支持检测及修复漏洞的列表
OpenSSL CVE-2021-3712
OpenSSH CVE-2021-41617
sudo CVE-2021-3156
glibc CVE-2018-11236
polkit CVE-2021-4034
wget CVE-2017-13090
kernel CVE-2016-5195
bash CVE-2016-7543
samba CVE-2021-44142
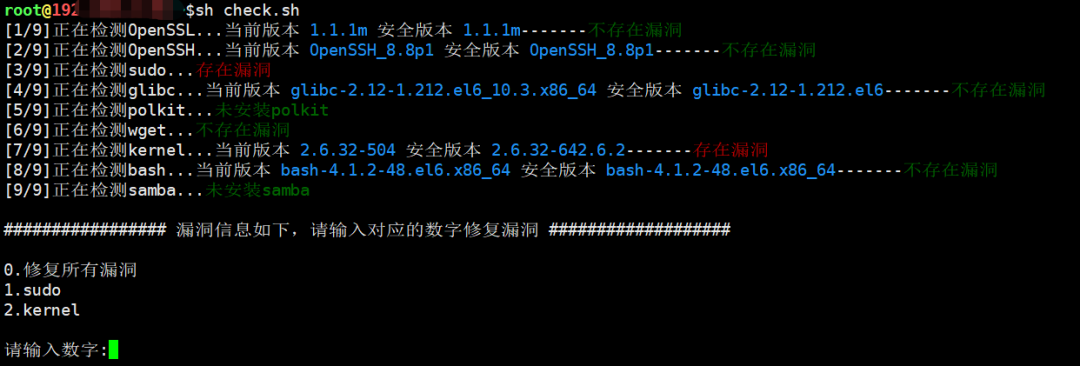
传入参数选项设置为No,自动升级设置为No,则根据提示输入相应的数字,修复漏洞,效果如下:
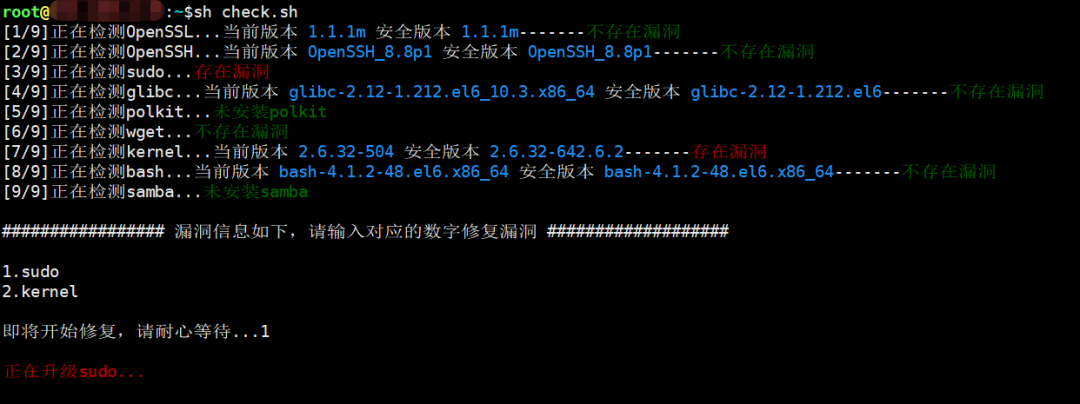
传入参数选项设置为No,自动升级设置为Yes,则无需干预,自动检测并修复漏洞,效果如下:
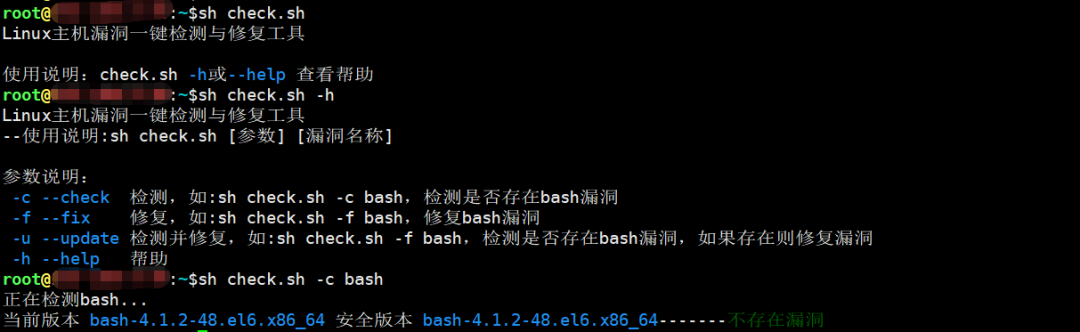
传入参数选项设置为Yes,则根据提示检测或修复漏洞,效果如下:
#!/bin/bash################################ Linux主机漏洞一键检测与修复工具 ###################################支持列表:
#OpenSSL CVE-2021-3712
#OpenSSH CVE-2021-41617
#sudo CVE-2021-3156
#glibc CVE-2018-11236
#polkit CVE-2021-4034
#wget CVE-2017-13090
#kernel CVE-2016-5195
#bash CVE-2016-7543
#samba CVE-2021-44142###支持系统:
#RedHat 6/7/8 x86_64
#CentOS 6/7/8 x86_64###使用须知
#1.RedHat/Centos7/8系统请配置好yum源,保持最新
#2.RedHat/Centos6系统由于yum源停止维护,故部分漏洞修复方式采用源码编译安装或者rpm包安装
#3.漏洞修复情况复杂,为防止意外,请先在测试环境进行测试
#4.编译安装OpenSSH和OpenSSL如出现编译失败会退出程序,需手动执行yum -y install gcc gcc-c++ automake autoconf libtool make zlib zlib-devel openssl-devel pam-devel
#5.传入参数选项开关,Yes为打开参数选项,No为关闭参数选项
#6.自动升级开关,Yes为检测后自动扫描,No为检测后手动输入###传入参数选项开关(Yes/No),默认为关
#ARGUMENT=Yes
ARGUMENT=No###自动升级开关(Yes/No),默认为关,当ARGUMENT=No时生效
#AUTO_UPDATE=Yes
AUTO_UPDATE=No#################################### 检测 ##################################### 检查当前账号是否为root
if [ $(id -u) != "0" ]; thenecho -e "\n\033[31m当前账号为: $(whoami),请切换至root账号\n\033[31m"exit 1
fi#升级包地址,可以将升级包放置内网环境,提高下载速度
OPENSSL_FILE='https://www.openssl.org/source/openssl-1.1.1m.tar.gz'
OPENSSH_FILE='https://cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-8.8p1.tar.gz'
SUDO_FILE='https://github.com/sudo-project/sudo/releases/download/SUDO_1_9_9/sudo-1.9.9-1.el6.x86_64.rpm'#操作系统版本判断
SYS_VERSION=`cat /etc/redhat-release | tr -cd "[0-9.]" | cut -c1`
SYS_VERSION_DE=`cat /etc/redhat-release | tr -cd "[0-9.]" | cut -c1-3`#初始化序号
NUM=0#OpenSSL检测
Check_OpenSSL()
{
P=OpenSSL
#C=`rpm -qa openssl`
#C=`openssl version|awk '{print $2}'|awk -F'-' '{print $1}'`if [ "$SYS_VERSION" == '6' -o "$SYS_VERSION" == '7' -o "$SYS_VERSION" == '8' ];thenif [ "$SYS_VERSION" == '6' ];thenC=`openssl version|awk '{print $2}'|awk -F'-' '{print $1}'`D='1.1.1m'elif [ "$SYS_VERSION" == '7' ];thenC=`rpm -qa openssl`D='openssl-1.0.2k-24.el7_9.x86_64'elif [ "$SYS_VERSION" == '8' ];thenC=`rpm -qa openssl`D='openssl-1.1.1k-5.el8_5.x86_64'fiecho -n -e "当前版本 \033[34m$C\033[0m ""安全版本 \033[34m$D\033[0m-------"RES=`echo -e "$D\n$C" | sort -V | head -n 1`if [ $C == $D ]; thenecho -e "\033[32m不存在漏洞\033[0m"elif [ $C != $RES ]; thenecho -e "\033[32m不存在漏洞\033[0m"elseecho -e "\033[31m存在漏洞\033[0m"NUM=$[$NUM+1]VUL=$PVUL_RES=$VUL_RES""$NUM.$P"\n"fi
elseecho -e "\033[33m检测失败,请检查系统版本\033[0m"
fi
}#OpenSSH检测
Check_OpenSSH()
{
P=OpenSSH
C=`ssh -V 2>&1 | awk -F',' '{print $1}'`
D='OpenSSH_8.8p1'echo -n -e "当前版本 \033[34m$C\033[0m ""安全版本 \033[34m$D\033[0m-------"
RES=`echo -e "$D\n$C" | sort -V | head -n 1`
if [ $C == $D ]; thenecho -e "\033[32m不存在漏洞\033[0m"
elif [ $C != $RES ]; thenecho -e "\033[32m不存在漏洞\033[0m"
elseecho -e "\033[31m存在漏洞\033[0m"NUM=$[$NUM+1]VUL=$PVUL_RES=$VUL_RES""$NUM.$P"\n"
fi
}#sudo检测
Check_sudo()
{
P=sudosudoedit -s / 2>&1 | grep regular > /dev/null
if [ $? == '0' ];thenecho -e "\033[31m存在漏洞\033[0m"NUM=$[$NUM+1]VUL=$PVUL_RES=$VUL_RES""$NUM.$P"\n"
elseecho -e "\033[32m不存在漏洞\033[0m"
fi
}#glibc检测
Check_glibc()
{
P=glibc
C=`rpm -qa glibc | grep 64`if [ "$SYS_VERSION_DE" == '6.6' -o "$SYS_VERSION_DE" == '6.8' -o "$SYS_VERSION" == '7' ];thenif [ "$SYS_VERSION_DE" == '6.6' ];thenD='glibc-2.12-1.212.el6'elif [ "$SYS_VERSION_DE" == '6.8' ];thenD='glibc-2.12-1.212.0.1.el6'elif [ "$SYS_VERSION" == '7' ];thenD='glibc-2.17-260.el7'fiecho -n -e "当前版本 \033[34m$C\033[0m ""安全版本 \033[34m$D\033[0m-------"RES=`echo -e "$D\n$C" | sort -V | head -n 1`if [ $C == $D ]; thenecho -e "\033[32m不存在漏洞\033[0m"elif [ $C != $RES ]; thenecho -e "\033[32m不存在漏洞\033[0m"elseecho -e "\033[31m存在漏洞\033[0m"NUM=$[$NUM+1]VUL=$PVUL_RES=$VUL_RES""$NUM.$P"\n"fielif [ "$SYS_VERSION" == '8' ];thenecho -e "\033[32m不存在漏洞\033[0m"
elseecho -e "\033[33m检测失败,请检查系统版本\033[0m"
fi
}#wget检测
Check_wget()
{
P=wget
C=`rpm -qa wget`rpm -qa wget | grep wget > /dev/null
if [ $? == '0' ];thenif [ "$SYS_VERSION" == '6' -o "$SYS_VERSION" == '7' -o "$SYS_VERSION" == '8' ];thenif [ "$SYS_VERSION" == '7' ];thenD='wget-1.14-15.el7_4.1'echo -n -e "当前版本 \033[34m$C\033[0m ""安全版本 \033[34m$D\033[0m-------"RES=`echo -e "$D\n$C" | sort -V | head -n 1`if [ $C == $D ]; thenecho -e "\033[32m不存在漏洞\033[0m"elif [ $C != $RES ]; thenecho -e "\033[32m不存在漏洞\033[0m"elseecho -e "\033[31m存在漏洞\033[0m"NUM=$[$NUM+1]VUL=$PVUL_RES=$VUL_RES""$NUM.$P"\n"fielseecho -e "\033[32m不存在漏洞\033[0m"fielseecho -e "\033[33m检测失败,请检查系统版本\033[0m"fi
elseecho -e "\033[32m未安装wget\033[0m"
fi
}#polkit检测
Check_polkit()
{
P=polkit
C=`rpm -qa polkit`if [ -f /usr/bin/pkexec ];thenls -al /usr/bin/pkexec | grep -e \-rwx > /dev/nullif [ $? == '0' ];thenecho -e "\033[32m漏洞已经临时修复\033[0m"elseif [ "$SYS_VERSION" == '6' -o "$SYS_VERSION" == '7' -o "$SYS_VERSION_DE" == '8.0' -o "$SYS_VERSION_DE" == '8.2' -o "$SYS_VERSION_DE" == '8.4' ];thenif [ "$SYS_VERSION" == '6' ];thenD='polkit-0.96-11.el6_10.2'elif [ "$SYS_VERSION" == '7' ];thenD='polkit-0.112-26.el7_9.1'elif [ "$SYS_VERSION_DE" == '8.0' ];thenD='polkit-0.115-13.el8_5.1'elif [ "$SYS_VERSION_DE" == '8.2' ];thenD='polkit-0.115-11.el8_2.2'elif [ "$SYS_VERSION_DE" == '8.4' ];thenD='polkit-0.115-11.el8_4.2'fiecho -n -e "当前版本 \033[34m$C\033[0m ""安全版本 \033[34m$D\033[0m-------"RES=`echo -e "$D\n$C" | sort -V | head -n 1`if [ $C == $D ]; thenecho -e "\033[32m不存在漏洞\033[0m"elif [ $C != $RES ]; thenecho -e "\033[32m不存在漏洞\033[0m"elseecho -e "\033[31m存在漏洞\033[0m"NUM=$[$NUM+1]VUL=$PVUL_RES=$VUL_RES""$NUM.$P"\n"fielseecho -e "\033[33m检测失败,请检查系统版本\033[0m"fifi
elseecho -e "\033[32m未安装polkit\033[0m"
fi
}#kernel检测
Check_kernel()
{
P=kernelif [ "$SYS_VERSION" == '6' -o "$SYS_VERSION" == '7' ];thenif [ "$SYS_VERSION" == '6' ];thenC=`uname -r | sed "s/.el6.x86_64//"`D='2.6.32-642.6.2'elif [ "$SYS_VERSION" == '7' ];thenC=`uname -r | sed "s/.el7.x86_64//"`D='3.10.0-327.36.3'fiecho -n -e "当前版本 \033[34m$C\033[0m ""安全版本 \033[34m$D\033[0m-------"RES=`echo -e "$D\n$C" | sort -V | head -n 1`if [ $C == $D ]; thenecho -e "\033[32m不存在漏洞\033[0m"elif [ $C != $RES ]; thenecho -e "\033[32m不存在漏洞\033[0m"elseecho -e "\033[31m存在漏洞\033[0m"NUM=$[$NUM+1]VUL=$PVUL_RES=$VUL_RES""$NUM.$P"\n"fielif [ "$SYS_VERSION" == '8' ];thenecho -e "\033[32m不存在漏洞\033[0m"
elseecho -e "\033[33m检测失败,请检查系统版本\033[0m"
fi
}#bash检测
Check_bash()
{
P=bash
C=`rpm -qa bash`if [ "$SYS_VERSION" == '6' -o "$SYS_VERSION" == '7' ];thenif [ "$SYS_VERSION" == '6' ];thenD='bash-4.1.2-48.el6.x86_64'elif [ "$SYS_VERSION" == '7' ];thenD='bash-4.2.46-28.el7.x86_64'fiecho -n -e "当前版本 \033[34m$C\033[0m ""安全版本 \033[34m$D\033[0m-------"RES=`echo -e "$D\n$C" | sort -V | head -n 1`if [ $C == $D ]; thenecho -e "\033[32m不存在漏洞\033[0m"elif [ $C != $RES ]; thenecho -e "\033[32m不存在漏洞\033[0m"elseecho -e "\033[31m存在漏洞\033[0m"NUM=$[$NUM+1]VUL=$PVUL_RES=$VUL_RES""$NUM.$P"\n"fielif [ "$SYS_VERSION" == '8' ];thenecho -e "\033[32m不存在漏洞\033[0m"
elseecho -e "\033[33m检测失败,请检查系统版本\033[0m"
fi
}#samba检测
Check_samba()
{
P=sambaC=`rpm -qa | grep -e ^samba-[0-9]`
if [ $? == '0' ];thenif [ "$SYS_VERSION" == '7' -o "$SYS_VERSION" == '8' ];thenif [ "$SYS_VERSION" == '7' ];thenD='samba-4.10.16-18.el7_9.x86_64'elif [ "$SYS_VERSION" == '8' ];thenD='samba-4.14.5-9.el8_5.s390x.rpm'fiecho -n -e "当前版本 \033[34m$C\033[0m ""安全版本 \033[34m$D\033[0m-------"RES=`echo -e "$D\n$C" | sort -V | head -n 1`if [ $C == $D ]; thenecho -e "\033[32m不存在漏洞\033[0m"elif [ $C != $RES ]; thenecho -e "\033[32m不存在漏洞\033[0m"elseecho -e "\033[31m存在漏洞\033[0m"NUM=$[$NUM+1]VUL=$PVUL_RES=$VUL_RES""$NUM.$P"\n"fielif [ "$SYS_VERSION" == '6' ];thenecho -e "\033[32m不存在漏洞\033[0m"elseecho -e "\033[33m检测失败,请检查系统版本\033[0m"fi
elseecho -e "\033[32m未安装samba\033[0m"
fi
}#################################### 修复 #######################################OpenSSL升级
Fix_OpenSSL()
{
#echo -e "\n\n\033[31m正在升级OpenSSL...\033[0m\n\n"if [ "$SYS_VERSION" == '7' -o "$SYS_VERSION" == '8' ];thenyum -y install openssl
elif [ "$SYS_VERSION" == '6' ];thenNEW_OPENSSL_VERSION='1.1.1m'#下载新版OpenSSLcd /usr/local/src/#wget不检测证书wget --no-check-certificate $OPENSSL_FILEif [ -f "openssl-${NEW_OPENSSL_VERSION}.tar.gz" ];thentar zxf openssl-$NEW_OPENSSL_VERSION.tar.gzcd openssl-$NEW_OPENSSL_VERSION./config shared zlib-dynamic --prefix=/usr/local/opensslmake && make installif [ $? -eq 0 ]; thenecho -e "\n\033[32mOpenSSL编译安装成功\033[0m"#备份证书文件和秘钥文件mv /usr/bin/openssl /usr/bin/openssl.oldmv /usr/include/openssl /usr/include/openssl.old#替换原openssl文件ln -s /usr/local/openssl/bin/openssl /usr/bin/opensslln -s /usr/local/openssl/include/openssl /usr/include/openssl#在/etc/ld.so.conf文件中写入openssl库文件的搜索路径echo "/usr/local/openssl/lib" >> /etc/ld.so.confldconfig -velseecho -e "\n\033[31mOpenSSL编译安装失败\033[0m\n"exit 1fielseecho -e "\n\033[31m未检测到OpenSSL安装包\033[0m\n"fi
fi
}###OpenSSH升级
Fix_OpenSSH()
{
#echo -e "\n\n\033[31m正在升级OpenSSH...\033[0m\n\n"
NEW_OPENSSH_NAME='openssh-8.8p1'#下载新版OpenSSH
cd /usr/local/src/
wget $OPENSSH_FILEif [ -f $NEW_OPENSSH_NAME.tar.gz ];then#备份sshmv /etc/ssh /usr/local/src/sshtar zxf $NEW_OPENSSH_NAME.tar.gzcd $NEW_OPENSSH_NAME./configure --prefix=/usr --sysconfdir=/etc/ssh --with-md5-passwords --with-pam --with-tcp-wrappers --with-ssl-dir=/usr/local/openssl --with-zlib=/usr/local/lib64 --without-hardeningmake && make installif [ $? -eq 0 ]; thenecho -e "\n\033[32mOpenSSH安装成功\033[0m\n"#复制文件到系统服务目录cp -rf /usr/local/src/$NEW_OPENSSH_NAME/contrib/redhat/sshd.init /etc/init.d/sshdcp -rf /usr/local/src/$NEW_OPENSSH_NAME/contrib/redhat/sshd.pam /etc/pam.d/sshd.pam#添加执行权限chmod +x /etc/init.d/sshd#移除原服务,防止有时重启后ssh无法启动if [ -f "/usr/lib/systemd/system/sshd.service" ];thenmv /usr/lib/systemd/system/sshd.service /usr/lib/systemd/system/sshd.service.bakfi#开启UsePAMsed -i 's/#UsePAM no/UsePAM yes/g' /etc/ssh/sshd_config#重新启动openssh、添加启动项if [ "$SYS_VERSION" == '7' -o "$SYS_VERSION" == '8' ];thensystemctl daemon-reloadsystemctl restart sshdelif [ "$SYS_VERSION" == '6' ];thenservice sshd restartchkconfig --add sshdchkconfig sshd onfielseecho -e "\n\033[31mOpenSSH编译安装失败\033[0m\n"mv /usr/local/src/ssh /etc/ssh exit 1fi
elseecho -e "\n\033[31m未检测到OpenSSH安装包\033[0m\n"
fi
}###sudo升级
Fix_sudo()
{
if [ "$SYS_VERSION" == '6' ];thenSUDO_FILE_6=`echo $SUDO_FILE | awk -F"/" '{print $NF}'`if [ -f $SUDO_FILE_6 ];thenwget $SUDO_FILEcp /etc/sudoers /etc/sudoers.bakrpm -e sudorpm -ivh $SUDO_FILE_6mv /etc/sudoers /etc/sudoers.new.bakcp /etc/sudoers.bak /etc/sudoersrm -f $SUDO_FILE_6elseecho -e "\n\033[31m未检测到sudo安装包\033[0m\n"fi
elif [ "$SYS_VERSION" == '7' -o "$SYS_VERSION" == '8' ];thenyum install -y sudo
fi
}###glibc升级
Fix_glibc()
{
yum install -y glibc
}###wget升级
Fix_wget()
{
yum install -y wget
}###polkit升级
Fix_polkit()
{
if [ "$SYS_VERSION" == '6' ];thenchmod 0755 /usr/bin/pkexec
elseyum install -y polkit
fi
}###kernel升级
Fix_kernel()
{yum install -y kernel*
}###bash升级
Fix_bash()
{yum install -y bash
}###samba升级
Fix_samba()
{yum install -y samba
}################################### 检测项 ####################################检测项加入数组
D=(
OpenSSL
OpenSSH
sudo
glibc
polkit
wget
kernel
bash
samba
)################################## 参数选项 ##################################if [ "$ARGUMENT" == 'Yes' ];thenif [ $# == '0' ];thenecho -e "Linux主机漏洞一键检测与修复工具"echo -e "\r"echo -e "使用说明:$0\033[34m -h\033[0m或\033[34m--help\033[0m 查看帮助"elif [ $# == '1' ];thenif [ "$1" == "-c" -o "$1" == '--check' ];thenecho -e " \033[34m-c --check\033[0m 检测,如:sh $0 -c bash,检测是否存在bash漏洞"elif [ "$1" == "-f" -o "$1" == '--fix' ];thenecho -e " \033[34m-f --fix\033[0m 修复,如:sh $0 -f bash,修复bash漏洞"elif [ "$1" == "-f" -o "$1" == '--fix' ];thenecho -e " \033[34m-u --update\033[0m 检测并修复,如:sh $0 -f bash,检测是否存在bash漏洞,如果存在则修复漏洞"elif [ "$1" == "-h" -o "$1" == '--help' ];thenecho -e "Linux主机漏洞一键检测与修复工具"echo -e "--使用说明:sh $0 [参数] [漏洞名称]"echo -e "\r"echo -e "参数说明:"echo -e " \033[34m-c --check\033[0m 检测,如:sh $0 -c bash,检测是否存在bash漏洞"echo -e " \033[34m-f --fix\033[0m 修复,如:sh $0 -f bash,修复bash漏洞"echo -e " \033[34m-u --update\033[0m 检测并修复,如:sh $0 -f bash,检测是否存在bash漏洞,如果存在则修复漏洞"echo -e " \033[34m-h --help\033[0m 帮助"elseecho -e "Linux主机漏洞一键检测与修复工具"echo -e "\r"echo -e "使用说明:$0\033[34m -h\033[0m或\033[34m--help\033[0m 查看帮助"fielif [ $# == '2' ];then INFO=`echo "${D[@]}" | grep -wq $2`if [ "$?" == "0" ];thenif [ "$1" == "-c" -o "$1" == "--check" ];thenecho "正在检测$2..."Check_$2elif [ "$1" == "-f" -o "$1" == "--fix" ];then echo "正在升级$2..."Fix_$2elif [ "$1" == "-u" -o "$1" == "--update" ];thenecho -e "\n\033[31m正在升级$2...\033[0m\n"Fix_$2echo -e "\n重新检测中...\n"Check_$2elseecho -e "Linux主机漏洞一键检测与修复工具"echo -e "\r"echo -e "使用说明:$0\033[34m -h\033[0m或\033[34m--help\033[0m 查看帮助"fielif [ "$?" == "1" -a "$1" == "-c" -o "$1" == "--check" -o "$1" == "-f" -o "$1" == "--fix" -o "$1" == "-u" -o "$1" == "--update" ];thenecho "$2 漏洞信息未收录"elseecho -e "Linux主机漏洞一键检测与修复工具"echo -e "\r"echo -e "使用说明:$0\033[34m -h\033[0m或\033[34m--help\033[0m 查看帮助"fielseecho -e "Linux主机漏洞一键检测与修复工具"echo -e "\r"echo -e "使用说明:$0\033[34m -h\033[0m或\033[34m--help\033[0m 查看帮助"fielif [ "$ARGUMENT" == 'No' ];then###检测函数调用#获取数组长度L_ARR=${#D[*]}#遍历数组for ((i=0; i<$L_ARR; i++))doeval echo -e -n [$[$i+1]/$L_ARR]echo -e -n "正在检测${D[i]}..."Check_${D[i]}done###漏洞修复#获取行数INFO_LINE=`echo -e $VUL_RES | wc -l`#判断是否存在漏洞if [[ $INFO_LINE > 1 ]]; thenecho -e "\n################# 漏洞信息如下,请输入对应的数字修复漏洞 ###################\n"if [ "$AUTO_UPDATE" == 'Yes' ];thenecho -e $VUL_RESTIME=5while [[ $TIME > 0 ]]doecho -n -e "\r"echo -n -e "即将开始修复,请耐心等待..."echo -ne $TIME(( TIME-- ))sleep 1done#遍历修复for ((i=1; i<$INFO_LINE; i++))doINFO=`echo -e $VUL_RES | grep $i | awk -F. '{print $2}'`echo -e "\n\n\033[31m正在升级$INFO...\033[0m\n\n"Fix_$INFOdone#重新检测echo -e "\n重新检测中...\n"for ((i=1; i<$INFO_LINE; i++))doINFO=`echo -e $VUL_RES | grep $i | awk -F. '{print $2}'`echo -e -n "正在检测$INFO..."Check_$INFOdoneelse#只存在一个漏洞情况 if [[ $INFO_LINE == 2 ]]; thenecho -e $VUL_RESread -p "请输入数字:" numberINFO=`echo -e $VUL_RES | grep $number | awk -F. '{print $2}'`#判断输入if [[ $number == 1 ]] ;thenFix_$INFOecho -e "\n重新检测中...\n"Check_$INFOelseecho -e "\n输入错误\n"fi#存在多个漏洞情况 elseecho -e "0.修复所有漏洞\n"$VUL_RESread -p "请输入数字:" number#判断输入if [[ $number =~ ^[0-9]*$ ]] && [[ $number < $INFO_LINE ]] ;thenINFO=`echo -e $VUL_RES | grep $number | awk -F. '{print $2}'`if [ "$number" == "0" ]; thenecho "正在修复所有漏洞,请耐心等待..."#遍历修复for ((i=1; i<$INFO_LINE; i++))doINFO=`echo -e $VUL_RES | grep $i | awk -F. '{print $2}'`echo -e "\n\n\033[31m正在升级$INFO...\033[0m\n\n"Fix_$INFOdone#重新检测echo -e "\n重新检测中...\n"for ((i=1; i<$INFO_LINE; i++))doINFO=`echo -e $VUL_RES | grep $i | awk -F. '{print $2}'`echo -e -n "正在检测$INFO..."Check_$INFOdoneelseecho -e "\n\n\033[31m正在升级$INFO...\033[0m\n\n"Fix_$INFOecho -e "\n重新检测中...\n"echo -e -n "正在检测$INFO..."Check_$INFOfielseecho -e "\n输入错误\n"fifififi
fi