网安第一课
改zip解压
找到key1
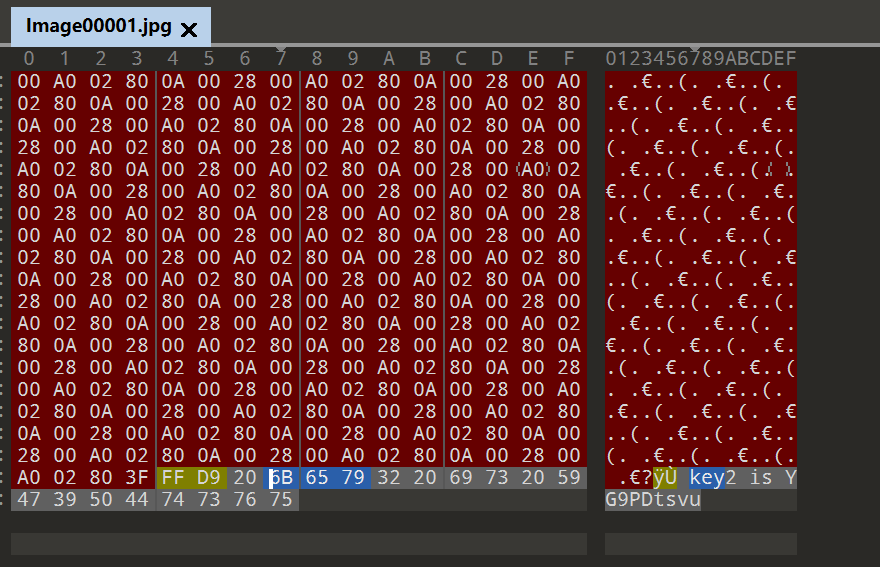
key2
6iMmn76ucYG9PDtsvu
解压之后
上脚本
from PIL import Imageimages = [Image.open(f"{i}.png") for i in range(1, 38)]
qr_code = Image.new("RGB", (128, 128), (255, 255, 255))
for i in range(37):img1 = images[i]for j in range(128):print(i, j, img1.getpixel((j, 0))[1])pixel_value = img1.getpixel((j, 0))[1]if pixel_value & 1:qr_code.putpixel((i, j), (0, 0, 0))else:qr_code.putpixel((i, j), (255, 255, 255))qr_code.save("qr_code.png")
需要改一下脚本
pcb-取证
vol.py -f flag.raw imageinfo
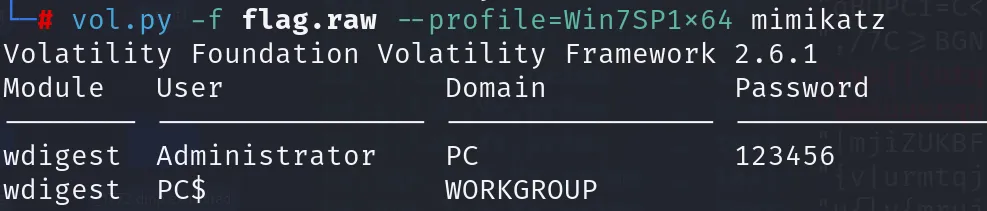
vol.py -f flag.raw --profile=Win7SP1x64 mimikatz
vol.py -f flag.raw --profile=Win7SP1x64 filescan | grep -E "png|jpg|rar|zip|Desktop"
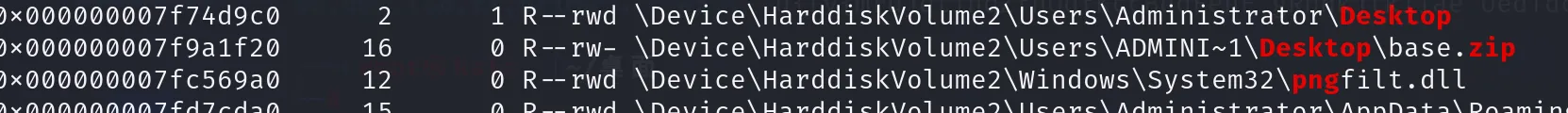
找到压缩包
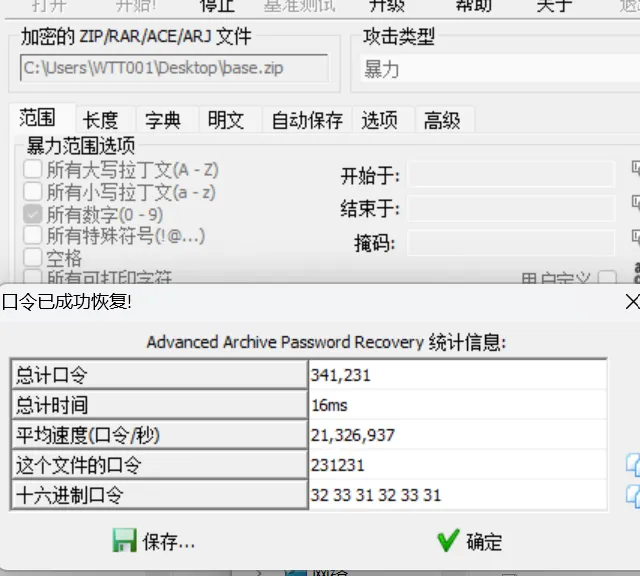
密码爆破
u3=LEnoG9HX2fJPVyIUpjax+8CSqsBOYWmzekwA1Z5grM0F/6DTNhQb4dKlR7tivc
得到这个
考虑到需要base64换表
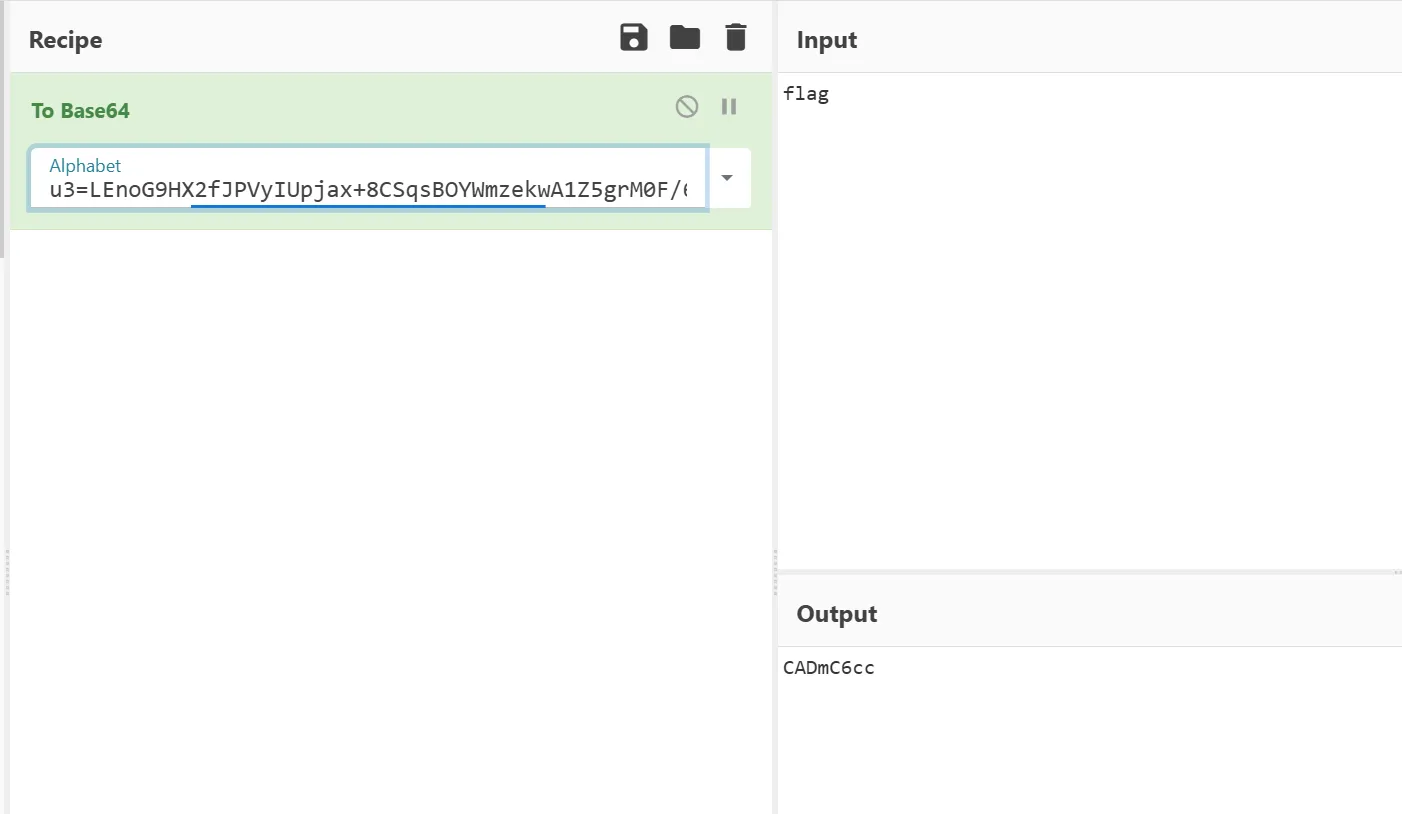
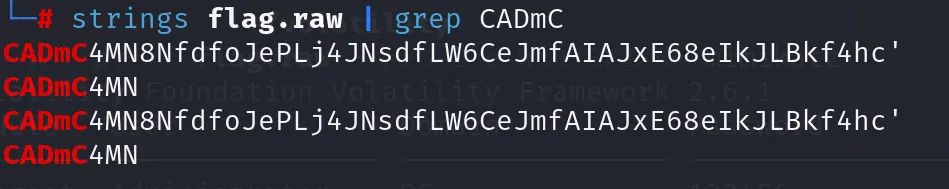
CADmC4MN8NfdfoJePLj4JNsdfLW6CeJmfAIAJxE68eIkJLBkf4hc
再解码
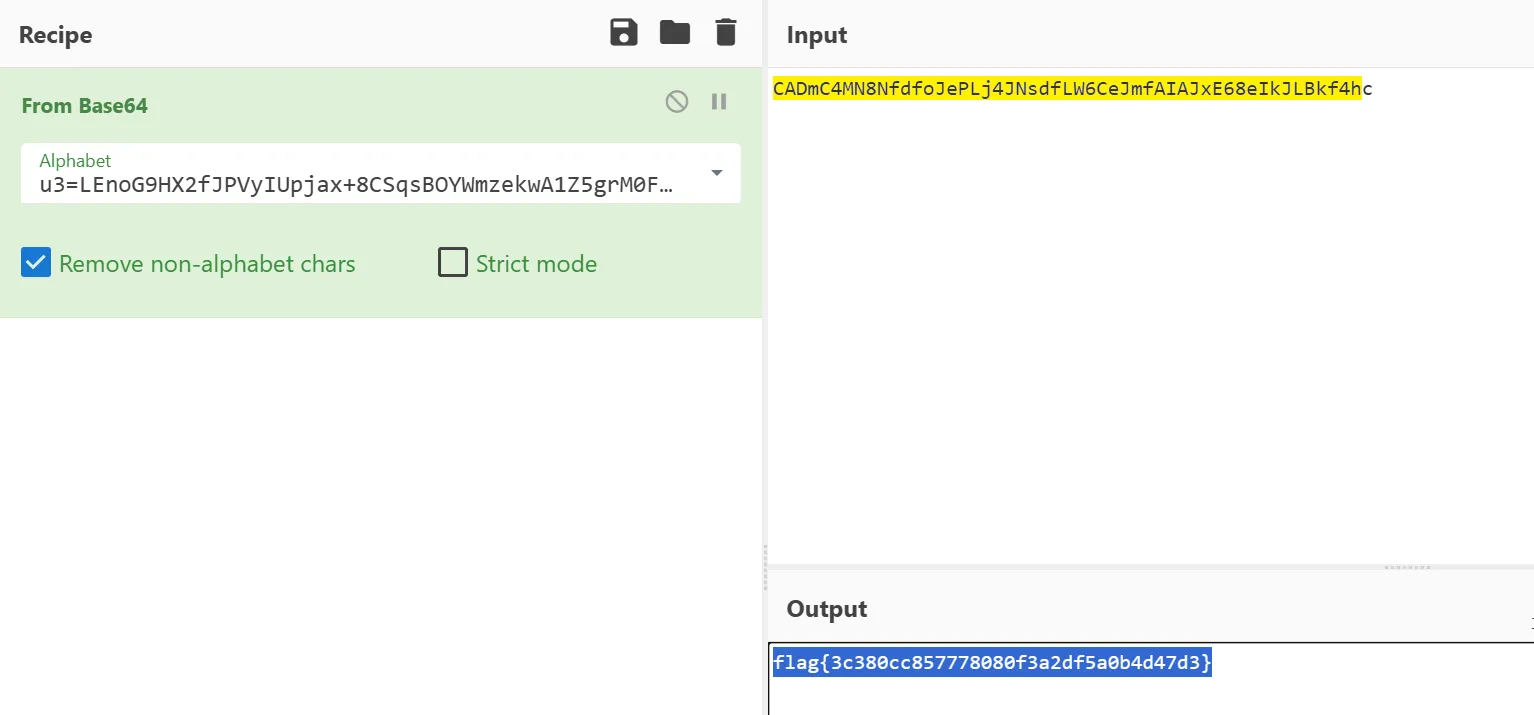
得到flag
flag{3c380cc857778080f3a2df5a0b4d47d3}
**Simple_steganography-pcb2024**
解压的rar文件用ntfsstreamseditor查看,发现有NTFS流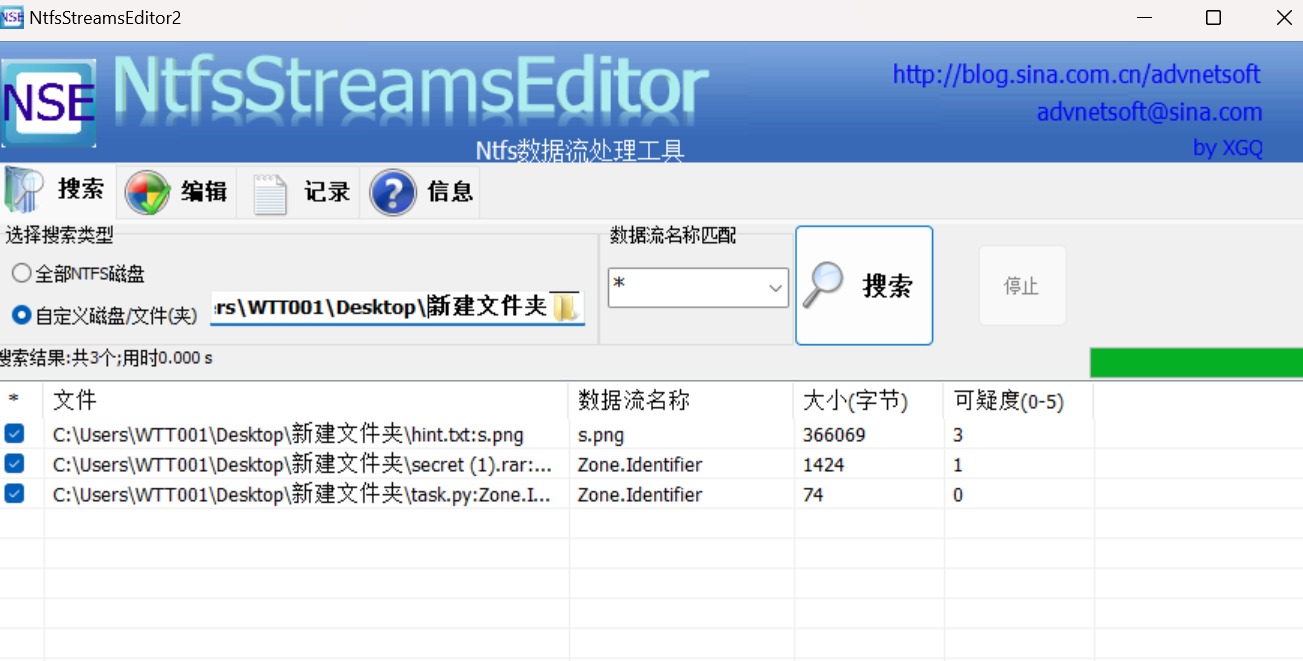
提取出来
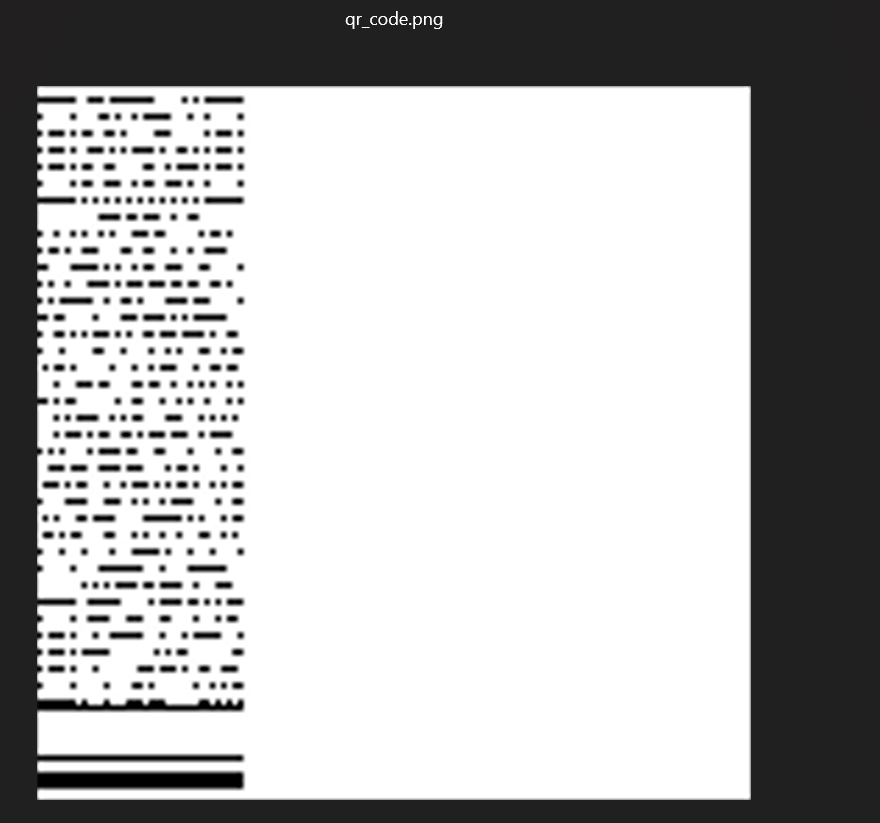
之后得到一个二维码
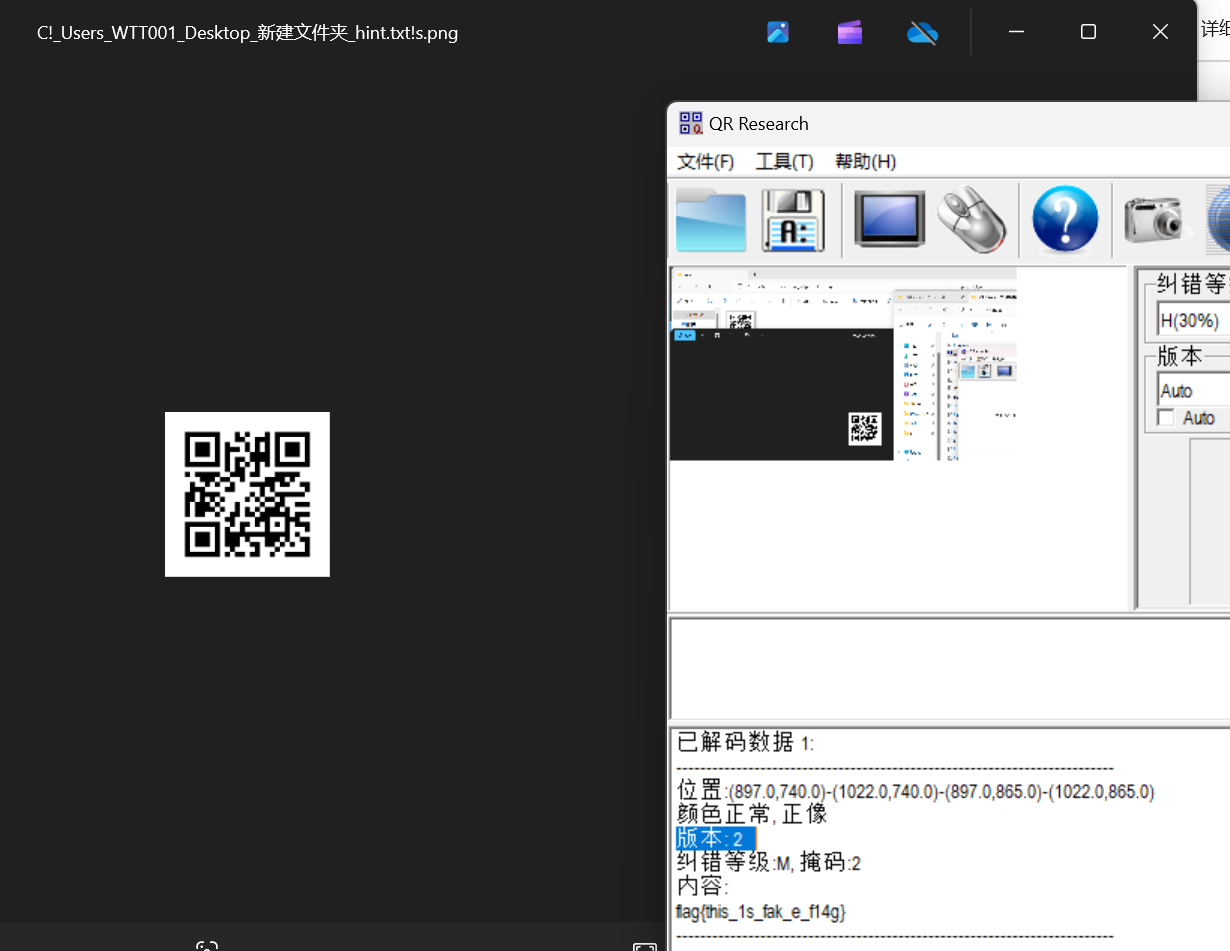
假的
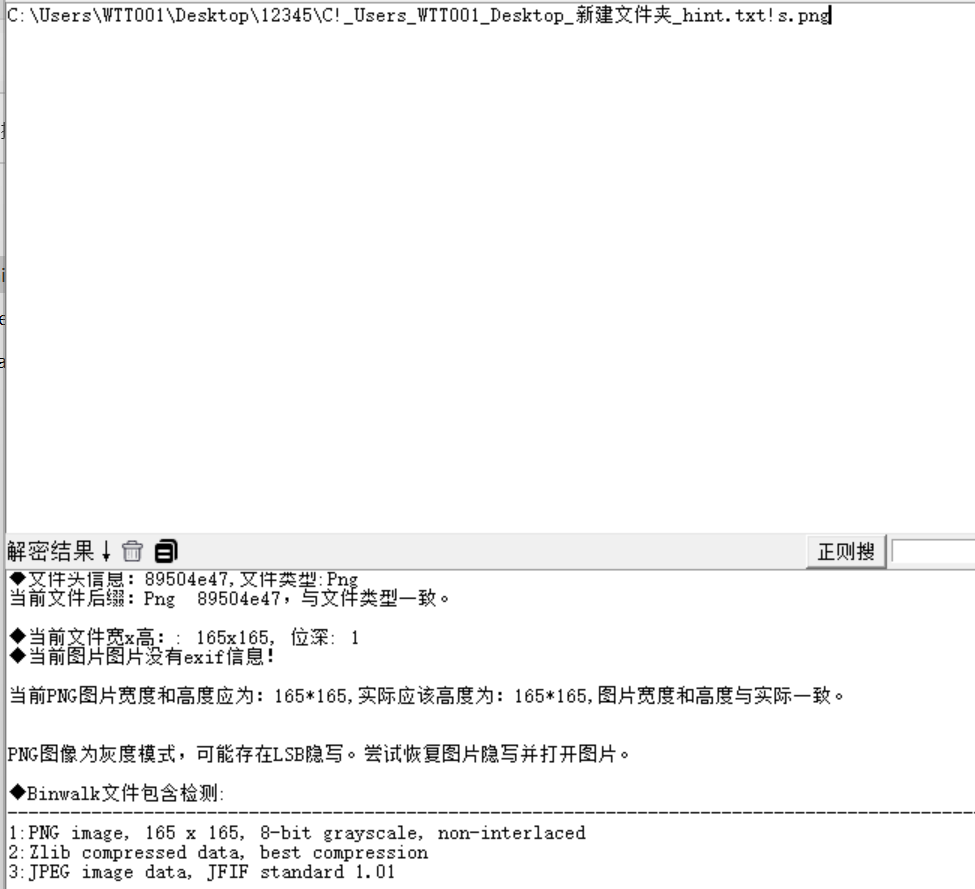
发现有隐藏图片,提取出来
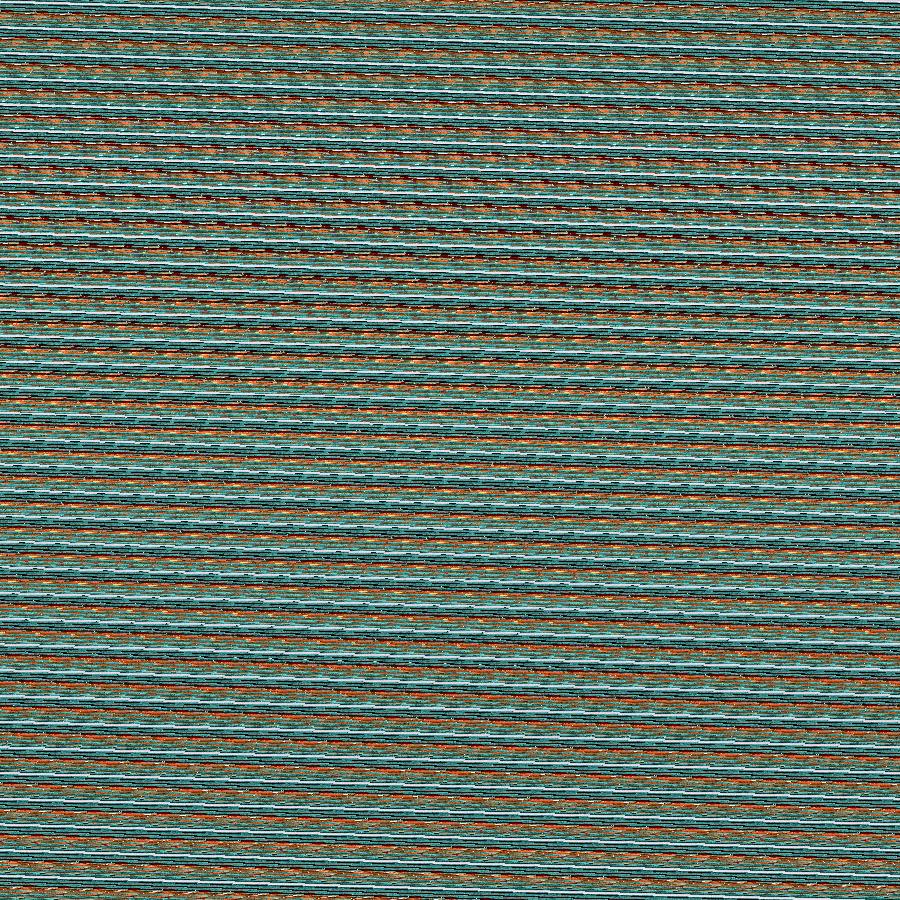
这张图片
hint.txt,里面是a=7,b=35
用脚本
from PIL import Imagedef arnold(infile: str, outfile: str = None, a: int = 1, b: int = 1, shuffle_times: int = 1, reverse: bool = False) -> None:"""Arnold猫脸变换函数Parameters:infile - 输入图像路径outfile - 输出图像路径a - Anrold 变换参数b - Anrold 变换参数shuffle_times - 置乱次数reverse - 逆变换"""inimg = Image.open(infile)width, height = inimg.sizeindata = inimg.load()outimg = Image.new(inimg.mode, inimg.size)outdata = outimg.load()for _ in range(shuffle_times):for x in range(width):for y in range(height):if reverse:nx = ((a * b + 1) * x - a * y) % widthny = (y - b * x) % heightelse:nx = (x + a * y) % widthny = (b * x + (a * b + 1) * y) % heightoutdata[ny, nx] = indata[y, x]outimg.save(outfile if outfile else "arnold_"+infile, inimg.format)arnold("flag.jpg", "decode.jpg", 7, 35, 1, True)
解出来得到第二部分flag
再用bkcrack进行明文攻击
echo 89504E470D0A1A0A0000000D49484452 | xxd -r -ps > png_header
bkcrack.exe -C secret.zip -c flag.png -p png_header -o 0
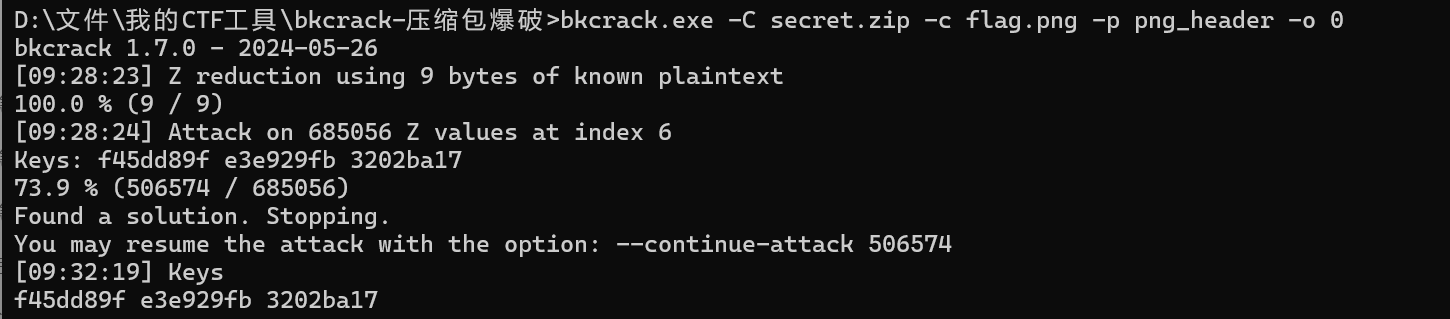
更改密码
bkcrack.exe -C secret.zip -K f45dd89f e3e929fb 3202ba17 -U flag.zip 123456
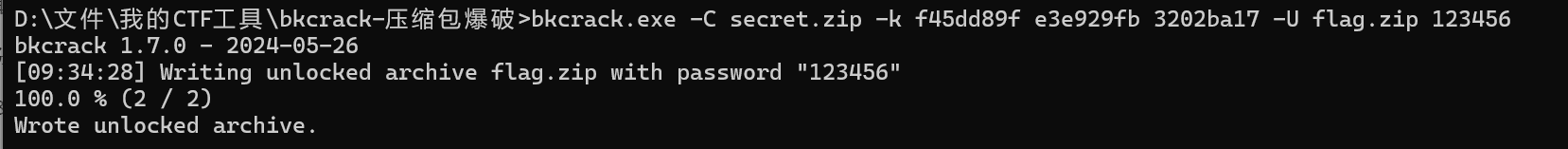
跑出来了,解压然后图片改宽高得到第一部分的flag

We_l1k3_h4ck1ng