参考视频:
【BUUCTF】每天一个CTF11“2019红帽杯easyRe”_哔哩哔哩_bilibili
(本人觉得看视频比看博客效率能提高十倍,呜呜呜,还是视频香~~~与君共勉)
下载地址:
BUUCTF在线评测
前言:虽然带有easy,但是并不是那么easy。CTF偏向于算法,实战偏向于程序逻辑,执行的流程
刷题所得:
AB键将转伪代码,与空格键配合使用
0→字符串的结束标志,查看字符串结尾
Shift+e:导出数据,提取数据
X;交叉引用,寻找哪个函数用了这段数据
*号键:可以创建数组,规定数组大小
题解:
1.ida64打开

(建议多看汇编,少看伪代码 )


(CTF解题大概就在这个函数里面了)

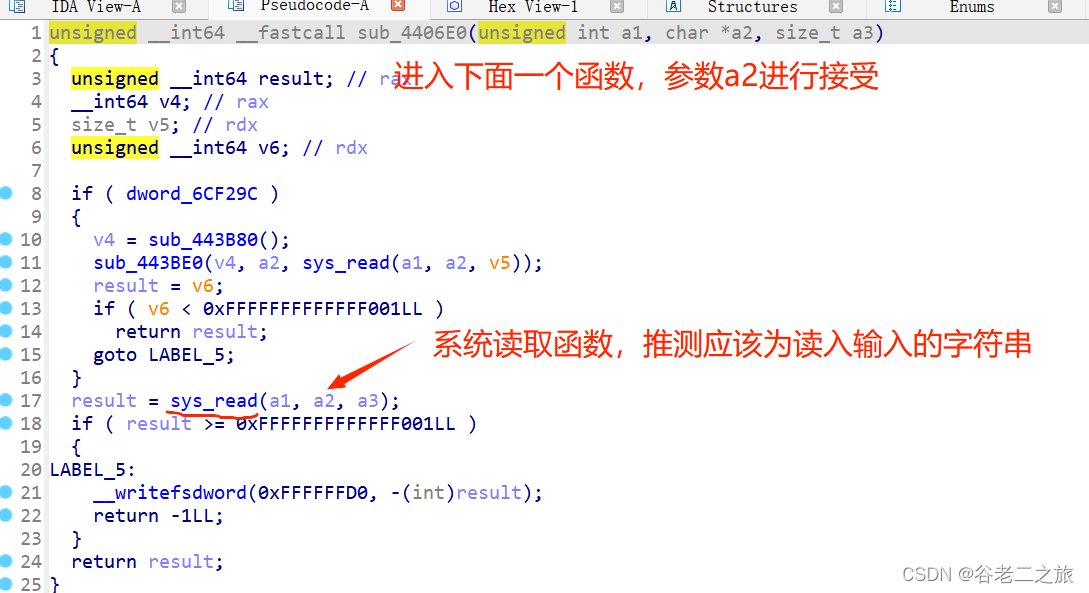
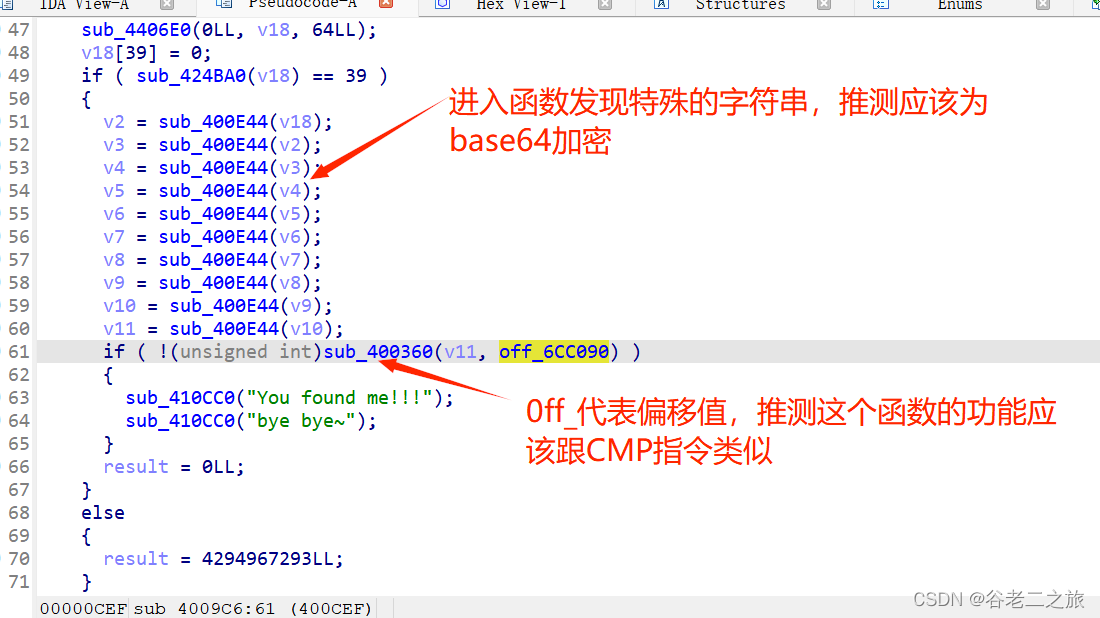 (推测flag可能在off_6CC090中)
(推测flag可能在off_6CC090中)
进入off_6CC090,进行base64解密
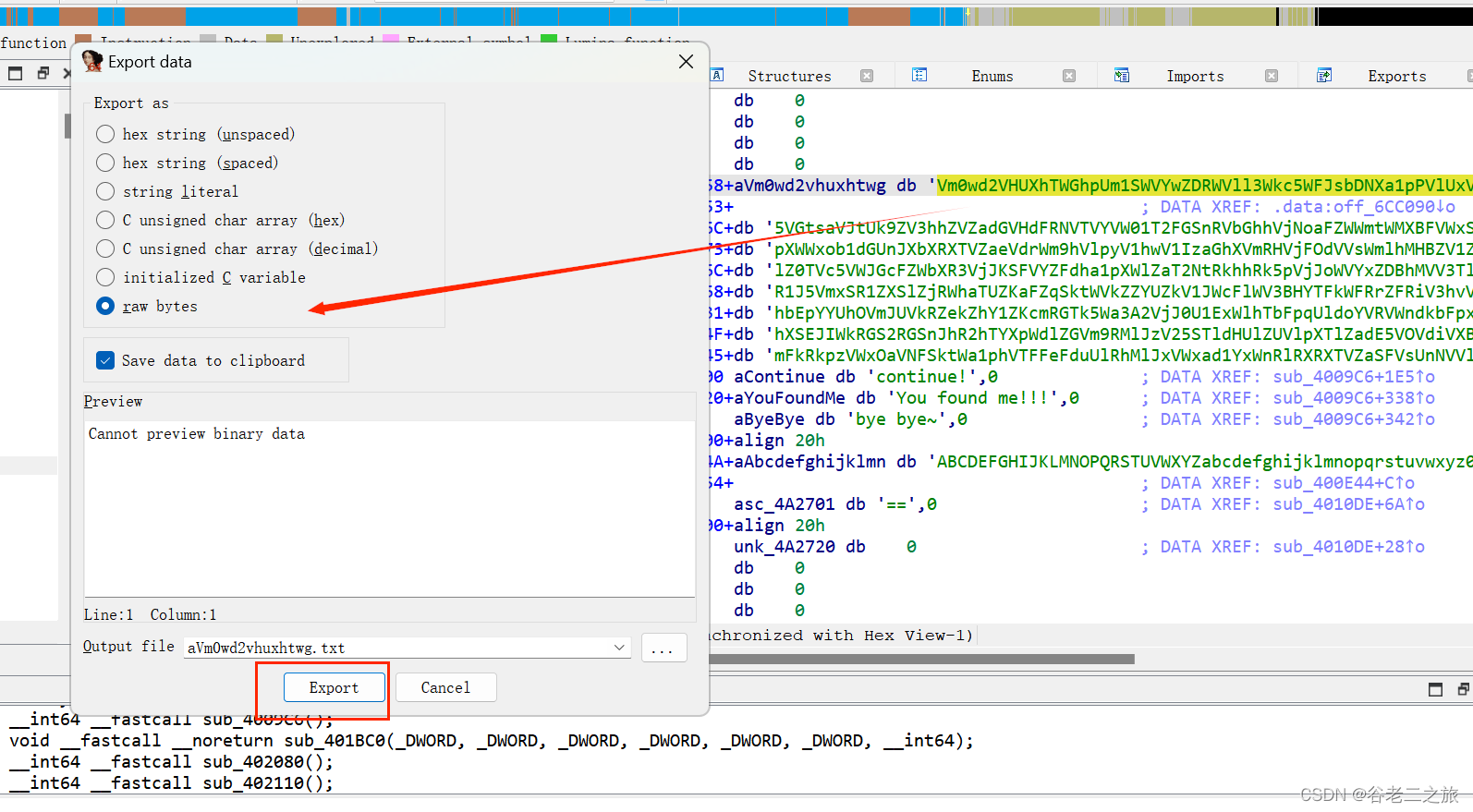
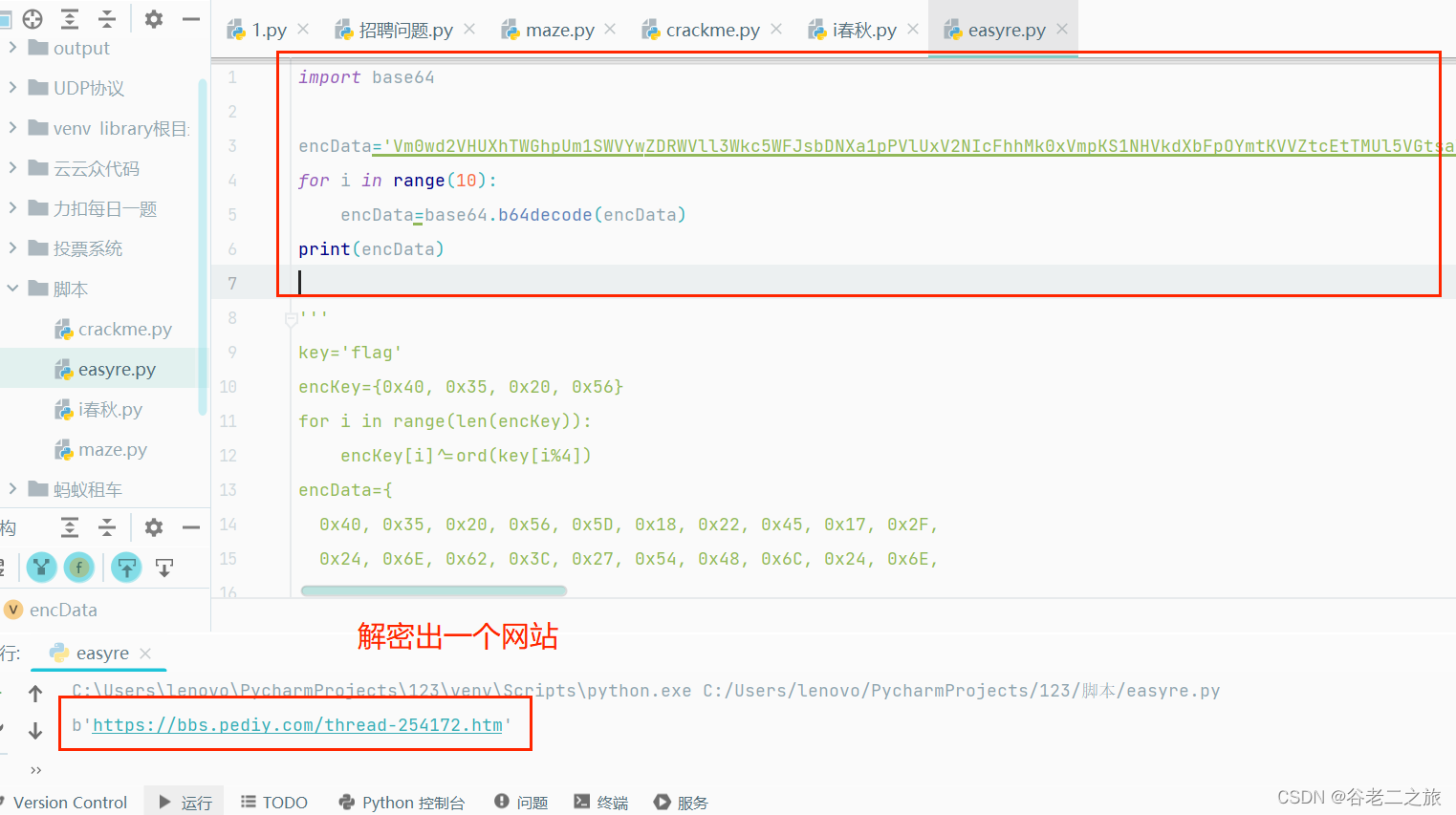
import base64encData='Vm0wd2VHUXhTWGhpUm1SWVYwZDRWVll3Wkc5WFJsbDNXa1pPVlUxV2NIcFhhMk0xVmpKS1NHVkdXbFpOYmtKVVZtcEtTMUl5VGtsaVJtUk9ZV3hhZVZadGVHdFRNVTVYVW01T2FGSnRVbGhhVjNoaFZWWmtWMXBFVWxSTmJFcElWbTAxVDJGV1NuTlhia0pXWWxob1dGUnJXbXRXTVZaeVdrWm9hVlpyV1hwV1IzaGhXVmRHVjFOdVVsWmlhMHBZV1ZSR1lWZEdVbFZTYlhSWFRWWndNRlZ0TVc5VWJGcFZWbXR3VjJKSFVYZFdha1pXWlZaT2NtRkhhRk5pVjJoWVYxZDBhMVV3TlhOalJscFlZbGhTY1ZsclduZGxiR1J5VmxSR1ZXSlZjRWhaTUZKaFZqSktWVkZZYUZkV1JWcFlWV3BHYTFkWFRrZFRiV3hvVFVoQ1dsWXhaRFJpTWtsM1RVaG9hbEpYYUhOVmJUVkRZekZhY1ZKcmRGTk5Wa3A2VjJ0U1ExWlhTbFpqUldoYVRVWndkbFpxUmtwbGJVWklZVVprYUdFeGNHOVhXSEJIWkRGS2RGSnJhR2hTYXpWdlZGVm9RMlJzV25STldHUlZUVlpXTlZadE5VOVdiVXBJVld4c1dtSllUWGhXTUZwell6RmFkRkpzVWxOaVNFSktWa1phVTFFeFduUlRhMlJxVWxad1YxWnRlRXRXTVZaSFVsUnNVVlZVTURrPQ== '
for i in range(10):encData=base64.b64decode(encData)
print(encData)然后怎么办呢?遇到了困难,请教别人,别人根据经验.........

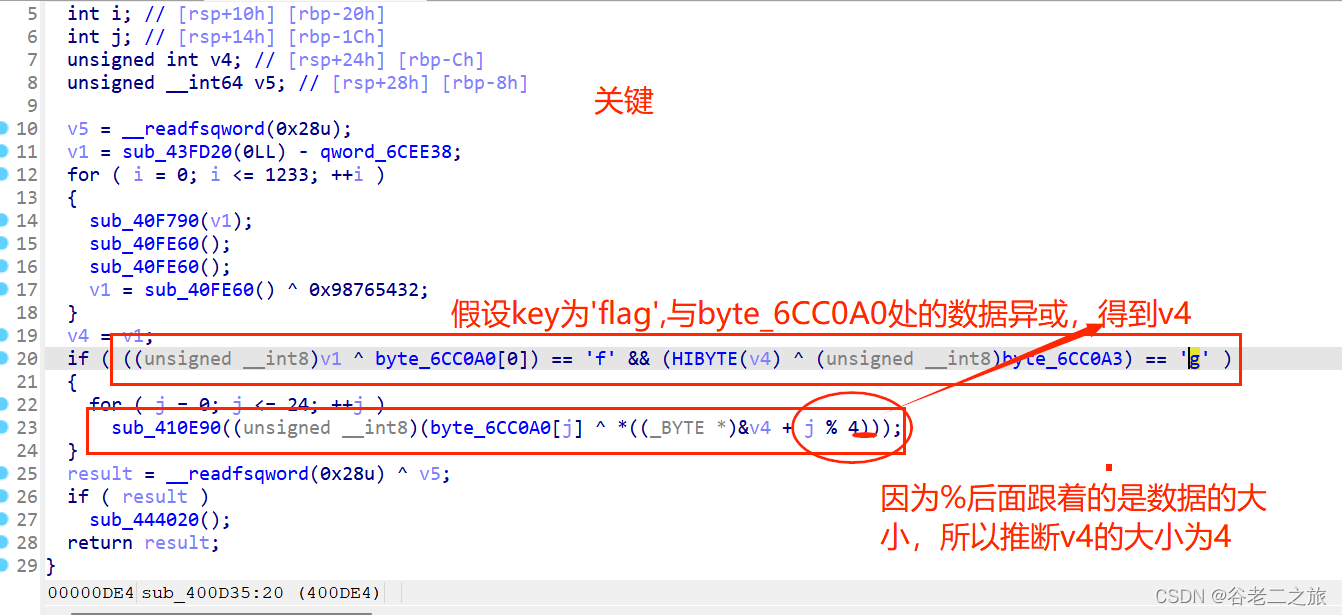
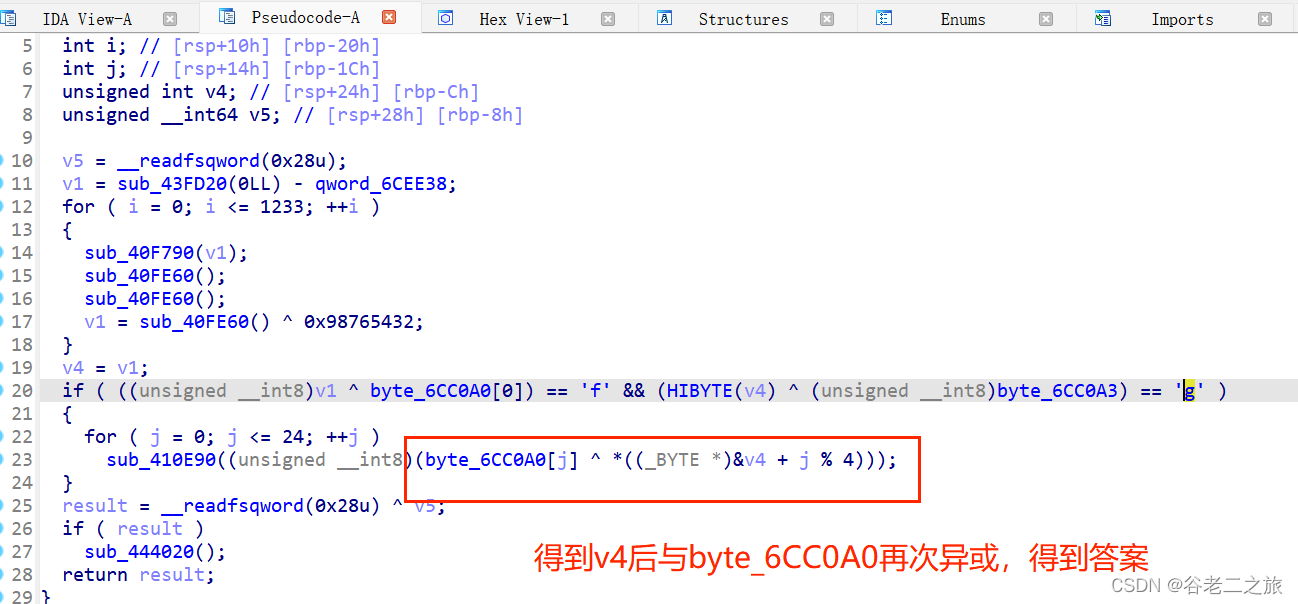
(从flag开始 两次异或)
key='flag'
encKey=[0x40, 0x35, 0x20, 0x56]
for i in range(len(encKey)):encKey[i]^=ord(key[i%4])
encData=[0x40, 0x35, 0x20, 0x56, 0x5D, 0x18, 0x22, 0x45, 0x17, 0x2F,0x24, 0x6E, 0x62, 0x3C, 0x27, 0x54, 0x48, 0x6C, 0x24, 0x6E,0x72, 0x3C, 0x32, 0x45, 0x5B
]
for i in range(len(encData)):print(chr(encData[i]^encKey[i%4]),end='')
#flag{Act1ve_Defen5e_Test}