日期:2024.11.9
参照:
- 鸟哥私房菜-第七章、Linux 防火牆設定
https://linux.vbird.org/linux_server/rocky9/0180firewall.php
在RHEL8.1的安装过程中没有注册,目前yum源不能用,先注册
[root@RHEL8 ~]# dnf repoinfo
Updating Subscription Management repositories.
Unable to read consumer identityThis system is not registered with an entitlement server. You can use subscription-manager to register.No repositories available
[root@RHEL8 ~]# subscription-manager register --username <username> --password <password> --auto-attach
Registering to: subscription.rhsm.redhat.com:443/subscription
The system has been registered with ID: 8c101d86-fa2d-45cf-a19c-02b621032703
The registered system name is: RHEL8
Ignoring the request to auto-attach. Attaching subscriptions is disabled for organization "32546913" because Simple Content Access (SCA) is enabled.
[root@RHEL8 ~]# dnf repolist
Updating Subscription Management repositories.
repo id repo name
rhel-8-for-x86_64-appstream-rpms Red Hat Enterprise Linux 8 for x86_64 - AppStream (RPMs)
rhel-8-for-x86_64-baseos-rpms Red Hat Enterprise Linux 8 for x86_64 - BaseOS (RPMs)
配置enp2s0和enp3s0两块网卡地址,按照规划
mac 52:54:00:00:31:72的网卡放DMZ网段,IP为172.31.0.254
mac 52:54:00:00:31:10的网卡放LAN网段,IP为10.31.0.254
[root@RHEL8 ~]# nmcli device show enp2s0
GENERAL.DEVICE: enp2s0
GENERAL.TYPE: ethernet
GENERAL.HWADDR: 52:54:00:00:31:72
GENERAL.MTU: 1500
GENERAL.STATE: 30 (disconnected)
GENERAL.CONNECTION: --
GENERAL.CON-PATH: --
WIRED-PROPERTIES.CARRIER: on
IP4.GATEWAY: --
IP6.GATEWAY: --
[root@RHEL8 ~]# nmcli device show enp3s0
GENERAL.DEVICE: enp3s0
GENERAL.TYPE: ethernet
GENERAL.HWADDR: 52:54:00:00:31:10
GENERAL.MTU: 1500
GENERAL.STATE: 30 (disconnected)
GENERAL.CONNECTION: --
GENERAL.CON-PATH: --
WIRED-PROPERTIES.CARRIER: on
IP4.GATEWAY: --
IP6.GATEWAY: --
[root@RHEL8 ~]# nmcli connection show
NAME UUID TYPE DEVICE
enp1s0 ff9cc8a4-1fd4-4809-a108-0e51df4c75dd ethernet enp1s0
enp2s0 6cc22494-8242-49ea-b27c-64152d90aea4 ethernet --
enp3s0 e73eef29-46c2-4cf5-ab11-1298739a98ab ethernet --
[root@RHEL8 ~]# nmcli connection delete enp2s0
Connection 'enp2s0' (6cc22494-8242-49ea-b27c-64152d90aea4) successfully deleted.
[root@RHEL8 ~]# nmcli connection delete enp3s0
Connection 'enp3s0' (e73eef29-46c2-4cf5-ab11-1298739a98ab) successfully deleted.
[root@RHEL8 ~]# nmcli connection show
NAME UUID TYPE DEVICE
enp1s0 ff9cc8a4-1fd4-4809-a108-0e51df4c75dd ethernet enp1s0
[root@RHEL8 ~]# nmcli connection add type ethernet autoconnect yes con-name enp2s0 ifname enp2s0 ipv4.method manual ipv4.addresses 172.31.0.254/24
Connection 'enp2s0' (e098b147-12be-415f-8ec7-a436fa30d38a) successfully added.
[root@RHEL8 ~]# nmcli connection add type ethernet autoconnect yes con-name enp3s0 ifname enp3s0 ipv4.method manual ipv4.addresses 10.31.0.254/24
Connection 'enp3s0' (831a2692-73fc-44ca-ba20-2f0f9bbeebe9) successfully added.
[root@RHEL8 ~]# nmcli connection up enp2s0
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/4)
[root@RHEL8 ~]# nmcli connection up enp3s0
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/5)
开启ip_forward
[root@RHEL8 ~]# cat /proc/sys/net/ipv4/ip_forward
0
[root@RHEL8 ~]# echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/ipforward.conf
[root@RHEL8 ~]# cat /etc/sysctl.d/ipforward.conf
net.ipv4.ip_forward=1
[root@RHEL8 ~]# sysctl -p /etc/sysctl.d/ipforward.conf
net.ipv4.ip_forward = 1
[root@RHEL8 ~]# cat /proc/sys/net/ipv4/ip_forward
1
来用下nftable
[root@RHEL8 ~]# systemctl mask firewalld.service iptables.service
Unit iptables.service does not exist, proceeding anyway.
Created symlink /etc/systemd/system/firewalld.service → /dev/null.
Created symlink /etc/systemd/system/iptables.service → /dev/null.
[root@RHEL8 ~]# systemctl stop firewalld.service
[root@RHEL8 ~]# systemctl enable --now nftables.service
Created symlink /etc/systemd/system/multi-user.target.wants/nftables.service → /usr/lib/systemd/system/nftables.service.
[root@RHEL8 ~]# systemctl status nftables.service
● nftables.service - Netfilter TablesLoaded: loaded (/usr/lib/systemd/system/nftables.service; enabled; vendor preset: disabled)Active: active (exited) since Sat 2024-11-09 22:39:24 CST; 20s agoDocs: man:nft(8)Process: 16431 ExecStart=/sbin/nft -f /etc/sysconfig/nftables.conf (code=exited, status=0/SUCCESS)Main PID: 16431 (code=exited, status=0/SUCCESS)Nov 09 22:39:24 RHEL8 systemd[1]: Starting Netfilter Tables...
Nov 09 22:39:24 RHEL8 systemd[1]: Started Netfilter Tables.
查看配置文件,配置nftable防火墙规则的保存路径并创建文件。
[root@RHEL8 ~]# rpm -qc nftables
/etc/nftables/main.nft
/etc/nftables/nat.nft
/etc/nftables/osf/pf.os
/etc/nftables/router.nft
/etc/sysconfig/nftables.conf
[root@RHEL8 ~]# echo include '"/etc/nftables/rhel8.nft"' >> /etc/sysconfig/nftables.conf
[root@RHEL8 ~]# cat /etc/sysconfig/nftables.conf
# Uncomment the include statement here to load the default config sample
# in /etc/nftables for nftables service.#include "/etc/nftables/main.nft"# To customize, either edit the samples in /etc/nftables, append further
# commands to the end of this file or overwrite it after first service
# start by calling: 'nft list ruleset >/etc/sysconfig/nftables.conf'.
include "/etc/nftables/rhel8.nft"
[root@RHEL8 ~]# touch /etc/nftables/rhel8.nft
[root@RHEL8 ~]# systemctl reload nftables.service
添加一个存放 ipv4和ipv6过滤规则 的表NF_FILTER
[root@RHEL8 ~]# nft add table inet NFT_FILTER
[root@RHEL8 ~]# nft list tables
table inet NFT_FILTER
添加一个 过滤进入路由封包 的链NFC_INPUT,策略默认为 允许,配置好进入路由的规则之后再将默认策略改为拒绝
[root@RHEL8 ~]# nft add chain inet NFT_FILTER NFC_INPUT { type filter hook input priority filter \; policy accept \; }
[root@RHEL8 ~]# nft list chains
table inet NFT_FILTER {chain NFC_INPUT {type filter hook input priority filter; policy accept;}
}
放行已经建立的连接的封包,放行与已经建立连接相关的封包
[root@RHEL8 ~]# nft add rule inet NFT_FILTER NFC_INPUT ct state established,related accept
[root@RHEL8 ~]# nft list ruleset
table inet NFT_FILTER {chain NFC_INPUT {type filter hook input priority filter; policy accept;ct state established,related accept}
}
现在将NFC_INPUT的默认规则改为dorp,通过Xshell正在连接的ssh22端口就不会断掉,但是一旦断掉了也连不回去
[root@RHEL8 ~]# nft -e chain inet NFT_FILTER NFC_INPUT { type filter hook input priority filter \; policy drop \;}
[root@RHEL8 ~]# nft list ruleset
table inet NFT_FILTER {chain NFC_INPUT {type filter hook input priority filter; policy drop;ct state established,related accept}
}
允许ping封包通过,用rhel9 ping rhel8 ,一直卡住无反应,加入规则后立刻ping通。提示之前发送了79个包,通了之后收到6个回应。
[root@RHEL8 ~]# nft -e add rule inet NFT_FILTER NFC_INPUT meta l4proto icmp accept
insert rule inet NFT_FILTER NFC_INPUT meta l4proto icmp accept
# new generation 106 by process 16776 (nft)
[root@RHEL9 ~]# ping 192.168.5.254
PING 192.168.5.254 (192.168.5.254) 56(84) bytes of data.64 bytes from 192.168.5.254: icmp_seq=74 ttl=64 time=0.142 ms
64 bytes from 192.168.5.254: icmp_seq=75 ttl=64 time=0.115 ms
64 bytes from 192.168.5.254: icmp_seq=76 ttl=64 time=0.116 ms
64 bytes from 192.168.5.254: icmp_seq=77 ttl=64 time=0.102 ms
64 bytes from 192.168.5.254: icmp_seq=78 ttl=64 time=0.098 ms
64 bytes from 192.168.5.254: icmp_seq=79 ttl=64 time=0.103 ms
^C
--- 192.168.5.254 ping statistics ---
79 packets transmitted, 6 received, 92.4051% packet loss, time 79910ms
rtt min/avg/max/mdev = 0.098/0.112/0.142/0.014 ms
放行 本地回环网卡 lo 的封包
[root@RHEL8 ~]# nft -e add rule inet NFT_FILTER NFC_INPUT iifname lo accept
insert rule inet NFT_FILTER NFC_INPUT iifname "lo" accept
# new generation 107 by process 16984 (nft)
放行 连接至enp1s0网卡的 目标端口22的 tpc协议的 封包
[root@RHEL8 ~]# nft add rule inet NFT_FILTER NFC_INPUT iifname enp1s0 tcp dport 22 accept
[root@RHEL8 ~]# nft list ruleset
table inet NFT_FILTER {chain NFC_INPUT {type filter hook input priority filter; policy drop;ct state established,related acceptmeta l4proto icmp acceptiifname "lo" acceptiifname "enp1s0" tcp dport 22 accept}
}
下一步要在enp3s0连接的LAN网段里架设一个dhcp服务器,ip:10.31.0.1,在rhel8上建立DHCPrelay,使enp2s0连接的DMZ网段里的主机也可以获得dncp服务
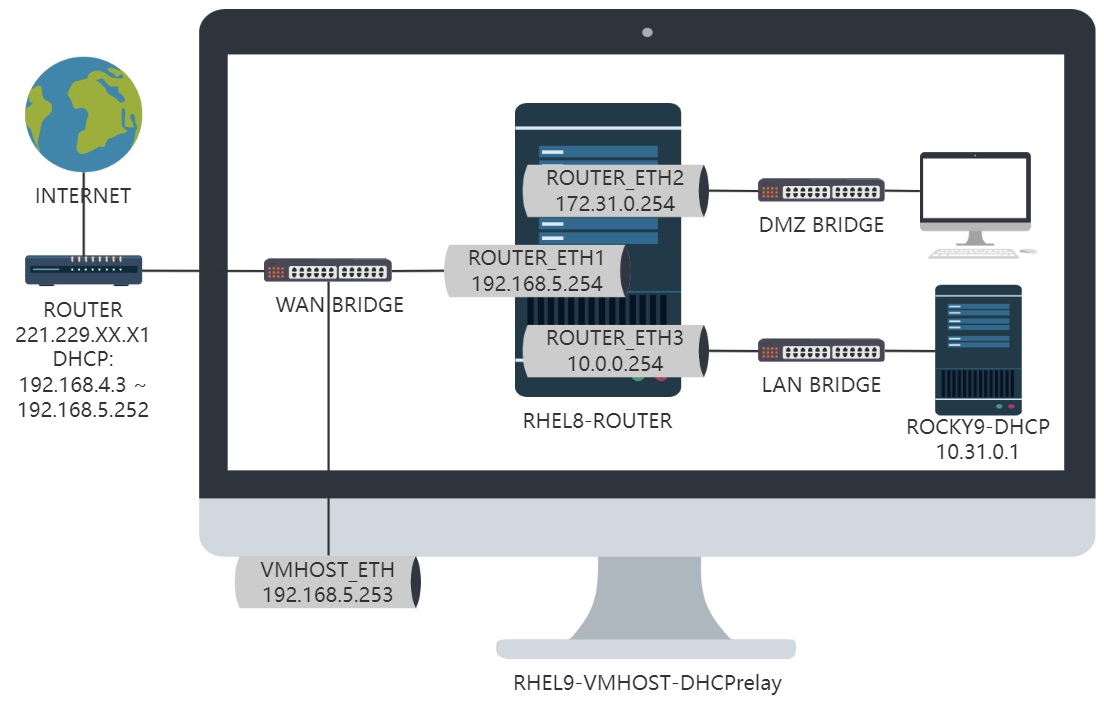
因此,放行 连接至enp2s0网卡的 目标端口为 67的 UPD封包,让DMZ网段里主机的DHCP请求能够通过enp2s0网卡发送给rhel8上运行的DHCPrelay服务。再由rhel8上的DHCPrelay转发到LAN网段的10.0.0.1上
[root@RHEL8 ~]# nft add rule inet NFT_FILTER NFC_INPUT iifname enp2s0 udp dport 67 accept
设置从公网能够ssh连接到计划搭建的10.0.0.1dhcp服务器的22端口
第一步 配置访问公网ip:221.229.XX.X1:62223 的请求转发到 rhel8 enp0s1 192.168.5.254:62223
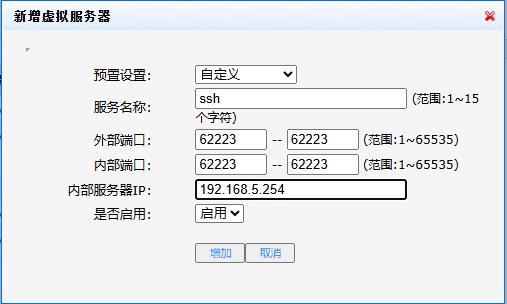
第二步 将访问rhel8 enp0s1 192.168.5.254:62223 的请求转发到 enp0s3 连接的 LAN 网段里的 10.31.0.1:22
添加一个存放 ipv4和ipv6网络地址转换规则 的表NFT_NAT
NAT:Network Address Translation
[root@RHEL8 ~]# nft add table inet NFT_NAT
[root@RHEL8 ~]# nft list tables
table inet NFT_FILTER
table inet NFT_NAT
添加一个存放 进入路由前规则 的链
[root@RHEL8 ~]# nft add chain inet NFT_NAT NFC_PRE { type nat hook prerouting priority dstnat \; policy accept \; }
[root@RHEL8 ~]# nft list chains
table inet NFT_FILTER {chain NFC_INPUT {type filter hook input priority filter; policy drop;}
}
table inet NFT_NAT {chain NFC_PRE {type nat hook prerouting priority dstnat; policy accept;}
}
添加规则将访问 enp0s1 192.168.5.254:62223 的请求转发到 enp0s3 连接的 LAN 网段里的 10.31.0.1:22
[root@RHEL8 ~]# nft add rule inet NFT_NAT NFC_PRE iifname enp3s0 tcp dport 62223 dnat ip to 10.31.0.1:22
[root@RHEL8 ~]# nft list chain inet NFT_NAT NFC_PRE
table inet NFT_NAT {chain NFC_PRE {type nat hook prerouting priority dstnat; policy accept;iifname "enp3s0" tcp dport 62223 dnat ip to 10.31.0.1:22}
}
配置enp2s0和enp3s0两个网段能够访问公网,通过这两个网段进入路由的数据包 在走到路由的后方时 伪装(masquerade)成公网的IP访问互联网
在NFT_NAT表中添加一个存放 通过路由后的规则 的链
[root@RHEL8 ~]# nft add chain inet NFT_NAT NFC_POST { type nat hook postrouting priority srcnat \; policy accept \; }
[root@RHEL8 ~]# nft list chains
table inet NFT_FILTER {chain NFC_INPUT {type filter hook input priority filter; policy drop;}
}
table inet NFT_NAT {chain NFC_PRE {type nat hook prerouting priority dstnat; policy accept;}chain NFC_POST {type nat hook postrouting priority srcnat; policy accept;}
}
伪装(masquerade) 由enp2s0 172.31.0.0/24 和 enp3s0 10.31.0.0/24 两个网段进入 然后从 epn1s0 出去的 数据包
[root@RHEL8 ~]# nft add rule inet NFT_NAT NFC_POST iifname enp2s0 oifname enp1s0 ip saddr 172.31.0.0/24 masquerade
[root@RHEL8 ~]# nft add rule inet NFT_NAT NFC_POST iifname enp3s0 oifname enp1s0 ip saddr 10.31.0.0/24 masquerade
[root@RHEL8 ~]# nft list chain inet NFT_NAT NFC_POST
table inet NFT_NAT {chain NFC_POST {type nat hook postrouting priority srcnat; policy accept;iifname "enp2s0" oifname "enp1s0" ip saddr 172.31.0.0/24 masqueradeiifname "enp3s0" oifname "enp1s0" ip saddr 10.31.0.0/24 masquerade}
}
存储规则到配置文件
[root@RHEL8 ~]# nft list ruleset >| /etc/nftables/rhel8.nft
设置单小时内失败登录超过10次加入黑名单
测试加入黑名单的语句,,这里的reject语句要插入在handle5之前,否则handle5判断22端口accept,后面的reject语句不会生效
[root@RHEL8 ~]# nft -a list chain inet NFT_FILTER NFC_INPUT
table inet NFT_FILTER {chain NFC_INPUT { # handle 1type filter hook input priority filter; policy drop;ct state established,related accept # handle 2meta l4proto icmp accept # handle 3iifname "lo" accept # handle 4iifname "enp1s0" tcp dport 22 accept # handle 5iifname "enp2s0" udp dport 67 accept # handle 6}
}
[root@RHEL8 ~]# nft insert rule inet NFT_FILTER NFC_INPUT handle 5 iifname enp1s0 ip saddr 192.168.5.253 reject
[root@RHEL8 ~]# nft -a list chain inet NFT_FILTER NFC_INPUT
table inet NFT_FILTER {chain NFC_INPUT { # handle 1type filter hook input priority filter; policy drop;ct state established,related accept # handle 2meta l4proto icmp accept # handle 3iifname "lo" accept # handle 4iifname "enp1s0" ip saddr 192.168.5.253 reject with icmp port-unreachable # handle 25iifname "enp1s0" tcp dport 22 accept # handle 5iifname "enp2s0" udp dport 67 accept # handle 6}
}
用RHEL9连接被拒绝,指令生效
[root@RHEL9 ~]# ssh 192.168.5.254
ssh: connect to host 192.168.5.254 port 22: Connection refused
将测试的规则移除
[root@RHEL8 ~]# nft delete rule inet NFT_FILTER NFC_INPUT handle 25
[root@RHEL8 ~]# nft -a list chain inet NFT_FILTER NFC_INPUT
table inet NFT_FILTER {chain NFC_INPUT { # handle 1type filter hook input priority filter; policy drop;ct state established,related accept # handle 2meta l4proto icmp accept # handle 3iifname "lo" accept # handle 4iifname "enp1s0" tcp dport 22 accept # handle 5iifname "enp2s0" udp dport 67 accept # handle 6}
}
将自动拉黑脚本的防火墙语句由原先的firewalld修改为nft
[root@RHEL8 ~]# cat awknftban.sh
#awkban.sh
#Date: 2024-11-11
#!/bin/bash#写入计划任务
#1.自动拉黑每小时登录失败超过指定次数的IPrulefile='/etc/nftables/rhel8.nft'cat << EOF >> /var/spool/cron/root
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="\$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '\$0~hourago{ip[\$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/sbin/nft insert rule inet NFT_FILTER NFC_INPUT handle 5 iifname enp1s0 ip saddr "i" reject;/usr/sbin/nft -a list ruleset >| ${rulefile};/usr/bin/echo \"\$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" XXXXX@XX.com && /usr/bin/rm -f /tmp/baninfo
EOF
[root@RHEL8 ~]# sh awknftban.sh
[root@RHEL8 ~]# crontab -l
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/sbin/nft insert rule inet NFT_FILTER NFC_INPUT handle 5 iifname enp1s0 ip saddr "i" reject;/usr/sbin/nft -a list ruleset >| /etc/nftables/rhel8.nft;/usr/bin/echo \"$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" XXXXX@XX.com && /usr/bin/rm -f /tmp/baninfo
在knock-server中使用nft语句
由于nft语句删除rule需要指定handle,但是handle需要增加rule的时候才能得到,这就造成了nft在knock-server中开门容易关门难的困境,于是我打算用replace修改其中一个已知handle的rule来解决这个问题,例如选择5号handle
[root@RHEL8 ~]# nft -a list chain inet NFT_FILTER NFC_INPUT
table inet NFT_FILTER {chain NFC_INPUT { # handle 1type filter hook input priority filter; policy drop;ct state established,related accept # handle 2meta l4proto icmp accept # handle 3iifname "lo" accept # handle 4iifname "enp1s0" tcp dport 22 accept # handle 5iifname "enp2s0" udp dport 67 accept # handle 6}
}
[root@RHEL8 ~]# nft replace rule inet NFT_FILTER NFC_INPUT handle 5 iifname enp1s0 ip saddr 127.0.0.1 tcp dport 33333 accept
[root@RHEL8 ~]# nft -a list chain inet NFT_FILTER NFC_INPUT
table inet NFT_FILTER {chain NFC_INPUT { # handle 1type filter hook input priority filter; policy drop;ct state established,related accept # handle 2meta l4proto icmp accept # handle 3iifname "lo" accept # handle 4iifname "enp1s0" ip saddr 127.0.0.1 tcp dport 33333 accept # handle 5iifname "enp2s0" udp dport 67 accept # handle 6}
}
[root@RHEL8 ~]# nft replace rule inet NFT_FILTER NFC_INPUT handle 5 iifname enp1s0 tcp dport 22 accept
[root@RHEL8 ~]# nft -a list chain inet NFT_FILTER NFC_INPUT
table inet NFT_FILTER {chain NFC_INPUT { # handle 1type filter hook input priority filter; policy drop;ct state established,related accept # handle 2meta l4proto icmp accept # handle 3iifname "lo" accept # handle 4iifname "enp1s0" tcp dport 22 accept # handle 5iifname "enp2s0" udp dport 67 accept # handle 6}
}
脚本自动化
[root@centos7 ~]# cat rhel8route-nfs.sh
#rhel8route-nfs.sh
#Date: 2024-11-13
#!/bin/bash#填写wan网段网卡名和ip
wanif='enp1s0'
wanip='192.168.5.254'#填写dmz和lan网段的网卡名和ip/掩码(CIDR)
dmzif='enp2s0'
lanif='enp3s0'
dmzip='172.31.0.254/24'
lanip='10.31.0.254/24'#填写nft防火墙自定义规则存放文件路径
rulefile='/etc/nftables/rhel8.nft'#配置wan网段参数
wan_netmask=$(nmcli connection show ${wanif} | sed -En 's/IP4.ADDRESS\[1\]: +.+\/([[:digit:]]+)$/\1/p')
wan_gateway=$(nmcli connection show ${wanif} | sed -En 's/^IP4.GATEWAY: +(.+)$/\1/p')
wan_dns1=$(nmcli connection show ${wanif} | sed -En 's/^IP4.DNS\[1\]: +(.+)$/\1/p')
wan_dns2=$(nmcli connection show ${wanif} | sed -En 's/^IP4.DNS\[2\]: +(.+)$/\1/p')
wanip=${wanip}/${wan_netmask}
nmcli connection modify ${wanif} ipv4.method manual ipv4.addresses ${wanip}
nmcli connection modify ${wanif} ipv4.gateway ${wan_gateway}
nmcli connection modify ${wanif} ipv4.dns ${wan_dns1} +ipv4.dns ${wan_dns2}
nmcli connection up ${wanif}#配置dmz和lan两个网段的网络参数
nmcli connection delete ${dmzif}
nmcli connection delete ${lanif}
nmcli connection add type ethernet autoconnect yes con-name ${dmzif} ifname ${dmzif} ipv4.method manual ipv4.addresses ${dmzip}
nmcli connection add type ethernet autoconnect yes con-name ${lanif} ifname ${lanif} ipv4.method manual ipv4.addresses ${lanip}
nmcli connection up ${dmzif}
nmcli connection up ${lanif}
dmznet=$(echo ${dmzip} | sed -En 's#([[:digit:]]+.[[:digit:]]+.[[:digit:]]+.)[[:digit:]]+(/[[:digit:]]+)#\10\2#p')
lannet=$(echo ${lanip} | sed -En 's#([[:digit:]]+.[[:digit:]]+.[[:digit:]]+.)[[:digit:]]+(/[[:digit:]]+)#\10\2#p')#开启IP forward
echo "net.ipv4.ip_forward=1" > /etc/sysctl.d/ipforward.conf
sysctl -p /etc/sysctl.d/ipforward.conf#配置使用nftables来管理防火墙
rpm -q nftables || yum install -y nftables
systemctl mask firewalld.service iptables.service
systemctl stop firewalld.service iptables.service
echo "include \"${rulefile}\"" >> /etc/sysconfig/nftables.conf
touch ${rulefile}
systemctl enable --now nftables.service#配置防火墙规则
nft flush rulesetnft add table inet NFT_FILTER
nft add chain inet NFT_FILTER NFC_INPUT { type filter hook input priority filter \; policy drop \; }
nft add rule inet NFT_FILTER NFC_INPUT ct state established,related accept
nft add rule inet NFT_FILTER NFC_INPUT meta l4proto icmp accept
nft add rule inet NFT_FILTER NFC_INPUT iifname lo accept
nft add rule inet NFT_FILTER NFC_INPUT iifname ${wanif} tcp dport 22 accept
nft add rule inet NFT_FILTER NFC_INPUT iifname enp2s0 udp dport 67 acceptnft add table inet NFT_NAT
nft add chain inet NFT_NAT NFC_PRE { type nat hook prerouting priority dstnat \; policy accept \; }
nft add rule inet NFT_NAT NFC_PRE iifname enp3s0 tcp dport 62223 dnat ip to 10.31.0.1:22nft add chain inet NFT_NAT NFC_POST { type nat hook postrouting priority srcnat \; policy accept \; }
nft add rule inet NFT_NAT NFC_POST iifname ${dmzif} oifname ${wanif} ip saddr ${dmznet} masquerade
nft add rule inet NFT_NAT NFC_POST iifname ${lanif} oifname ${wanif} ip saddr ${lannet} masqueradenft -a list ruleset >| ${rulefile}#写入计划任务
#1.自动拉黑每小时登录失败超过指定次数的IP
cat << EOF >> /var/spool/cron/root
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="\$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '\$0~hourago{ip[\$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/sbin/nft insert rule inet NFT_FILTER NFC_INPUT handle 5 iifname enp1s0 ip saddr "i" reject;/usr/sbin/nft -a list ruleset >| ${rulefile};/usr/bin/echo \"\$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" xxxxx@xx.com && /usr/bin/rm -f /tmp/baninfo
EOF