = aAbcdefghijklmn[byte_41A144[2] & 0x3F];v4 = v7 + 1;break;}}*((_BYTE *)v12 + v4) = 0;return v12;
}
对于该函数的具体操作不必太多深究,通过该源码的大概分析就可以猜测到该函数实现了 Base64 编码功能。
因此,提取出程序中的目标字符串,如下。
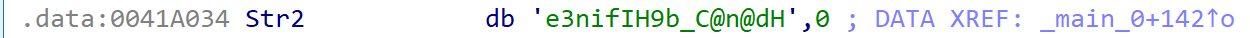
即。
data = [0x65, 0x33, 0x6E, 0x69, 0x66, 0x49, 0x48, 0x39, 0x62, 0x5F, 0x43, 0x40, 0x6E, 0x40, 0x64, 0x48
]
随后编写出与程序相反操作的 Python 脚本。
import base64data = [0x65, 0x33, 0x6E, 0x69, 0x66, 0x49, 0x48, 0x39, 0x62, 0x5F, 0x43, 0x40, 0x6E, 0x40, 0x64, 0x48
]data_re1 = []for i in range(len(data)):data_re1.append(data[i] - i)string = ""for i in range(len(data_re1)):string += chr(data_re1[i])print(string)print(base64.b64decode(string))
即可获得 flag。