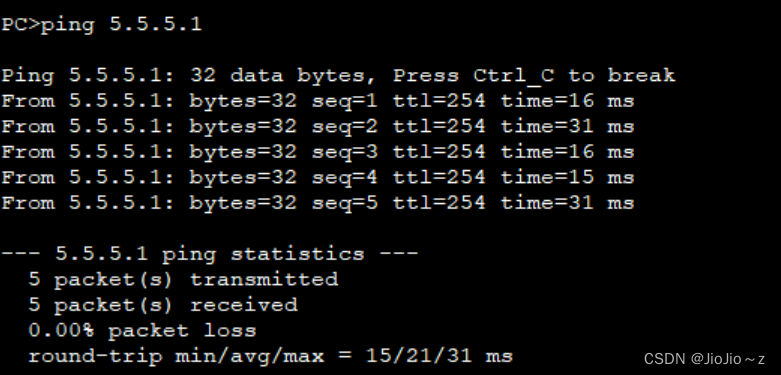
一、实验拓扑
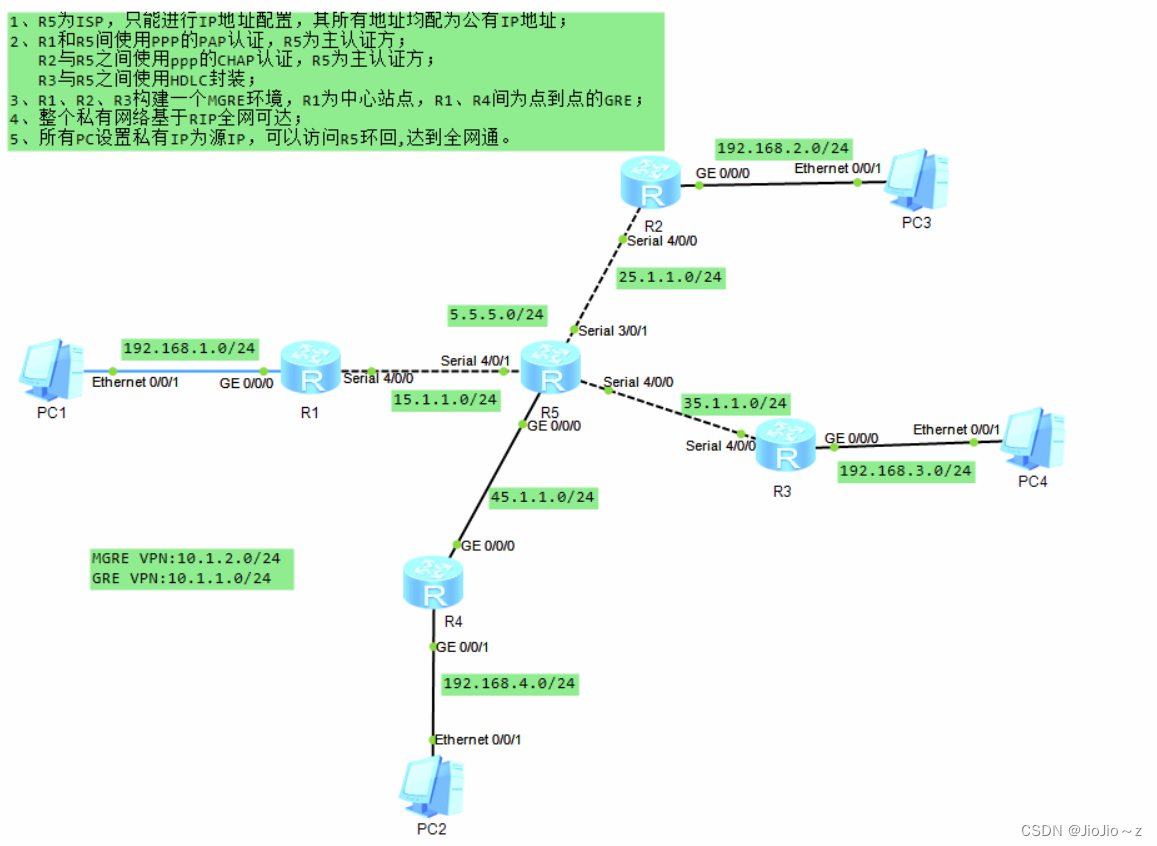
二、实验划分
三、实验需求
四、实验结果
1.配置各端口和pc的IP:
pc1:
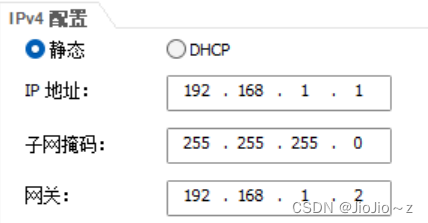
pc2:

pc3:
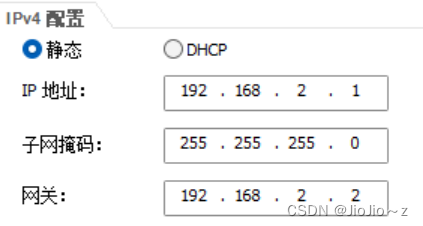
pc4:
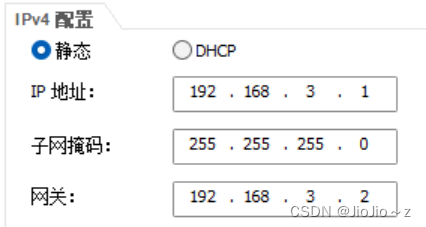
R1:
[r1]inter g0/0/0
[r1-GigabitEthernet0/0/0]ip ad 192.168.1.2 24
[r1-GigabitEthernet0/0/0]int s4/0/0
[r1-Serial4/0/0]ip ad 15.1.1.1 24R2:
[r2]inter g0/0/0
[r2-GigabitEthernet0/0/0]ip ad 192.168.2.2 24
[r2-GigabitEthernet0/0/0]int s4/0/0
[r2-Serial4/0/0]ip ad 25.1.1.2 24R3:
[r3]int g0/0/0
[r3-GigabitEthernet0/0/0]ip ad 192.168.3.2 24
[r3-GigabitEthernet0/0/0]int s4/0/0
[r3-Serial4/0/0]ip ad 35.1.1.3 24R4:
[r4]int g0/0/1
[r4-GigabitEthernet0/0/1]ip ad 192.168.4.2 24
[r4-GigabitEthernet0/0/1]int g0/0/0
[r4-GigabitEthernet0/0/0]ip ad 45.1.1.4 24R5:
[r5]int s4/0/1
[r5-Serial4/0/1]ip ad 15.1.1.5 24
[r5-Serial4/0/1]int s3/0/1
[r5-Serial3/0/1]ip ad 25.1.1.5 24
[r5-Serial3/0/1]int s4/0/0
[r5-Serial4/0/0]ip ad 35.1.1.5 24
[r5-Serial4/0/0]int g0/0/0
[r5-GigabitEthernet0/0/0]ip ad 45.1.1.5 24
[r5]int LoopBack 0
[r5-LoopBack0]ip ad 5.5.5.1 242.实现公私网通
公网通,配置静态缺省路由:
R1:
[r1]ip route-static 0.0.0.0 0 15.1.1.5R2:
[r2]ip route-static 0.0.0.0 0 25.1.1.5R3:
[r3]ip route-static 0.0.0.0 0 35.1.1.5R4:
[r4]ip route-static 0.0.0.0 0 45.1.1.53.R1和R5之间使用ppp的PAP认证,R5为主认证方;R2和R5之间使用ppp的CHAP认证,R5为主认证方;R3和R5之间使用HDLC封装
R1和R5之间:
R5:
[r5]aaa
[r5-aaa]local-user jio1 password cipher jio1123
[r5-aaa]local-user jio1 service-type ppp
[r5]inter s4/0/1
[r5-Serial4/0/1]ppp authentication-mode papR1:
[r1-Serial4/0/0]ppp pap local-user jiojio password cipher 123456R2和R5之间:
R5:
[r5]aaa
[r5-aaa]local-user duer password cipher 123456
[r5-aaa]local-user duer service-type ppp
[r5]int s3/0/1
[r5-Serial3/0/1]ppp authentication-mode chapR2:
[r2-Serial4/0/0]ppp chap user duer
[r2-Serial4/0/0]ppp chap password cipher 123456R3和R5之间使用HDLC封装:
R3:
[r3-Serial4/0/0]link-protocol hdlc
Warning: The encapsulation protocol of the link will be changed. Continue? [Y/N]
:y
R5:
[r5-Serial4/0/0]link-protocol hdlc
Warning: The encapsulation protocol of the link will be changed. Continue? [Y/N]
:y
4.R1~R3构建MGRE
R1:
[r1]int Tunnel 0/0/0
[r1-Tunnel0/0/0]ip address 10.1.2.1 24
[r1-Tunnel0/0/0]tunnel-protocol gre p2mp
[r1-Tunnel0/0/0]source 15.1.1.1
[r1-Tunnel0/0/0]nhrp network-id 100R2:
[r2]int Tunnel 0/0/0
[r2-Tunnel0/0/0]ip ad 10.1.2.2 24
[r2-Tunnel0/0/0]tunnel-protocol gre p2mp
[r2-Tunnel0/0/0]source s4/0/0
[r2-Tunnel0/0/0]nhrp network-id 100
[r2-Tunnel0/0/0]nhrp entry 10.1.2.1 15.1.1.1 registerR3:
[r3]int Tunnel 0/0/0
[r3-Tunnel0/0/0]ip ad 10.1.2.3 24
[r3-Tunnel0/0/0]tunnel-protocol gre p2mp
[r3-Tunnel0/0/0]source s4/0/0
[r3-Tunnel0/0/0]nhrp network-id 100
[r3-Tunnel0/0/0]nhrp entry 10.1.2.1 15.1.1.1 register
5.R1到R4之间配置GRE VPN
R1:
[r1]int Tunnel 0/0/1
[r1-Tunnel0/0/1]ip ad 10.1.1.1 24
[r1-Tunnel0/0/1]tunnel-protocol gre
[r1-Tunnel0/0/1]source 15.1.1.1
[r1-Tunnel0/0/1]destination 45.1.1.4
R4:
[r4]int t0/0/1
[r4-Tunnel0/0/1]ip ad 10.1.1.4 24
[r4-Tunnel0/0/1]tunnel-protocol gre
[r4-Tunnel0/0/1]source 45.1.1.4
[r4-Tunnel0/0/1]destination 15.1.1.16.RIP配置
R1:
[r1]rip 1
[r1-rip-1]version 2
[r1-rip-1]undo summary
[r1-rip-1]network 192.168.1.0
[r1-rip-1]network 10.0.0.0R2:
[r2]rip 1
[r2-rip-1]v 2
[r2-rip-1]undo summary
[r2-rip-1]network 192.168.2.0
[r2-rip-1]network 10.0.0.0R3:
[r3]rip 1
[r3-rip-1]v 2
[r3-rip-1]undo summary
[r3-rip-1]network 192.168.3.0
[r3-rip-1]network 10.0.0.0R4:
[r4]rip 1
[r4-rip-1]v 2
[r4-rip-1]undo summary
[r4-rip-1]network 192.168.4.0
[r4-rip-1]network 10.0.0.07.关闭水平分割
R1:
[r1]int Tunnel 0/0/0
[r1-Tunnel0/0/0]nhrp entry multicast dynamic
[r1-Tunnel0/0/0]undo rip split-horizon R2:
[r2]int Tunnel 0/0/0
[r2-Tunnel0/0/0]nhrp entry multicast dynamic
[r2-Tunnel0/0/0]undo rip split-horizon
R3:
[r3]int Tunnel 0/0/0
[r3-Tunnel0/0/0]nhrp entry multicast dynamic
[r3-Tunnel0/0/0]undo rip split-horizon 8.配置ACL
R1:
[r1]acl 2000
[r1-acl-basic-2000]rule permit source 192.168.1.1 0.0.0.255
[r1]int s4/0/0
[r1-Serial4/0/0]nat outbound 2000R2:
[r2]acl 2000
[r2-acl-basic-2000]rule permit source 192.168.2.1 0.0.0.255
[r2]int s4/0/0
[r2-Serial4/0/0]nat outbound 2000R3:
[r3]acl 2000
[r3-acl-basic-2000]rule permit source 192.168.3.1 0.0.0.255
[r3]int s4/0/0
[r3-Serial4/0/0]nat outbound 2000R4:
[r4]acl 2000
[r4-acl-basic-2000]rule permit source 192.168.4.1 0.0.0.255
[r4]int g0/0/0
[r4-GigabitEthernet0/0/0]nat outbound 20009.测试