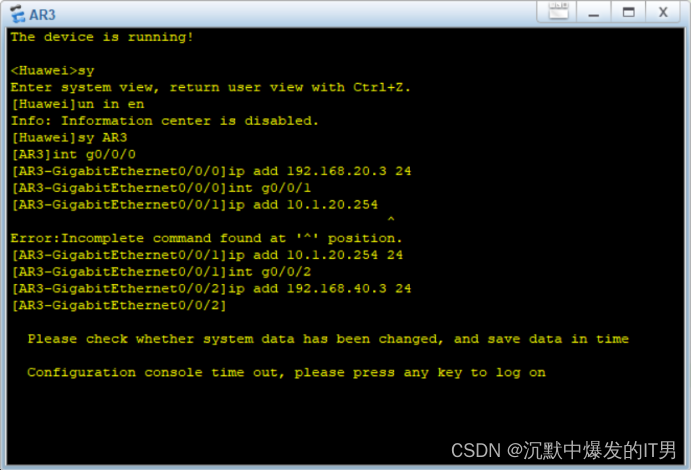



查看接口配置display ip interface brief

<AR1>display ip interface brief
*down: administratively down
^down: standby
(l): loopback
(s): spoofing
The number of interface that is UP in Physical is 4
The number of interface that is DOWN in Physical is 0
The number of interface that is UP in Protocol is 4
The number of interface that is DOWN in Protocol is 0
Interface IP Address/Mask Physical Protocol
GigabitEthernet0/0/0 192.168.10.1/24 up up
GigabitEthernet0/0/1 10.1.10.254/24 up up
GigabitEthernet0/0/2 192.168.30.1/24 up up
NULL0 unassigned up up(s)
<AR2>display ip interface brief
*down: administratively down
^down: standby
(l): loopback
(s): spoofing
The number of interface that is UP in Physical is 4
The number of interface that is DOWN in Physical is 0
The number of interface that is UP in Protocol is 4
The number of interface that is DOWN in Protocol is 0
Interface IP Address/Mask Physical Protocol
GigabitEthernet0/0/0 192.168.10.2/24 up up
GigabitEthernet0/0/1 192.168.20.2/24 up up
GigabitEthernet0/0/2 60.222.227.130/24 up up
NULL0 unassigned up up(s)
<AR3>display ip interface brief
*down: administratively down
^down: standby
(l): loopback
(s): spoofing
The number of interface that is UP in Physical is 4
The number of interface that is DOWN in Physical is 0
The number of interface that is UP in Protocol is 4
The number of interface that is DOWN in Protocol is 0
Interface IP Address/Mask Physical Protocol
GigabitEthernet0/0/0 192.168.20.3/24 up up
GigabitEthernet0/0/1 10.1.20.254/24 up up
GigabitEthernet0/0/2 192.168.40.3/24 up up
NULL0 unassigned up up(s)
<AR4>display ip interface brief
*down: administratively down
^down: standby
(l): loopback
(s): spoofing
The number of interface that is UP in Physical is 2
The number of interface that is DOWN in Physical is 2
The number of interface that is UP in Protocol is 2
The number of interface that is DOWN in Protocol is 2
Interface IP Address/Mask Physical Protocol
GigabitEthernet0/0/0 60.222.227.1/24 up up
GigabitEthernet0/0/1 unassigned down down
GigabitEthernet0/0/2 unassigned down down
NULL0 unassigned up up(s)
<AR5>display ip interface brief
*down: administratively down
^down: standby
(l): loopback
(s): spoofing
The number of interface that is UP in Physical is 3
The number of interface that is DOWN in Physical is 1
The number of interface that is UP in Protocol is 3
The number of interface that is DOWN in Protocol is 1
Interface IP Address/Mask Physical Protocol
GigabitEthernet0/0/0 192.168.30.5/24 up up
GigabitEthernet0/0/1 192.168.40.5/24 up up
GigabitEthernet0/0/2 unassigned down down
NULL0 unassigned up up(s)
防环检测配置
[AR1]interface LoopBack 0
[AR1-LoopBack0]ip address 1.1.1.1 32
[AR1-LoopBack0]quit
[AR1]quit
<AR1>save
[AR2]interface LoopBack 0
[AR2-LoopBack0]ip address 2.2.2.2 32
[AR2-LoopBack0]quit
[AR2]quit
<AR2>save
[AR3]interface LoopBack 0
[AR3-LoopBack0]ip address 3.3.3.3 32
[AR3-LoopBack0]quit
[AR3]quit
<AR3>save
[AR4]interface LoopBack 0
[AR4-LoopBack0]ip address 4.4.4.4 32
[AR4-LoopBack0]quit
[AR4]quit
<AR4>save
[AR5]interface LoopBack 0
[AR5-LoopBack0]ip address 5.5.5.5 32
[AR5-LoopBack0]quit
[AR5]quit
<AR5>save
配置ospf
[AR1]ospf 1 router-id 1.1.1.1
[AR1-ospf-1-area-0.0.0.0]network 192.168.10.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]network 192.168.30.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]network 10.1.10.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]network 1.1.1.1 0.0.0.0
[AR1-ospf-1-area-0.0.0.0]quit
[AR1-ospf-1]quit
[AR1]quit
<AR1>save
[AR2]ospf 1 router-id 2.2.2.2
[AR2-ospf-1-area-0.0.0.0]network 192.168.10.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]network 192.168.20.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]network 2.2.2.2 0.0.0.0
[AR2-ospf-1-area-0.0.0.0]quit
[AR2-ospf-1]quit
[AR2]quit
<AR2>save
[AR3]ospf 1 router-id 3.3.3.3
[AR3-ospf-1]area 0
[AR3-ospf-1-area-0.0.0.0]network 192.168.10.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]network 192.168.40.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]network 10.1.20.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]network 3.3.3.3 0.0.0.0
[AR3-ospf-1-area-0.0.0.0]quit
[AR3-ospf-1]quit
[AR3]quit
<AR3>save
[AR5]ospf 1 router-id 5.5.5.5
[AR5-ospf-1]area 0
[AR5-ospf-1-area-0.0.0.0]network 192.168.30.0 0.0.0.255
[AR5-ospf-1-area-0.0.0.0]network 192.168.40.0 0.0.0.255
[AR5-ospf-1-area-0.0.0.0]network 5.5.5.5 0.0.0.0
[AR5-ospf-1-area-0.0.0.0]quit
[AR5-ospf-1]quit
[AR5]quit
<AR5>save
通信测试
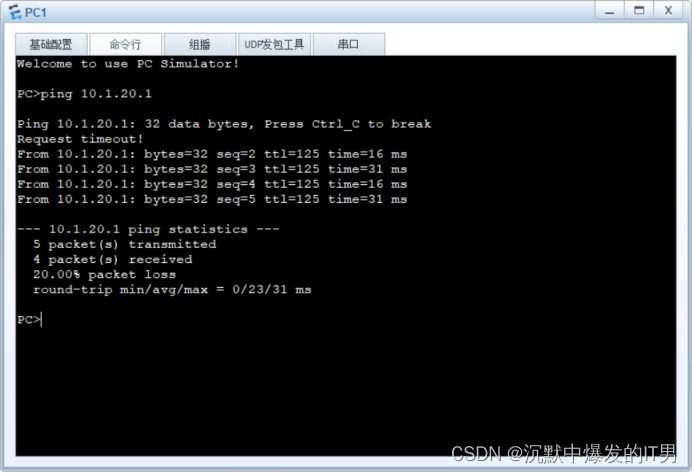
display ip routing-table protocol ospf查看ospf路由表

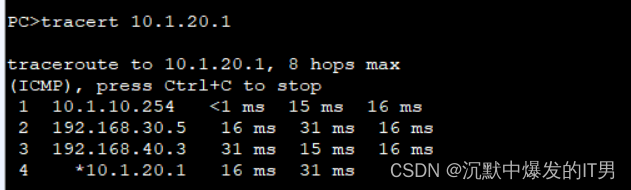
tracert 查看路由节点
dis cur查看全局配置

<AR1>dis cur
[V200R003C00]
#
sysname AR1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 192.168.10.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.1.10.254 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 192.168.30.1 255.255.255.0
#
interface NULL0
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 10.1.10.0 0.0.0.255
network 192.168.10.0 0.0.0.255
network 192.168.30.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<AR1>
<AR2>dis cur
[V200R003C00]
#
sysname AR2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 192.168.10.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.20.2 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 60.222.227.130 255.255.255.0
#
interface NULL0
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 2.2.2.2 0.0.0.0
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<AR3>dis cur
[V200R003C00]
#
sysname AR3
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 192.168.20.3 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.1.20.254 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 192.168.40.3 255.255.255.0
#
interface NULL0
#
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
ospf 1 router-id 3.3.3.3
area 0.0.0.0
network 3.3.3.3 0.0.0.0
network 10.1.20.0 0.0.0.255
network 192.168.10.0 0.0.0.255
network 192.168.40.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<AR4>dis cur
[V200R003C00]
#
sysname AR4
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 60.222.227.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 4.4.4.4 255.255.255.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<AR5>dis cur
[V200R003C00]
#
sysname AR5
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 192.168.30.5 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.40.5 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 5.5.5.5 255.255.255.255
#
ospf 1 router-id 5.5.5.5
area 0.0.0.0
network 5.5.5.5 0.0.0.0
network 192.168.30.0 0.0.0.255
network 192.168.40.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return